When you open the Security Event log, the log may contain many “Filtering Platform Connection” events. The event ID of these entries maybe 5156 or 5158. The security log may record close to 100 events per minute, containing the event ID 5156 or 5158. This causes the security event log to become full very quickly.
Sample Event ID 5156 entry
Log Name: Security Source: Microsoft-Windows-Security-Auditing Date: 7/19/2022 11:27:37 AM Event ID: 5156 Task Category: Filtering Platform Connection Level: Information Keywords: Audit Success User: N/A Computer: OptiPlex-9020 Description: The Windows Filtering Platform has permitted a connection. Application Information: Process ID: 2592 Application Name: \device\harddiskvolume2\program files (x86)\microsoft\edge\application\msedge.exe Network Information: Direction: Outbound Source Address: 192.168.0.101 Source Port: 63386 Destination Address: 239.255.255.250 Destination Port: 1900 Protocol: 17 Filter Information: Filter Run-Time ID: 144025 Layer Name: Connect Layer Run-Time ID: 48
Sample Event ID 5158 entry
Log Name: Security Source: Microsoft-Windows-Security-Auditing Date: 7/19/2022 11:27:51 AM Event ID: 5158 Task Category: Filtering Platform Connection Level: Information Keywords: Audit Success User: N/A Computer: OptiPlex-9020 Description: The Windows Filtering Platform has permitted a bind to a local port. Application Information: Process ID: 7612 Application Name: \device\harddiskvolume2\program files (x86)\google\chrome\application\chrome.exe Network Information: Source Address: :: Source Port: 60420 Protocol: 17 Filter Information: Filter Run-Time ID: 145279 Layer Name: Resource Assignment Layer Run-Time ID: 38
The security event log getting bombarded with 100 events per minute is never a good thing. Not only it’s an unnecessary disk I/O operation, but it also FIFOs out other vital security log data.
Cause
Windows Filtering Platform (WFP) is a set of API and system services that provide a platform for creating network filtering applications. Windows Firewall is based on WFP.
On a standard Windows installation, the Success/Failure entries for “Filtering Platform Connection” aren’t audited/logged. However, third-party software may have enabled auditing for this category. If auditing is enabled, Windows Filtering Platform generates the events 5156 and 5158 when it has allowed a connection. Event ID 5157 is written when WFP has blocked a connection.
For more information on WFP auditing, see this Microsoft article.
This article tells you how to prevent a spate of “Filtering Platform Connection” events from being written to the Security event Log every minute.
Solution
To stop Windows Filtering Platform from (“Filtering Platform Connection”) from logging Success and Failure events (5156, 5157, and 5158) in the Security event log, follow these steps:
Disable “Filtering Platform Connection” Success Audit
First, open an admin Command Prompt.
Type the following command and press Enter:
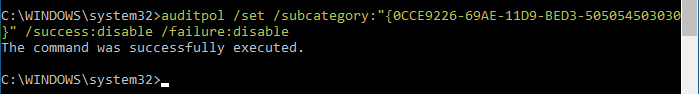
auditpol /set /subcategory:"{0CCE9226-69AE-11D9-BED3-505054503030}" /success:disable /failure:disable
That’s it. The Security event log should no longer get bombarded with events 5156, 5157, or 5158 from now on.
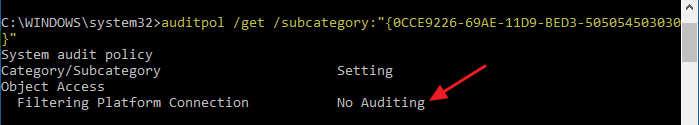
Optionally, to verify if the auditing has been successfully disabled for “Success” and “Failure” events, run this command:
auditpol /get /subcategory:"{0CCE9226-69AE-11D9-BED3-505054503030}"
You should see the following output:
System audit policy Category/Subcategory Setting Object Access Filtering Platform Connection No Auditing
The above output means auditing is disabled (for both “Success” and “Failure” WFP events) and nothing will be logged. This is what we wanted.
The security event log will have recorded the following event after the audit policy change:
Log Name: Security
Source: Microsoft-Windows-Security-Auditing
Date: 7/19/2022 12:50:01 PM
Event ID: 4719
Task Category: Audit Policy Change
Level: Information
Keywords: Audit Success
User: N/A
Computer: OptiPlex-9020
Description:
System audit policy was changed.
Subject:
Security ID: OPTIPLEX-9020\ramesh
Account Name: ramesh
Account Domain: OPTIPLEX-9020
Logon ID: 0x92A6F
Audit Policy Change:
Category: Object Access
Subcategory: Filtering Platform Connection
Subcategory GUID: {0cce9226-69ae-11d9-bed3-505054503030}
Changes: Success removed, Failure removed
“Filtering Platform Connection” Audit enables automatically?
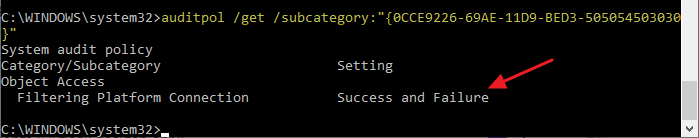
On some systems, the WFP auditing may get re-enabled automatically in a few minutes. If you run the above “auditpol /get ...” command-line, you may see that audit of “Success and Failure” entries have been switched on automatically (perhaps by some third-party security software installed on the computer.)
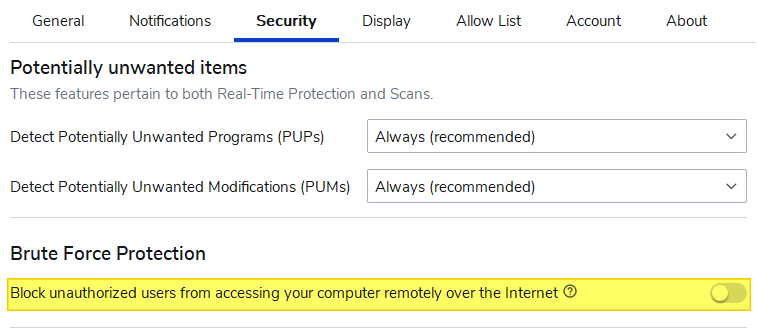
Malwarebytes “Brute Force Protection” setting
If you’re using Malwarebytes Premium and have enabled the Brute Force Protection option in the Security tab, turn the setting off.
If this setting is turned on, it enables WFP “Success and Failure” auditing automatically. Even if you disable auditing manually using auditpol.exe, Malwarebytes re-enables WFP auditing every 4-5 minutes.
Editor’s note: If you need the “Brute Force Protection” turned on and yet want to disable the WFP event logging, you may contact Malwarebytes support to see if a workaround is available.
Once done, re-run the following command from the admin Command Prompt:
auditpol /set /subcategory:"{0CCE9226-69AE-11D9-BED3-505054503030}" /success:disable /failure:disable
This disables the excessive logging of the Windows Filtering Platform (“Filtering Connection Platform”) “Success” and “Failure” events (Event ID 5156, 5157, and 5158).
Alternatively, for diagnostic purposes, you can opt to log only the “Failure” entries using the auditpol.exe command. The “Failure” entries would be significantly less in number when compared to “Success” entries.
As of this blog post, Malwarebyte’s current version is 4.5.11.202 — Update package version is 1.0.57424 — Component package version is 1.0.1716.
One small request: If you liked this post, please share this?
One «tiny» share from you would seriously help a lot with the growth of this blog.
Some great suggestions:
- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!
So thank you so much for your support. It won’t take more than 10 seconds of your time. The share buttons are right below. 
I noticed event ID 5156 is filling up my event logs. It logs one or two of these events literally every 2-3 seconds. Now my security logs are useless. I run SEP 11 which takes control of the windows firewall as well uses its own fire wall. I googled and
found that anti-virus software can be responsible for this behavior (like macaffee) and saw how I could disable logging of this event with auditpol.
My question is how can I be sure that this is my anti-virus software doing this? I can’t see anywhere in the log itself something that would link this to my antivirus product. The source address listed is always the broadcast address of my subnet and the
destination is any computer I make ANY network connection to (file servers, DCs, etc).
Here is what I am seeing:
The Windows Filtering Platform has permitted a connection. Application Information: Process ID: 4 Application Name: System Network Information: Direction: Inbound Source Address: mybroadcast.address.for.subnet Source Port: 137 Destination Address: IP.of.destination.PC Destination Port: 137 Protocol: 17 Filter Information: Filter Run-Time ID: 0 Layer Name: Receive/Accept Layer Run-Time ID: 44
I haven’t really found to much info on event ID 5156, or at least info I can make
that much sense of. Would I ever really need this event to be logged? And why would my anti-virus software cause so many of these events?
I have seen more number of logs with the Event ID 5156 while working with File System Auditing where this event is being repeatedly logged on my server 2008 R2 machine.
See the event in this picture
After I have analyzed for the reason of Event ID 5156 is being repeatedly logged, found the below solutions to stop the Event ID 5156 from being logged continuously
Event ID 5156 should occur if the Success or Failure audit was enabled for Filtering Platform Connection in Advanced Audit Policy Configuration setting which is available from Windows 2008 R2 and later versions.
Category: Object Access
Subcategory: Filtering Platform Connection
You will get the following Event IDs if the Filtering Platform Connection is enabled.
5031 – The Windows Firewall Service blocked an application from accepting incoming connections on the network.
5154 – The Windows Filtering Platform has permitted an application or service to listen on a port for incoming connections.
5155 – The Windows Filtering Platform has blocked an application or service from listening on a port for incoming connections.
5156 – The Windows Filtering Platform has allowed a connection
5157 – The Windows Filtering Platform has blocked a connection
5158 – The Windows Filtering Platform has permitted a bind to a local port.
5159 -The Windows Filtering Platform has blocked a bind to a local port.
We should disable the audit policy setting Filtering Platform Connection in Advanced Audit Policy Configuration to stop this event. We can do it in the following ways.
Possible Solution: 1- using Auditpol exe
If you would like to get rid of this Filtering Platform Connection event 5156 then you need to run the following commands in an elevated command prompt (Run As Administrator):
Auditpol /set /subcategory:”Filtering Platform Connection” /Success:disable
Then update gpo by this command
gpupdate /force
Possible Solution: 2 – using Local Security Policy
You can also disable Filtering Platform Connection in Advanced Audit Policy Configuration of Local Security Policy.
1. Press the key Windows + R
2. Type command secpol.msc, click OK
3. Then go to the node Advanced Audit Policy Configuration->Object Access.
4. Check the audit setting Audit Filtering Platform Connection If it is configured as Success, you can revert it Not Configured and Apply the setting.
Possible Solution: 3 – using Group Policy Object
If the setting is inherited from any other GPO to Local Security Policy,You need to edit the specific GPO which is configured with the setting Audit Filtering Platform Connection. You can find the GPO by running Resultant Set of Policy.
1. Press the key Windows + R
2. Type command rsop.msc, click OK.
3. Now you can the below result window. Then go to the node Computer Configuration ->Windows Settings ->Local Polices-> Audit Policy.
4. Now, you can see the Source GPO of the setting Audit Object Access which is the root Setting for Audit Filtering Platform Connection.
5. Then you can edit the Audit Filtering Platform Connection of corresponding GPO by running GPMC.msc command through Run window or command window.
Note:You need run the command GPUpdate /force after every changes to apply group policy to system immediately.
Morgan
Software Developer
Если у вас в журнале безопасности регистрируется довольно много сообщений с Event ID 5156, которые сообщают что
The Windows Filtering Platform has allowed a connection
и вы хотите их отключить, сделайте следующее:
- Запустите gpedit.msc
- Перейдите в ветку «Computer Configuration/Windows Settings/Security Settings/Local Policies/Security Options».
- Убедитесь что у вас, в Windows 2008, включена опция: «Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings».
После этого нужно воспользоваться командой «auditpol». Введите команду:
auditpol /set /subcategory:"Filtering Platform Connection" /success:disable /failure:enable
Если же вам хочется еще отключить и такие сообщения:
The Windows Filtering Platform blocked a packet
То выполняем команду:
auditpol /set /subcategory:"Filtering Platform Packet Drop" /failure:disable
Хотя, если честно, после жалоб «безопасника» на сообщения не несущие полезную информацию сообщения я отключаю вот так :
auditpol /set /subcategory:"Filtering Platform Connection" /success:disable /failure:disable auditpol /set /subcategory:"Filtering Platform Packet Drop" /success:disable /failure:disable
Чтоб посмотреть синтаксис этой команды введите в командной строке:
auditpol /?
Чтоб получить список всех категорий и под категорий введите:
auditpol /list /subcategory:*
Чтоб отобразить текущую политику аудита для всех категорий и подкатегорий введите:
auditpol /get /category:*
Начиная с Windows Server 2008 R2 (серверные ОС) и Windows 7 (не серверные ОС) в политиках по адресу «Computer Configuration/Windows Settings/Security Settings/Advanced Audit Policy Configuration» появились более тонкие настройки аудита из более чем 50-ти различных настроек политики — Advanced Security Audit Policy Settings.
Если при использовании команды auditpol выскакивает «ошибка 0x00000057 произошла: Параметр задан неверно.», то скорее всего вы используете не тот язык в названии категорий, если ОС на русском языке, то категории аудита нужно писать на русском языке.
Понравилось? =) Поделись с друзьями:
Search code, repositories, users, issues, pull requests…
Provide feedback
Saved searches
Use saved searches to filter your results more quickly
Sign up