DO NOT SUBMIT NEW ISSUES OR PULL REQUESTS
THIS REPOSITORY IS HERE FOR ARCHIVAL PURPOSES ONLY. THIS SOFTWARE RECEIVED IT’S LAST RELEASE ON 01/2019 AND LAST COMMIT ON 12/2020.
Someone has forked and continued the project here: https://github.com/bitlog2/DisableWinTracking
As with any fork of a project, we cannot verify the integrity of their code, so report any issues with their fork to THAT repository, not this one.
—————————
DisableWinTracking
A tool that I created to use some of the known methods of disabling tracking in Windows 10.
CYRILLIC LANGUAGES WARNING
ПРЕДУПРЕЖДЕНИЕ ДЛЯ КИРИЛЛИЧЕСКИХ ЯЗЫКОВ
Slavic languages: Belarusian, Bulgarian, Macedonian, Russian, Rusyn, Serbo-Croatian (for Standard Serbian, Bosnian, and Montenegrin), Ukrainian.
Славянские языки: белорусский, болгарский, македонский, русский, русинский, сербохорватский (для стандартного сербского, боснийского и черногорского), украинский.
This program cannot run correctly from a file path that contains Cyrillic characters. Make sure to run it from your root folder (usually C:/ ) so that you don’t get runtime errors.
Эта программа не может работать корректно, если в пути к файлу есть кириллические символы. Обязательно запустите его из корневой папки ( обычно C:/ ), чтобы вы не получали ошибок во время выполнения.
DOWNLOAD
DOWNLOAD EXE HERE
Note: Windows Defender may report the EXE as a trojan (Win32/Pocyx.C!cl), and may therefore prevent you from extracting the EXE to anywhere on your computer. Set up an exclusion in Settings > Update & Security > Windows Defender > Exclusions by adding the folder you intend to extract the EXE to.
How to Use
You can either:
A. Run the binary uploaded to the Release tab as an Administrator and select which options you’d like
B. Install Python and the dependencies listed below and run the script from an elevated command prompt and select which options you’d like
Silent
Either can be run with the -silent argument as of v3.1. This will perform all available options of the version you’re using.
You still need to run it as administrator.
Dependencies
This is only to run the script from source, download the exe here
- Tested on Python 3.7.2 since DisableWinTracking 3.2.4 (commit 9f1d2aa)
- wxPython
- PyWin32
- Windows 10 (Duh)
Methods Used
Telemetry
Set the AllowTelemetry string in HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\DataCollection to 0
DiagTrack Log
Clears and disables writing to the log located in C:\ProgramData\Microsoft\Diagnosis\ETLLogs\AutoLogger
Services
You can delete or disable the 2 services below:
DiagTrack(aka. Connected User Experiences and Telemetry) Diagnostics Tracking ServicedmwappushsvcWAP Push Message Routing Service
Action:
- Delete: Remove both services
- Disable: Set the
Startregistry key for both services to4(Disabled) Located atHKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\
HOSTS
Append known tracking domains to the HOSTS file located in C:\Windows\System32\drivers\etc
IP Blocking
Blocks known tracking IPs with the Windows Firewall. The rules are named TrackingIPX, replacing X with the IP numbers.
Windows Defender
Disables the following:
- Automatic Sample Submission
- Delivery Optimization Download Mode
WifiSense
Disables the following:
- Credential Share
- Open-ness
OneDrive
Runs C:\Windows\SysWOW64\OneDriveSetup.exe /uninstall (64 bit) or
C:\Windows\System32\OneDriveSetup.exe /uninstall (32 bit)
Also disables registry entries that keep the OneDrive Icon pinned to your Windows Explorer list:
Xbox DVR
Action:
- Disable: Set the
GameDVR_Enabledregistry key for both services to0(Disabled) Located atHKEY_CURRENT_USER\System\GameConfigStore - Disable: Set the
AllowGameDVRregistry key for both services to0(Disabled) Located atHKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\GameDVR
This action requires reboot computer for completely applying.
Delete Services vs Disable Services?
Selecting «Disable» will simply stop the services from being able to run.
Selecting the «Delete» choice will completely delete the tracking services.
License
Copyright (C) 10se1ucgo 2016
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program. If not, see <http://www.gnu.org/licenses/>.
Search code, repositories, users, issues, pull requests…
Provide feedback
Saved searches
Use saved searches to filter your results more quickly
Sign up
This repository has been archived by the owner on Feb 9, 2021. It is now read-only.
Archived4
Archived3
Archived2
Archived
Disable Windows 10 Tracking, version 3.1.1
This version of Disable Windows 10 Tracking pretty much fixes like, everything. I think?
Instructions
- Download dwt-x.x-cp27-win_x86.zip below
- Extract the files in any directory.
- Right click on
DisableWinTracking.exeand pressRun as administrataor - Choose any/all of the options you’d like
- Select either «Privacy» to enable the tweaks, or «Revert» to revert them.
- You can read the output in the console dialog to see if it worked.
- That’s it!
You can read the license at Info>About
RUN AS ADMINISTRATOR!
I cannot stress this enough, not running the program as an administrator will result in none of the tweaks being applied.
Changes since v3.1.0
- Fixed #316
Have fun!
Disable Windows 10 Tracking, version 3.1.0
This version of Disable Windows 10 Tracking pretty much fixes like, everything. I think?
Instructions
- Download dwt-x.x-cp27-win_x86.zip below
- Extract the files in any directory.
- Right click on
DisableWinTracking.exeand pressRun as administrataor - Choose any/all of the options you’d like
- Select either «Privacy» to enable the tweaks, or «Revert» to revert them.
- You can read the output in the console dialog to see if it worked.
- That’s it!
You can read the license at Info>About
RUN AS ADMINISTRATOR!
I cannot stress this enough, not running the program as an administrator will result in none of the tweaks being applied.
Changes since v3.0.1
- added
-silentargument to just run all available options with logging - removed (commented out) section of program for app uninstall/reinstall. resized form. it’s totally broken.
- removed windows defender option for now. it’s totally broken. thank microsoft for protecting the keys
- fixed DiagTrack option with code rewrite. it’s ugly, but it works. tried to fix original first.
Have fun!
Disable Windows 10 Tracking, version 3.0.1
This version of Disable Windows 10 Tracking pretty much fixes like, everything. I think?
Instructions
- Download dwt-x.x-cp27-win_x86.zip below
- Extract the files in any directory.
- Right click on
DisableWinTracking.exeand pressRun as administrataor - Choose any/all of the options you’d like
- Select either «Privacy» to enable the tweaks, or «Revert» to revert them.
- You can read the output in the console dialog to see if it worked.
- That’s it!
You can read the license at Info>About
RUN AS ADMINISTRATOR!
I cannot stress this enough, not running the program as an administrator will result in none of the tweaks being applied.
Changes since v3.0
- Reverted to Python 2 to fix PyInstaller errors like this one:
- Fixed
Failed to execute script dwton some systems. [untested]
- Fixed
- Fixed WindowsError
The handle is invalid. - Added «Sway» to list of uninstallable apps.
- File size reduced from ~9 MB to ~6 MB.
Have fun!
Disable Windows 10 Tracking
_PRE-RELEASE: Not tested thoroughly._
_EVERYTHING IS BROKEN DON’T DOWNLOAD THIS DAMMIT_
Instructions
- Download dwt-x.x-cp35-win_x86.zip below
- Extract the files in any directory.
- Right click on
DisableWinTracking.exeand pressRun as administrataor - Choose any/all of the options you’d like
- Select either «Privacy» to enable the tweaks, or «Revert» to revert them.
- You can read the output in the console dialog to see if it worked.
- That’s it!
You can read the license at Info>About
RUN AS ADMINISTRATOR!
I cannot stress this enough, not running the program as an administrator will result in none of the tweaks being applied.
Changes since v2.5.1
- Everything rewritten! Many things borrowed from my other program, pyjam.
- Split Windows Defender and WifiSense into two options
- GUI should now scale properly (hopefully)
- Everything is less terrible!
- Code is somewhat cleaner!
- Fixed DiagTrack service
- Settings now works completely
- Added license list
- Updated copyright year
- License changed to GPLv3
- Loads of bugs fixed.
Have fun!
Disable Windows 10 Tracking
Instructions
- Download DisableWinTracking.exe below
- Open it. It should request for administrator privileges.
- Choose any/all of the options you’d like
- Select either «Privacy» to enable the tweaks, or «Revert» to revert them.
- You can read the output in the console dialog to see if it worked.
- That’s it!
You can read the license at Info>About
RUN AS ADMINISTRATOR!
I cannot stress this enough, not running the program as an administrator will result in none of the tweaks being applied.
Changes since v2.5
- Settings — Customize which domains should be blocked. IP blocking settings will come soon.
Have fun!
Disable Windows 10 Tracking
GitHub, I released this on 9/21/15 not 9/9/15!
Instructions
- Download DisableWinTracking.exe below
- Open it. It should request for administrator privileges.
- Choose any/all of the options you’d like
- Press «Get privacy!»
- You can read the output in the console dialog to see if it worked.
- That’s it!
If you ever need to revert
- Download DisableWinTracking.exe below
- Open it. It should request for administrator privileges.
- Choose any/all of the options you’d like
- Press «Revert»
- You can read the output in the console dialog to see if it worked.
- That’s it!
You can read the license at Info>About
RUN AS ADMINISTRATOR!
I cannot stress this enough, not running the program as an administrator will result in none of the tweaks being applied.
Changes since v2.4.3
- Windows 10 default app removal
Have fun!
Время на прочтение
10 мин
Количество просмотров 346K
Микрософт с помощью пасьянса и косынки учила пользователей пользоваться мышью,
теперь с помощью windows 10 учит читать лицензионное соглашение.
После выхода windows 10 сразу появились сообщения о сборе информации о действиях пользователей и много обсуждений, что делать. Достаточно быстро пользователи составили список основных серверов, собирающих информацию и попытались их заблокировать через файл hosts. Но скептики сразу выдвинули здравое предположение, что MS мог предусмотреть этот метод и некоторые адреса прописать в коде. Тем более, что MS всегда может актуализировать адреса серверов через windows update.
В нашей компании начали появляться первые пользователи windows 10, и мы решили опробовать блокировку передачи телеметрии через встроенный windows firewall.
Итак, собран простой тестовый стенд:
Два ноутбука, на один из них ставим Windows 10 и подключим его к интернету через второй ноутбук, используя internet sharing. На втором ноутбуке, который работает как NAT роутер, поставим Wireshark и определим исходящий трафик на сервера MS с первого ноутбука.
Что получилось:
- Да, Windows 10 отправляет данные;
- Список серверов почти полностью совпал с указанным в статье habrahabr.ru/company/pt/blog/264763 и forums.untangle.com/web-filter/35894-blocking-windows-10-spying-telemetry.html
- Встроенный Windows Firewall полностью блокирует передачу данных на эти узлы.
Правила для Firewall
После того как мы получили список IP и убедились в эффективности их блокировки, можно, с помощью Powershell скрипта, внести их в настройки.
Для добавления правила в Firewall необходимо выполнить следующую команду (в качестве примера возьмем сервер «watson.telemetry.microsoft.com»):
netsh advfirewall firewall add rule name="telemetry_watson.telemetry.microsoft.com" dir=out action=block remoteip=65.55.252.43,65.52.108.29 enable=yes
Где:
name – имя правила и по совместимости название сервера Microsoft;
dir = out – параметр указывающий, что правило соответствует только исходящему сетевому трафику;
action=block – сетевые пакеты, указанные в этом правиле, будут отбрасываются firewall;
remoteip – IP-адрес получателя области исходящего сетевого пакета;
enable=yes – указывает на то, что правило в настоящее время включено.
Аналогично этому будут прописаны и другие правила. В итоге, скрипт будет иметь примерно следующий вид:
Firewall rules
Set-NetFirewallProfile -all
netsh advfirewall firewall add rule name=«telemetry_vortex.data.microsoft.com» dir=out action=block remoteip=191.232.139.254 enable=yes
netsh advfirewall firewall add rule name=«telemetry_telecommand.telemetry.microsoft.com» dir=out action=block remoteip=65.55.252.92 enable=yes
netsh advfirewall firewall add rule name=«telemetry_sqm.telemetry.microsoft.com» dir=out action=block remoteip=65.55.252.93 enable=yes
netsh advfirewall firewall add rule name=«telemetry_watson.telemetry.microsoft.com» dir=out action=block remoteip=65.55.252.43,65.52.108.29 enable=yes
netsh advfirewall firewall add rule name=«telemetry_redir.metaservices.microsoft.com» dir=out action=block remoteip=194.44.4.200,194.44.4.208 enable=yes
netsh advfirewall firewall add rule name=«telemetry_choice.microsoft.com» dir=out action=block remoteip=157.56.91.77 enable=yes
netsh advfirewall firewall add rule name=«telemetry_df.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.7 enable=yes
netsh advfirewall firewall add rule name=«telemetry_reports.wes.df.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.91 enable=yes
netsh advfirewall firewall add rule name=«telemetry_wes.df.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.93 enable=yes
netsh advfirewall firewall add rule name=«telemetry_services.wes.df.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.92 enable=yes
netsh advfirewall firewall add rule name=«telemetry_sqm.df.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.94 enable=yes
netsh advfirewall firewall add rule name=«telemetry_telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.9 enable=yes
netsh advfirewall firewall add rule name=«telemetry_watson.ppe.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.11 enable=yes
netsh advfirewall firewall add rule name=«telemetry_telemetry.appex.bing.net» dir=out action=block remoteip=168.63.108.233 enable=yes
netsh advfirewall firewall add rule name=«telemetry_telemetry.urs.microsoft.com» dir=out action=block remoteip=157.56.74.250 enable=yes
netsh advfirewall firewall add rule name=«telemetry_settings-sandbox.data.microsoft.com» dir=out action=block remoteip=111.221.29.177 enable=yes
netsh advfirewall firewall add rule name=«telemetry_vortex-sandbox.data.microsoft.com» dir=out action=block remoteip=64.4.54.32 enable=yes
netsh advfirewall firewall add rule name=«telemetry_survey.watson.microsoft.com» dir=out action=block remoteip=207.68.166.254 enable=yes
netsh advfirewall firewall add rule name=«telemetry_watson.live.com» dir=out action=block remoteip=207.46.223.94 enable=yes
netsh advfirewall firewall add rule name=«telemetry_watson.microsoft.com» dir=out action=block remoteip=65.55.252.71 enable=yes
netsh advfirewall firewall add rule name=«telemetry_statsfe2.ws.microsoft.com» dir=out action=block remoteip=64.4.54.22 enable=yes
netsh advfirewall firewall add rule name=«telemetry_corpext.msitadfs.glbdns2.microsoft.com» dir=out action=block remoteip=131.107.113.238 enable=yes
netsh advfirewall firewall add rule name=«telemetry_compatexchange.cloudapp.net» dir=out action=block remoteip=23.99.10.11 enable=yes
netsh advfirewall firewall add rule name=«telemetry_cs1.wpc.v0cdn.net» dir=out action=block remoteip=68.232.34.200 enable=yes
netsh advfirewall firewall add rule name=«telemetry_a-0001.a-msedge.net» dir=out action=block remoteip=204.79.197.200 enable=yes
netsh advfirewall firewall add rule name=«telemetry_statsfe2.update.microsoft.com.akadns.net» dir=out action=block remoteip=64.4.54.22 enable=yes
netsh advfirewall firewall add rule name=«telemetry_sls.update.microsoft.com.akadns.net» dir=out action=block remoteip=157.56.77.139 enable=yes
netsh advfirewall firewall add rule name=«telemetry_fe2.update.microsoft.com.akadns.net» dir=out action=block remoteip=134.170.58.121,134.170.58.123,134.170.53.29,66.119.144.190,134.170.58.189,134.170.58.118,134.170.53.30,134.170.51.190 enable=yes
netsh advfirewall firewall add rule name=«telemetry_diagnostics.support.microsoft.com» dir=out action=block remoteip=157.56.121.89 enable=yes
netsh advfirewall firewall add rule name=«telemetry_corp.sts.microsoft.com» dir=out action=block remoteip=131.107.113.238 enable=yes
netsh advfirewall firewall add rule name=«telemetry_statsfe1.ws.microsoft.com» dir=out action=block remoteip=134.170.115.60 enable=yes
netsh advfirewall firewall add rule name=«telemetry_pre.footprintpredict.com» dir=out action=block remoteip=204.79.197.200 enable=yes
netsh advfirewall firewall add rule name=«telemetry_i1.services.social.microsoft.com» dir=out action=block remoteip=104.82.22.249 enable=yes
netsh advfirewall firewall add rule name=«telemetry_feedback.windows.com» dir=out action=block remoteip=134.170.185.70 enable=yes
netsh advfirewall firewall add rule name=«telemetry_feedback.microsoft-hohm.com» dir=out action=block remoteip=64.4.6.100,65.55.39.10 enable=yes
netsh advfirewall firewall add rule name=«telemetry_feedback.search.microsoft.com» dir=out action=block remoteip=157.55.129.21 enable=yes
netsh advfirewall firewall add rule name=«telemetry_rad.msn.com» dir=out action=block remoteip=207.46.194.25 enable=yes
netsh advfirewall firewall add rule name=«telemetry_preview.msn.com» dir=out action=block remoteip=23.102.21.4 enable=yes
netsh advfirewall firewall add rule name=«telemetry_dart.l.doubleclick.net» dir=out action=block remoteip=173.194.113.220,173.194.113.219,216.58.209.166 enable=yes
netsh advfirewall firewall add rule name=«telemetry_ads.msn.com» dir=out action=block remoteip=157.56.91.82,157.56.23.91,104.82.14.146,207.123.56.252,185.13.160.61,8.254.209.254 enable=yes
netsh advfirewall firewall add rule name=«telemetry_a.ads1.msn.com» dir=out action=block remoteip=198.78.208.254,185.13.160.61 enable=yes
netsh advfirewall firewall add rule name=«telemetry_global.msads.net.c.footprint.net» dir=out action=block remoteip=185.13.160.61,8.254.209.254,207.123.56.252 enable=yes
netsh advfirewall firewall add rule name=«telemetry_az361816.vo.msecnd.net» dir=out action=block remoteip=68.232.34.200 enable=yes
netsh advfirewall firewall add rule name=«telemetry_oca.telemetry.microsoft.com.nsatc.net» dir=out action=block remoteip=65.55.252.63 enable=yes
netsh advfirewall firewall add rule name=«telemetry_reports.wes.df.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.91 enable=yes
netsh advfirewall firewall add rule name=«telemetry_ssw.live.com» dir=out action=block remoteip=207.46.101.29 enable=yes
netsh advfirewall firewall add rule name=«telemetry_msnbot-65-55-108-23.search.msn.com» dir=out action=block remoteip=65.55.108.23 enable=yes
netsh advfirewall firewall add rule name=«telemetry_a23-218-212-69.deploy.static.akamaitechnologies.com» dir=out action=block remoteip=23.218.212.69 enable=yes
Выполнение созданного скрипта
Чтобы не проходить долгий путь по запуску этого power shell скрипта с правами администратора, проще создать .bat файл и запустить его. UAC сам запросит подтверждение прав.
@echo off
cls
echo Telemetry
echo Rules of Firewall
echo.
echo press any key to continue...
pause > NUL
echo Rules of Firewall
echo.
PowerShell -NoProfile -ExecutionPolicy Bypass -Command "& {Start-Process PowerShell -ArgumentList '-NoProfile -ExecutionPolicy Bypass -File ""%~dp0.\ms_new.ps1""' -Verb RunAs}"
echo Rules included in Firewall...
echo.
pause
Где ms_new.ps1 – имя созданного файла с power shell командами.
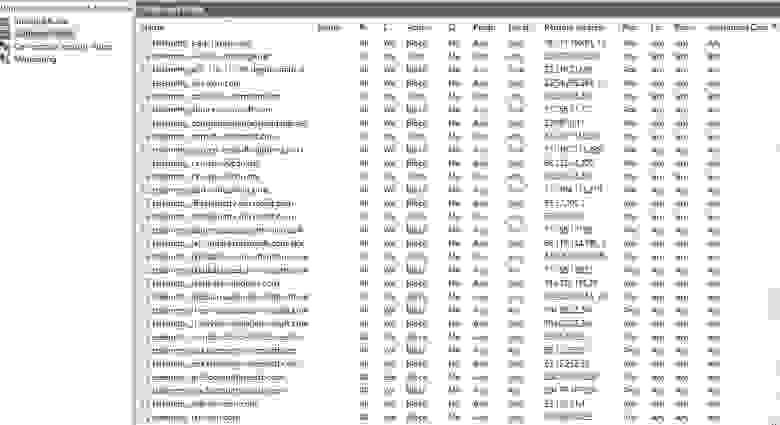
После этого, добавленные правила будут отображаться в Windows Firewall, как на скриншоте ниже:
И, дополнительно, информация, не относящиеся к firewall, но относящаяся к сбору телеметрии
Windows 7/8/8.1
Также стоит отметить, что пользователи ОС Windows 7/8/8.1 получили обновления, которые расширяют возможности системы по сбору и отправке телеметрических данных. Соответственно, к этим пользователям также можно применить рекомендации, представленные в этой статье, или удалить обновления habrahabr.ru/post/265283.
Key logger
Надо отключить «DiagTrack» (сбор данных в компонентах Windows) и «dmwappushservice» (cлужба маршрутизации push-сообщений WAP). Для этого запускаем командную строку от имени администратора и отключаем службы:
sc stop DiagTrack
sc stop dmwappushserviceИли же вообще их удаляем:
sc delete DiagTrack
sc delete dmwappushservice
Планировщик отправки телеметрии
В консоли Taskschd.msc надо запретить задания:
Заголовок спойлера
REM *** Task that collects data for SmartScreen in Windows ***
schtasks /Change /TN "Microsoft\Windows\AppID\SmartScreenSpecific" /Disable
REM *** Collects program telemetry information if opted-in to the Microsoft Customer Experience Improvement Program ***
schtasks /Change /TN "Microsoft\Windows\Application Experience\ProgramDataUpdater" /Disable
REM *** Collects program telemetry information if opted-in to the Microsoft Customer Experience Improvement Program ***
schtasks /Change /TN "Microsoft\Windows\Application Experience\Microsoft Compatibility Appraiser" /Disable
REM *** Aggregates and uploads Application Telemetry information if opted-in to the Microsoft Customer Experience Improvement Program ***
schtasks /Change /TN "Microsoft\Windows\Application Experience\AitAgent" /Disable
REM *** This task collects and uploads autochk SQM data if opted-in to the Microsoft Customer Experience Improvement Program ***
schtasks /Change /TN "Microsoft\Windows\Autochk\Proxy" /Disable
REM *** If the user has consented to participate in the Windows Customer Experience Improvement Program, this job collects and sends usage data to Microsoft ***
schtasks /Change /TN "Microsoft\Windows\Customer Experience Improvement Program\Consolidator" /Disable
REM *** The Kernel CEIP (Customer Experience Improvement Program) task collects additional information about the system and sends this data to Microsoft. ***
REM *** If the user has not consented to participate in Windows CEIP, this task does nothing ***
schtasks /Change /TN "Microsoft\Windows\Customer Experience Improvement Program\KernelCeipTask" /Disable
REM *** The Bluetooth CEIP (Customer Experience Improvement Program) task collects Bluetooth related statistics and information about your machine and sends it to Microsoft ***
REM *** The information received is used to help improve the reliability, stability, and overall functionality of Bluetooth in Windows ***
REM *** If the user has not consented to participate in Windows CEIP, this task does not do anything.***
schtasks /Change /TN "Microsoft\Windows\Customer Experience Improvement Program\BthSQM" /Disable
REM *** Create Object Task ***
schtasks /Change /TN "Microsoft\Windows\CloudExperienceHost\CreateObjectTask" /Disable
REM *** The Windows Disk Diagnostic reports general disk and system information to Microsoft for users participating in the Customer Experience Program ***
schtasks /Change /TN "Microsoft\Windows\DiskDiagnostic\Microsoft-Windows-DiskDiagnosticDataCollector" /Disable
REM *** Measures a system's performance and capabilities ***
schtasks /Change /TN "Microsoft\Windows\Maintenance\WinSAT" /Disable
REM *** Network information collector ***
schtasks /Change /TN "Microsoft\Windows\NetTrace\GatherNetworkInfo" /Disable
REM *** Initializes Family Safety monitoring and enforcement ***
schtasks /Change /TN "Microsoft\Windows\Shell\FamilySafetyMonitor" /Disable
REM *** Synchronizes the latest settings with the Family Safety website ***
schtasks /Change /TN "Microsoft\Windows\Shell\FamilySafetyRefresh" /Disable
REM *** SQM (Software Quality Management) ***
schtasks /Change /TN "Microsoft\Windows\IME\SQM data sender" /Disable
REM *** This task initiates the background task for Office Telemetry Agent, which scans and uploads usage and error information for Office solutions ***
schtasks /Change /TN "Microsoft\Office\OfficeTelemetryAgentFallBack" /Disable
REM *** This task initiates Office Telemetry Agent, which scans and uploads usage and error information for Office solutions when a user logs on to the computer ***
schtasks /Change /TN "Microsoft\Office\OfficeTelemetryAgentLogOn" /Disable
также подозриетльные задачи в планировщике, рекомендую отключить:
Заголовок спойлера
REM *** Scans startup entries and raises notification to the user if there are too many startup entries ***
schtasks /Change /TN "Microsoft\Windows\Application Experience\StartupAppTask" /Disable
REM *** Protects user files from accidental loss by copying them to a backup location when the system is unattended ***
schtasks /Change /TN "Microsoft\Windows\FileHistory\File History (maintenance mode)" /Disable
REM *** This task gathers information about the Trusted Platform Module (TPM), Secure Boot, and Measured Boot ***
schtasks /Change /TN "Microsoft\Windows\PI\Sqm-Tasks" /Disable
REM *** This task analyzes the system looking for conditions that may cause high energy use ***
schtasks /Change /TN "Microsoft\Windows\Power Efficiency Diagnostics\AnalyzeSystem" /Disable
Все вышесказанное не 100% панацея, но одно из компромиссных решений.
Мы будем обновлять в этой статье список серверов и PS скрипт для них.
update 1: Обновили список планировщика задач.
Как фаерволом защитится от зловредов, можно прочитать в моей статье:
Простой, но надежный способ защитить свой компьютер от вирусов и троянов.
C уважением коллектив компании Servilon.ru Servilon.com
Get the Reddit app
Scan this QR code to download the app now
Or check it out in the app stores
Go to programming
r/programming
r/programming
Computer Programming
Members
Online
•
by
sqlplex
GitHub project for disabling W10 spying/telemetry. Anyone checked out the code?


github.com
Top Posts
-
Reddit
reReddit: Top posts of November 4, 2015
-
Reddit
reReddit: Top posts of November 2015
-
Reddit
reReddit: Top posts of 2015