How do I find out which process is listening on a TCP or UDP port on Windows?
Mateen Ulhaq
24.7k19 gold badges102 silver badges136 bronze badges
asked Sep 7, 2008 at 6:26
readonlyreadonly
344k107 gold badges204 silver badges205 bronze badges
11
PowerShell
TCP
Get-Process -Id (Get-NetTCPConnection -LocalPort YourPortNumberHere).OwningProcess
UDP
Get-Process -Id (Get-NetUDPEndpoint -LocalPort YourPortNumberHere).OwningProcess
cmd
netstat -a -b
(Add -n to stop it trying to resolve hostnames, which will make it a lot faster.)
Note Dane’s recommendation for TCPView. It looks very useful!
-a Displays all connections and listening ports.
-b Displays the executable involved in creating each connection or listening port. In some cases well-known executables host multiple independent components, and in these cases the sequence of components involved in creating the connection or listening port is displayed. In this case the executable name is in [] at the bottom, on top is the component it called, and so forth until TCP/IP was reached. Note that this option can be time-consuming and will fail unless you have sufficient permissions.
-n Displays addresses and port numbers in numerical form.
-o Displays the owning process ID associated with each connection.
answered Sep 7, 2008 at 6:28
15
There’s a native GUI for Windows:
-
Start menu → All Programs → Accessories → System Tools → Resource Monitor
-
or run
resmon.exe, -
or from TaskManager → Performance tab.
serge
14.1k35 gold badges124 silver badges206 bronze badges
answered May 18, 2014 at 5:02
bcorsobcorso
45.7k10 gold badges63 silver badges76 bronze badges
10
For Windows:
netstat -aon | find /i "listening"
xash
3,70210 silver badges22 bronze badges
answered Sep 7, 2008 at 6:32
akuaku
122k32 gold badges174 silver badges203 bronze badges
6
Use TCPView if you want a GUI for this. It’s the old Sysinternals application that Microsoft bought out.
answered Sep 7, 2008 at 6:38
DaneDane
9,7375 gold badges28 silver badges23 bronze badges
3
The -b switch mentioned in most answers requires you to have administrative privileges on the machine. You don’t really need elevated rights to get the process name!
Find the pid of the process running in the port number (e.g., 8080)
netstat -ano | findStr "8080"
Find the process name by pid
tasklist /fi "pid eq 2216"
Jaywalker
3,0793 gold badges29 silver badges44 bronze badges
answered Jan 24, 2018 at 3:50
Ram SharmaRam Sharma
2,4971 gold badge8 silver badges7 bronze badges
You can get more information if you run the following command:
netstat -aon | find /i "listening" |find "port"
using the ‘Find’ command allows you to filter the results. find /i "listening" will display only ports that are ‘Listening’. Note, you need the /i to ignore case, otherwise you would type find «LISTENING». | find "port" will limit the results to only those containing the specific port number. Note, on this it will also filter in results that have the port number anywhere in the response string.
answered Oct 8, 2013 at 18:56
Nathan24Nathan24
1,3721 gold badge11 silver badges20 bronze badges
4
-
Open a command prompt window (as Administrator) From «Start\Search box» Enter «cmd» then right-click on «cmd.exe» and select «Run as Administrator»
-
Enter the following text then hit Enter.
netstat -abno-a Displays all connections and listening ports.
-b Displays the executable involved in creating each connection or
listening port. In some cases well-known executables host
multiple independent components, and in these cases the
sequence of components involved in creating the connection
or listening port is displayed. In this case the executable
name is in [] at the bottom, on top is the component it called,
and so forth until TCP/IP was reached. Note that this option
can be time-consuming and will fail unless you have sufficient
permissions.-n Displays addresses and port numbers in numerical form.
-o Displays the owning process ID associated with each connection.
-
Find the Port that you are listening on under «Local Address»
-
Look at the process name directly under that.
NOTE: To find the process under Task Manager
-
Note the PID (process identifier) next to the port you are looking at.
-
Open Windows Task Manager.
-
Select the Processes tab.
-
Look for the PID you noted when you did the netstat in step 1.
-
If you don’t see a PID column, click on View / Select Columns. Select PID.
-
Make sure “Show processes from all users” is selected.
-
answered Nov 8, 2012 at 1:49
CyborgCyborg
1,24412 silver badges12 bronze badges
Get PID and Image Name
Use only one command:
for /f "tokens=5" %a in ('netstat -aon ^| findstr 9000') do tasklist /FI "PID eq %a"
where 9000 should be replaced by your port number.
The output will contain something like this:
Image Name PID Session Name Session# Mem Usage
========================= ======== ================ =========== ============
java.exe 5312 Services 0 130,768 K
Explanation:
-
it iterates through every line from the output of the following command:
netstat -aon | findstr 9000 -
from every line, the PID (
%a— the name is not important here) is extracted (PID is the5th element in that line) and passed to the following commandtasklist /FI "PID eq 5312"
If you want to skip the header and the return of the command prompt, you can use:
echo off & (for /f "tokens=5" %a in ('netstat -aon ^| findstr 9000') do tasklist /NH /FI "PID eq %a") & echo on
Output:
java.exe 5312 Services 0 130,768 K
answered Feb 10, 2016 at 10:17
ROMANIA_engineerROMANIA_engineer
54.6k29 gold badges203 silver badges200 bronze badges
1
First we find the process id of that particular task which we need to eliminate in order to get the port free:
Type
netstat -n -a -o
After executing this command in the Windows command line prompt (cmd), select the pid which I think the last column. Suppose this is 3312.
Now type
taskkill /F /PID 3312
You can now cross check by typing the netstat command.
NOTE: sometimes Windows doesn’t allow you to run this command directly on CMD, so first you need to go with these steps:
From the start menu -> command prompt (right click on command prompt, and run as administrator)
answered Aug 23, 2014 at 15:25
1
With PowerShell 5 on Windows 10 or Windows Server 2016, run the Get-NetTCPConnection cmdlet. I guess that it should also work on older Windows versions.
The default output of Get-NetTCPConnection does not include Process ID for some reason and it is a bit confusing. However, you could always get it by formatting the output. The property you are looking for is OwningProcess.
-
If you want to find out the ID of the process that is listening on port 443, run this command:
PS C:\> Get-NetTCPConnection -LocalPort 443 | Format-List LocalAddress : :: LocalPort : 443 RemoteAddress : :: RemotePort : 0 State : Listen AppliedSetting : OwningProcess : 4572 CreationTime : 02.11.2016 21:55:43 OffloadState : InHost -
Format the output to a table with the properties you look for:
PS C:\> Get-NetTCPConnection -LocalPort 443 | Format-Table -Property LocalAddress, LocalPort, State, OwningProcess LocalAddress LocalPort State OwningProcess ------------ --------- ----- ------------- :: 443 Listen 4572 0.0.0.0 443 Listen 4572 -
If you want to find out a name of the process, run this command:
PS C:\> Get-Process -Id (Get-NetTCPConnection -LocalPort 443).OwningProcess Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName ------- ------ ----- ----- ------ -- -- ----------- 143 15 3448 11024 4572 0 VisualSVNServer
answered Nov 2, 2016 at 19:19
bahrepbahrep
30k12 gold badges103 silver badges151 bronze badges
To get a list of all the owning process IDs associated with each connection:
netstat -ao |find /i "listening"
If want to kill any process have the ID and use this command, so that port becomes free
Taskkill /F /IM PID of a process
answered Apr 17, 2014 at 14:38
Monis MajeedMonis Majeed
1,35814 silver badges21 bronze badges
1
It is very simple to get the port number from a PID in Windows.
The following are the steps:
-
Go to run → type cmd → press Enter.
-
Write the following command…
netstat -aon | findstr [port number](Note: Don’t include square brackets.)
-
Press Enter…
-
Then cmd will give you the detail of the service running on that port along with the PID.
-
Open Task Manager and hit the service tab and match the PID with that of the cmd, and that’s it.
answered May 30, 2016 at 6:36
Nishat LakhaniNishat Lakhani
7331 gold badge8 silver badges20 bronze badges
0
netstat -aof | findstr :8080 (Change 8080 for any port)
answered Feb 16, 2021 at 23:59
David JesusDavid Jesus
1,9812 gold badges29 silver badges34 bronze badges
To find out which specific process (PID) is using which port:
netstat -anon | findstr 1234
Where 1234 is the PID of your process. [Go to Task Manager → Services/Processes tab to find out the PID of your application.]
answered Dec 14, 2018 at 6:55
Talha ImamTalha Imam
1,0461 gold badge20 silver badges22 bronze badges
2
In case someone need an equivalent for macOS like I did, here is it:
lsof -i tcp:8080
After you get the PID of the process, you can kill it with:
kill -9 <PID>
answered Aug 12, 2020 at 11:22
wzsowzso
3,5325 gold badges28 silver badges48 bronze badges
2
Just open a command shell and type (saying your port is 123456):
netstat -a -n -o | find "123456"
You will see everything you need.
The headers are:
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:37 0.0.0.0:0 LISTENING 1111
This is as mentioned here.
answered Jan 25, 2017 at 0:13
1
If you’d like to use a GUI tool to do this there’s Sysinternals’ TCPView.
answered Sep 7, 2008 at 6:40
David WebbDavid Webb
191k57 gold badges313 silver badges299 bronze badges
-
Open the command prompt — start → Run →
cmd, or start menu → All Programs → Accessories → Command Prompt. -
Type
netstat -aon | findstr '[port_number]'
Replace the [port_number] with the actual port number that you want to check and hit Enter.
- If the port is being used by any application, then that application’s detail will be shown. The number, which is shown at the last column of the list, is the PID (process ID) of that application. Make note of this.
-
Type
tasklist | findstr '[PID]'
Replace the [PID] with the number from the above step and hit Enter.
- You’ll be shown the application name that is using your port number.
answered May 9, 2019 at 12:18
Anatole ABEAnatole ABE
5751 gold badge7 silver badges12 bronze badges
2
PowerShell
If you want to have a good overview, you can use this:
Get-NetTCPConnection -State Listen | Select-Object -Property *, `
@{'Name' = 'ProcessName';'Expression'={(Get-Process -Id $_.OwningProcess).Name}} `
| select ProcessName,LocalAddress,LocalPort
Then you get a table like this:
ProcessName LocalAddress LocalPort
----------- ------------ ---------
services :: 49755
jhi_service ::1 49673
svchost :: 135
services 0.0.0.0 49755
spoolsv 0.0.0.0 49672
For UDP, it is:
Get-NetUDPEndpoint | Select-Object -Property *, `
@{'Name' = 'ProcessName';'Expression'={(Get-Process -Id $_.OwningProcess).Name}} `
| select ProcessName,LocalAddress,LocalPort
answered Feb 27, 2022 at 22:16
Oliver GaidaOliver Gaida
1,7327 silver badges14 bronze badges
Netstat:
- -a displays all connection and listening ports
- -b displays executables
- -n stop resolve hostnames (numerical form)
-
-o owning process
netstat -bano | findstr "7002" netstat -ano > ano.txt
The Currports tool helps to search and filter
answered Sep 23, 2018 at 5:05
Blue CloudsBlue Clouds
7,3655 gold badges72 silver badges113 bronze badges
Type in the command: netstat -aon | findstr :DESIRED_PORT_NUMBER
For example, if I want to find port 80: netstat -aon | findstr :80
This answer was originally posted to this question.
answered Nov 22, 2016 at 15:36
TechnotronicTechnotronic
8,4744 gold badges40 silver badges53 bronze badges
netstat -ao and netstat -ab tell you the application, but if you’re not a system administrator you’ll get «The requested operation requires elevation».
It’s not ideal, but if you use Sysinternals’ Process Explorer you can go to specific processes’ properties and look at the TCP tab to see if they’re using the port you’re interested in. It is a bit of a needle and haystack thing, but maybe it’ll help someone…
answered Mar 13, 2014 at 19:57
Tony DelroyTony Delroy
103k15 gold badges177 silver badges253 bronze badges
1
Using Windows’ default shell (PowerShell) and without external applications
For those using PowerShell, try Get-NetworkStatistics:
> Get-NetworkStatistics | where Localport -eq 8000
ComputerName : DESKTOP-JL59SC6
Protocol : TCP
LocalAddress : 0.0.0.0
LocalPort : 8000
RemoteAddress : 0.0.0.0
RemotePort : 0
State : LISTENING
ProcessName : node
PID : 11552
answered Aug 25, 2016 at 13:36
mikemaccanamikemaccana
112k99 gold badges392 silver badges497 bronze badges
3
I recommend CurrPorts from NirSoft.
CurrPorts can filter the displayed results. TCPView doesn’t have this feature.
Note: You can right click a process’s socket connection and select «Close Selected TCP Connections» (You can also do this in TCPView). This often fixes connectivity issues I have with Outlook and Lync after I switch VPNs. With CurrPorts, you can also close connections from the command line with the «/close» parameter.
answered Jun 29, 2015 at 22:07
JoshJosh
2,1422 gold badges23 silver badges20 bronze badges
0
A single-line solution that helps me is this one. Just substitute 3000 with your port:
$P = Get-Process -Id (Get-NetTCPConnection -LocalPort 3000).OwningProcess; Stop-Process $P.Id
Edit: Changed kill to Stop-Process for more PowerShell-like language
answered Feb 3, 2019 at 14:46
Angel VenchevAngel Venchev
7071 gold badge7 silver badges18 bronze badges
2
Use:
netstat -a -o
This shows the PID of the process running on a particular port.
Keep in mind the process ID and go to Task Manager and services or details tab and end the process which has the same PID.
Thus you can kill a process running on a particular port in Windows.
answered Aug 13, 2013 at 2:32
nishanisha
7112 gold badges14 silver badges28 bronze badges
To find pid who using port 8000
netstat -aon | findstr '8000'
To Kill that Process in windows
taskkill /pid pid /f
where pid is the process id which you get form first command
answered Jul 14, 2020 at 6:13
jizjiz
3083 silver badges7 bronze badges
2
Follow these tools: From cmd: C:\> netstat -anob with Administrator privileges.
Process Explorer
Process Dump
Port Monitor
All from sysinternals.com.
If you just want to know process running and threads under each process, I recommend learning about wmic. It is a wonderful command-line tool, which gives you much more than you can know.
Example:
c:\> wmic process list brief /every:5
The above command will show an all process list in brief every 5 seconds. To know more, you can just go with /? command of windows , for example,
c:\> wmic /?
c:\> wmic process /?
c:\> wmic prcess list /?
And so on and so forth. 
1
You can also check the reserved ports with the command below. Hyper-V reserve some ports, for instance.
netsh int ipv4 show excludedportrange protocol=tcp
answered Nov 24, 2020 at 14:50
At any one time, there’s a whole bunch of information being sent between your Windows 10 PC and the endless void of the Internet. This is done using a process whereby network-dependent processes seek out TCP and UDP ports, which they use to communicate with the Internet. First, your data gets sent to remote ports at the destination or website your processes are trying to connect to, then it gets received at local ports back on your PC.
Most of the time, Windows 10 knows how to manage ports and ensure that traffic is being directed through the right ports so that those processes can connect with what they need to. But sometimes two processes may be assigned to one port, or maybe you just want to get a better picture of your network traffic and what’s going in and out.
That’s why wrote this guide that shows you how to check open ports on Windows and see which applications are using which ports.
Also read: How to Set Up Port Forwarding in Windows
Check Port Usage With Nirsoft CurrPorts
NirSoft is one of the best indie software developers, giving us great utilities, like PassView and WirelessKeyView. While some people will prefer checking their ports without installing third-party software (in which case, scroll down to the CMD method), CurrPorts is easily the fastest and most convenient way to check port status on Windows.

Once you’ve installed CurrPorts, just open it to see a list of all your ports currently in use. If you’re looking for local ports in use, just click the «Local Port» column at the top to order the list by port number (handy if you’re looking for a specific one). You can do the same thing with remote ports, too.
If you want to really find specific ports, click the «Advanced Filters» icon at the top and enter your string in the format they suggest. It should look something like the below image.

Hit OK when you’re ready, and the list will filter down to your queries.
Also read: How to Open Ports and Set Up Port Forwarding on Your Router
List Open Ports Using the Command Prompt
The integrated — though not necessarily the simplest — way to check open ports is to use the trusty command prompt.
Click the Start button, type cmd, then right-click «Command Prompt» when it shows up in the search results. Click «Run as administrator.»
Once you’re in the elevated command prompt, enter the following command:
This will steadily bring up a list of open ports that is probably quite long, along with the Windows processes that are using them. (You can press Ctrl + A , then Ctrl + C to copy all information to the clipboard.) On the average PC, there will be two main local IP addresses that contain ports on your PC.

The first, in our case, is «127.0.0.1.» This IP address is otherwise known as «localhost» or a «loopback address,» and any process listening to ports here is communicating internally on your local network without using any network interface. The actual port is the number you see after the colon. (See image below.)

The bulk of your processes will probably be listening to ports prefixed with «192.168.xxx.xxx,» which is your IP address. This means the processes you see listed here are listening for communications from remote Internet locations (such as websites). Again, the port number is the number after the colon.

Also read: How to Disable USB Ports in Windows 10
Install TCPView to Check Open Ports
If you don’t mind installing a third-party app and want to have more control over what’s going on with all your ports, you can use a lightweight app called TCPView. This immediately brings up a list of processes and their associated ports.

What make this better than the command prompt is that you can actively see the ports opening, closing and sending packets. Just look for the green, red and yellow highlights. You can also reorder the list by clicking the column headings, making it easier to find the process you want or two separate processes vying for the same port.
If you do find a process or connection you want to close, just right-click that process. You can then select «End process,» which is exactly the same function as the one in Windows task manager. Or you can click «Close Connection» to leave the process open but stop it from listening on a given port.

If you’re having some trouble in Windows 10, then see whether a Windows update may be causing it. We also have a handy guide for managing the health of your hard drive in Windows 10.
Tech writer at Make Tech Easier. Enjoys Android, Windows, and tinkering with retro console emulation to breaking point.
Subscribe to our newsletter!
Our latest tutorials delivered straight to your inbox
In this tutorial, we will learn how to run the netstat command to check open ports in Windows Operating System. We will also look at command options and how to use the findstr command (similar to grep) to filter the netstat output.
To check open ports, open a command prompt (or PowerShell) as administrator and run the netstat command as follows:
netstat -aonThe command displays lots of information. What you should pay attention to are Local Addresses that are in the LISTENING state.
As you can see in the previous screenshot, In my Windows 10 computer, port 22 (SSH) is open.
Administrators can run the following command to show opened ports only without all other details:
netstat -aon | findstr /i listeningOne important point is that the Windows Firewall may block a port even if it is in the listening state. In the Windows Defender Firewall with Advanced Security, there has to be a corresponding inbound firewall rule to match the listening port (Anything with a green checkmark is an open rule).
The Foreign Address column of the output shows the IP address and port of the computer/server at the remote end of the connection.
To check that the port is open from a remote computer, an administrator can run the telnet command from a remote computer against the IP address of the Windows computer.
For example, to check if port 22 is open, I will run the telnet command from a remote computer as follows:
telnet IP_ADDRESS 22Replace IP_ADDRESS with the actual IP Address of the Windows computer.
Filtering netstat using findstr
Administrators can use the findstr CMD command (which is similar to grep) to filter netstat command data based on string patterns.
For example, run the following command to check TCP connections in TIME_WAIT State.
netstat -a | findstr /i TIME_WAITThe /I option is for the case insensitive matching.
Command Options
Windows netstat command, without any command-line arguments, displays active TCP connections.
It also includes some useful command options to show network connections and ports in various forms, such as show connections and opened ports based on the protocol, find the process id of a connection/port, view network statics, and find the application that utilizes connections and ports.
| -a | displays all network connections and ports on which Windows is listening (include both IPv4 or IPv6 addresses). |
| -b | The output shows you which applications are using each active connection and ports (need administrative privileges). |
| -e | Displays network statistics, such as the Errors, the number of bytes, and packets sent and received. |
| -n | Displays addresses and ports in numerical format. |
| -f | When used, the output will contain Fully Qualified Domain Names (FQDNs) of IP addresses, if available. |
| -o | Displays an additional column that contains the Process ID (PID). |
| -p | Display data for a specific protocol (e.g., -p TCP). The Protocol can be one of the following: TCP, UDP, TCPv6, or UDPv6. If combined with the -s option, Protocol can be TCP, UDP, ICMP, IP, TCPv6, UDPv6, ICMPv6, or IPv6. |
| -r | Check Windows routing table. |
| -s | Displays detailed network statistics for each protocol (IPv4, IPv6, ICMPv4, ICMPv6, TCP, and UDP). |
| interval | Sets Time interval (in seconds) to automatically update the output. See examples to learn more. |
Examples: Using the netstat command
List all Active TCP connections:
netstatCheck open ports:
netstat -aon | findstr /i listeningOnly want to see information about TCP protocol:
netstat -a -p tcpShow network statistics:
netstat -sReal-time network monitoring — In the following example, we set a 5 second time interval to check active network connections in real-time. The number 5 causes the command to repeat every five seconds (Press CTRL+C to quit).
netstat -n 5If you need more information about the Windows netstat command, type netstat \? in the command prompt.
Whenever an application wants to make itself accessible over the network, it claims a TCP/IP port, which means that port can’t be used by anything else. So if you need to use an in-use port, how do you tell what application is holding it?
There’s a number of ways to tell which application has the port locked, here we will use a windows built-in way using the command line and Task Manager.
Using Built-In Tools to See What is Listening on a Port
The first step is to use a command-line tool to see what ports are in use, and use a special flag that tells us which port is assigned to each Windows process identifier number. Then we can use that number to look up exactly which process it is.
Open up a command prompt and type in the following—you may have to open in Administrator mode to see all processes:
netstat -ab | more
This will immediately show you a list, although it’s maybe a little complicated. You’ll see the process name in the list, and you can search for it.
You can also use this other method, which takes an extra step, but makes it easier to locate the actual process:
netstat -aon | more
If you look on the right-hand side, you’ll see where I’ve highlighted the list of PIDs, or Process Identifiers. Find the one that’s bound to the port that you’re trying to troubleshoot—for this example, you’ll see that 0.0.0.0:80, or port 80, is in use by PID 1184.
Now you can simply open up Task Manager—you might have to use the option to Show Processes for All Users, and then you’ll be able to find the PID in the list. Once you’re there, you can use the End Process, Open File Location, or Go to Service(s) options to control the process or stop it.
Alternatively you can even use resource monitor to stop any process that is running. To open resource monitor type resmon.exe in run. This will bring up the resource monitor window.
There would be situations were some other process is running at port 80. To stop anything running in port 80 the following command can be used from command prompt.
net stop http /y
Frequently Asked Questions (FAQs)
What application is listening on a TCP IP port in Windows?
Netstat is a diagnostic tool that creates a list of open ports that the machine is listening to, as well as the ports it is currently connected to on other machines. In Netstat, stat stands for state or statistics, which tells you the current network status of every TCP connection.
How do I find out what application is using a TCP port?
You can use Netstat -b -a -o.
This tool provides a list of all open ports and their associated processes. The -o shows the process id, which you can look up in your task manager or processes tab. To end that process, simply enter taskkill /PID xxxx.
How can I tell if a server is listening on a port?
On the server itself, use Netstat -an to check to see which ports are listening. From outside the server, telnet host port can be used to check connections. A refused connection means nothing is running, whereas an accepted connection means something is running. Timeout implies a firewall is blocking access.
How do I find out what application is using port 8080?
Open the diagnostic tool, netstat -ano. This tool will list the PID (Process Identifier) that is listening to port 80. Open the Task Manager’s Processes tab. Select “View” and “Select Columns” menu. Activate the PID column to see the name of the process listening on port 80.
Is Port 8080 http or https?
Port 8080 is a non-standard, high number port that is popular as an alternative port for HTTP servers, most often application servers. Port 8443 is a default alternative port for HTTPS servers. It can also be used as an alternative port for any protocol like ssh, FTP, NTP, BOOTP, etc.
Why is port 8080 default?
Historically, only authorized system administrators were able to establish and operate a web server on port 80, since this was within the first 1023-port privileged region. When non-administrators wished to run their own web servers, they often chose port 8080 to host a secondary or alternate web server.
Содержание
- Используем команду netstat для просмотра открытых портов
- Отображение всех подключений и ожидающих портов
- Постраничное отображение открытых портов
- Запись результатов в текстовый файл
- Поиск по содержимому
- Вопросы и ответы
Netstat — одна из встроенных команд операционной системы Windows. В ее функциональность входит отображение состояния сети со всеми требуемыми деталями. Пользователь задействует встроенный синтаксис, чтобы отфильтровать результаты или задать дополнительные действия для этой утилиты. В рамках сегодняшнего материала мы бы хотели рассказать о доступных методах просмотра открытых портов с помощью этого стандартного инструмента.
Портами называют натуральные числа, которые записываются в заголовках протоколов передачи данных (TCP, UDP и так далее). Они определяют процесс получения и передачи информации в рамках одного хоста и в большинстве случаев используются онлайн-программами для установки соединения. Просмотр открытых портов может понадобиться в случае определения работоспособности приложений или при стандартном мониторинге сети. Лучше всего с этим справится команда netstat, а ее активация доступна с применением разных аргументов.
Отображение всех подключений и ожидающих портов
Самый простой аргумент, применяемый к утилите netstat, имеет обозначение -a, и отвечает за вывод сведений обо всех активных подключениях их портов, которые ожидают соединения. Такая информация доступна к просмотру без применения прав администратора и выводится на экран следующим образом:
- Поскольку рассматриваемая команда является консольной, потребуется запустить приложение, чтобы ее выполнить. Откройте меню «Пуск», найдите там «Командную строку» и запустите ее. О других методах перехода в консоль читайте в другом нашем материале по следующей ссылке.
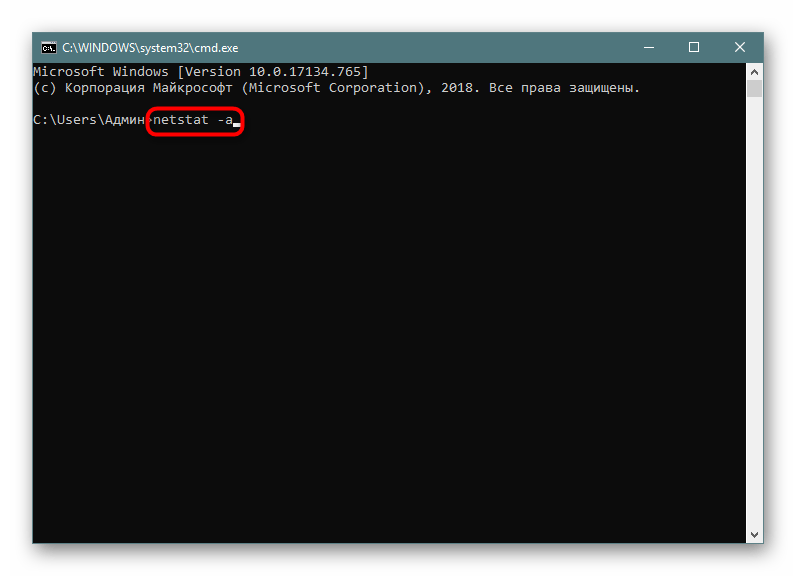
- В поле ввода напечатайте
netstat -a, а затем нажмите на клавишу Enter. - На экране тут же начнет появляться список с доступными адресами.
Подробнее: Открытие командной строки в Windows 10
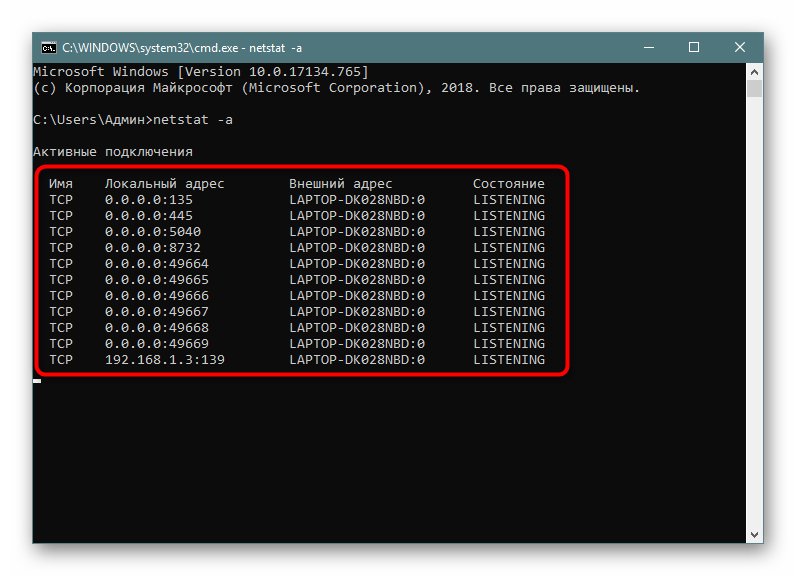
Мониторинг производится в режиме реального времени, поэтому не все результаты будут доступны к просмотру сразу. Придется подождать немного времени, чтобы все они могли прогрузиться. Во время этого не закрывайте консоль, если не хотите прервать процесс, ведь при повторном запуске команды все начнется заново.
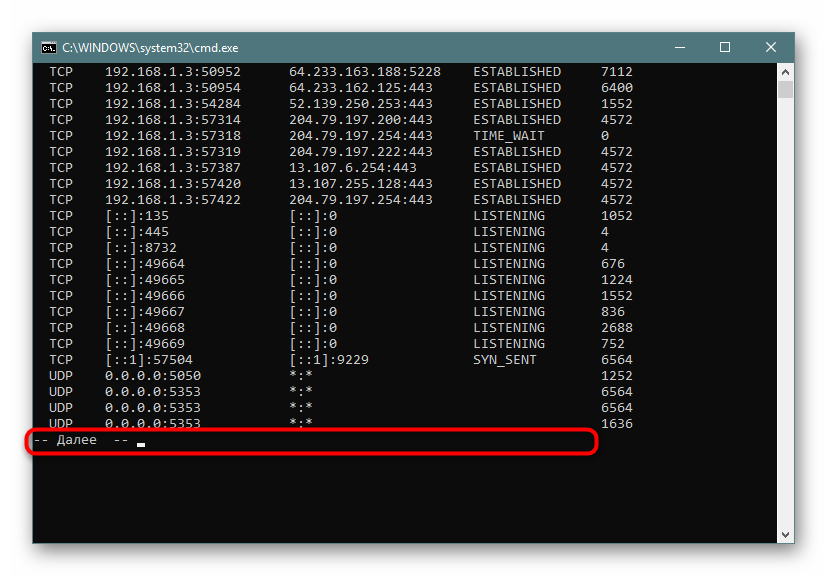
Постраничное отображение открытых портов
К сожалению, приведенный выше вариант отображает не все необходимые данные об открытых портах, поскольку выводит он только те параметры, которые на текущий момент находятся в состоянии LISTENING. К тому же там не указывались уникальные идентификаторы процессов (PID), что тоже играет важную роль во время определенного мониторинга. Потому советуем обратить внимание немного на другие аргументы.
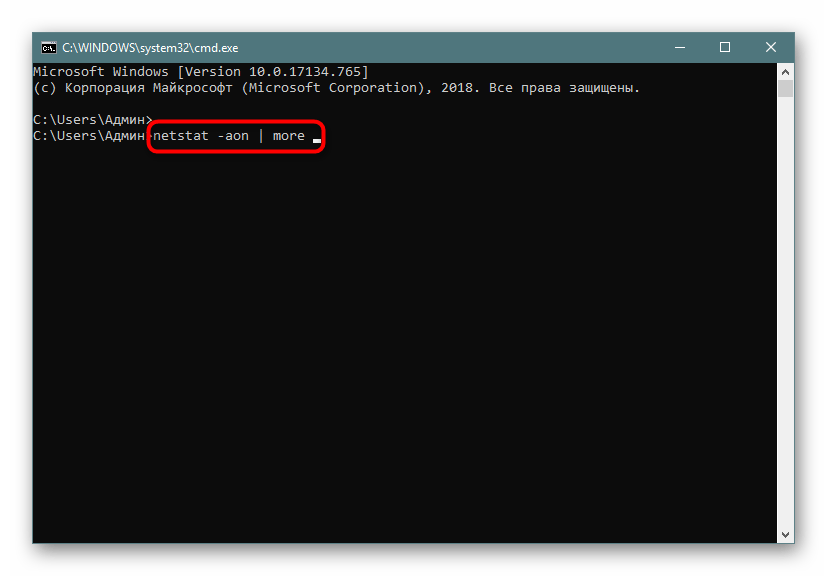
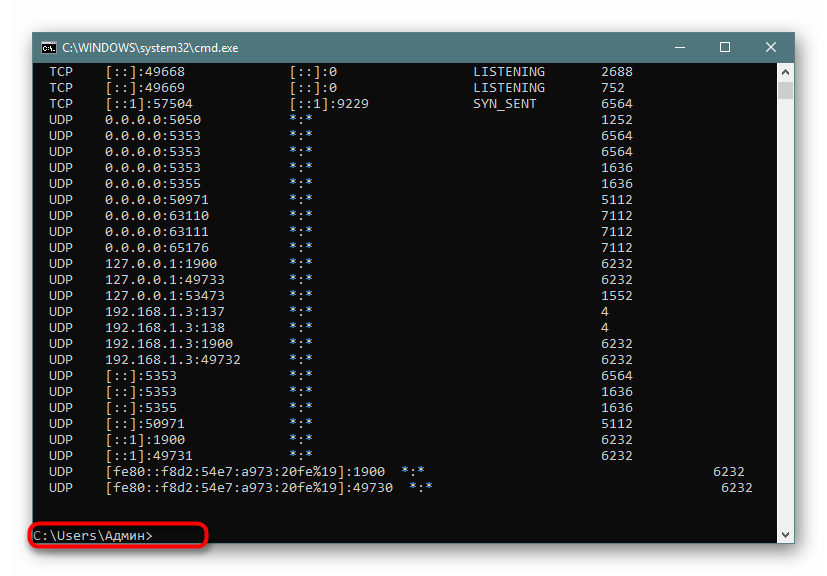
- В консоли пропишите
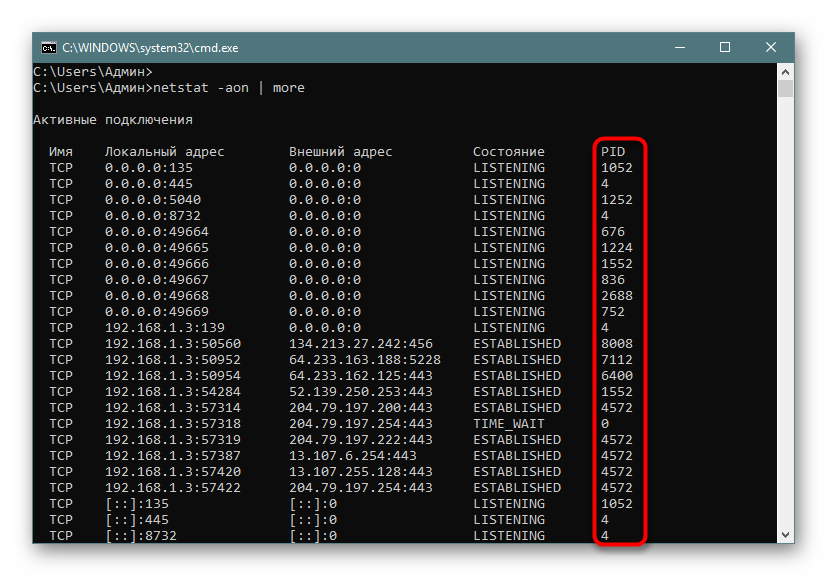
netstat -aon | moreи нажмите на Enter. - Здесь сразу же появится вся важная информация о портах, которые находятся в разных состояниях. В пятой колонке обозначаются идентификаторы.
- Не все порты выводятся сразу, поэтому нужно жать на Enter, чтобы каждый раз отображать еще по одной строке.
- Если вы увидите поле ввода, значит все страницы были успешно выведены на экран.
Теперь хотелось бы поговорить про используемые аргументы и значение увиденных параметров. Давайте сначала затронем знакомые буквы синтаксиса:
| Аргумент | Описание |
|---|---|
| -a | Отображает сведения обо всех подключениях |
| -o | Отвечает за включение колонки с идентификатором каждого адреса |
| -n | Переводит адреса портов и их номера в числовой формат |
| more | Постраничный вывод элементов |
Важно также уточнить и состояние портов, поскольку они могут являться открытыми, но на этот момент не использоваться или ожидать своего подключения. В колонке «Состояние» могут отображаться такие показатели:
| Показатель | Описание |
|---|---|
| CLOSE_WAIT | Подключение ожидает своего закрытия |
| CLOSED | Подключение было успешно закрыто |
| ESTABLISHED | Активная работа соединения |
| LISTENING | Ожидается соединение или еще говорят: «Слушается порт» |
| TIME_WAIT | Время ответа было превышено |
Эти объяснения должны разобраться помочь не только с составлением запросов для netstat, но и без проблем разобраться с полученной информацией.
Запись результатов в текстовый файл
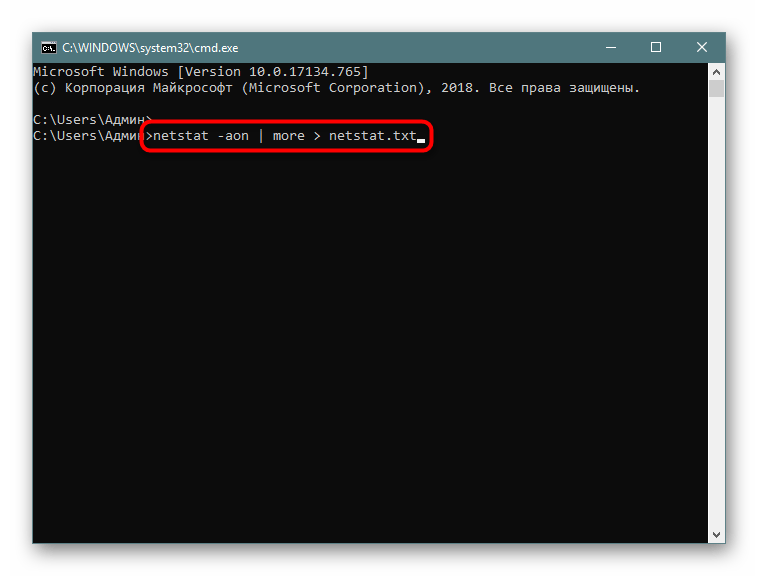
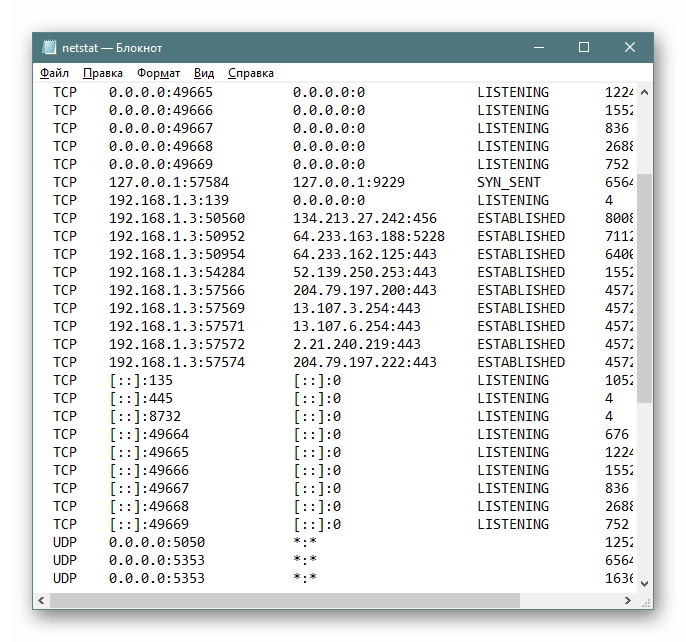
Иногда требуется сохранить готовые результаты мониторинга в текстовый файл, чтобы выполнить дальнейшие действия, ведь копировать информацию прямо из консоли не всегда удобно, да и займет это намного больше времени, нежели просто указать дополнительный аргумент при вводе команды.
- Напишите, например,
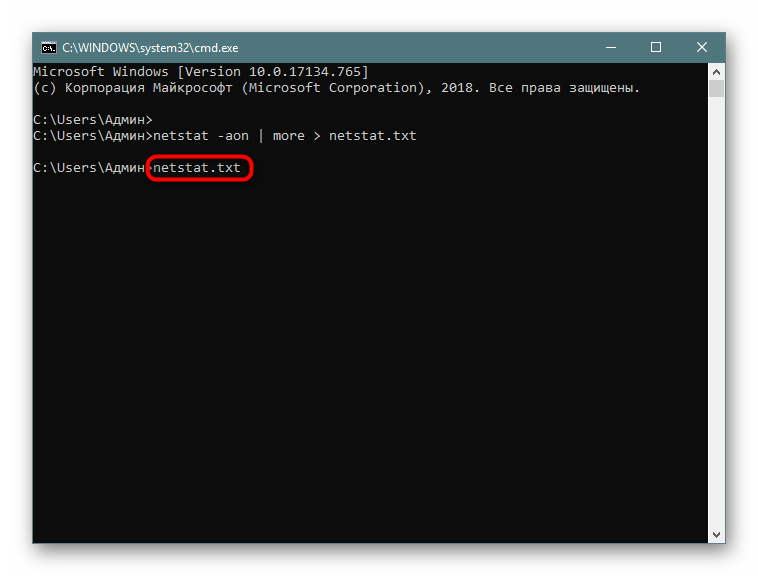
netstat -aon | moreилиnetstat - a, а затем добавьте> netstat.txt, что означает запись результатов в указанный файл (он будет создан в пользовательской папке). После ввода нажмите на Enter. - Запустите файл, введя его название и формат в консоли.
- Теперь вы можете управлять содержимым и сохранить его в любом другом удобном месте.
Поиск по содержимому
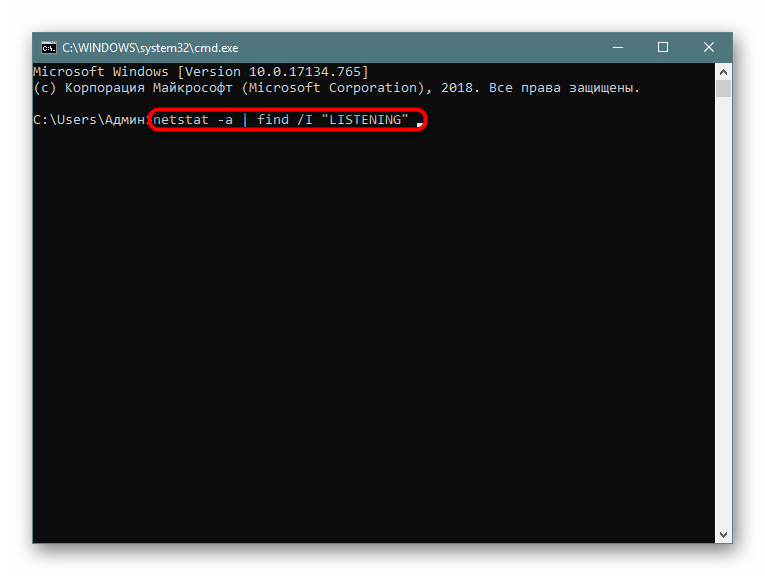
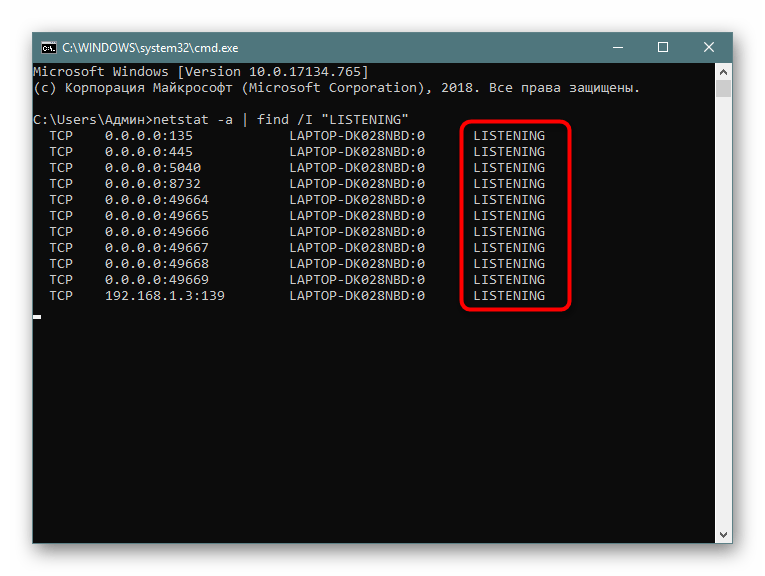
В случае необходимости отображения только подключений с определенными параметрами или адресами лучше всего использовать дополнительную команду find, которая перед выводом сведений произведет фильтрацию данных, и это освободит вас от надобности вручную искать каждый соответствующий пункт. Тогда полная консольная команда приобретает следующий вид:
- Введите
netstat -a | find /I "LISTENING", что задаст параметр отображения только портов с состоянием LISTENING, аргумент /I при этом используется для отмены учета регистра символов. - В результатах отобразится только подходящая информация.
Выше вы узнали о методах определения открытых портов через встроенную команду netstat. После этого можете приступить к работе с программами или пробросу других портов в случае необходимости. К слову, этой теме посвящен отдельный материал на нашем сайте. Перейдите по указанным ниже ссылкам, чтобы ознакомиться с подробными инструкциями.
Читайте также:
Открываем порты на роутере
Открываем порты в брандмауэре Windows 10
Команда netstat всегда показывает правильные результаты, однако если хотите убедиться в открытости порта другим путем, рекомендуем задействовать специальные онлайн-сервисы, позволяющие справиться с поставленной задачей.
Читайте также: Сканирование портов онлайн