Microsoft has been releasing Security baseline since the Windows XP days. Windows 10 is no exception to this, except now there’s a new release of security baseline following each major build of Windows 10. The concept of the Security Baseline is to provide Microsoft guidance for IT administrators on how to secure the operating system, by using GPOs, in the following areas :
- Computer security
- User security
- Internet Explorer
- BitLocker
- Credential Guard
- Windows Defender Antivirus
- Domain Security
Implementing the security baseline in GPOs is not a complex or long task. The challenge that the security baseline provide is that it will expose areas of the environment that are not secure.
This means that to follow all Microsoft security guidelines, it would be required to fix many other systems outside of Windows 10 to achieve this.
In this post, we will describe what is the Security baseline, how to use them and key points that will most likely be challenging for other systems in the environment
Prerequisites
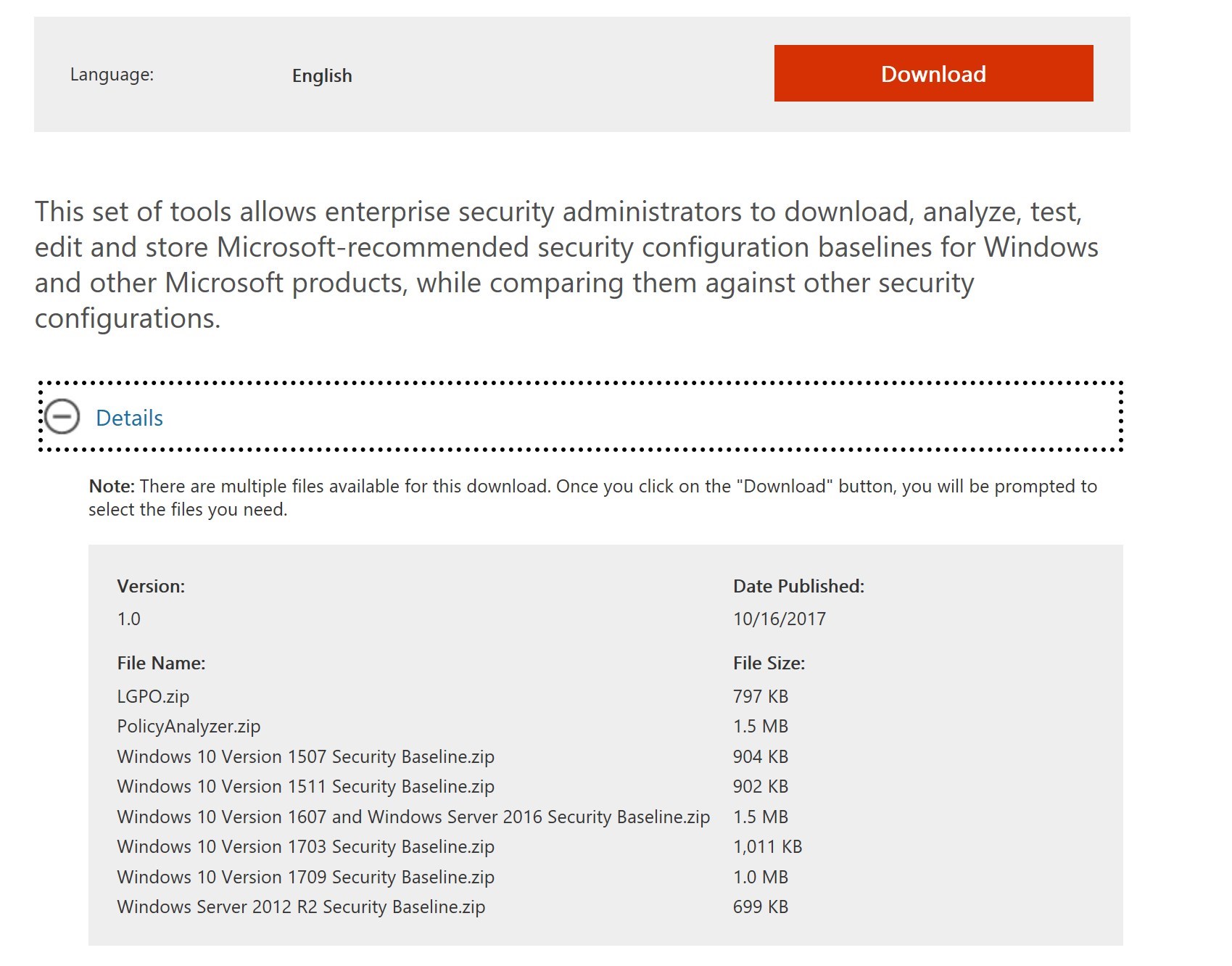
- Download the Security Baseline zip file that matches the Windows 10 version
- A new version is released for each Windows 10 major build. First in draft and then for production, in the same link
- Baselines are backward compatible, newer version provides mostly new GPOs to support Windows 10 newest features
- Security access for Group Policy Management
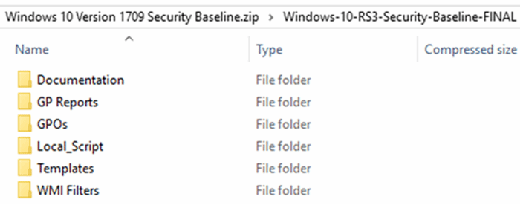
- The downloaded zip file contains all the required bits to help implement the baseline in your environment.
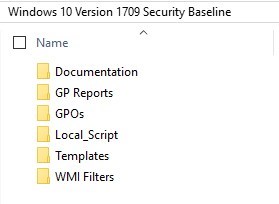
- Documentation folder contains a large Excel file with all the details of every configuration part of the baseline
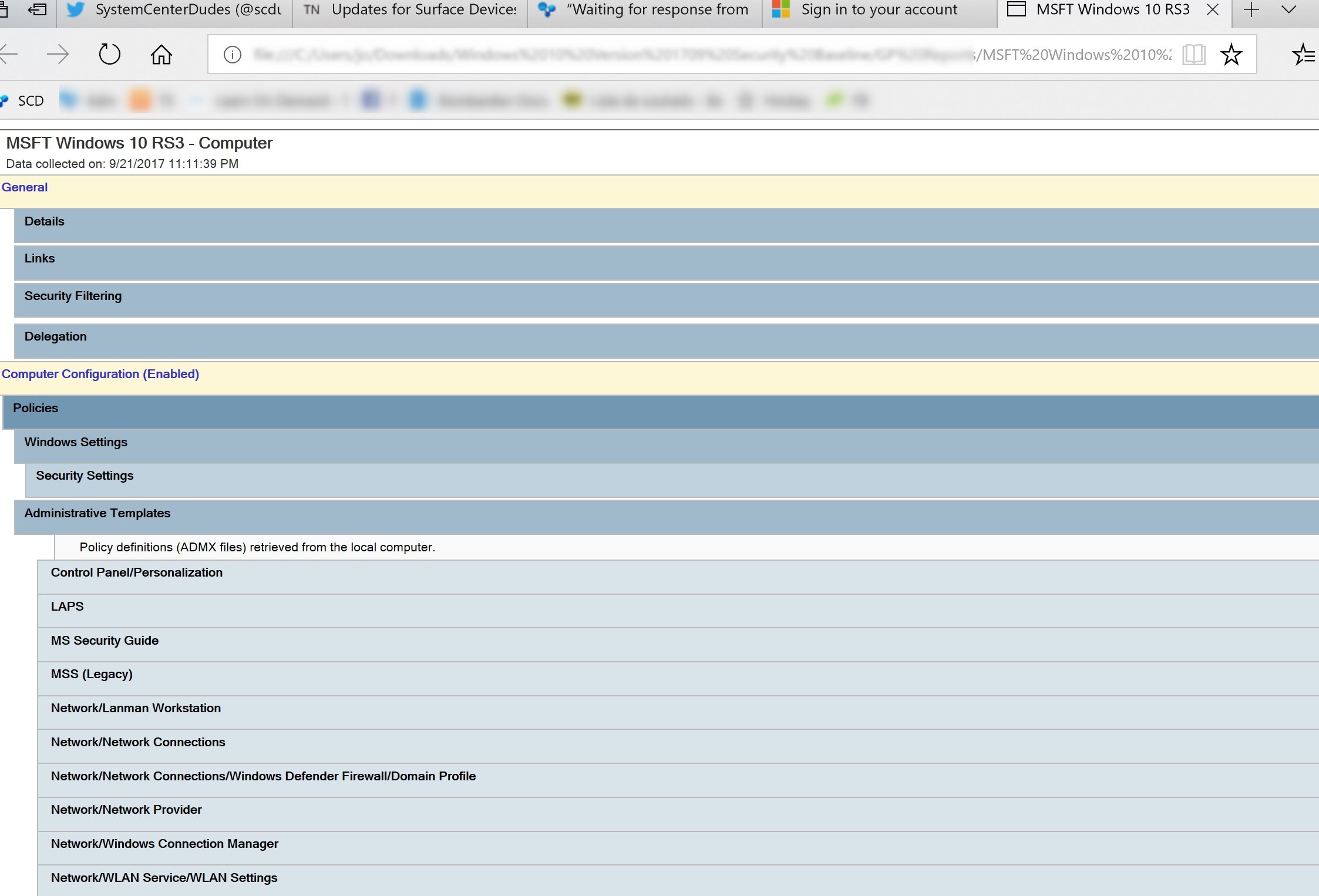
- GP Reports folder contains HTML report of GPO templates available as part of the Windows 10 Security Baseline
- GPOs folder contain the actual GPO files that can be imported in the Group Policy Management console
- Local_Script folder contains a script to install the security baseline into the local policy for Windows 10
- this is more for testing the actual configuration
- Templates contain ADML and ADMX files for additional settings in the GPOs
- WMI Filters folder contains two WMI filters: Windows 10 and Internet Explorer 11
How to use Windows 10 Security Baseline
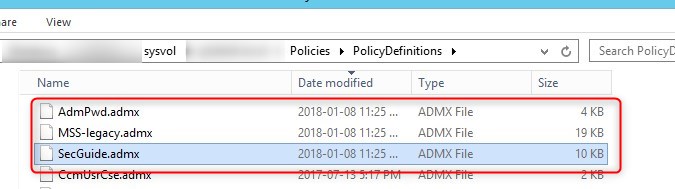
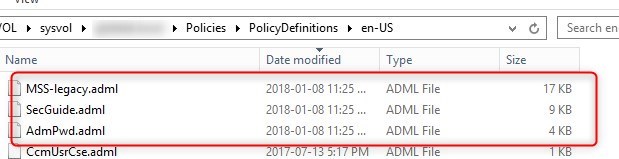
Add Templates to Central Store
- Copy the ADMX from the Templates to the GPO Central Store
- Copy the ADML from the templates to the GPO Central Store EN-US subfolder
Import GPOs
- Create a new blank GPO
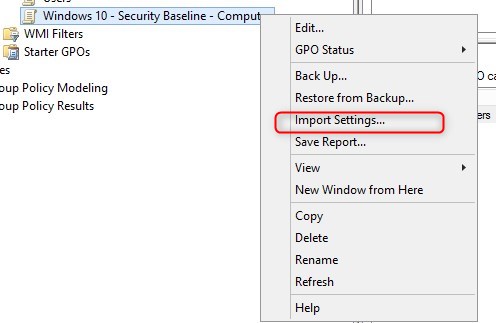
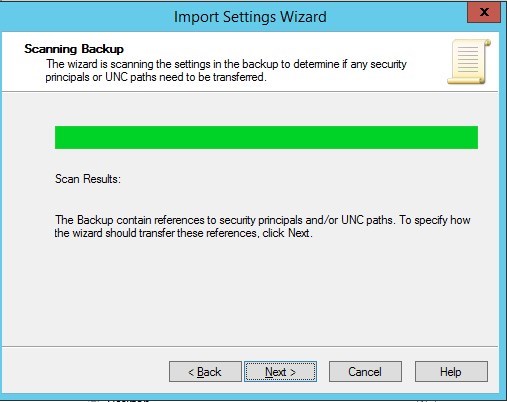
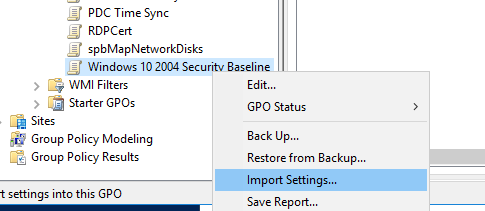
- Right-click on the GPO, and select Import Settings
- Click Next
- Click Next, no need to take a backup of a new blank GPO.
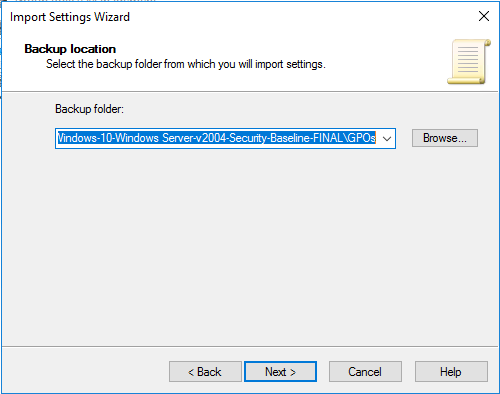
- Browse to the GPOs folder and click Next
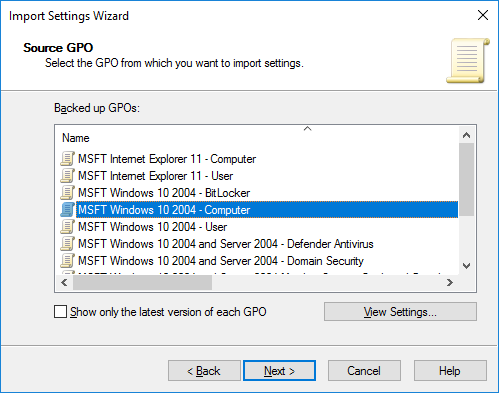
- Select the GPO to be imported, based on the name and click Next
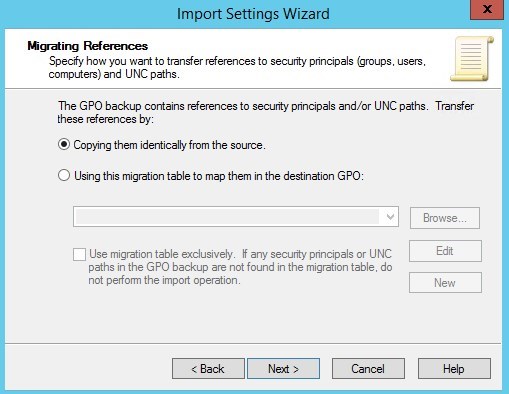
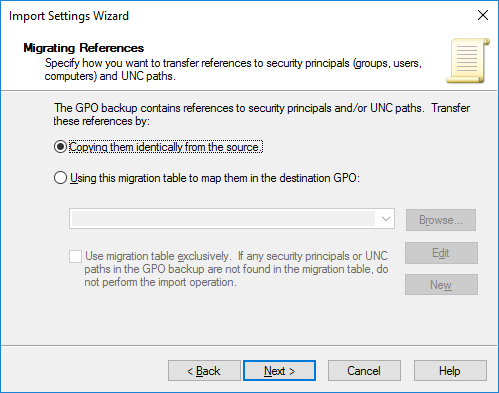
- Click Next
- Select Copying them identically from the source and click next
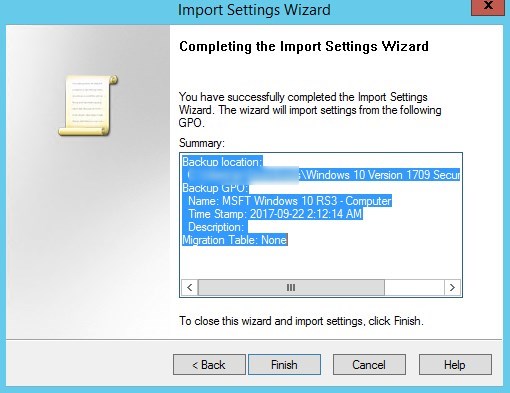
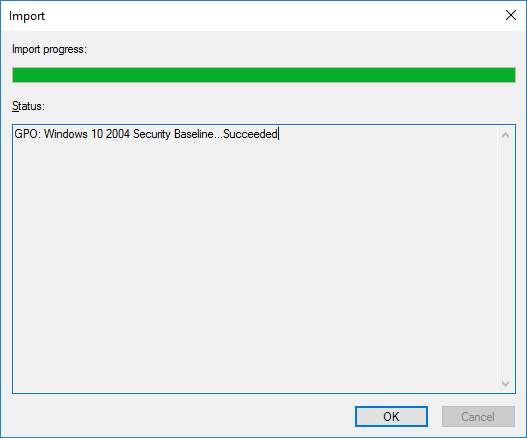
- Click Finish
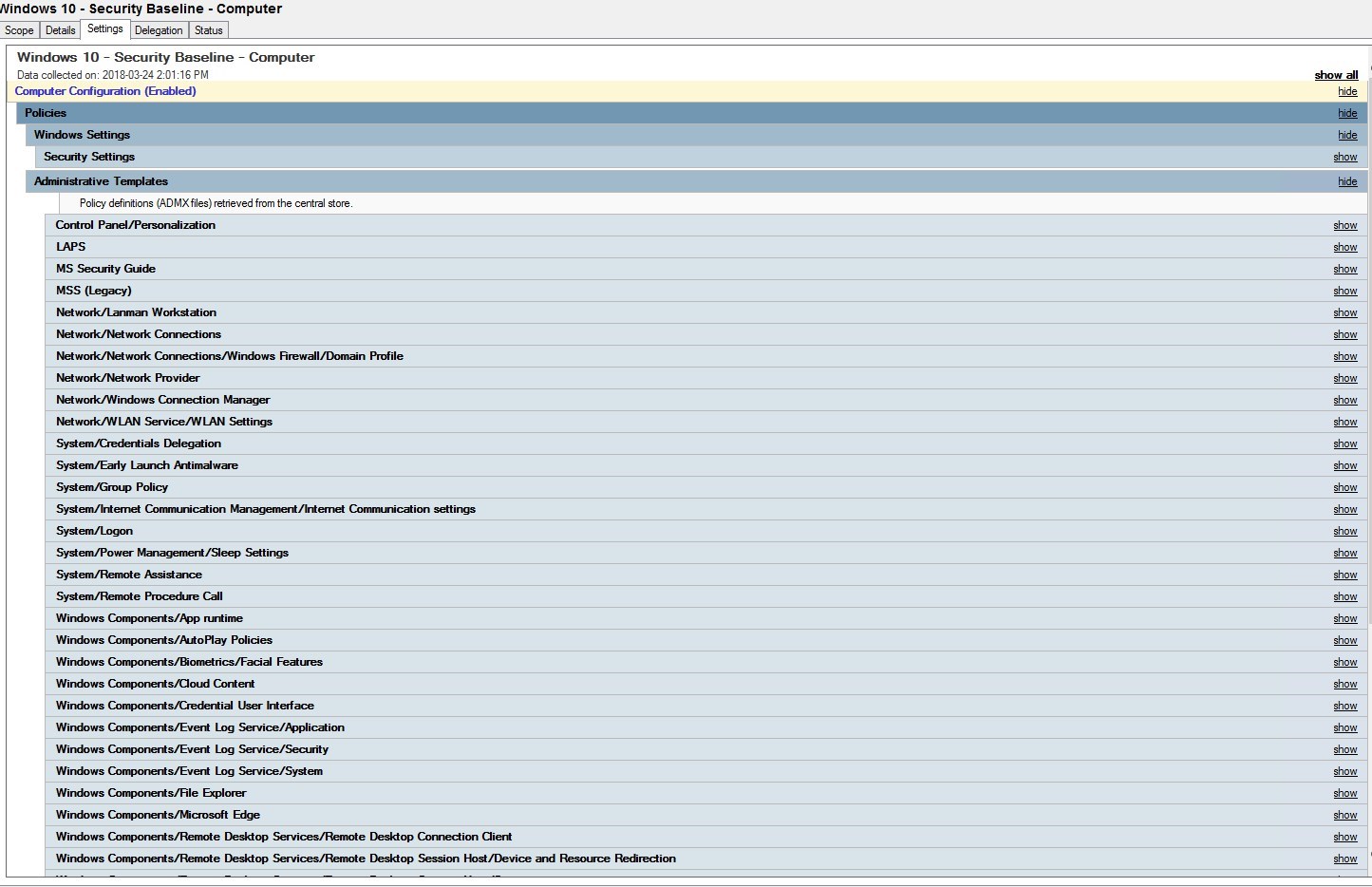
- Click the Settings tab to see all the configuration imported
Once the GPOs are imported, testing is key!
No magic trick here, start with test computers and then IT users/pilot users prior to applying this to production.
Key points that provide challenges
Here are some configurations that are part of the baseline that should be looked at up front as they might provide issues with your environment. The idea here is to have a better understanding of what is going on. Don’t go and change those settings to avoid issues. The issues should be fixed at the other end for better security.
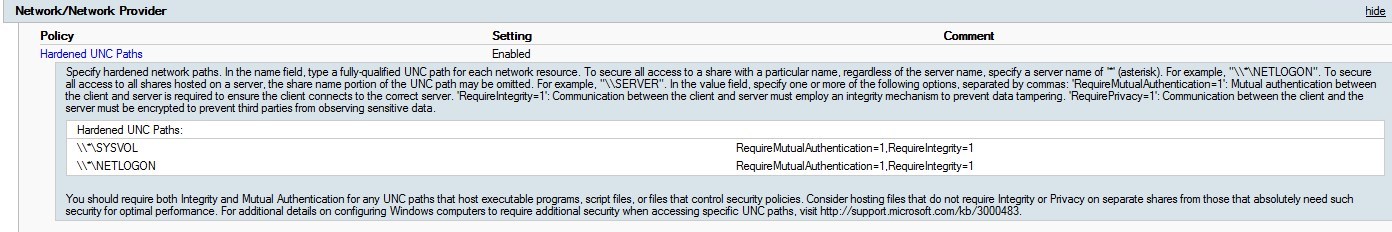
Hardened UNC path
This setting is likely to give the following error when trying to process GPO on Windows 10.
Error
The processing of Group Policy failed. Windows attempted to read the file \\yourdomain.fqdn\sysvol\yourdomain.fqdn\Policies\{GPO GUID}\gpt.ini from a domain controller and was not successful.
The configuration Computer/Administrative Template/Network/Network Provider/Hardened UNC Path
Review the following post by Lee Stevens for details on the UNC hardening path to help define this setting for your environment
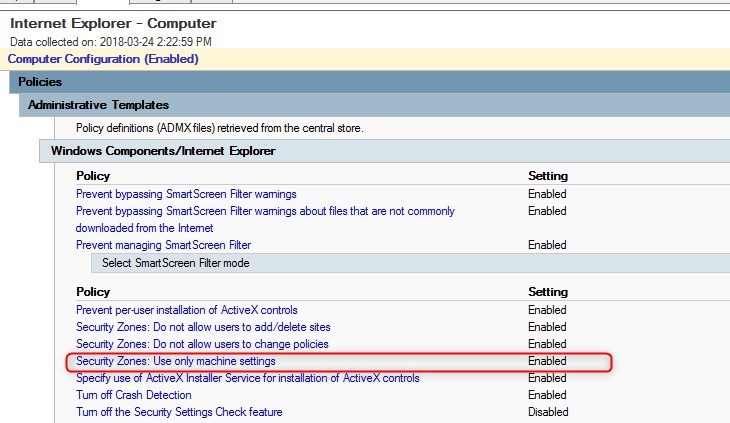
Internet Explorer process only computer GPO
If you have user GPO for Internet Explorer, in the Security Zone, adding the baseline for Internet Explorer will prevent those settings to be applied.
Two options are available if this causes issue:
- Move your Internet Explorer configuration to computer GPO instead of user GPO
- Change the configuration back to Not Configured for this GPO
More details on this KB from Microsoft
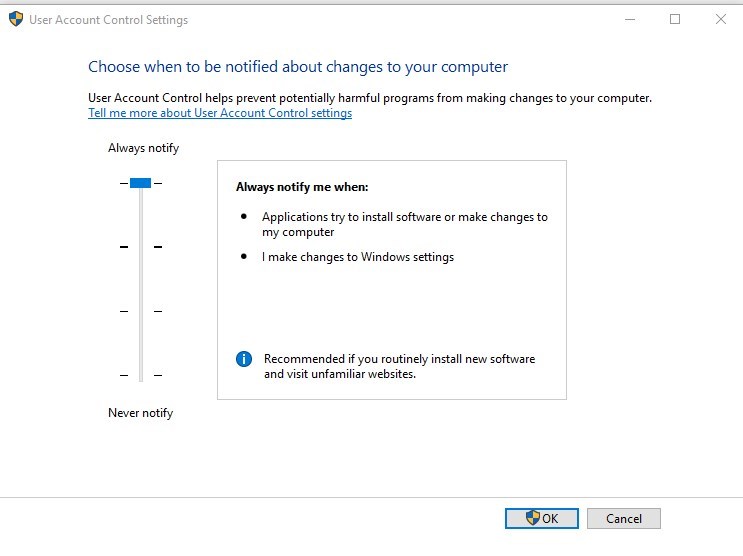
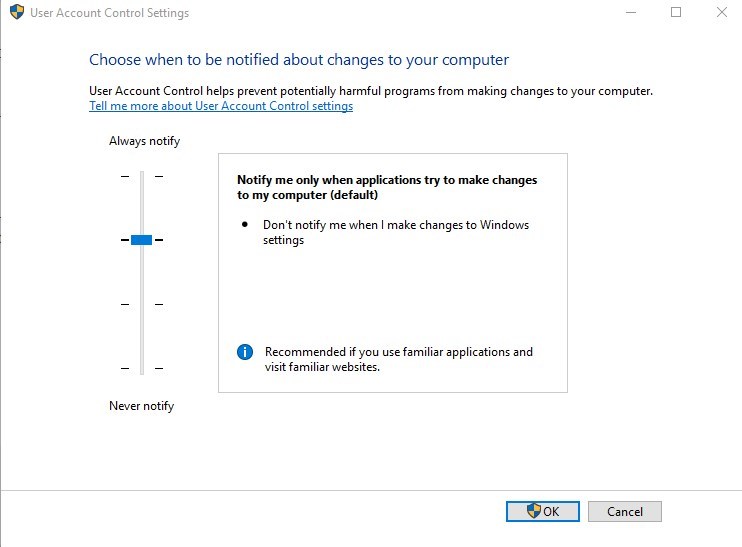
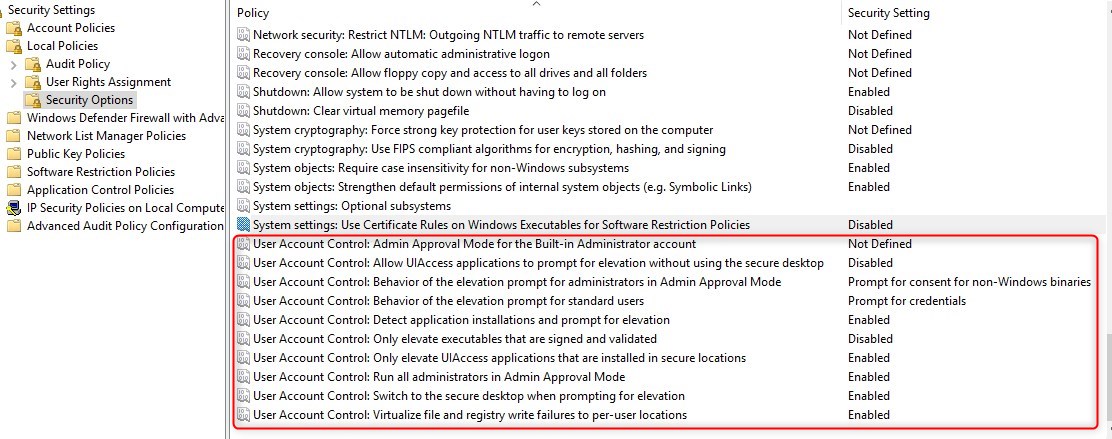
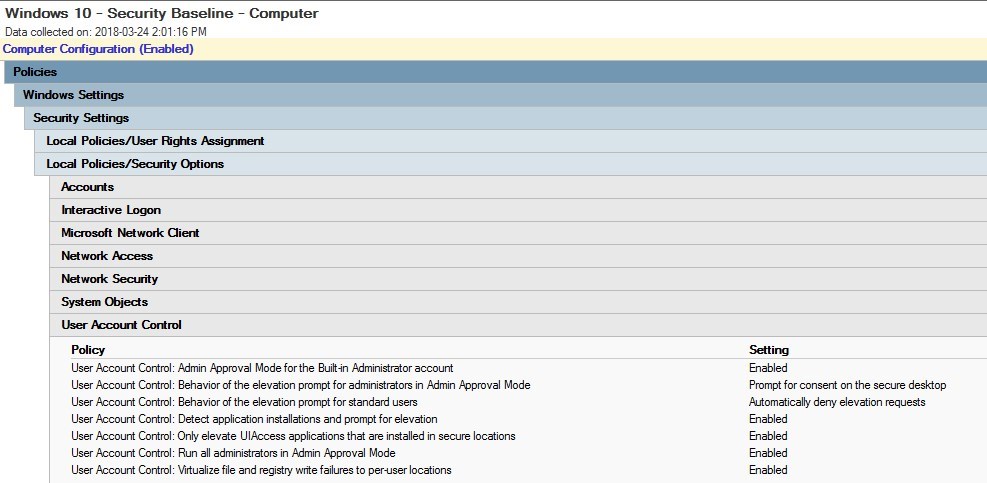
User Account Control
The user account control (UAC) is configured to the maximum level with the Security Baseline.
The default Windows 10 level is set to Notify me only when applications try to make changes to my computer (level 3 out of 4)
This is configured by a local security policy
To modify the GPO, under the Windows 10 Computer GPO Computer/Windows Settings/Security Settings/Local Policies/Security Options/User Account Control
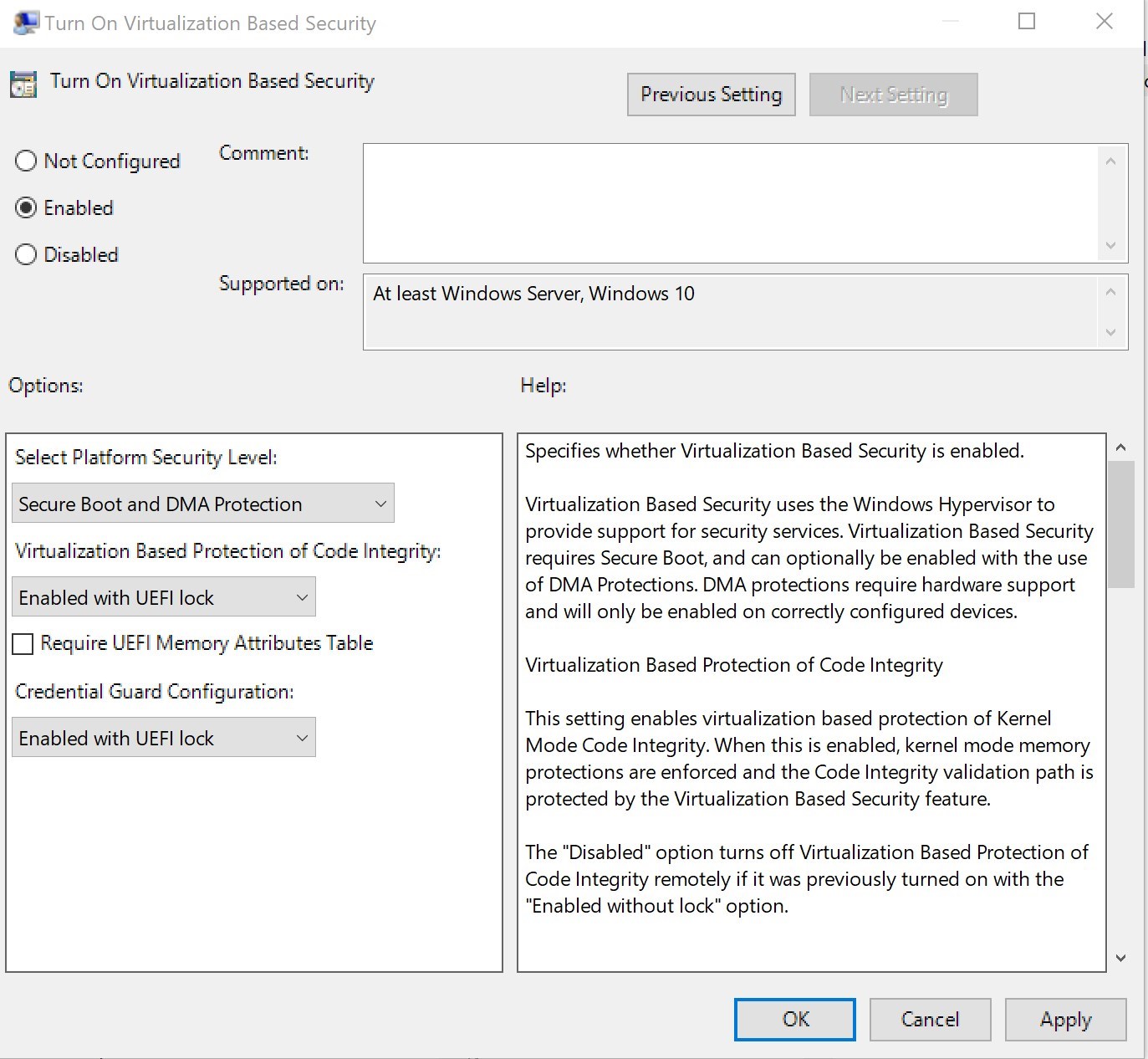
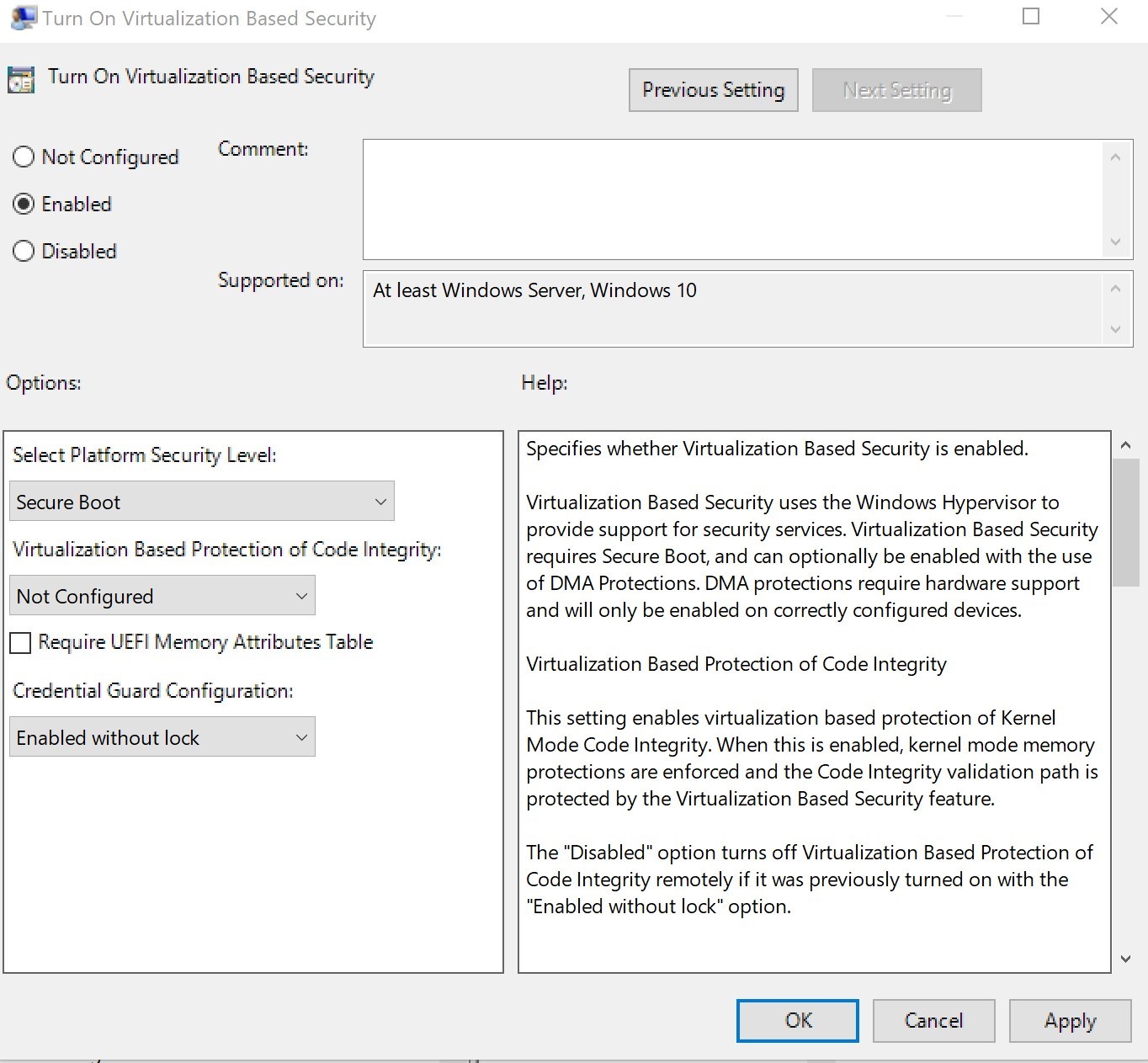
Credential guard
Having Credential guard in Windows 10 is categorized as a quick win solution as the requirement and setup is easy.
The default configuration as part of MSFT Windows 10 and Server 2016 – Credential Guard GPO is configured in a way that is likely to crash the computer or have an undesired requirement for future needs if applied as is.
We strongly recommend to carefully read the Help section of the Computer/Administrative Templates/System/Device Guard/Turn On Virtualization based security GPO
To take advantage of Credential Guard safely, this would be the required configuration.
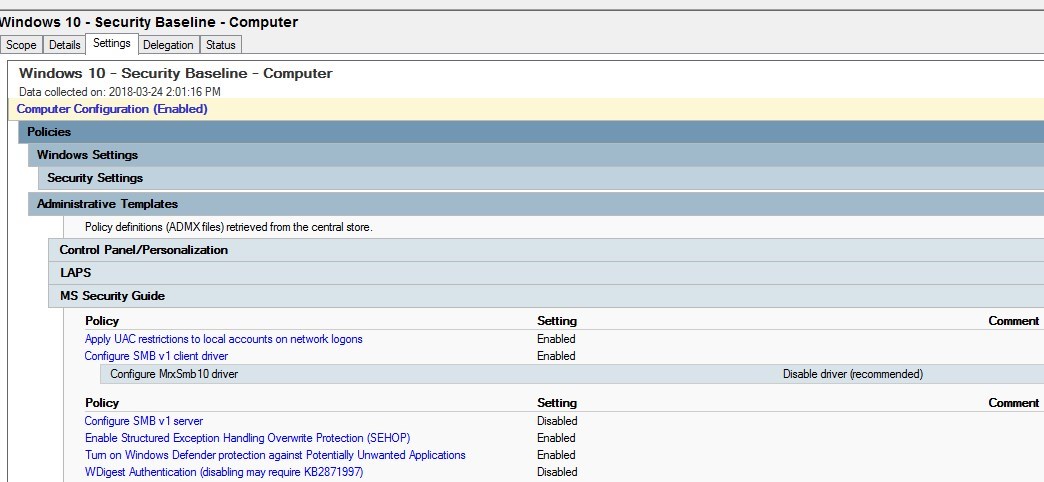
SMB v1
This topic is the most important of all key points. With Windows 10 v1709, SMB v1 is disabled by default. But what if you still need this in your environment?
Let me make this clear, we do not recommend enabling SMB v1. It has been proven to be one of the most critical security hole as of late with malware like WannaCry.
On the other hand, sometimes we don’t have much choice to go against security.
So to leave SMB v1 enabled as part of the security baseline GPO, we suggest reading the following blog post by Aaron Margosis
The GPO settings for SMB v1 are under Computer/Administrative Templates/MS Security Guide
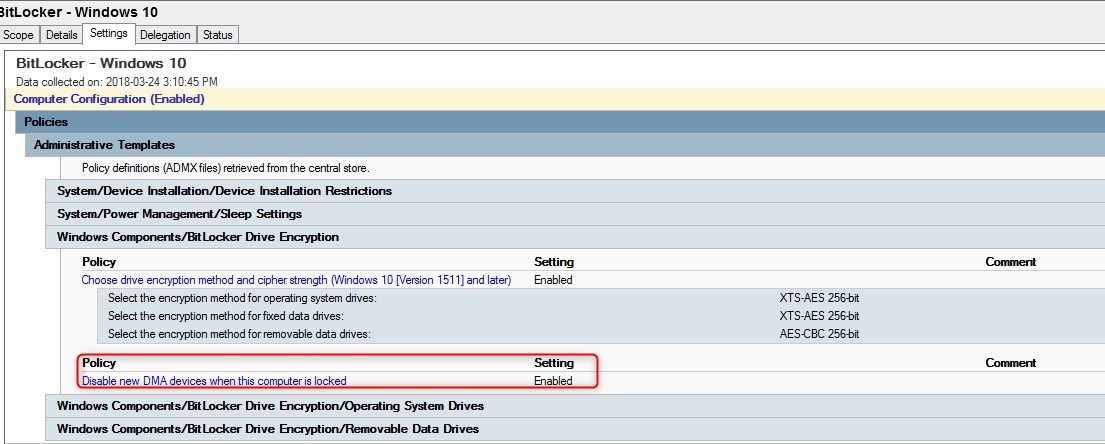
Issue with BitLocker on Windows 10 1709
The MSFT Windows 10 RS3 – BitLocker GPO contains a setting to Disable new DMA devices, that broke some computer.
See the following blog post by Aaron Margosis for details on the issue.
The setting Computer/Administrative Templates/Windows Components/BitLocker Drive Encryption/Disable new DMA devices when this computer is locked, should be reviewed prior to being applied.
What to do when a new version of Security baseline is available?
A new version of Security baseline usually come out at the same time as a Windows 10 build goes RTM.
Microsoft has always released them as a DRAFT version that goes on for a couple months and then release the FINAL version.
Here’s a checklist for what to do when the new version is available :
- Start by reviewing the Excel file to see what’s new to the baseline
- Most of the new settings in the baseline will be in line with new features as part of the Windows 10 release
- Update ADMX in the Central store with the ones from the latest Windows 10 build prior to adding new settings
- New settings should then be added to your environment by one of the following :
- Import the new GPOs
- Add new settings to current GPO
Follow us on Twitter to get a notification when a new version of the Security baseline is released.
Bonus Tip
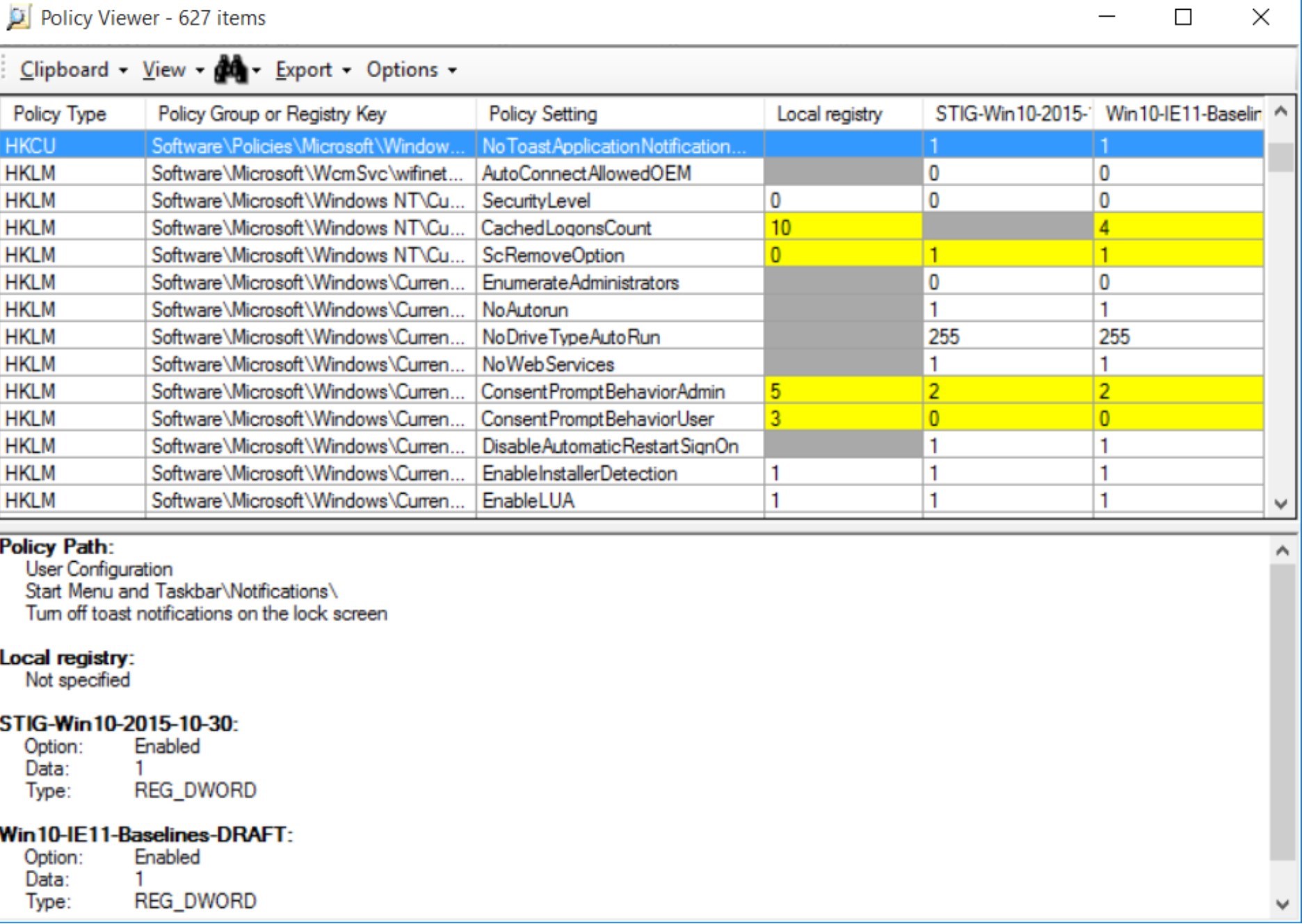
The Policy Analyzer is a great tool to compare current GPOs against the ones from the Security Baseline.
This can give an idea of the conflicting settings as well as additional settings from the Security Baseline
A set of Group Policy configurations is called a Group Policy Object (GPO). A version of Group Policy called Local Group Policy (LGPO or LocalGPO) allows Group Policy Object management without Active Directory on standalone computers. Group policy can be launched via “gpedit.msc” locally or just by typing “gpedit” to launch the Local group policy console. In this guide, I will be discussing some new group policies that are being added to Windows 10 21H1. They are as follows “show or hide the Most used list from Start menu, Not allow sideloaded apps to auto-update in the background, Not allow sideloaded apps to auto-update in the background on a metered network, Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria, Do not allow location redirection, and Specify source service for specific classes of Windows Updates”.
For other articles I have written on GPO, see the following link. See this guide if you ever wanted to know what group policies are enabled or analyze GPO computers, Why use RSAT? How to Install RSAT on Windows 10, Remote Server Administration Tools: To install RSAT on Windows Server, and what is Group Policy Object and how can it be launched in Windows.
Windows 10, version 21H1 is a client only release. Windows Server, version 20H2 is the current Windows Server Semi-Annual Channel release and per our lifecycle policy is supported until May 10, 2022. This Windows 10 feature update brings very few new policy settings. At this point, no new 21H1 policy settings meet the criteria for inclusion in the security baseline. We are, however, refreshing the package to ensure the latest content is available to you. The refresh contains an updated administrative template for SecGuide.admx/adml that are released with Microsoft 365 Apps for Enterprise baseline. Also, Microsoft CEO has announced new changes that will be introduced in Windows10. Here is a link for more information. Windows 10 has an option that lets you hide the apps list in the Start menu. This policy can be found in the following area below.
Computer Configuration > Administrative Templates > Start Menu and Taskbar.
Via Windows Settings: These settings can also use the Start settings page to hide the all apps list from the menu for a more compact and personal design as shown in the image below. To do this follow the steps discussed here. Open Settings, and click on Personalisation.
– Turn on or off the Show app list in the Start menu toggle switch.
If you enable this policy setting, you can configure the Start menu to show or hide the list of used apps. The Start menu will only display the tiles section henceforth. However, the menu will now include two buttons in the top-left corner to switch between all apps and pinned tiles sections.
Both the “Not allow sideloaded apps to auto-update in the background on a metered network” and “Not allow sideloaded apps to auto-update in the background” can be accessed and configured via the Computer Configuration > Administrative Templates > Windows Components.
Computer Configuration > Administrative Templates > Windows Components > App Package Deployment.
Disable auto-update for sideloaded apps
Below are the respective settings for “Not allow sideloaded apps to auto-update in the background on a metered network” and “Not allow sideloaded apps to auto-update in the background“.
Apply layered order of evaluation to Allow and Prevent device installation policies across all device match criteria: Additionally, When this policy setting is enabled, Windows is allowed to install or update any device whose Plug and Play hardware ID or compatible ID appears in the list you create unless another policy setting at the same or higher layer in the hierarchy specifically prevents that installation, such as the following policy settings:
– Prevent installation of devices that match these device IDs
– Prevent installation of devices that match any of these device instance IDs
If the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting is not enabled with this policy setting, then any other policy settings specifically preventing installation will take precedence.Therefore, Both the “Do not allow location redirection” and the “Allow UI Automation redirection” can be found under Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host. This policy can be found in the following area below.
Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Device and Resource Redirection
Do not allow location redirection:
This policy setting lets you control the redirection of location data to the remote computer in a Remote Desktop Services session.
– By default, Remote Desktop Services allows redirection of location data.
– Similarly, users cannot redirect their location data to the remote computer if you enable this policy setting.
– Nevertheless, Users can redirect their location data to the remote computer if you disable or do not configure this policy setting.
Allow UI Automation redirection: This policy setting determines whether User Interface (UI) Automation client applications running on the local computer can access UI elements on the server. Furthermore, UI Automation gives programs access to most UI elements, which lets you use assistive technology products like Magnifier and Narrator that need to interact with the UI to work correctly. However, UI information also allows automated test scripts to interact with the UI.
Security Baseline: Moreover, Microsoft announced the final release of the Windows 10, version 21H1 (a.k.a. May 2021 Update) security baseline package, which can be downloaded from the Microsoft Security Compliance Toolkit. Nonetheless, you can test the recommended configurations and customize/implement them as appropriate in your environment.
I hope you found this blog post helpful. Consequently, Please let me know in the comment session if you have any questions.
The Security Baseline for Windows 10 Version 21H2 has been officially released and is ready for the sysadmins to download, install, and begin Microsoft-recommended configurations.
A Security Baseline is an additional set of security enhancements that can be added to the original security protocols already in place in Windows. This is especially useful for the companies and organizations that prefer to take more control of their virtual security.
This Baseline adds ransomware protection for your operating system and other new policies discussed below.
Table of contents
- New in Windows 10 Version 21H2 Security Baseline
- Removed Microsoft Edge Legacy Policies
- Restrict Printer Driver Installation
- Tamper Protection Included
- Download and Install Windows 10 Version 21H2 Security Baseline
- Closing Words
New in Windows 10 Version 21H2 Security Baseline
Removed Microsoft Edge Legacy Policies
Since Microsoft Edge Legacy had reached the end of support earlier this year, Windows 10 v21H2 came with only Edge Chromium. Therefore, policies for Edge Legacy have not been included with this Security Baseline.
Restrict Printer Driver Installation
Sysadmins can now prevent users with administrative rights from installing printer drivers. This addition has been included in light of a remote code execution vulnerability (CVE-2021-34527) codenamed “PrintNightmare.”
System administrators can find the Group Policy “Limits print driver installation to Administrators” at the following location within the Group Policy Editor after installing this Security Baseline:
Local Computer Policy >> Computer Configuration >> Administrative Templates >> Printers
When enabled, users with administrative privileges will no longer be able to update printer drivers.
Tamper Protection Included
Administrators can now secure their devices by enabling Microsoft Defender for Endpoint’s Tamper Protection. Enabling it will block human-operated ransomware attacks by making the necessary changes in Windows Registry so a program cannot make unauthorized changes to the operating system’s security features.
Enabling this option will prevent the attackers from performing the following tasks:
- Disable Virus and threat Protection
- Disable Real-Time Protection
- Switch off Behavior Monitoring
- Disable antivirus
- Remove security updates
- Disable automatic actions upon threat detection
You can enable Tamper Protection from the following path after installing this Security Baseline:
Settings app >> Update and Security >> Windows Security >> Virus and threat protection >> Virus and threat protection settings (Manage Settings)
Download and Install Windows 10 Version 21H2 Security Baseline
Follow the guide below to install the new Security Baseline on your Windows 10 device:
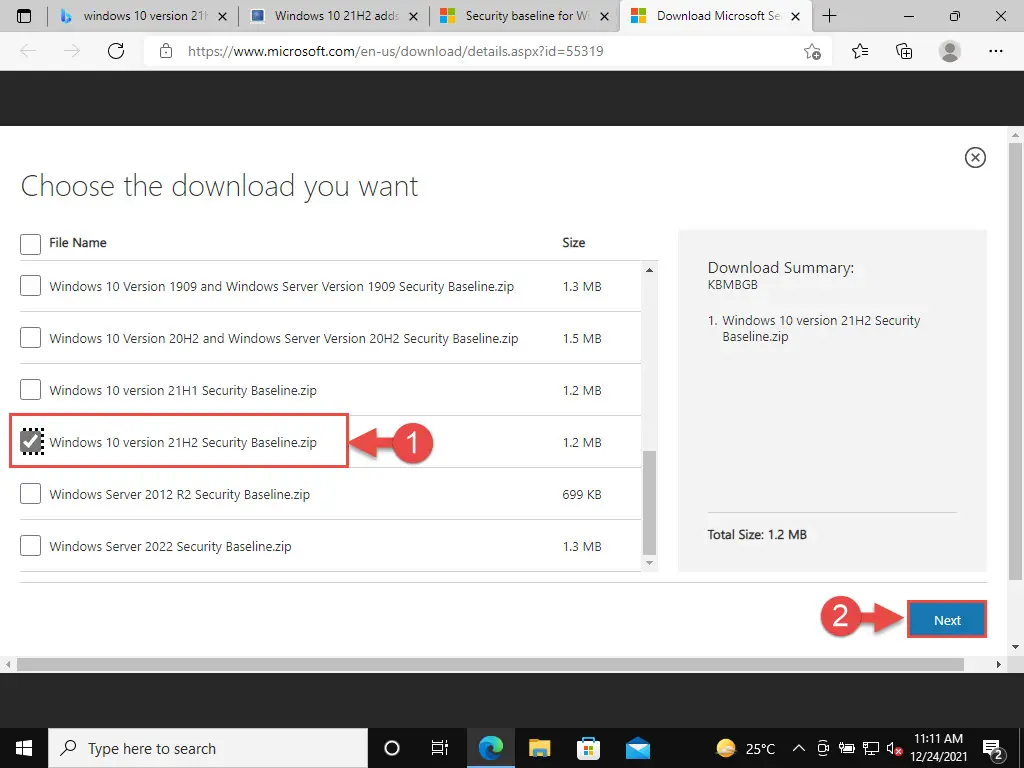
Check your current OS version by typing in winver in Run.
- Open the Microsoft Security Compliance Toolkit page and click Download.
- Check the box next to “Windows 10 version 21H2 Security Baseline.zip” and click Next.
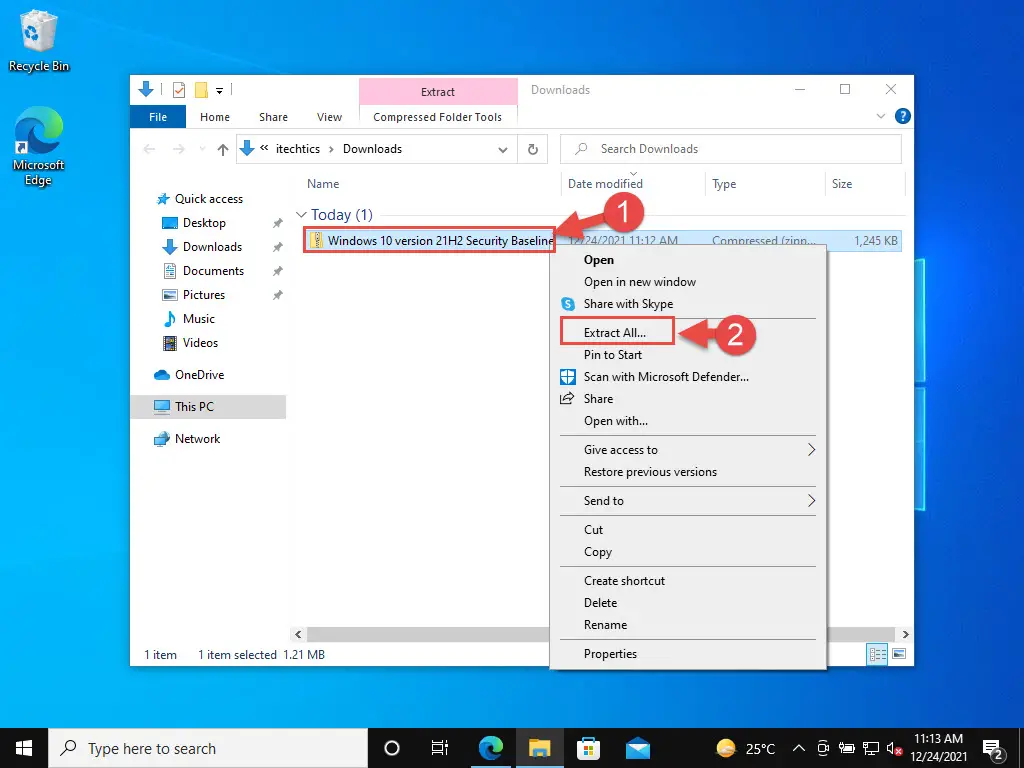
- Windows 10 Security Baseline will now download. Since it is of only 1.2 MBs, it should be downloaded instantly. Extract the content of the zip file to a folder.
- Now navigate to the extracted folder using File Explorer and open the Scripts sub-folder. Here you will find 3 PowerShell ISE files. Right-click any one of those files and then click Run with PowerShell from the context menu.
- If prompted with a Smart Screen notification, click Run.
- If asked for a confirmation via PowerShell, type in “A” and press Enter to choose “Yes to All.”
- Now repeats steps 4, 5, and 6 for the the remaining 2 PowerShell ISE files.
Once all 3 files are executed via Windows PowerShell, Windows 10 version 21H2 Security Baseline will be installed successfully. You may now begin configuring the new changes introduced with this Baseline.
Closing Words
Security Baselines are an optional update for your operating system’s security. If you are an individual user and not part of an organization, you could also benefit from such Baselines by preventing other users on your PC from performing tasks that could potentially expose the system to outside threats.
В Microsoft Security Baseline содержатся рекомендованные настройки, которые Microsoft предлагает использовать на рабочих станциях и серверах Windows для обеспечения безопасной конфигурации для защиты контролеров домена, рядовых серверов, компьютеров и пользователей. На основе Microsoft Security Baseline разработаны эталонные групповые политики (GPO), которые администраторы могут использовать в своих доменах AD. Настройки безопасности в групповых политиках Microsoft Security Baseline позволяют администраторам обеспечить уровень защиты корпоративной инфраструктуры Windows, соответствующий актуальным мировым стандартам. В этой статье мы покажем, как внедрить групповые политики на основе Microsoft Security Baseline в вашем домене.
Эталонные политики Microsoft Security Baseline входят в состав продукта Microsoft Security Compliance Manager (SCM). SCM это бесплатный продукт, в который входит несколько инструментов для анализа, тестирование и применения лучших и актуальных рекомендаций безопасности для Windows и других продуктов Microsoft.
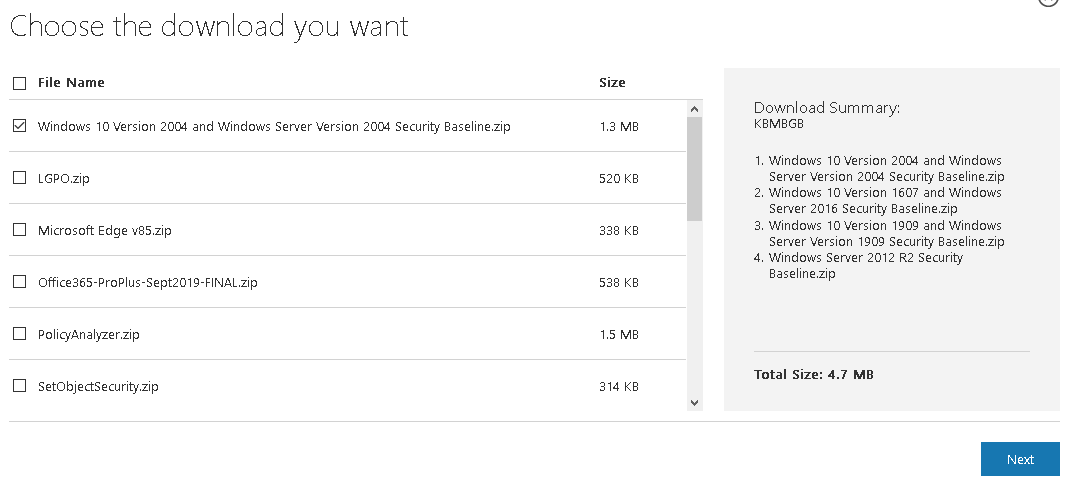
Microsoft Security Compliance Toolkit доступен по ссылке https://www.microsoft.com/en-us/download/details.aspx?id=55319. На данный момент в Security Compliance Toolkit доступны Baseline для следующих продуктов:
- Windows 10 Version 2004 and Windows Server Version 2004;
- Windows 10 Version 1909 and Windows Server Version 1909;
- Windows 10 Version 1903 and Windows Server Version 1903;
- Windows 10 Version 1809 and Windows Server 2019;
- Microsoft Edge v85;
- Office365 ProPlus;
- Windows Server 2012 R2.
Также можно скачать утилиты:
- LGPO – используется для управления настройками локальной политики;
- PolicyAnalyzer – инструмент для анализа имеющихся групповых политик и сравнения их с эталонными политиками в Security Baseline;
- SetObjectSecurity.
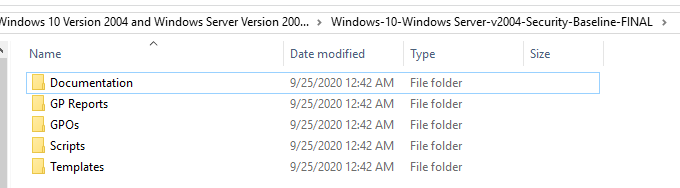
Архив с Security Baseline для каждой версии Windows содержит несколько папок:
- Documentation – xlsx и docx файлы с подробным описанием настроек, которые применяются в данном Security Baseline;
- GP Reports – html отчеты с настройками GPO, которые будут применены;
- GPOs – каталог с готовыми объектами GPO для различных сценариев. Данные политики можно импортировать в Group Policy Management console;
- Scripts – PowerShell скрипты для упрощения импорта настроек GPO в доменные или локальные политики): Baseline-ADImport.ps1, Baseline-LocalInstall.ps1, Remove-EPBaselineSettings.ps1, MapGuidsToGpoNames.ps1;
- Templates – дополнительные admx/adml шаблоны GPO (например, AdmPwd.admx – настройки управления локальными паролями для LAPS, MSS-legacy.admx, SecGuide.admx).
В доменной среде Active Directory проще всего внедрить Security Baseline через групповые политики (в рабочей группе можно применять рекомендованные настройки безопасности через локальную политику с помощью утилиты LGPO.exe) .
Есть шаблоны GPO Security Baseline для различных элементов инфраструктуры Windows: политики для компьютеров, пользователей, доменных серверов, контроллеров домена (есть отдельная политика для виртуальных DC), настройки Internet Explorer, BitLocker, Credential Guard, Windows Defender Antivirus. В папке GPOs хранятся готовые GPO политики для различных сценариев использования Windows (далее перечислен список GPO для Windows Server 2019 и Windows 10 1909):
- MSFT Internet Explorer 11 — Computer
- MSFT Internet Explorer 11 — User
- MSFT Windows 10 1909 — BitLocker
- MSFT Windows 10 1909 — Computer
- MSFT Windows 10 1909 — User
- MSFT Windows 10 1909 and Server 1909 — Defender Antivirus
- MSFT Windows 10 1909 and Server 1909 — Domain Security
- MSFT Windows 10 1909 and Server 1909 Member Server — Credential Guard
- MSFT Windows Server 1909 — Domain Controller Virtualization Based Security
- MSFT Windows Server 1909 — Domain Controller
- MSFT Windows Server 1909 — Member Server
Обратите внимание, что для каждой версии Windows Server или билда Windows 10 есть собственный набор Security Baseline.
Распакуйте архив с версией Security Baseline для нужной версии Windows и запустите консоль управления доменными групповыми политиками Group Policy Management (gpmc.msc).
- Скопируйте ADMX шаблоны в центральное хранилище GPO (Central Store) PolicyDefinitions на DC;
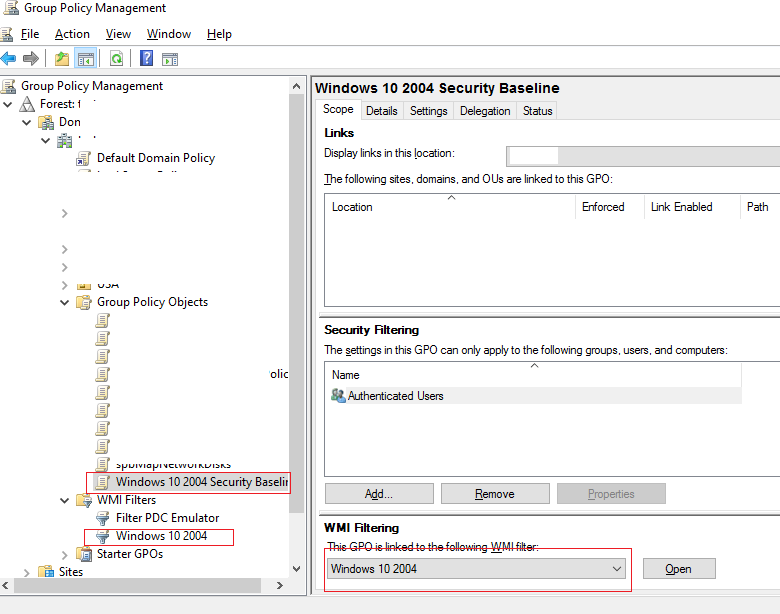
- Создайте новую политику с названием Windows 10 2004 Security Baseline;
- Щелкните по новой GPO правой кнопкой и выберите Import Settings;
- В качестве Backup Location укажите путь к файлу с Security Baseline для нужной версии Windows (например, C:\distr\SCM\Windows 10 Version 2004 and Windows Server Version 2004 Security Baseline\Windows-10-Windows Server-v2004-Security-Baseline-FINAL\GPOs);
- Перед вами появится список шаблонов политик. В нашем случае я импортирую политику с настройками компьютера. Выберите политику MSFT Windows 10 2004 – Computer (с помощью кнопки View Settings можно посмотреть настройки политики в виде отчета gpresult);
- Далее предлагается указать как нужно переносить ссылки на объекты безопасности и UNC пути. Т.к. политика у нас чистая, выберите пункт Copying them identically from the source;
- После этого настройки эталонной политики Security Baseline для компьютеров с Windows 10 2004 будут импортированы в новую GPO.
Чтобы применить данную политику только для компьютеров с нужной версией Windows, нужно использовать WMI фильтры GPO. Например, для Windows 10 2004 можно использовать такой WMI фильтр:
Select Version,ProductType from Win32_OperatingSystem WHERE Version LIKE "10.0.19041%" and ProductType = "1"
Примените данный фильтр к вашей политике.
Аналогично можно импортировать Security Baseline для пользователей, контроллеров домена, рядовых серверов и т.д.
Перед применением Security Baseline на компьютеры пользователей, нужно внимательно проверить предлагаемые настройки и сначала применить на OU с тестовыми пользователями или компьютерами. При необходимости, вы можете в политике отключить некоторые настройки, которые предлагаются в Security Baseline.Только после успешного испытания настроек Security Baseline на тестовых компьютерах можно применять настройки для всех компьютеров/серверов в домене.
В Security Baseline содержаться десятки и сотни настроек. Рассмотреть их все в рамках одной статье довольно сложно. Рассмотрим настройки безопасности, которые так или иначе мы рассматривали в рамках других статей сайта:
- Управление правилами запуска и установки программ: AppLocker (SRP), UAC и Windows Installer
- Политики паролей и блокировки учетных записей
- Ограничения административных аккаунтов
- Ограничение анонимного доступа
- Настройки политик аудита для получения информации о всех событиях и входов пользователей
- Защита памяти LSA (для
- Доступ к периферийным устройствам (в том числе политики установки принтеров и USB)
- Отключение NetBIOS и NTLM
- Настройки Remote Assistance, теневых подключений, таймаутов RDS, параметров CredSSP Oracle Remediation
- Политика запуска скриптов PowerShell
- Настройка Windows Error Reporting
- Управление правилами Windows Firewall
- Настройки WinRM
- Отключение встроенного администратора
- Политика Hardened UNC paths
- Отключение SMBv1
Если вы хотите защитить более надежно защитить свой домашний компьютер с Windows 10, вы можете применить на нем политики Security Baseline с помощью готового PowerShell скрипта.
Разрешите запуск неподписанных скриптов:
Set-ExecutionPolicy -ExecutionPolicy
Примените политику:
Baseline-LocalInstall.ps1 -Win10NonDomainJoined.
Политики Security Baseline позволяет существенно повысить защищенность инфраструктуры Windows и гарантировать, что одинаковые настройки применяются на всех (в том числе новых) компьютерах в сети.
IT should consider following Microsoft’s Windows 10 security recommendations in the Security Compliance Toolkit to better protect the operating system.
Many organizations lack security standards across their desktop deployments, and across all Microsoft products…
and platforms for that matter.
If IT professionals really want to shore up the gaps and weaknesses in their security standards, they must check out and integrate Microsoft’s Security Compliance Toolkit and its Windows 10 security baselines. The baselines go beyond common endpoint security controls, such as malware protection, and they are a gold mine for security guidance in Windows 10.
What are the Windows 10 security baselines?
Based on expert feedback from both inside and outside Microsoft, the Windows 10 security baselines are effectively a set of best practices IT pros can use to further lock down their Windows desktops and create and support security policies and standards in their organizations.
The security baselines can also help save IT time and effort and help it focus on the security of the thousands of Group Policy Objects (GPOs) and settings built into Windows 10. In addition, the existence and implementation of Windows 10 security best practices can help demonstrate to third parties, such as business partners and customers, that a company is following an industry standard that serves to minimize network security-related risks.
Not only is this Microsoft guidance free, it’s coming from the very creator of the software, so it’s well-researched and properly vetted.
How does it work?
Once IT pros download the Security Compliance Toolkit for their particular version of Windows 10, they can peruse the accompanying spreadsheet — as shown in Figure A — to see which areas of security they might want to address on an ad hoc basis.
IT pros can use the analysis and testing capabilities in the Security Compliance Toolkit to establish the Windows 10 security best practices for their organizations.
Selecting the download option for the Windows 10 Version 1709 Security Baseline.zip file provides IT with the spreadsheet above, as well as the necessary GPOs, templates and client install script it needs to get rolling.
On the Security Compliance Toolkit download page, IT also has the option to download Microsoft’s policy analyzer tools, as well as the Local Group Policy Object Utility for managing local Windows policies.
When establishing Windows 10 security baselines, IT pros should proceed with the goal of balancing Microsoft’s recommendations with what they actually need — based on the results of their vulnerability and penetration testing — and how it will best work in their deployment.
Dig Deeper on Windows OS and management
-
Windows Server 2022 security hardening guide for admins
By: Brien Posey
-
PrintNightmare haunts Microsoft as patch may miss mark
By: Alex Scroxton
-
6 Group Policy best practices for Windows 10 admins
By: Brien Posey
-
Get to know Workspace One for Microsoft Endpoint Manager
By: Johan van Amersfoort
E-Handbook: Get to know your Windows 10 security options
Article3 of 4
Up Next