When businesses and organizations have to deal with multiple networks or complex server infrastructure devices, a central authentication mechanism is essential to control their users getting access to the network. Considering the amount of damage that could happen if the servers get hacked by unauthenticated, unauthorized or unaccountable users, security teams must implement new strategies to authenticate users and authorize their access to their requested network.
One authentication method that is designed to allow network devices to authenticate users is Remote Authentication Dial-In User Service – Windows RADIUS Servers.

What is a RADIUS Server?
Remote Authentication Dial-In User Service (RADIUS) is a client/server protocol that allows for centralized authentication, authorization, and accounting (AAA). The RADIUS protocol provides network access control or remote access servers for dial-in users to communicate with a central server. Integrating a RADIUS Server into a system not only prevents private information from being leaked but also maintains the user profiles in a central database individual and assigns them with unique network permissions. It offers better security, allowing organizations to set up policies that can be applied at a single network point.
RADIUS is used to control the access for all types of networks, ranging from dial-up to wireless to VPN, even router to router connections. A RADIUS server can also be used as a proxy client to other RADIUS servers and other types of authentication servers. The RADIUS Server can run either on a UNIX or Windows server.
NPS Server in RADIUS Authentication
Network Policy Server (NPS) is Microsoft’s implementation to give IT organizations the ability to authenticate client devices through various network access points. The RADIUS protocol works with a RADIUS Server, running NPS Server on Windows, and RADIUS Client, which is a Network Access Server (NAS). The communication between the NAS and the RADIUS server is established on the User Datagram Protocol (UDP), a connectionless protocol that does not use direct connections. However, this could lead to certain issues such as availability of server, re-transmission, and timeouts that are managed by the RADIUS-enabled devices and not by the transmission protocol.
RADIUS Server Authentication Flow
The authentication and authorization process:
- With a network access server acting as a RADIUS client it conveys authentication requests to a RADIUS server that runs as a background process on Windows.
- The user credentials and access privileges are checked by the RADIUS server and compared with the information stored in the central database. The user database is either stored in a flat-file format or stored externally on an SQL Server or Active Directory Server.
- If the user credentials and privileges are found on the database by the RADIUS server, the information is passed back to the NAS. Once the NAS receives the authentication and authorization message, the user is allowed access to the network and the other applications and services.
- While the users are logged onto the server, the RADIUS Client (NAS) passes accounting requests to the RADIUS server. These requests monitor and record the activities of the users onto the RADIUS server.

The RADIUS protocol supports two-factor and multi-factor authentication (MFA) mechanisms. These mechanisms use one-time passwords or more Access-Challenge messages as well as additional messages from the client to the server. Some of the forms of authentication are Challenge-Handshake Authentication Protocol (CHAP), Password Authentication Protocol (PAP) and Extensible Authentication Protocol (EAP). Integrating both authentication and authorization operations in RADIUS limits traffic flow, thereby, increasing the efficiency and security of the network.
Authenticating using Windows RADIUS Server
Other than RADIUS, there are other software and protocols used for authenticating and authorizing users; out of which Lightweight Directory Access Protocol (LDAP) is commonly used. To decide whether you need to use a windows RADIUS Server or any other protocol, one needs to understand the differences, the levels of security they offer, the network traffic of your system and setting up the services. Though both protocols perform similar tasks, they operate differently, making it hard to determine which to use.
The differences between the protocols as well as the security considerations will help you understand when to use a RADIUS Server in windows.
LDAP — Lightweight Directory Access Protocol
LDAP is a software protocol that is used to access and manage directory services through the use of Transport Layer Security (TLS). Since LDAP runs through TLS, it can encrypt user sessions between the client and server. LDAP does not support user accounting.
RADIUS vs LDAP
The main differences between LDAP and RADIUS protocols lie in how they interact over the network. While LDAP runs on a Transmission Control Protocol (TCP) to make sure that there is a reliable connection across the network, RADIUS is deployed through User Datagram Protocol (UDP), which minimizes network overhead. In other words, whereas TCP ensures a connection, but does require more network overhead, RADIUS does not ensure a connection. There are chances of errors cropping up in the server as well as intermittent timeouts. If not implemented properly, it may also make the network susceptible to replay attacks.
On a RADIUS Server, other than the password, all other user information is not encrypted. This means that sensitive user information is visible to others in the network as it is sent across in clear text. To avoid sensitive information falling into wrong hands, users need to beef up the security measures and implement additional security mechanisms. To encrypt all the user attributes, using a virtual private network (VPN) between RADIUS servers and clients is a good idea.
On its own, LDAP does not support multifactor authentication. Though many solutions exist, they require additional resources like implementing other protocols, including RADIUS.

LDAP protocols require multiple transactions between the server and the client, which can cause significant delays during user authentication attempts. However, once a user logs into the RADIUS directory server, the information is cached which can lessen login times. In comparison to LDAP, RADIUS is a simpler protocol and the speed of authentication transactions are faster, even for a large database of users.
However, since RADIUS uses UDP, if the network quality is weak, there are chances that requests may time out and have to be repeated. On the brighter side, in a RADIUS Server, as the network load is minimal, the authentication client load is lesser. Moreover, there is no need for complex settings or directory searches to take place between the user and the directory service.
However, since RADIUS uses UDP, if the network quality is weak, there are chances that requests may time out and have to be repeated. On the brighter side, in a RADIUS Server, as the network load is minimal, the authentication client load is lesser. Moreover, there is no need for complex settings or directory searches to take place between the user and the directory service.
As a developer, understanding Windows Radius Server is an essential part of your job. In simple terms, a radius server is a type of authentication server that authorizes and authenticates remote users and devices. With the increasing popularity of remote work, the demand for radius servers has grown dramatically, making it a vital component of any organization’s security infrastructure. In this article, we’ll provide a comprehensive guide to Windows Radius Server, including its functions, benefits, and how to set it up.
What is a Windows Radius Server?
A Windows Radius Server is a network server that uses the Remote Authentication Dial-In User Service (RADIUS) protocol to authenticate and authorize remote users and devices. The server typically sits between the network device and a central authentication database, such as Active Directory. When a user or device attempts to connect to the network, the network device sends a request to the Radius Server, which then forwards the request to the authentication database. The authentication database checks the credentials and sends back a response to the Radius Server, which then forwards the response back to the network device.
How Does Windows Radius Server Work?
The Windows Radius Server works by using the RADIUS protocol, which is a client-server protocol that runs on UDP (User Datagram Protocol) and is designed to provide centralized authentication, authorization, and accounting (AAA) management for network devices. When a user or device attempts to connect to the network, the network device sends an access request to the Radius Server. The Radius Server then forwards this request to the authentication database, which can be an Active Directory, LDAP, or any other database that supports the RADIUS protocol.
The authentication database then checks the user’s or device’s credentials and sends back an access accept or access reject message to the Radius Server. If the access is accepted, the Radius Server then sends an access accept message to the network device, which then allows the user or device to connect to the network. If the access is rejected, the Radius Server sends an access reject message to the network device, which then denies access to the user or device.
The Benefits of Using Windows Radius Server
Using a Windows Radius Server offers several benefits for organizations, including:
|
Benefit |
Description |
|---|---|
|
Centralized Management |
Allows organizations to manage authentication and authorization from a central location, simplifying network management. |
|
Improved Security |
Provides additional security measures, such as two-factor authentication, to prevent unauthorized access to the network. |
|
Scalability |
Can handle a large number of users and devices, making it suitable for organizations of all sizes. |
|
Cost-Effective |
Can be used with existing infrastructure, reducing the need for additional hardware or software. |
Setting up Windows Radius Server
Prerequisites
Before setting up Windows Radius Server, you must have:
- A Windows Server with administrative access.
- The latest version of .NET framework installed.
- The Windows Server role of Network Policy and Access Services installed.
- Access to an authentication database, such as Active Directory or LDAP.
Step-by-Step Guide
Follow these steps to set up Windows Radius Server:
- Open the Network Policy Server (NPS) console from the Administrative Tools menu.
- On the left-hand side, right-click on RADIUS Clients and select New.
- Enter a friendly name for the client, such as the network device name.
- Enter the IP address or hostname of the network device and click Next.
- Select the option to automatically generate a shared secret or enter a custom secret and click Next.
- Click Finish to add the client.
- Next, right-click on Network Policies and select New.
- Enter a name for the policy and click Next.
- Under Conditions, select the appropriate conditions for your organization, such as Windows groups or Active Directory attributes.
- Under Constraints, select the appropriate constraints for your organization, such as encryption or authentication methods.
- Under Settings, select the appropriate settings for your organization, such as session timeout or access permissions.
- Click Finish to create the policy.
- Finally, right-click on the RADIUS Clients and select Show Shared Secret to view the shared secret.
- Enter the shared secret on the network device and test the connection.
FAQs
What is the difference between RADIUS and TACACS+?
RADIUS and TACACS+ are both authentication and authorization protocols, but they differ in their security mechanisms. RADIUS uses a shared secret to encrypt data between the network device and the Radius Server, while TACACS+ uses SSL/TLS encryption to secure data in transit. Additionally, RADIUS only supports authentication and authorization, while TACACS+ supports authentication, authorization, and accounting.
Can I use Windows Radius Server with non-Windows devices?
Yes, Windows Radius Server can be used with non-Windows devices, as long as the device supports the RADIUS protocol. Most network devices, such as routers, switches, and firewalls, support the RADIUS protocol.
What is AAA in networking?
AAA stands for Authentication, Authorization, and Accounting, which are essential components of network security. Authentication is the process of verifying a user’s identity, authorization is the process of granting access based on the user’s credentials, and accounting is the process of tracking network usage for billing or auditing purposes.
What is Active Directory?
Active Directory is a centralized directory service that manages authentication and authorization for Windows-based networks. It provides a hierarchical structure for organizing network resources, such as users, computers, and applications, and allows administrators to manage access permissions and policies from a central location.
Conclusion
Windows Radius Server is an essential component of any organization’s security infrastructure. By providing centralized authentication and authorization management, Windows Radius Server enables organizations to improve security, scalability, and cost-effectiveness. Setting up Windows Radius Server may seem daunting, but by following our step-by-step guide, you can easily configure it to meet your organization’s needs. We hope this article has been helpful in understanding Windows Radius Server and its benefits.
There are thousands of deployed instances of Windows RADIUS Server across the world, but users still debate its capabilities to keep their large networks intact and secure, giving rise to questions like:
“Is a Windows RADIUS Server sufficient for my organization?”
“Is Windows RADIUS Server still in use?”
“Are there better alternatives?”.
After all, cybersecurity is constantly in the news these days. Every day a different company is victimized by hackers. According to research by IBM, it takes 280 days to find and contain the average cyberattack, while the average attack costs $3.86 million—which is why providing robust network security for your users is more important than ever. Let’s examine the pros and cons of using the Microsoft solution for network access control.
What is a Windows RADIUS Server?
A Windows RADIUS Server is a RADIUS server created using Microsoft’s Network Policy Server (NPS). NPS performs authentication, authorization, and accounting (AAA) for the connection requests from:
- Wireless network
- Virtual Private Network (VPN) remote access
- 802.1x switches
- Dial-up
- Router to router connections
A Network Access Server (NAS) acts as a RADIUS client and sends all connection requests from users to NPS, which then provides authorization data back to the NAS.
The Pros and Cons of NPS
Windows RADIUS comes with both pros and cons. To make the best decision for your organization, use this list to come up with a solution that best suits your organization.
Advantages of a Windows RADIUS Server
Confidentiality Of Data
The biggest advantage is that NPS as a RADIUS houses applications and data on-premise and in-house, allowing you to maintain full control over that data. It’s the only way to ensure that a third party never sees your data (assuming your cybersecurity is up to snuff).
For some organizations, keeping the data on-premise may be a requirement for compliance and audits.
Solve Problems On The Spot
Another convenience that results from the local storage of data is that, in the case of network problems or internet interruption, data can still be accessed with on-premise solutions. Assuming the IT team is on-site, which may be a big assumption, it can be addressed without the need for intervention by a third party.
No Dependence On Internet
With cloud servers, your access is only as good as your connection. NPS eliminates this concern since you can access all your company data as long as the power is on.
Load Balancing
NPS allows the creation of both network policies for connection request authentication/authorization and configures RADIUS to forward connection requests to remote RADIUS servers, which helps load-balancing the connection requests.
NPS Accounting
You can store RADIUS accounting data in log files or a SQL database. NPS can log accounting data, such as user authentication and accounting requests, in three formats:
- IAS format
- Database-compatible format
- Microsoft SQL Server logging
Disadvantages of a Windows RADIUS Server
The Troubles Of On-Premise Servers
NPS requires physical installation, space, and configuration that depends on a skilled contractor in most cases, or an experienced and dedicated on-site manager. As a result, NPS’s dependence on regular maintenance can be costly. If you are using multiple on-site servers, it multiplies the number of headaches (and locations) you will need to service when things go wrong.
Forget about hacking, your servers could be physically stolen without adequate physical protection. Loss of hardware is one thing, what’s scary is, theft is specifically aimed at stealing servers with valuable data on them. Unavoidable natural calamities such as fires, earthquakes, jeopardizing the entire network is a real possibility.
On the other hand, a Managed Cloud RADIUS server gives you a centralized infrastructure. It removes the hassle of maintaining and updating systems, allowing you to invest your time, money and resources into fulfilling your core business strategies. Providing real-time visibility of the entire network regardless of the location, with guaranteed 24/7 access and disaster recovery, cloud servers are becoming the number one choice for businesses, with adoption rates reaching 88% in 2021.
NPS Is Not Economical For Anything But The Largest Organizations
NPS has a higher overall cost compared to cloud solutions. It requires hardware, maintenance, physical space, and dedicated staff (both IT employees to run it and security to guard the physical location). It’s also a “one-size-fits-all” solution, you are stuck with a fixed plan and must shell out money for services you may never use. In contrast, the Software as a Service (SaaS) model of cloud RADIUS vendors lends itself to a “pay-as-you-use” plan that can scale to fit your needs.
NPS Requires Redundant Servers
Enterprises with on-premise solutions such as NPS, need redundant servers on hand when trouble strikes or during service outages, because 100% uptime is critical. Whereas the customers of cloud infrastructure are provided redundancy, disaster recovery, and fail-over natively.
No Automatic Scalability
Users of NPS must set up new hardware when looking to scale up and take the hardware out when scaling down. Cloud Server expansion is virtually limitless and provides users with on-demand virtual resources and offer unrivaled scalability in a click.
NPS Doesn’t Support Cloud
NPS was designed to be used as an on-premise solution with Active Directory, because it was made long before cloud solutions were possible. There is no native ability to connect NPS with cloud directories. It doesn’t even work with Microsoft’s own cloud platform, Azure AD, without workarounds and proxy servers.
NPS Is Less Secure Than Cloud RADIUS
Mandiant Threat Intelligence observed that roughly 80% of successful cybersecurity breaches stem from zero-day attacks (i.e “zero days” to fix it). It’s more likely than you think that physical servers are vulnerable to zero day exploits because the servers go unattended for a long time when the team is asleep. Whereas cloud servers run 24/7 under the care of network engineers, with up-to-date software and zero downtime, leaving no excuse for zero day attacks.
NPS Server Failures
The end of a server’s life is rarely an enjoyable time. With it comes re-evaluating applications and preparing for migrations. Failures start to occur as servers age, a four year-old server has an 11 percent annual failure frequency. Unplanned incidents and emergencies start to rise as the server gets older. A Cloud Radius server makes sense because you can avoid the high upfront cost and effort of replacing the servers.
NPS is Outdated
NPS was made long before cloud computing became popular. It was designed first in 2003 to be used as an on-premise solution with Active Directory, and it’s had four major updates since then. The latest version (2019) still clings to that tradition, lacking the modern protocols and methods that cloud solutions provide. With cloud taking the stage, NPS may become obsolete.
A Windows RADIUS Server in the Cloud
In general, Cloud RADIUS server is loved by end users and admins alike because it’s a breeze (just like the cloud!). Cloud RADIUS comes with many benefits that a physical server simply cannot match. It has built-in redundancy, modern protocols, integrations for cloud applications, limitless resources/storage, can perform all the RADIUS functions with no physical servers and authenticate remote users securely.
Ultimately, the only really compelling reason for a business to stay on-prem is the need to keep all of their data in-house and not leave in the hands of a third party.
Check out our pricing page to see if SecureW2’s Cloud RADIUS servers fit the network needs of your organization.
Last updated on May 13, 2022
Network Policy Server (NPS) is Microsoft’s implementation of a Remote Authentication Dial-In User Service (RADIUS) server. NPS provides centralized authentication, authorization, and accounting (AAA) capabilities to your network. Under this setup, your network access server (NAS) acts as a RADIUS client and sends all connection requests from users to a RADIUS server running NPS on Windows, which then provides authentication and authorization information back to the NAS. While users are connected to your network, NPS logs their activities as part of its RADIUS accounting role.
What Is the RADIUS Protocol?
RADIUS is a client-server networking protocol with AAA management features that uses the connectionless User Datagram Protocol (UDP) for its transport layer and uses port 1812 for authentication and port 1813 for authorization.
Since UDP does not require a reliable connection across a network, using RADIUS means minimal network overhead. However, this can also lead to request timeouts in case of poor network quality. When this happens, the RADIUS client sends another request to the server. To ensure that RADIUS runs on a secure network connection, there have been past initiatives to make it work with Transmission Control Protocol (TCP), but these have not gone beyond the experimental stage.
Authentication Process
As a client-server networking protocol, RADIUS has client and server components. In a typical network that uses RADIUS, the authentication and authorization process goes like this:
- A NAS serves as a RADIUS client and passes authentication requests to a RADIUS server that runs as a background process on Windows or any other server operating system.
- The RADIUS server authenticates the user credentials and checks the user’s access privileges against its central database, which can be in a flat-file format or stored on an external storage source such as SQL Server or Active Directory Server.
- When the RADIUS server finds the users and their associated privileges in its database, it passes back an authentication and authorization message back to the NAS, which then allows the user access to the network and its array of applications and services.
- The NAS, still acting as a RADIUS client, passes accounting requests back to the RADIUS server while users are connected to the network. These requests log all user activities onto the RADIUS server.
RADIUS supports various authentication mechanisms, including:
- Challenge-Handshake Authentication Protocol (CHAP)
- Password Authentication Protocol (PAP)
- Extensible Authentication Protocol (EAP)
The combined authentication and authorization operation in RADIUS minimizes traffic flow and makes for a more efficient network. RADIUS also supports multi-factor authentication (MFA) using one-time passwords or some other mechanism, which often require clients and servers to pass more messages than normal.
In larger networks, a RADIUS server can also act as a proxy client to other RADIUS servers.
RADIUS or LDAP: Which to Use for Centralized Authentication?
LDAP
Like RADIUS, Lightweight Directory Access Protocol (LDAP) is used for user authentication and authorization. LDAP performs this role by accessing and managing directory services, such as Microsoft’s proprietary Active Directory service. As to which is better depends on your specific requirements.
Since LDAP uses TLS, the connections and messages between client and server are always encrypted. Moreover, since LDAP uses TCP, chances of dropped requests are nil, although this often means more network overhead. LDAP is also simpler to set up than RADIUS.
On the other hand, LDAP does not support user accounting, though this can be accommodated using other tools such as Syslog. It also does not support multi-factor authentication out of the box, though you can use other solutions if you need this feature.
RADIUS
By default, RADIUS does not encrypt any of the other attributes passed between client and server, except for passwords. It does support other authentication mechanisms such as EAP, allowing it to circumvent this weakness. You can also implement other security mechanisms, such as putting servers and clients behind virtual private networks (VPNs), with RADIUS.
Although more complex, RADIUS supports user accounting and MFA, making it ideal for use in large enterprises. However, it is also useful for smaller organizations looking to secure their networks.
Network Policy Server as a RADIUS Server
NPS was known as Internet Authentication Service (IAS) in earlier Windows versions. Starting with Windows 2008, IAS became NPS, with Microsoft adding new features to the component, including Network Access Protection and IPv6 support. NPS works with many types of networks.
To authenticate user credentials on your Windows network, NPS relies on an Active Directory Domain Services (AD DS) domain or the local Security Accounts Manager (SAM) user accounts database. You can use NPS as part of a single sign-on solution when the server running it belongs to an AD DS domain. In this case, NPS authenticates users via the directory service’s user-account database, logging authenticated users into the AD DS domain.
With RADIUS, NPS acts as the central location for user data related to authentication, authorization, and accounting instead of the NAS. If you combine NPS with Remote Access Services, you can use RADIUS to authenticate and authorize users in your remote access networks.
A RADIUS server running NPS provides the easiest authentication mechanism for Windows Servers running on AWS.
Network Policy Server as a RADIUS Proxy
Aside from having NPS as a RADIUS server on Windows, you can also use NPS as a RADIUS proxy client that forwards authentication or accounting messages to other RADIUS servers.
Some scenarios where this use case is useful is if you:
- Provide outsourced network-access services. Then you can forward connection requests to RADIUS servers that your customers maintain.
- Have user accounts that don’t belong to the same domain as the Windows RADIUS server or that belong to another domain with a two-way trust relationship with the NPS RADIUS server’s domain.
- Use a non-Windows account database.
- Have a large number of users requesting connections.
- Provide RADIUS authentication and authorization to your vendors.
How Does Accounting for RADIUS Server Work?
RADIUS Servers are also used for accounting purposes. RADIUS accounting collects data for network monitoring, billing, or statistical purposes. The accounting process typically starts when the user is granted access to the RADIUS Server. However, RADIUS accounting can also be used independently of RADIUS authentication and authorization.
A basic RADIUS accounting process includes the following steps:
- The process starts when the user is granted access to the RADIUS Server.
- The RADIUS Client sends a RADIUS Accounting-Request packet known as Accounting Start to the RADIUS Server. The request packet comprises the user ID, network address, session identifier, and point of access.
- During the session, the Client may send additional Accounting-Request packets known as Interim Update to the RADIUS Server. These packets include details like the current session duration and data usage. This packet serves the purpose of updating the information about the user’s session to the RADIUS Server.
- Once the user’s access to the RADIUS Server ends, the RADIUS Client sends another Accounting-Request packet, known as Accounting Stop, to the RADIUS Server. The packet includes total time, data, packets transferred, reason for disconnection, and other information relevant to the user’s session.
Secure Your Application Access with Parallels RAS
Parallels® Remote Application Server (RAS) has a wide range of features that can help secure access to your applications and data, including support for MFA using any RADIUS server.
Parallels RAS provides high-availability configuration support for two RADIUS servers. High-availability modes for RADIUS servers may be set as Active-Active, to make use of both servers simultaneously or as Active-Passive, for failover purposes.
Moreover, with Parallels RAS, you can create filtering rules for users based on user, IP address, MAC address, and gateway. You can group users and push different Parallels Client settings to your user devices using client policies.
Parallels RAS supports:
- Smart card authentication
- Kiosk mode
- Security Assertion Markup Language single sign-on (SAML SSO) authentication.
Parallels RAS also supports Secure Sockets Layer (SSL) or Federal Information Processing Standard (FIPS) 140-2 protocol encryption in accordance with the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS).
Parallels RAS comes with a standard Reporting Engine that allows your raw data to be transformed into visual and intuitive reports.
Check out how Parallels RAS can help secure your networks!
Download the Trial
В этой статье мы покажем, как настроить сервер централизованной аутентификации, авторизации и аккаунтинга (RADIUS) на операционной системе Windows Server 2016, а также как настроить Radius-аутентификацию на Cisco устройствах с помощью службы Политики сети и доступа (Network Policy Server).
RADIUS (англ. Remote Authentication in Dial-In User Service) — протокол для реализации аутентификации, авторизации и сбора сведений об использованных ресурсах, разработанный для передачи сведений между центральным севером и различными сетевым оборудованием и клиентами.
В первую очередь создайте в домене Active Directory группу безопасности AllowRemoteCiscoUsers, в которую нужно добавить пользователей, которым будет разрешена аутентификации на маршрутизаторах и коммутаторах Cisco.
Далее нужно установить на сервере, с помощью которого будет выполнятся аутентификация клиентов и назначаться права доступа, роль RADIUS сервера. Для этого на сервере Windows Server 2016 откройте оснастку Server Manager и вызовите мастер добавления ролей — Add Roles and features.
В открывшемся мастере на шаге выбора ролей отметьте роль Network Policy and Access Services. На шаге выбора служб роли в нашей ситуации достаточно будет выбрать только службу Network Policy Server.
Протокол Remote Authentication Dial In User Service (RADIUS) в Windows Server 2016 включен в состав роли Network Policy Server.
В консоли Server Manager выберите меню Tools и откройте консоль Network Policy Server (nps.msc).
Для полноценного использования NPS-сервера в домене необходимо зарегистрировать его в домене Active Directory. В оснастке на NPS, щелкните ПКМ по вашему NPS узлу и выберите Register server in Active Directory.
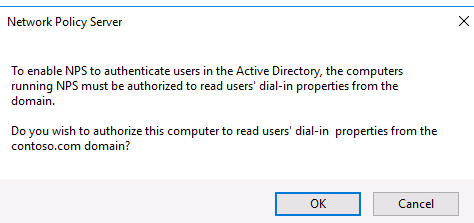
Подтвердите регистрацию сервера в Active Directory:
При этом мы должны предоставите серверу полномочия на чтение свойств учётных записей пользователей, касающихся удалённого доступа. Сервер при этом будет добавлен во встроенную доменную группу RAS and IAS Servers.
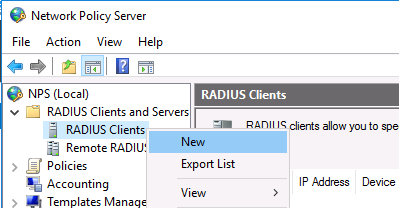
Теперь можно добавить клиента Radius. Для этого в дереве консоли NPS разверните раздел RADIUS Clients and Servers и на элементе RADIUS Clients выберите пункт New.
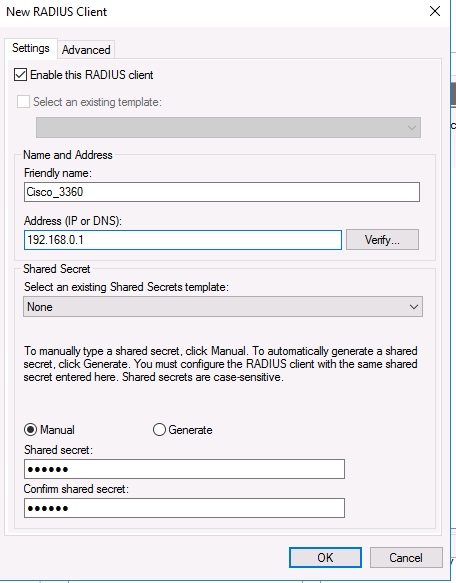
На вкладке Settings заполните поля Friendly name, Client address (можно указать IP адрес или DNS имя подключающегося сетевого устройства) и пароль — Shared Secret + Confirm shared (этот пароль вы будете использовать в настройках коммутатора или маршрутизатора Cisco для установления доверительных отношений с Radius сервером).
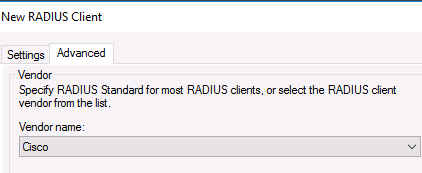
Во вкладке Advanced выберите в поле Vendor name — Cisco.
Теперь нужно создать политики доступа на сервере RADIUS. С помощью политик доступа мы свяжем клиента Radius и доменную группу пользователей.
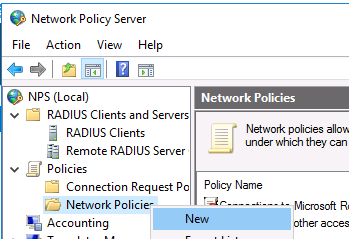
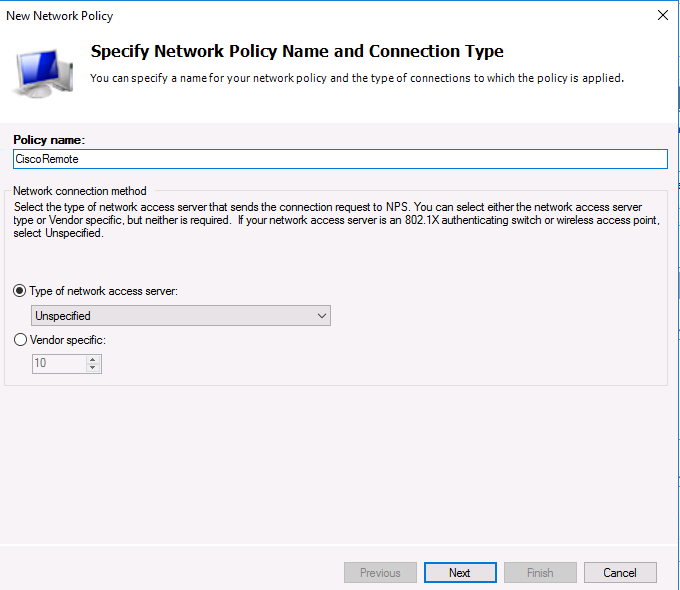
Раскройте ветку Policies —> Network Policies, и выберите пункт меню New:
Укажите Имя политики (Policy name). Тип сервера доступа к сети (Type of network access server) оставьте без изменения (Unspecified):
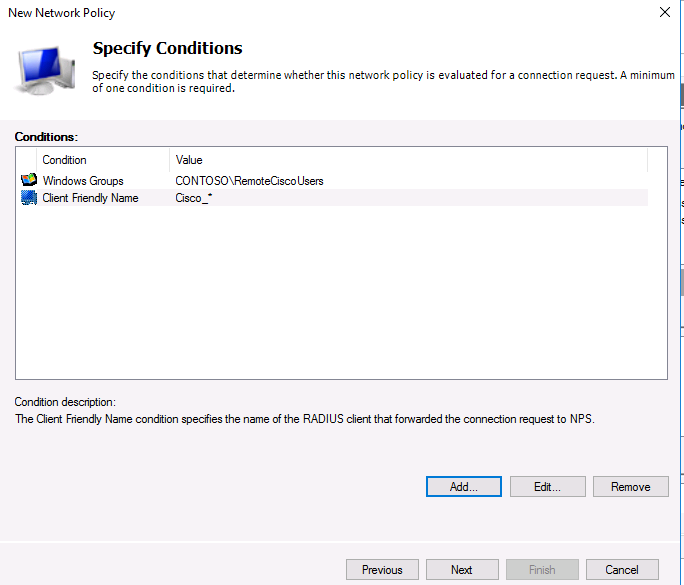
На следующем шаге Specify conditions нам нужно добавить условия, при которых будет применяться данная политика RADIUS. Добавим два условия: вы хотите, что для успешной авторизации пользователь входил в определенную доменную группу безопасности, и устройство, к которому осуществляется доступ, имело определённое имя. С помощью кнопки Add добавим сначала условие, выбрав тип Windows Group (добавьте группу RemoteCiscoUsers) и укажите Client Friendly Name (Cisco_*).
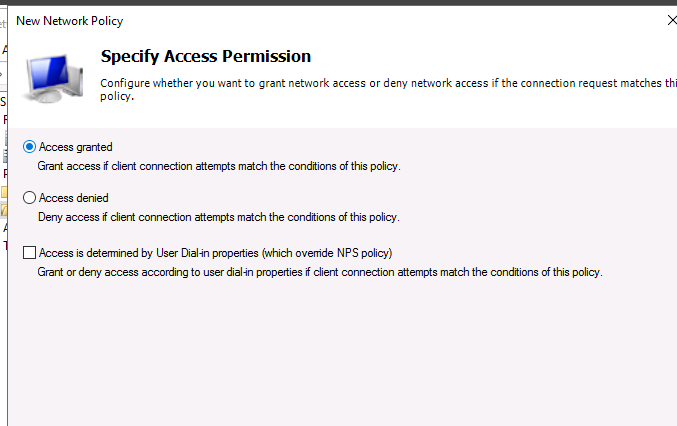
На следующем выберите значение Доступ разрешен (Access Granted).
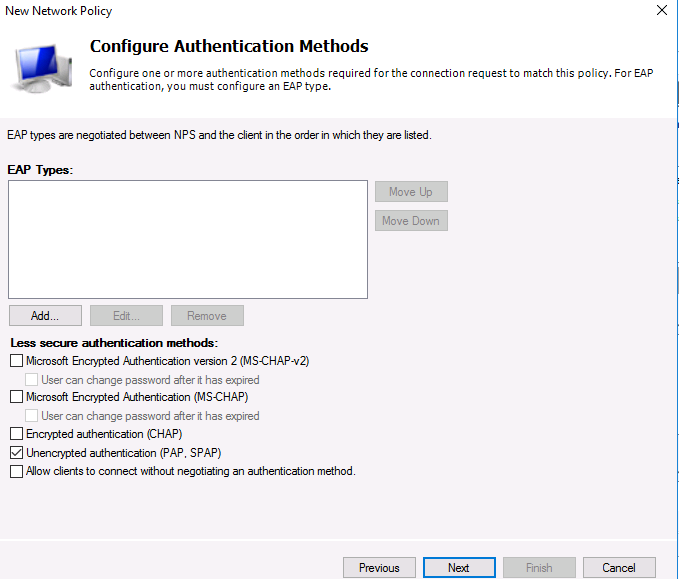
Т.к. наш коммутатор Cisco поддерживает только метод аутентификации Unencrypted authentication (PAP, SPAP), снимите все остальные флажки.
Следующий шаг настройки ограничений (Constraints) мы пропустим.
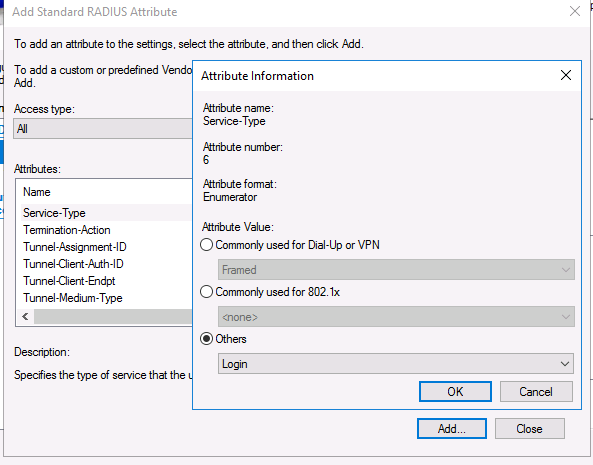
В разделе Configure Settings перейдите секцию RADIUS Attributes -> Standard. Удалите имеющиеся там атрибуты и нажмите кнопку Add.
Выберите Access type -> All, затем Service-Type->Add. Укажите Others=Login.
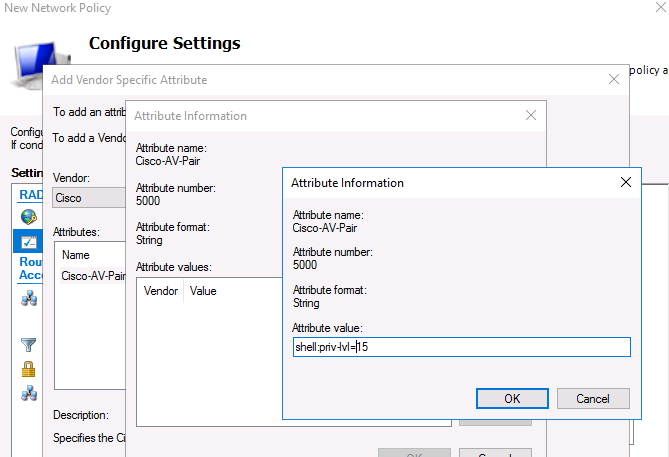
Теперь в секции RADIUS Attributes -> Vendor Specific добавьте новый атрибут. В пункте Vendor, найдите Cisco и нажмите Add. Здесь нужно добавить сведения об атрибуте. Нажмите Add и укажите следующее значение атрибута:
shell: priv-lvl = 15
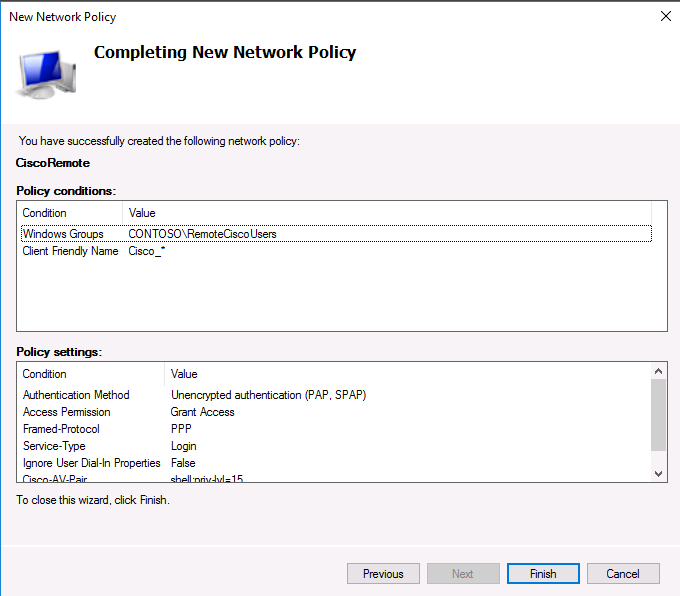
На последнем экране будут указаны все созданные вами настройки политики NPS. Нажмите Finish:
При создании и планировании политик обратите внимание на то, что имеет значение их порядок. Политики обрабатываются сверху вниз, и все условия очередной политике соблюдены, эта политика применяется к клиенту, а дальнейшая обработка других политик прекращается. То есть с точки зрения безопасности и разрешения конфликтов между политиками правильнее будет располагать политики в порядке возрастания административных полномочий.
После создания политики, можно переходить к настройке маршрутизаторов и коммутаторов Cisco для аутентификации на сервере Radius NPS.
AAA работает таким образом, что, если не получен ответ от сервера, клиент предполагает, что аутентификация не выполнена. Чтобы не потерять доступ к своим сетевым устройствам, которые вы переключаете на авторизацию на Radius сервера, обязательно создайте локальных пользователей на случай если RADIUS сервер станет недоступен по какой-либо причине.
Ниже пример конфигурации для авторизации на Radius (NPS) сервере для коммутатора Cisco Catalyst:
aaa new-model
aaa authentication login default group radius local
aaa authorization exec default group radius if-authenticated
radius-server host 192.168.1.16 key R@diu$pa$$
service password-encryption
На этом минимальная настройка коммутатора закончена и можно испытать новый механизм аутентификации и авторизации в действии.