Windows Packet Filter (WinpkFilter) is a high-performance packet filtering framework designed for Windows that enables developers to efficiently filter (inspect and modify) raw network packets at the NDIS level of the network stack with minimal impact on network activity. This is achieved without the need for writing any low-level driver code.
Windows Packet Filter framework includes NDIS 3.1/4 hooking VxD driver for Windows 95/ME, NDIS 4 hooking filter driver for Windows NT/2000/XP, NDIS 5 Intermediate for Windows XP/2003, and NDIS 6 Lightweight Filter (LWF) drivers for Windows Vista and later. Additionally, it comes with a companion user-mode API DLL and sample code.
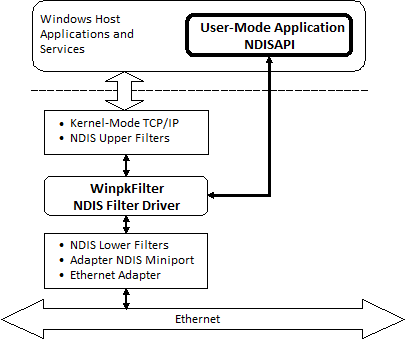
One of the key benefits of using Windows Packet Filter in comparison to other packet filtering frameworks for Windows, such as those based on the Windows Filtering Platform (WFP) callout drivers, Layered Service Providers (LSP), TDI filters, etc., is its ability to manipulate raw Ethernet frames by installing the driver below all network protocol drivers and just above the network interface driver. This gives the WinpkFilter driver ultimate control over all network traffic flow entering and leaving the system, allowing you to modify any packet, drop it, or even forge and insert a new one. With Windows Packet Filter, there’s no need to have experience in kernel-mode programming, as it provides a powerful user-level API. However, if you need to improve performance by implementing your solution in kernel mode, you can do so by directly adding your functional code to the Windows Packet Filter driver’s code.
System Requirements
| Windows 95/98/Millennium | Windows Server 2008* | Windows Server 2012 R2 |
| Windows NT 4.0 | Windows 7 | Windows 10 |
| Windows 2000 | Windows Server 2008 R2 | Windows Server 2016 |
| Windows XP | Windows 8 | Windows Server 2019 |
| Windows Server 2003 | Widows Server 2012 | Windows 11 |
| Windows Vista* | Windows 8.1 | Windows Server 2022 |
The following connections types are supported for the operating systems above:
- Wired Ethernet (802.3)
- Wi-Fi (802.11)
- WAN (Analog/ISDN modems, PPPoE, 3G/4G mobile modems)
- Mobile Broadband (PPIP)
- VPN network interfaces (WinTun, WireGuard etc.)
Product features
- Windows Packet Filter has been confirmed for its reliability and stability by hundreds of satisfied customers, ranging from small shareware companies to well-known corporations, since its launch in 2002.
- It boasts high performance, allowing for seamless handling of Gigabit network bandwidth in user-mode applications without any noticeable degradation in performance.
- It is completely portable across all Windows desktop platforms and operates on RAS/PPP adapters, as well as supporting Windows 7 Mobile Broadband stack (PPIP).
- It offers both passive network listening (packet collection) and active filtering (with the ability to edit or drop packets) modes.
- There is also an interface for injecting raw Ethernet frames into the network stack, in both directions from TCP/IP to the network and vice versa.
- The support for MTU decrement (setting system-wide MTU decrement) is useful for adding additional headers to IP packets, such as for IP in IP packet tunneling, IPSEC-based VPN, and so on.
- The powerful built-in network filters engine allows you to set rules to pass, block, or redirect network packets to a Windows Packet Filter-based application for further processing.
Applicability/Usage Scope
Windows Packet Filter can be used as a foundation for various types of network applications, including but not limited to:
- User-mode firewall and content filtering solutions, eliminating the need to write kernel-mode drivers.
- Kernel-mode firewall and content filtering solutions, which require kernel-mode programming skills and a Source Code license, but offer the maximum possible performance.
- Internet Connection Sharing (Network Address Translation) that can be implemented in either user or kernel mode, depending on performance requirements.
- Virtual Private Network solutions (IPSEC, SSL VPN, WireGuard, etc.) that can also be implemented in either user or kernel mode, depending on performance requirements.
- Network packet tunneling solutions, where packets captured from the network can be tunneled from the client to the remote system using SSL, SSH, HTTP, ICMP, etc. The remote host can extract the packets and inject them into the real network after modifying the required packet headers. Response packets can be returned to the client in the same manner, potentially bypassing certain network access limitations.
- Packet sniffer, allowing you to capture and inspect all packets sent and received by TCP/IP.
- IP shaping solutions, to limit bandwidth for Internet users.
- Network traffic counting and bandwidth management solutions.
- Wireless Firewall Gateways, even with HTTP authorization.
- Transparent proxy solutions based on NDIS level packet redirection, which can be used for tasks such as decrypting SSL (Man-In-The-Middle), parental content control, and e-mail SPAM filtering.
- Transparent filtering network bridges.
Downloads
You can download the latest Windows Packet Filter driver installer at no cost, making it suitable for personal, educational, or non-profit organization use. This enables you to test and evaluate the software’s reliability and performance. The driver installer for your platform, as well as example binaries, can be downloaded from GitHub.
The source code for Windows Packet Filter samples, along with the most recent ndisapi library, is also accessible on GitHub. This offers a comprehensive resource for those interested in delving deeper into the software.
For .NET developers, the ndisapi library includes a C++/CLI class library. Alternatively, the ndisapi.net p/Invoke C# library is available for those who prefer working in C#.
Rust developers can take advantage of the ndisapi-rs crate, which provides a complete, idiomatic Rust API built on top of the Windows Packet Filter driver. This enables the utilization of Rust’s safety and performance features for network packet manipulation.
Important notes:
Please note that the standard driver builds have a network MTU limit of 1500 bytes, which may result in a performance degradation for 10 Gbps networks with Jumbo frames. However, builds supporting Ethernet Jumbo frames up to 9000 bytes are available to licensed customers for a better network experience.
Windows Packet Filter Advanced Samples
The available example applications provided with Windows Packet Filter include:
- ProxiFyre – an advanced SOCKS5 Proxifier for Windows, expanding upon the base version of the Windows Packet Filter socksify demo below by introducing support for UDP and the capability to handle multiple proxy instances.
- Internet Gateway – a simple MFC application for Internet connection sharing.
- WAN Emulator – a console application that simulates Long Fat Network behavior.
- Capture Packet Filter – a native C++ example that intercepts and saves packets to a PCAP file.
- DNS Proxy Server – a native C++ example that redirects DNS protocol through a transparent UDP proxy.
- DNS Tracer – a native C++ example that intercepts and decodes DNS responses.
- Ethernet Bridge – a native C++ example that implements bridging wired and wireless networks.
- IPv6 Parser – a native C++ example that intercepts IPv6 packets and matches to the originating process.
- SNI Inspector – a native C++ example that intercepts network packets and extracts SNI from HTTPS and Host from HTTP packets.
- Socksify – a native C++ example that redirects selected TCP connections through a SOCKS5 proxy.
- UDP to TCP Converter – a native C++ example that demonstrates how to convert UDP packets to TCP and vice versa.
- Rebind – a native C++ example that demonstrates how to rebind outgoing TCP/UDP connections for the specified application from the default network interface to a different one.
- Hyperscan – a high-performance native C++ example showcasing the integration of the Hyperscan and llhttp libraries. This application intercepts network packets, parses them, detects HTTP protocol sessions, and applies the HTTP protocol parsing on the detected sessions using
llhttp. - PcapPlusPlus – native C++ example that leverages the PcapPlusPlus library to intercept network packets, specifically focusing on extracting the Server Name Indication (SNI) from HTTPS packets. The program also performs Transport Layer Security (TLS) fingerprinting to identify the specific version of TLS being utilized.
- TestDotNet – a C# example that demonstrates the usage of the NDISAPI library in filtering scenarios.
These sample applications offer a great starting point for exploring the capabilities of Windows Packet Filter and can be used as a foundation for building your own custom network applications.
License
Windows Packet Filter is free for personal or educational use, including non-profit organizations.
For the software publishers who wish to use Windows Packet Filter in their products, we offer two types of licenses. Each license includes one year of free updates & support and custom driver build*.
The first type of license is a Binary License, which allows the use of our pre-compiled Windows Packet Filter driver in your product. This license is ideal for software publishers who do not need to modify the driver or its behavior.
The second type of license is a Source Code License, which provides access to the source code of Windows Packet Filter driver and allows you to modify it to fit your specific needs. This license is ideal for software publishers who require customization of the driver or its behavior.
| License type | Complete Source Code | Price (USD) | Online Order |
| Developer | NO | 3000.00 | Buy Now! |
| Source Code | YES | 9000.00 | Buy Now! |
| Developer to Source Upgrade | YES | 6000.00 | Buy Now! |
Notes:
* – For those who need to redistribute the WinpkFilter drivers as part of their software, it is advisable to create or request a custom build. This can help prevent potential conflicts with other applications that are based on WinpkFilter. As a licensed Developer, you can request a custom build by contacting support@ntkernel.com. A single custom build per license is included with both the Developer and Source Code subscriptions, and any additional custom-builds will incur an additional charge of 100 USD each.
Subscription Renewal
To renew your support plan, simply select the desired option and follow the checkout process. If you have any questions or need assistance, please do not hesitate to contact us at support@ntkernel.com. Our team is always ready to help and ensure that you get the most out of your investment in Windows Packet Filter.
- Renew Support & Updates for 1 year: This option allows you to receive software updates and technical support for a period of 1 year.
- Renew Support & Updates for 2 years: This option provides you with two years of software updates and technical support.
- Renew Support & Updates for 3 years: This option offers you a three-year period of software updates and technical support.
| License type | Price (USD) | Online Order |
| Developer Renew Support & Updates for 1 year | 2000.00 | Buy Now! |
| Developer Renew Support & Updates for 2 years | 3000.00 | Buy Now! |
| Developer Renew Support & Updates for 3 years | 4000.00 | Buy Now! |
| Source Code Renew Support & Updates for 1 year | 6000.00 | Buy Now! |
| Source Code Renew Support & Updates for 2 years | 9000.00 | Buy Now! |
| Source Code Renew Support & Updates for 3 years | 12000.00 | Buy Now! |
Support
Please ask questions in our support forum.
* – due to EOL of SHA-1 code signing on December 1, 2020, it is no longer possible to sign drivers for Windows Vista/2008. To run Windows Packet Filter on these operating systems, you will need to use the Disable Driver Signing Enforcement option.
Windows Packet Filter (WinpkFilter©) is a high-performance packet filtering framework for Windows that allows developers to transparently filter (view and modify) raw network packets at the NDIS level of the network stack with minimal impact on network activity and without having to write any low-level driver code.
Windows Packet Filter includes NDIS 3.1/4 hooking VxD driver (Windows 95/ME), NDIS 4 hooking filter driver (Windows NT/2000/XP), NDIS 5 Intermediate (Windows XP/2003) and NDIS 6 Lightweight Filter (LWF) drivers as well as companion user-mode API DLL and samples.
A key advantage of Windows Packet Filter in comparison to other packets filtering frameworks for Windows (based on Windows Filtering Platform (WFP) callout drivers, Layered Service Providers (LSP), TDI filters etc…) is the ability to manipulate raw Ethernet frames achieved by installing driver below all network protocol drivers and just above network interface driver. Thus, WinpkFilter driver has an ultimate control over all network traffic flow destined to or originated from your system and allows you to modify any packet, drop it or even forge and insert an entirely new one. Using Windows Packet Filter requires no experience in kernel mode programming on your behalf, since it provides you with a powerful user level API. However, if you need to implement your solution (to achieve better performance) in kernel mode, you can do that as well by adding your functional code directly to Windows Packet Filter driver’s code.
System Requirements
| Windows 95/98/Millennium | Windows Server 2008* | Windows Server 2012 R2 |
| Windows NT 4.0 | Windows 7 | Windows 10 |
| Windows 2000 | Windows Server 2008 R2 | Windows Server 2016 |
| Windows XP | Windows 8 | Windows Server 2019 |
| Windows Server 2003 | Widows Server 2012 | Windows 11 |
| Windows Vista* | Windows 8.1 | Windows Server 2022 |
The following connections types are supported for the operating systems above:
- Wired Ethernet (802.3)
- Wi-Fi (802.11)
- WAN (Analog/ISDN modems, PPPoE, 3G/4G mobile modems)
- Mobile Broadband (PPIP)
Product features
- Reliability and stability confirmed by hundreds of satisfied customers since product launch in 2002 ranged from small shareware companies to world known corporations.
- High performance. WinpkFilter allows handling Gigabit network bandwidth in user mode application without noticeable performance degradation.
- Complete and easy portability across all Windows desktop platforms.
- Operates on RAS/PPP adapters and supports Windows 7 Mobile Broadband stack(PPIP)
- Passive network listening (collecting network packets) and active filtering (with capability to edit/drop network packets) modes
- Interface for injecting raw Ethernet frames into the network stack (either destined from the TCP/IP to the network and in reversed direction)
- Support for MTU decrement (allows setting system-wide MTU decrement). This option is useful if you plan to add additional headers to IP packets (implement IP in IP packet tunneling, IPSEC based VPN and so on).
- The powerful built-in network filters engine allows setting rules to pass, block or redirect a network packet to a Windows Packet Filter-based application for further processing.

Applicability/Usage Scope
Windows Packet Filter can be used as a base for the following kinds of network applications (including but not limited to):
- User-mode firewall and content filtering solutions. No more need to write kernel mode drivers to implement the firewall!
- Kernel-mode firewall and content filtering solutions. This requires kernel-mode programming skills and Source Code license (to integrate your network packet processing code directly into the drivers) but provides the maximum possible performance.
- Internet Connection Sharing (Network Address Translation) that can be implemented either in user or kernel depending on performance requirements.
- Virtual Private Network solution (IPSEC, SSL VPN, Wireguard etc.) that can also be implemented both in user and kernel depending on performance requirements.
- Network packets tunneling solution. An example, packets captured from the network can be tunneled from the client to the remote system inside the SSL, SSH, HTTP, ICMP etc., extracted by the remote host and injected into the real network (after required packet headers modifications). Response packets can be returned to the client in the same manner. This may allow bypassing certain network access limitations.
- Packet sniffer. You can capture and inspect all packets sent to (received from) TCP/IP.
- IP shaping solutions (when you need to limit bandwidth for Internet users).
- Network traffic counting and bandwidth management solutions.
- Wireless Firewall Gateways, even with HTTP authorization.
- Transparent proxy solution based on NDIS level packet redirection. This can be used, an example, to decrypt SSL(Man-In-The-Middle), parent content control, e-mail SPAM filtering etc…
- Transparent filtering bridge
Windows packet filter (фильтр пакетов Windows) — это программное обеспечение, которое позволяет пользователям контролировать и мониторить сетевой трафик на компьютере под управлением операционной системы Windows. С его помощью можно фильтровать и анализировать данные пакеты, проходящие через сетевое соединение.
Windows packet filter позволяет пользователям определять определенные правила, которые будут применяться к каждому пакету данных. Эти правила могут включать в себя такие параметры, как IP-адрес источника или назначения, порт, протокол и многое другое. Таким образом, пользователь может настроить фильтр таким образом, чтобы он пропускал только нужные пакеты и блокировал нежелательные.
Использование Windows packet filter может быть полезно для повышения безопасности системы, защиты от вредоносного ПО и мониторинга сетевого трафика. Это особенно важно в условиях активных сетей, где представляется угроза для конфиденциальности и безопасности данных.
Для того чтобы использовать Windows packet filter, пользователю необходимо установить специальное программное обеспечение, поддерживающее эту функцию. После чего, следует настроить нужные правила фильтрации и мониторинга сетевого трафика. Получившаяся конфигурация фильтра применяется автоматически к каждому новому пакету данных, проходящему через сетевое соединение.
Содержание
- Основы работы с Windows packet filter
- Что такое Windows packet filter?
- Преимущества использования Windows packet filter
Основы работы с Windows packet filter
Основная задача Windows packet filter заключается в мониторинге сетевого трафика и анализе данных, пересылаемых между компьютерами и сетевыми устройствами. Благодаря этому инструменту можно получить информацию о передаваемых пакетах, протоколах, IP-адресах и других сетевых параметрах.
Прежде чем начать использовать Windows packet filter, необходимо установить соответствующую библиотеку на компьютер. Для этого можно скачать и установить официальную версию WinPcap с официального сайта.
После установки библиотеки вы можете начать использовать Windows packet filter в своих программных решениях. Обычно программисты пишут специальные приложения для анализа сетевого трафика, создания сетевых утилит или обеспечения безопасности сети.
Windows packet filter предоставляет различные функции для работы с сетевыми пакетами. Разработчики могут использовать эти функции для захвата и анализа пакетов, управления фильтрацией трафика, анализа данных и обработки событий, связанных с сетевыми пакетами.
Важно отметить, что правильное использование Windows packet filter требует знаний о протоколах сетевого взаимодействия, структуре сетевых пакетов и основах программирования. Также необходимо учитывать проблемы безопасности и защиты данных.
В целом, Windows packet filter является мощным и гибким инструментом для работы с сетевым трафиком в операционных системах Windows. Он позволяет анализировать, фильтровать и контролировать пакеты данных, пересылаемые в сети, и может быть полезен для различных задач, связанных с сетевой безопасностью, мониторингом и отладкой сетевых приложений.
Что такое Windows packet filter?
Фильтр пакетов Windows используется для множества задач, таких как:
- Контроль и фильтрация входящего и исходящего трафика;
- Детализированный анализ пакетов и отслеживание соединений;
- Проверка безопасности и блокирование вредоносных пакетов;
- Настройка портов и протоколов для обеспечения безопасности и функциональности сетевых приложений.
Фильтр пакетов Windows обеспечивает гибкий и мощный механизм для управления сетевым трафиком, позволяя пользователям создавать правила, которые определяют, какие пакеты должны быть разрешены или заблокированы на основе различных условий. Настройки фильтра пакетов Windows можно изменять с помощью специальных программных средств или командной строки операционной системы.
Преимущества использования Windows packet filter
Основные преимущества использования Windows packet filter:
| Преимущество | Описание |
|---|---|
| Улучшенная безопасность | WPf позволяет настраивать правила фильтрации, блокируя нежелательный и потенциально опасный сетевой трафик. Это может помочь в предотвращении взломов, атак и утечек данных. |
| Контроль сетевого трафика | С помощью WPf администраторы могут управлять сетевым трафиком, настраивая правила фильтрации для различных протоколов, портов и IP-адресов. Это дает возможность ограничить доступ к определенным ресурсам или установить приоритеты в использовании сетевого соединения. |
| Отладка и мониторинг сетевой активности | WPf позволяет отслеживать сетевую активность, анализировать пакеты данных и захватывать сетевой трафик для последующего изучения. Это полезно при поиске и устранении проблем с сетью и при отладке приложений. |
| Гибкость настройки | WPf предоставляет возможность настройки правил фильтрации с учетом конкретных потребностей и требований пользователя или организации. Это позволяет точно определить, какой сетевой трафик должен быть разрешен или заблокирован. |
В целом, использование Windows packet filter может повысить безопасность, обеспечить контроль над сетевым трафиком и помочь в отладке и мониторинге сетевой активности. Это мощный инструмент, который может быть полезен для пользователя как в домашних условиях, так и в организационной сети.
Search code, repositories, users, issues, pull requests…
Provide feedback
Saved searches
Use saved searches to filter your results more quickly
Sign up
How do I turn off Windows Filtering Platform?
Page Contents
- 1 How do I turn off Windows Filtering Platform?
- 2 What is event id 5152?
- 3 How do I turn off packet filtering in Windows 10?
- 4 How do I disable WFP?
- 5 What is Windows packet filter?
- 6 What is WFP driver?
- 7 What does ” Windows Filtering Platform blocked a packet ” mean?
- 8 What does event ID 5152 in Windows Firewall mean?
How to disable Windows 10 system log
- Open the CMD prompt as Administrator: Press Windows , type cmd , press Ctrl + Shift + Enter and confirm.
- Type (or copy/paste) the following and press Enter : auditpol /set /subcategory:”Filtering Platform Connection” /success:disable /failure:enable.
What is event id 5152?
When a network packet is blocked by the Windows Filtering Platform, event 5152 is logged. This event is logged for every received network packet.
What does Windows Filtering Platform do?
Purpose. Windows Filtering Platform (WFP) is a set of API and system services that provide a platform for creating network filtering applications. With the WFP API, developers can implement firewalls, intrusion detection systems, antivirus programs, network monitoring tools, and parental controls.
What is filtering platform packet drop?
Audit Filtering Platform Packet Drop determines whether the operating system generates audit events when packets are dropped by the Windows Filtering Platform. A high rate of dropped packets may indicate that there have been attempts to gain unauthorized access to computers on your network.
How do I turn off packet filtering in Windows 10?
Disable TCP/IP packet filtering
- In Control Panel, double-click Network Connections.
- Right-click the connection, and then click Properties.
- Select Internet Protocol (TCP/IP), and then click the Properties tab.
- Click Advanced, and then click the Options tab.
How do I disable WFP?
You may disable WFP by setting the value SFCDisable (REG_DWORD) in HKEY_LOCAL_MACHINE\ SOFTWARE\ Microsoft\ Windows NT\ CurrentVersion\ Winlogon. By default, SFCDisable is set to 0, which means WFP is active. Setting SFCDisable to 1 will disable WFP.
What is Microsoft Security auditing?
Windows security auditing is a Windows feature that helps to maintain the security on the computer and in corporate networks. Windows auditing is intended to monitor user activity, perform forensic analysis and incident investigation, and troubleshooting.
What is audit handle manipulation?
Handle Manipulation auditing under Object Access is needed to correctly enable the recording of events related to the access and changing of files and directories. Auditing must also be enabled on the specific objects to be audited or with Global Audit Access Auditing configured on the file system.
What is Windows packet filter?
Windows Packet Filter (WinpkFilter) is a high performance packet filtering framework for Windows that allows developers to transparently filter (view and modify) raw network packets at the NDIS level of the network stack with minimal impact on network activity and without having to write any low level driver code.
What is WFP driver?
Windows Filtering Platform (WFP) is a set of system services in Windows Vista and later that allows Windows software to process and filter network traffic. Microsoft intended WFP for use by firewalls, antimalware software, and parental controls apps. WFP relies on Windows Vista’s Next Generation TCP/IP stack.
What is Microsoft WFP?
Windows Filtering Platform (WFP) is a network traffic processing platform designed to replace the Windows XP and Windows Server 2003 network traffic filtering interfaces. WFP consists of a set of hooks into the network stack and a filtering engine that coordinates network stack interactions.
Can I disable packet filter?
In the System tab choose “advanced” and there is a checkbox to disable all packet filtering. It will also turn off NAT. If you want to keep the ability to filter packets based on firewall rules, go to NAT >> Outbound and change it to Manual and delete the rule it creates.
What does ” Windows Filtering Platform blocked a packet ” mean?
5152 (F) The Windows Filtering Platform blocked a packet. (Windows 10) – Windows security | Microsoft Docs 5152 (F): The Windows Filtering Platform blocked a packet. This event generates when Windows Filtering Platform has blocked a network packet. This event is generated for every received network packet.
What does event ID 5152 in Windows Firewall mean?
5152 The Windows Filtering Platform blocked a packet. Event 5152 indicates that a packet (IP layer) is blocked. Event 5157 and Event 5152 are general Windows Firewall security audit, you should look into the event detail of the blocked connection attempt to decide whether that attempt should be allowed.
How to find Windows Filtering Platform Layer ID?
To find a specific Windows Filtering Platform layer ID, run the following command: netsh wfp show state. As a result of this command wfpstate.xml file will be generated. Open this file and find specific substring with required layer ID ( ), for example: For 5152 (F): The Windows Filtering Platform blocked a packet.
How to find the process ID of a blocked packet?
Event Versions: 0. Process ID [Type = Pointer]: hexadecimal Process ID of the process to which blocked network packet was sent. Process ID (PID) is a number used by the operating system to uniquely identify an active process. To see the PID for a specific process you can, for example, use Task Manager (Details tab, PID column):