При запуске новых сервисов в Windows, вы можете обнаружить что нужный порт уже занят (слушается) другой программой (процессом). Разберемся, как определить какая программ прослушивает определенный TCP или UDP порт в Windows.
Например, вы не можете запустить сайт IIS на стандартном 80 порту в Windows, т.к. этот порт сейчас занят (при запуске нескольких сайтов в IIS вы можете запускать их на одном или на разных портах). Как найти службу или процесс, который занял этот порт и завершить его?
Чтобы вывести полный список TCP и UDP портов, которые прослушиваются вашим компьютером, выполните команду:
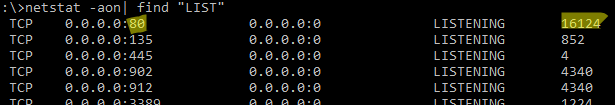
netstat -aon| find "LIST"
Или вы можете сразу указать искомый номер порта:
netstat -aon | findstr ":80" | findstr "LISTENING"
Используемые параметры команды netstat:
- a – показывать сетевые подключения и открытые порты
- o – выводить идентфикатор професса (PID) для каждого подключения
- n – показывать адреса и номера портов в числовом форматер
По выводу данной команды вы можете определить, что 80 порт TCP прослушивается (статус
LISTENING
) процессом с PID 16124.
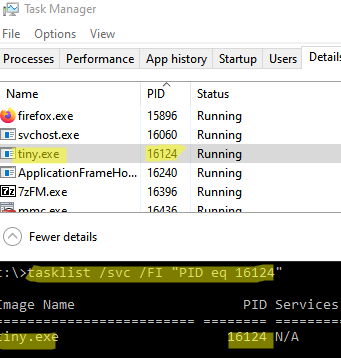
Вы можете определить исполняемый exe файл процесса с этим PID с помощью Task Manager или с помощью команды:
tasklist /FI "PID eq 16124"
Можно заменить все указанные выше команды одной:
for /f "tokens=5" %a in ('netstat -aon ^| findstr :80') do tasklist /FI "PID eq %a"
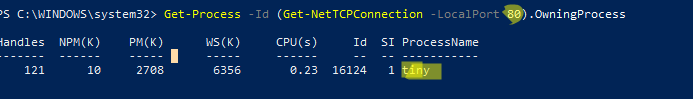
С помощью однострочной PowerShell команды можно сразу получить имя процесса, который прослушивает:
- TCP порт:
Get-Process -Id (Get-NetTCPConnection -LocalPort 80).OwningProcess - UDP порт:
Get-Process -Id (Get-NetUDPEndpoint -LocalPort 53).OwningProcess
Можно сразу завершить этот процесс, отправив результаты через pipe в командлет Stop-Process:
Get-Process -Id (Get-NetTCPConnection -LocalPort 80).OwningProcess| Stop-Process
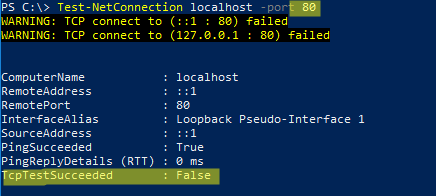
Проверьте, что порт 80 теперь свободен:
Test-NetConnection localhost -port 80
Чтобы быстрой найти путь к исполняемому файлу процесса в Windows, используйте команды:
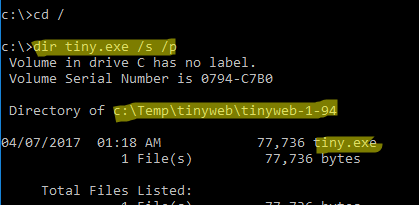
cd /
dir tiny.exe /s /p
Или можно для поиска файла использовать встроенную команду where :
where /R C:\ tiny
В нашем случае мы нашли, что исполняемый файл
tiny.exe
(легкий HTTP сервер), который слушает 80 порт, находится в каталоге c:\Temp\tinyweb\tinyweb-1-94
How do I find out which process is listening on a TCP or UDP port on Windows?
Mateen Ulhaq
24.7k19 gold badges102 silver badges136 bronze badges
asked Sep 7, 2008 at 6:26
readonlyreadonly
344k107 gold badges204 silver badges205 bronze badges
11
PowerShell
TCP
Get-Process -Id (Get-NetTCPConnection -LocalPort YourPortNumberHere).OwningProcess
UDP
Get-Process -Id (Get-NetUDPEndpoint -LocalPort YourPortNumberHere).OwningProcess
cmd
netstat -a -b
(Add -n to stop it trying to resolve hostnames, which will make it a lot faster.)
Note Dane’s recommendation for TCPView. It looks very useful!
-a Displays all connections and listening ports.
-b Displays the executable involved in creating each connection or listening port. In some cases well-known executables host multiple independent components, and in these cases the sequence of components involved in creating the connection or listening port is displayed. In this case the executable name is in [] at the bottom, on top is the component it called, and so forth until TCP/IP was reached. Note that this option can be time-consuming and will fail unless you have sufficient permissions.
-n Displays addresses and port numbers in numerical form.
-o Displays the owning process ID associated with each connection.
answered Sep 7, 2008 at 6:28
15
There’s a native GUI for Windows:
-
Start menu → All Programs → Accessories → System Tools → Resource Monitor
-
or run
resmon.exe, -
or from TaskManager → Performance tab.
serge
14.1k35 gold badges124 silver badges206 bronze badges
answered May 18, 2014 at 5:02
bcorsobcorso
45.7k10 gold badges63 silver badges76 bronze badges
10
For Windows:
netstat -aon | find /i "listening"
xash
3,70210 silver badges22 bronze badges
answered Sep 7, 2008 at 6:32
akuaku
122k32 gold badges174 silver badges203 bronze badges
6
Use TCPView if you want a GUI for this. It’s the old Sysinternals application that Microsoft bought out.
answered Sep 7, 2008 at 6:38
DaneDane
9,7375 gold badges28 silver badges23 bronze badges
3
The -b switch mentioned in most answers requires you to have administrative privileges on the machine. You don’t really need elevated rights to get the process name!
Find the pid of the process running in the port number (e.g., 8080)
netstat -ano | findStr "8080"
Find the process name by pid
tasklist /fi "pid eq 2216"
Jaywalker
3,0793 gold badges29 silver badges44 bronze badges
answered Jan 24, 2018 at 3:50
Ram SharmaRam Sharma
2,4971 gold badge8 silver badges7 bronze badges
You can get more information if you run the following command:
netstat -aon | find /i "listening" |find "port"
using the ‘Find’ command allows you to filter the results. find /i "listening" will display only ports that are ‘Listening’. Note, you need the /i to ignore case, otherwise you would type find «LISTENING». | find "port" will limit the results to only those containing the specific port number. Note, on this it will also filter in results that have the port number anywhere in the response string.
answered Oct 8, 2013 at 18:56
Nathan24Nathan24
1,3721 gold badge11 silver badges20 bronze badges
4
-
Open a command prompt window (as Administrator) From «Start\Search box» Enter «cmd» then right-click on «cmd.exe» and select «Run as Administrator»
-
Enter the following text then hit Enter.
netstat -abno-a Displays all connections and listening ports.
-b Displays the executable involved in creating each connection or
listening port. In some cases well-known executables host
multiple independent components, and in these cases the
sequence of components involved in creating the connection
or listening port is displayed. In this case the executable
name is in [] at the bottom, on top is the component it called,
and so forth until TCP/IP was reached. Note that this option
can be time-consuming and will fail unless you have sufficient
permissions.-n Displays addresses and port numbers in numerical form.
-o Displays the owning process ID associated with each connection.
-
Find the Port that you are listening on under «Local Address»
-
Look at the process name directly under that.
NOTE: To find the process under Task Manager
-
Note the PID (process identifier) next to the port you are looking at.
-
Open Windows Task Manager.
-
Select the Processes tab.
-
Look for the PID you noted when you did the netstat in step 1.
-
If you don’t see a PID column, click on View / Select Columns. Select PID.
-
Make sure “Show processes from all users” is selected.
-
answered Nov 8, 2012 at 1:49
CyborgCyborg
1,24412 silver badges12 bronze badges
Get PID and Image Name
Use only one command:
for /f "tokens=5" %a in ('netstat -aon ^| findstr 9000') do tasklist /FI "PID eq %a"
where 9000 should be replaced by your port number.
The output will contain something like this:
Image Name PID Session Name Session# Mem Usage
========================= ======== ================ =========== ============
java.exe 5312 Services 0 130,768 K
Explanation:
-
it iterates through every line from the output of the following command:
netstat -aon | findstr 9000 -
from every line, the PID (
%a— the name is not important here) is extracted (PID is the5th element in that line) and passed to the following commandtasklist /FI "PID eq 5312"
If you want to skip the header and the return of the command prompt, you can use:
echo off & (for /f "tokens=5" %a in ('netstat -aon ^| findstr 9000') do tasklist /NH /FI "PID eq %a") & echo on
Output:
java.exe 5312 Services 0 130,768 K
answered Feb 10, 2016 at 10:17
ROMANIA_engineerROMANIA_engineer
54.6k29 gold badges203 silver badges200 bronze badges
1
First we find the process id of that particular task which we need to eliminate in order to get the port free:
Type
netstat -n -a -o
After executing this command in the Windows command line prompt (cmd), select the pid which I think the last column. Suppose this is 3312.
Now type
taskkill /F /PID 3312
You can now cross check by typing the netstat command.
NOTE: sometimes Windows doesn’t allow you to run this command directly on CMD, so first you need to go with these steps:
From the start menu -> command prompt (right click on command prompt, and run as administrator)
answered Aug 23, 2014 at 15:25
1
With PowerShell 5 on Windows 10 or Windows Server 2016, run the Get-NetTCPConnection cmdlet. I guess that it should also work on older Windows versions.
The default output of Get-NetTCPConnection does not include Process ID for some reason and it is a bit confusing. However, you could always get it by formatting the output. The property you are looking for is OwningProcess.
-
If you want to find out the ID of the process that is listening on port 443, run this command:
PS C:\> Get-NetTCPConnection -LocalPort 443 | Format-List LocalAddress : :: LocalPort : 443 RemoteAddress : :: RemotePort : 0 State : Listen AppliedSetting : OwningProcess : 4572 CreationTime : 02.11.2016 21:55:43 OffloadState : InHost -
Format the output to a table with the properties you look for:
PS C:\> Get-NetTCPConnection -LocalPort 443 | Format-Table -Property LocalAddress, LocalPort, State, OwningProcess LocalAddress LocalPort State OwningProcess ------------ --------- ----- ------------- :: 443 Listen 4572 0.0.0.0 443 Listen 4572 -
If you want to find out a name of the process, run this command:
PS C:\> Get-Process -Id (Get-NetTCPConnection -LocalPort 443).OwningProcess Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName ------- ------ ----- ----- ------ -- -- ----------- 143 15 3448 11024 4572 0 VisualSVNServer
answered Nov 2, 2016 at 19:19
bahrepbahrep
30k12 gold badges103 silver badges151 bronze badges
To get a list of all the owning process IDs associated with each connection:
netstat -ao |find /i "listening"
If want to kill any process have the ID and use this command, so that port becomes free
Taskkill /F /IM PID of a process
answered Apr 17, 2014 at 14:38
Monis MajeedMonis Majeed
1,35814 silver badges21 bronze badges
1
It is very simple to get the port number from a PID in Windows.
The following are the steps:
-
Go to run → type cmd → press Enter.
-
Write the following command…
netstat -aon | findstr [port number](Note: Don’t include square brackets.)
-
Press Enter…
-
Then cmd will give you the detail of the service running on that port along with the PID.
-
Open Task Manager and hit the service tab and match the PID with that of the cmd, and that’s it.
answered May 30, 2016 at 6:36
Nishat LakhaniNishat Lakhani
7331 gold badge8 silver badges20 bronze badges
0
netstat -aof | findstr :8080 (Change 8080 for any port)
answered Feb 16, 2021 at 23:59
David JesusDavid Jesus
1,9812 gold badges29 silver badges34 bronze badges
To find out which specific process (PID) is using which port:
netstat -anon | findstr 1234
Where 1234 is the PID of your process. [Go to Task Manager → Services/Processes tab to find out the PID of your application.]
answered Dec 14, 2018 at 6:55
Talha ImamTalha Imam
1,0461 gold badge20 silver badges22 bronze badges
2
In case someone need an equivalent for macOS like I did, here is it:
lsof -i tcp:8080
After you get the PID of the process, you can kill it with:
kill -9 <PID>
answered Aug 12, 2020 at 11:22
wzsowzso
3,5325 gold badges28 silver badges48 bronze badges
2
Just open a command shell and type (saying your port is 123456):
netstat -a -n -o | find "123456"
You will see everything you need.
The headers are:
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:37 0.0.0.0:0 LISTENING 1111
This is as mentioned here.
answered Jan 25, 2017 at 0:13
1
If you’d like to use a GUI tool to do this there’s Sysinternals’ TCPView.
answered Sep 7, 2008 at 6:40
David WebbDavid Webb
191k57 gold badges313 silver badges299 bronze badges
-
Open the command prompt — start → Run →
cmd, or start menu → All Programs → Accessories → Command Prompt. -
Type
netstat -aon | findstr '[port_number]'
Replace the [port_number] with the actual port number that you want to check and hit Enter.
- If the port is being used by any application, then that application’s detail will be shown. The number, which is shown at the last column of the list, is the PID (process ID) of that application. Make note of this.
-
Type
tasklist | findstr '[PID]'
Replace the [PID] with the number from the above step and hit Enter.
- You’ll be shown the application name that is using your port number.
answered May 9, 2019 at 12:18
Anatole ABEAnatole ABE
5751 gold badge7 silver badges12 bronze badges
2
PowerShell
If you want to have a good overview, you can use this:
Get-NetTCPConnection -State Listen | Select-Object -Property *, `
@{'Name' = 'ProcessName';'Expression'={(Get-Process -Id $_.OwningProcess).Name}} `
| select ProcessName,LocalAddress,LocalPort
Then you get a table like this:
ProcessName LocalAddress LocalPort
----------- ------------ ---------
services :: 49755
jhi_service ::1 49673
svchost :: 135
services 0.0.0.0 49755
spoolsv 0.0.0.0 49672
For UDP, it is:
Get-NetUDPEndpoint | Select-Object -Property *, `
@{'Name' = 'ProcessName';'Expression'={(Get-Process -Id $_.OwningProcess).Name}} `
| select ProcessName,LocalAddress,LocalPort
answered Feb 27, 2022 at 22:16
Oliver GaidaOliver Gaida
1,7327 silver badges14 bronze badges
Netstat:
- -a displays all connection and listening ports
- -b displays executables
- -n stop resolve hostnames (numerical form)
-
-o owning process
netstat -bano | findstr "7002" netstat -ano > ano.txt
The Currports tool helps to search and filter
answered Sep 23, 2018 at 5:05
Blue CloudsBlue Clouds
7,3655 gold badges72 silver badges113 bronze badges
Type in the command: netstat -aon | findstr :DESIRED_PORT_NUMBER
For example, if I want to find port 80: netstat -aon | findstr :80
This answer was originally posted to this question.
answered Nov 22, 2016 at 15:36
TechnotronicTechnotronic
8,4744 gold badges40 silver badges53 bronze badges
netstat -ao and netstat -ab tell you the application, but if you’re not a system administrator you’ll get «The requested operation requires elevation».
It’s not ideal, but if you use Sysinternals’ Process Explorer you can go to specific processes’ properties and look at the TCP tab to see if they’re using the port you’re interested in. It is a bit of a needle and haystack thing, but maybe it’ll help someone…
answered Mar 13, 2014 at 19:57
Tony DelroyTony Delroy
103k15 gold badges177 silver badges253 bronze badges
1
Using Windows’ default shell (PowerShell) and without external applications
For those using PowerShell, try Get-NetworkStatistics:
> Get-NetworkStatistics | where Localport -eq 8000
ComputerName : DESKTOP-JL59SC6
Protocol : TCP
LocalAddress : 0.0.0.0
LocalPort : 8000
RemoteAddress : 0.0.0.0
RemotePort : 0
State : LISTENING
ProcessName : node
PID : 11552
answered Aug 25, 2016 at 13:36
mikemaccanamikemaccana
112k99 gold badges392 silver badges497 bronze badges
3
I recommend CurrPorts from NirSoft.
CurrPorts can filter the displayed results. TCPView doesn’t have this feature.
Note: You can right click a process’s socket connection and select «Close Selected TCP Connections» (You can also do this in TCPView). This often fixes connectivity issues I have with Outlook and Lync after I switch VPNs. With CurrPorts, you can also close connections from the command line with the «/close» parameter.
answered Jun 29, 2015 at 22:07
JoshJosh
2,1422 gold badges23 silver badges20 bronze badges
0
A single-line solution that helps me is this one. Just substitute 3000 with your port:
$P = Get-Process -Id (Get-NetTCPConnection -LocalPort 3000).OwningProcess; Stop-Process $P.Id
Edit: Changed kill to Stop-Process for more PowerShell-like language
answered Feb 3, 2019 at 14:46
Angel VenchevAngel Venchev
7071 gold badge7 silver badges18 bronze badges
2
Use:
netstat -a -o
This shows the PID of the process running on a particular port.
Keep in mind the process ID and go to Task Manager and services or details tab and end the process which has the same PID.
Thus you can kill a process running on a particular port in Windows.
answered Aug 13, 2013 at 2:32
nishanisha
7112 gold badges14 silver badges28 bronze badges
To find pid who using port 8000
netstat -aon | findstr '8000'
To Kill that Process in windows
taskkill /pid pid /f
where pid is the process id which you get form first command
answered Jul 14, 2020 at 6:13
jizjiz
3083 silver badges7 bronze badges
2
Follow these tools: From cmd: C:\> netstat -anob with Administrator privileges.
Process Explorer
Process Dump
Port Monitor
All from sysinternals.com.
If you just want to know process running and threads under each process, I recommend learning about wmic. It is a wonderful command-line tool, which gives you much more than you can know.
Example:
c:\> wmic process list brief /every:5
The above command will show an all process list in brief every 5 seconds. To know more, you can just go with /? command of windows , for example,
c:\> wmic /?
c:\> wmic process /?
c:\> wmic prcess list /?
And so on and so forth. 
1
You can also check the reserved ports with the command below. Hyper-V reserve some ports, for instance.
netsh int ipv4 show excludedportrange protocol=tcp
answered Nov 24, 2020 at 14:50
На днях снова поступил вопрос: Как узнать что слушает TCP/IP порт в Windows?
Я уже когда-то писал об этом, но видать пришло время сделать это еще раз…
Задача: узнать процесс, который занял конкретный порт.
Решение: воспользуемся командной строкой, чтобы увидеть, какие порты используются в данный момент и имеют специальный флаг, который говорит нам, какой порт назначен на каждый номер идентификатора процесса Windows. Тогда мы можем использовать этот номер, чтобы найти, какой именно это процесс.
Откройте командную строку и введите следующее, возможно, придется запустить ее в режиме администратора, чтобы увидеть все процессы:
NETSTAT -AON | MORE
Если вы посмотрите на правую часть, то вы увидите список PID-ов или идентификаторов процессов. Найдите тот, который привязан к порту, с которым вы работаете, вы увидите 0.0.0.0:80 или порт 80, его PID — 4708.
Теперь вы можете просто открыть диспетчер задач, возможно, придется использовать опцию Показать процессы для всех пользователей, и тогда вы сможете найти PID в списке.
Есть еще один вариант:
Например C:\>netstat -an|findstr /i listen
Подробней читаем здесь: http://dosprompt.info/network/netstat.example.asp
Всем хорошей работы !!!
08.08.2012 —
Posted by |
ms windows server 2008
Sorry, the comment form is closed at this time.
Whenever an application wants to make itself accessible over the network, it claims a TCP/IP port, which means that port can’t be used by anything else. So if you need to use an in-use port, how do you tell what application is holding it?
There’s a number of ways to tell which application has the port locked, here we will use a windows built-in way using the command line and Task Manager.
Using Built-In Tools to See What is Listening on a Port
The first step is to use a command-line tool to see what ports are in use, and use a special flag that tells us which port is assigned to each Windows process identifier number. Then we can use that number to look up exactly which process it is.
Open up a command prompt and type in the following—you may have to open in Administrator mode to see all processes:
netstat -ab | more
This will immediately show you a list, although it’s maybe a little complicated. You’ll see the process name in the list, and you can search for it.
You can also use this other method, which takes an extra step, but makes it easier to locate the actual process:
netstat -aon | more
If you look on the right-hand side, you’ll see where I’ve highlighted the list of PIDs, or Process Identifiers. Find the one that’s bound to the port that you’re trying to troubleshoot—for this example, you’ll see that 0.0.0.0:80, or port 80, is in use by PID 1184.
Now you can simply open up Task Manager—you might have to use the option to Show Processes for All Users, and then you’ll be able to find the PID in the list. Once you’re there, you can use the End Process, Open File Location, or Go to Service(s) options to control the process or stop it.
Alternatively you can even use resource monitor to stop any process that is running. To open resource monitor type resmon.exe in run. This will bring up the resource monitor window.
There would be situations were some other process is running at port 80. To stop anything running in port 80 the following command can be used from command prompt.
net stop http /y
Frequently Asked Questions (FAQs)
What application is listening on a TCP IP port in Windows?
Netstat is a diagnostic tool that creates a list of open ports that the machine is listening to, as well as the ports it is currently connected to on other machines. In Netstat, stat stands for state or statistics, which tells you the current network status of every TCP connection.
How do I find out what application is using a TCP port?
You can use Netstat -b -a -o.
This tool provides a list of all open ports and their associated processes. The -o shows the process id, which you can look up in your task manager or processes tab. To end that process, simply enter taskkill /PID xxxx.
How can I tell if a server is listening on a port?
On the server itself, use Netstat -an to check to see which ports are listening. From outside the server, telnet host port can be used to check connections. A refused connection means nothing is running, whereas an accepted connection means something is running. Timeout implies a firewall is blocking access.
How do I find out what application is using port 8080?
Open the diagnostic tool, netstat -ano. This tool will list the PID (Process Identifier) that is listening to port 80. Open the Task Manager’s Processes tab. Select “View” and “Select Columns” menu. Activate the PID column to see the name of the process listening on port 80.
Is Port 8080 http or https?
Port 8080 is a non-standard, high number port that is popular as an alternative port for HTTP servers, most often application servers. Port 8443 is a default alternative port for HTTPS servers. It can also be used as an alternative port for any protocol like ssh, FTP, NTP, BOOTP, etc.
Why is port 8080 default?
Historically, only authorized system administrators were able to establish and operate a web server on port 80, since this was within the first 1023-port privileged region. When non-administrators wished to run their own web servers, they often chose port 8080 to host a secondary or alternate web server.
Introduction
Like Linux, Windows does have a netstat command and it can come handy when you are in need of network-related monitoring and troubleshooting.
Consider you have any of the following requirement
- How to find who or which process owns the port in Windows Server
- To see how many HTTP/DB connections opened by IIS/Any other App server runs on windows.
- To make sure the port is open and listening for incoming calls in Windows Server
- How many connections are open from IIS to Database in WIndows server
- How many Connections are open from Application Server like Tomcat running on Windows Server
- Connection leaks to the database from windows server etc
Netstat command windows have the following syntax and options support.
using this various options given in the preceding picture you can derive many useful commands to help you in your endeavour
- Find all the ESTABLISHED and WAITING TCP connections
- Get Detailed info of TCP and UDP connections
- List of Connections and Ports open with Process information – Find Who Owns the port
- Find Who owns the port with Process ID and Process Name
- Get Fully Qualified remote address on the open connections
- How to Grep for a Specific port with windows netstat command
- Execute Windows Netstat commands in interval
Here we have given some of the most used and quick netstat command snippets. You can choose one or you can frame one using the options shown in the preceding picture
To find all the Established and Waiting for TCP connections.
This is a Simple Netstat command it would result the simple list of TCP connections Established on the server
netstat
To get Detailed info on Ports Open, Ports Listening, Connections Established for TCP/UDP connections
netstat -a command would give the extended result of ports opened on the server and established connections and their current state for both TCP and UDP connections.
this command can be used to check if your application server (Tomcat,Weblogic,IIS) or any process running on the windows server has opened and listening on a certain port.
netstat -a
You can also use the netstat -an command to get faster results as netstat -a would take longer time in the name resolution of the remote foreign address
netstat -an
So, What is the Difference between netstat -a and netstat -an why the latter one is faster
Simply put,
netstat -ancommand would only show the remote server IP addresses wherenetstat -awould try to resolve the name for that IP address. Thusnetstat -anwould be faster than thenetstat -a
How to get the Process name [service name] along with connections – Who owns the port
Consider that you have any of the tomcat ,weblogic, websphere, Apache HTTPD, IIS, MSSQL server, Oracle DB product running on the windows server
During issues, It might be necessary for you to validate which process owns which port. or would have wanted to know how many connections are currently open or established.
In Such cases, you can use the following command which would result in the great detailed info along with the process name (or) the binary name which opened the port or the connection.
You have to run the command prompt as Administrator [ Run as Administrator ] before running this command
netstat -ab
If you do not want the the Domain Name be displayed in the Foreign Address and OK with the numeric IP information. You can use netstat -anb as said earlier, adding an -n option makes the command faster
Get the Process ID and Process Name of the Ports and Connections Open
In the previous example, with netstat -ab we were only getting the Process name who owns the port. not the Process ID.
Getting a Process ID of the process who owns the port would also be helpful in most of the cases.
To get the PID information you need to use -o option along with -ab
netstat -abo
Using -f option to get Fully Qualified Domain Names (FQDN) or Remote Address
With any preceding command, you can use the -f option to get the Fully Qualified Domain Names (FQDN) of the remote address
netstat -afb
You cannot use -n with -f is for FQDN where -n is for only numeric.
Look for a Specific Port or Process ID using FINDSTR [ equivalent to grep ]
How to make sure a Specific port is listening in windows
The windows netstat command output is so large and if you are looking for a precise port or process or PID. you can use findstr , a windows equivalent for Linux grep command
netstat -afb |findstr 8080
in the preceding snapshot you can see that findstr was used to check if port 8080 is open and tomcat is listening
Using Netstat in Script with Sleep interval. Monitor a Port status with Netstat
Let’s suppose you want to monitor if a port is listening at a constant interval. Windows netstat command can accept sleep interval.
You can use any netstat command with a specific interval. The command will run in a loop with a Specified interval and it can be stopped with CTRL+C
netstat -abo 5|findstr 8080
here the interval is 5 seconds,
The netstat -abo command would run every 5 seconds until interrupted or stopped with CTRL+C
Various other Windows Netstat commands and their usage
netstat has more to offer and here I have listed some of the command snippets and their usage as quick gist.
Display Routing table
netstat -r
Display only UDP connections
netstat -abp udp -ab
Display only TCP connections
netstat -abp tcp -ab
Display Detailed Ethernet and Connection Usage Statistics
netstat -es
Hope it helps
Thanks
Rumen Lishkov
Follow us onFacebook orTwitter
For more practical videos and tutorials. Subscribe to our channel
Find me on Linkedin My Profile
For any Consultation or to hire us [email protected]
If you like this article. Show your Support! Buy me a Coffee.
Signup for Exclusive «Subscriber-only» Content