The amount of resources Wireshark needs depends on your environment and on the
size of the capture file you are analyzing. The values below should be fine for
small to medium-sized capture files no more than a few hundred MB. Larger
capture files will require more memory and disk space.
![[Note]](https://www.wireshark.org/docs/wsug_html_chunked/images/note.svg) |
Busy networks mean large captures |
|---|---|
|
A busy network can produce huge capture files. Capturing on |
If Wireshark runs out of memory it will crash. See
https://gitlab.com/wireshark/wireshark/-/wikis/KnownBugs/OutOfMemory for details and workarounds.
Although Wireshark uses a separate process to capture packets, the packet
analysis is single-threaded and won’t benefit much from multi-core systems.
1.2.1. Microsoft Windows
Wireshark should support any version of Windows that is still within its
extended support
lifetime. At the time of writing this includes Windows 10, 8.1,
Server 2019,
Server 2016,
Server 2012 R2,
and Server 2012.
It also requires the following:
-
The Universal C Runtime. This is included with Windows 10 and Windows
Server 2019 and is installed automatically on earlier versions if
Microsoft Windows Update is enabled. Otherwise you must install
KB2999226 or
KB3118401. - Any modern 64-bit Intel or Arm processor.
- 500 MB available RAM. Larger capture files require more RAM.
- 500 MB available disk space. Capture files require additional disk space.
-
Any modern display. 1280 × 1024 or higher resolution is
recommended. Wireshark will make use of HiDPI or Retina resolutions if
available. Power users will find multiple monitors useful. -
A supported network card for capturing
-
Ethernet. Any card supported by Windows should work. See the wiki pages on
Ethernet capture and
offloading for issues that
may affect your environment. -
802.11. See the Wireshark
wiki page. Capturing raw 802.11 information may be difficult without
special equipment. - Other media. See https://gitlab.com/wireshark/wireshark/-/wikis/CaptureSetup/NetworkMedia.
-
Ethernet. Any card supported by Windows should work. See the wiki pages on
Older versions of Windows which are outside Microsoft’s extended lifecycle
support window are no longer supported. It is often difficult or impossible to
support these systems due to circumstances beyond our control, such as third
party libraries on which we depend or due to necessary features that are only
present in newer versions of Windows such as hardened security or memory
management.
- Wireshark 3.6 was the last release branch to officially support 32-bit Windows.
- Wireshark 3.2 was the last release branch to officially support Windows 7 and Windows Server 2008 R2.
- Wireshark 2.2 was the last release branch to support Windows Vista and Windows Server 2008 sans R2
- Wireshark 1.12 was the last release branch to support Windows Server 2003.
- Wireshark 1.10 was the last release branch to officially support Windows XP.
See the Wireshark
release lifecycle page for more details.
1.2.2. macOS
Wireshark supports macOS 10.14 and later.
Similar to Windows, supported macOS versions depend on third party libraries and on Apple’s requirements.
Apple Silicon hardware is supported natively starting with version 4.0
- Wireshark 3.6 was the last release branch to support macOS 10.13.
- Wireshark 3.4 was the last release branch to support macOS 10.12.
- Wireshark 2.6 was the last release branch to support Mac OS X 10.6 and 10.7 and OS X 10.8 to 10.11.
- Wireshark 2.0 was the last release branch to support OS X on 32-bit Intel.
- Wireshark 1.8 was the last release branch to support Mac OS X on PowerPC.
The system requirements should be comparable to the specifications listed above for Windows.
1.2.3. UNIX, Linux, and BSD
Wireshark runs on most UNIX and UNIX-like platforms including Linux and most BSD variants.
The system requirements should be comparable to the specifications listed above for Windows.
Binary packages are available for most Unices and Linux distributions
including the following platforms:
- Alpine Linux
- Arch Linux
- Canonical Ubuntu
- Debian GNU/Linux
- FreeBSD
- Gentoo Linux
- HP-UX
- NetBSD
- OpenPKG
- Oracle Solaris
- Red Hat Enterprise Linux / CentOS / Fedora
If a binary package is not available for your platform you can download
the source and try to build it. Please report your experiences to
wireshark-dev[AT]wireshark.org.
The amount of resources Wireshark needs depends on your environment and on the
size of the capture file you are analyzing. The values below should be fine for
small to medium-sized capture files no more than a few hundred MB. Larger
capture files will require more memory and disk space.
![[Note]](https://www.wireshark.org/docs/wsug_html_chunked/images/note.svg) |
Busy networks mean large captures |
|---|---|
|
A busy network can produce huge capture files. Capturing on |
If Wireshark runs out of memory it will crash. See
https://gitlab.com/wireshark/wireshark/wikis/KnownBugs/OutOfMemory for details and workarounds.
Although Wireshark uses a separate process to capture packets, the packet
analysis is single-threaded and won’t benefit much from multi-core systems.
1.2.1. Microsoft Windows
Wireshark should support any version of Windows that is still within its
extended support
lifetime. At the time of writing this includes Windows 10, 8.1,
Server 2019,
Server 2016,
Server 2012 R2,
and Server 2012.
It also requires the following:
-
The Universal C Runtime. This is included with Windows 10 and Windows
Server 2019 and is installed automatically on earlier versions if
Microsoft Windows Update is enabled. Otherwise you must install
KB2999226 or
KB3118401. - Any modern 64-bit AMD64/x86-64 or 32-bit x86 processor.
- 500 MB available RAM. Larger capture files require more RAM.
- 500 MB available disk space. Capture files require additional disk space.
-
Any modern display. 1280 × 1024 or higher resolution is
recommended. Wireshark will make use of HiDPI or Retina resolutions if
available. Power users will find multiple monitors useful. -
A supported network card for capturing
-
Ethernet. Any card supported by Windows should work. See the wiki pages on
Ethernet capture and
offloading for issues that
may affect your environment. -
802.11. See the Wireshark
wiki page. Capturing raw 802.11 information may be difficult without
special equipment. - Other media. See https://gitlab.com/wireshark/wireshark/wikis/CaptureSetup/NetworkMedia.
-
Ethernet. Any card supported by Windows should work. See the wiki pages on
Older versions of Windows which are outside Microsoft’s extended lifecycle
support window are no longer supported. It is often difficult or impossible to
support these systems due to circumstances beyond our control, such as third
party libraries on which we depend or due to necessary features that are only
present in newer versions of Windows such as hardened security or memory
management.
- Wireshark 3.6 was the last release branch to officially support 32-bit Windows.
- Wireshark 3.2 was the last release branch to officially support Windows 7 and Windows Server 2008 R2.
- Wireshark 2.2 was the last release branch to support Windows Vista and Windows Server 2008 sans R2
- Wireshark 1.12 was the last release branch to support Windows Server 2003.
- Wireshark 1.10 was the last release branch to officially support Windows XP.
See the Wireshark
release lifecycle page for more details.
1.2.2. macOS
Wireshark supports macOS 10.14 and later.
Similar to Windows, supported macOS versions depend on third party libraries and on Apple’s requirements.
Apple Silicon hardware is supported natively starting with version 4.0
- Wireshark 3.6 was the last release branch to support macOS 10.13.
- Wireshark 3.4 was the last release branch to support macOS 10.12.
- Wireshark 2.6 was the last release branch to support Mac OS X 10.6 and 10.7 and OS X 10.8 to 10.11.
- Wireshark 2.0 was the last release branch to support OS X on 32-bit Intel.
- Wireshark 1.8 was the last release branch to support Mac OS X on PowerPC.
The system requirements should be comparable to the specifications listed above for Windows.
1.2.3. UNIX, Linux, and BSD
Wireshark runs on most UNIX and UNIX-like platforms including Linux and most BSD variants.
The system requirements should be comparable to the specifications listed above for Windows.
Binary packages are available for most Unices and Linux distributions
including the following platforms:
- Alpine Linux
- Arch Linux
- Canonical Ubuntu
- Debian GNU/Linux
- FreeBSD
- Gentoo Linux
- HP-UX
- NetBSD
- OpenPKG
- Oracle Solaris
- Red Hat Enterprise Linux / CentOS / Fedora
If a binary package is not available for your platform you can download
the source and try to build it. Please report your experiences to
wireshark-dev[AT]wireshark.org.
The current stable release of Wireshark is 4.0.4. It supersedes all previous releases.
Old Stable Release: 3.6.12
Support open source packet analysis.
The non-profit Wireshark Foundation supports the development of Wireshark, a free, open-source tool used by millions around the world.
Not What You’re Looking For?
Older Releases
All present and past releases can be found in our our download area.
Installation Notes
For a complete list of system requirements and supported platforms, please consult the User’s Guide.
Information about each release can be found in the release notes.
Each Windows package comes with the latest stable release of Npcap, which is required for live packet capture. If needed you can download separately from the Npcap web site.
Live on the Bleeding Edge
You can download source code packages and Windows installers which are automatically created each time code is checked into the source code repository. These packages are available in the automated build section of our download area.
Go Spelunking
You can explore the download areas of the main site and mirrors below. Past releases can be found by browsing the all-versions directories under each platform directory.
- Wireshark Foundation (https, us)
- Wireshark Foundation (https, us)
- Wireshark Foundation (https, us)
- Wireshark Foundation (https, us)
- University of Kaiserslautern (ftp, de)
- University of Kaiserslautern (http, de)
- Yamagata University, Japan (http, jp)
- Yamagata University, Japan (ftp, jp)
- Yamagata University, Japan (rsync, jp)
- MARWAN, Morocco (https, ma)
- Wireshark.org (https, us)
Stay Current
You can stay informed about new Wireshark releases by subscribing to the wireshark-announce mailing list. We also provide a PAD file to make automated checking easier.
Verify Downloads
File hashes for the current release can be found in the signatures file. It is signed with key id 0xE6FEAEEA. Prior to April 2016 downloads were signed with key id 0x21F2949A.
Stay Legal
Wireshark is subject to U.S. export regulations. Take heed. Consult a lawyer if you have any questions.
Wireshark
1.2. System Requirements
What you’ll need to get Wireshark up and running …
-
The values below are the minimum requirements and only
«rules of thumb» for use on a moderately used network -
Working with a busy network can easily produce huge
memory and disk space usage! For example: Capturing on a fully saturated
100MBit/s Ethernet will produce ~ 750MBytes/min! Having a fast processor,
lots of memory and disk space is a good idea in that case. -
If Wireshark is running out of memory it crashes,
see: http://wiki.wireshark.org/KnownBugs/OutOfMemory
for details and workarounds -
Wireshark won’t benefit much from Multiprocessor/Hyperthread
systems as time consuming tasks like filtering packets are single threaded.
No rule is without exception: during an «Update list of packets in real
time» capture, capturing traffic runs in one process and dissecting and
displaying packets runs in another process — which should benefit from two
processors.
1.2.2. Microsoft Windows
-
Windows XP Home, XP Pro, XP Tablet PC, XP Media
Center, Server 2003, Vista, 2008, 7, or 2008 R2 -
Any modern 32-bit x86 or 64-bit AMD64/x86-64 processor.
-
128MB available RAM. Larger capture files require more RAM.
-
75MB available disk space. Capture files require additional disk space.
-
800*600 (1280*1024 or higher recommended) resolution with
at least 65536 (16bit) colors (256 colors should work if Wireshark is
installed with the «legacy GTK1» selection of the Wireshark 1.0.x releases) -
A supported network card for capturing:
-
Ethernet: Any card supported by Windows should work. See the wiki
pages on Ethernet
capture and offloading
for issues that may affect your environment. -
802.11: See the Wireshark
wiki page. Capturing raw 802.11 information may be difficult without special equipment. -
Other media: See http://wiki.wireshark.org/CaptureSetup/NetworkMedia
-
Remarks:
-
Many older Windows versions are no longer supported for three reasons:
None of the developers use those systems which makes support
difficult. The libraries Wireshark depends on (GTK, WinPcap, …) have
dropped support for older releases. Microsoft has also dropped
support for these systems. -
Windows 95, 98 and ME are no longer supported. The «old technology»
releases of Windows lack memory protection (specifically VirtualProtect)
which we use to improve program safety and security. The last known
version to work was Ethereal 0.10.14 (which includes WinPcap 3.1). You
can get it from http://ethereal.com/download.html.
According to this
bug report, you may need to install Ethereal 0.10.0 on some
systems.Microsoft retired support for Windows 98 and ME in 2006.
-
Windows NT 4.0 no longer works with Wireshark. The last known version
to work was Wireshark 0.99.4 (which includes WinPcap 3.1). You still
can get it from http://www.wireshark.org/download/win32/all-versions/wireshark-setup-0.99.4.exe.Microsoft retired support for Windows NT 4.0 in 2004.
-
Windows 2000 no longer works with Wireshark. The last known version
to work was Wireshark 1.2.x (which includes WinPcap 4.1.2). You still
can get it from http://www.wireshark.org/download/win32/all-versions/.Microsoft retired support for Windows 2000 in 2010.
-
Windows CE and the embedded versions of Windows are not currently supported.
-
Multiple monitor setups are supported but may behave a bit
strangely.
1.2.3. Unix / Linux
Wireshark currently runs on most UNIX platforms.
The system requirements should be comparable to the Windows values
listed above.
Binary packages are available for at least the following platforms:
-
Apple Mac OS X
-
Debian GNU/Linux
-
FreeBSD
-
Gentoo Linux
-
HP-UX
-
Mandriva Linux
-
NetBSD
-
OpenPKG
-
Red Hat Enterprise/Fedora Linux
-
rPath Linux
-
Sun Solaris/i386
-
Sun Solaris/Sparc
-
Canonical Ubuntu
If a binary package is not available for your platform, you should
download the source and try to build it.
Please report your experiences
to wireshark-dev[AT]wireshark.org
.
General Information
Wireshark is a network traffic analyzer, or «sniffer», for Linux, macOS,
*BSD and other Unix and Unix-like operating systems and for Windows.
It uses Qt, a graphical user interface library, and libpcap and npcap as
packet capture and filtering libraries.
The Wireshark distribution also comes with TShark, which is a
line-oriented sniffer (similar to Sun’s snoop or tcpdump) that uses the
same dissection, capture-file reading and writing, and packet filtering
code as Wireshark, and with editcap, which is a program to read capture
files and write the packets from that capture file, possibly in a
different capture file format, and with some packets possibly removed
from the capture.
The official home of Wireshark is https://www.wireshark.org.
The latest distribution can be found in the subdirectory https://www.wireshark.org/download
Installation
The Wireshark project builds and tests regularly on the following platforms:
- Linux (Ubuntu)
- Microsoft Windows
- macOS / {Mac} OS X
Official installation packages are available for Microsoft Windows and
macOS.
It is available as either a standard or add-on package for many popular
operating systems and Linux distributions including Debian, Ubuntu, Fedora,
CentOS, RHEL, Arch, Gentoo, openSUSE, FreeBSD, DragonFly BSD, NetBSD, and
OpenBSD.
Additionally it is available through many third-party packaging systems
such as pkgsrc, OpenCSW, Homebrew, and MacPorts.
It should run on other Unix-ish systems without too much trouble.
In some cases the current version of Wireshark might not support your
operating system. This is the case for Windows XP, which is supported by
Wireshark 1.10 and earlier. In other cases the standard package for
Wireshark might simply be old. This is the case for Solaris and HP-UX.
Python 3 is needed to build Wireshark. AsciiDoctor is required to build
the documentation, including the man pages. Perl and flex are required
to generate some of the source code.
You must therefore install Python 3, AsciiDoctor, and GNU «flex» (vanilla
«lex» won’t work) on systems that lack them. You might need to install
Perl as well.
Full installation instructions can be found in the INSTALL file and in the
Developer’s Guide at https://www.wireshark.org/docs/wsdg_html_chunked/
See also the appropriate README.OS files for OS-specific installation
instructions.
Usage
In order to capture packets from the network, you need to make the
dumpcap program set-UID to root or you need to have access to the
appropriate entry under /dev if your system is so inclined (BSD-derived
systems, and systems such as Solaris and HP-UX that support DLPI,
typically fall into this category). Although it might be tempting to
make the Wireshark and TShark executables setuid root, or to run them as
root please don’t. The capture process has been isolated in dumpcap;
this simple program is less likely to contain security holes and is thus
safer to run as root.
Please consult the man page for a description of each command-line
option and interface feature.
Multiple File Types
Wireshark can read packets from a number of different file types. See
the Wireshark man page or the Wireshark User’s Guide for a list of
supported file formats.
Wireshark can transparently read compressed versions of any of those files if
the required compression library was available when Wireshark was compiled.
Currently supported compression formats are:
- GZIP
- ZSTD
- LZ4
You can disable zlib support by running cmake -DENABLE_ZLIB=OFF.
Although Wireshark can read AIX iptrace files, the documentation on
AIX’s iptrace packet-trace command is sparse. The iptrace command
starts a daemon which you must kill in order to stop the trace. Through
experimentation it appears that sending a HUP signal to that iptrace
daemon causes a graceful shutdown and a complete packet is written
to the trace file. If a partial packet is saved at the end, Wireshark
will complain when reading that file, but you will be able to read all
other packets. If this occurs, please let the Wireshark developers know
at wireshark-dev@wireshark.org; be sure to send us a copy of that trace
file if it’s small and contains non-sensitive data.
Support for Lucent/Ascend products is limited to the debug trace output
generated by the MAX and Pipline series of products. Wireshark can read
the output of the wandsession, wandisplay, wannext, and wdd
commands.
Wireshark can also read dump trace output from the Toshiba «Compact Router»
line of ISDN routers (TR-600 and TR-650). You can telnet to the router
and start a dump session with snoop dump.
CoSine L2 debug output can also be read by Wireshark. To get the L2
debug output first enter the diags mode and then use
create-pkt-log-profile and apply-pkt-lozg-profile commands under
layer-2 category. For more detail how to use these commands, you
should examine the help command by layer-2 create ? or layer-2 apply ?.
To use the Lucent/Ascend, Toshiba and CoSine traces with Wireshark, you must
capture the trace output to a file on disk. The trace is happening inside
the router and the router has no way of saving the trace to a file for you.
An easy way of doing this under Unix is to run telnet <ascend> | tee <outfile>.
Or, if your system has the «script» command installed, you can save
a shell session, including telnet, to a file. For example to log to a file
named tracefile.out:
$ script tracefile.out
Script started on <date/time>
$ telnet router
..... do your trace, then exit from the router's telnet session.
$ exit
Script done on <date/time>
Name Resolution
Wireshark will attempt to use reverse name resolution capabilities
when decoding IPv4 and IPv6 packets.
If you want to turn off name resolution while using Wireshark, start
Wireshark with the -n option to turn off all name resolution (including
resolution of MAC addresses and TCP/UDP/SMTP port numbers to names) or
with the -N mt option to turn off name resolution for all
network-layer addresses (IPv4, IPv6, IPX).
You can make that the default setting by opening the Preferences dialog
using the Preferences item in the Edit menu, selecting «Name resolution»,
turning off the appropriate name resolution options, and clicking «OK».
SNMP
Wireshark can do some basic decoding of SNMP packets; it can also use
the libsmi library to do more sophisticated decoding by reading MIB
files and using the information in those files to display OIDs and
variable binding values in a friendlier fashion. CMake will automatically
determine whether you have the libsmi library on your system. If you
have the libsmi library but do not want Wireshark to use it, you can run
cmake with the -DENABLE_SMI=OFF option.
How to Report a Bug
Wireshark is under constant development, so it is possible that you will
encounter a bug while using it. Please report bugs at https://gitlab.com/wireshark/wireshark/-/issues.
Be sure you enter into the bug:
-
The complete build information from the «About Wireshark»
item in the Help menu or the output ofwireshark -vfor
Wireshark bugs and the output oftshark -vfor TShark bugs; -
If the bug happened on Linux, the Linux distribution you were
using, and the version of that distribution; -
The command you used to invoke Wireshark, if you ran
Wireshark from the command line, or TShark, if you ran
TShark, and the sequence of operations you performed that
caused the bug to appear.
If the bug is produced by a particular trace file, please be sure to
attach to the bug a trace file along with your bug description. If the
trace file contains sensitive information (e.g., passwords), then please
do not send it.
If Wireshark died on you with a ‘segmentation violation’, ‘bus error’,
‘abort’, or other error that produces a UNIX core dump file, you can
help the developers a lot if you have a debugger installed. A stack
trace can be obtained by using your debugger (‘gdb’ in this example),
the wireshark binary, and the resulting core file. Here’s an example of
how to use the gdb command ‘backtrace’ to do so.
$ gdb wireshark core
(gdb) backtrace
..... prints the stack trace
(gdb) quit
$
The core dump file may be named «wireshark.core» rather than «core» on
some platforms (e.g., BSD systems). If you got a core dump with
TShark rather than Wireshark, use «tshark» as the first argument to
the debugger; the core dump may be named «tshark.core».
License
Wireshark is distributed under the GNU GPLv2. See the file COPYING for
the full text of the license. When in doubt the full text is the legally
binding part. These notes are just to make it easier for people that are not
familiar with the GPLv2.
There are no restrictions on its use. There are restrictions on its distribution
in source or binary form.
Most parts of Wireshark are covered by a «GPL version 2 or later» license.
Some files are covered by different licenses that are compatible with
the GPLv2.
As a notable exception, some utilities distributed with the Wireshark source are
covered by other licenses that are not themselves directly compatible with the
GPLv2. This is OK, as only the tools themselves are licensed this way, the
output of the tools is not considered a derived work, and so can be safely
licensed for Wireshark’s use. An incomplete selection of these tools includes:
- the pidl utility (tools/pidl) is licensed under the GPLv3+.
Parts of Wireshark can be built and distributed as libraries. These
parts are still covered by the GPL, and NOT by the Lesser General Public
License or any other license.
If you integrate all or part of Wireshark into your own application, then
that application must be released under a license compatible with the GPL.
Disclaimer
There is no warranty, expressed or implied, associated with this product.
Use at your own risk.
Gerald Combs gerald@wireshark.org
Gilbert Ramirez gram@alumni.rice.edu
Guy Harris gharris@sonic.net
Wireshark is a popular network packet capture and analysis tool. It is previously named as Ethereal. Wireshark captures packets from a different type of interfaces and prints them as a floating list to the screen. It also provides detailed information about a specific packet. Wireshark can also read already captured packets in different formats like cap , pcap etc.
Download and Install
Wireshark is supported by a lot of platforms. Let’s install
For Windows operating system we need to download the wireshark installation file from the official web site. The latest version of Wireshark can be downloaded from the following link.
https://www.wireshark.org/#download
Windows provides a different type of installers like 32 bit, 64 bit, portable. If we do not have required privileges to install application we can use portable Wireshark which do not needs installation.
Ubuntu, Debian, Mint:
Ubuntu, Debian, Mint and other deb based distributions provide Wireshark from their official repositories. Just issue the following command to install Wireshark.
$ sudo apt install wireshark-qt
Fedora, CentOS, RedHat:
Fedora, CentOS, and RedHat provide Wireshark package in their repositories too. In order to install Wireshark in Fedora, CentOS and RedHat issue following command.
$ sudo yum install wireshark-qt
Select Interface and Capture Packets
One of the fundamental operation with Wireshark is selecting an interface to capture network packets. When we open Wireshark we will see the following screen. Available interfaces are listed with their name current network traffic on that interface is shown with a simple graph.
Here we will see that namedLocal Area Connection interface has some network traffic. By the way, Wireshark can listen to USB interfaces too.
We double click on andLocal Area Connection this will start network capture on this interface and a new screen will be opened where the network packets flow.
Show Specific Packet Details
We generally look at some specific packets to analyze. We can locate the packet we want in a simple way from the right side of the packet flow list and click on the packet. This will show detailed packet information in the middle section where Frame, Ethernet, IP, TCP/UDP, and Application layer information provided. In the lowest and third section, we will see application layer data in hex format.
Filter Captured Packets
In a busy network, there will be a lot of packets flying around. This will make to look some packets one by one very hard job. Wireshark has very powerful filtering features. We can filter captured packets according to a protocol like IP, TCP, UDP, IP address, Source address destination address, TCP port, mac address, DNS packet, SNMP packet etc. There are a lot of them. We will simply look most popular of them. We can get the whole list of supported filter expressions by clicking buttonExpression on the left up corner. We can see the filter textbox and buttonExpression.
List of supported expressions. As we can see there are a lot of protocols like.
In this example we will filter ARP packets and section or the packet list only provides ARP protocol packets. We will only use arp in the filter box.
arp
Filter According To Destination IP Address
Another popular usage is filtering packet those have specified destination IP address. In this example, we will filter and only show those packets which have a destination IP address is 192.168.122.ip.
ip.dst == 192.168.122.1
Filter According To Source IP Address
We can also filter according to source IP address too. In this example, we will filter IP source address 192.168.122.1
ip.src == 192.168.122.1
Filter DNS Packets
We can filter DNS packets with keyworddnsserver like below.
dnsserver
Follow TCP Stream
During a regular web page load or request, there will be some round trip to download data. If we need to inspect the whole request and response traffic we need to filter multiple packets. We can accomplish this by filtering according to a TCP session or TCP stream. It is called Follow TCP Stream .
This will provide the following screen which provides the whole HTTP request and response session. We can also search these with bottomFind.
Packet Statistics
One of the best features is the packet statistics. We can get a lot of different type of statistics with the menuStatistics from up. We can get the following statistical information.
- Endpoints
- HTTP
- IP
- Ethernet
- PRotocol Hierarchy
Stop Capturing
We can stop capturing network packets with Wireshark with the red button in the toolbar menu.
Save Captured Packets
We can save captured files. In order to save we firstly stop live packet capture. Then from the menuFile and save or Save as menus.
Open Capture Files Like Cap , Pcap
We can open already saved a different type of capture formats like cap, pcap ,ngcap etc. from File menu. We can also open recently opened capture files.
Алексей Максимов показывает, как перехватывать сетевой трафик с сервера без Network Monitor/Wireshark.
В системах Windows для захвата и последующего анализа сетевого трафика многие из нас пользуются такими известными инструментами как Network Monitor или Wireshark. Захват трафика через эти инструменты в наблюдаемой системе предполагает установку дополнительных компонент, выстраивающихся в функции сетевого обмена. Начиная с Windows 7 / Windows Server 2008 R2 у нас появилась возможность выполнять захват трафика встроенными в систему средствами, то есть мы можем выполнить захват трафика на интересующей нас системе не выполняя непосредственную установку дополнительных программных средств, а полученный в результате захвата файл сетевого дампа в дальнейшем анализировать на той системе где установлены соответствующие средства анализа, например на рабочей станции администратора с установленным Network Monitor.
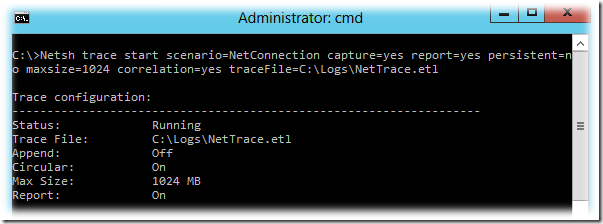
Для того, чтобы активировать захват сетевого трафика проходящего через все сетевые интерфейсы на интересующей нас системе выполним команду с правами Администратора:
|
Netsh trace start scenario=NetConnection capture=yes report=yes persistent=no maxsize=1024 correlation=yes traceFile=C:LogsNetTrace.etl |
При этом каталог, который мы указываем в качестве сохранения файла захвата должен существовать в файловой системе, иначе мы получим ошибку ‘The system cannot find the path specified‘.
Если обследуемая система имеет несколько сетевых интерфейсов и нас интересует трафик только на определённом интерфейсе, то синтаксис команды будет выглядеть примерно так:
|
Netsh trace start scenario=NetConnection capture=yes ipv4.address=192.168.0.100 report=yes persistent=no maxsize=1024 correlation=yes traceFile=C:LogsNetTrace.etl |
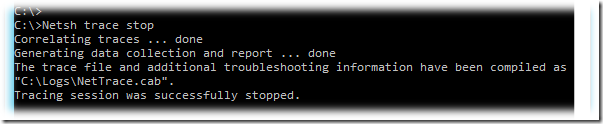
Захват трафика запущен и после того, как мы выполнили необходимые манипуляции, например воспроизвели изучаемую проблему из-за которой мы и решили анализировать трафик, останавливаем захват трафика командой:
В результате будет сгенерирован ETL файл а также CAB архив содержащий дополнительные данные, которые могут потребоваться для анализа сетевых проблем.
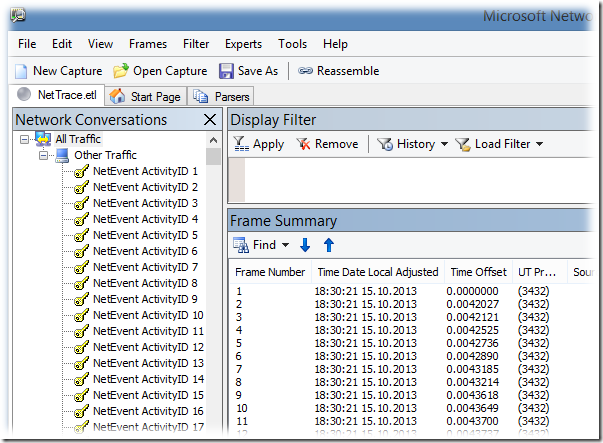
Полученный ETL файл копируем на рабочую станцию Администратора, запускаем Network Monitor и открываем файл из меню File > Open > Capture
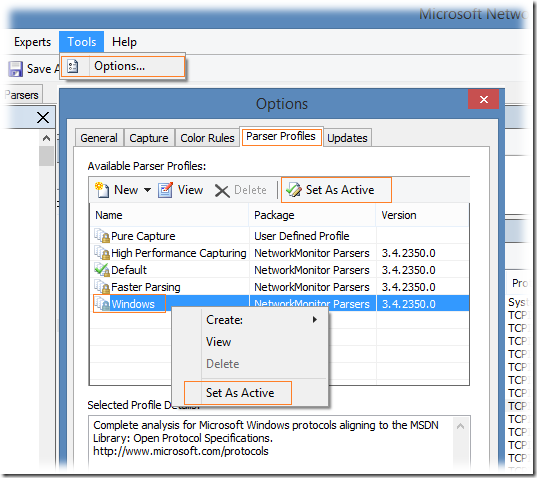
Загруженные данные будут разложены на фреймы с малопонятной структурой, да ещё и с предупреждением в описании практически каждого фрейма типа ‘Windows stub parser: Requires full Common parsers. See the «How Do I Change Parser Set Options(Version 3.3 or before) or Configure Parser Profile (Version 3.4)» help topic for tips on loading these parser sets‘. Для того чтобы получить более или менее читаемый вид, нужно применить так называемый Parser Profile. Через меню Tools > Options откроем свойства Parser Profiles и назначим в качестве активного профиля – Windows
После этого данные трассировки будут перечитаны и представлены в более удобоваримой форме и теперь можно «забуриваться» в анализ…
Дополнительная информация:
The troubleshooters and problem solvers — Network tracing (packet sniffing) built-in to Windows Server 2008 R2 and Windows Server 2012
Blog IT, IS, etc… — Network trace without NetMon, WireShark, etc…
Blog IT, IS, etc… — Network trace without NetMon, wireShark, etc… Part 2
Wireshark is a software tool used to monitor the network traffic through a network interface. It is the most widely used network monitoring tool today. Wireshark is loved equally by system administrators, network engineers, network enthusiasts, network security professionals, and black hat hackers.
It is a network protocol analyzer that captures packets from a network connection. The packet is the name given to a distinct unit of data in a typical Ethernet network.
System Requirements :
System requirements are the required specifications a device must have in order to use certain hardware or software. Before installing a software program or purchasing a hardware device, you can check the system requirements to make sure the product is compatible with your system. Typical system requirements for a Wireshark include:
The system requirement of Wireshark depends on the environment in which you are using it and on the size of the captured file you are going to examine. If the files captured are large then they will require more memory and disk space. The time-consuming task like packet filtering or packet analysis is single-threaded in Wireshark. Therefore it does not make a difference whether you are using Multiprocessor/Hyper thread systems or not.
System Requirements for Windows :
Wireshark should work for any version of Windows that is still within its extended support period. Wireshark currently supports Windows 11, 10, 8.1, 8, Server 2019, Server 2016, Server 2012 R2, and Server 2012. The following requirements are also needed:
- 64-bit AMD64/x86-64 or 32-bit x86 CPU architecture.
- At least 500 MB available RAM. It requires more RAM to process Larger capture files.
- At least 500 MB of available disk space. The capture files require extra disk space.
- It requires a minimum resolution of 1280 × 1024 or higher.
A supported network card for capturing packets. In the case of Ethernet, any card supported by Windows should work and in the case of WLAN, it requires special equipment to capture raw 802.11 information.
The older version of Wireshark supports Windows which is outside Microsoft’s extended lifecycle support.
- Wireshark 3.6 was the last official release to support 32-bit Windows
- Wireshark 3.2 was the last official release to support Windows 7 and Windows Server 2008 R2.
- Wireshark 2.2 was the last official release to support Windows Vista and Windows Server 2008 sans R2
- Wireshark 1.12 was the last official release to support Windows Server 2003
System Requirements for macOS:
Currently, Wireshark supports macOS 10.13 and later. The older version of Wireshark before 3.6 supports macOS 10.12. The other system requirements are similar to the specifications listed above for Windows.
- Wireshark 3.4 was the last official release to support macOS 10.12.
- Wireshark 2.6 was the last official release to support Mac OS X 10.6 and 10.7 and OS X 10.8 to 10.11.
- Wireshark 2.0 was the last official release to support OS X on 32-bit Intel.
- Wireshark 1.8 was the last official release to support Mac OS X on PowerPC.
System Requirements for UNIX/LINUX:
Wireshark also runs on most UNIX and Linux distros and most BSD variants. The other system requirements are similar to the specifications listed above for Windows.
Wireshark Binary packages are available for the following platforms :
- Alpine Linux
- Arch Linux
- Red Hat Enterprise Linux / CentOS / Fedora
- Debian GNU/Linux
- FreeBSD
- Oracle Solaris
You can also refer to the article How to Install Wireshark on Windows? to know more about Wireshark.
Last Updated :
25 Aug, 2022
Like Article
Save Article
Алексей Максимов показывает, как перехватывать сетевой трафик с сервера без Network Monitor/Wireshark.
В системах Windows для захвата и последующего анализа сетевого трафика многие из нас пользуются такими известными инструментами как Network Monitor или Wireshark. Захват трафика через эти инструменты в наблюдаемой системе предполагает установку дополнительных компонент, выстраивающихся в функции сетевого обмена. Начиная с Windows 7 / Windows Server 2008 R2 у нас появилась возможность выполнять захват трафика встроенными в систему средствами, то есть мы можем выполнить захват трафика на интересующей нас системе не выполняя непосредственную установку дополнительных программных средств, а полученный в результате захвата файл сетевого дампа в дальнейшем анализировать на той системе где установлены соответствующие средства анализа, например на рабочей станции администратора с установленным Network Monitor.
Для того, чтобы активировать захват сетевого трафика проходящего через все сетевые интерфейсы на интересующей нас системе выполним команду с правами Администратора:
|
Netsh trace start scenario=NetConnection capture=yes report=yes persistent=no maxsize=1024 correlation=yes traceFile=C:\Logs\NetTrace.etl |
При этом каталог, который мы указываем в качестве сохранения файла захвата должен существовать в файловой системе, иначе мы получим ошибку ‘The system cannot find the path specified‘.
Если обследуемая система имеет несколько сетевых интерфейсов и нас интересует трафик только на определённом интерфейсе, то синтаксис команды будет выглядеть примерно так:
|
Netsh trace start scenario=NetConnection capture=yes ipv4.address=192.168.0.100 report=yes persistent=no maxsize=1024 correlation=yes traceFile=C:\Logs\NetTrace.etl |
Захват трафика запущен и после того, как мы выполнили необходимые манипуляции, например воспроизвели изучаемую проблему из-за которой мы и решили анализировать трафик, останавливаем захват трафика командой:
В результате будет сгенерирован ETL файл а также CAB архив содержащий дополнительные данные, которые могут потребоваться для анализа сетевых проблем.
Полученный ETL файл копируем на рабочую станцию Администратора, запускаем Network Monitor и открываем файл из меню File > Open > Capture
Загруженные данные будут разложены на фреймы с малопонятной структурой, да ещё и с предупреждением в описании практически каждого фрейма типа ‘Windows stub parser: Requires full Common parsers. See the «How Do I Change Parser Set Options(Version 3.3 or before) or Configure Parser Profile (Version 3.4)» help topic for tips on loading these parser sets‘. Для того чтобы получить более или менее читаемый вид, нужно применить так называемый Parser Profile. Через меню Tools > Options откроем свойства Parser Profiles и назначим в качестве активного профиля – Windows
После этого данные трассировки будут перечитаны и представлены в более удобоваримой форме и теперь можно «забуриваться» в анализ…
Дополнительная информация:
The troubleshooters and problem solvers — Network tracing (packet sniffing) built-in to Windows Server 2008 R2 and Windows Server 2012
Blog IT, IS, etc… — Network trace without NetMon, WireShark, etc…
Blog IT, IS, etc… — Network trace without NetMon, wireShark, etc… Part 2
- Remove From My Forums
-
Question
-
Hi friends,
I downloaded wire shark to monitor my home network traffic it work perfect,
So i tried to install it on a WINDOWS SERVER 2008, it works but the problem is it only show me the local activity of the machine.(THE SBS2008) not of the network, Yeah it show me which IP is retrieving information from the server in vise verse, which website
I’m hosting (it shows me only the local activity of the ADMINISTRATOR of the SERVER)I want to monitor ALL the internet activity (HTTP, FTP etc..) of my users log in on my domain.how to i configure wire shark configuration to do so??
I will appreciate your help
Thanks in advance .
Answers
-
Hi,
Thanks for posting here.
Not sure if the “Port Mirroring” feature is supported on your network devices . If so , you can create a mirror port on that device in order to connect
with a WIRESHARK installed host for capturing the traffics :Port mirroring
http://en.wikipedia.org/wiki/Port_mirroring
Thanks.
Tiger Li
Please remember to click “Mark as Answer” on the post that helps you, and to click “Unmark as Answer” if a marked post does not actually answer your question. This can be beneficial to other community members reading the thread.
-
Marked as answer by
Monday, September 12, 2011 5:19 AM
-
Marked as answer by