This general issue has been plaguing me for a couple of months. I first noticed it when trying to get a local virtual machine to fetch Python packages, so I already had an idea that certificates would be an issue. I solved it for my VMs, but hadn’t until today been able to work out a solution for Docker. The trick is to add the certificates to Docker’s cert store and have them persist. This is accomplished by using a bootlocal.sh script that executes every time the machine starts.
I assume if you’ve already found the answers for Linux, you already know the first steps. I will document them here for the sake of being thorough, because others may not have gotten this far. Start with #3 below if you’ve already done #1 and #2 by way of previous attempts.
-
Get the set of corporate root certificates, which should be installed in your corporate-configured browser. In Chrome, you can go to Settings, click Show advanced settings, and scroll down to HTTPS/SSL, where you can choose Manage Certificates. My organization has put them in Trusted Root Certification Authorities and named them after the organization. Export each (I have two), one at a time. You can either choose DER format and do step #2 below to convert to PEM, or you can choose Base-64 encoded x.509 (.CER) and simply rename the extension to .pem and skip step #2.
-
Once you have them saved to a known location, you will want to convert them to PEM format unless you save as duch. The easiest way I found to do this was to run the openssl.exe[1] command from within the Docker Quickstart Terminal.
openssl x509 -inform der -in certificate.cer -out certificate.pem -
Once you have the .pem files, you will want to copy them to a location to which your Docker machine has access to. Typically for MS Windows, you’ll have /c/Users of the host machine automatically mounted inside your docker machine. I made a directory in c:\Users\my.username\certs and copied them there.
-
This step may not be strictly necessary, but it’s what I did, and it works. You will want to copy those certificates into your boot2docker partition, which is persistent. I am connecting to my default machine, which IS something you will need to do for Step 5.
MINGW64:$ docker-machine ssh default docker@default:~$ sudo -s root@default:/home/docker# mkdir /var/lib/boot2docker/certs root@default:/home/docker# cp /c/Users/my.username/certs/*.pem /var/lib/boot2docker/certs/ -
Now it’s time to write a bootlocal.sh script, which will copy the certificates to the proper location each time the system starts.[2] If you haven’t already, open an SSH connection to the machine, per Step 4.
touch /var/lib/boot2docker/bootlocal.sh && chmod +x /var/lib/boot2docker/bootlocal.sh vi /var/lib/boot2docker/bootlocal.sh
Insert the following and save the file:
#!/bin/sh
mkdir -p /etc/docker/certs.d && cp /var/lib/boot2docker/certs/*.pem /etc/docker/certs.d
-
Restart the machine, either by using the reboot command from within the machine, or by using the docker-machine command from the Docker terminal:
docker-machine restart default
Now you should be able to run ‘hello-world’ and others.
Sources
[1] https://serverfault.com/questions/254627/how-to-convert-a-cer-file-in-pem
[2] https://github.com/boot2docker/boot2docker/issues/347#issuecomment-189112043
The «x509: certificate signed by unknown authority» error in Golang HTTP is a common issue faced by developers when making secure connections to a server over HTTPS. This error occurs because Go does not trust the certificate presented by the server by default, leading to a failure to establish a secure connection. The root cause of this error can be the absence of the server’s root certificate in the local trust store or the certificate being signed by an untrusted certificate authority (CA).
Method 1: Setting Environment Variables
Here are the steps to fix the «x509: certificate signed by unknown authority» error in Golang HTTP on Windows using Environment Variables:
- Open the Windows start menu and search for «Environment Variables».
- Click on «Edit the system environment variables» and then click on the «Environment Variables» button.
- Under the «System Variables» section, click on the «New» button.
- In the «Variable name» field, enter «SSL_CERT_FILE».
- In the «Variable value» field, enter the path to the root certificate file. For example, «C:\Program Files\Git\mingw64\ssl\certs\ca-bundle.crt».
- Click «OK» to save the new environment variable.
- Restart your command prompt or IDE to apply the changes.
Here is an example code snippet that uses the updated environment variable to make an HTTPS request:
package main
import (
"crypto/tls"
"fmt"
"io/ioutil"
"net/http"
)
func main() {
// Create a new HTTP client with custom TLS config
tr := &http.Transport{
TLSClientConfig: &tls.Config{InsecureSkipVerify: true},
}
client := &http.Client{Transport: tr}
// Make HTTPS request
resp, err := client.Get("https://example.com")
if err != nil {
fmt.Println(err)
return
}
defer resp.Body.Close()
// Read response body
body, err := ioutil.ReadAll(resp.Body)
if err != nil {
fmt.Println(err)
return
}
// Print response body
fmt.Println(string(body))
}In this example, the TLSClientConfig is set to skip certificate verification. This is not recommended in production environments, but can be useful for testing and development purposes.
Method 2: Modifying the source code
To fix the «x509: certificate signed by unknown authority» error in Golang HTTP on Windows by modifying the source code, follow these steps:
- Import the crypto/tls package and add the following code to your main function:
http.DefaultTransport.(*http.Transport).TLSClientConfig = &tls.Config{InsecureSkipVerify: true}This will configure the default transport to skip certificate verification.
- Replace the http.Get() method with your own custom method that uses the default transport with certificate verification disabled:
func myGet(url string) (*http.Response, error) {
client := &http.Client{
Transport: &http.Transport{
TLSClientConfig: &tls.Config{InsecureSkipVerify: true},
},
}
return client.Get(url)
}- Use your custom method instead of http.Get() to make HTTP requests:
resp, err := myGet("https://example.com")This will make the request using your custom method with certificate verification disabled.
Note: Disabling certificate verification can make your application vulnerable to man-in-the-middle attacks. Use this solution only if you trust the server you are connecting to and are unable to obtain a valid certificate.
Method 3: Using a CA Bundle
If you are encountering a Golang HTTP x509: certificate signed by unknown authority error on Windows, you can fix it by using a CA bundle. This error occurs when the server’s SSL certificate is not recognized by your system. Here are the steps to fix it using a CA bundle.
Step 1: Download the CA Bundle
Download the CA bundle from a trusted source. You can download the Mozilla CA Bundle from here.
Step 2: Import the CA Bundle
Import the CA bundle into your Go program using the crypto/x509 package.
package main
import (
"crypto/tls"
"crypto/x509"
"net/http"
)
func main() {
// Load the CA bundle
caCert, err := ioutil.ReadFile("path/to/ca-bundle.crt")
if err != nil {
panic(err)
}
// Create a certificate pool and add the CA bundle to it
caCertPool := x509.NewCertPool()
caCertPool.AppendCertsFromPEM(caCert)
// Create a TLS configuration with the certificate pool
tlsConfig := &tls.Config{
RootCAs: caCertPool,
}
// Create a HTTPS client with the TLS configuration
httpClient := &http.Client{
Transport: &http.Transport{
TLSClientConfig: tlsConfig,
},
}
// Use the HTTPS client to make requests
resp, err := httpClient.Get("https://example.com")
if err != nil {
panic(err)
}
defer resp.Body.Close()
// Handle the response
// ...
}Step 3: Use the HTTPS Client
Use the HTTPS client to make requests to the server. The TLS configuration will use the CA bundle to verify the server’s SSL certificate.
// Use the HTTPS client to make requests
resp, err := httpClient.Get("https://example.com")
if err != nil {
panic(err)
}
defer resp.Body.Close()
// Handle the response
// ...That’s it! You have successfully fixed the Golang HTTP x509: certificate signed by unknown authority error on Windows using a CA bundle.
I encountered this error when moving my Azure Pipeline from Linux (ubuntu-latest) to windows (windows-latest). The pipeline tries to connect to a self-hosted Artifactory Server – but the error is a generic one and can occur with any Services that runs SSL with certificates from certain certificate authorities. In my case it was Quo Vadis.
What is the problem? The problem is, that Windows Server 2019 has less Root CAs installed then Windows 10 or Linux. You can verify this by running gci Cert:\CurrentUser\AuthRoot in a PowerShell on the server and compare it with the output from i.e. Windows 10. My Windows 10 has 30 entries – the Windows Server 2019 only 19.
So the solution to is simple – install the Root CA certificates on the server.
If you want to use the Azure hosted agents (i.e. windows-latest) you can use certutil to install the certificate in the pipeline. Add the certificates as .cer files to your repository and the following script to your yaml pipleine:
- script: |
certutil -f -addstore root certs\quovadis_rca_der.cer
certutil -f -addstore root certs\quovadis_rca2_der.cer
certutil -f -addstore root certs\quovadis_rca3_der.cer
certutil -f -addstore root certs\quovadis_rcag3_der.cer
certutil -f -addstore root certs\quovadis_rca2g3_der.cer
certutil -f -addstore root certs\quovadis_rca3g3_der.cer
displayName: 'Install Quo Vadis Root CA'
That’s it – now the error should be gone.
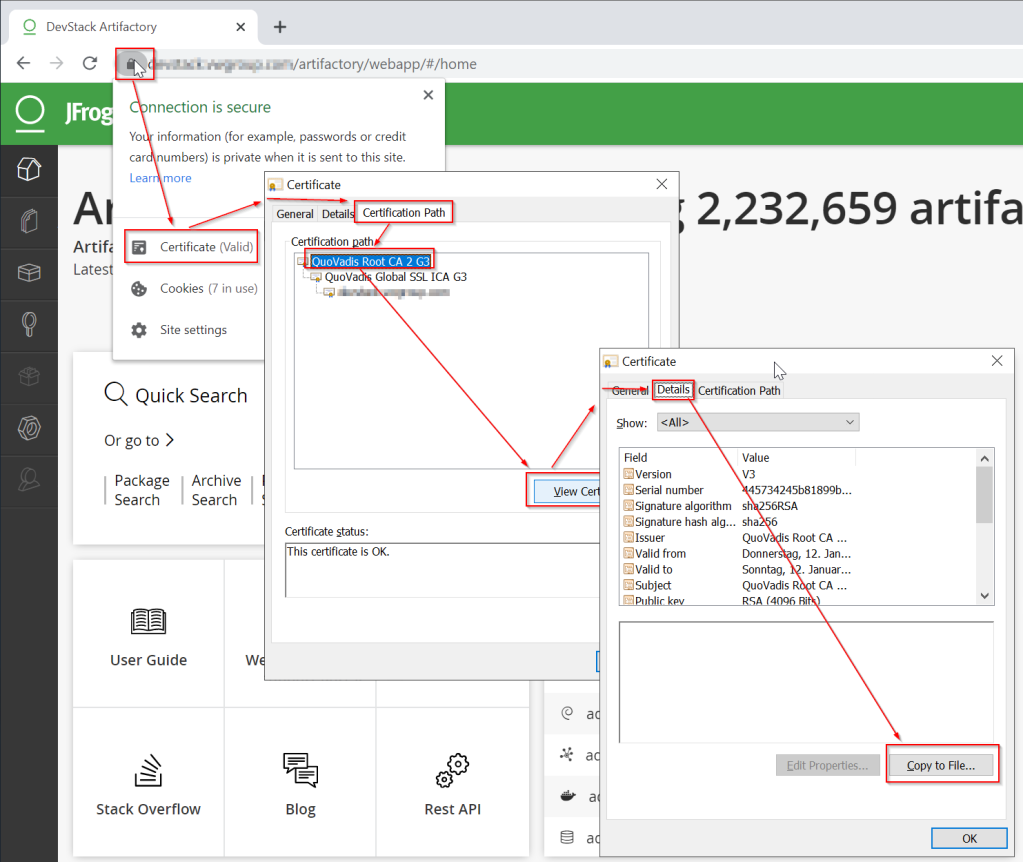
If you don’t know the root CA, open the URL that gives you the error in a browser (i.e. Chrome). Click the lock next to the URL and select Certificate (Valid). Under “Certification path” select the Root CA and click view details.
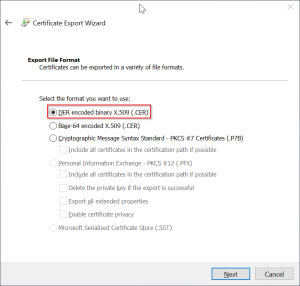
I downloaded the certificates from issuers web site – but you can also export the certificate here. Select “Copy to File…” on the “Details” tab and follow the wizard steps. Select DER format if asked and save the file to disk.
I filed an issue on GitHub and I hope it will be resolved so that we don’t need this workaround.
UPDATE: the issue on GitHub Actions and Azure DevOps Hosted Agents should be resolved. The certificates are now preinstalled.
Using the toolbox MINGW64 Bash command
docker-machine ssh default
then docker run hello-world
docker: Error while pulling image: Get https://index.docker.io/v1/repositories/library/hello-world/images: x509: certificate signed by unknown authority.
Get the same error when running the same command with the MINGW64 Bash command line.
Also get the same error using MINGW64 with docker login and enter my userID and password:
$ docker login
Login with your Docker ID to push and pull images from Docker Hub. If you don't have a Docker ID, head over to https://hub.docker.com to create one.
Username: ****
Password: ****
Error response from daemon: Get https://index.docker.io/v1/users/: x509: certificate signed by unknown authority
This is a new install on Windows 7 Enterprise. No proxy or VPN being used. My docker versions are below:
Client:
Version: 1.12.2
API version: 1.24
Go version: go1.6.3
Git commit: bb80604
Built: Tue Oct 11 17:00:50 2016
OS/Arch: windows/amd64
Server:
Version: 1.12.3
API version: 1.24
Go version: go1.6.3
Git commit: 6b644ec
Built: Wed Oct 26 23:26:11 2016
OS/Arch: linux/amd64
Here is the docker.log
/usr/local/bin/docker daemon -D -g "/var/lib/docker" -H unix:// -H tcp://0.0.0.0:2376
--label provider=virtualbox
--tlsverify --tlscacert=/var/lib/boot2docker/ca.pem --tlscert=/var/lib/boot2docker/server.pem --tlskey=/var/lib/boot2docker/server-key.pem -s aufs >> "/var/lib/boot2docker/docker.log"
time="2016-12-02T17:40:30.744686465Z" level=debug msg="Trusting 1 certs"
time="2016-12-02T17:40:30.744757096Z" level=debug msg="docker group found. gid: 100"
time="2016-12-02T17:40:30.744773618Z" level=debug msg="Listener created for HTTP on unix (/var/run/docker.sock)"
time="2016-12-02T17:40:30.745164208Z" level=debug msg="Listener created for HTTP on tcp (0.0.0.0:2376)"
time="2016-12-02T17:40:30.749858087Z" level=info msg="libcontainerd: new containerd process, pid: 1403"
time="2016-12-02T17:40:30.751232622Z" level=debug msg="libcontainerd: containerd connection state change: TRANSIENT_FAILURE"
time="2016-12-02T17:40:30.754248386Z" level=debug msg="containerd: read past events" count=0
time="2016-12-02T17:40:30.754312675Z" level=debug msg="containerd: supervisor running" cpus=1 memory=995 runtime=docker-runc runtimeArgs=[] stateDir="/var/run/docker/libcontainerd/containerd"
time="2016-12-02T17:40:30.754433105Z" level=debug msg="containerd: grpc api on /var/run/docker/libcontainerd/docker-containerd.sock"
time="2016-12-02T17:40:31.752647725Z" level=debug msg="Using default logging driver json-file"
time="2016-12-02T17:40:31.752690751Z" level=debug msg="Golang's threads limit set to 6840"
time="2016-12-02T17:40:31.752721505Z" level=debug msg="[graphdriver] trying provided driver \"aufs\""
time="2016-12-02T17:40:31.756491840Z" level=debug msg="Using graph driver aufs"
time="2016-12-02T17:40:31.756755448Z" level=debug msg="Max Concurrent Downloads: 3"
time="2016-12-02T17:40:31.756769285Z" level=debug msg="Max Concurrent Uploads: 5"
time="2016-12-02T17:40:31.758545195Z" level=info msg="Graph migration to content-addressability took 0.00 seconds"
time="2016-12-02T17:40:31.758669664Z" level=warning msg="Your kernel does not support cgroup blkio weight"
time="2016-12-02T17:40:31.758682044Z" level=warning msg="Your kernel does not support cgroup blkio weight_device"
time="2016-12-02T17:40:31.758984336Z" level=debug msg="Option DefaultDriver: bridge"
time="2016-12-02T17:40:31.758994250Z" level=debug msg="Option DefaultNetwork: bridge"
time="2016-12-02T17:40:31.764196394Z" level=debug msg="Fail to initialize firewalld: Failed to connect to D-Bus system bus: dial unix /var/run/dbus/system_bus_socket: connect: no such file or directory, using raw iptables instead"
time="2016-12-02T17:40:31.764892490Z" level=debug msg="/usr/local/sbin/iptables, [--wait --version]"
time="2016-12-02T17:40:31.765543798Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -D PREROUTING -m addrtype --dst-type LOCAL -j DOCKER]"
time="2016-12-02T17:40:31.772927899Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -D OUTPUT -m addrtype --dst-type LOCAL ! --dst 127.0.0.0/8 -j DOCKER]"
time="2016-12-02T17:40:31.773677414Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -D OUTPUT -m addrtype --dst-type LOCAL -j DOCKER]"
time="2016-12-02T17:40:31.774327019Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -D PREROUTING]"
time="2016-12-02T17:40:31.774928100Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -D OUTPUT]"
time="2016-12-02T17:40:31.775544188Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -F DOCKER]"
time="2016-12-02T17:40:31.776085017Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -X DOCKER]"
time="2016-12-02T17:40:31.776626424Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -F DOCKER]"
time="2016-12-02T17:40:31.777206016Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -X DOCKER]"
time="2016-12-02T17:40:31.777755328Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -F DOCKER-ISOLATION]"
time="2016-12-02T17:40:31.778304247Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -X DOCKER-ISOLATION]"
time="2016-12-02T17:40:31.778845101Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -n -L DOCKER]"
time="2016-12-02T17:40:31.779393672Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -N DOCKER]"
time="2016-12-02T17:40:31.779994206Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -n -L DOCKER]"
time="2016-12-02T17:40:31.780561001Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -N DOCKER]"
time="2016-12-02T17:40:31.781207318Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -n -L DOCKER-ISOLATION]"
time="2016-12-02T17:40:31.781791215Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -N DOCKER-ISOLATION]"
time="2016-12-02T17:40:31.782346071Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C DOCKER-ISOLATION -j RETURN]"
time="2016-12-02T17:40:31.783018224Z" level=debug msg="/usr/local/sbin/iptables, [--wait -I DOCKER-ISOLATION -j RETURN]"
time="2016-12-02T17:40:31.787270767Z" level=warning msg="Could not load necessary modules for IPSEC rules: Running modprobe xfrm_user failed with message: `modprobe: module xfrm_user not found in modules.dep`, error: exit status 1"
time="2016-12-02T17:40:31.787346607Z" level=debug msg="Did not find any interface with name docker0: Link not found"
time="2016-12-02T17:40:31.789910140Z" level=debug msg="Setting bridge mac address to 02:42:0d:c5:90:dc"
time="2016-12-02T17:40:31.789997612Z" level=debug msg="Assigning address to bridge interface docker0: 172.17.0.1/16"
time="2016-12-02T17:40:31.790053336Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -C POSTROUTING -s 172.17.0.0/16 ! -o docker0 -j MASQUERADE]"
time="2016-12-02T17:40:31.790895486Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -I POSTROUTING -s 172.17.0.0/16 ! -o docker0 -j MASQUERADE]"
time="2016-12-02T17:40:31.793281905Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -C DOCKER -i docker0 -j RETURN]"
time="2016-12-02T17:40:31.793927677Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -I DOCKER -i docker0 -j RETURN]"
time="2016-12-02T17:40:31.794558636Z" level=debug msg="/usr/local/sbin/iptables, [--wait -D FORWARD -i docker0 -o docker0 -j DROP]"
time="2016-12-02T17:40:31.795173446Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -i docker0 -o docker0 -j ACCEPT]"
time="2016-12-02T17:40:31.795764807Z" level=debug msg="/usr/local/sbin/iptables, [--wait -I FORWARD -i docker0 -o docker0 -j ACCEPT]"
time="2016-12-02T17:40:31.796351001Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -i docker0 ! -o docker0 -j ACCEPT]"
time="2016-12-02T17:40:31.796938536Z" level=debug msg="/usr/local/sbin/iptables, [--wait -I FORWARD -i docker0 ! -o docker0 -j ACCEPT]"
time="2016-12-02T17:40:31.797557497Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -o docker0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT]"
time="2016-12-02T17:40:31.798218826Z" level=debug msg="/usr/local/sbin/iptables, [--wait -I FORWARD -o docker0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT]"
time="2016-12-02T17:40:31.798875539Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -C PREROUTING -m addrtype --dst-type LOCAL -j DOCKER]"
time="2016-12-02T17:40:31.799561268Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -A PREROUTING -m addrtype --dst-type LOCAL -j DOCKER]"
time="2016-12-02T17:40:31.800206353Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -C OUTPUT -m addrtype --dst-type LOCAL -j DOCKER ! --dst 127.0.0.0/8]"
time="2016-12-02T17:40:31.800845743Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -A OUTPUT -m addrtype --dst-type LOCAL -j DOCKER ! --dst 127.0.0.0/8]"
time="2016-12-02T17:40:31.801556457Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -o docker0 -j DOCKER]"
time="2016-12-02T17:40:31.802147116Z" level=debug msg="/usr/local/sbin/iptables, [--wait -I FORWARD -o docker0 -j DOCKER]"
time="2016-12-02T17:40:31.802737882Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -j DOCKER-ISOLATION]"
time="2016-12-02T17:40:31.803331101Z" level=debug msg="/usr/local/sbin/iptables, [--wait -I FORWARD -j DOCKER-ISOLATION]"
time="2016-12-02T17:40:31.804007143Z" level=debug msg="Network (769a472) restored"
time="2016-12-02T17:40:31.817909885Z" level=debug msg="Allocating IPv4 pools for network bridge (769a4727f21c2c93bc5ab0d73b2221bf589b61d72286703044df82dff4404bdb)"
time="2016-12-02T17:40:31.817936450Z" level=debug msg="RequestPool(LocalDefault, 172.17.0.0/16, , map[], false)"
time="2016-12-02T17:40:31.817963419Z" level=debug msg="RequestAddress(LocalDefault/172.17.0.0/16, 172.17.0.1, map[RequestAddressType:com.docker.network.gateway])"
time="2016-12-02T17:40:31.818944639Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -C POSTROUTING -s 172.17.0.0/16 ! -o docker0 -j MASQUERADE]"
time="2016-12-02T17:40:31.819794283Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -D POSTROUTING -s 172.17.0.0/16 ! -o docker0 -j MASQUERADE]"
time="2016-12-02T17:40:31.820419933Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -C DOCKER -i docker0 -j RETURN]"
time="2016-12-02T17:40:31.821095012Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -D DOCKER -i docker0 -j RETURN]"
time="2016-12-02T17:40:31.821706584Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -i docker0 -o docker0 -j ACCEPT]"
time="2016-12-02T17:40:31.822306310Z" level=debug msg="/usr/local/sbin/iptables, [--wait -D FORWARD -i docker0 -o docker0 -j ACCEPT]"
time="2016-12-02T17:40:31.822917846Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -i docker0 ! -o docker0 -j ACCEPT]"
time="2016-12-02T17:40:31.823555089Z" level=debug msg="/usr/local/sbin/iptables, [--wait -D FORWARD -i docker0 ! -o docker0 -j ACCEPT]"
time="2016-12-02T17:40:31.824172614Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -o docker0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT]"
time="2016-12-02T17:40:31.824865567Z" level=debug msg="/usr/local/sbin/iptables, [--wait -D FORWARD -o docker0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT]"
time="2016-12-02T17:40:31.825579043Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -o docker0 -j DOCKER]"
time="2016-12-02T17:40:31.826190711Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -o docker0 -j DOCKER]"
time="2016-12-02T17:40:31.826793517Z" level=debug msg="/usr/local/sbin/iptables, [--wait -D FORWARD -o docker0 -j DOCKER]"
time="2016-12-02T17:40:31.827856201Z" level=debug msg="releasing IPv4 pools from network bridge (769a4727f21c2c93bc5ab0d73b2221bf589b61d72286703044df82dff4404bdb)"
time="2016-12-02T17:40:31.827873323Z" level=debug msg="ReleaseAddress(LocalDefault/172.17.0.0/16, 172.17.0.1)"
time="2016-12-02T17:40:31.827889444Z" level=debug msg="ReleasePool(LocalDefault/172.17.0.0/16)"
time="2016-12-02T17:40:31.829420991Z" level=info msg="Default bridge (docker0) is assigned with an IP address 172.17.0.0/16. Daemon option --bip can be used to set a preferred IP address"
time="2016-12-02T17:40:31.829449564Z" level=debug msg="Allocating IPv4 pools for network bridge (df4bd823534e55e46fab6700e94d5e3728ae40f7cdf6e4ce9fb523f4ef6a84d6)"
time="2016-12-02T17:40:31.829461383Z" level=debug msg="RequestPool(LocalDefault, 172.17.0.0/16, , map[], false)"
time="2016-12-02T17:40:31.829480436Z" level=debug msg="RequestAddress(LocalDefault/172.17.0.0/16, 172.17.0.1, map[RequestAddressType:com.docker.network.gateway])"
time="2016-12-02T17:40:31.829604904Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -C POSTROUTING -s 172.17.0.0/16 ! -o docker0 -j MASQUERADE]"
time="2016-12-02T17:40:31.830263211Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -I POSTROUTING -s 172.17.0.0/16 ! -o docker0 -j MASQUERADE]"
time="2016-12-02T17:40:31.830897081Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -C DOCKER -i docker0 -j RETURN]"
time="2016-12-02T17:40:31.831580401Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -I DOCKER -i docker0 -j RETURN]"
time="2016-12-02T17:40:31.832186563Z" level=debug msg="/usr/local/sbin/iptables, [--wait -D FORWARD -i docker0 -o docker0 -j DROP]"
time="2016-12-02T17:40:31.832832277Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -i docker0 -o docker0 -j ACCEPT]"
time="2016-12-02T17:40:31.833438658Z" level=debug msg="/usr/local/sbin/iptables, [--wait -I FORWARD -i docker0 -o docker0 -j ACCEPT]"
time="2016-12-02T17:40:31.834113557Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -i docker0 ! -o docker0 -j ACCEPT]"
time="2016-12-02T17:40:31.834778734Z" level=debug msg="/usr/local/sbin/iptables, [--wait -I FORWARD -i docker0 ! -o docker0 -j ACCEPT]"
time="2016-12-02T17:40:31.835383516Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -o docker0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT]"
time="2016-12-02T17:40:31.836099155Z" level=debug msg="/usr/local/sbin/iptables, [--wait -I FORWARD -o docker0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT]"
time="2016-12-02T17:40:31.836963236Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -C PREROUTING -m addrtype --dst-type LOCAL -j DOCKER]"
time="2016-12-02T17:40:31.837678997Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -C PREROUTING -m addrtype --dst-type LOCAL -j DOCKER]"
time="2016-12-02T17:40:31.838404700Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -C OUTPUT -m addrtype --dst-type LOCAL -j DOCKER ! --dst 127.0.0.0/8]"
time="2016-12-02T17:40:31.839196159Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t nat -C OUTPUT -m addrtype --dst-type LOCAL -j DOCKER ! --dst 127.0.0.0/8]"
time="2016-12-02T17:40:31.839951001Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -o docker0 -j DOCKER]"
time="2016-12-02T17:40:31.840701682Z" level=debug msg="/usr/local/sbin/iptables, [--wait -I FORWARD -o docker0 -j DOCKER]"
time="2016-12-02T17:40:31.841384288Z" level=debug msg="/usr/local/sbin/iptables, [--wait -t filter -C FORWARD -j DOCKER-ISOLATION]"
time="2016-12-02T17:40:31.842035782Z" level=debug msg="/usr/local/sbin/iptables, [--wait -D FORWARD -j DOCKER-ISOLATION]"
time="2016-12-02T17:40:31.842667948Z" level=debug msg="/usr/local/sbin/iptables, [--wait -I FORWARD -j DOCKER-ISOLATION]"
time="2016-12-02T17:40:31.844980088Z" level=info msg="Daemon has completed initialization"
time="2016-12-02T17:40:31.845016496Z" level=info msg="Docker daemon" commit=6b644ec graphdriver=aufs version=1.12.3
time="2016-12-02T17:40:31.845082732Z" level=debug msg="Registering routers"
time="2016-12-02T17:40:31.845090452Z" level=debug msg="Registering HEAD, /containers/{name:.*}/archive"
time="2016-12-02T17:40:31.845196210Z" level=debug msg="Registering GET, /containers/json"
time="2016-12-02T17:40:31.845249996Z" level=debug msg="Registering GET, /containers/{name:.*}/export"
time="2016-12-02T17:40:31.845332988Z" level=debug msg="Registering GET, /containers/{name:.*}/changes"
time="2016-12-02T17:40:31.845405539Z" level=debug msg="Registering GET, /containers/{name:.*}/json"
time="2016-12-02T17:40:31.845461108Z" level=debug msg="Registering GET, /containers/{name:.*}/top"
time="2016-12-02T17:40:31.845590507Z" level=debug msg="Registering GET, /containers/{name:.*}/logs"
time="2016-12-02T17:40:31.845654350Z" level=debug msg="Registering GET, /containers/{name:.*}/stats"
time="2016-12-02T17:40:31.845718392Z" level=debug msg="Registering GET, /containers/{name:.*}/attach/ws"
time="2016-12-02T17:40:31.845782209Z" level=debug msg="Registering GET, /exec/{id:.*}/json"
time="2016-12-02T17:40:31.845841816Z" level=debug msg="Registering GET, /containers/{name:.*}/archive"
time="2016-12-02T17:40:31.845906266Z" level=debug msg="Registering POST, /containers/create"
time="2016-12-02T17:40:31.845956564Z" level=debug msg="Registering POST, /containers/{name:.*}/kill"
time="2016-12-02T17:40:31.846072344Z" level=debug msg="Registering POST, /containers/{name:.*}/pause"
time="2016-12-02T17:40:31.846142240Z" level=debug msg="Registering POST, /containers/{name:.*}/unpause"
time="2016-12-02T17:40:31.846203895Z" level=debug msg="Registering POST, /containers/{name:.*}/restart"
time="2016-12-02T17:40:31.846274390Z" level=debug msg="Registering POST, /containers/{name:.*}/start"
time="2016-12-02T17:40:31.846335739Z" level=debug msg="Registering POST, /containers/{name:.*}/stop"
time="2016-12-02T17:40:31.846397909Z" level=debug msg="Registering POST, /containers/{name:.*}/wait"
time="2016-12-02T17:40:31.846455319Z" level=debug msg="Registering POST, /containers/{name:.*}/resize"
time="2016-12-02T17:40:31.846581902Z" level=debug msg="Registering POST, /containers/{name:.*}/attach"
time="2016-12-02T17:40:31.846648077Z" level=debug msg="Registering POST, /containers/{name:.*}/copy"
time="2016-12-02T17:40:31.846703368Z" level=debug msg="Registering POST, /containers/{name:.*}/exec"
time="2016-12-02T17:40:31.846757547Z" level=debug msg="Registering POST, /exec/{name:.*}/start"
time="2016-12-02T17:40:31.855298945Z" level=debug msg="Registering POST, /exec/{name:.*}/resize"
time="2016-12-02T17:40:31.855476145Z" level=debug msg="Registering POST, /containers/{name:.*}/rename"
time="2016-12-02T17:40:31.855680517Z" level=debug msg="Registering POST, /containers/{name:.*}/update"
time="2016-12-02T17:40:31.855823007Z" level=debug msg="Registering PUT, /containers/{name:.*}/archive"
time="2016-12-02T17:40:31.855965910Z" level=debug msg="Registering DELETE, /containers/{name:.*}"
time="2016-12-02T17:40:31.856156286Z" level=debug msg="Registering GET, /images/json"
time="2016-12-02T17:40:31.856248747Z" level=debug msg="Registering GET, /images/search"
time="2016-12-02T17:40:31.856338764Z" level=debug msg="Registering GET, /images/get"
time="2016-12-02T17:40:31.856428471Z" level=debug msg="Registering GET, /images/{name:.*}/get"
time="2016-12-02T17:40:31.856609363Z" level=debug msg="Registering GET, /images/{name:.*}/history"
time="2016-12-02T17:40:31.856737561Z" level=debug msg="Registering GET, /images/{name:.*}/json"
time="2016-12-02T17:40:31.856858547Z" level=debug msg="Registering POST, /commit"
time="2016-12-02T17:40:31.856932825Z" level=debug msg="Registering POST, /images/load"
time="2016-12-02T17:40:31.857067111Z" level=debug msg="Registering POST, /images/create"
time="2016-12-02T17:40:31.857171220Z" level=debug msg="Registering POST, /images/{name:.*}/push"
time="2016-12-02T17:40:31.857289494Z" level=debug msg="Registering POST, /images/{name:.*}/tag"
time="2016-12-02T17:40:31.857408848Z" level=debug msg="Registering DELETE, /images/{name:.*}"
time="2016-12-02T17:40:31.857600539Z" level=debug msg="Registering OPTIONS, /{anyroute:.*}"
time="2016-12-02T17:40:31.857700202Z" level=debug msg="Registering GET, /_ping"
time="2016-12-02T17:40:31.857773927Z" level=debug msg="Registering GET, /events"
time="2016-12-02T17:40:31.857843765Z" level=debug msg="Registering GET, /info"
time="2016-12-02T17:40:31.857908064Z" level=debug msg="Registering GET, /version"
time="2016-12-02T17:40:31.858001946Z" level=debug msg="Registering POST, /auth"
time="2016-12-02T17:40:31.858134328Z" level=debug msg="Registering GET, /volumes"
time="2016-12-02T17:40:31.858215934Z" level=debug msg="Registering GET, /volumes/{name:.*}"
time="2016-12-02T17:40:31.858338159Z" level=debug msg="Registering POST, /volumes/create"
time="2016-12-02T17:40:31.858435864Z" level=debug msg="Registering DELETE, /volumes/{name:.*}"
time="2016-12-02T17:40:31.858623798Z" level=debug msg="Registering POST, /build"
time="2016-12-02T17:40:31.858699227Z" level=debug msg="Registering POST, /swarm/init"
time="2016-12-02T17:40:31.858782830Z" level=debug msg="Registering POST, /swarm/join"
time="2016-12-02T17:40:31.858882884Z" level=debug msg="Registering POST, /swarm/leave"
time="2016-12-02T17:40:31.858975348Z" level=debug msg="Registering GET, /swarm"
time="2016-12-02T17:40:31.859090616Z" level=debug msg="Registering POST, /swarm/update"
time="2016-12-02T17:40:31.859185927Z" level=debug msg="Registering GET, /services"
time="2016-12-02T17:40:31.859271129Z" level=debug msg="Registering GET, /services/{id:.*}"
time="2016-12-02T17:40:31.859392667Z" level=debug msg="Registering POST, /services/create"
time="2016-12-02T17:40:31.859498568Z" level=debug msg="Registering POST, /services/{id:.*}/update"
time="2016-12-02T17:40:31.860487935Z" level=debug msg="Registering DELETE, /services/{id:.*}"
time="2016-12-02T17:40:31.860600622Z" level=debug msg="Registering GET, /nodes"
time="2016-12-02T17:40:31.860638114Z" level=debug msg="Registering GET, /nodes/{id:.*}"
time="2016-12-02T17:40:31.860689203Z" level=debug msg="Registering DELETE, /nodes/{id:.*}"
time="2016-12-02T17:40:31.860739964Z" level=debug msg="Registering POST, /nodes/{id:.*}/update"
time="2016-12-02T17:40:31.860791527Z" level=debug msg="Registering GET, /tasks"
time="2016-12-02T17:40:31.860823214Z" level=debug msg="Registering GET, /tasks/{id:.*}"
time="2016-12-02T17:40:31.860872242Z" level=debug msg="Registering GET, /networks"
time="2016-12-02T17:40:31.860907071Z" level=debug msg="Registering GET, /networks/{id:.*}"
time="2016-12-02T17:40:31.860959816Z" level=debug msg="Registering POST, /networks/create"
time="2016-12-02T17:40:31.861000434Z" level=debug msg="Registering POST, /networks/{id:.*}/connect"
time="2016-12-02T17:40:31.861149382Z" level=debug msg="Registering POST, /networks/{id:.*}/disconnect"
time="2016-12-02T17:40:31.861212449Z" level=debug msg="Registering DELETE, /networks/{id:.*}"
time="2016-12-02T17:40:31.861470361Z" level=info msg="API listen on [::]:2376"
time="2016-12-02T17:40:31.861560675Z" level=info msg="API listen on /var/run/docker.sock"
time="2016-12-02T17:40:33.751508859Z" level=debug msg="libcontainerd: containerd connection state change: READY"
time="2016-12-02T17:40:47.157118325Z" level=debug msg="Calling POST /v1.24/containers/create"
time="2016-12-02T17:40:47.157318825Z" level=debug msg="form data: {\"AttachStderr\":true,\"AttachStdin\":false,\"AttachStdout\":true,\"Cmd\":null,\"Domainname\":\"\",\"Entrypoint\":null,\"Env\":[],\"HostConfig\":{\"AutoRemove\":false,\"Bind
time="2016-12-02T17:40:47.157354807Z" level=debug msg="Client and server don't have the same version (client: 1.12.2, server: 1.12.3)"
time="2016-12-02T17:40:47.158018832Z" level=error msg="Handler for POST /v1.24/containers/create returned error: No such image: hello-world:latest"
time="2016-12-02T17:40:47.168659719Z" level=debug msg="Calling GET /v1.24/info"
time="2016-12-02T17:40:47.168702458Z" level=debug msg="Client and server don't have the same version (client: 1.12.2, server: 1.12.3)"
time="2016-12-02T17:40:47.175273487Z" level=debug msg="Calling POST /v1.24/images/create?fromImage=hello-world&tag=latest"
time="2016-12-02T17:40:47.175301389Z" level=debug msg="Client and server don't have the same version (client: 1.12.2, server: 1.12.3)"
time="2016-12-02T17:40:47.175394394Z" level=debug msg="Trying to pull hello-world from https://registry-1.docker.io v2"
time="2016-12-02T17:40:47.267928949Z" level=warning msg="Error getting v2 registry: Get https://registry-1.docker.io/v2/: x509: certificate signed by unknown authority"
time="2016-12-02T17:40:47.267962791Z" level=error msg="Attempting next endpoint for pull after error: Get https://registry-1.docker.io/v2/: x509: certificate signed by unknown authority"
time="2016-12-02T17:40:47.267980757Z" level=debug msg="Trying to pull hello-world from https://index.docker.io v1"
time="2016-12-02T17:40:47.268000661Z" level=debug msg="hostDir: /etc/docker/certs.d/docker.io"
time="2016-12-02T17:40:47.268523687Z" level=debug msg="[registry] Calling GET https://index.docker.io/v1/repositories/library/hello-world/images"
time="2016-12-02T17:40:47.343322233Z" level=error msg="Not continuing with pull after error: Error while pulling image: Get https://index.docker.io/v1/repositories/library/hello-world/images: x509: certificate signed by unknown authority"
Ok here is what I don’t understand, you can see in the beginning of the log it is using 0.0.0.0:2376 for the docker VM. When I run docker-machine ls I see this:
$ docker-machine ls
NAME ACTIVE DRIVER STATE URL SWARM DOCKER ERRORS
default * virtualbox Running tcp://192.168.99.100:2376 v1.12.3
According boot2docker you are suppose to use hostname however it looks like two different IP addresses are being used. What should be used?
X509 certificate signed by unknown authority error occurs when a client device does not trust the certificate authority (CA) that issued the SSL/TLS certificate for a website. This is especially common when using self-signed certificates.
The error means the client does not recognize the issuer of the certificate and considers the certificate to be invalid. In this guide, you will learn about the causes of this error and how to solve it.
Contents
- Why Is the X509 Certificate Error Showing Up on My Device?
- – Self-signed Certificates: The Weak Link in Online Security
- – Expired Certificates: The Ultimate Threat to Online Security
- – Certificate Chaos: The Nightmare of Incorrect Installation
- – Surprising Scenarios That May Trigger the Error in Practice
- Quick Fixes to the Dreaded X509 Certificate Authority Error
- – Certificate Renewal: The Key To Unlocking Secure Connections
- – Ensure Certificates Are Properly Installed and Configured
- Conclusion
Why Is the X509 Certificate Error Showing Up on My Device?
The X509 certificate error is showing up on your device because the website you are trying to access has an SSL certificate that is either expired or from untrusted authority. It also occurs when the browser is unable to verify the website’s certificate authenticity.
X.509 certificate authentication is commonly used in secure communication protocols such as SSL/TLS, which are used to encrypt data transmitted over the internet. Also, X.509 certificates are used for secure email communication, VPNs, and other applications that require secure authentication.
Now, this is where the X.509 certificate authentication process, which involves confirmation of user or device identity through the use of a digital certificate, comes in.
This is done by presenting a certificate to a server or service during a secure communication and having the server validate the certificate against a list of trusted CAs. If the certificate is recognized as being issued by a trusted CA and is valid and current, the user or device is authenticated and granted access to the network or resource.
However, if there is an issue with the certificate, be it expired, configuration-wise, or a certificate from an untrusted authority, it will trigger the error in question.
– Self-signed Certificates: The Weak Link in Online Security
The use of self-signed certificates is one of the causes of this error. Self-signed certificates are issued by the website owner or administrator rather than a trusted certificate authority (CA).
This means that the browser does not recognize the certificate as one issued by a trusted third party, so it is unable to verify the authenticity of the website. As a result, the browser displays an X509 certificate error to warn you that the website may not be secure and that the connection is not encrypted.
Self-signed certificates are not recommended for use on websites that handle sensitive information, such as personal data, credit card numbers, or other confidential information, because they do not provide the same level of security as certificates issued by trusted CAs.
Therefore, when a browser encounters a website that uses a self-signed certificate, it will display an X509 certificate error to alert you that the website may not be trustworthy and that your data may be at risk of being intercepted or compromised.
– Expired Certificates: The Ultimate Threat to Online Security
An X.509 certificate error can occur when a certificate has expired. A digital certificate has a limited lifespan, and when the validity period of the certificate expires, the certificate is no longer considered to be valid.
When you try to access a website that uses an expired certificate, the browser will display an X.509 certificate error because it is unable to verify the authenticity of the website.
This error occurs because the certificate can no longer be trusted to verify the identity of the website, and the browser cannot be sure that the connection is secure.
– Certificate Chaos: The Nightmare of Incorrect Installation
The x509 certificate signed by unknown authority error can also be triggered when a certificate is incorrectly installed on a device or server. This can arise for several reasons.
For instance, if the certificate is not properly configured, it may not be recognized as a valid certificate by browsers or other devices. Also, if the root certificate of the certificate authority that issued the certificate is not installed on the device or server, the certificate may not be trusted.
As well, the private key used to install the certificate must match the public key included in the certificate. If the private key is incorrect, the certificate will not be trusted, which will trigger the error.
In addition, if the certificate is not installed in the correct file format, it may not be recognized as a valid certificate. For example, if a .pem file is incorrectly installed as a .cer file, the certificate may not be trusted, triggering the error in question.
– Surprising Scenarios That May Trigger the Error in Practice
If you like to explore the internet on various platforms, you may come across this error when trying to access useful resources. Below is a quick look at some of them:
- x509: certificate signed by unknown authority docker – It occurs when Docker is unable to verify the identity of the server or registry it is trying to connect to.
- x509: certificate signed by unknown authority linux – This error happens when a Linux server or client cannot verify the identity of the server it is trying to access.
- x509: certificate signed by unknown authority vault – The error happens when Vault is unable to verify the identity of the server it is trying to connect to.
- x509: certificate signed by unknown authority terraform – Occurs when Terraform is unable to verify the identity of the server it is trying to connect to.
- x509: certificate signed by unknown authority- kubernetes – The error occurs when a Kubernetes cluster is unable to verify the identity of the server it is trying to connect to.
- x509: certificate signed by unknown authority github – This error can occur when a client or server is unable to verify the identity of GitHub.
- x509: certificate signed by unknown authority docker pull – The error appears when Docker is unable to verify the identity of the registry it is trying to download the image from.
The quick solutions to the dreaded X509 certificate authority error include obtaining a certificate from a trusted certificate authority (CA). When a certificate is issued by a trusted CA, it undergoes a rigorous verification process to confirm the identity of the entity requesting the certificate.
This process helps to ensure that the certificate is issued to a legitimate entity and helps prevent phishing and other security risks.
By obtaining a certificate from a trusted CA, the client device can verify that the certificate was issued by a trusted authority and therefore trust the identity of the entity presenting the certificate.
As such, it allows for secure communication between the client device and the server which ultimately prevents this error. That is how to fix x509: certificate signed by unknown authority error.
– Certificate Renewal: The Key To Unlocking Secure Connections
Another solution is to renew or replace expired certificates. When a certificate has expired, it is no longer considered valid, and the client device will reject it, triggering the error. Renewing an expired certificate involves obtaining a new certificate from a trusted certificate authority (CA). The new certificate will have a new expiration date and will be considered valid for a set period.
By renewing or replacing expired certificates, the client device will trust the new certificate, which will resolve the error. In return, it allows for secure communication between the client device and the server.
– Ensure Certificates Are Properly Installed and Configured
When installing trusted certificates on the server, it is important to ensure that the correct certificate is installed in the correct location to avoid this error. Therefore, when configuring the server to use the certificate, the certificate’s Common Name (CN) or Subject Alternative Name (SAN) should match the domain name that the client device will use to connect to the server.
This ensures that the client device will trust the certificate, as it will match the domain name that it is expecting. By properly installing and configuring certificates, client devices will trust the certificates and solve the error.
Conclusion
In this article, you delved into the causes and solutions to the x509: certificate signed by unknown authority error. To recap, here is what you have learned about this error and its solutions:
- The error is a security warning that arises when the client device cannot verify the authenticity of the server’s certificate.
- Self-signed certificates, certificates from an untrusted authority, expired certificates, and incorrect certificate installation are common causes of this error.
- Obtaining certificates from trusted certificate authorities and renewing or replacing expired certificates are effective solutions.
- Another effective solution to this error is ensuring proper installation and configuration of certificates.
With this newfound knowledge, you are now equipped to handle the error with ease and confidence.
- Author
- Recent Posts
Your Go-To Resource for Learn & Build: CSS,JavaScript,HTML,PHP,C++ and MYSQL. Meet The Team