Some people have offered to provide OpenSSL binary distributions for selected operating systems. The condition to get a link here is that the link is stable and can provide continued support for OpenSSL for a while.
Note: many Linux distributions come with pre-compiled OpenSSL packages. Those are already well-known among the users of said distributions, and will therefore not be mentioned here. If you are such a user, we ask you to get in touch with your distributor first. This service is primarily for operating systems where there are no pre-compiled OpenSSL packages.
Important Disclaimer:
The listing of these third party products does not imply any endorsement by the OpenSSL project, and these organizations are not affiliated in any way with OpenSSL other than by the reference to their independent web sites here. In particular any donations or payments to any of these organizations will not be known to, seen by, or in any way benefit the OpenSSL project.
To make a donation to the project directly go to our github sponsors page. Alternatively consider becoming a corporate sponsor.
Use these OpenSSL derived products at your own risk; these products have not been evaluated or tested by the OpenSSL project.
| Product | Description | URL |
|---|---|---|
| OpenSSL for Web (using WebAssembly) | OpenSSL 3.0 ported to WebAssembly (in October 2021). Uses Emscripten and xterm.js to emulate a terminal in your browser. WASI binaries are supported too. The Wasm execution happens using WebWorkers if the browser supports them. Originally developed for the cryptology playground «CrypTool-Online». Code is open-source on GitHub. | OpenSSL-React app: https://github.com/cryptool-org/openssl-webterm Basic Wasm terminal: https://github.com/cryptool-org/wasm-webterm Running sample: https://www.cryptool.org/en/cto/openssl |
| OpenSSL for Windows | Works with MSVC++, Builder 3/4/5, and MinGW. Comes in form of self-install executables. | https://slproweb.com/products/Win32OpenSSL.html |
| OpenSSL for Windows | Pre-compiled Win32/64 libraries without external dependencies to the Microsoft Visual Studio Runtime DLLs, except for the system provided msvcrt.dll. | https://indy.fulgan.com/SSL/ |
| OpenSSL for Windows | Reproducible builds with latest MinGW-w64, 64/32-bit, static/dynamic libs and executable. | https://github.com/curl/curl-for-win |
| OpenSSL for Solaris | Versions for Solaris 2.5 — 11 SPARC and X86 | http://www.unixpackages.com/ |
| OpensSSL for Windows, Linux, OSX, Android | Pre-compiled packages at conan.io package manager: Windows x86/x86_64 (Visual Studio 10, 12, 14, 15) Linux x86/x86_64 (gcc 4.6, 4.8, 4.9, 5, 6, 7) OSx (Apple clang). Cross-building ready recipe: Linux ARM, Android. |
https://www.conan.io https://conan.io/center/openssl |
| OpenSSL for Windows | Pre-compiled Win32/64 1.0.2, 1.1.0, 1.1.1 and 3.0 libraries without external dependencies, primarily built for François Piette’s Internet Component Suite (ICS) for Embarcadero (Borland) Delphi and C++ development tools, but may be used for any Windows applications. The OpenSSL DLLs and EXE files are digitally code signed ‘Open Source Developer, François PIETTE’, so applications can self verify them for corruption. | http://wiki.overbyte.eu/wiki/index.php/ICS_Download |
| OpenSSL for Windows | OpenSSL 3.1, 3.0, and 1.1.1 pre-compiled for Microsoft Windows with no external dependencies. The binary distributions can be used standalone or integrated into any Windows application. Installer, EXEs and DLLs are digitally signed with ‘FireDaemon Technologies Limited’ Extended Validation (EV) code signing certificate. | https://www.firedaemon.com/get-openssl |
| OpenSSL for NonStop | Pre-compiled NonStop ia64/x86 1.0.2, 1.1.1 executables and libraries for the HPE NonStop Operating Systems. Threaded versions are included. The SPT version depends on FLOSS, otherwise there are no other dependencies. 32-bit versions are available. The builds are done by the ITUGLIB Technical Committee as part of Connect. | https://ituglib.connect-community.org/apps/Ituglib/SrchOpenSrcLib.xhtml |
Engines[edit]
Some third parties provide OpenSSL compatible engines. As for the binaries above the following disclaimer applies:
Important Disclaimer:
The listing of these third party products does not imply any endorsement by the OpenSSL project, and these organizations are not affiliated in any way with OpenSSL other than by the reference to their independent web sites here. In particular any donations or payments to any of these organizations will not be known to, seen by, or in any way benefit the OpenSSL project.
| Product | Description | URL |
|---|---|---|
| Intel® QuickAssist Technology engine | Intel® QuickAssist Technology (http://www.intel.com/content/www/us/en/embedded/technology/quickassist/overview.html) provides acceleration for a number of cryptographic algorithms. QAT_engine adds support for Intel® QuickAssist Technology to OpenSSL-1.1.0 via the ENGINE framework. The definitive list of algorithms exposed into OpenSSL (a subset of those supported in the device) is defined on the associated github page. | https://github.com/01org/QAT_Engine |
| ATECCX08 engine | Support for the Atmel ATECC508A (http://www.atmel.com/devices/ATECC508A.aspx) hardware to provide secure key storage, ECC cryptographic calculations for the ECC NIST P-256 curve, and FIPS certified hardware Random Number Generator. | https://github.com/AtmelCSO/cryptoauth-openssl-engine |
| GOST engine | A reference implementation of the Russian GOST crypto algorithms for OpenSSL. The presence of this engine also enables the built-in OpenSSL support for GOST TLS ciphersuites. (Note: this engine is for OpenSSL version 1.1.0 and above. Previous versions of OpenSSL used a built-in GOST engine) | https://github.com/gost-engine/engine |
| ISARA Radiate Solution Suite OpenSSL Connector | Commercially available engine and source code patch for OpenSSL 1.0.2 branch. The ISARA Radiate OpenSSL Connector lets you implement OpenSSL using quantum safe algorithms. ISARA Radiate (https://www.isara.com/isara-radiate/) gives you the cryptographic building blocks to create applications that will resist attacks by quantum computers. | https://www.isara.com/openssl/1/ |
| BEE2EVP engine | Implements the Belarusian national cryptography: symmetric and public-key encryption, MAC, AEAD, hashing, digital signature. Encapsulates the Bee2 core cryptographic library into OpenSSL using the EVP interface. | https://github.com/bcrypto/bee2evp |
| wolfSSL wolfEngine | wolfSSL has an OpenSSL engine, wolfEngine. wolfEngine is structured as a separate standalone library which links against wolfSSL (libwolfssl) and OpenSSL. wolfEngine implements and exposes an OpenSSL engine implementation which wraps the wolfCrypt native API internally. Algorithm support matches that as listed on the wolfCrypt FIPS 140-2 certificate #3389. | https://github.com/wolfSSL/wolfEngine |
| wolfSSL wolfProvider | Similar to the wolfEngine above, the wolfSSL team has also created the wolfProvider. The wolfProvider is structured as a separate standalone library which links against wolfSSL (libwolfssl) and OpenSSL 3.0.0 using the new provider API. Algorithm support matches that as listed on the wolfCrypt FIPS 140-2 certificate #3389. | https://github.com/wolfSSL/wolfProvider |
Table of Contents
- About OpenSSL
- Download OpenSSL
- Installation Instructions
- OpenSSL ZIP Files
- OpenSSL Windows Installer
- OpenSSL Screenshot
- OpenSSL Documentation
- Checking SSL / TLS Certificate Validity with Certify One
- Compiling OpenSSL From Source
- Release Policy
- Source
- Build Script
- Compilation
- Integrating OpenSSL with Your Visual Studio Project
- Additional Include Directories
- Additional Library Directories
- Privilege Escalation Mitigation
- Compatibility and Support Matrix
- License, Warranty, and Support
- Acknowledgments
- Buy SSL / TLS Certificates
About OpenSSL
OpenSSL is a popular open-source, publicly available software library that provides a robust, full-featured set of cryptographic functions and tools to secure communications over computer networks. When we build and ship FireDaemon Certify One, FireDaemon Fusion, and FireDaemon Lozenge we try to ensure it contains the most recent version of OpenSSL. We thought it would be useful to make our OpenSSL Binary Distribution available to you to download and use free of charge. The key advantages of using our OpenSSL Binary Distribution for Microsoft Windows over others that are available are:
- No need to deploy various software tools in order to attempt to compile the source from scratch. Our build script is available for free too if you do want to compile OpenSSL yourself.
- No external dependencies. There is no need to install or distribute the Visual C++ Redistributable Runtime (MSVC). There is an implicit dependency on the Windows Universal C Runtime (UCRT) which is included by default in all modern versions of Microsoft Windows.
- Packaged for simple deployment and use case scenarios including standalone, embeddable, deployable, or portable
- Digitally signed with our Extended Validation (EV) code signing certificate in order to avoid Windows SmartScreen warnings, and increase trust by virtue of Sectigo’s authentication and verification procedures on us: FireDaemon Technologies Limited and validatable binary integrity to meet your compliance requirements.
Download OpenSSL
Pre-compiled executables (EXE) and libraries (DLL) for Microsoft Windows Operating Systems. The distributions can be used standalone or integrated into any Windows application. The EXE and DLL are digitally signed with our Extended Validation (EV) code signing certificate. Note that we do not have an EAR CCL ECCN for our Binary Distributions. This is intentional. You must seek independent legal advice prior to using/integrating/exporting our Binary Distributions in your own products.
|
Download OpenSSL Binary Distributions for Microsoft Windows |
|
|
OpenSSL 3.1.3 ZIP File September 2023 SHA2-256 19AB74ECFCC724C70978E115130FA1A0779F0F8315E0F3554496331A031C514C Git commit openssl-3.1.3-0-g7b649c73a2 |
OpenSSL 3.1.3 Windows x64 Installer
SHA2-256 C897942F2F319E070DCD0D882149E40B700ACAAA27532CC31439E172B5840DF1 Git commit openssl-3.1.3-0-g7b649c73a2 |
|
OpenSSL 3.0.11 ZIP File September 2023 SHA2-256 14B0825F8C9885EDC14E205300CA0005B13F5C2162936ABBDAD431258E63F2A0 Git commit openssl-3.0.11-0-g6ba3884c32 |
OpenSSL 1.1.1w ZIP File
SHA2-256 1870B15BF6749E65FFBBADF52CDFF3EE0E9F02943550BF4395574BB432AF3EB8 Git commit OpenSSL_1_1_1w-0-ge04bd3433f |
|
For 64-bit / Win64 / x64 and 32-bit / Win32 / x86 Microsoft Windows Operating Systems To calculate / verify the SHA2-256 checksums please use FireDaemon Lozenge! OpenSSL maintains a list of 3rd-party maintained binary distributions of OpenSSL. Please review our Release Policy before downloading and using this distribution. You must seek independent legal advice prior to using / integrating / exporting our Binary Distributions. |
Installation Instructions
OpenSSL ZIP Files
- Follow the instructions below if you have downloaded one of the ZIP files above and want to deploy OpenSSL manually (e.g. on the local hard disk or on a USB drive for a portable installation)
- Download the appropriate FireDaemon OpenSSL Binary Distribution ZIP file via the links above.
- Unpack the contents of the «openssl-1.1» or «openssl-3» or «openssl-3.1.0» folder in the respective ZIP file to a temporary directory (e.g. C:\Temp)
- Copy the contents of (i.e. the files and directories contained within) the x64 folder or x86 folder to your target directory (e.g. C:\OpenSSL)
- Copy the ssl folder and contents to the target directory (e.g. C:\OpenSSL).
The commands to copy the files correctly from the location where you unpacked the ZIP file (assuming C:\Temp) are as follows:
: For OpenSSL 1.1 cd C:\Temp\openssl-1.1 : For OpenSSL 3.0 and 3.1 cd C:\Temp\openssl-3 : Copy the binaries specific to your platform : Copy 64-bit binaries robocopy x64 C:\OpenSSL /E : Or, copy 32-bit binaries. Don't copy both! robocopy x86 C:\OpenSSL /E : Copy the ssl folder robocopy ssl C:\OpenSSL\ssl /E
Your directory structure should look as follows:
C:\OpenSSL>dir /b bin include lib ssl
To use OpenSSL, simply open an elevated Command Prompt then (adjusting the path in OPENSSL_HOME to suit your manual installation):
: You can set OPENSSL_HOME=%~dp0 in a batch script for portable installs set OPENSSL_HOME=C:\OpenSSL set OPENSSL_CONF=%OPENSSL_HOME%\ssl\openssl.cnf set PATH=%OPENSSL_HOME%\bin;%PATH% cd /d %OPENSSL_HOME% openssl version -a
To create a certificate signing request and private key using the same environment variables as above :
openssl genrsa -out server.key 4096 openssl req -new -key server.key -out server.csr -sha256 openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
OpenSSL Windows Installer
Instead of downloading the ZIP file, and for convenience, you can download our Windows installer via the link above in the «Download OpenSSL» section. Installation is straightforward. OpenSSL is installed into the following file system locations. These locations are specified during the build and follow OpenSSL’s own conventions. Thanks to Advanced Installer for helping us out.
%PROGRAMFILES%\FireDaemon OpenSSL 3 %PROGRAMFILES%\Common Files\FireDaemon SSL 3
You can silently install OpenSSL with the following command in an elevated command prompt:
FireDaemon-OpenSSL-x64-3.1.3.exe /exenoui /exelog fdopenssl3.log /qn /norestart REBOOT=ReallySuppress
You can silently uninstall OpenSSL with the following command in an elevated command prompt:
: Verify Product GUID
wmic product where name="FireDaemon OpenSSL 3" get IdentifyingNumber
: Uninstall silently
msiexec /x {A8B0D50D-F952-49EB-A53A-BDB95BA32284} /quiet /noreboot
OpenSSL Screenshot
Below is a screenshot showing the executed commands at an elevated command prompt:
OpenSSL Documentation
Please refer to OpenSSL’s documentation.
Checking SSL / TLS Certificate Validity with Certify One
FireDaemon Certify One allows you to audit, check, inspect, and validate SSL / TLS certificates and certificate chains. Fortify also has a browser-based TLS Encryption Check Tool available.
Compiling OpenSSL From Source
Release Policy
Whenever we release an updated version of FireDaemon Fusion, FireDaemon Certify One, or OpenSSL gets updated with security fixes, we will provide the latest tagged version of the OpenSSL stable branch. The currently deployed OpenSSL library commit versions are listed underneath the download links above. Commit is described viz:
git describe --always --tag --long --first-parent --dirty
Source
We directly pull from OpenSSL’s official GitHub repository.
Build Script
You can use our build script to create the binary distributions. The build script has the following dependencies:
- Visual Studio Community Edition
- Git for Windows
- Strawberry Perl.
Compilation
The actual command line to build OpenSSL is as follows (where %toolset% is VC-WIN32 and VC-WIN64A respectively):
perl ..\Configure %toolset% no-asm no-ssl3 no-zlib no-comp no-autoload-config --api=1.1.0 --prefix="%installdir%" --openssldir="%commoninstalldir%" -DOPENSSL_NO_DEPRECATED
Integrating OpenSSL with Your Visual Studio Project
To use the headers and libraries present in OpenSSL in your Visual Studio project, you will need to configure the properties of your project.
Additional Include Directories
Prepend «C:\Program Files\FireDaemon Open SSL 3\include»; to Property Pages -> C/C++ -> General -> Additional Include Directories in your project per the screenshot below (adjusting the prepended path to suit your installation):
Additional Library Directories
Prepend «C:\Program Files\FireDaemon Open SSL 3\lib»; to Property Pages -> Linker -> General -> Additional Library Directories in your project per the screenshot below (adjusting the prepended path to suit your installation):
Privilege Escalation Mitigation
When building OpenSSL, the build scripts bake the default location of the library (ie. the installation directory) and the SSL configuration into the final product. By default, OpenSSL automatically loads the SSL configuration file from the default file system location. This leads to an easily exploitable privilege escalation scenario documented in CVE-2019-12572. Our build of OpenSSL mitigates this flaw using the following preventative measures:
- The target directories we have chosen are Windows’ default system program files directories assuming a 64-bit architecture with a shared configuration file directory common to both x64 and x86:
- x64: C:\Program Files\FireDaemon OpenSSL, C:\Program Files\Common Files\FireDaemon SSL
- x86: C:\Program Files (x86)\FireDaemon OpenSSL, C:\Program Files\Common Files\FireDaemon SSL
- To mitigate security holes even on non-default installations, we build the library such that it doesn’t automatically load the SSL configuration. Hence, when using the OpenSSL tools or the DLLs in your products you have to explicitly load the SSL configuration.
- All FireDaemon software products that utilise OpenSSL initialise the OpenSSL library at runtime using a flag that prevents the loading of the default configuration.
Compatibility and Support Matrix
The table below provides a compatibility and support matrix, mapping specific compatible Microsoft Windows operating system versions to specific FireDaemon OpenSSL software versions.
| OpenSSL Versions |
OpenSSL 3.1, 3.0, and 1.1.1 | |
| Windows Operating System Version | 32-bit (x86) | 64-bit (x64) |
| Windows XP (1) | ||
| Windows Vista (1) | ||
| Windows 7 (1) | ||
| Windows 8 (1) | ||
| Windows 8.1 (1) | ||
| Windows 10 | ||
| Windows 11 | ||
| Server 2008 (2) | ||
| Server 2008 R2 (2) | ||
| Server 2012 | ||
| Server 2012 R2 | ||
| Server 2016 | ||
| Server 2019 | ||
| Server 2022 |
(1) Windows Desktop Operating System is End of Support
(2) Windows Server Operating System is End of Support
| Compatible / Supported | The software product is designed to be installed on the Microsoft Windows operating system version. The operating system version plus software version combination is actively supported by us on the proviso that the 32-bit (x86) version is deployed on a 32-bit (x86) operating system and the 64-bit (x64) version is deployed on a 64-bit (x64) operating system. Please see the License, Warranty, and Support section below. |
| Compatible / Unsupported | The software product should install on the Microsoft Windows operating system version. The operating system version plus software version combination is not supported by us. This is typically due to the operating system version reaching End of Support. |
| Incompatible / Unsupported | The software product should not or does not install on the Microsoft Windows operating system version or does not work. The operating system version plus software version combination is not supported by us. |
License, Warranty, and Support
Our OpenSSL Binary Distribution is free to use and redistribute. Product use, redistribution, and warranty are governed by the OpenSSL License. If you have questions regarding OpenSSL, wish to report bugs, or require implementation guidance please consider joining the OpenSSL Community.
Acknowledgments
This product includes:
- Software developed by the OpenSSL Project for use in the OpenSSL Toolkit
- Cryptographic software written by Eric Young
- Software written by Tim Hudson.
Buy SSL / TLS Certificates
OpenSSL 1.1.1i — криптографическая библиотека с кодом открытого типа «Open source». Она предназначена для работы с протоколами SSL и TLS, а также доступна для платформ Windows и Unix.
Основные возможности
- Поддержка практически всех алгоритмов хеширования, шифрования и электронной подписи.
- Реализация большинства криптографических стандартов.
- Работа с ключами (RSA, DH, DSA) и сертификатами.
- Поддержка сертификатов X.509.
- Формирование приватных ключей CRT и CSR.
- Тестирование соединений: SSL и TLS.
Удобство использования
Библиотеку используют все разработчики WEB-приложений, поскольку она отвечает за безопасность. При создании сайта обязательно необходимо создавать SSL-ключ (файл, позволяющий связать криптографический ключ с доменным именем или сервером). Библиотеку можно использовать для тестирования соединений SSL и TTL.
Специальных приложений для работы с библиотекой в графическом интерфейсе не существует. В этом случае приходится довольствоваться только консольным режимом, в котором требуется вводить команды.
Для новичка, на первый взгляд, покажется все очень сложным, но на самом деле это не так. Для работы с библиотекой в Интернете можно найти множество инструкций и видеоуроков, в которых детально объясняются основные аспекты ее использования.
«Изюминка» библиотеки заключается в открытом коде, в который можно вносить изменения, переписывать и удалять ненужные функции, т. е. создавать свой собственный модуль.
Разработчики рекомендуют скачивать ее с официального сайта. Однако не стоит забывать и о «GitHub» (хранилище, которое IT-специалисты используют для обмена программным кодом).
Достоинства
- Поддержка алгоритмов шифрования, хеширования.
- Работа с сертификатами и электронной подписью.
- Тестирование SSL/TTL-соединений.
- Гибкая настройка параметров создаваемых сертификатов.
- Поддержка CRT и CSR, а также сертификата X.509.
- Работа с ключами RSA, DH и DSA.
- Бесплатная версия.
- Открытый код (можно вносить свои коррективы в исходный программный код библиотеки).
- Высокая степень надежности.
- Реализация всех типов криптографических стандартов.
Недостатки
- Отсутствие графического интерфейса.
- Сложный синтаксис команд для новичков.
Библиотека является неотъемлемой частью каждого WEB-приложения и напрямую связана с его безопасностью. Благодаря открытому коду, ее можно изменить и доработать под свои предпочтения.
This project offers OpenSSL for Windows (static as well as shared). It supports: FIPS Object Module 1.2 and CAPI engine. It includes most of the features available on Linux. It works out of the box so no additional software is needed.
Blocks phishing, spam emails, malware, viruses, ransomware and malicious email threats. Provides advanced yet easy to use email spam filtering. Perfect for businesses, schools and managed service providers.
User Ratings
5.0
out of 5 stars
★★★★★
★★★★
★★★
★★
★
ease
1 of 5
2 of 5
3 of 5
4 of 5
5 of 5
4 / 5
features
1 of 5
2 of 5
3 of 5
4 of 5
5 of 5
4 / 5
design
1 of 5
2 of 5
3 of 5
4 of 5
5 of 5
4 / 5
support
1 of 5
2 of 5
3 of 5
4 of 5
5 of 5
4 / 5
Additional Project Details
В эпоху кибервойн единственная разумная позиция – быть параноиком, а это означает, помимо прочего, быть параноиком по поводу обновлений программного обеспечения.
Взять к примеру OpenSSL.
Эта криптографическая библиотека с открытым исходным кодом, которая реализует протоколы Transport Layer Security (TLS) и Secure Sockets Layer (SSL), разработана для «защиты связи по компьютерным сетям от перехвата», но угадайте, что?
С самого начала она была пронизана ошибками.
Это может быть неизбежно, в определенной степени – в конце концов, мы говорим о программном обеспечении.
Несмотря на то, что вы не можете ничего сделать с ошибками, которые еще предстоит идентифицировать, вы можете по крайней мере защитить свои системы от тех ошибок, которые уже исправлены и задокументированы.
Жаль, что официальный сайт OpenSSL предлагает только исходники для Linux.
Хотя дистрибутивы Linux обычно поставляются с OpenSSL, это не никак относится к Windows … или, скажем, «дистрибутивам Windows».
Если вы хотите запустить его, вам нужен бинарник под Windows, и если вы не хотите его собирать самостоятельно, вы должны найти другой вариант.
В этой статье я покажу,как можно настроить OpenSSL в Windows, не имея дело при этом дела со сборкой из исходников.
Содержание
- Шаг 1. Скачать бинарник
- Шаг 2. Запустите установщик
- Шаг 3. Запустите бинарный файл OpenSSL
Шаг 1. Скачать бинарник
Поиск бинарных файлов OpenSSL для Windows – непростая задача, но не отчаивайтесь.
Они существуют.
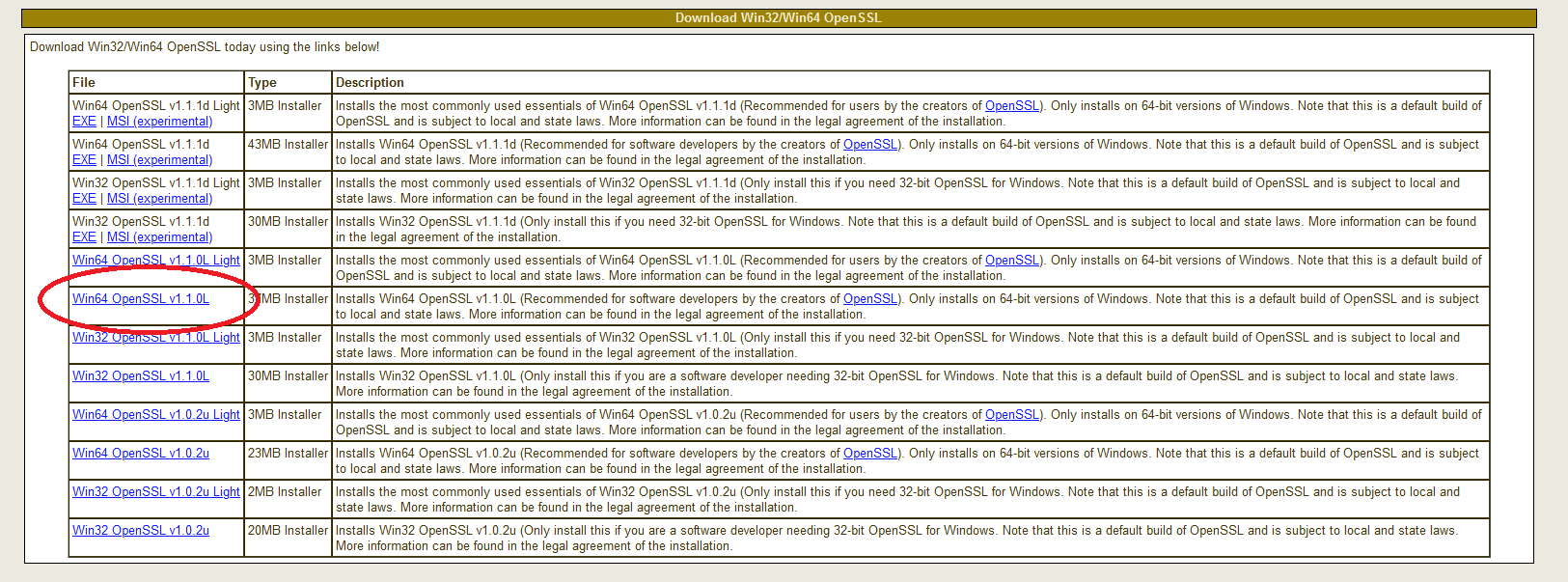
Чтобы загрузить нужный, перейдите по ссылке:
https://slproweb.com/products/Win32OpenSSL.html
Не дайте себя одурачить ни строкой Win32 в URL-адресе, ни навигацией, указывающей на казалось бы древнюю страницу загрузки еще с 2004 года.
Прокрутите страницу вниз до раздела «Download Win32 OpenSSL».
Теперь вам нужно выбрать правильный файл из этого списка.
Для каждой версии есть два основных типа: light и full.
Загрузите файл под названием «Win64 OpenSSL v1.1.0f» (или версию с более новой версией, как только она станет доступна), чтобы скачать фулл установщик.
Текущая версия на момент написания этой статьи (OpenSSL 1.1.0h) сильно отличается от предыдущих версий.
Это совсем не одно и то же, поэтому обратите внимание на номера релизов!
Худшее, что вы можете сделать, – это использовать старую версию, в которой есть задокументированные ошибки.
Шаг 2. Запустите установщик
Мы рекомендуем установить OpenSSL вне вашей системной директории Windows.
Следуйте инструкциям по установке через GUI.
Шаг 3. Запустите бинарный файл OpenSSL
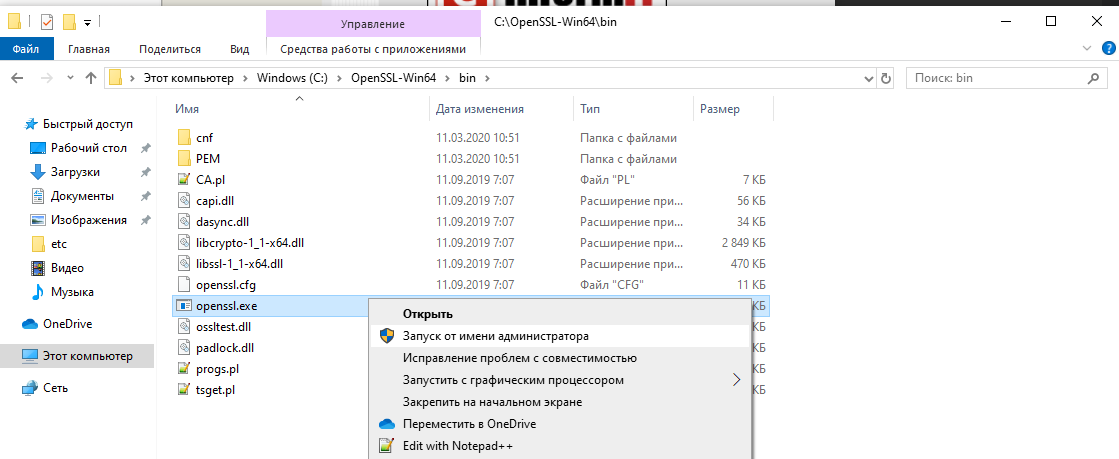
Чтобы начать работу с OpenSSL, вы можете просто щелкнуть по нему правой кнопкой мыши в проводнике Windows в месте его установки, например в моем случае:
C:\OpenSSL-Win64\bin\
затем выберите «Запуск от имени администратора».
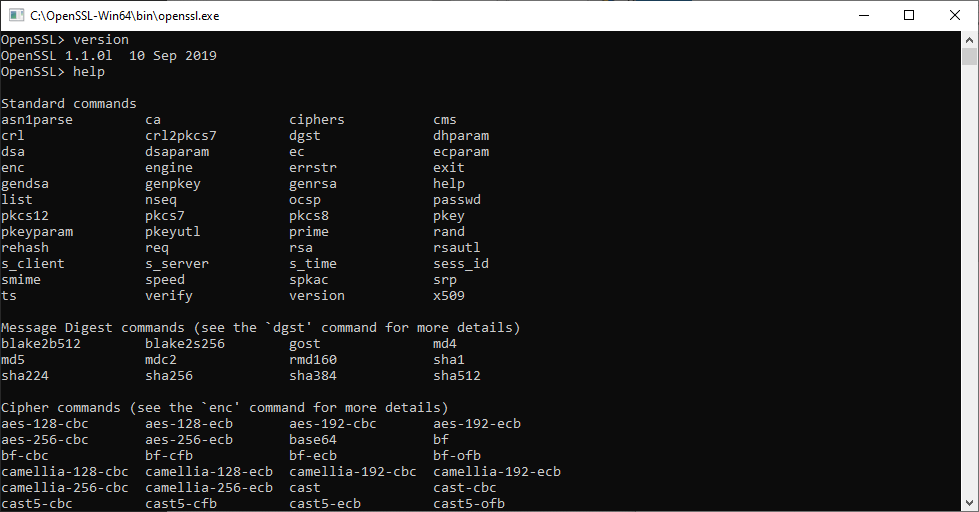
Откроется окно cmd с командной строкой OpenSSL:
Теперь вы можете начать создавать ключи OpenSSL. (Кстати, пользователи утилиты удаленного доступа PuTTY могут экспортировать ключ OpenSSH из PuTTYgen.)
При использовании OpenSSL в Windows таким способом вы просто пропускаете команду openssl, которую видите в приглашении.
Например, чтобы создать пару ключей с помощью OpenSSL в Windows, вы можете ввести:
openssl req -newkey rsa:2048 -nodes -keyout key.pem -x509 -days 365 -out certificate.pem
и следуйте инструкциям на экране, как обычно.
Чтобы просмотреть сертификат:
openssl x509 -text -noout -in certificate.pem