Follow our tested procedures to solve the issue right away
by Vladimir Popescu
Being an artist his entire life while also playing handball at a professional level, Vladimir has also developed a passion for all things computer-related. With an innate fascination… read more
Updated on
- The SSH keys are used to enable a connection to the server in a very safe and secure method.
- Sometimes, you may receive the SSH Permission denied message when attempting to connect.
- This could possibly be resolved by checking if the server address is correct or by changing the permissions of the SSH key.
SSH, or Secure Socket Shell, is an encrypted protocol that enables secure access to any remote device or server over an unsecured network.
When some of our readers tried to authenticate using these keys, they received an SSH permission denied message on their Windows 11 PC.
The users can unaware of the causes of this type of error message on the system. This is impacting the productivity of their work.
Some users also faced the SSH exchange identification error on the system but the link will bring you to a helpful guide to fix it.
Why do I get SSH permission denied message in Windows 11?
There could be a number of factors responsible for this error message, which are listed below:
- Incorrect server – If you are trying to connect to some wrong server with its IP address, you might receive an access denied message on your system
- Wrong password – Some users try to access the server using the wrong credentials
- Too many SSH keys – When there are a large number of SSH keys present in the system, so the system may select the wrong one from among those accessible
- SSH key permissions are too open – If the SSH key’s permissions are wide open and accessible to the majority of users in the system, the security purpose of employing the key may be jeopardized
If you are encountering this problem on your Windows 11 PC, this article will walk you through the five best solutions available, which are detailed below.
How do I bypass the SSH permission denied in Windows 11?
1. Check if you are connecting to the right server
This might sound silly, but many users tend to make this mistake and wonder why they are facing such an error message on their system.
When you are trying to connect to a server using the SSH key and the server address, you need to recheck the server address two to three times before trying to access it.
How we test, review and rate?
We have worked for the past 6 months on building a new review system on how we produce content. Using it, we have subsequently redone most of our articles to provide actual hands-on expertise on the guides we made.
For more details you can read how we test, review, and rate at WindowsReport.
There might be a possibility of missing a few numbers or misplacing the numbers in the server address. So always confirm the server address before continuing.
2. Try to log in with a password
You can always try logging in to the server using the password method. But for this to work, you need to enable the Password Authentication feature.
If it is already enabled, then you can access the server using the following command line:
ssh -o PreferredAuthentications=password -o PubkeyAuthentication=no [email protected]
In the above command, you have to replace [email protected] with the actual server address and password with the real password.
If the PasswordAuthentication is disabled, first you need to enable it and then generate a new ssh key using the following command: ssh-keygen -R server.IP.address
You have to replace the server.IP.address with the real IP address of the server.
3. Add your SSH key to the VPS server
In this method, you are trying to add the SSH key created on the system to the VPS server. This can be done by first generating a new SSH key on the system using the following command: ssh-keygen -t rsa
Now you might have to add this SSH key to the server by following this command: ssh-copy-id [email protected]
Here, you have to change the server.ip.address to the actual server address value and execute the command.
Also, disable the Password authentication feature and edit the ssh_config file for changing the sole authentication method to SSH keys.
- How to Type Accents on Windows 11
- How to Disable the Insert Your Security Key Into the USB Port popup
- DTS Sound Unbound for Windows 11: Download & Install
- Fix: EXCEPTION_ILLEGAL_INSTRUCTION Error on Windows 11
4. Manually select the key to use
When there are too many SSH keys available in the system, it can choose any random SSH key and create such issues.
So, you can execute the following command for making it choose the SSH key provided by you in the command: ssh -i /users/user_name/.shh/id_rsa [email protected]
Before executing the command, you have to replace /users/user_name/.shh/id_rsa with the path of the SSH key you want to add and [email protected] with the actual values.
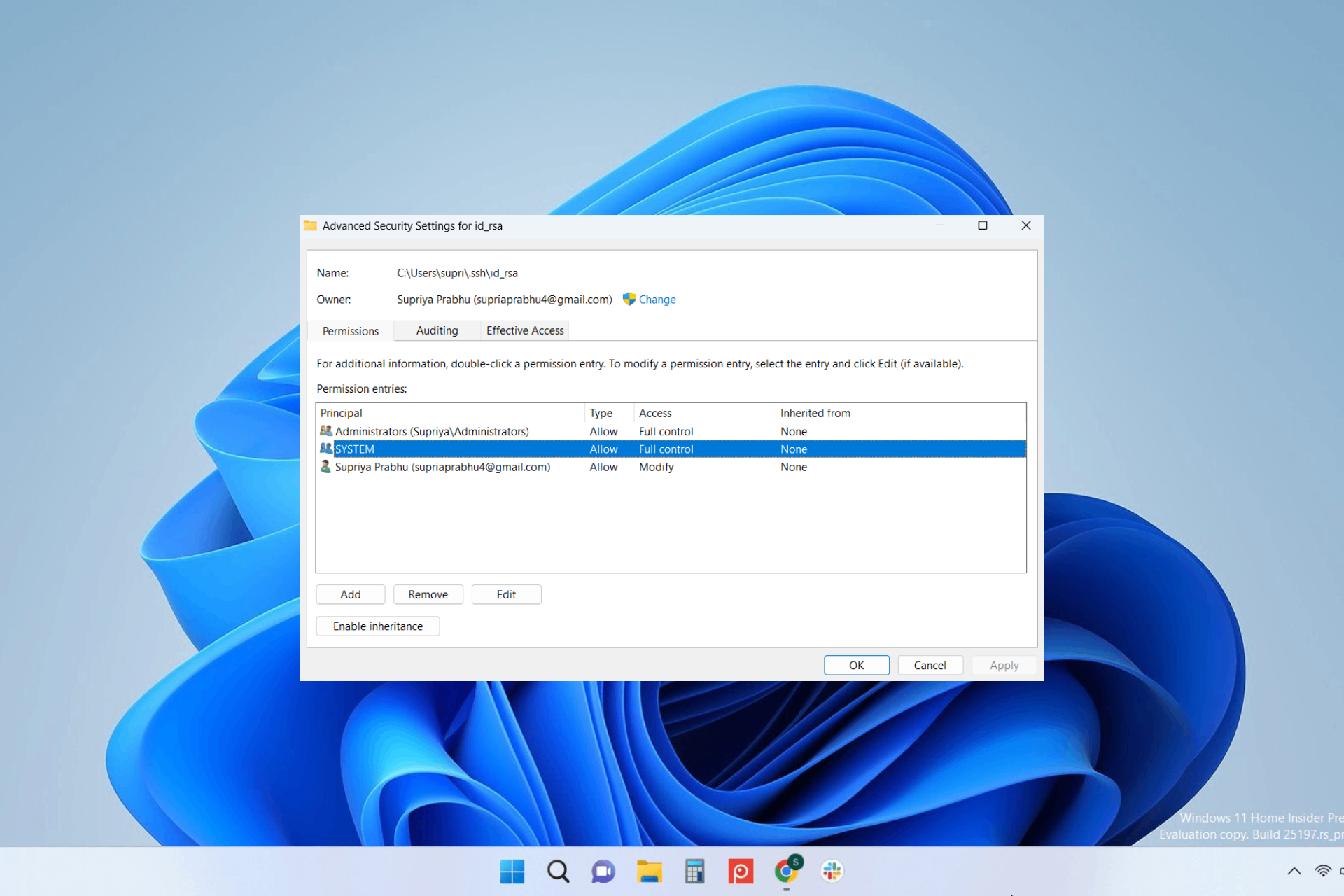
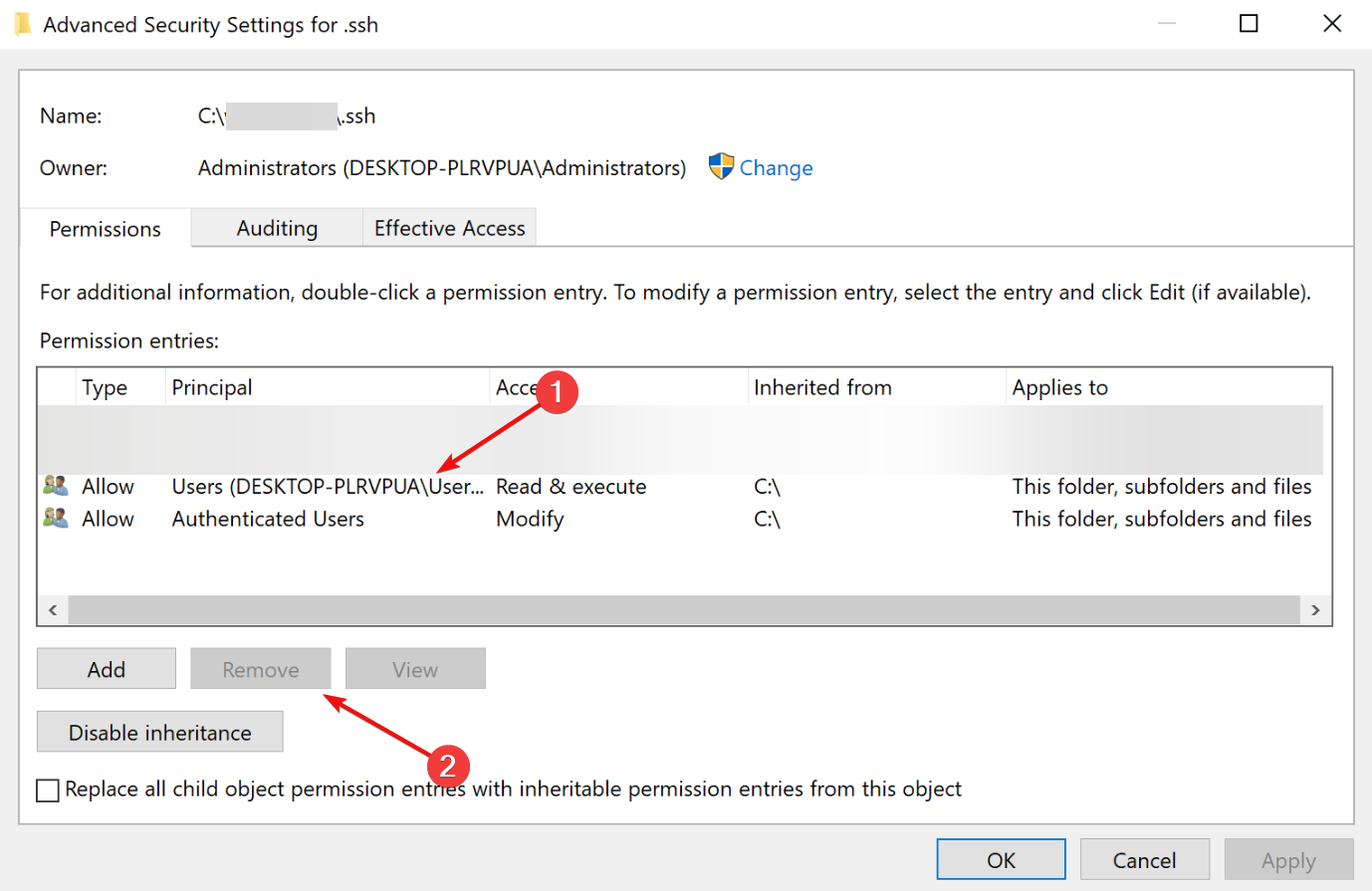
5. Change the permissions of your SSH key
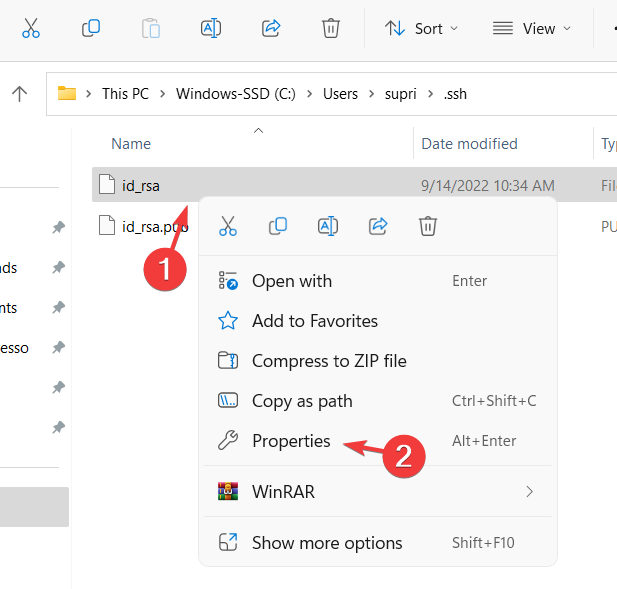
- Press the Windows key + F to launch File Explorer and open the folder where the SSH key is present.
- Right-click on the SSH key and click Properties from the context menu.
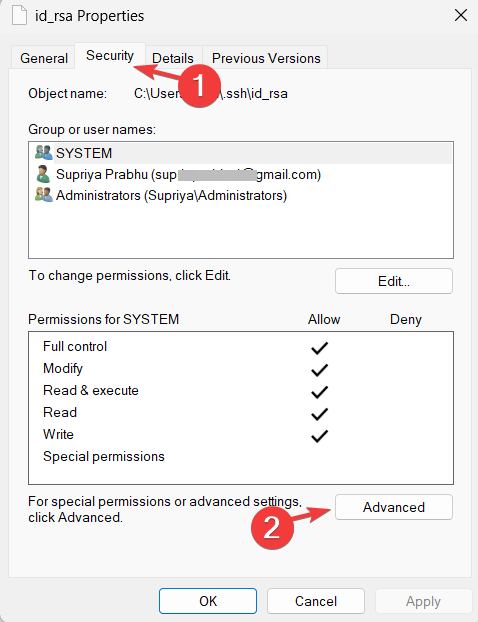
- Go to the Security tab and click Advanced at the bottom.
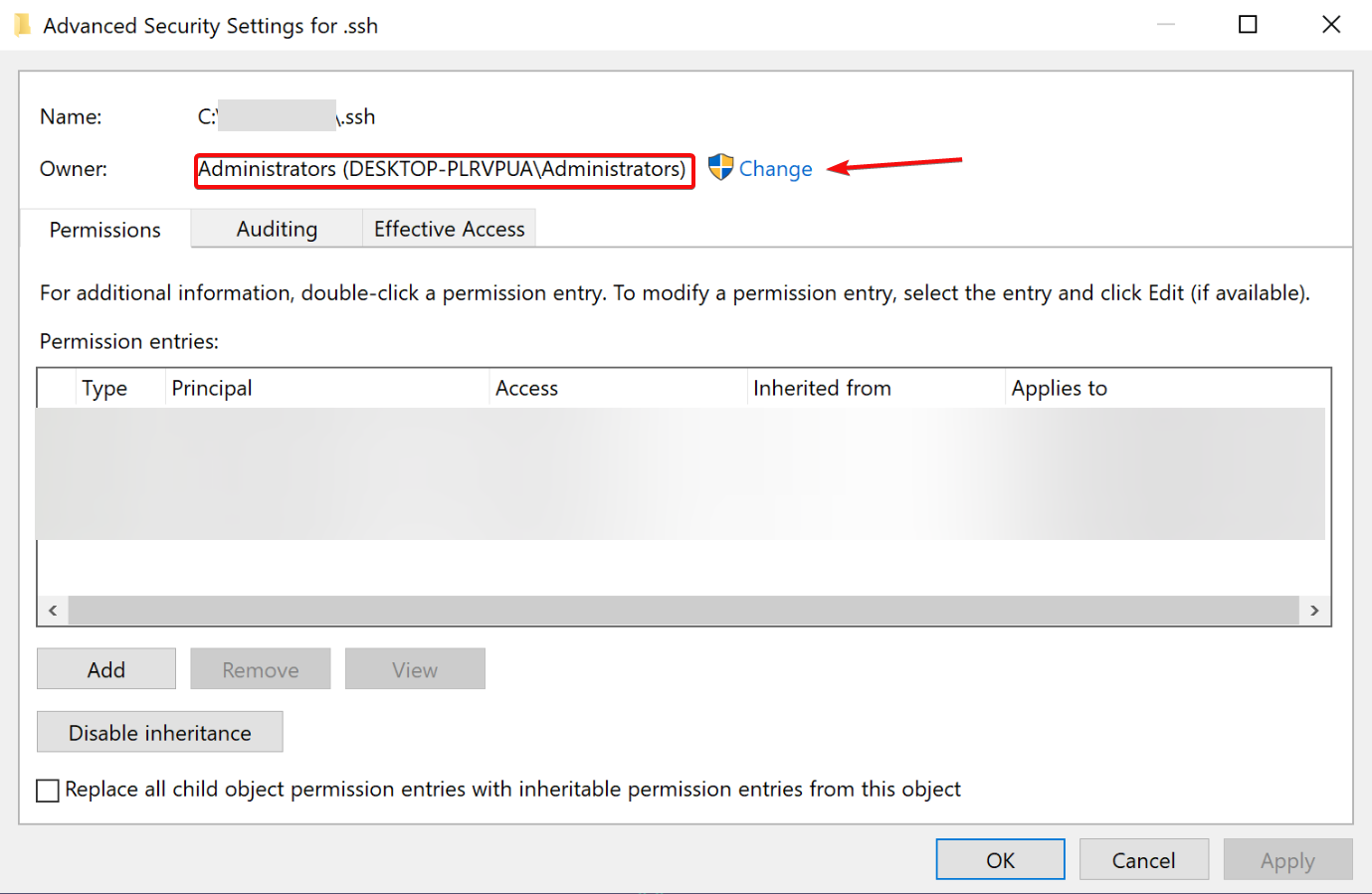
- Now click Disable inheritance at the bottom and make sure Owner is your username only.
- If the owner is somebody else, click Change and select your username.
- After this, choose any other users from the Permission entries section and click Remove.
- When done, click Apply and OK.
- This will change the permissions to the SSH key.
Where are SSH keys stored in Windows?
All the SSH keys are stored on the system drive in the following folder (replace username with the actual name): C:\Users\username\.ssh
Of course, if your system drive has another letter, you should replace the letter in the path above with your own.
Hope this article was worth reading and was able to resolve the SSH Permission denied issue.
You should also consult our guide on how to fix bad owner or permissions on SSH config because it might offer some additional information.
Our readers also complained that they encountered the Unable to establish host authenticity error. If you’re among them, read the highlighted guide for instructions to fix it.
If you know any other possible solutions for this problem or would like to ask something about this problem, use the comments section below.
Introduction
The SSH Permission denied error appears after permission-related settings are modified on the SSH server. Usual scenarios include a new package installation or the creation of new users.
In this tutorial, you will learn how to troubleshoot the SSH Permission denied error and reconnect to your SSH server.
Prerequisites
- SSH client on the local machine and SSH server on the remote system
- A user account to access the remote server (for password-based login)
- A user account with sudo or root privileges
The SSH Permission denied error appears when trying to SSH into a server:
Permission denied (publickey,gssapi-keyex,gssapi-with-mic)
Following the Permission denied statement, the bracket contains the attempted authentication methods that failed at the initiation of the connection. The error suggests that the public key is the issue, which is misleading.
One reason for the error may be sshd_config, the file that contains SSH server configuration. The other possibility is that the authorized_keys file has insufficient permissions. This file contains the list of public keys for the clients allowed to SSH into the server. Consequently, the system’s inability to read from the file results in the Permission denied error.
How to fix SSH Permission denied
Both solutions contain steps you need to perform on the server-side. Start by opening the terminal on your server and proceed with one of the solutions below.
Solution 1: Enable Password Authentication
If you want to use a password to access the SSH server, a solution for fixing the Permission denied error is to enable password login in the sshd_config file.
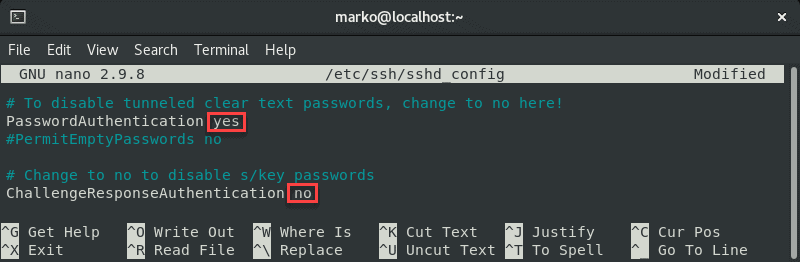
To do this, open the file in a text editor. This example uses the nano editor:
sudo nano /etc/ssh/sshd_configIn the file, find the PasswordAuthentication line and make sure it ends with yes.
Find the ChallengeResponseAuthentication option and disable it by adding no.
If lines are commented out, remove the hash sign # to uncomment them.
Save the file and exit.
Restart the SSH service by typing the following command:
sudo systemctl restart sshdSolution 2: Change File System Permissions
Using the password-based login as the SSH authentication method is not recommended due to security concerns. Therefore, the following solution may be preferable since it troubleshoots the public key authentication method.
First, open the sshd_config file using a text editor:
sudo nano /etc/ssh/sshd_configIn the file, make sure the following options are set as follows:
PermitRootLogin no
PubkeyAuthentication yes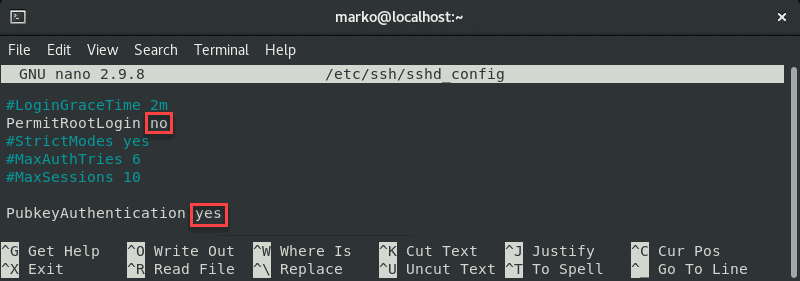
Note: The steps above are considered best security practices. If you need to use root login, set the relevant line to yes.
Comment out the GSSAPI-related options by adding the hash sign at the beginning of the line:
#GSSAPIAuthentication yes
#GSSAPICleanupCredentials no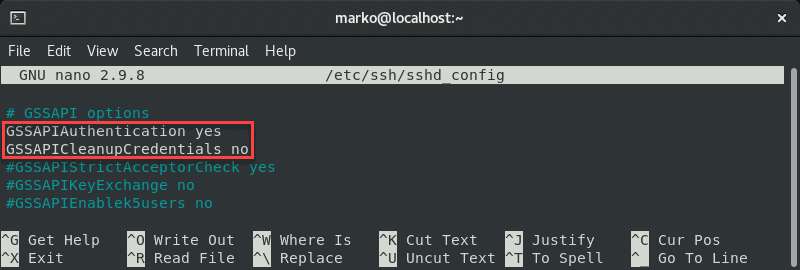
Also, make sure the UsePAM line is set to yes:
UsePAM yes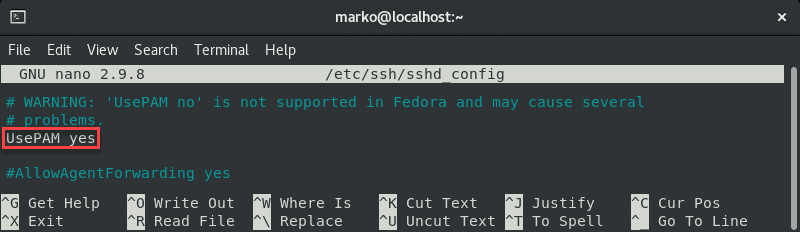
Save the file and restart the sshd service:
systemctl restart sshdNow navigate to your home folder and check the permissions:
ls -ld
If your owner permissions are not set to read, write, and execute (drwx------), use the chmod command to change them:
chmod 0700 /home/[your-username]Now go to the .ssh folder and recheck the permissions:
ls -ld
This directory should also have read, write, and execute permissions for the file owner. To enforce them, use chmod again:
chmod 0700 /home/your_home/.sshThe .ssh folder contains the authorized_keys file. Check its permissions with:
ls -ld authorized_keys
The file owner should have read and write permissions. To set them, use:
chmod 0600 /home/[username]/.ssh/authorized_keysNow try logging in with the key pair again. The output below shows a successful login attempt.
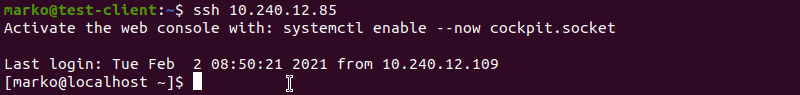
Conclusion
This tutorial covered the steps necessary to troubleshoot the SSH Permission denied (publickey,gssapi-keyex,gssapi-with-mic) error. By completing the steps in the guide, you should fix the error and successfully SSH into your server.
I’m trying to follow the SSH setup on a Win10 PC.
When I run the command, I am prompted for a password, but I always get a denied error.
ssh -p 2222 -o StrictHostKeyChecking=no localhost lost\user13@localhost's password: Permission denied, please try again.
If I try ssh-add, the password is accepted.
I have it working in WSL though I think it might there might be an issue with Win10?
OS: Win10
DDEV:
Win10 DDEV 1.18.2, 1.19.0-alpha3
WSL: 1.19.0-alpha3
#1 2018-07-14 15:26:02
- TheMohawkNinja
- Member
- Registered: 2017-07-11
- Posts: 39
[SOLVED] SSH into Windows permission denied
Hello,
I am trying to give my Arch machine the capability to SSH (via OpenSSH) into a Windows 10 machine. I’ve gotten it to the point where it will connect to the Windows 10 machine, however when I put in the password for the user, I receive a «Permission denied, please try again.» error.
-
I made sure that the user wasn’t attached to a Microsoft account to avoid potential authentication issues (it’s just a straight username and password).
-
I logged in to the user’s account in-case the profile would need to be generated.
-
I have tried both setting the user as a standard and administrator account.
-
I have made sure that port 22 is open on inbound traffic on the Windows 10 machine.
Unless the router is blocking local SSH access (which I won’t have the ability to check until Monday due to currently renting a router from my ISP which I discovered means I can’t do any configurations to said router), I have run out of things that I can think of to look for.
Last edited by TheMohawkNinja (2018-07-14 23:50:03)
#2 2018-07-14 15:30:29
- ewaller
- Administrator
- From: Pasadena, CA
- Registered: 2009-07-13
- Posts: 19,471
Re: [SOLVED] SSH into Windows permission denied
Post the actual output of the ssh command.
When you first tried, did ssh tell you that it could not verify the authenticity of the machine, and did you want to add the fingerprint of that machine to your known hosts? Did you?
This sounds like Windows «security» is rejecting the long in request. Check your logs on windows and see if it blocked a log on attempt
Nothing is too wonderful to be true, if it be consistent with the laws of nature — Michael Faraday
Sometimes it is the people no one can imagine anything of who do the things no one can imagine. — Alan Turing
—
How to Ask Questions the Smart Way
#3 2018-07-14 16:40:03
- TheMohawkNinja
- Member
- Registered: 2017-07-11
- Posts: 39
Re: [SOLVED] SSH into Windows permission denied
ewaller wrote:
Post the actual output of the ssh command.
ssh root@192.160.0.2
root@192.168.0.2’s password:
Permission denied, please try again.
ewaller wrote:
When you first tried, did ssh tell you that it could not verify the authenticity of the machine, and did you want to add the fingerprint of that machine to your known hosts? Did you?
Yes, I did add the fingerprint to the known hosts list, as I was prompted to.
ewaller wrote:
This sounds like Windows «security» is rejecting the long in request. Check your logs on windows and see if it blocked a log on attempt
Event Viewer seems to contradict what’s happening. It records the key check, a successful login of the user, and then an immediate logout of the user.
An account was logged off.
Subject:
Security ID: Ben_PC\root
Account Name: root
Account Domain: Ben_PC
Logon ID: 0x25AC185
Logon Type: 2
This event is generated when a logon session is destroyed. It may be positively correlated with a logon event using the Logon ID value. Logon IDs are only unique between reboots on the same computer.
------------------------------------------------------------
An account was logged off.
Subject:
Security ID: Ben_PC\root
Account Name: root
Account Domain: Ben_PC
Logon ID: 0x25AC1A7
Logon Type: 2
This event is generated when a logon session is destroyed. It may be positively correlated with a logon event using the Logon ID value. Logon IDs are only unique between reboots on the same computer.
------------------------------------------------------------
Special privileges assigned to new logon.
Subject:
Security ID: Ben_PC\root
Account Name: root
Account Domain: Ben_PC
Logon ID: 0x25AC185
Privileges: SeSecurityPrivilege
SeTakeOwnershipPrivilege
SeLoadDriverPrivilege
SeBackupPrivilege
SeRestorePrivilege
SeDebugPrivilege
SeSystemEnvironmentPrivilege
SeImpersonatePrivilege
------------------------------------------------------------
An account was successfully logged on.
Subject:
Security ID: SYSTEM
Account Name: BEN_PC$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Logon Information:
Logon Type: 2
Restricted Admin Mode: -
Virtual Account: No
Elevated Token: No
Impersonation Level: Impersonation
New Logon:
Security ID: Ben_PC\root
Account Name: root
Account Domain: Ben_PC
Logon ID: 0x25AC1A7
Linked Logon ID: 0x25AC185
Network Account Name: -
Network Account Domain: -
Logon GUID: {00000000-0000-0000-0000-000000000000}
Process Information:
Process ID: 0x1640
Process Name: C:\Windows\System32\svchost.exe
Network Information:
Workstation Name: BEN_PC
Source Network Address: -
Source Port: -
Detailed Authentication Information:
Logon Process: Advapi
Authentication Package: MICROSOFT_AUTHENTICATION_PACKAGE_V1_0
Transited Services: -
Package Name (NTLM only): -
Key Length: 0
This event is generated when a logon session is created. It is generated on the computer that was accessed.
The subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The logon type field indicates the kind of logon that occurred. The most common types are 2 (interactive) and 3 (network).
The New Logon fields indicate the account for whom the new logon was created, i.e. the account that was logged on.
The network fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The impersonation level field indicates the extent to which a process in the logon session can impersonate.
The authentication information fields provide detailed information about this specific logon request.
- Logon GUID is a unique identifier that can be used to correlate this event with a KDC event.
- Transited services indicate which intermediate services have participated in this logon request.
- Package name indicates which sub-protocol was used among the NTLM protocols.
- Key length indicates the length of the generated session key. This will be 0 if no session key was requested.
------------------------------------------------------------
An account was successfully logged on.
Subject:
Security ID: SYSTEM
Account Name: BEN_PC$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Logon Information:
Logon Type: 2
Restricted Admin Mode: -
Virtual Account: No
Elevated Token: Yes
Impersonation Level: Impersonation
New Logon:
Security ID: Ben_PC\root
Account Name: root
Account Domain: Ben_PC
Logon ID: 0x25AC185
Linked Logon ID: 0x25AC1A7
Network Account Name: -
Network Account Domain: -
Logon GUID: {00000000-0000-0000-0000-000000000000}
Process Information:
Process ID: 0x1640
Process Name: C:\Windows\System32\svchost.exe
Network Information:
Workstation Name: BEN_PC
Source Network Address: -
Source Port: -
Detailed Authentication Information:
Logon Process: Advapi
Authentication Package: MICROSOFT_AUTHENTICATION_PACKAGE_V1_0
Transited Services: -
Package Name (NTLM only): -
Key Length: 0
This event is generated when a logon session is created. It is generated on the computer that was accessed.
The subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The logon type field indicates the kind of logon that occurred. The most common types are 2 (interactive) and 3 (network).
The New Logon fields indicate the account for whom the new logon was created, i.e. the account that was logged on.
The network fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The impersonation level field indicates the extent to which a process in the logon session can impersonate.
The authentication information fields provide detailed information about this specific logon request.
- Logon GUID is a unique identifier that can be used to correlate this event with a KDC event.
- Transited services indicate which intermediate services have participated in this logon request.
- Package name indicates which sub-protocol was used among the NTLM protocols.
------------------------------------------------------------
An account was successfully logged on.
Subject:
Security ID: SYSTEM
Account Name: BEN_PC$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Logon Information:
Logon Type: 2
Restricted Admin Mode: -
Virtual Account: No
Elevated Token: No
Impersonation Level: Impersonation
New Logon:
Security ID: Ben_PC\root
Account Name: root
Account Domain: Ben_PC
Logon ID: 0x25AC1A7
Linked Logon ID: 0x25AC185
Network Account Name: -
Network Account Domain: -
Logon GUID: {00000000-0000-0000-0000-000000000000}
Process Information:
Process ID: 0x1640
Process Name: C:\Windows\System32\svchost.exe
Network Information:
Workstation Name: BEN_PC
Source Network Address: -
Source Port: -
Detailed Authentication Information:
Logon Process: Advapi
Authentication Package: MICROSOFT_AUTHENTICATION_PACKAGE_V1_0
Transited Services: -
Package Name (NTLM only): -
Key Length: 0
This event is generated when a logon session is created. It is generated on the computer that was accessed.
The subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The logon type field indicates the kind of logon that occurred. The most common types are 2 (interactive) and 3 (network).
The New Logon fields indicate the account for whom the new logon was created, i.e. the account that was logged on.
The network fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The impersonation level field indicates the extent to which a process in the logon session can impersonate.
The authentication information fields provide detailed information about this specific logon request.
- Logon GUID is a unique identifier that can be used to correlate this event with a KDC event.
- Transited services indicate which intermediate services have participated in this logon request.
- Package name indicates which sub-protocol was used among the NTLM protocols.
- Key length indicates the length of the generated session key. This will be 0 if no session key was requested.
------------------------------------------------------------
An account was successfully logged on.
Subject:
Security ID: SYSTEM
Account Name: BEN_PC$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Logon Information:
Logon Type: 2
Restricted Admin Mode: -
Virtual Account: No
Elevated Token: Yes
Impersonation Level: Impersonation
New Logon:
Security ID: Ben_PC\root
Account Name: root
Account Domain: Ben_PC
Logon ID: 0x25AC185
Linked Logon ID: 0x25AC1A7
Network Account Name: -
Network Account Domain: -
Logon GUID: {00000000-0000-0000-0000-000000000000}
Process Information:
Process ID: 0x1640
Process Name: C:\Windows\System32\svchost.exe
Network Information:
Workstation Name: BEN_PC
Source Network Address: -
Source Port: -
Detailed Authentication Information:
Logon Process: Advapi
Authentication Package: MICROSOFT_AUTHENTICATION_PACKAGE_V1_0
Transited Services: -
Package Name (NTLM only): -
Key Length: 0
This event is generated when a logon session is created. It is generated on the computer that was accessed.
The subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The logon type field indicates the kind of logon that occurred. The most common types are 2 (interactive) and 3 (network).
The New Logon fields indicate the account for whom the new logon was created, i.e. the account that was logged on.
The network fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The impersonation level field indicates the extent to which a process in the logon session can impersonate.
The authentication information fields provide detailed information about this specific logon request.
- Logon GUID is a unique identifier that can be used to correlate this event with a KDC event.
- Transited services indicate which intermediate services have participated in this logon request.
- Package name indicates which sub-protocol was used among the NTLM protocols.
- Key length indicates the length of the generated session key. This will be 0 if no session key was requested.
A logon was attempted using explicit credentials.
Subject:
Security ID: SYSTEM
Account Name: BEN_PC$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Logon GUID: {00000000-0000-0000-0000-000000000000}
Account Whose Credentials Were Used:
Account Name: root
Account Domain: Ben_PC
Logon GUID: {00000000-0000-0000-0000-000000000000}
Target Server:
Target Server Name: localhost
Additional Information: localhost
Process Information:
Process ID: 0x1640
Process Name: C:\Windows\System32\svchost.exe
Network Information:
Network Address: -
Port: -
This event is generated when a process attempts to log on an account by explicitly specifying that account’s credentials. This most commonly occurs in batch-type configurations such as scheduled tasks, or when using the RUNAS command.
------------------------------------------------------------
Cryptographic operation.
Subject:
Security ID: SYSTEM
Account Name: BEN_PC$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Cryptographic Parameters:
Provider Name: Microsoft Software Key Storage Provider
Algorithm Name: RSA
Key Name: Ssh-Rsa
Key Type: Machine key.
Cryptographic Operation:
Operation: Open Key.
Return Code: 0x0
------------------------------------------------------------
Key file operation.
Subject:
Security ID: SYSTEM
Account Name: BEN_PC$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Process Information:
Process ID: 5696
Process Creation Time: 2018-07-14T14:46:59.595658200Z
Cryptographic Parameters:
Provider Name: Microsoft Software Key Storage Provider
Algorithm Name: UNKNOWN
Key Name: Ssh-Rsa
Key Type: Machine key.
Key File Operation Information:
File Path: C:\ProgramData\Microsoft\Crypto\Keys\<key file name omitted>
Operation: Read persisted key from file.
Return Code: 0x0
------------------------------------------------------------
Key migration operation.
Subject:
Security ID: SYSTEM
Account Name: BEN_PC$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Process Information:
Process ID: 5696
Process Creation Time: 2018-07-14T14:46:59.595658200Z
Cryptographic Parameters:
Provider Name: Microsoft Software Key Storage Provider
Algorithm Name: RSA
Key Name: Ssh-Rsa
Key Type: Machine key.
Additional Information:
Operation: Export of persistent cryptographic key.
Return Code: 0x0
----------------------------------------------------------
Cryptographic operation.
Subject:
Security ID: SYSTEM
Account Name: BEN_PC$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Cryptographic Parameters:
Provider Name: Microsoft Software Key Storage Provider
Algorithm Name: RSA
Key Name: Ssh-Rsa
Key Type: Machine key.
Cryptographic Operation:
Operation: Open Key.
Return Code: 0x0
------------------------------------------------------------
Key file operation.
Subject:
Security ID: SYSTEM
Account Name: BEN_PC$
Account Domain: WORKGROUP
Logon ID: 0x3E7
Process Information:
Process ID: 5696
Process Creation Time: 2018-07-14T14:46:59.595658200Z
Cryptographic Parameters:
Provider Name: Microsoft Software Key Storage Provider
Algorithm Name: UNKNOWN
Key Name: Ssh-Rsa
Key Type: Machine key.
Key File Operation Information:
File Path: C:\ProgramData\Microsoft\Crypto\Keys\<key file name omitted>
Operation: Read persisted key from file.
Return Code: 0x0Last edited by TheMohawkNinja (2018-07-14 16:40:54)
#4 2018-07-14 16:43:09
- loqs
- Member
- Registered: 2014-03-06
- Posts: 16,581
Re: [SOLVED] SSH into Windows permission denied
`ssh -vvv root@192.160.0.2` should provide more output that might explain the disconnect
#5 2018-07-14 16:54:45
- ewaller
- Administrator
- From: Pasadena, CA
- Registered: 2009-07-13
- Posts: 19,471
Re: [SOLVED] SSH into Windows permission denied
So, you are hitting the Windows box and you are trying to log in as root. Is that the user name you created on Windows?
Nothing is too wonderful to be true, if it be consistent with the laws of nature — Michael Faraday
Sometimes it is the people no one can imagine anything of who do the things no one can imagine. — Alan Turing
—
How to Ask Questions the Smart Way
#6 2018-07-14 18:41:25
- ua4000
- Member
- Registered: 2015-10-14
- Posts: 333
Re: [SOLVED] SSH into Windows permission denied
What happens, if you install and start Putty on Windows, and try to ssh with your credentials into Windows?
#7 2018-07-14 23:49:49
- TheMohawkNinja
- Member
- Registered: 2017-07-11
- Posts: 39
Re: [SOLVED] SSH into Windows permission denied
loqs wrote:
`ssh -vvv root@192.160.0.2` should provide more output that might explain the disconnect
I forgot about verbosity lol.
After a few hours of a rabbit hole of Google searches related to what outputted from that, I managed to track down the issue: Password authentication was commented out in the configuration file and the keys that generated were in someway corrupted or not being read correctly which led to OpenSSH Server service not starting.
I am trying to configure git server and client on two local windows machines. I installed git software on both the machines. Enabled openssh server optional feature on the server and created a bare repository on the server. Then tried to clone the server’s bare repository on the client, it asked me the password of the server’s user but, even after I entered the right password it was giving the below error message.
Permission denied (publickey,password,keyboard-interactive).
I have tried to figure out the cause for the error. After browsing for this error on google I got to know that it is ssh not configured properly. One suggestion I found was to check if ssh working properly without git involvement using the command
ssh -Tv ram-[email protected], it also failed by giving below error message:
$ ssh -Tv [email protected]
OpenSSH_7.7p1, OpenSSL 1.0.2p 14 Aug 2018
debug1: Reading configuration data /etc/ssh/ssh_config
debug1: Connecting to 10.208.27.100 [10.208.27.100] port 22.
debug1: Connection established.
debug1: identity file /c/Users/Admin/.ssh/id_rsa type 0
debug1: key_load_public: No such file or directory
debug1: identity file /c/Users/Admin/.ssh/id_rsa-cert type -1
debug1: key_load_public: No such file or directory
debug1: identity file /c/Users/Admin/.ssh/id_dsa type -1
debug1: key_load_public: No such file or directory
debug1: identity file /c/Users/Admin/.ssh/id_dsa-cert type -1
debug1: key_load_public: No such file or directory
debug1: identity file /c/Users/Admin/.ssh/id_ecdsa type -1
debug1: key_load_public: No such file or directory
debug1: identity file /c/Users/Admin/.ssh/id_ecdsa-cert type -1
debug1: key_load_public: No such file or directory
debug1: identity file /c/Users/Admin/.ssh/id_ed25519 type -1
debug1: key_load_public: No such file or directory
debug1: identity file /c/Users/Admin/.ssh/id_ed25519-cert type -1
debug1: key_load_public: No such file or directory
debug1: identity file /c/Users/Admin/.ssh/id_xmss type -1
debug1: key_load_public: No such file or directory
debug1: identity file /c/Users/Admin/.ssh/id_xmss-cert type -1
debug1: Local version string SSH-2.0-OpenSSH_7.7
debug1: Remote protocol version 2.0, remote software version OpenSSH_for_Windows_7.6
debug1: match: OpenSSH_for_Windows_7.6 pat OpenSSH* compat 0x04000000
debug1: Authenticating to 10.208.27.100:22 as 'ram-pc1'
debug1: SSH2_MSG_KEXINIT sent
debug1: SSH2_MSG_KEXINIT received
debug1: kex: algorithm: curve25519-sha256
debug1: kex: host key algorithm: ecdsa-sha2-nistp256
debug1: kex: server->client cipher: [email protected] MAC: <implicit> compression: none
debug1: kex: client->server cipher: [email protected] MAC: <implicit> compression: none
debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
debug1: Server host key: ecdsa-sha2-nistp256 SHA256:27NSp0TODhiZ68zbYLvsaqPNMp8tE0ZanMeoeQp+u14
debug1: Host '10.208.27.100' is known and matches the ECDSA host key.
debug1: Found key in /c/Users/Admin/.ssh/known_hosts:1
debug1: rekey after 134217728 blocks
debug1: SSH2_MSG_NEWKEYS sent
debug1: expecting SSH2_MSG_NEWKEYS
debug1: SSH2_MSG_NEWKEYS received
debug1: rekey after 134217728 blocks
debug1: SSH2_MSG_EXT_INFO received
debug1: kex_input_ext_info: server-sig-algs=<ssh-ed25519,ssh-rsa,rsa-sha2-256,rsa-sha2-512,ssh-dss,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521>
debug1: SSH2_MSG_SERVICE_ACCEPT received
debug1: Authentications that can continue: publickey,password,keyboard-interactive
debug1: Next authentication method: publickey
debug1: Offering public key: RSA SHA256:2KyRU6bbWWkN+IBYN6xiuWQuHl0pKL6Cim6K4/6RBek /c/Users/Admin/.ssh/id_rsa
debug1: Authentications that can continue: publickey,password,keyboard-interactive
debug1: Trying private key: /c/Users/Admin/.ssh/id_dsa
debug1: Trying private key: /c/Users/Admin/.ssh/id_ecdsa
debug1: Trying private key: /c/Users/Admin/.ssh/id_ed25519
debug1: Trying private key: /c/Users/Admin/.ssh/id_xmss
debug1: Next authentication method: keyboard-interactive
debug1: Authentications that can continue: publickey,password,keyboard-interactive
debug1: Next authentication method: password
[email protected]'s password:
debug1: Authentications that can continue: publickey,password,keyboard-interactive
Permission denied, please try again.
[email protected]'s password:
debug1: Authentications that can continue: publickey,password,keyboard-interactive
Permission denied, please try again.
[email protected]'s password:
debug1: Authentications that can continue: publickey,password,keyboard-interactive
debug1: No more authentication methods to try.
[email protected]: Permission denied (publickey,password,keyboard-interactive).
Below is my ssh_config file settings:
#Port 22
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::
#HostKey __PROGRAMDATA__/ssh/ssh_host_rsa_key
#HostKey __PROGRAMDATA__/ssh/ssh_host_dsa_key
#HostKey __PROGRAMDATA__/ssh/ssh_host_ecdsa_key
#HostKey __PROGRAMDATA__/ssh/ssh_host_ed25519_key
# Ciphers and keying
#RekeyLimit default none
# Logging
#SyslogFacility AUTH
#LogLevel INFO
# Authentication:
#LoginGraceTime 2m
#PermitRootLogin prohibit-password
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10
#PubkeyAuthentication yes
# The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2
# but this is overridden so installations will only check .ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keys
#AuthorizedPrincipalsFile none
# For this to work you will also need host keys in %programData%/ssh/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes
# To disable tunneled clear text passwords, change to no here!
#PasswordAuthentication yes
#PermitEmptyPasswords no
#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
#PermitTTY yes
#PrintMotd yes
#PrintLastLog yes
#TCPKeepAlive yes
#UseLogin no
#PermitUserEnvironment no
#ClientAliveInterval 0
#ClientAliveCountMax 3
#UseDNS no
#PidFile /var/run/sshd.pid
#MaxStartups 10:30:100
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none
# no default banner path
#Banner none
# override default of no subsystems
Subsystem sftp sftp-server.exe
# Example of overriding settings on a per-user basis
#Match User anoncvs
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
I have spent a lot of time to resolve this error. But not succeeded. Please help in solving this problem. Thanks in advance.