To obtain updates from this website, scripting must be enabled.
To use this site to find and download updates, you need to change your security settings to allow ActiveX controls and active scripting. To get updates but allow your security settings to continue blocking potentially harmful ActiveX controls and scripting from other sites, make this site a trusted website:
In Internet Explorer, click Tools, and then click Internet Options.
On the Security tab, click the Trusted Sites icon.
Click Sites and then add these website addresses one at a time to the list:
You can only add one address at a time and you must click Add after each one:
http://*.update.microsoft.com
https://*.update.microsoft.com
http://download.windowsupdate.com
Note:
You might have to uncheck the Require server verification (https:) for all sites in the zone option to enter all the addresses.
The cumulative security update for Windows Server 2016 and Windows Server 2016 Server Core Installation has been released on 12th April 2022. KB5011296 security update supersedes the previous month’s security update KB5011495. If you have not patched the Windows Server 2016 or Windows Server 2016 (Server Core Installation), please follow the instructions given in the document for KB5011495. Over here, we will look at the key aspects of the KB5012596 cumulative security update. We will also list the vulnerabilities that affect Windows Server 2016 and Windows Server 2016 (Server Core Installation).
Salient points about KB5012596 for Windows Server 2016 and Windows Server 2016 (Server Core Installation)
- KB5012596 supersedes KB5011495 for Windows Server 2016 and Windows Server 2016 Server Core Installation.
- KB5011570 SSU needs to be installed prior to patching Windows Server 2016 with KB5012596.
- Two zero-day vulnerabilities affect Windows Server 2016 and Windows Server 2016 Server Core. Both are patched as part of KB5012596. The zero-day threats are CVE-2022-26904 and CVE-2022-24521.
- Over and above the zero-day threats, we found 12 other threats of critical or high significance for Windows Server 2016. Details are shared below. Some of these have a CVSS score of 9.8.
- The server requires a reboot after the deployment of KB5012596.
- The update file for KB5012596 is 1544.6 MB in size. Please plan a change ticket as the update process may not be as brisk as you want it to be.
- KB5012596 resolves the issue with resetting passwords on the Windows Server 2016 after the passwords have expired.
- If you did not install KB5011495, KB5012596 can be deployed straight away.
KB5013952 is the cumulative update for Windows Server 2016 for the month of May 2022. You can read more about the May month’s KB5013952 cumulative update for Windows Server 2016 on this page.
Topics covered in this post
Zero-Day Vulnerabilities on Windows Server 2016
There are two zero-day vulnerabilities that affect Windows Server 2016 and Windows Server 2016 (Server Core Installation). Both are patched as part of the KB5012596 security update released on 12th April. We list the vulnerabilities with a brief description below:
CVE-2022-26904 – CVSS 7 – Windows User Profile Service
KB5012596 security update contains a fix for the zero-day vulnerability in the User Profile Service on Windows operating system across the server and desktop versions. The vulnerability carries a CVSS score of 7 and has a ‘high impact’ on the associated infrastructure based on the Windows Server or Desktop operating systems. It could be exploited and lead to the elevation of privileges on the Windows Server 2016.
Since this vulnerability is publicly known and is more likely to be exploited, we suggest deploying the KB5012596 security updates for April Patch Tuesday on a priority basis.
CVE-2022-24521 – CVSS 7.8 – Windows Log File System Driver
This is the second zero-day vulnerability disclosed by Microsoft on 12th April. It affects the Windows Log File System Driver and can lead to ‘Elevation of Privileges’. It has not been publicly shared earlier. However, the vulnerability has been found to be under active exploitation attempts. It carries a CVSS score of 7.8, leading to a high-level impact on the target Windows Server 2016. KB5012596 resolves the security threat on Windows Server 2016 and Windows Server 2016 (Server Core).
Other Vulnerabilities on Windows Server 2016 – KB5012596
We list the vulnerabilities that carry significant risks for the infrastructure compirsing of Windows Server 2016. All these vulnerabilities are more likely to be exploited on Windows Server 2016 or Windows Server 2016 Server Core installation.
- CVE-2022-24474 – Windows Win32k Elevation of Privilege Vulnerability – This vulnerability exists in the Win32K module and can cause ‘Elevation of Privileges’ on the target Windows 2016 server. It has a CVSS score of 7.8 and a high impact on the associated infrastructure.
- CVE-2022-24481 – Windows Common Log File System Driver Elevation of Privilege Vulnerability – This vulnerability exists in the Windows Common Log File System Driver and could lead to ‘elevation of privileges’. The CVSS score is 7.8.
- CVE-2022-24491 – Windows Network File System Remote Code Execution Vulnerability – This is a Remote Code Execution vulnerability on the Windows Network File System. It has a critical severity with a CVSS score of 9.8.
- CVE-2022-26809 – Remote Procedure Call Runtime Remote Code Execution Vulnerability – This is a critical Remote Code Execution vulnerability with a CVSS score of 9.8. You can mitigate this vulnerability from external traffic by blocking TCP port 445 on the firewall. For the internal traffic, you will need to take steps to secure the SMB traffic.
- CVE-2022-26904 – Windows User Profile Service Elevation of Privilege Vulnerability – This is the zero-day vulnerability that has already been discussed above.
- CVE-2022-24542 – Windows Win32k Elevation of Privilege Vulnerability – This vulnerability affects the Win32K module and could lead to ‘Elevation of Privileges’. It has a CVSS score of 7.8.
- CVE-2022-24547 – Windows Digital Media Receiver Elevation of Privilege Vulnerability – This is an Elevation of Privilege vulnerability with a CVSS score of 7.8. It affects the Windows Digital Media Receiver on specific versions of Windows operating systems.
The zero-day vulnerability CVE-2022-26904 is also more likely to be exploited. However, no exploitation attempt has been detected by Microsoft as yet.
RCE Vulnerabilities Windows Server 2016 – KB5012596
Over and above the vulnerabilities that we have shared above, there are a few more security threats that you need to be aware of. All these vulnerabilities can lead to ‘Remote Code Execution.
These RCE vulnerabilities have critical severity or high-level impact on your infrastructure. The vulnerabilities of interest are mentioned below for a quick summary and action points:
- CVE-2022-24497 – CVSS 9.8 – RCE on Windows Network File System.
- CVE-2022-24541 – CVSS 8.8 – RCE on Windows Server Service.
- CVE-2022-24500 – CVSS 8.8 – RCE on Windows SMB.
- CVE-2022-26919 – CVSS 8.1 – RCE on Windows LDAP.
- CVE-2022-22008 – CVSS 7.7 – RCE on Hyper-V.
- CVE-2022-24537 – CVSS 7.7 – RCE on Hyper-V.
Servicing Stack Update KB5011570 will need to be deployed prior to installing the KB5012596 security update for Windows Server 2016. If you will use the Windows Update for automatic patching, KB5011570 will be deployed automatically before KB5012596 is deployed. If you will patch the Windows Server 2016 manually, please download the SSU KB5011570 from this page to patch it before deploying KB5012596. The SSU update is a small file of 11.6 MB.
How to get KB5012596 for Windows Server 2016?
All regular methods to update Windows Server 2016 are available for installing the KB5012596. Windows Server 2016 can be patched in any of the following methods.
- Windows Update can be used to automatically deploy KB5012596. SSU KB5011570 will be deployed automatically.
- Windows Update for Business can deploy KB5012596 and the SSU KB5011570 automatically.
- WSUS can be used for automatic patching of Windows Server 2016. Both, KB5011570 and KB5012596 will be installed automatically.
- You can choose to manually install the KB5012596 cumulative security update. The file is a little over 1.5 GB in size and downloaded from this KB5012596 page.
KB5012596 – Other Issues resolved in security update
- KB5012596 also resolves CVE-2022-26784, a Denial of Service vulnerability on the Cluster Shared Volumes (CSV). This is a CVSS 6.5 vulnerability.
- .NET framework issues with Active Directory Trust information developed post-deployment of January updates. The .NET framework on Windows Server 2016 and the Windows Server 2016 Server Core need to be upgraded with the corresponding .NET patches.
- .NET Framework 4.6.2, 4.7, 4.7.1 or 4.7.2 should be patched with KB5011329. File size is 371 KB.
- .NET Framework 4.8 should be patched with KB5011264. File size is 358 KB.
- There have been reports of the Recovery Discs not working after deployment of January security updates. The recovery discs created through the Backup and Restore program do not load on the affected servers. This issue remains unresolved for now.
- The KB5012596 security update also resolved the issue with password reset problems. KB5012596 addresses an issue that prevents you from changing a password that has expired when you sign in to a Windows device.
Summary
KB5012596 supersedes KB5011495 security update and resolves zero-day vulnerabilities. It also resolves issues with password reset on the servers after deploying the January updates. SSU KB5011570 will need to be installed before deployin KB5012596. We also suggest patching the .NET Framework with the corresponding .NET patches for Windows Server 2016.
You may also like to read the following content related to Windows Updates:
- Zero-day vulnerability in Microsoft April Updates
- KB5011495 for Windows Server 2016 – March Security Update
Rajesh Dhawan is a technology professional who loves to blog about smart wearables, Cloud computing and Microsoft technologies. He loves to break complex problems into manageable chunks of meaningful information.
Critical Plugin ID: 159677
This page contains detailed information about the KB5012596: Windows 10 version 1607 / Windows Server 2016 Security Update (April 2022) Nessus plugin including available exploits and PoCs found on GitHub, in Metasploit or Exploit-DB for verifying of this vulnerability.
- Plugin Overview
- Vulnerability Information
- Synopsis
- Description
- Solution
- Public Exploits
- Risk Information
- Plugin Source
- How to Run
- References
- Version
Plugin Overview
ID: 159677
Name: KB5012596: Windows 10 version 1607 / Windows Server 2016 Security Update (April 2022)
Filename: smb_nt_ms22_apr_5012596.nasl
Vulnerability Published: 2022-04-12
This Plugin Published: 2022-04-12
Last Modification Time: 2022-04-26
Plugin Version: 1.6
Plugin Type: local
Plugin Family: Windows : Microsoft Bulletins
Dependencies:
ms_bulletin_checks_possible.nasl, smb_check_rollup.nasl, smb_hotfixes.nasl
Required KB Items [?]: SMB/MS_Bulletin_Checks/Possible
Vulnerability Information
Severity: Critical
Vulnerability Published: 2022-04-12
Patch Published: 2022-04-12
CVE [?]: CVE-2022-21983, CVE-2022-22008, CVE-2022-24474, CVE-2022-24479, CVE-2022-24481, CVE-2022-24482, CVE-2022-24483, CVE-2022-24484, CVE-2022-24485, CVE-2022-24486, CVE-2022-24487, CVE-2022-24489, CVE-2022-24490, CVE-2022-24491, CVE-2022-24492, CVE-2022-24493, CVE-2022-24494, CVE-2022-24495, CVE-2022-24496, CVE-2022-24497, CVE-2022-24498, CVE-2022-24499, CVE-2022-24500, CVE-2022-24521, CVE-2022-24527, CVE-2022-24528, CVE-2022-24530, CVE-2022-24533, CVE-2022-24534, CVE-2022-24536, CVE-2022-24537, CVE-2022-24538, CVE-2022-24539, CVE-2022-24540, CVE-2022-24541, CVE-2022-24542, CVE-2022-24544, CVE-2022-24545, CVE-2022-24547, CVE-2022-24549, CVE-2022-24550, CVE-2022-26783, CVE-2022-26784, CVE-2022-26785, CVE-2022-26786, CVE-2022-26787, CVE-2022-26788, CVE-2022-26790, CVE-2022-26792, CVE-2022-26794, CVE-2022-26796, CVE-2022-26797, CVE-2022-26798, CVE-2022-26801, CVE-2022-26802, CVE-2022-26803, CVE-2022-26807, CVE-2022-26808, CVE-2022-26809, CVE-2022-26810, CVE-2022-26811, CVE-2022-26812, CVE-2022-26813, CVE-2022-26814, CVE-2022-26815, CVE-2022-26816, CVE-2022-26817, CVE-2022-26818, CVE-2022-26819, CVE-2022-26820, CVE-2022-26821, CVE-2022-26822, CVE-2022-26823, CVE-2022-26824, CVE-2022-26825, CVE-2022-26826, CVE-2022-26827, CVE-2022-26829, CVE-2022-26831, CVE-2022-26903, CVE-2022-26904, CVE-2022-26915, CVE-2022-26916, CVE-2022-26917, CVE-2022-26918, CVE-2022-26919
CPE [?]: cpe:/o:microsoft:windows
Synopsis
The remote Windows host is affected by multiple vulnerabilities.
Description
The remote Windows host is missing security update 5012591.
It is, therefore, affected by multiple vulnerabilities:
— An elevation of privilege vulnerability. An attacker can exploit this to gain elevated privileges.
(CVE-2022-26827, CVE-2022-24549, CVE-2022-26810, CVE-2022-26803, CVE-2022-26808, CVE-2022-26807, CVE-2022-26792, CVE-2022-26801, CVE-2022-26802, CVE-2022-26794, CVE-2022-26790, CVE-2022-26797, CVE-2022-26787, CVE-2022-26798, CVE-2022-26796, CVE-2022-26786, CVE-2022-26904, CVE-2022-26788, CVE-2022-24496, CVE-2022-24544, CVE-2022-24540, CVE-2022-24489, CVE-2022-24486, CVE-2022-24481, CVE-2022-24479, CVE-2022-24527, CVE-2022-24474, CVE-2022-24521, CVE-2022-24547, CVE-2022-24550, CVE-2022-24499, CVE-2022-24494, CVE-2022-24542, CVE-2022-24530)
— A denial of service (DoS) vulnerability. An attacker can exploit this issue to cause the affected component to deny system or application services. (CVE-2022-26831, CVE-2022-26915, CVE-2022-24538, CVE-2022-24484, CVE-2022-26784)
— A remote code execution vulnerability. An attacker can exploit this to bypass authentication and execute unauthorized arbitrary commands. (CVE-2022-26823, CVE-2022-26812, CVE-2022-26919, CVE-2022-26811, CVE-2022-26809, CVE-2022-26918, CVE-2022-26917, CVE-2022-26813, CVE-2022-26826, CVE-2022-26824, CVE-2022-26815, CVE-2022-26814, CVE-2022-26916, CVE-2022-26822, CVE-2022-26829, CVE-2022-26820, CVE-2022-26819, CVE-2022-26818, CVE-2022-26825, CVE-2022-26817, CVE-2022-26821, CVE-2022-24545, CVE-2022-24541, CVE-2022-24492, CVE-2022-24491, CVE-2022-24537, CVE-2022-24536, CVE-2022-24487, CVE-2022-24534, CVE-2022-24485, CVE-2022-24533, CVE-2022-26903, CVE-2022-24495, CVE-2022-24528, CVE-2022-21983, CVE-2022-22008, CVE-2022-24500)
— An information disclosure vulnerability. An attacker can exploit this to disclose potentially sensitive information. (CVE-2022-26816, CVE-2022-24493, CVE-2022-24539, CVE-2022-24490, CVE-2022-26783, CVE-2022-26785, CVE-2022-24498, CVE-2022-24483)
Solution
Apply Cumulative Update 5012596
Public Exploits
Target Network Port(s): 139, 445
Target Asset(s): Host/patch_management_checks
Exploit Available: True (Metasploit Framework, GitHub)
Exploit Ease: Exploits are available
Here’s the list of publicly known exploits and PoCs for verifying the KB5012596: Windows 10 version 1607 / Windows Server 2016 Security Update (April 2022) vulnerability:
- Metasploit: exploit/windows/local/cve_2022_26904_superprofile
[User Profile Arbitrary Junction Creation Local Privilege Elevation] - GitHub: https://github.com/waleedassar/CVE-2022-24483
[CVE-2022-24483: POC For CVE-2022-24483] - GitHub: https://github.com/corelight/CVE-2022-24491
[CVE-2022-24491: A Zeek CVE-2022-24491 detector.] - GitHub: https://github.com/corelight/CVE-2022-24497
[CVE-2022-24497: A Zeek detector for CVE-2022-24497.] - GitHub: https://github.com/BugHunter010/CVE-2022-26809
[CVE-2022-26809: CVE-2022-26809 exploit] - GitHub: https://github.com/CberryAIRDROP/CVE-2022-26809-RCE
[CVE-2022-26809] - GitHub: https://github.com/DESC0N0C1D0/CVE-2022-26809-RCE
[CVE-2022-26809: This repository contains a PoC for remote code execution CVE-2022-26809] - GitHub: https://github.com/F1uk369/CVE-2022-26809
[CVE-2022-26809: A proof of concept of the CVE-2022-26809-RCE vulnerability.] - GitHub: https://github.com/HellKnightsCrew/CVE-2022-26809
[CVE-2022-26809: vuln scaner and exploit] - GitHub: https://github.com/SeptS0/CVE-2022-26809-RCE
[CVE-2022-26809] - GitHub: https://github.com/SeptS9119/CVE-2022-26809
[CVE-2022-26809: CVE-2022-26809-RCE-EXP-POC] - GitHub: https://github.com/SeptS9119/CVE-2022-26809-RCE
[CVE-2022-26809: CVE-2022-26809-RCE-EXP] - GitHub: https://github.com/XHSecurity/CVE-2022-26809
[CVE-2022-26809] - GitHub: https://github.com/XmasSnow1/cve-2022-26809
[CVE-2022-26809: cve-2022-26809 Remote Code Execution Exploit in the RPC Library] - GitHub: https://github.com/XmasSnowREAL/CVE-2022-26809-RCE
[CVE-2022-26809: CVE-2022-26809 is a vulnerability in Remote Procedure Call Runtime] - GitHub: https://github.com/XmasSnow-is-scammer/CVE-2022-26809
[CVE-2022-26809: XmasSnow-is-scammer] - GitHub: https://github.com/XmasSnow/CVE-2022-26809-RCE
[CVE-2022-26809] - GitHub: https://github.com/ZyxelTeam/CVE-2022-26809-RCE
[CVE-2022-26809: This repository contains a PoC for remote code execution CVE-2022-26809] - GitHub: https://github.com/auduongxuan/CVE-2022-26809
[CVE-2022-26809] - GitHub: https://github.com/f8al/CVE-2022-26809
[CVE-2022-26809: CVE-2022-26809 PoC] - GitHub: https://github.com/genieyou/CVE-2022-26809-RCE
[CVE-2022-26809: CVE-2022-26809-RCE-EXP] - GitHub: https://github.com/gitcomit/scemer2
[CVE-2022-26809: CVE-2022-26809-RCE-EXP] - GitHub: https://github.com/hemazoher/CVE-2022-26809-RCE
[CVE-2022-26809] - GitHub: https://github.com/killvxk/CVE-2022-26809
[CVE-2022-26809: not an exploit or a poc] - GitHub: https://github.com/mr-r3b00t/cve-2022-26809
[CVE-2022-26809] - GitHub: https://github.com/nanaao/CVE-2022-26809
[CVE-2022-26809: A proof of concept of the CVE-2022-26809-RCE vulnerability.] - GitHub: https://github.com/oppongjohn/CVE-2022-26809-RCE
[CVE-2022-26809: CVE-2022-26809-RCE] - GitHub: https://github.com/roger109/CVE-2022-26809-RCE-POC
[CVE-2022-26809] - GitHub: https://github.com/sherlocksecurity/Microsoft-CVE-2022-26809
[CVE-2022-26809: The poc for CVE-2022-26809 RCE via RPC will be updated here.] - GitHub: https://github.com/sherlocksecurity/Microsoft-CVE-2022-26809-The-Little-Boy
[CVE-2022-26809: The poc for CVE-2022-26809 RCE via RPC will be updated here.] - GitHub: https://github.com/websecnl/CVE-2022-26809
[CVE-2022-26809: Remote Code Execution Exploit in the RPC Library] - GitHub: https://github.com/yuanLink/CVE-2022-26809
[CVE-2022-26809] - GitHub: https://github.com/crypt0r00t/CVE-2022-26809
[CVE-2022-26809: Final exploit!] - GitHub: https://github.com/jones199023/CVE-2022-26809
[CVE-2022-26809: Python]
Before running any exploit against any system, make sure you are authorized by the owner of the target system(s) to perform such activity. In any other case, this would be considered as an illegal activity.
WARNING: Beware of using unverified exploits from sources such as GitHub or Exploit-DB. These exploits and PoCs could contain malware. For more information, see how to use exploits safely.
Risk Information
CVSS Score Source [?]: CVE-2022-26809
CVSS V2 Vector: AV:N/AC:L/Au:N/C:C/I:C/A:C/E:H/RL:OF/RC:C
| CVSS Base Score: | 10.0 (High) |
| Impact Subscore: | 10.0 |
| Exploitability Subscore: | 10.0 |
| CVSS Temporal Score: | 8.7 (High) |
| CVSS Environmental Score: | NA (None) |
| Modified Impact Subscore: | NA |
| Overall CVSS Score: | 8.7 (High) |
CVSS V3 Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:H/RL:O/RC:C
| CVSS Base Score: | 9.8 (Critical) |
| Impact Subscore: | 5.9 |
| Exploitability Subscore: | 3.9 |
| CVSS Temporal Score: | 9.4 (Critical) |
| CVSS Environmental Score: | NA (None) |
| Modified Impact Subscore: | NA |
| Overall CVSS Score: | 9.4 (Critical) |
STIG Severity [?]: I
STIG Risk Rating: High
Go back to menu.
Plugin Source
This is the smb_nt_ms22_apr_5012596.nasl nessus plugin source code. This script is Copyright (C) 2022 and is owned by Tenable, Inc. or an Affiliate thereof.
#%NASL_MIN_LEVEL 70300
##
# (C) Tenable, Inc.
##
include('deprecated_nasl_level.inc');
include('compat.inc');
if (description)
{
script_id(159677);
script_version("1.6");
script_set_attribute(attribute:"plugin_modification_date", value:"2022/04/26");
script_cve_id(
"CVE-2022-21983",
"CVE-2022-22008",
"CVE-2022-24474",
"CVE-2022-24479",
"CVE-2022-24481",
"CVE-2022-24482",
"CVE-2022-24483",
"CVE-2022-24484",
"CVE-2022-24485",
"CVE-2022-24486",
"CVE-2022-24487",
"CVE-2022-24489",
"CVE-2022-24490",
"CVE-2022-24491",
"CVE-2022-24492",
"CVE-2022-24493",
"CVE-2022-24494",
"CVE-2022-24495",
"CVE-2022-24496",
"CVE-2022-24497",
"CVE-2022-24498",
"CVE-2022-24499",
"CVE-2022-24500",
"CVE-2022-24521",
"CVE-2022-24527",
"CVE-2022-24528",
"CVE-2022-24530",
"CVE-2022-24533",
"CVE-2022-24534",
"CVE-2022-24536",
"CVE-2022-24537",
"CVE-2022-24538",
"CVE-2022-24539",
"CVE-2022-24540",
"CVE-2022-24541",
"CVE-2022-24542",
"CVE-2022-24544",
"CVE-2022-24545",
"CVE-2022-24547",
"CVE-2022-24549",
"CVE-2022-24550",
"CVE-2022-26783",
"CVE-2022-26784",
"CVE-2022-26785",
"CVE-2022-26786",
"CVE-2022-26787",
"CVE-2022-26788",
"CVE-2022-26790",
"CVE-2022-26792",
"CVE-2022-26794",
"CVE-2022-26796",
"CVE-2022-26797",
"CVE-2022-26798",
"CVE-2022-26801",
"CVE-2022-26802",
"CVE-2022-26803",
"CVE-2022-26807",
"CVE-2022-26808",
"CVE-2022-26809",
"CVE-2022-26810",
"CVE-2022-26811",
"CVE-2022-26812",
"CVE-2022-26813",
"CVE-2022-26814",
"CVE-2022-26815",
"CVE-2022-26816",
"CVE-2022-26817",
"CVE-2022-26818",
"CVE-2022-26819",
"CVE-2022-26820",
"CVE-2022-26821",
"CVE-2022-26822",
"CVE-2022-26823",
"CVE-2022-26824",
"CVE-2022-26825",
"CVE-2022-26826",
"CVE-2022-26827",
"CVE-2022-26829",
"CVE-2022-26831",
"CVE-2022-26903",
"CVE-2022-26904",
"CVE-2022-26915",
"CVE-2022-26916",
"CVE-2022-26917",
"CVE-2022-26918",
"CVE-2022-26919"
);
script_xref(name:"MSKB", value:"5012596");
script_xref(name:"MSFT", value:"MS22-5012596");
script_xref(name:"IAVA", value:"2022-A-0147");
script_xref(name:"IAVA", value:"2022-A-0145");
script_xref(name:"CISA-KNOWN-EXPLOITED", value:"2022/05/04");
script_xref(name:"CISA-KNOWN-EXPLOITED", value:"2022/05/16");
script_name(english:"KB5012596: Windows 10 version 1607 / Windows Server 2016 Security Update (April 2022)");
script_set_attribute(attribute:"synopsis", value:
"The remote Windows host is affected by multiple vulnerabilities.");
script_set_attribute(attribute:"description", value:
"The remote Windows host is missing security update 5012591.
It is, therefore, affected by multiple vulnerabilities:
- An elevation of privilege vulnerability. An attacker can
exploit this to gain elevated privileges.
(CVE-2022-26827, CVE-2022-24549, CVE-2022-26810,
CVE-2022-26803, CVE-2022-26808, CVE-2022-26807,
CVE-2022-26792, CVE-2022-26801, CVE-2022-26802,
CVE-2022-26794, CVE-2022-26790, CVE-2022-26797,
CVE-2022-26787, CVE-2022-26798, CVE-2022-26796,
CVE-2022-26786, CVE-2022-26904, CVE-2022-26788,
CVE-2022-24496, CVE-2022-24544, CVE-2022-24540,
CVE-2022-24489, CVE-2022-24486, CVE-2022-24481,
CVE-2022-24479, CVE-2022-24527, CVE-2022-24474,
CVE-2022-24521, CVE-2022-24547, CVE-2022-24550,
CVE-2022-24499, CVE-2022-24494, CVE-2022-24542,
CVE-2022-24530)
- A denial of service (DoS) vulnerability. An attacker can
exploit this issue to cause the affected component to
deny system or application services. (CVE-2022-26831,
CVE-2022-26915, CVE-2022-24538, CVE-2022-24484,
CVE-2022-26784)
- A remote code execution vulnerability. An attacker can
exploit this to bypass authentication and execute
unauthorized arbitrary commands. (CVE-2022-26823,
CVE-2022-26812, CVE-2022-26919, CVE-2022-26811,
CVE-2022-26809, CVE-2022-26918, CVE-2022-26917,
CVE-2022-26813, CVE-2022-26826, CVE-2022-26824,
CVE-2022-26815, CVE-2022-26814, CVE-2022-26916,
CVE-2022-26822, CVE-2022-26829, CVE-2022-26820,
CVE-2022-26819, CVE-2022-26818, CVE-2022-26825,
CVE-2022-26817, CVE-2022-26821, CVE-2022-24545,
CVE-2022-24541, CVE-2022-24492, CVE-2022-24491,
CVE-2022-24537, CVE-2022-24536, CVE-2022-24487,
CVE-2022-24534, CVE-2022-24485, CVE-2022-24533,
CVE-2022-26903, CVE-2022-24495, CVE-2022-24528,
CVE-2022-21983, CVE-2022-22008, CVE-2022-24500)
- An information disclosure vulnerability. An attacker can
exploit this to disclose potentially sensitive
information. (CVE-2022-26816, CVE-2022-24493,
CVE-2022-24539, CVE-2022-24490, CVE-2022-26783,
CVE-2022-26785, CVE-2022-24498, CVE-2022-24483)");
script_set_attribute(attribute:"see_also", value:"https://support.microsoft.com/en-us/help/5012596");
script_set_attribute(attribute:"solution", value:
"Apply Cumulative Update 5012596");
script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C");
script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C");
script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H");
script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C");
script_set_attribute(attribute:"cvss_score_source", value:"CVE-2022-26809");
script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available");
script_set_attribute(attribute:"exploit_available", value:"true");
script_set_attribute(attribute:"metasploit_name", value:'User Profile Arbitrary Junction Creation Local Privilege Elevation');
script_set_attribute(attribute:"exploit_framework_metasploit", value:"true");
script_set_attribute(attribute:"vuln_publication_date", value:"2022/04/12");
script_set_attribute(attribute:"patch_publication_date", value:"2022/04/12");
script_set_attribute(attribute:"plugin_publication_date", value:"2022/04/12");
script_set_attribute(attribute:"plugin_type", value:"local");
script_set_attribute(attribute:"cpe", value:"cpe:/o:microsoft:windows");
script_set_attribute(attribute:"stig_severity", value:"I");
script_end_attributes();
script_category(ACT_GATHER_INFO);
script_family(english:"Windows : Microsoft Bulletins");
script_copyright(english:"This script is Copyright (C) 2022 and is owned by Tenable, Inc. or an Affiliate thereof.");
script_dependencies("smb_check_rollup.nasl", "smb_hotfixes.nasl", "ms_bulletin_checks_possible.nasl");
script_require_keys("SMB/MS_Bulletin_Checks/Possible");
script_require_ports(139, 445, "Host/patch_management_checks");
exit(0);
}
include('smb_func.inc');
include('smb_hotfixes.inc');
include('smb_hotfixes_fcheck.inc');
include('smb_reg_query.inc');
get_kb_item_or_exit('SMB/MS_Bulletin_Checks/Possible');
bulletin = 'MS22-04';
kbs = make_list(
'5012596'
);
if (get_kb_item('Host/patch_management_checks')) hotfix_check_3rd_party(bulletin:bulletin, kbs:kbs, severity:SECURITY_HOLE);
get_kb_item_or_exit('SMB/Registry/Enumerated');
get_kb_item_or_exit('SMB/WindowsVersion', exit_code:1);
if (hotfix_check_sp_range(win10:'0') <= 0) audit(AUDIT_OS_SP_NOT_VULN);
share = hotfix_get_systemdrive(as_share:TRUE, exit_on_fail:TRUE);
if (!is_accessible_share(share:share)) audit(AUDIT_SHARE_FAIL, share);
if (
smb_check_rollup(os:'10',
sp:0,
os_build:'14393',
rollup_date:'04_2022',
bulletin:bulletin,
rollup_kb_list:[5012596])
)
{
replace_kb_item(name:'SMB/Missing/'+bulletin, value:TRUE);
hotfix_security_hole();
hotfix_check_fversion_end();
exit(0);
}
else
{
hotfix_check_fversion_end();
audit(AUDIT_HOST_NOT, hotfix_get_audit_report());
}
The latest version of this script can be found in these locations depending on your platform:
- Linux / Unix:
/opt/nessus/lib/nessus/plugins/smb_nt_ms22_apr_5012596.nasl - Windows:
C:\ProgramData\Tenable\Nessus\nessus\plugins\smb_nt_ms22_apr_5012596.nasl - Mac OS X:
/Library/Nessus/run/lib/nessus/plugins/smb_nt_ms22_apr_5012596.nasl
Go back to menu.
How to Run
Here is how to run the KB5012596: Windows 10 version 1607 / Windows Server 2016 Security Update (April 2022) as a standalone plugin via the Nessus web user interface (https://localhost:8834/):
- Click to start a New Scan.
- Select Advanced Scan.
- Navigate to the Plugins tab.
- On the top right corner click to Disable All plugins.
- On the left side table select Windows : Microsoft Bulletins plugin family.
- On the right side table select KB5012596: Windows 10 version 1607 / Windows Server 2016 Security Update (April 2022) plugin ID 159677.
- Specify the target on the Settings tab and click to Save the scan.
- Run the scan.
Here are a few examples of how to run the plugin in the command line. Note that the examples below demonstrate the usage on the Linux / Unix platform.
Basic usage:
/opt/nessus/bin/nasl smb_nt_ms22_apr_5012596.nasl -t <IP/HOST>Run the plugin with audit trail message on the console:
/opt/nessus/bin/nasl -a smb_nt_ms22_apr_5012596.nasl -t <IP/HOST>Run the plugin with trace script execution written to the console (useful for debugging):
/opt/nessus/bin/nasl -T - smb_nt_ms22_apr_5012596.nasl -t <IP/HOST>Run the plugin with using a state file for the target and updating it (useful for running multiple plugins on the target):
/opt/nessus/bin/nasl -K /tmp/state smb_nt_ms22_apr_5012596.nasl -t <IP/HOST>Go back to menu.
References
MSKB | Microsoft Knowledge Base:
- 5012596
MSFT | Microsoft Security Bulletin:
- MS22-5012596
IAVA | Information Assurance Vulnerability Alert:
- 2022-A-0145, 2022-A-0147
See also:
- https://www.tenable.com/plugins/nessus/159677
- https://support.microsoft.com/en-us/help/5012596
- https://vulners.com/nessus/SMB_NT_MS22_APR_5012596.NASL
Similar and related Nessus plugins:
- 159679 — KB5012591: Windows 10 version 1909 / Windows Server 1909 Security Update (April 2022)
- 159671 — KB5012592: Windows 11 Security Update (April 2022)
- 159685 — KB5012599: Windows 10 Version 2004 / Windows 10 Version 20H2 / Windows 10 Version 21H1 Security Update (April 2022)
- 159681 — KB5012604: Windows Server 2022 Security Update (April 2022)
- 159684 — KB5012632: Windows Server 2008 Security Update (April 2022)
- 159682 — KB5012670: Windows Server 2012 R2 Security Update (April 2022)
- 159675 — KB5012647: Windows 10 version 1809 Security Update (April 2022)
- 159672 — KB5012649: Windows Server 2008 R2 Security Update (April 2022)
- 159680 — KB5012653: Windows 10 version 1507 LTS Security Update (April 2022)
- 159676 — KB5012666: Windows Server 2012 Security Update (April 2022)
- 159887 — Security Update for Visual Studio 2019 (April 2022) (macOS)
- 159975 — Oracle Java SE Multiple Vulnerabilities (April 2022 CPU)
- 159974 — Oracle Java SE Multiple Vulnerabilities (Unix April 2022 CPU)
- 160204 — Oracle JDeveloper Multiple Vulnerabilities (April 2022 CPU)
Version
This page has been produced using Nessus Professional 10.1.2 (#68) LINUX, Plugin set 202205072148.
Plugin file smb_nt_ms22_apr_5012596.nasl version 1.6. For more plugins, visit the Nessus Plugin Library.
Go back to menu.
Microsoft выпускает новые обновления безопасности для своих продуктов как минимум один раз в месяц. В большинстве случаев служба Windows Update прекрасно справляется с автоматическим получением и установкой обновлений Windows. Также вы можете вручную найти, скачать и установить актуальное кумулятивное обновление безопасности для вашей редакции и версии Windows. Например, на компьютерах с отключенной службой wususerv, в изолированных от интернета сетях (если у вас не используется WSUS сервер, где можно вручную управлять тестированием и одобрением обновлений Windows), в локальной сети с лимитным подключением (metered connection) и т.д.
Содержание:
- Узнать дату установки последних обновлений Windows
- Как найти и скачать последние обновления безопасности для вашей версии Windows?
- Ручная установка кумулятивных обновлений в Windows
- Ручное обновление билда Windows 10 (Feature Update)
Каждый второй вторник месяца Microsoft выпускает новые обновления для всех поддерживаемых редакций Windows (исправления для особо критичных уязвимостей могут выпускаться быстрее, не дожидаясь этой даты. Также имейте в виду, что в Windows используется кумулятивная модель обновлений. Это означает, что для обновления Windows достаточно установить только один, последний, кумулятивный пакет безопасности.
Узнать дату установки последних обновлений Windows
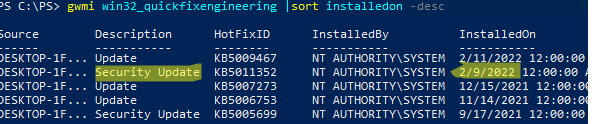
Проверьте дату установки последних обновлений на вашем компьютере с помощью PowerShell команды:
gwmi win32_quickfixengineering |sort installedon -desc
Source Description HotFixID InstalledBy InstalledOn PCname1 Security Update KB5011352 NT AUTHORITY\SYSTEM 2/9/2022 12:00:00 AMН
В данном случае видно, что последний раз на этом компьютере обновление безопасности устанавливалось 9 февраля 2022 года.
Так же вы можете вывести историю установки обновлений с помощью командлета
Get-WUHistory
из модуля PSWindowsUpdate:
Get-WUHistory|Where-Object {$_.Title -match "KB*"} |Sort-Object date -desc
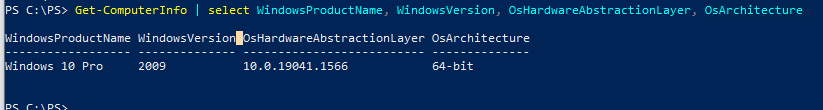
Затем вам нужно узнать версию и номер билда вашей Windows. Воспользуйтесь командой:
Get-ComputerInfo | select WindowsProductName, WindowsVersion, OsHardwareAbstractionLayer, OsArchitecture
WindowsProductName WindowsVersion OsHardwareAbstractionLayer, OsArchitecture Windows 10 Pro 2009 10.0.19041.1566 64-bit
В моем случае мне нужно скачать последние обновления безопасности для Windows 10 20H2 x64.
Как найти и скачать последние обновления безопасности для вашей версии Windows?
Вы можете вручную скачать последние обновления для продуктов Microsoft из каталога обновлений Microsoft Update Catalog — https://www.catalog.update.microsoft.com/Home.aspx. В каталоге вы можете найти обновления для всех поддерживаемых версий Windows (также поддерживается прямой импорт обновлений через консоль WSUS). Главная проблема, что в каталоге отсутствует удобная система поиска. Если вы не знаете номер KB, который вам нужно установить, найти и скачать пакет с обновлением довольно трудно.
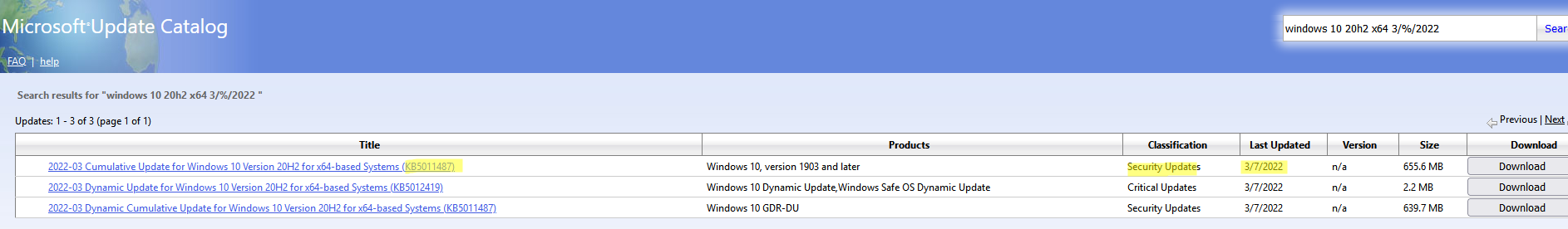
Рассмотрим, как сформировать правильный запрос для поиска обновлений для вашей редакции Windows в каталоге обновлений Microsoft. Статья пишется 9 марта 2022 года, соответственно последние обновления безопасности были выпушены вчера, 8 марта (второй вторник месяца). Для поиска обновлений безопасности для Windows 10 20H2 x64 за март 2022 года, воспользуйтесь таким поисковым запросом, который нужно вставить в поисковую строку в верхнем правом углу:
windows 10 20h2 x64 3/%/2022
Каталог Microsoft Update вернул список из 3 обновлений.
Как решить какие из этих обновлений нужно скачать и установить? Конечно, можно скачать и установить вручную все эти обновления, но можно сэкономить время. Т.к. Microsoft перешла на кумулятивные обновления, вам достаточно скачать и установить последнее Cumulative Update для вашей системы.
В моем случае доступно одно большое кумулятивное обновление для Windows 10:
- 2022-03 Cumulative Update for Windows 10 Version 20H2 for x64-based Systems (KB5011487), Windows 10 version 1903 and later, Security Updates, 3/7/2022 — 655.6 MB
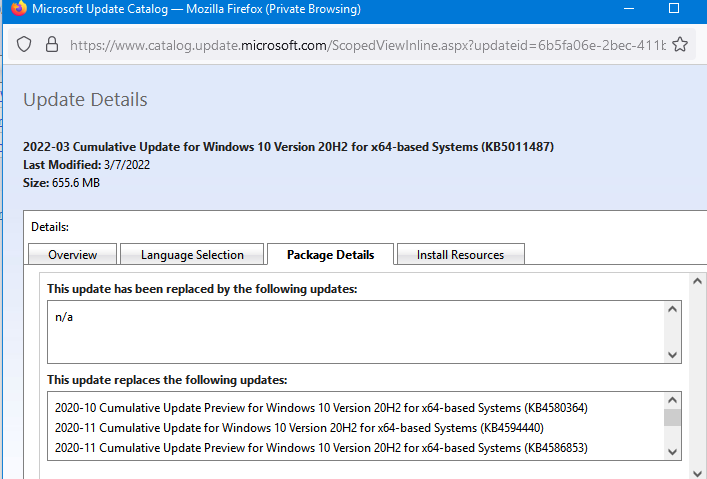
Щелкните по названию обновления безопасности KB5011487. В открывшемся окне с информацией об обновлении перейдите на вкладку Package Details. На этой вкладке видно какие обновления заменяет данное обновление (This update replaces the following updates:), и каким обновлением заменяется в свою очередь оно (This update has been replaced by the following updates).
Как вы это обновление ничем не заменяется: This update has been replaced by the following updates: n/a. Значит это самое последнее и актуальное кумулятивное обновление безопасности для вашей версии Windows 10.
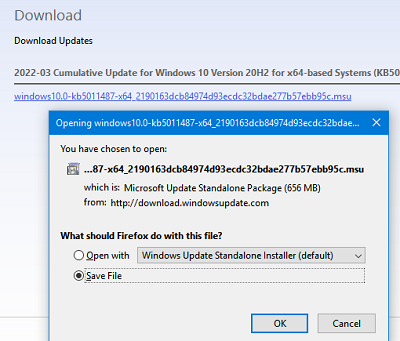
Нажмите на кнопку Download, в открывшемся окне появится прямая ссылка на загрузку MSU файла обновлений. Скачайте файл и сохраните его на диск.
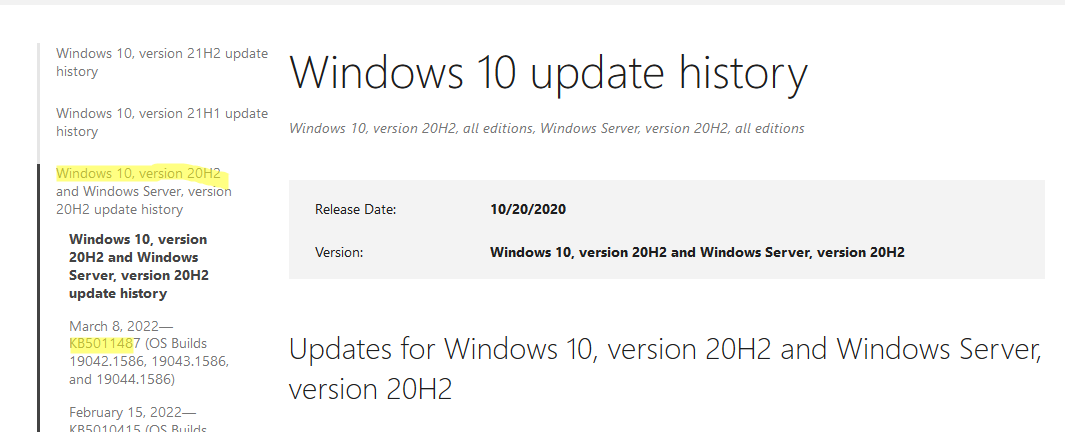
Также вы можете найти номер KB актуального кумулятивного обновления для вашей версии Windows 10 с помощью страницы https://support.microsoft.com/en-us/topic/windows-10-update-history-7dd3071a-3906-fa2c-c342-f7f86728a6e3.
В списке слева выберите вашу версию Windows 10 (в моем примере это Windows 10 20H2), затем обратите внимание на список In this release. Самая первая запись ссылается на статью базы знаний для последнего кумулятивного обновления Windows этой редакции. В нашем примере это March 8, 2022—KB5011487 (OS Builds 19042.1586, 19043.1586, and 19044.1586). Именно это обновление мы и скачали согласно методике выше.
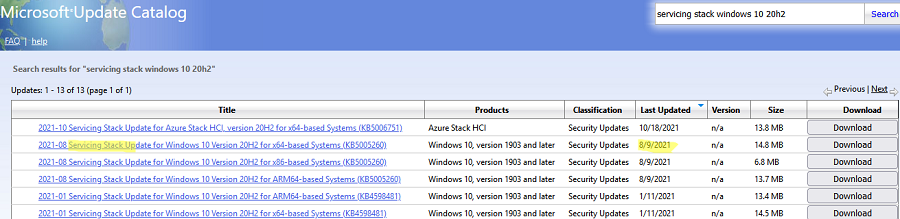
Затем скачайте последнее доступное обновление служебного стека Windows 10 (SSU — Servicing Stack Updates). Это обновление также можно найти в Windows Update Catalog по ключевой фразе:
servicing stack windows 10 20h2
Обязательно установите Servicing Stack Update до установки накопительного обнолвения безопасности Windows.
C марта 2021 года, Microsoft перестала выпускать отдельные обновления SSU для билдов Windows 10 2004 и старше. Теперь они интегрируются в последнее кумулятивное обновление LCU (Latest Cumulative Update).
Скачать файлы обновлений Windows с помощью PowerShell
Для скачивания файлов MSU обновлений из Microsoft Update Catalog можно использовать командлет Save-KBFile из модуля KBUpdate (KB Viewer, Saver, Installer and Uninstaller) — https://github.com/potatoqualitee/kbupdate
Установите модуль из PowerShell Gallery:
Install-Module kbupdate -Scope CurrentUser
Для загрузки определенных файлов обновлений выполните команду PowerShell:
Save-KBFile -Name KB5011487, 5005260 -Architecture x64 -Path C:\Updates
Ручная установка кумулятивных обновлений в Windows
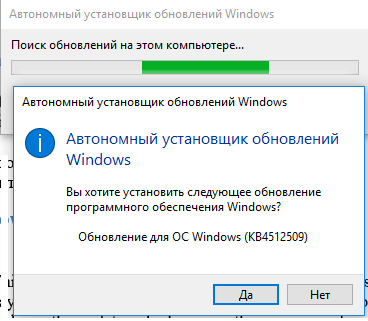
После того, как вы скачали MSU файл с актуальным кумулятивным обновлением для вашей редакции Windows 10, вы можете его установить.
Щелкните дважды по скачанному msu файлу и следуйте шагам мастера автономного установщика обновлений Windwows.
После окончания установки пакета обновлений нужно перезагрузить компьютер (если после установки обновления вы наблюдаете проблемы с работой ОС или приложений, вы можете удалить его).
Также вы можете установить обновление Windows из командной строки в тихом режиме с помощью утилиты wusa.exe (Windows Update Standalone Installer). Следующая команда установит указанное обновление в тихом режиме и отложит автоматическую перезагрузку системы после завершения установки:
wusa C:\updates\windows10.0-kb5011487-x64_2190163dcb84974d93ecdc32bdae277b57ebb95c.msu /quiet /norestart
Ручное обновление сигнатур Windows Defender
Если на вашем устройстве Windows включен встроенный Windows Defender Antivirus, вы можете вручную обновить его сигнатуры. Обновление с новым набором сигнатур можно скачать с Microsoft Update Catalog, либо (проще) со страницы https://www.microsoft.com/en-us/wdsi/defenderupdates#manual.
Скачайте файл офлайн установки для вашей версии Window. Например, Microsoft Defender Antivirus for Windows 10 and Windows 8.1 64-bit.
Запустите и установите файл
fpam-fe.exe
для обновления антивирусных баз.
Ручное обновление билда Windows 10 (Feature Update)
Также вы можете вручную обновить билд Windows 10 (Feature Update). Например, вы хотите вручную обновить билд Windows 10 на своем компьютере с 20H2 (окончание поддержки 10 мая 2022) на 21H2.
Для этого перейдите на страницу https://www.microsoft.com/en-us/software-download/windows10 и нажмите кнопку Update Now.
Скачайте и запустите файл Windows 10 Update Assistant (
Windows10Upgrade9252.exe)
.
Мастер предложит вам обновится до последней версии Windows 10 (Windows 10 November 2021 Update). Для такого обновления требуется подключение к интернету.
Чтобы выполнить оффлайн обновление билда Windows 10, сформируйте установочный ISO образ с новый билдом Windows 10 с помощью Media Citation Tool (позволяет создать iso образ или загрузочную флешку с Windows 10).
Затем смонтируйте ISO образ в виртуальный привод и запустите файл setup.exe. Следуйте шагам мастера обновления Windows. Подробнее это описано в статье про обновление билда Windows 10 из командной строки.
This list contains all of the known Microsoft Knowledge Base articles, howtos, fixes, hotfixes, webcasts and updates of Microsoft Windows Server 2016 starts with letter M that have been released. The list is daily updated.
- 5011495 March 8, 2022—KB5011495 (OS Build 14393.5006) — EXPIRED Q5011495 KB5011495 September 20, 2023
- 5003197 May 11, 2021—KB5003197 (OS Build 14393.4402) — EXPIRED Q5003197 KB5003197 September 20, 2023
- 5000803 March 9, 2021—KB5000803 (OS Build 14393.4283) — EXPIRED Q5000803 KB5000803 September 20, 2023
- 4568292 Microsoft Defender update for Windows operating system installation images Q4568292 KB4568292 August 10, 2023
- 5026363 May 9, 2023—KB5026363 (OS Build 14393.5921) Q5026363 KB5026363 May 9, 2023
- 5004442 Manage changes for Windows DCOM Server Security Feature Bypass (CVE-2021-26414) Q5004442 KB5004442 March 20, 2023
- 5023697 March 14, 2023—KB5023697 (OS Build 14393.5786) Q5023697 KB5023697 March 14, 2023
- 5015019 May 19, 2022—KB5015019 (OS Build 14393.5127) Out-of-band Q5015019 KB5015019 June 3, 2022
- 5013952 May 10, 2022—KB5013952 (OS Build 14393.5125) Q5013952 KB5013952 June 3, 2022
- 4054531 Microsoft .NET Framework 4.7.2 web installer for Windows Q4054531 KB4054531 March 24, 2022
- 4054530 Microsoft .NET Framework 4.7.2 offline installer for Windows Q4054530 KB4054530 March 24, 2022
- 4577252 Managing deployment of RBCD/Protected User changes for CVE-2020-16996 Q4577252 KB4577252 January 22, 2022
- 4599464 Managing deployment of Printer RPC binding changes for CVE-2021-1678 (KB4599464) Q4599464 KB4599464 September 14, 2021
- 5005413 Mitigating NTLM Relay Attacks on Active Directory Certificate Services (AD CS) Q5005413 KB5005413 August 16, 2021
- 4557232 Minimum Password Length auditing and enforcement on certain versions of Windows Q4557232 KB4557232 July 13, 2021
- 3151934 Microsoft .NET Framework 4.6.2 Developer Pack and language packs Q3151934 KB3151934 June 23, 2021
- 5001633 March 18 2021—KB5001633 (OS Build 14393.4288) Out-of-band Q5001633 KB5001633 May 27, 2021
- 4598347 Managing deployment of Kerberos S4U changes for CVE-2020-17049 Q4598347 KB4598347 February 26, 2021
- 4033339 Microsoft .NET Framework 4.7.1 Language Pack (Offline Installer) for Windows Q4033339 KB4033339 January 26, 2021
- 4013076 MS17-011: Security update for Microsoft Uniscribe: March 14, 2017 Q4013076 KB4013076 January 26, 2021
- 3202790 MS16-141: Security update for Adobe Flash Player: November 8, 2016 Q3202790 KB3202790 January 26, 2021
- 3199647 MS16-138: Security update to Microsoft virtual hard drive: November 8, 2016 Q3199647 KB3199647 January 26, 2021
- 3193479 MS16-140: Security update for boot manager: November 8, 2016 Q3193479 KB3193479 January 26, 2021
- 4047409 Mitigation Plan for Active Directory Certificate Services-based scenarios Q4047409 KB4047409 January 25, 2021
- 4025686 Microsoft security advisory 4025685: Guidance for supported platforms: June 13, 2017 Q4025686 KB4025686 January 25, 2021
- 4025685 Microsoft Security Advisory 4025685: Guidance related to June 2016 security update release: June 13, 2017 Q4025685 KB4025685 January 25, 2021
- 4013389 MS17-010: Security update for Windows SMB Server: March 14, 2017 Q4013389 KB4013389 January 25, 2021
- 4013083 MS17-018: Security update for Windows Kernel-Mode Drivers: March 14, 2017 Q4013083 KB4013083 January 25, 2021
- 4013082 MS17-008: Security update for Windows Hyper-V: March 14, 2017 Q4013082 KB4013082 January 25, 2021
- 4013081 MS17-017: Security update for Windows Kernel: March 14, 2017 Q4013081 KB4013081 January 25, 2021
- 4013078 MS17-012: Security update for Microsoft Windows: March 14, 2017 Q4013078 KB4013078 January 25, 2021
- 4013074 MS17-016: Security update for Internet Information Services: March 14, 2017 Q4013074 KB4013074 January 25, 2021
- 4010323 Microsoft security advisory: SHA-1 deprecation for SSL/TLS certificates: May 9, 2017 Q4010323 KB4010323 January 25, 2021
- 4010321 MS17-022: Security update for Microsoft XML Core Services: March 14, 2017 Q4010321 KB4010321 January 25, 2021
- 4010320 MS17-019: Security update for Active Directory Federation Services: March 14, 2017 Q4010320 KB4010320 January 25, 2021
- 4010319 MS17-009: Security update for Microsoft Windows PDF Library: March 14, 2017 Q4010319 KB4010319 January 25, 2021
- 4010318 MS17-021: Security update for Windows DirectShow: March 14, 2017 Q4010318 KB4010318 January 25, 2021
- 3214288 MS17-001: Security update for Microsoft Edge: January 10, 2017 Q3214288 KB3214288 January 25, 2021
- 3207328 MS16-153: Security update for Common Log File System driver: December 13, 2016 Q3207328 KB3207328 January 25, 2021
- 3205651 MS16-151: Security update for Windows kernel-mode drivers: December 13, 2016 Q3205651 KB3205651 January 25, 2021
- 3205642 MS16-150: Security update for secure kernel mode: December 13, 2016 Q3205642 KB3205642 January 25, 2021
- 3204066 MS16-146: Security update for Microsoft graphics component: December 13, 2016 Q3204066 KB3204066 January 25, 2021
- 3204063 MS16-147: Security update for Microsoft Uniscribe: December 13, 2016 Q3204063 KB3204063 January 25, 2021
- 3199709 MS16-152: Security update for Windows kernel: December 13, 2016 Q3199709 KB3199709 January 25, 2021
- 3199173 MS16-137: Security update for Windows authentication methods: November 8, 2016 Q3199173 KB3199173 January 25, 2021
- 3199151 MS16-131: Security update for Microsoft Video Control: November 8, 2016 Q3199151 KB3199151 January 25, 2021
- 3199135 MS16-135: Security update for Windows kernel-mode drivers: November 8, 2016 Q3199135 KB3199135 January 25, 2021
- 3199120 MS16-132: Security update for Microsoft graphics component: November 8, 2016 Q3199120 KB3199120 January 25, 2021
- 3198389 MS16-140: Description of the security update for Windows Server 2016 TP5 boot manager: November 8, 2016 Q3198389 KB3198389 January 25, 2021
- 3193706 MS16-134: Security update for common log file system driver: November 8, 2016 Q3193706 KB3193706 January 25, 2021
- 4073705 Microsoft .NET Framework 4.7.2 Language Pack on Windows 10, version 1709 and Windows Server, version 1709 Q4073705 KB4073705 January 16, 2021
- 4073120 Microsoft .NET Framework 4.7.2 for Windows 10, version 1709 and Windows Server, version 1709 Q4073120 KB4073120 January 16, 2021
- 3202122 Microsoft Distributed Transaction Coordinator (MSDTC) service does not start after you run Sysprep Q3202122 KB3202122 December 18, 2020
- 4556813 May 12, 2020—KB4556813 (OS Build 14393.3686) Q4556813 KB4556813 October 23, 2020
- 4541329 March 17, 2020—KB4541329 (OS Build 14393.3595) Q4541329 KB4541329 October 23, 2020
- 4540670 March 10, 2020—KB4540670 (OS Build 14393.3564) Q4540670 KB4540670 October 23, 2020
- 4520296 MS Mincho and MS PMincho fonts do not show the new Japanese era as expected Q4520296 KB4520296 October 23, 2020
- 4505052 May 19, 2019—KB4505052 (OS Build 14393.2972) Q4505052 KB4505052 October 23, 2020
- 4499177 May 23, 2019—KB4499177 (OS Build 14393.2999) Q4499177 KB4499177 October 23, 2020
- 4494440 May 14, 2019—KB4494440 (OS Build 14393.2969) Q4494440 KB4494440 October 23, 2020
- 4489889 March 19, 2019—KB4489889 (OS Build 14393.2879) Q4489889 KB4489889 October 23, 2020
- 4489882 March 12, 2019—KB4489882 (OS Build 14393.2848) Q4489882 KB4489882 October 23, 2020
- 4103723 May 8, 2018—KB4103723 (OS Build 14393.2248) Q4103723 KB4103723 October 23, 2020
- 4103720 May 17, 2018—KB4103720 (OS Build 14393.2273) Q4103720 KB4103720 October 23, 2020
- 4096309 March 29, 2018—KB4096309 (OS Build 14393.2156) Q4096309 KB4096309 October 23, 2020
- 4088889 March 22, 2018—KB4088889 (OS Build 14393.2155) Q4088889 KB4088889 October 23, 2020
- 4088787 March 13, 2018—KB4088787 (OS Build 14393.2125 and 14393.2126) Q4088787 KB4088787 October 23, 2020
- 4019472 May 9, 2017—KB4019472 (OS Build 14393.1198) Q4019472 KB4019472 October 23, 2020
- 4015438 March 20, 2017—KB4015438 (OS Build 14393.969) Q4015438 KB4015438 October 23, 2020
- 4013429 March 14, 2017—KB4013429 (OS Build 14393.953) Q4013429 KB4013429 October 23, 2020
- 4013075 MS17-013: Security Update for Microsoft Graphics Component: March 14, 2017 Q4013075 KB4013075 October 23, 2020
- 4497410 Microsoft .NET Framework 4.8 Language Pack (Offline Installer) for Windows Q4497410 KB4497410 October 22, 2020
- 4486129 Microsoft .NET Framework 4.8 for Windows 10 version 1607, Windows 10 version 1703 and Windows Server 2016 Q4486129 KB4486129 October 22, 2020
- 4087515 Microsoft .NET Framework 4.8 Language Pack on Windows 10 version 1609, Windows 10 version 1703 and Windows Server 2016 Q4087515 KB4087515 October 22, 2020
- 4054535 Microsoft .NET Framework 4.7.2 Language Pack on Windows 10 Anniversary Update, Windows 10 Creators Update, and Windows Server 2016 Q4054535 KB4054535 October 22, 2020
- 4054529 Microsoft .NET Framework 4.7.2 Language Pack (Offline Installer) for Windows Q4054529 KB4054529 October 22, 2020
- 2510009 Microsoft support policy for 4K sector hard drives in Windows Q2510009 KB2510009 May 31, 2020
- 957006 Microsoft server software and supported virtualization environments Q957006 KB957006 April 13, 2020
- 3201860 MS16-128: Security update for Adobe Flash Player: October 27, 2016 Q3201860 KB3201860 November 16, 2019
- 4032986 Most recent previous versions are missing for a share that has Previous Versions enabled in Windows Q4032986 KB4032986 October 2, 2018
- 3011079 MPIO is not supported for pass-through disks in virtual machines Q3011079 KB3011079 October 2, 2018
- 3120865 Microsoft .NET Framework 4.6.2 Developer Pack and language packs Q3120865 KB3120865 November 30, 2017
- 4043838 MPIO storage is inaccessible after a path failure in Windows Server Q4043838 KB4043838 September 29, 2017