I’m trying to configure Windows Firewall on Server 2008 R2 to block everything except for the traffic that I add to the rule list.
I see there are three policies — public/private/domain. I’ve been making the same setting changes to each one, though I only have a single NIC and its assigned the domain policy.
In the domain policy properties I’ve set the Inbound Connections to «Block (default)» but this still let’s ICMP through. I changed it to «block all connections» and created an inbound rule that allows ICMP from all three profiles, for all programs on all interfaces but this made the firewall drop ICMP traffic even though I have an allow rule created for it.
According to this documentation the allow rules are supposed to take precidence over default rules. I want to set my default rule to block all traffic and only allow certain traffic with allow rules.
I created two custom allow rules:
- Allow inbound ICMPv4 traffic for all programs/IP addresses.
- Allow inbound ICMPv6 traffic for all programs/IP addresses.
With the Inbound connections policy set to block all connections and the above allow rules enabled it still blocks my remote pings.
How do I configure Windows Firewall to do this?
Update — It turns out I was using the wrong GUI (embarrassing). Instead of using the GUI in Administrative Tools I was using the one in Group Policy editor (which happen to look identical). There were already rules set on the firewall that I couldn’t see in the group policy editor. These rules were taking effect without me realizing it which caused my confusion. To do what I wanted I just had to set the policy to «Block (default)» (with the right tool of course). After deleting all the pre-existing rules (that I didn’t see with the group policy editor) I was able to only allow the traffic that I wanted by creating specific allow rules.
- Remove From My Forums
-
Question
-
I tried to block all the traffic and allow only my IP in windows firewall. Unfortunately its blocking all my traffic. Is there any priority level need to set in firewall ?. I don’t have much knowledge in Windows as i’m a Linux Admin.
in Linux, first rule is preferred in policy. In windows, I did the same put my allow rule first and put my Deny rule underneath.
Someone have any idea on what is the reason for this.
Thanks
Answers
-
For the built-in Windows firewall, deny rules take precedence over allow rules regardless of order.
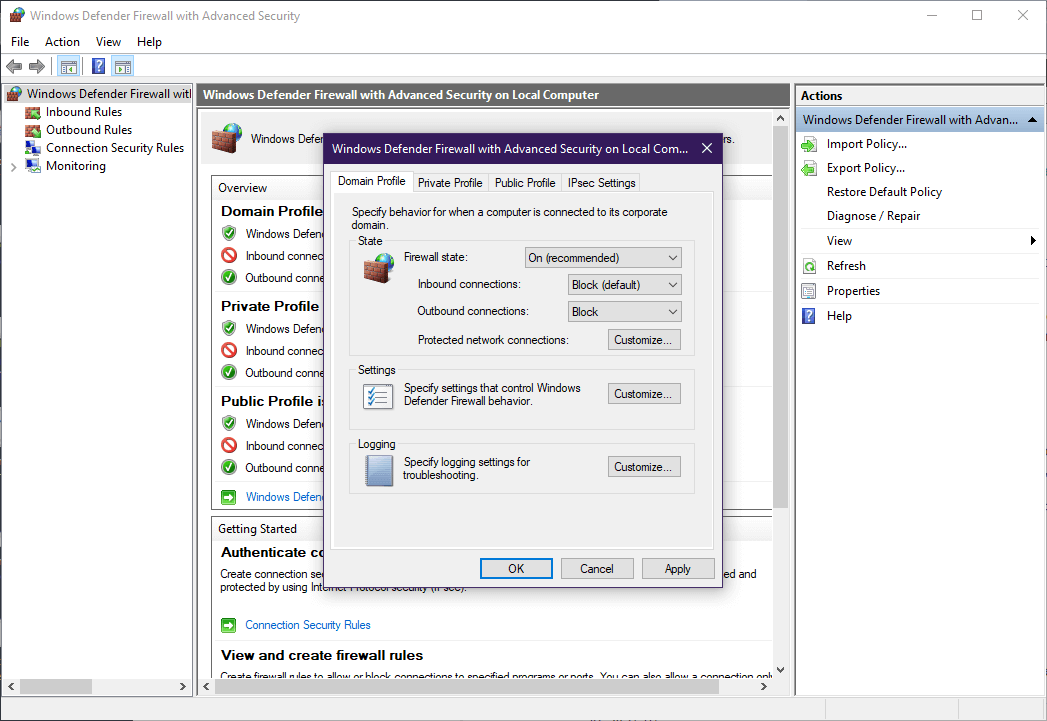
If you’re wanting to block all traffic, then you want to change the «default action» to «block»
WARNING: If you are connected remotely, this change may disconnect you from the computer.
First, add in your desired «Allow» rules and delete (or disable) your «Block» rules.
Open the «Windows Firewall with Advanced Security» snapin, select «Windows Firewall Properties», and then change the «Inbound Connections» and/or «Outbound Connections» to «Block»
-
Proposed as answer by
Wednesday, January 16, 2019 4:13 AM
-
Marked as answer by
Mark sutton2
Wednesday, January 16, 2019 4:14 AM
-
Proposed as answer by
To block all apps from the web, you need to configure the firewall
by Teodor Nechita
Eager to help those in need, Teodor writes articles daily on subjects regarding Windows, Xbox, and all things tech-related. When not working, you may usually find him either… read more
Updated on
- To block all apps except one in Windows Firewall, you need to configure it properly.
- For more advanced users, you can always use IPSec on your PC to achieve the same results.
Users have been asking on the official forums if there is a way to block all Internet traffic except one program.
While this is possible, keep in mind that Windows Firewall can prevent connection if you choose to do that. But if you’re determined to block all traffic, you can do it by following the instructions from this guide.
How we test, review and rate?
We have worked for the past 6 months on building a new review system on how we produce content. Using it, we have subsequently redone most of our articles to provide actual hands-on expertise on the guides we made.
For more details you can read how we test, review, and rate at WindowsReport.
How can I block all Internet traffic except one program?
1. Manually block processes one-by-one
- Press Windows + R, and type in control.
- Select View by (Top-right corner) to Category.
- Click on System and Security.
- Under the Windows Defender Firewall, select Allow an app through Windows Firewall.
- Deselect both boxes corresponding to each process until you finish the list.
2. Make Windows Firewall block all outgoing traffic by default
- Press Windows + R and type in control.exe, which will open the Control Panel.
- Select View by (Top-right corner) to Small icons.
- Click Administrative Tools.
- Select Windows Defender Firewall with Advanced Security.
- Click Windows Firewall Properties (on the right side).
- Click next to Outbound connections and select Block from the list.
- Confirm your changes by selecting OK.
- Delete the block all outgoing traffic rule.
This is a great way to block all Internet traffic except one program, so be sure to try it.
- Protected: How to Download Video from Facebook on PC
- Microsoft Authenticator App: Download & Install
- Is Windows 11 Faster Than Windows 10?
- How to Change the Icon Size on Windows 10
3. Use IPSec
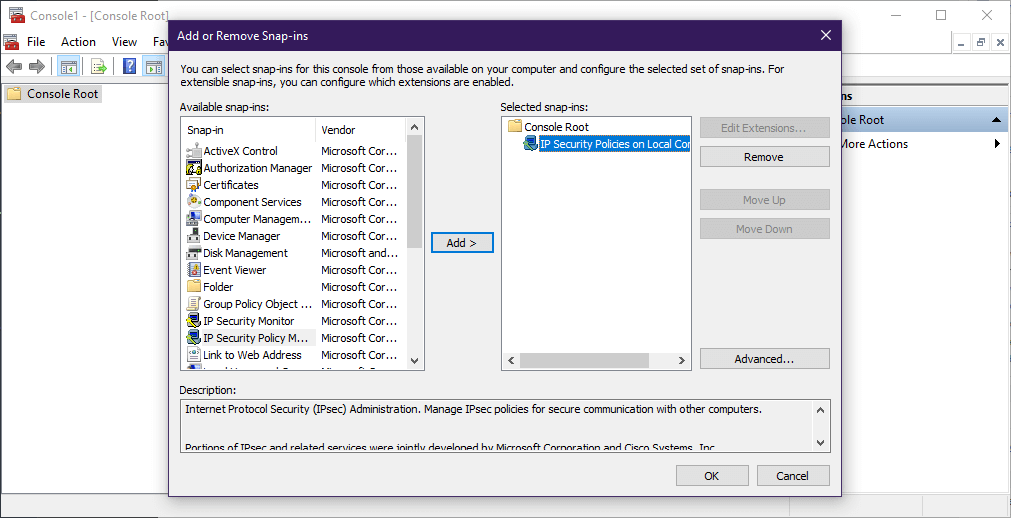
- Click Windows, type in MMC and select it from the list.
- In the new window, click File.
- Click Add/Remove Snap-In.
- Select Add the IP Security Policy Snap-In.
- Click OK.
- Right-click on the middle section and click Create IP Security Policy.
- Follow the wizard using default values and whatever names you want.
- After the first wizard, a new window will appear, When it does, click Add.
- Click Next 3 times, and then click Add.
- Name it something relevant, like Block all, and click Add.
- Go through that wizard with just default values, and click OK at the end.
- Select Block All and click Next and then Add… again.
- Follow the wizard, and give it the name Block, then select it as an action.
- Repeat Steps 9-14 selecting the proper source, destination or protocol and selecting Permit in Step 14
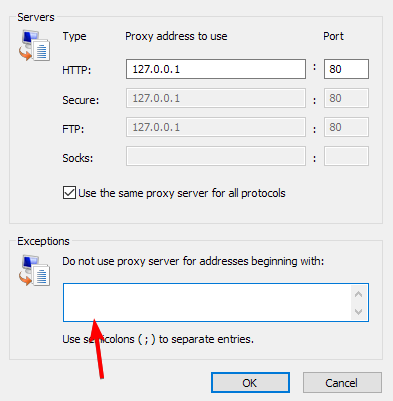
How do I block Internet access except for one site?
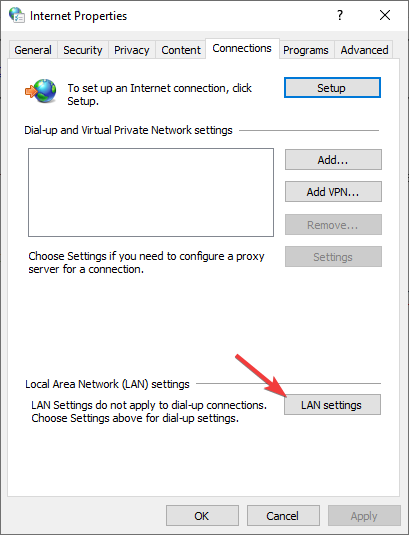
- Search for Internet Options and open it.
- Go to the Connections tab and click on LAN Settings.
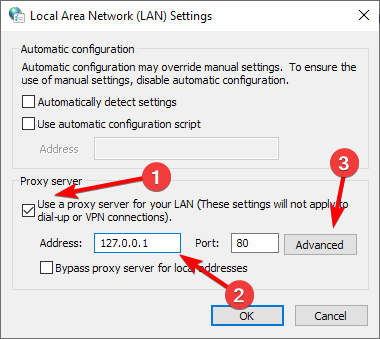
- Select use a proxy server. Set the Address to 127.0.0.1 and click on Advanced.
- Now in the exceptions field, enter the websites you want to allow.
NOTE
This is just a workaround and shouldn’t be used in professional settings.
As you can see, blocking all internet traffic except one program is somewhat simple, but that can negatively affect your PC. So, you may consider blocking Internet access for specific apps.
To learn more, we suggest reading our guide on how to block applications in Windows Firewall.
Did you find a different method to use? If so, share it with us in the comments below.
When enabled, the Windows Firewall blocks all incoming network traffic to your computer except those applications and ports you allow. Use the Windows Firewall control panel utility to manage these exceptions.
Note: It is not necessary to disable the Windows Firewall to use our software. Firewalls provide a much higher level of security to your computer than default Windows security.
We strongly recommend that you leave the firewall in place and use the mechanisms in the firewall to allow the traffic you need.
Firewall Program Exception
The installers for RPM Remote Print Manager® (RPM) and ExcelliPrint® create a program exception. The program exception allows the software to receive print jobs from your host system. You might enable the exception only for specific network types. If our software is not receiving connections, and you have already established that the host system uses the correct IP address, we recommend reviewing the firewall exception.
Adding Program Exception
- Open the Control Panel. In Category view, click System and Security.
- Beneath Windows Defender Firewall, click Check Firewall Status.
- Determine the status of the Windows Firewall for each type of active network. Network types include Domain, Private, or Public. If the Windows Firewall is off, then it is not blocking connections from your host system. It may be a good idea to add the exception in case Windows Firewall is turned on at a later time.
- Click Allow an app or feature through Windows Defender Firewall.
- Look for the RPM Remote Print Manager or ExcelliPrint exception. Enable this exception for the active network types you noted in the previous step. You may need to click Change settings to elevate the process before you can add exceptions.
- If not found, click the»Allow another app…» button. Then, click Browse in the «Add an App» dialog and locate the executable you wish to allow. By default, the RPM program is RpmSrv.exe in C:\Program Files\Brooks Internet Software\RPM for RPM and C:\Program Files\Brooks Internet Software\ExcelliPrint\EPrintSrv.exe for ExcelliPrint.
- Click Add.
- Verify the program is listed in the Allowed apps and features list. Then, click the OK button to accept the changes and dismiss the dialog.
- Click OK on the network connection’s «Properties» dialog to apply the changes.
Note: Do not make any changes to existing exceptions.
Your new firewall exceptions will take effect immediately.
Firewall Port Exceptions
Determine Ports to Allow for RPM
While this is a more involved process, you may wish to use port exceptions instead. If so, delete the auto-created program exception and follow the instructions below.
- In RPM, choose General Settings from the View menu. Click Ports.
- Note the port number for each entry in the list, especially telnet and LPD ports. Usually, this will include 515 and possibly 9100. This is because RPM uses RPC ports only for the service and UI to communicate with each other. Therefore, you should only include RPC ports if you use the UI on a remote computer.
Determine Ports to Allow for ExcelliPrint
You can configure the software to listen on multiple TCP ports simultaneously. First, you need to determine which ports your print host uses, then create an exception for each port in the Windows Firewall.
To determine the ports in use, follow these instructions.
- Open your Internet browser on the computer with ExcelliPrint installed, then access the ExcelliPrint website (http://localhost:8080). Now choose View from the Log menu.
- Select Info. Choose High from the Network Detail drop list, None from Device Detail, and Low in Application Detail. Now click the View button.
- Scan the log for messages similar to PROTOCOL port xxxx now accepting connections. You should have a single HTTP and one or more IPDS messages. You may also have an HTTPS message as well. Note each port number used in the Add Port Firewall Exceptions section.
Note: If you connect to ExcellePrint only from the local computer, adding exceptions for HTTP and HTTPS ports is unnecessary.
Adding Port Exceptions
Now that you have determined which port numbers need to be allowed, add an exception to the Windows Firewall for each port. To add the firewall exceptions, follow these instructions.
- Open the Control Panel. In Category view. Next, click System and Security. Then, beneath Windows Defender Firewall, click Check Firewall Status.
- Determine the status of the Windows Firewall. If the Windows Firewall is off, then it is not blocking connections from your host system. It may still be good to add the port exceptions if you turn the firewall on later.
- Click the «Allow another app…» button. In the «Add an App» dialog, enter a port number (i.e. ) to allow data in the Port Number field and provide a name for the exception. We suggest using a descriptive name such as the one shown in the graphic. In this case, is the protocol, and is the program requiring the exception. Repeat this step to add an exception for each port is configured to use.
- If not found, click the «Allow another app…» button. Then, click Browse in the «Add an App» dialog and locate the executable you wish to allow. By default, the RPM program is RpmSrv.exe in C:\Program Files\Brooks Internet Software\RPM for RPM and C:\Program Files\Brooks Internet Software\ExcelliPrint\EPrintSrv.exe for ExcelliPrint. Click Add.
- Verify all exceptions are listed in the Programs and Services list and press the OK button to accept the changes and dismiss the dialog. Press OK on the network connection’s «Properties» dialog to apply the changes.
Note: Do not make any changes to the existing exceptions.
Your new firewall exceptions will take effect immediately.
Brooks products use firewall exceptions
This topic first came up for us many years ago when Microsoft added a firewall to Windows XP. So naturally, we found as soon as the first user tried to run one of our products; consequently, this may be one of the longest-running pages on our website.
If you need a good software print server, please give our RPM Remote Print Manager product a try! Download the free 21-day trial and see what it can do for you. Be sure your firewall is open on ports 515 and 9100 and that you’re not already running the Microsoft TCP/IP services module.
My pick would be for you to get a desktop firewall. There’s certainly different brands out there, and if you are a novice user, you may want to read reviews on usability before buying and take a serious look at screen shots.
What you describe is called «whitelisting» — meaning that you set up 1 rule on a firewall that says «block everything» (deny all any/any where «deny» = don’t let anything through, all = all types of traffic, any/any — any source, any destination). Then you set up the «white list» — meaning the list of good destinations that you want to allow.
Quite honestly, from a practical perspective, whitelisting is the strongest, but most time consuming approach to this type of security problem. If you are coming from the experience of not knowing the following words:
- IP Address
- Port
- Protocol — plus if SSL, HTTP, FTP, HTTPS, DNS Request, and ping — are all new words to you
- DNS address
Then you are dealing in this area at a severe disadvantage. Now would be a good time to brush up on these concepts — an intro network security course would cover them, as should a book on the basics of network security. The art of figuring out how to permit what you want to permit is definitely a craft that gets learned over time. Big networks have teams of people that figure this stuff out, and sometimes these folks decide NOT to white list, because it is simply too expensive and limiting for the average user community.
If you’re coming at this as cold as it sounds, figure that you will spend 20-40 hours figuring out enough to get your basic setup done, and then 3 months of frustration as you find out from experience what you need to tune to give yourselve the internet access you need without reconfiguring your network and setting it wide open. It’s easy to think that internet sites like Skype, Facebook, Google, and others use just 1 simple destination (www.google.com), but in reality, most of the super-big sites scrape together content from all over the place, so that while allowing www.facebook.com will give you a a webpage, it’s likely that large areas of the page will show red X’s and other error messages because the traffic to certain connecting sites is still denied. This is helpful when you want to block things like game-sites, but difficult if you are new to boundary protections (a subset of security expertise including but not limited to desktop firewalls).
Another way to approach this problem would be to survey desktop firewall products and see what rulesets are delivered by default and how they are updated. This should work much like an anti-virus — that you can bank on the collective knowledge of a company or group and pay a maintenance fee to maintain the ability to download updates as the group adds expertise to the blocking rules that are used by your product. That will save you the many hours of work required to figure all this out yourself, and will get you basically decent, but not state of the art, security rules to protect a home system or other fairly standard environment.
Another possibility is that some types of devices in this range offer a «learning mode» — you can ask the device to watch your traffic for some time, and it will collect information about where you go and what you do. You can review the information and make choices from there and have the device block anything that doesn’t fit your standard pattern. I’m seeing enough Google tidbits out there to believe that this is a potential feature. That saves you the money of a subscription fee, but may increase the price of the product. It may also continue to require tweaking, as learning modes are not perfect. It’s a balance of you knowing enough about the traffic on your system to made educated choices, and the product being smart enough to help you streamline your decision making. If you and the tool fail to communicate, you will encounter time-consuming frustration…