Disclaimer:
Oracle and Java are registered trademarks of Oracle and/or its affiliates
Testpreptraining material do not contain actual actual Oracle Exam Questions or material.
Testpreptraining doesn’t offer Real Microsoft Exam Questions.
Microsoft®, Azure®, Windows®, Windows Vista®, and the Windows logo are registered trademarks of Microsoft Corporation
Testpreptraining Materials do not contain actual questions and answers from Cisco’s Certification Exams. The brand Cisco is a registered trademark of CISCO, Inc
Testpreptraining Materials do not contain actual questions and answers from CompTIA’s Certification Exams. The brand CompTIA is a registered trademark of CompTIA, Inc
CFA Institute does not endorse, promote or warrant the accuracy or quality of these questions. CFA® and Chartered Financial Analyst® are registered trademarks owned by CFA Institute
Testpreptraining.com does not offer exam dumps or questions from actual exams. We offer learning material and practice tests created by subject matter experts to assist and help learners prepare for those exams. All certification brands used on the website are owned by the respective brand owners. Testpreptraining does not own or claim any ownership on any of the brands.
Время на прочтение
6 мин
Количество просмотров 23K
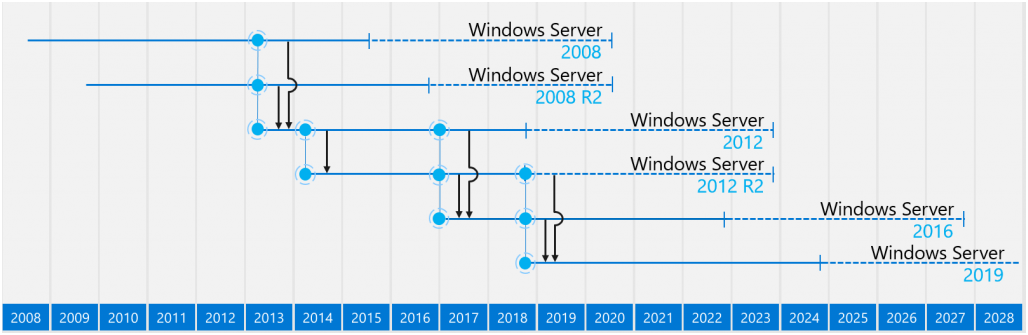
Привет, Хабр! 14/01/2020 приближается и эта дата знаменует окончание расширенной поддержки для Windows Server 2008 R2, и если вы все еще используете Windows Server 2008 R2, вам следует задуматься про миграцию на более актуальную платформу.
Под катом находится небольшое сравнение потребляемых ресурсов старой и новых платформ Windows Server — роль RDSH. В первую очередь меня интересовала возможность продолжить использование уже имеющихся в наличии серверов HP G6/G7 под управлением VMware Vsphere 5.5.
Информация о Windows Server Lifecycle доступна по этой ссылке Search Product Lifecycle.
У меня будет два тестовых стенда:
- HP DL120 G7, 1*cpu Intel Xeon E3-1240
- HP ML350 G6, 2*cpu Intel Xeon E5620
Сервера будут работать под управлением VMware ESXi 5.5, образ VMware-ESXi-5.5.0-Update1-1746018-HP-5.75.4-Dec2014. Я также пробовал использовать образ VMware-ESXi-5.5.0-Update3-3116895-HP-550.9.4.26-Nov2015, но на полученные результаты это не влияет.
А вот образ VMware-ESXi-5.5.0-Update2-2403361-HP-550.9.2.40.2-Sep2015 дает искаженные результаты, по какой-то причине статистика которую показывает сервер отличается от реальной в два раза. С этим образом максимум что показывает сервер это 50 процентов нагрузки на процессор, видимо какой-то баг. Я вначале обрадовался когда получил первые результаты, но потом понял что что-то не так…
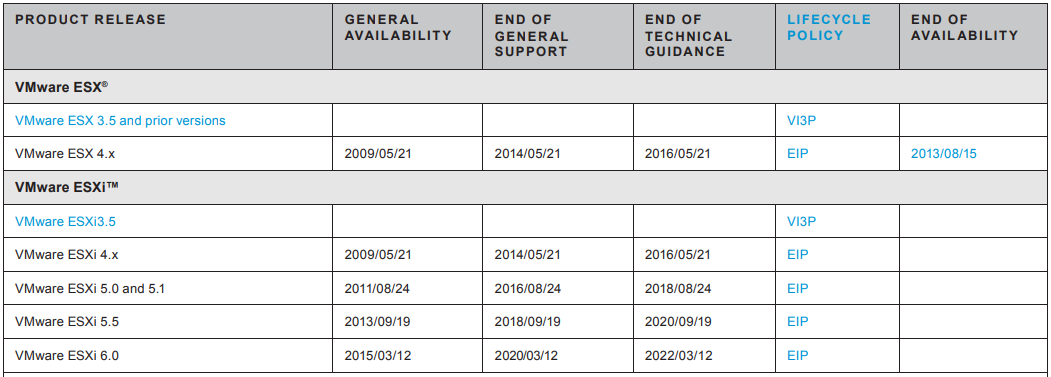
Также следует упомянуть, что поддержка VMware Vsphere 5.5 тоже не вечная, и платформа уже не актуальна, и стоит задуматься про обновление. Информация про VMware Lifecycle доступна в данном документе VMware Lifecycle Product Matrix.
И не стоит забывать про VMware Compatibility Guide. Если говорить про сервер HP DL120 G7, этот сервер никогда не присутствовал в матрицах совместимости, а вот на сервер HP ML350 G6 официально допускается установка ESXi 5.5 U3.
Гостевые ОС
Информация про совместимость ESXi с гостевыми ОС также доступна в VMware Compatibility Guide.
ESXi 5.5 U3 позволяет в качестве гостевой ОС установить Windows Server 2016, и даже версии 5.5 будет для этого достаточно. А вот для установки Windows Server 2019 понадобится ESXi версии 6+, но это никак не помешает мне протестировать задуманное.
У меня будут следующие тестовые VM: WS2008R2SP1, WS2012R2, WS2016 и WS2019.
На все VM установлены агенты VMware Tools 5.5.0-10.2.5.8068406. Установлены все обновления от Microsoft за май 2019 и даже какие-то за июнь 2019, после чего служба обновления была отключена.
Для моих тестов я выполнил минимальный тюнинг, хочу чтобы все работало с максимально стандартными параметрами. Для этого я буду использовать локальные групповые политики, немного подробней про это я напишу в конце.
- отключил «desktop composition»
- разрешил редирект звука и видео
- включил RemoteFX для WS2008R2SP1 и клиентов WS2008R2SP1
- отключил сглаживание шрифтов
- ограничил разрядность цветовой палитры на значении 32
- ограничил количество мониторов на значении 1
Что бы кодек RemoteFX начал работать на WS2008R2SP1 необходимо установить роль RDSH, для более новых версий этого можно не делать. Возможно, RemoteFX используется на WS2008R2SP1 без установки RDSH, но в логах отсутствуют события про активацию этого кодека.
Тест 1
В качестве теста я буду использовать ролик на YouTube с разрешением 720p, What’s new in Remote Desktop Services on Windows Server 2019 — BRK2242.
На каждом из серверов я поочередно открою одну rdp сессию и тестовый ролик в Chrome (версия 75.0.3770.80(64bit)).
В этом тесте в качестве клиента будет использоваться тонкий клиент HP t510 под управлением ОС HP ThinOS 4.4 и с пакетом Freerdp-1.1hp10d-all-4.4-x86-SQ. Данный аппарат подключен к монитору с разрешением Full HD, и профиль тонкого клиента был сброшен до заводского.
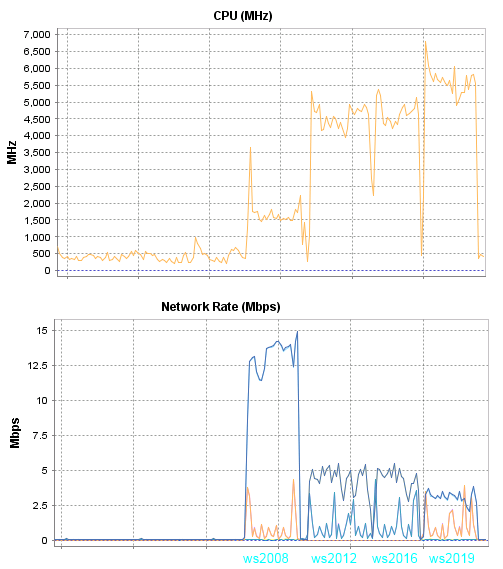
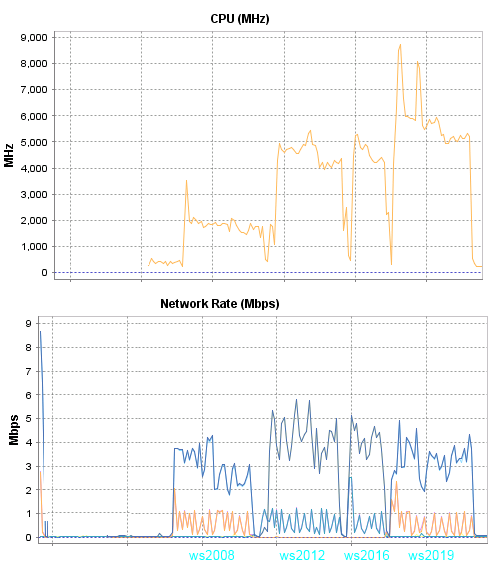
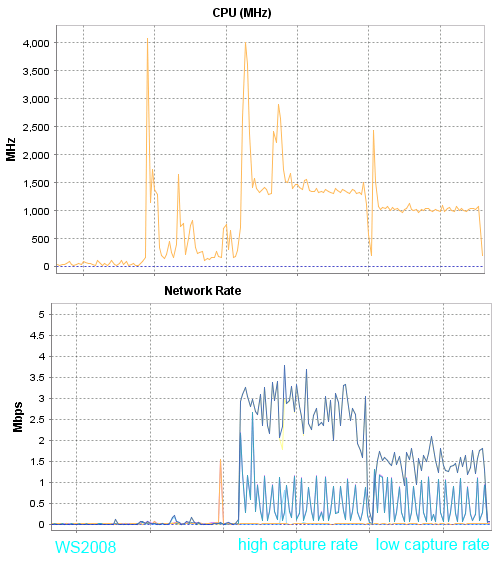
Графики я снимал с хоста, все первые тесты будут выполняться на сервере HP DL120G7.
Комментарии к результатам первого теста:
В данном тесте ws2008 потребляет в три раза меньше процессорных ресурсов, но при этом в три раза больше трафика чем другие участники теста.
При током трафике, в один гигабит можно поместить 66 сессий, а вот переход на новую версию сервера вероятно уменьшит в три раза количество пользователей которые смогу работать при таком потреблении процессора.
Визуально картинка в данной презентации приемлема на всех версиях Windows Server. Конечно если запустить что-то более динамичное, то более новые версии серверов показывают картинку заметно лучше. Предположу что это связано с количество кадров, больше кадров = плавное воспроизведение = больше нагрузка на процессор.
Тест 2
Сценарий для второго теста остается без изменений, за исключением использования Firefox (версия 67.0.2 (64bit))
Комментарии к результатам второго теста:
Firefox в паре с ws2019 показывает не плохой результат, потребляет немного больше процессора и заметно меньше трафика чем ws2008.
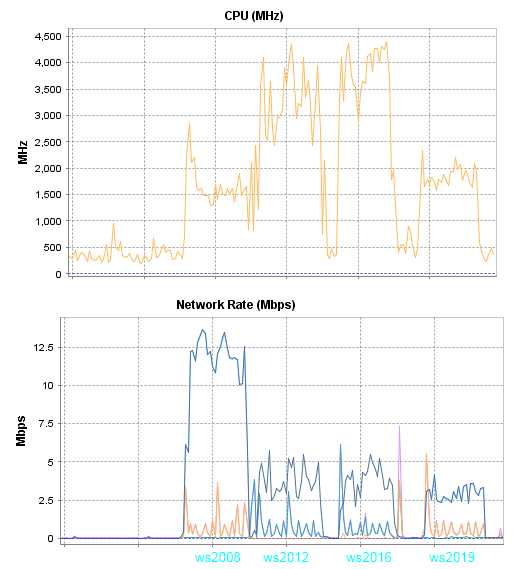
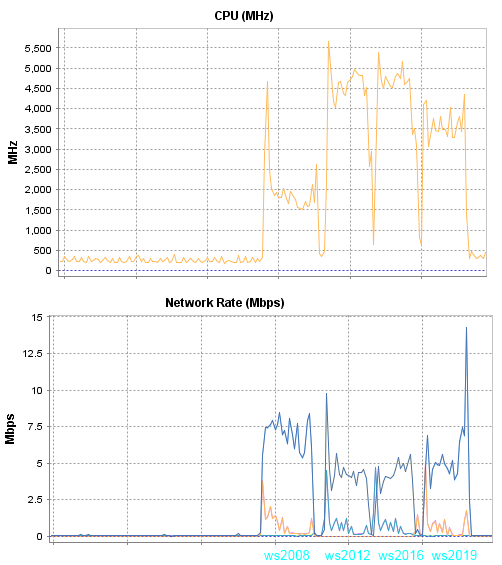
Тест 3
В этом тесте будет использоваться Chrome, но клиентом уже будет выступать ноутбук с Windows 10 1903, ноутбук подключен к монитору с разрешением FullHD.
Комментарии к результатам третьего теста:
В случаи с ws2008 потребляется меньше трафика, другие изменения не значительны…
Также я заметил что Chrome при отображении на фоне ролика прогресс бара потребляет на 1000 мгц больше, а вот в Firefox такого эффекта я не заметил, и прорисовка прогресс бара на количество потребляемых ресурсов не влияет.
Тест 4
Ноутбук с Windows 10 в паре с Firefox
Комментарии к результатам четвертого теста:
В такой комбинации сервер-клиент-браузер, ws2019+Firefox потребляет меньше ресурсов чем с Chrome, но стал потреблять заметно больше процессора если сравнить с результатами Теста 2.
В случаях с ws2012 и ws2016 результаты всех проведенных тестов получаются заметно ровнее, нету такого разброса как у ws2019.
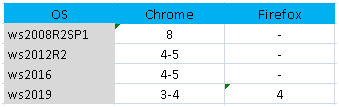
Тест 5
Данный тест заключен в запуске максимального количества rdp сессий и запуска презентации в каждой из сессии. В этом мне будет помогать Remote Desktop Connection Manager, RDCM будет запущен на ноутбуке с Windows 10.
Разрешение сессий пришлось уменьшить до 1440*900. В качестве результатов просто приведу сводную таблицу:
Комментарии к результатам пятого теста:
Неожиданно, 2019 сервер показал результаты хуже чем ws2012 и ws2016. Сервер 2008 смог открыть 8 сессий в то время как сервера 2012/2016 могут открыть 4 сессии, и 5-я поднимает нагрузку до 100%. Сервер 2019 смог работать максимум с 4-мя сессиями.
Firefox не является для меня приоритетным браузером, и поэтому я запускал его только в ws2019 чтобы убедиться в полученных цифрах.
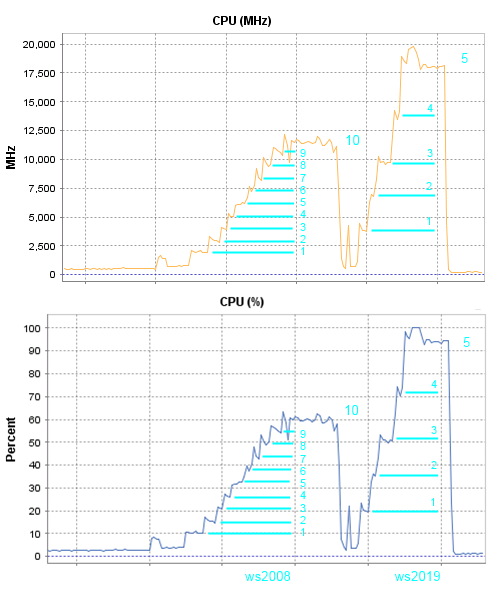
Тест 6
В этом тесте в игру вступает сервер HP ML350G6 с двумя процессорами Е5620, тестировать буду только 2008 и 2019 сервера. Тест прежний, запуск максимального количества сессий, использоваться будет только Chrome.
Комментарии к результатам шестого теста:
Для запуска 10 сессий на сервере 2008 понадобилось 60 процентов процессорных ресурсов, а для запуска всего 5 сессий на 2019 сервере нужно больше 90 процентов.
Заключительная часть — Тюнинг
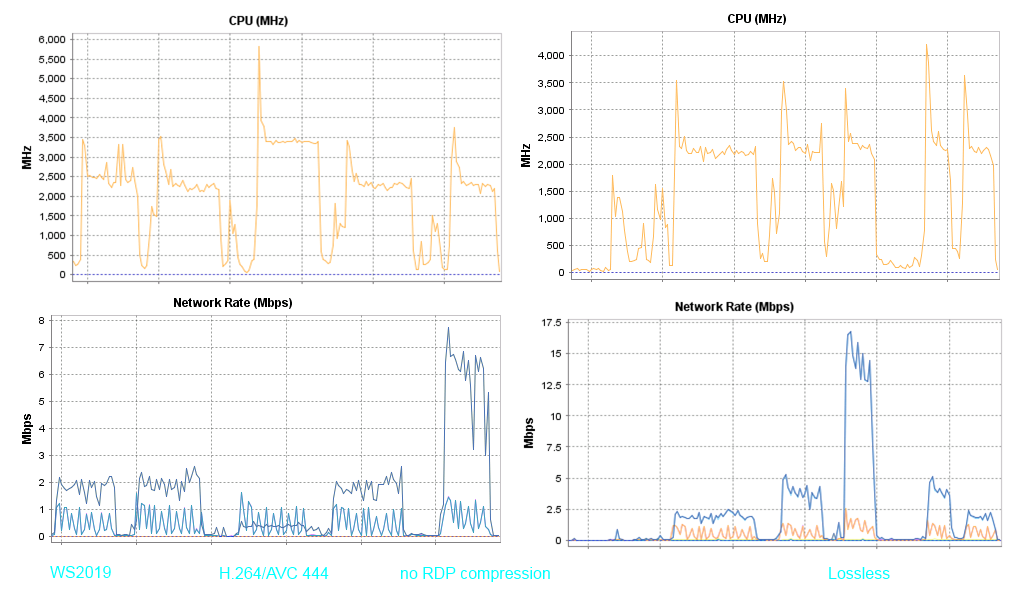
Все тестовые VM я вернул на сервер HP DL120G7 и в качестве клиента использовал ноутбук с Windows 10 и его штатный экран с разрешением 1366*768.
К сожалению попытки уменьшить потребление процессора я бы не назвал успешными, но сказать что результатов нету тоже нельзя. Вот список всех доступных параметров локальных групповых политик которые можно использовать для тюнига:
В Windows Server 2008R2 параметры «Optimize visual experience when using RemoteFX» позволяют управлять качеством картинки и количеством кадров, и это дает заметный результат. Уменьшение количества кадров снижает нагрузку на процессор и сеть. Для Windows Server 2019 эти параметры не работают.
Качеством картинки в Windows Server 2019 можно управлять параметром «Configure image quality for RemoteFX Adaptive Graphics», а вот изменить количество кадров нечем, или я такой параметр не нашел.
Я пробовал различные комбинации параметров, но заметные изменения в результатах я смог получить только в нескольких случаях. И самое интересное то что можно заметить изменения в трафике но при этом нагрузка на процессор меняется слабо.
— Приоритезация H.264/AVC 444 увеличила нагрузку на процессор но при это трафик заметно снизился с 2х до 1 мегабита.
This policy setting prioritizes the H.264/AVC 444 graphics mode for non-RemoteFX vGPU scenarios. When you use this setting on the RDP server, the server will use H.264/AVC 444 as the codec in an RDP 10 connection where both the client and server can use H.264/AVC 444.
— Отключение компрессии RDP не снизило загрузку на процессор, но при этом трафик увеличился с 2х до 7 мегабит.
— Включение Losles параметра для image quality приводит к не адекватному потреблению трафика, без изменения нагрузки на процессор. Для каких сценариев данная опция добавлена мне не совсем понятно.
If you enable this policy setting and set quality to Lossless, RemoteFX Adaptive Graphics uses lossless encoding. In this mode, the color integrity of the graphics data is not impacted. However, this setting results in a significant increase in network bandwidth consumption. We recommend that you set this for very specific cases only.
Итоги
Если раньше для работы 10 активных пользователей было достаточно 8 ядерного сервера и еще оставалось свободное место, то теперь такого сервера хватит только на 5 пользователей.
Думаю что пора готовится к замене серверов HP G6 и G7 поколения. Очень жалко расставаться с серверами в которых установлено >100 гб оперативной памяти, я предполагал что они послужат дальше.
Не исключаю что в старых процессорах не хватает аппаратных инструкций, по этому в ближайшее время планирую получить на тест современный сервер. Но честно говоря прогноз у меня пессимистичный, думаю что получить желаемый результат будет возможно только грубой силой, увеличением количества процессорных ядер, а это повлечет за собой увеличение количества необходимых лицензий и стоимости.
The End
Your network consists of a single Active Directory domain. All servers run Windows Server
2008 R2. You plan to publish a Web site on two Web servers.
You need to deploy an availability solution for your Web servers that meets the following requirements:
-> Supports the addition of more Web servers without interrupting client connections
-> Ensures that the Web site is accessible even if a single server fails
What should you do?
- A. Configure a failover cluster.
- B. Configure a Web garden on each Web server.
- C. Create a Network Load Balancing cluster.
- D. Create two Application pools on each Web server.
Answer :
C
Explanation:
Windows Web Server 2008 —
Windows Web Server 2008 is designed to function specifically as a Web applications server. Other roles, such as Windows Deployment Server and Active Directory Domain
Services, are not supported on Windows Web Server 2008. You deploy this server role either on a screened subnet to support a Web site viewable to external hosts or as an intranet server. As appropriate given its stripped-down role, Windows Web Server 2008 does not support the high-powered hardware configurations that other editions of Windows
Server 2008 do.
Windows Web Server 2008 has the following properties:
The 32-bit version (x86) supports a maximum of 4 GB of RAM and 4 processors in SMP configuration.
The 64-bit version (x64) supports a maximum of 32 GB of RAM and 4 processors in SMP configuration.
Supports Network Load Balancing clusters.
You should plan to deploy Windows Web Server 2008 in the Server Core configuration, which minimizes its attack surface, something that is very important on a server that interacts with hosts external to your network environment. You should only plan to deploy the full version of Windows Web Server 2008 if your organizations Web applications rely on features such as ASP.NET, because the .NET Framework is not included in a Server
Core installation.
Configuring Windows Network Load Balancing
While DNS Round Robin is a simple way of distributing requests, Windows Server 2008
NLB is a much more robust form of providing high availability to applications. Using NLB, an administrator can configure multiple servers to operate as a single cluster and control the usage of the cluster in near real-time.
NLB operates differently than DNS Round Robin in that NLB uses a virtual network adapter on each host. This virtual network adapter gets a single IP and media access control
(MAC) address, which is shared among the hosts participating in the load-balancing cluster. Clients requesting services from an NLB cluster have their requests sent to the IP address of the virtual adapter, at which point it can be handled by any of the servers in the cluster.
NLB automatically reconfigures as nodes are added and removed from the cluster. An administrator can add and remove nodes through the NLB Manager interface or the command line. For example, an administrator might remove each node in turn to perform maintenance on the nodes individually and cause no disruption in service to the end user.
Servers within NLB clusters are in constant communication with each other, determining which servers are available with a process known as heartbeats and convergence. The heartbeat consists of a server participating in an NLB cluster that sends out a message each second to its NLB-participating counterparts.
When five (by default) consecutive heartbeats are missed, convergence begins.
Convergence is the process by which the remaining hosts determine the state of the cluster.
During convergence, the remaining hosts listen for heartbeats from th
Your network consists of a single Active Directory domain. The network contains a file server that runs Windows Server 2008 R2. All servers use internal storage only. You plan to deploy a client/server Application.
You need to deploy the Application so that it is available if a single server fails. You must achieve this goal while minimizing costs.
What should you do?
- A. Deploy RemoteApp.
- B. Deploy a failover cluster that uses No Majority: Disk Only.
- C. Deploy a failover cluster that uses Node and File Share Disk Majority.
- D. Deploy Distributed File System (DFS) and configure replication.
Answer :
C
Explanation:
Understanding Cluster Quorum Models
Quorums are used to determine the number of failures that can be tolerated within a cluster before the cluster itself has to stop running. This is done to protect data integrity and prevent problems that could occur because of failed or failing communication between nodes.
Quorums describe the configuration of the cluster and contain information about the cluster components such as network adapters, storage, and the servers themselves. The quorum exists as a database in the registry and is maintained on the witness disk or witness share.
The witness disk or share keeps a copy of this configuration data so that servers can join the cluster at any time, obtaining a copy of this data to become part of the cluster.
One server manages the quorum resource data at any given time, but all participating servers also have a copy.
You can use the following four quorum models with Windows Server 2008 Failover
Clusters:
Node Majority Microsoft recommends using this quorum model in Failover Cluster deployments that contain an odd number of cluster nodes. A cluster that uses the Node
Majority quorum model is called a Node Majority cluster and remains up and running if the number of available nodes exceeds the number of failed nodesthat is, half plus one of its nodes is available. For example, for a seven-node cluster to remain online, four nodes must be available. If four nodes fail in a seven-node Node Majority cluster, the entire cluster shuts down. You should use Node Majority clusters in geographically or network- dispersed cluster nodes. To operate successfully this model requires an extremely reliable network, high-quality hardware, and a third-party mechanism to replicate back-end data.
Node and Disk Majority Microsoft recommends using this quorum model in clusters that contain even numbers of cluster nodes. Provided that the witness disk remains available, a
Node and Disk Majority cluster remains up and running when one-half or more of its nodes are available. A six-node cluster will not shut down if three or more nodes plus its witness disk are available. In this model, the cluster quorum is stored on a cluster disk that is accessible to all cluster nodes through a shared storage device using Serial Attached SCSI
(SAS), Fibre Channel, or iSCSI connections. The model consists of two or more server nodes connected to a shared storage device and a single copy of the quorum data is maintained on the witness disk. You should use the Node and Disk Majority quorum model in Failover Clusters with shared storage, all connected on the same network and with an even number of nodes. In the case of a witness disk failure, a majority of the nodes need to remain up and running. For example, a six-node cluster will run if (at a minimum) three nodes and the witness disk are available. If the witness disk is offline, the same six-node cluster requires that four nodes are available.
Exam Tip If the 70-646 examination asks
You need to recommend changes to Web1 to ensure that server backups can be performed remotely from Backup1.
Which two changes should you include in the recommendation? (Each correct answer presents part of the solution. Choose two.)
- A. Install Windows PowerShell.
- B. Install Windows Server Backup.
- C. Modify the Windows Firewall settings.
- D. Enable the IIS Management Service feature.
A company has a single Active Directory Domain Services (AD DS) domain and a single
Remote Desktop Session Host (RD Session Host). The RD Session Host is approaching full memory capacity. All servers run Windows Server 2008 R2.
You are designing a Remote Desktop Services (RDS) infrastructure. The infrastructure must meet the following requirements:
-> Allow infrastructure capacity to increase.
-> Minimize the number of physical servers.
-> Do not require administrative action on the client computers if the infrastructure capacity increases.
You need to design an RDS infrastructure that meets the requirements.
What should you recommend? (More than one answer choice may achieve the goal. Select the BEST answer.)
- A. Migrate the RD Session Host to a virtual machine (VM) running in Microsoft Hyper-V. Add memory to the VM as demand increases.
- B. Add RD Session Hosts as demand increases, and use Group Policy to direct users to the correct server.
- C. Install and configure Windows Server Resource Manager (WSRM) on the RD Session Host to control user resource allocation.
- D. Implement an RD Session Host server farm and add servers as required.
Answer :
A
Explanation:
Virtualization meets the requirements easily enough, as capacity needs grow the VMs can be migrated to more powerful physical servers, again virtualization reduces the number of physical servers and finally as the actual RD Session Host wont change regardless of the location of that VM it will meet the third requirement Ans D does not meet the 3rd requirement
Ans C wont resolve the problem of running out of memory only that addition of RAM will resolve that issue
Ans B again does not meet the 3rd requirement
Your network consists of a single Active Directory domain. All domain controllers run
Windows Server 2008 R2.
You need to plan an auditing strategy that meets the following requirements:
-> Audits all changes to Active Directory Domain Services (AD DS)
-> Stores all auditing data in a central location
What should you include in your plan?
- A. Configure an audit policy for the domain. Configure Event Forwarding.
- B. Configure an audit policy for the domain controllers. Configure Data Collector Sets.
- C. Implement Windows Server Resource Manager (WSRM) in managing mode.
- D. Implement Windows Server Resource Manager (WSRM) in accounting mode.
Answer :
A
Explanation:
MCITP Self-Paced Training Kit Exam 70-646 Windows Server Administration:
The configuration of a subscription filter is more like the configuration of a custom view in that you are able to specify multiple event log sources, rather than just a single Event Log source. In addition, the subscription will be saved whereas you need to re-create a filter each time you use one. By default, all collected Event Log data will be written to the
Forwarded Event Event Log. You can forward data to other logs by configuring the properties of the subscription. Even though you use a filter to retrieve only specific events from source computers and place them in the destination log, you can still create and apply a custom view to data that is located in the destination log. You could create a custom view for each source computer, which would allow you to quickly limit events to that computer rather than viewing data from all source computers at the same time.
You configure collector initiated subscriptions through the application of Group Policy. To do this you must configure the collector computer in the same manner as you did in the previous steps. When configuring the subscription type, select Source Computer Initiated rather than Collector Initiated. To set up the source computers, apply a GPO where you have configured the Computer Configuration\Policies\AdministrativeTemplates\Windows
Components\Event Forwarding node and configure the Server Address, Refresh Interval,
And Issuer Certificate policy with the details of the collector computer, as shown in Figure
7-10.
Auditing enhancements You can use the new Directory Service Changes audit policy subcategory when auditing Windows Server 2008 AD DS. This lets you log old and new values when changes are made to AD DS objects and their attributes. You can also use this new feature when auditing Active Directory Lightweight Directory Services (AD LDS).
Planning AD DS Auditing —
In Windows Server 2008, the global audit policy Audit Directory Service Access is enabled by default. This policy controls whether auditing for directory service events is enabled or disabled. If you configure this policy setting by modifying the Default Domain Controllers
Policy, you can specify whether to audit successes, audit failures, or not audit at all. You can control what operations to audit by modifying the System Access Control List (SACL) on an object. You can set a SACL on an AD DS object on the Security tab in that objects
Properties dialog box.
As an administrator one of your tasks is to configure audit policy. Enabling success or failure auditing is a straightforward procedure. Deciding which objects to audit; whether to audit success, failure or both; and whether to record new and old values if changes are made is much more difficult. Auditing everything is never an optiontoo much information is as bad as too little. You need to be selective. In Windows 2000 Server and Windows
Server 2003, you could specify only w
Your network consists of a single Active Directory domain. All domain controllers run
Windows Server 2008 R2. All servers run Windows Server 2008 R2. All client computers run Windows 7.
You need to generate a monthly report on the status of software updates for the client computers.
Your solution must meet the following requirements:
-> Display all of the operating system updates that installed successfully
-> Display all of the Microsoft Application updates that installed successfully
-> Display all of the operating system updates that failed to install
-> Display all of the Microsoft Application updates that failed to install
-> Minimize administrative effort
-> Minimize costs
What should you do?
- A. Install Microsoft System Center Essentials (Essentials) 2007. Deploy management agents on all client computers.
- B. Install Microsoft System Center Configuration Manager (SysMgr) 2007. Deploy management agents on all client computers.
- C. Install Windows Server Update Services (WSUS) 3.0 SP2. Configure Windows Update by using a Group Policy object (GPO).
- D. Deploy Microsoft Baseline Security Analyzer (MBSA) 2.1 on the client computers. Run MBSA on each client computer, and save the report to a shared folder on the network.
Answer :
C
Explanation:
http://technet.microsoft.com/en-us/library/dd939886%28WS.10%29.aspx
Whats new in this release?
Integration with Windows Server 2008 R2
Support for the BranchCache feature in Windows Server 2008 R2
Support for Windows 7 client computers New features
Automatic approval rules include the ability to specify the approval deadline date and time for all computers or for specific computer groups.
Improved handling of language selection for downstream servers includes a new warning dialog that appears when you decide to download updates only for specified languages.
New Update and Computer Status reports let you filter updates that are approved for installation. You can run these reports from the WSUS administration console or use the application programming interface (API) to incorporate this functionality into your own reports.
Windows Update Agent improvements
Client computer scan time is faster than previous versions.
Computers that are managed by WSUS servers can now run scoped scans against those servers, instead of performing a full scan. This results in faster scans for applications that use Microsoft Update APIs such as Windows Defender.
User experience improvements help users organize updates and provide greater clarity on update value and behavior.
Imaged computers are more clearly displayed in the WSUS administration console.
For more information, see article 903262 in the Microsoft Knowledge Base.
Prevents APIs that are called by non-local system callers in a non-interactive session from failing.
Prevents error code 0x80070057 when you try to install 80 or more updates at the same time from the Windows Update Web page or from the Microsoft Update Web page.
Improves scan times for Windows Update
Improves the speed at which signature updates are delivered
Enables support for Windows Installer reinstallation functionality
Improves error messaging
Your network consists of a single Active Directory domain. The domain contains a file server named Server1 that runs Windows Server 2008 R2. The file server contains a shared folder named UserDocs. Each user has a subfolder in UserDocs that they use to store personal data.
You need to design a data management solution that meets the following requirements:
-> Limits the storage space that is available to each user in UserDocs
-> Sends a notification to the administrator if a users attempts to save multimedia files in UserDocs
-> Minimizes administrative effort
What should you include in your design?
- A. Configure NTFS quotas on UserDocs. Configure a task in Event Viewer to send an email notification.
- B. Configure NTFS quotas on UserDocs. Schedule a script to monitor the contents of UserDocs and send an email notification if a multimedia file is found.
- C. Install the File Server Resource Manager (FSRM) role service on Server1. Configure event subscriptions.
- D. Install the File Server Resource Manager (FSRM) role service on Server1. Configure hard quotas and file screening.
Answer :
D
Explanation:
MCITP Self-Paced Training Kit Exam 70-646 Windows Server Administration:
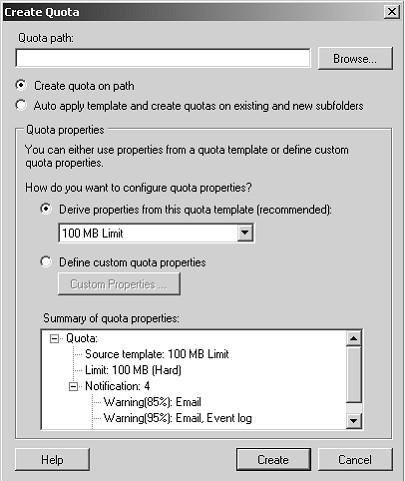
Creating Quotas —
If the FSRM File Services server role is installed, you can use FSRM to create quotas. The
Create Quota dialog box is shown in Figure 6-13. Note that you will be unable to access this box if you have not installed the appropriate server role, which you will do in the practice session later in this lesson.
Figure 6-13 —
The Create Quota dialog box —
You specify a path to the volume or folder for which you want to create the quota and then specify whether you want to create a quota only on that path or whether a template-based quota will be automatically generated and applied to existing and new subfolders on the path of the parent volume or folder. To specify the latter action, select Auto Apply Template
And Create Quotas On Existing And New Subfolders. Typically you would select Derive
Properties From This Quota Template (Recommended) and select a template. You can, if you want, define custom quota properties, but this is not recommended. You can select templates that specify the quota size that is allocated to each user and whether the quota is hard or soft. A hard quota cannot be exceeded. A user can exceed a soft quota, but typically exceeding the quota limit generates a report in addition to sending an e-mail notification and logging the event. Soft quotas are used for monitoring. Quota templates include the following:
100 MB Limit This is a hard quota. It e-mails the user and specified administrators if the100 percent quota limit has been reached and writes an event to the event log.
200 MB Limit Reports to User This is a hard quota. It generates a report, sends e-mails, and writes an event to the event log if the 100 percent quota limit has been reached.
200 MB Limit with 50 MB Extension Technically this is a hard quota because it performs an action when the user attempts to exceed the limit, rather than merely monitoring the exceeded limit. The action is to run a program that applies the 250 MB Extended Limit template and effectively gives the user an additional 50 MB.
E-mails are sent and the event is logged when the limit is extended.
250 MB Extended Limit The 250 MB limit cannot be exceeded. E-mails are sent and the event is logged when the limit is reached.
Monitor 200 GB Volume Usage This is a soft quota that can be applied only to volumes. It is used for monitoring.
Monitor 50 MB Share Usage This is a soft quota that can be applied only to shares. It is used for monitoring.
Managing File Screens —
You can use FSRM to create and manage file screens that control the types of files that users can save, and generate notifications when users attempt to save unauthorized files.
You can also define file screening templates that you can apply to new volumes or folders and use across your organization.
FSRM also enables you to create file screening exceptions that extend the flexibility of the file
Your company purchases 15 new 64bit servers as follows:
-> Five of the servers have a single processor.
-> Five of the servers have a single dual core processor.
-> Five of the servers have two quad core processors.
You plan to deploy Windows Server 2008 R2 on the new servers by using Windows
Deployment Services (WDS). You need to recommend a WDS install image strategy that meets the following requirements:
-> Minimizes the number of install images
-> Supports the deployment of Windows Server 2008 R2
What should you recommend?
- A. one install image file that contains three install images
- B. one install image file that contains a single install image
- C. two install image files that each contain a single install image
- D. three install image files that each contain a single install image
Answer :
B
Explanation:
You only need one image per processor type
Windows Deployment Services Images
Windows Deployment Services uses two different types of images: install images and boot images. Install images are the operating system images that will be deployed to Windows
Server 2008 or Windows Vista client computers. A default installation image is located in the \Sources directory of the Windows Vista and Windows Server 2008 installation DVDs. If you are using WDS to deploy Windows Server 2008 to computers with different processor architectures, you will need to add separate installation images for each architecture to the
WDS server. Architecture-specific images can be found on the architecture-specific installation media. For example, the Itanium image is located on the Itanium installation media and the x64 default installation image is located on the x64 installation media.
Although you can create custom images, you only need to have one image per processor architecture. For example, deploying Windows Server 2008 Enterprise Edition x64 to a computer with 1 x64 processor and to a computer with 8 x64 processors in SMP configuration only requires access to the default x64 installation image. Practice exercise 2 at the end of this lesson covers the specifics ol adding a default installation image to a
WDS server.
Your network consists of a single Active Directory domain. Users access and share documents by using a DFS namespace.
You need to recommend a solution to manage user access to documents. The solution must meet the following requirements:
-> Allow for document versioning
-> Allow for online collaboration
What should you recommend?
- A. File Server Resource Manager (FSRM)
- B. Volume Shadow Copy Service (VSS)
- C. Microsoft SharePoint Foundation 2010
- D. Windows System Resource Manager (WSRM)
Answer :
C
Explanation:
sharepoint allows collaboration and versioning
http://www.plusconsulting.com/WhitePapers/SharePoint%202010%20Business%20Value%
20WhitePaper.pdf
A company has a print server that runs Windows Server 2003 R2 Enterprise (x86). The print server is configured with 2S0 print queues.
You are planning to migrate the print server to a new server that runs Windows Server
2008 R2 Enterprise. The destination server has the Print and Document Services role installed.
You need to ensure that printer queues migrate successfully.
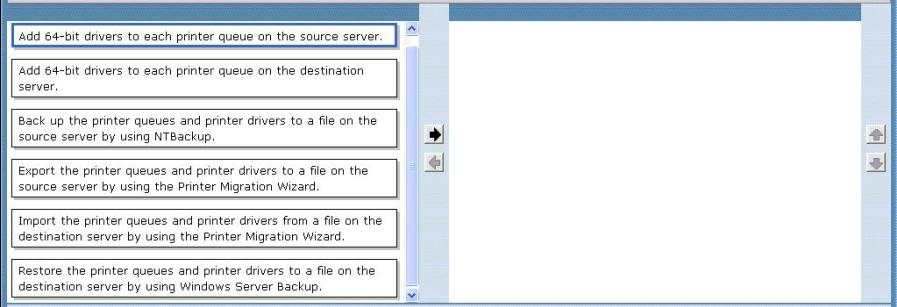
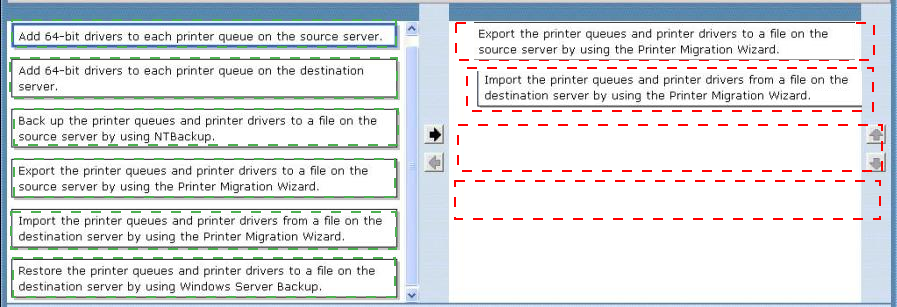
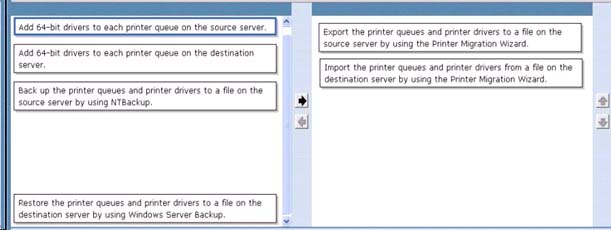
Which actions should you perform in sequence?
To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order, (use only actions that Apply.)
Answer :
Explanation:
http://technet.microsoft.com/en-us/library/cc722360.aspx
Migrating print servers —
Using the Windows interface —
Using a command prompt —
To migrate print servers by using Print Management
Open Print Management.
In left pane, click Print Servers, right-click the print server that contains the printer queues that you want to export, and then click Export printers to a file. This starts the Printer
Migration Wizard.
On the Select the file location page, specify the location to save the printer settings, and then click Next to save the printers.
Right-click the destination computer on which you want to import the printers, and then click Import printers from a file. This launches the Printer Migration Wizard.
On the Select the file location page, specify the location of the printer settings file, and then click Next.
On the Select import options page, specify the following import options:
Import mode. Specifies what to do if a specific print queue already exists on the destination computer.
List in the directory. Specifies whether to publish the imported print queues in the Active
Directory Domain Services.
Convert LPR Ports to Standard Port Monitors. Specifies whether to convert Line Printer
Remote (LPR) printer ports in the printer settings file to the faster Standard Port Monitor when importing printers.
Click Next to import the printers.
To migrate print servers by using a command prompt
To open a Command Prompt window, click Start, click All Programs, click Accessories, right-click Command
Prompt, and then click Run as administrator.
Type:
CD %WINDIR%\System32\Spool\Tools Printbrm -s \\<sourcecomputername> -b -f
<filename>.printerExport
Type: Printbrm -s \\<destinationcomputername> -r -f <filename>.printerExport
Your company has 250 branch offices. Your network contains an Active Directory domain.
The domain controllers run Windows Server 2008 R2. You plan to deploy Readonly
Domain Controllers (RODCs) in the branch offices.
You need to plan the deployment of the RODCs to meet the following requirements:
-> Build each RODC at the designated branch office.
-> Ensure that the RODC installation source files do not contain cached secrets.
-> Minimize the bandwidth used during the initial synchronization of Active Directory
Domain Services (AD?DS).
What should you include in your plan?
- A. Use Windows Server Backup to perform a full backup of an existing domain controller. Use the backup to build the new RODCs.
- B. Use Windows Server Backup to perform a custom backup of the critical volumes of an existing domain controller. Use the backup to build the new RODCs.
- C. Create a DFS namespace that contains the Active Directory database from one of the existing domain controllers. Build the RODCs by using an answer file.
- D. Create an RODC installation media. Build the RODCs from the RODC installation media.
Answer :
D
Explanation:
http://technet.microsoft.com/en-us/library/cc770654%28WS.10%29.aspx
Installing AD DS from Media —
Applies To: Windows Server 2008, Windows Server 2008 R2
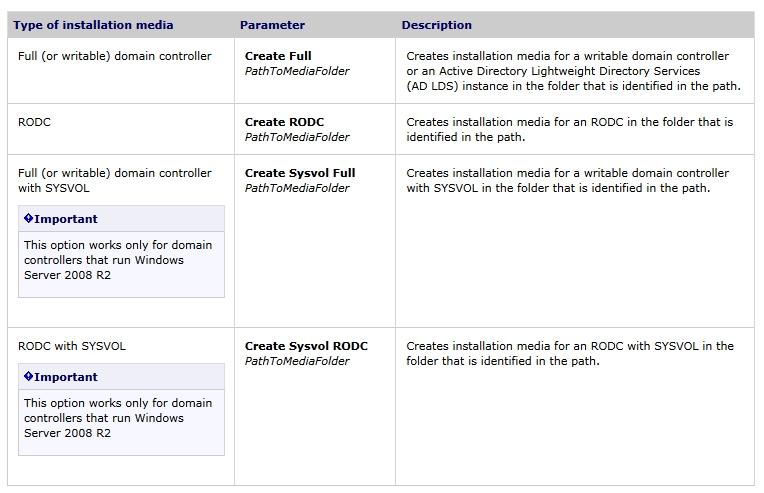
You can use the Ntdsutil.exe tool to create installation media for additional domain controllers that you are creating in a domain. By using the Install from Media (IFM) option, you can minimize the replication of directory data over the network. This helps you install additional domain controllers in remote sites more efficiently.
Ntdsutil.exe can create four types of installation media, as described in the following table.
You must use read-only domain controller (RODC) installation media to install an RODC.
For RODC installation media, the ntdsutil command removes any cached secrets, such as passwords. You can create RODC installation media either on an RODC or on a writeable domain controller. You must use writeable domain controller installation media to install a writeable domain controller. You can create writeable domain controller installation media only on a writeable domain controller.
If the source domain controller where you create the installation media and the destination server where you plan to install ActiveDirectory Domain Services (ADDS) both run
Windows Server2008 with Service Pack2 or later or Windows Server2008R2, and if you are using Distributed File System (DFS) Replication for SYSVOL, you can run the ntdsutil ifm command with an option to include the SYSVOL shared folder in the installation media.
If the installation media includes SYSVOL, you must use Robocopy.exe to copy the installation media from the source domain controller to the destination server. For more information, see Installing an Additional Domain Controller by Using IFM.
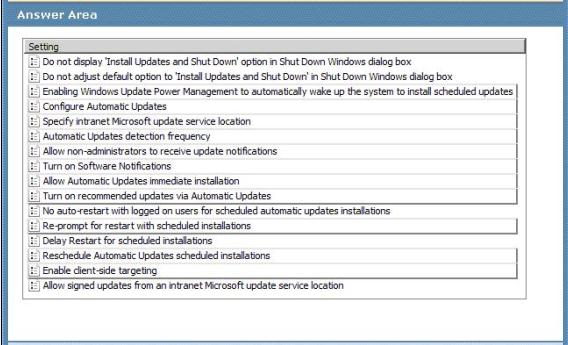
Your company has recently implemented Windows Server Update Services (WSUS). All client computers run Windows 7 Enterprise Edition. Only some users have local administrative privileges.
You are designing a Group Policy object (GPO) to configure the client computers. The
GPO must Apply only the following settings:
-> Updates must be downloaded from the WSUS server.
-> Automatically download and install updates every Thursday at 12:00 P.M.
-> Configure WSUS client-side targeting through Group Policy.
-> Delay the installation of updates until 20 minutes after a client computer is started, if the client computer was shut down at the specified installation time.
You need to design the GPO to meet the requirements.
Which settings should you configure to meet the requirements?
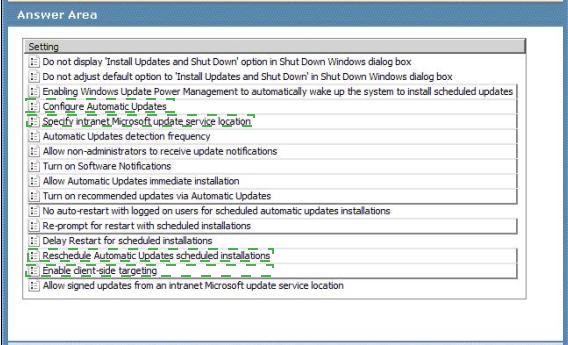
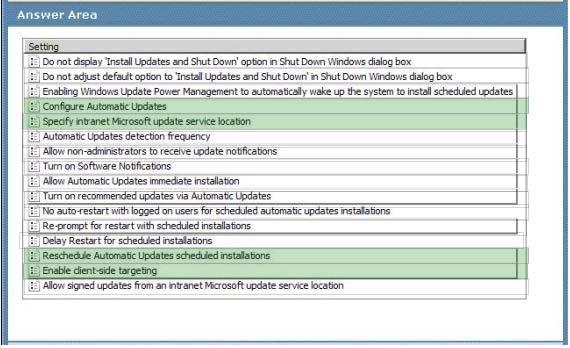
To answer, select the appropriate settings in the answer area.
Answer :
Explanation:
Configure Automatic Updates —
By enabling this setting you enable your computer to receive updates through Automatic
Updates on a computer or computer group. To complete this setting, you must then select one of the following four options:
Notify before downloading any updates and notify again before installing them.
Download the updates automatically and notify when they are ready to be installed (default setting)
Automatically download updates and install them on the schedule specified below
Allow local administrators to select the configuration mode that Automatic Updates should notify and install updates
Best preactices http://technet.microsoft.com/en-us/library/cc720525%28v=ws.10%29.aspx deployment http://www.windows-noob.com/forums/index.php?/topic/588-how-can-i- configure-wsus-todeploy-updates/
A company has servers that run a Server Core installation of Windows Server 2008.
You are designing the migration of the servers to Windows Server 2008 R2. After the migration, you will install the Remote Desktop Services server role and the Print and
Document Services server role on the servers.
You need to ensure that shared resources on the servers are available after the migration, and minimize administrative effort.
What should you recommend? (More than one answer choice may achieve the goal. Select the BEST answer.)
- A. Deploy new servers with a Server Core installation of Windows Server 2008 R2. Migrate the shared resources to the new servers.
- B. Upgrade the existing servers to a Server Core installation of Windows Server 2008 R2, and then upgrade the servers to a full installation of Windows Server 2008 R2.
- C. Move the shared resources off of the existing servers. Perform a clean installation of Windows Server 2008 R2 on the servers. Move the shared resources back onto the servers.
- D. Deploy new servers with Windows Server 2008 R2 installed. Migrate the shared resources to the new servers.
Answer :
D
Explanation:
The key here is minimize effort & remote desktop services.
Server core wouldn’t allow remote desktop services as it has no GUI so that would rule out answer A you also cant upgrade from core to full see http://www.windowsitpro.com/article/tips/can-i-upgrade-fromserver-core-2008-to-the-full- windows-server-2008- or http://serverfault.com/questions/92523/upgrade-fromwindows-
2008-server-core-to-full-windows-2008-server upgrade considerations for server core installations of windows server 2008 so that rules our B
You can use the server core installation option only by performing a clean installation.
You cannot upgrade from earlier versions of windows to server core installations of windows server 2008.
You cannot upgrade from non-server core installations of windows server 2008 to server core installations of windows server 2008.
You cannot convert server core installations of windows server 2008 to non-server core installations of windows server 2008.
You can upgrade server core installations of windows server 2008 only to windows server core r2 when it is released.
Answer C is possible but again you’re asked to minimize effort so D would be 1 step less thus reducing your effort and possible down time.
Your network contains a single Active Directory domain. You have 100 servers that run
Windows Server 2008 R2 and 5,000 client computers that run Windows 7. You plan to deploy Applications to the client computers.
You need to recommend an Application deployment strategy that meets the following requirements:
Applications must be deployed only to client computers that meet the minimum hardware requirements.
Deployments must be scheduled to occur outside business hours.
Detailed reports on the success or failure of the Application deployments must be provided.
What should you recommend?
- A. Deploy Applications by using Group Policy.
- B. Implement Windows Server Update Services (WSUS).
- C. Implement Microsoft System Center Operations Manager (SCOM) 2007 R2.
- D. Implement Microsoft System Center Configuration Manager (SCCM) 2007 R2.
Answer :
D
Explanation:
http://technet.microsoft.com/en-us/library/bb680651.aspx
Welcome to Microsoft System Center Configuration Manager 2007. Configuration Manager
2007 contributes to a more effective Information Technology (IT) department by enabling secure and scalable operating system and application deployment and desired configuration management, enhancing system security, and providing comprehensive asset management of servers, desktops, and mobile devices.
Post-Setup Configuration Tasks —
After Setup has run, there are still a few tasks you must perform to have a functioning
Configuration Manager 2007 site. For example, you might need to assign new site system roles and install clients. For more information, see Checklist for Required Post Setup
Configuration Tasks.
Common Configuration Manager Tasks
For more information about how to do common Configuration Manager 2007 tasks, see the following topics.
-> Planning and Deploying the Server Infrastructure for Configuration Manager 2007
-> Planning and Deploying Clients for Configuration Manager 2007
-> Collect hardware and software asset information
-> Distribute software
-> Deploy software updates
-> Deploy operating systems
-> Manage desired configurations
-> Remotely administer a computer
-> Restrict non-compliant computers from accessing the network
-> Manage mobile devices like Smartphones and Pocket PCs
Your network contains several branch offices. All servers run Windows Server 2008 R2.
Each branch office contains a domain controller and a file server.
The DHCP Server server role is installed on the branch office domain controllers. Each office has a branch office administrator.
You need to delegate the administration of DHCP to meet the following requirements:
-> Allow branch office administrators to manage DHCP scopes for their own office
-> Prevent the branch office administrators from managing DHCP scopes in other offices
-> Minimize administrative effort
What should you do?
- A. In the Active Directory domain, add the branch office administrators to the Server Operators builtin local group.
- B. In the Active Directory domain, add the branch office administrators to the Network Configuration Operators builtin local group.
- C. In each branch office, migrate the DHCP Server server role to the file server. On each file server, add the branch office administrator to the DHCP Administrators local group.
- D. In each branch office, migrate the DHCP Server server role to the file server. In the Active Directory domain, add the branch office administrators to the DHCP Administrators domain local group.
Answer :
C
Explanation:
http://technet.microsoft.com/en-us/library/dd379494%28WS.10%29.aspx http://technet.microsoft.com/en-us/library/dd379483%28WS.10%29.aspx http://technet.microsoft.com/en-us/library/dd379535%28WS.10%29.aspx http://technet.microsoft.com/en-us/library/cc737716%28WS.10%29.aspx
DHCP Administrators —
Members of the DHCP Administrators group can view and modify any data at the DHCP server. DHCP Administrators can create and delete scopes, add reservations, change option values, create superscopes, or perform any other activity needed to administer the
DHCP server, including export or import of the DHCP server configuration and database.
DHCP Administrators perform these tasks using the Netsh commands for DHCP or the
DHCP console. For more information, see DHCP tools.
Members of the DHCP Administrators group do not have unlimited administrative rights.
For example, if a DHCP server is also configured as a DNS server, a member of the DHCP
Administrators group can view and modify the DHCP configuration but cannot modify DNS server configuration on the same computer.
Because members of the DHCP Administrators group have rights on the local computer only, DHCP Administrators cannot authorize or unauthorize DHCP servers in Active
Directory. Only members of the Domain Admins group can perform this task. If you want to authorize or unauthorize a DHCP server in a child domain, you must have enterprise administrator credentials for the parent domain. For more information about authorizing
DHCP servers in Active Directory, see Authorizing DHCP servers and Authorize a DHCP server in Active Directory.
Using groups to administer DHCP servers in a domain
When you add a user or group to a DHCP Users or DHCP Administrators group on a
DHCP server, the rights of the DHCP group member do not apply to all of the DHCP servers in the domain. The rights apply only to the DHCP service on the local computer.
You work as the network administrator at TestKing.com. TestKing.com utilizes Microsoft WindowsServer 2008 R2 as their networking operating system. The client computers are running MicrosoftWindows 7 Enterprise.TestKing.com utilizes a computer named TESTKING-DC01 configured as the DCHP serverleasing addresses in the scope range of 192.168.1.2 t 192.168.1.200. During the course of theweek you receive instruction to deploy a second DHCP server to improve redundancy. You installand configure the DHCP service on a computer named TESTKING-DC02.TestKing.com wants you to ensure when TESTKING-DC01 fails that TESTKING-DC02 wouldcontinue leasing IP addresses from the same range.What configurations should be considered?
Options are :
- You should consider the configuration and utilization of Network Load Balancing on the two DHCP
servers. - You should consider utilization of the Split-Scope wizard on KingScope on TESTKING-DC01.
- You should consider the creation of a scope named KingScope on TESTKING-DC02 before
running the Split-Scope wizard on TESTKING-DC02. - You should consider the creation of a scope named KingScope on TESTKING-DC02 configured
with the Ipv4 address range192.168.1.2 to 192.168.1.200 range.
Answer : You should consider utilization of the Split-Scope wizard on KingScope on TESTKING-DC01.
70-642 Windows Server 2008 Network Infrastructure Exam Set 4
You work as the network administrator at TestKing.com. TestKing.com utilizes Microsoft WindowsServer 2008 R2 as their networking operating system. The client computers are running MicrosoftWindows 7 Enterprise. TestKing.com has recently deployed two computers named TESTKING-DC01 and TESTKING-DC02. TESTKING-DC01 is the network Primary DNS server and TESTKING-DC02 is the Web server. The network users utilize custom apps and access Intranet web sites hosted onTESTKING-DC02. The custom applications utilize Ipv6 to locate resources. During the course of the day you receiveinstruction to create DNS records to ensure Intranet web sites are able to locate Ipv6 resources.Which DNS record type should be created?
Options are :
- You should consider the creation of an Alias CNAME record.
- You should consider the creation of a Name Server (NS) record.
- You should consider the creation of a Quad-A record.
- You should consider the creation of a Host A record.
Answer : You should consider the creation of a Quad-A record.
You work as the network administrator at TestKing.com. TestKing.com utilizes Microsoft WindowsServer 2008 R2. TestKing.com has recently deployed two computers named TESTKING-DC01 and TESTKING-DC02. TESTKING-DC01 is configured as a Web server which is accessible from the Internet and TESTKING-DC02 is a gateway server utilized by network users to access the Internet. During thecourse of the day you receive instruction from TestKing.com to configure Network AddressTranslation (NAT) on TESTKING-DC02 to ensure the websites can be accessed publicly.What configurations should be made on TESTKING-DC02?
Options are :
- You should consider having the RIP routing protocol enabled.
- You should consider having the Network Policy Server role installed.
- You should consider having the Host Credential Authorization Protocol role installed.
- You should consider having the Routing and Remote Access Service (RRAS) and Routing roles
installed.
Answer : You should consider having the Routing and Remote Access Service (RRAS) and Routing roles
installed.
You work in a team of network administrators at TestKing.com. The TestKing.com networkconsists of a single Active Directory Domain Services domain named Testking.com. The networkincludes servers running Windows Server 2008 R2 and client computers running Windows 7Enterprise.A server named TK-CA1 runs the Active Directory Certificate Services (AD CS) role and isconfigured as a certificate authority for the Testking.com domain.The network administrators manage all network servers by establishing Remote Desktopconnections to the servers from their client computers.A new company security policy states that all Remote Desktop connections should be as secureas possible.To comply with the security policy, you obtain user certificates from TK-CA1.What else should you do to ensure the RDP connections are as secure as possible?
Options are :
- You should configure the servers to use a Remote Desktop Gateway.
- You should disable Remote Assistance on the servers.
- You should configure the servers to require connections that use the RDP Security Layer.
- You should configure the servers to only allow connections from Remote Desktop client computers
that use Network Level Authentication.
Answer : You should configure the servers to only allow connections from Remote Desktop client computers
that use Network Level Authentication.
70-642 Windows Server 2008 Network Infrastructure Exam Set 4
You work as the network administrator at TestKing.com. The TestKing.com network consists of asingle Active Directory Domain Services domain named Testking.com.The network includes servers running Windows Server 2008 R2 and client computers runningWindows 7 Enterprise.A Windows Server 2008 R2 server named TK-DNS1 runs the DNS Server role. TK-DNS1 hoststhe publicly accessible DNS zone for Testking.com.You are in the process of configuring a new email server for the Testking.com users. You install aWindows Server 2008 R2 server named TK-Mail1 and install and configure Exchange Server 2007on it. You need to configure the appropriate DNS resource records in the Testking.com DNS zone onTK-DNS1 for the email server. Which type of DNS resource record should you create on TK-DNS1?
Options are :
- You should create a Pointer (PTR) record.
- You should create a Canonical Name (CNAME) record.
- You should create a Mail Exchanger (MX) record.
- You should create a Well-Known Service (WKS) record.
Answer : You should create a Mail Exchanger (MX) record.
You work as the network administrator for TestKing.com. TestKing.com utilizes Microsoft WindowsServer 2008 R2 as the networking operating system and Windows 7 Enterprise as the clientoperating system.TestKing.com has recently deployed a computer named TESTKING-DC01 configured with a staticIpv4 addressing. During the course of the week whilst performing maintenance you discover theDHCP database on the cluster has grown preposterously large. TestKing.com wants you toreduce the size of the DHCP database. How would you decrease the database size?
Options are :
- You should consider deployment of an additional DHCP server named TESTKING-DC02 for
splitting the scope between the servers. - You should consider utilizing the Windows Command Prompt to rung the jetpack.exe utility.
- You should consider Compressing contents to save disk space by right click on the dhcp.mdb file
and select Properties. - You should consider utilizing the Windows Command Prompt to run the eseutil.exe utility.
Answer : You should consider utilizing the Windows Command Prompt to rung the jetpack.exe utility.
You work as the network administrator at TestKing.com. TestKing.com utilizes Microsoft WindowsServer 2008 R2 as their networking operating system. The client computers are running MicrosoftWindows XP Professional and Microsoft Windows 7 Enterprise. Service Pack 3 is installed on allWindows XP Professional computers and Service Pack 1 is installed on all Windows 7 Enterprisecomputers.TestKing.com has recently deployed a computer named TESTKING-DC01 which will hostcompany confidential information across shared folders. TestKing.com wants you to ensure that allnetwork transmissions to and from TESTKING-DC01 are encrypted.During the course of the day you configure a connection security rule which utilizes Kerberos forinbound and outbound authentication. TestKing.com wants you to ensure the client computers areable to connect to TESTKING-DC01. How would you accomplish this task?
Options are :
- You should consider having the Server (Request Security) IPSec policy assigned to TESTKING-
DC01. - You should consider having the Client (Respond Only) IPSec policy assigned to the client
computers using a Group Policy Object. - You should consider having outbound rules configured on the client computers using a Group
Policy Object. - You should consider having inbound rules configured on TESTKING-DC01 using the Windows
Firewall with Advanced Security console.
Answer : You should consider having the Client (Respond Only) IPSec policy assigned to the client
computers using a Group Policy Object.
Microsoft Windows Server 2016 Certification: Exam 70-741 Set 4
You work as the network administrator for TestKing.com. TestKing.com utilizes Microsoft WindowsServer 2008 R2 as the networking operating system.TestKing.com has recently deployed a computer named TESTKING-DC01 configured as thenetwork DHCP server with a single scope configured. TESTKING-DC01 is configured with a staticIpv4 network address. TestKing.com has deployed a computer named TESTKLING-DC02configured with the File Services role. TestKing.com wants you to ensure TESTKING-DC02 isassigned the same IP configuration.What should you do to ensure TESTKING-DC02 receives the same IP configuration?
Options are :
- You should consider creating an IP exclusion in the DHCP scope on TESTKING-DC01.
- You should consider extending the lease time in the DHCP scope options on TESTKING-DC01.
- You should consider creating a reservation in the DHCP scope on TESTKING-DC01.
- You should consider configuration of a Vendor Class in the DHCP server options on TESTKING-
DC01.
Answer : You should consider creating a reservation in the DHCP scope on TESTKING-DC01.
You work as the network administrator at TestKing.com. The TestKing.com network consists of asingle Active Directory Domain Services domain named Testking.com.The network includes 500 physical servers running Windows Server 2008 R2 and 10,000 clientcomputers running Windows 7 Enterprise.The 500 servers are located on two subnets. The two subnet IP address ranges are 10.44.0.0/24and 10.44.1.24. You are planning to migrate the physical servers to virtual machines. You need to plan the IPaddressing scheme of the virtual infrastructure. You want all servers to be in a single subnet whileminimizing the number of unused IP addresses in the subnet.Which of the following address ranges should you use for the server subnet?
Options are :
- You should use the 10.50.0.0/22 address range.
- You should use the 10.50.0.0/21 address range.
- You should use the 10.50.0.0/23 address range.
- You should use the 10.50.0.0/24 address range.
Answer : You should use the 10.50.0.0/23 address range.
You work as the network administrator at TestKing.com. The TestKing.com network consists of asingle Active Directory forest named Testking.com that contains three domains namedTestking.com, north.testking.com and south.testking.com.Each domain contains two Windows Server 2008 R2 servers that run the Active Directory DomainServices (AD DS) role and are configured as domain controllers. Each domain controller also runsthe DNS Server role and hosts an Active Directory integrated DNS zone.Each domain has a number of single name resources. Name resolution for the single nameresources is currently performed by a WINS server in each domain.You want to decommission the WINS servers and use DNS to perform the single name resolution.How should you configure DNS to enable forest-wide single name resolution?
Options are :
- You should enter static host (A) records in the Testking.com, north.testking.com and
south.testking.com DNS zones for the single name resources. - You should create an Active Directory-integrated zone named GlobalNames and create Alias
(CNAME) records for the single name resources. - You should create an Active Directory-integrated zone named GlobalNames and create host (A)
records for the single name resources. - You should modify the lmhosts files on each DNS server.
Answer : You should create an Active Directory-integrated zone named GlobalNames and create host (A)
records for the single name resources.
Microsoft Dynamics Expand and Test Your Skills Practice Test Set 1
You are the network administrator of your company. The servers on the company’s network runWindows Server 2008. The company’s network consists of a single Active Directory domain. Aserver named DNS1 is configured as a Domain Name System (DNS) server and stores thedirectory-integrated DNS zone for your company.You promote a member server to a domain controller, but you discover that the Service Record(SRV) for the new domain controller is not created in the directory-integrated DNS zone. Whatshould you do to create an SRV record for the new domain controller by involving leastadministrative effort?
Options are :
- Restart the Netlogon service.
- Configure the properties for forward lookup zone to allow only secure updates.
- Restart the DHCP Client service.
- Manually add an SRV record for the new domain controller.
Answer : Restart the DHCP Client service.
70-642 Windows Server 2008 Network Infrastructure Exam Set 4
Paige is a systems administrator who is responsible for performing backups on several servers.Recently, she has been asked to take over operations of several new servers. Unfortunately, noinformation about the standard upkeep and maintenance of those servers is available. Paigewants to begin by making configuration changes to these servers, but she wants to first ensurethat she has a full backup of all the data on each of these servers.Paige decides to use the Windows Server 2008 Backup utility to perform the backups. She wantsto choose a backup type that will back up all files on each of these servers, regardless of whenthey were last changed or if they have been previously backed up. Which of the following types ofbackup operations store all the selected files, without regard to the Archive bit setting?(Choose all that apply.)
Options are :
- Normal
- Differential
- Copy
- Incremental
Answer : Normal
You have upgraded all servers in your company’s single Active Directory domain to WindowsServer 2008. The organization’s SharePoint Server intranet Web site is hosted on four differentWeb servers. The web servers are configured with identical hardware and each one is assigned aunique IP address. You need to configure the network such that incoming SharePoint connectionrequests are distributed evenly across all four Web servers.What action should you perform?A.Enable round-robin at the DNS zone level.B.Enable netmask ordering at the DNS server level.C.Enable round-robin at the DNS server level.D.Enable netmask ordering at the DNS zone level.
Options are :
- A,B
- A,C
- B,C
- C,D
Answer : A,C
You are the network administrator for your company. All servers on the company’s network runWindows Server 2008. You are required to install a Dynamic Host Configuration Protocol (DHCP) server on the network to enable client computers on the network to obtain IP addressautomatically from the DHCP server.You want to ensure that when you install the DHCP server, the server is automatically authorized.What should you do?
Options are :
- Install the DHCP server on a member server and the DHCP Relay Agent on the domain controller
- Install the DHCP server on a stand-alone server.
- Install the DHCP server on the domain controller.
- Install the DHCP server on a server that is member of the domain.
Answer : Install the DHCP server on the domain controller.
70-647 Pro Windows Server 2008 Enterprise Administrator Exam Set 1
Your organization is organized as a single Active Directory forest with one domain. All servers runWindows Server 2008. The headquarters contains a Windows Server 2008 DNS server that hostsan Active Directory-integrated zone. You install a Windows Server 2008 DNS server in a branchoffice with a standard secondary zone that pulls updates from the master server at headquarters.You receive complaints from users in the branch office that the WAN link between it andheadquarters is slow. You suspect that the bottleneck is produced by DNS zone replication traffic.What action should you perform?
Options are :
- Remove the secondary DNS server and deploy a RODC at the branch office.
- Enable Round-robin on the primary DNS server at headquarters.
- Decrease the Refresh interval on the SOA record in the primary DNS zone.
- Increase the Refresh interval on the SOA record in the primary DNS zone.
Answer : Increase the Refresh interval on the SOA record in the primary DNS zone.
Mark works as a Network Administrator for TestKing Inc. The company has a Windows Server2008 domain-based network. The network has a file server that runs on Windows Server 2008.Mark wants to secure all the important data so that only he can access the data. All the data isstored on a Windows Server 2008 member. As the data volume is large, it is kept in a compressedform on the NTFS partition. He decides to encrypt the data with the Encrypting File System (EFS) .When he attempts to encrypt the data, he is unable to do it. What is the most likely cause of theissue?
Options are :
- The data files are larger than 2MB.
- Windows Server 2008 does not support EFS.
- EFS does not support compression.
- Data is stored on NTFS file system.
Answer : EFS does not support compression.
Which of the following types of backup operations should be used to back up all the files that havechanged since the last full backup or incremental backup and mark these files as having beenbacked up?
Options are :
- Incremental
- Copy
- Differential
- Normal
Answer : Incremental
70-647 Pro Windows Server 2008 Enterprise Administrator Exam Set 2
You are the system administrator for a company that has purchased another company. The newcompany has several UNIX computers.You install a Windows 2008 Server Core server and several Windows Vista computers at the newcompany’s location. A proprietary application runs on some of the UNIX computers. You need toconfigure a print server on the Windows Server 2008 Server Core computer to enable users at theUNIX computers to print.What should you do?
Options are :
- Run Slmgr.vbs -ato.
- Run net start LPDSVC.
- Run Start /w ocsetup Printing-LPDPrintService.
- Run cscript scregedit.wsf /LDP /4.
Answer : Run Start /w ocsetup Printing-LPDPrintService.
Mark works as a Network Administrator for TestKing Inc. The company has a Windows Server2008 domain-based network. The network has a file server that runs on Windows Server 2008.His assistant wants to know about the wireless local area network (WLAN) SSID. Which of thefollowing statements are true about WLAN SSID?Each correct answer represents a complete solution. Choose three.A.All wireless devices on a wireless network must have different SSIDs.B.It has a maximum length of 32 characters.C.It is a sequence of alphanumeric characters.D.It is the name of a wireless local area network (WLAN).E.It has a maximum length of 24 characters.
Options are :
- B,C,D
- A,B,C
- D,B,A
- B,C,D
Answer : B,C,D
Mark works as a Network Administrator for TestKing Inc. The company has a Windows Server2008 domain-based network. The domain consists of four domain controllers, two Windows 2008member servers, and 100 Windows Vista and 50 Windows XP Professional client computers. Thenetwork has two subnets with subnet addresses 192.168.0.0/24 and 192.168.1.0/24. Mark wants to scan the computers in the network by using the Microsoft Baseline SecurityAnalyzer (MSBA) tool. All the computers that he wants to scan are in a single subnet192.168.0.0/24. Mark installs MBSA on a client computer named BSACOMP and runsMBSA.EXE. After scanning the computers, he finds that the report does not contain any data ofthe computers in the subnet 192.168.0.0/24. Mark wants to generate a report that includes resultsfrom all the computers in the subnet 192.168.0.0/24. What will he do to accomplish the task?
Options are :
- In the MBSA tool window, specify the subnet mask of the subnet 192.168.0.0/24.
- In the MBSA tool window, specify the IP address range from 192.168.0.1 to 192.168.0.254 and
start scanning. - In the MBSA tool window, specify NetBios names of all the computers in the subnet
192.168.0.0/24. - In the MBSA tool window, specify host names of all the computers in the subnet 192.168.0.0/24.
Answer : In the MBSA tool window, specify the IP address range from 192.168.0.1 to 192.168.0.254 and
start scanning.
70-642 Windows Server 2008 Network Infrastructure Exam Set 5
Your network consists of a single Active Directory domain in which all servers run Windows Server2008 and all client workstations run Windows Vista. You manage the network from anadministrative workstation named THOTH. You want to configure THOTH to receive Windowsevent log data from a domain controller named SERVER01. What actions should you perform? (Select two answers. Each correct answer represents a part ofa single solution).A.Run the winrm quickconfig command on SERVER01.B.Run the wecutil command on THOTH.C.Run the wecutil command on SERVER01.D.Run the winrm quickconfig command on THOTH.
Options are :
- C,D
- A,B
- B,C
- D,A
Answer : A,B
You are the network administrator for your company. The company’s network consists of WindowsServer 2008, Windows XP, and Windows Vista computers.Your company has a partner company with which you need to share applications using a virtualprivate network (VPN). You need to deploy the VPN on a Windows Server 2008 computer.Which service role should you install?
Options are :
- Terminal Services role
- Web Server (IIS) role
- Application Server role
- Network Policy and Access Service role
Answer : Network Policy and Access Service role
You are the network administrator for your company. You have recently installed Windows Server2008 for your company. You want to create a test network of five subnets that will use IPv6. Youhave to create the network in such a way that the client computers on the test network are able tocommunicate with each other while ensuring that they cannot access the Internet. In addition, theaddresses used should be unique across all sites within your company.Which IP address could you use?
Options are :
- FE80:AB10:2B5C:B000:: /64
- 0:0:0:0:0:0:0:0
- FEC0:AB10:2B5C:B000::/10
- FD00:AB10:2B5C:B000::/8
Answer : FD00:AB10:2B5C:B000::/8
70-642 Windows Server 2008 Network Infrastructure Exam Set 7
You are the network administrator for your company. You have installed Windows Server 2008 onall servers and Windows XP Professional Service Pack 2 (SP2) or Windows Vista on the clientcomputers in your company.Your company wants to restrict non-compliant computers from communicating on a network. Thecomputers must meet the system health requirements as stated in a corporate security statementbefore they connect to the network.Which role service should you install?
Options are :
- Terminal Services Licensing
- Routing and Remote Access Services
- Terminal Services Gateway
- Network Policy and Access Services
Answer : Network Policy and Access Services
You are the network administrator for your company. The network contains a single Windows2008 Active Directory domain. A Windows Server 2008 computer named Remote1 is a member Microsoft 70-642 Exam «Pass Any Exam. Any Time.» — www.actualtests.com 154 server with Routing and Remote Access installed. Remote1 allows both dial-up and virtual privatenetwork (VPN) connections.Smart cards are issued to all users who will access the network remotely. The smart cards will beused for both dial-up and VPN connections. All users who will access the network remotely areissued Windows 2000 Professional portable computers with smart card readers. The writtensecurity policy for your company states that the users are required to use the smart cards onlywhen connecting to the network remotely. When connecting to the network locally, smart cardsshould not be used.You must implement a remote access solution that will enforce the written security policy.What should you do?
Options are :
- Install a computer certificate on each computer. Configure the remote access policy on Remote1
to accept only EAP-TLS authentication. Use the computer certificate for authentication. - Install a computer certificate on Remote1. Configure the remote access policy on Remote1 to
accept only EAP-MD5 authentication. Use the Remote1 computer certificate for authentication. - Install a computer certificate on each computer. Configure the remote access policy on Remote1
to accept only EAP-MD5 authentication. Use the computer certificate for authentication. - In the Active Directory Users and Computers console, enable the Smart card is required for
interactive logon option for each user account that will access the network remotely. - Install a computer certificate on Remote1. Configure the remote access policy on Remote1 to
accept only EAP-TLS authentication. Use the Remote1 computer certificate for authentication.
Answer : Install a computer certificate on each computer. Configure the remote access policy on Remote1
to accept only EAP-TLS authentication. Use the computer certificate for authentication.
Your organization uses the IPv4 network address 172.16.30.0/22. All client computers in thedomain run Windows Vista. HostA (IP address 172.16.8.111, subnet mask 255.255.252.0) isunable to connect to HostB (IP address 172.16.12.23, subnet mask 255.255.252.0) when usingNetBIOS broadcasts. What is the most likely explanation of the problem?
Options are :
- HostA and HostB are using different default gateway addresses.
- HostA and HostB reside on different IP subnets.
- HostA and HostB are using an incorrect subnet mask.
- The network’s DHCP server is offline.
Answer : HostA and HostB reside on different IP subnets.
70-647 Pro Windows Server 2008 Enterprise Administrator Exam Set 1
You are the administrator for your organization. You have two groups, Sales and Marketing, whichuse a laser printer. The Sales group prints a lot of invoices and quotes for companies. TheMarketing group usually prints large presentations that take a long time to print. You want theSales group’s documents to print before the Marketing group. How do you set this up?
Options are :
- Assign the Marketing group a priority of 1 and the Sales group a priority of 100.
- Assign the Marketing group a priority of 1 and the Sales group a priority of 99.
- Assign the Marketing group a priority of 100 and the Sales group a priority of 1.
- Assign the Marketing group a priority of 99 and the Sales group a priority of 1.
Answer : Assign the Marketing group a priority of 1 and the Sales group a priority of 99.
You are the systems administrator of your company. The company’s network is configured to use Internet Protocol version 6 (IPv6). You install a Dynamic Host Configuration Protocol (DHCP) server on a server named DHCP1 that runs Windows Server 2008.
You want to ensure that neither IP addresses nor other configuration settings are automatically allocated to DHCP clients on a subnet that does not use DHCPv6 from DHCP1. How should you configure the Managed Address Configuration flag, and the Other Stateful Configuration flag in the router advertisements?
Options are :
- Set the Managed Address Configuration flag to 0 and the Other Stateful Configuration flag to 1.
- Set both Managed Address Configuration and Other Stateful Configuration flags to 1.
- Set both Managed Address Configuration and Other Stateful Configuration flags to 0 (zero).
- Set the Managed Address Configuration flag to 1 and the Other Stateful Configuration flag to 0.
Answer : Set both Managed Address Configuration and Other Stateful Configuration flags to 0 (zero).
You are the network administrator for your company. The network contains Windows Server 2008and Windows Vista computers. You are configuring FileSrv2 to forward Event Viewer events toSrv2.On FileSrv2, you run the winrm quickconfig command. Then on Srv2, you run the wecutil qccommand. Finally, you add the Srv2 account to the local Administrators group on FileSrv2.What should you do next?
Options are :
- Create a new subscription on FileSrv2.
- Create a custom view on Srv2.
- Create a custom view on FileSrv2.
- Create a new subscription on Srv2.
Answer : Create a new subscription on Srv2.
PIC Microcontroller Test Your Skills and Get Certified Set 1
Your corporate network consists of a single Active Directory domain. The network consists of 3domain controllers and 10 member servers, all of which run Windows Serve 2008. All clientcomputers in the domain run Windows Vista Enterprise. Due to security policy, the network is notconnected to the Internet. The network contains a server named DNS01 that hosts a standardprimary zone for the domain. You need to configure DNS01 such that if a DNS client queries for aname outside the company network, DNS01 will not attempt to contact DNS servers outside thenetwork.What action should you perform?
Options are :
- Disable recursion on DNS01.
- Ensure that DNS01 is not configured to use forwarders.
- Issue the command dnscmd /clearcache on DNS01.
- Remove root hints on DNS01.
Answer : Disable recursion on DNS01.
|
|
Цель данного теста — оценить знания и навыки слушателя в области эксплуатации сетевых служб и приложений на платформе Windows Server 2008 После прохождения теста сертификат тестирования не выдается Тест доступен после регистрации |
Статистика
|