From Wikipedia, the free encyclopedia
Not to be confused with OpenSSL.

«Keeping your communiqués secret» |
|
| Developer(s) | The OpenBSD Project |
|---|---|
| Initial release | 1 December 1999; 23 years ago |
| Stable release |
9.5[1] |
| Repository | github |
| Written in | C |
| Operating system | Cross-platform[2] |
| Standard(s) | RFC 4250, RFC 4251, RFC 4252, RFC 4253, RFC 4254, RFC 4255, RFC 4256, RFC 4335, RFC 4344, RFC 4345, RFC 4419, RFC 4462, RFC 5656, RFC 6594, RFC 6668, RFC 7479[3] |
| Type | Remote access |
| License | BSD, ISC, public domain |
| Website | openssh.com |
OpenSSH (also known as OpenBSD Secure Shell[a]) is a suite of secure networking utilities based on the Secure Shell (SSH) protocol, which provides a secure channel over an unsecured network in a client–server architecture.[4][5]
OpenSSH started as a fork of the free SSH program developed by Tatu Ylönen; later versions of Ylönen’s SSH were proprietary software offered by SSH Communications Security.[6] OpenSSH was first released in 1999 and is currently developed as part of the OpenBSD operating system.
OpenSSH is not a single computer program, but rather a suite of programs that serve as alternatives to unencrypted protocols like Telnet and FTP. OpenSSH is integrated into several operating systems, namely Microsoft Windows, macOS and most Linux operating systems,[7][8] while the portable version is available as a package in other systems.[9][10][11]
History[edit]
OpenBSD Secure Shell was created by OpenBSD developers as an alternative to the original SSH software by Tatu Ylönen, which is now proprietary software.[12] Although source code is available for the original SSH, various restrictions are imposed on its use and distribution. OpenSSH was created as a fork of Björn Grönvall’s OSSH that itself was a fork of Tatu Ylönen’s original free SSH 1.2.12 release,[13] which was the last one having a license suitable for forking.[14][15] The OpenSSH developers claim that their application is more secure than the original, due to their policy of producing clean and audited code and because it is released under the BSD license, the open-source license to which the word open in the name refers.
OpenSSH first appeared in OpenBSD 2.6. The first portable release was made in October 1999.[16] Developments since then have included the addition of ciphers (e.g., ChaCha20-Poly1305 in 6.5 of January 2014[17]), cutting the dependency on OpenSSL (6.7, October 2014[18]) and an extension to facilitate public-key discovery and rotation for trusted hosts (for transition from DSA to Ed25519 public host keys, version 6.8 of March 2015[19]).
On 19 October 2015, Microsoft announced that OpenSSH will be natively supported on Microsoft Windows and accessible through PowerShell, releasing an early implementation and making the code publicly available.[20] OpenSSH-based client and server programs have been included in Windows 10 since version 1803. The SSH client and key agent are enabled and available by default, and the SSH server is an optional Feature-on-Demand.[21]
In October 2019 protection for private keys at rest in RAM against speculation and memory side-channel attacks were added in OpenSSH 8.1.[22]
Development[edit]
OpenSSH is developed as part of the OpenBSD operating system. Rather than including changes for other operating systems directly into OpenSSH, a separate portability infrastructure is maintained by the OpenSSH Portability Team, and «portable releases» are made periodically. This infrastructure is substantial, partly because OpenSSH is required to perform authentication, a capability that has many varying implementations. This model is also used for other OpenBSD projects such as OpenNTPD.
The OpenSSH suite includes the following command-line utilities and daemons:
- scp, a replacement for rcp.
- sftp, a replacement for ftp to copy files between computers.
- ssh, a replacement for rlogin, rsh and telnet to allow shell access to a remote machine.
- ssh-add and ssh-agent, utilities to ease authentication by holding keys ready and avoid the need to enter passphrases every time they are used.
- ssh-keygen, a tool to inspect and generate the RSA, DSA and elliptic-curve keys that are used for user and host authentication.
- ssh-keyscan, which scans a list of hosts and collects their public keys.
- sshd, the SSH server daemon.
The OpenSSH server can authenticate users using the standard methods supported by the SSH protocol: with a password; public-key authentication, using per-user keys; host-based authentication, which is a secure version of rlogin‘s host trust relationships using public keys; keyboard-interactive, a generic challenge–response mechanism, which is often used for simple password authentication, but which can also make use of stronger authenticators such as tokens; and Kerberos/GSSAPI. The server makes use of authentication methods native to the host operating system; this can include using the BSD Authentication system or pluggable authentication modules (PAM) to enable additional authentication through methods such as one-time passwords. However, this occasionally has side effects: when using PAM with OpenSSH, it must be run as root, as root privileges are typically required to operate PAM. OpenSSH versions after 3.7 (16 September 2003) allow PAM to be disabled at run-time, so regular users can run sshd instances.
On OpenBSD, OpenSSH uses a dedicated sshd user by default to drop privileges and perform privilege separation in accordance with the principle of least privilege, applied throughout the operating system including the Xenocara X server.
Features[edit]
OpenSSH includes the ability to set up a secured channel through which data sent to local, client-side Unix domain sockets or local, client-side TCP ports may be «forwarded» (sent across the secured channel) for routing on the server side; when this forwarding is set up, the server is instructed to send that forwarded data to some socket or TCP host/port (the host could be the server itself, «localhost»; or, the host may be some other computer, so that it appears to the other computer that the server is the originator of the data). The forwarding of data is bidirectional, meaning that any return communication is itself forwarded back to the client-side in the same manner; this is known as an «SSH tunnel»,[23] and it can be used to multiplex additional TCP connections over a single SSH connection since 2004,[24] to conceal connections, to encrypt protocols that are otherwise unsecured, and to circumvent firewalls by sending/receiving all manner of data through one port that is allowed by the firewall. For example, an X Window System tunnel may be created automatically when using OpenSSH to connect to a remote host, and other protocols, such as HTTP and VNC, may be forwarded easily.[25]
Tunneling a TCP-encapsulating payload (such as PPP) over a TCP-based connection (such as SSH’s port forwarding) is known as «TCP-over-TCP», and doing so can induce a dramatic loss in transmission performance (a problem known as «TCP meltdown»),[26][27] which is why virtual private network software may instead use for the tunnel connection a protocol simpler than TCP. However, this is often not a problem when using OpenSSH’s port forwarding, because many use cases do not entail TCP-over-TCP tunneling; the meltdown is avoided because the OpenSSH client processes the local, client-side TCP connection in order to get to the actual payload that is being sent, and then sends that payload directly through the tunnel’s own TCP connection to the server side, where the OpenSSH server similarly «unwraps» the payload in order to «wrap» it up again for routing to its final destination.[28]
In addition, some third-party software includes support for tunnelling over SSH. These include DistCC, CVS, rsync, and Fetchmail. On some operating systems, remote file systems can be mounted over SSH using tools such as sshfs (using FUSE).
An ad hoc SOCKS proxy server may be created using OpenSSH. This allows more flexible proxying than is possible with ordinary port forwarding.
Beginning with version 4.3, OpenSSH implements an OSI layer 2/3 tun-based VPN. This is the most flexible of OpenSSH’s tunnelling capabilities, allowing applications to transparently access remote network resources without modifications to make use of SOCKS.[29]
Supported public key types[edit]
OpenSSH supports the following public key types:[30][31]
- ssh-dss (disabled at run-time since OpenSSH 7.0 released in 2015)[32]
- ssh-rsa (disabled at run-time since OpenSSH 8.8 released in 2021)[33]
- ecdsa-sha2-nistp256 (since OpenSSH 5.7 released in 2011)[34]
- ecdsa-sha2-nistp384 (since OpenSSH 5.7)
- ecdsa-sha2-nistp521 (since OpenSSH 5.7)
- ssh-ed25519 (since OpenSSH 6.5 released in 2014)[35]
- rsa-sha2-256 (since OpenSSH 7.2 released in 2016)[36]
- rsa-sha2-512 (since OpenSSH 7.2)
- ecdsa-sk (since OpenSSH 8.2 released in 2020)[37]
- ed25519-sk (since OpenSSH 8.2)
- NTRU Prime-x25519 (since OpenSSH 9.0)[38]
Vulnerabilities[edit]
Before version 5.2 of OpenSSH, it was possible for an attacker to recover up to 14 bits of plaintext with a success probability of 2−14.[39] The vulnerability was related to the CBC encryption mode. The AES CTR mode and arcfour ciphers are not vulnerable to this attack.
A local privilege escalation vulnerability existed in OpenSSH 6.8 to 6.9 (CVE-2015-6565) due to world-writable (622) TTY devices, which was believed to be a denial of service vulnerability.[40] With the use of the TIOCSTI ioctl, it was possible for authenticated users to inject characters into other users terminals and execute arbitrary commands on Linux.[41]
Malicious or compromised OpenSSH servers could read sensitive information on the client such as private login keys for other systems, using a vulnerability that relies on the undocumented connection-resuming feature of the OpenSSH client, which is called roaming, enabled by default on the client, but not supported on the OpenSSH server. This applies to versions 5.4 (released on 8 March 2010[42]) to 7.1 of the OpenSSH client, and was fixed in OpenSSH 7.1p2, released on 14 January 2016. CVE numbers associated to this vulnerability are CVE-2016-0777 (information leak) and CVE-2016-0778 (buffer overflow).[43][44]
Trademark[edit]
In February 2001, Tatu Ylönen, Chairman and CTO of SSH Communications Security informed the OpenSSH development mailing list that the company intended to assert its ownership of the «SSH» and «Secure Shell» trademarks,[45] and sought to change references to the protocol to «SecSH» or «secsh», in order to maintain control of the «SSH» name. He proposed that OpenSSH change its name in order to avoid a lawsuit, a suggestion that developers resisted. OpenSSH developer Damien Miller replied urging Ylönen to reconsider, arguing that «SSH» had long since been a generic trademark.[46]
At the time, «SSH», «Secure Shell» and «ssh» had appeared in documents proposing the protocol as an open standard. Without marking these within the proposal as registered trademarks, Ylönen ran the risk of relinquishing all exclusive rights to the name as a means of describing the protocol. Improper use of a trademark, or allowing others to use a trademark incorrectly, results in the trademark becoming a generic term, like Kleenex or Aspirin, which opens the mark to use by others.[47] After study of the USPTO trademark database, many online pundits opined that the term «ssh» was not trademarked, merely the logo using the lower case letters «ssh». In addition, the six years between the company’s creation and the time when it began to defend its trademark, and that only OpenSSH was receiving threats of legal repercussions, weighed against the trademark’s validity.[48]
Both developers of OpenSSH and Ylönen himself were members of the IETF working group developing the new standard; after several meetings this group denied Ylönen’s request to rename the protocol, citing concerns that it would set a bad precedent for other trademark claims against the IETF. The participants argued that both «Secure Shell» and «SSH» were generic terms and could not be trademarks.[6]
See also[edit]
- Comparison of SSH clients
- Comparison of SSH servers
- SSH File Transfer Protocol (SFTP)
Notes[edit]
- ^ «OpenBSD Secure Shell» name is mainly used in various sshd startup scripts.
References[edit]
- ^ Error: Unable to display the reference properly. See the documentation for details.
- ^ «OpenSSH Portable Release». OpenBSD. Retrieved 15 October 2015.
- ^ «Specifications implemented by OpenSSH». The OpenBSD Project. The OpenBSD Project. Retrieved 14 October 2015.
- ^ Venkatachalam, Girish (April 2007). «The OpenSSH Protocol under the Hood». Linux Journal (156): 74–77Accessed via the Discovery Database at LSU
{{cite journal}}: CS1 maint: postscript (link) - ^
Network Working Group of the IETF,
January 2006,
RFC 4252,
The Secure Shell (SSH) Authentication Protocol. - ^ a b Duffy Marsan, Carolyn (22 March 2001). «Secure Shell inventor denied trademark request». ITworld.com. Retrieved 14 December 2021.
- ^ «dragonfly.git/blob — crypto/openssh/README». gitweb.dragonflybsd.org. Retrieved 19 May 2016.
This is the port of OpenBSD’s excellent OpenSSH to Linux and other Unices.
- ^ «src/crypto/external/bsd/openssh/dist/README — view — 1.4». NetBSD CVS Repositories. Retrieved 19 May 2016.
- ^ «openssh». OpenSUSE. Retrieved 17 May 2016.
- ^ «Debian — Details of package openssh-client in jessie». Debian. Retrieved 17 May 2016.
- ^ «Arch Linux — openssh 7.2p2-1 (x86_64)». Arch Linux. Retrieved 17 May 2016.
- ^ «Project History and Credits». OpenBSD. Retrieved 8 April 2008.
- ^ OSSH sources
- ^ ssh-1.2.13 now available: copying policy changed (permission now required to sell ssh commercially, use is still permitted for any purpose)
- ^ «OpenSSH: Project History and Credits». openssh.com. 22 December 2004. Retrieved 27 February 2014.
- ^ «Portable OpenSSH – Freecode». Freshmeat.net. Retrieved 11 February 2014.
- ^ Murenin, Constantine A. (11 December 2013). Unknown Lamer (ed.). «OpenSSH Has a New Cipher — Chacha20-poly1305 — from D.J. Bernstein». Slashdot. Retrieved 26 December 2014.
- ^ Murenin, Constantine A. (30 April 2014). Soulskill (ed.). «OpenSSH No Longer Has To Depend On OpenSSL». Slashdot. Retrieved 26 December 2014.
- ^ Murenin, Constantine A. (1 February 2015). Soulskill (ed.). «OpenSSH Will Feature Key Discovery and Rotation For Easier Switching To Ed25519». Slashdot. Retrieved 1 February 2015.
- ^ «OpenSSH for Windows Update». 19 October 2015. Retrieved 23 October 2015.
- ^ Durr, Yosef (7 March 2018). «What’s new for the Command Line in Windows 10 version 1803». Windows Command Line Tools For Developers.
- ^ «Protection for private keys at rest in RAM».
- ^ «OpenBSD manual pages: SSH». openbsd.org. 3 July 2014. Retrieved 14 July 2014.
- ^ «OpenSSH Release Notes».
- ^ «Features». OpenSSH. Retrieved 26 June 2016.
- ^ Titz, Olaf (23 April 2001). «Why TCP Over TCP Is A Bad Idea». Retrieved 17 October 2015.
- ^ Honda, Osamu; Ohsaki, Hiroyuki; Imase, Makoto; Ishizuka, Mika; Murayama, Junichi (October 2005). «Understanding TCP over TCP: effects of TCP tunneling on end-to-end throughput and latency». In Atiquzzaman, Mohammed; Balandin, Sergey I (eds.). Performance, Quality of Service, and Control of Next-Generation Communication and Sensor Networks III. Vol. 6011. Bibcode:2005SPIE.6011..138H. CiteSeerX 10.1.1.78.5815. doi:10.1117/12.630496. S2CID 8945952.
- ^ Kaminsky, Dan (13 June 2003). «Re: Extensions for long fat networks?». openssh-unix-dev@mindrot.org (Mailing list).
the TCP forwarding code is pretty speedy as well. Just to pre-answer a question, ssh decapsulates and re-encapsulates TCP, so you don’t have classic TCP-over-TCP issues.
- ^ «OpenSSH 4.3 Release Notes». openssh.com. 1 February 2006. Retrieved 14 July 2014.
- ^ «SSHD(8) — Linux manual page».
- ^ «Sshd_config(5) — OpenBSD manual pages».
- ^ «OpenSSH 7.0 release notes». OpenSSH. 11 August 2015. Retrieved 13 November 2022.
- ^ «OpenSSH 8.8 release notes». OpenSSH. 26 September 2021. Retrieved 13 November 2022.
- ^ «OpenSSH 5.7 release notes». OpenSSH. 24 January 2011. Retrieved 13 November 2022.
- ^ «OpenSSH 6.5 release notes». OpenSSH. 29 January 2014. Retrieved 13 November 2022.
- ^ «OpenSSH 7.2 release notes». OpenSSH. 29 February 2016. Retrieved 13 November 2022.
- ^ «OpenSSH 8.2 release notes». OpenSSH. 14 February 2020. Retrieved 13 November 2022.
- ^ «Changes since OpenSSH 8.9 (OpenSSH 9.0 release notes)». OpenSSH developers. 8 April 2022.
- ^ OpenSSH Security Advisory CBC Attack
- ^ CVE-2015-6565
- ^ OpenSSH PTY vulnerability
- ^ OpenSSH 5.4 released
- ^ Thomson, Iain (14 January 2016). «Evil OpenSSH servers can steal your private login keys to other systems – patch now». The Register.
- ^ OpenSSH 7.1p2 has just been released.
- ^ Ylonen, Tatu (14 February 2001). «SSH trademarks and the OpenSSH product name». openssh-unix-dev (Mailing list). MARC. Retrieved 11 February 2014.
- ^ Miller, Damien (14 February 2001). «Re: SSH trademarks and the OpenSSH product name». openssh-unix-dev (Mailing list). MARC. Retrieved 11 February 2014.
- ^ Lemos, Robert (2 January 2002). «Ssh! Don’t use that trademark». CNET. Retrieved 19 May 2016.
- ^ Ylonen, Tatu (1 March 2002). «Ylönen: We own ssh trademark, but here’s a proposal». NewsForge. Archived from the original on 1 March 2002. Retrieved 20 May 2016.
External links[edit]
Wikibooks has more on the topic of: OpenSSH
Wikimedia Commons has media related to OpenSSH.
- Official website
ssh(1)– OpenBSD General Commands Manualsshd(8)– OpenBSD System Manager’s Manual- OpenSSH at the Super User’s BSD Cross Reference (BXR.SU) OpenGrok
- SSH OpenSSH — Windows CMD — SS64.com
OpenSSH for Windows – это программное обеспечение, которое позволяет пользователям подключаться к удаленному компьютеру или серверу с помощью протокола SSH (Secure Shell) через интернет. OpenSSH является надежным и безопасным средством для передачи данных по сети, так как оно шифрует все передаваемые данные и защищает их от несанкционированного доступа.
Установка и использование OpenSSH на Windows очень просты. Сначала нужно скачать исполняемый файл с официального сайта OpenSSH. Затем следует запустить установочный файл и выполнить несколько простых шагов. После успешной установки пользователь может безопасно подключаться к удаленному серверу или компьютеру с помощью программы командной строки или графического интерфейса SSH-клиента.
Основными функциями OpenSSH для Windows являются возможность удаленного управления и обмена файлами между локальным и удаленным компьютерами, создание и управление SSH-ключами для аутентификации пользователей, а также шифрование и защита передаваемых данных. OpenSSH также предоставляет пользователю удобный интерфейс для работы с удаленными файлами и папками, что делает его незаменимым инструментом для системных администраторов и разработчиков.
Содержание
- Openssh for windows: начало работы, установка, настройка
- Что такое Openssh for windows и как его использовать
- Установка Openssh for windows на компьютер
Openssh for windows: начало работы, установка, настройка
Чтобы начать использовать OpenSSH for Windows, сначала вам нужно установить его на ваш компьютер. Для этого выполните следующие шаги:
- Перейдите на официальный сайт OpenSSH для Windows.
- Загрузите установочный файл для вашей операционной системы.
- Запустите установку и следуйте инструкциям на экране.
После установки вы можете настроить OpenSSH для Windows, чтобы начать использовать его:
- Откройте командную строку или PowerShell.
- Введите
ssh-keygen, чтобы сгенерировать ключи для аутентификации. - Следуйте инструкциям на экране для создания нового ключевого пароля.
- Добавьте свой открытый ключ в файл
~/.ssh/authorized_keysна удаленном компьютере. - Теперь вы можете использовать команду
sshдля присоединения к удаленному компьютеру.
Настройка OpenSSH for Windows может включать такие функции, как настройка соединения через прокси-сервер, использование аутентификации по ключу и установка пароля для доступа к вашей учетной записи. Конкретные детали настройки зависят от ваших потребностей и сетевой среды.
Что такое Openssh for windows и как его использовать
SSH — это протокол сетевой безопасности, который обеспечивает защищенное соединение между клиентом и сервером. Он шифрует данные, передаваемые между ними, и предотвращает их перехват или изменение злоумышленником.
С помощью Openssh for windows вы можете:
- Устанавливать и использовать SSH-сервер на компьютере с Windows
- Подключаться к удаленному компьютеру или серверу через SSH-протокол
- Передавать файлы между компьютером и удаленным сервером
- Выполнять команды и управлять удаленным сервером с помощью командной строки
Для использования Openssh for windows вам необходимо скачать и установить его с официального сайта. После установки вы сможете запускать программы из командной строки или использовать графический интерфейс, если он предоставляется.
Openssh for windows предоставляет надежный и безопасный способ удаленного доступа и управления компьютерами и серверами на операционной системе Windows. Он часто используется администраторами и разработчиками для удаленного управления и обслуживания систем.
Установка Openssh for windows на компьютер
1. Скачайте установочный файл из официального репозитория Openssh for windows. Вы можете найти его на официальном сайте проекта или на странице загрузки ведущих платформ, таких как GitHub или SourceForge.
2. Запустите установочный файл и следуйте инструкциям мастера установки. Вам будет предложено выбрать путь установки, настройки безопасности и другие опции.
3. После завершения установки, проверьте, что сервис OpenSSH установлен и запущен на вашем компьютере. Вы можете найти его в списке служб Windows или в системном лотке.
4. Настройте OpenSSH для использования. Для этого вам понадобится учетная запись администратора. Откройте командную строку от имени администратора и выполните необходимые команды, чтобы включить, настроить и проверить OpenSSH.
5. После настройки, вы можете использовать Openssh for windows для удаленного доступа к вашему компьютеру или управления удаленными компьютерами через командную строку.
Установка Openssh for windows на компьютер позволяет вам использовать мощные сетевые возможности OpenSSH на операционной системе Windows. Она также обеспечивает безопасную передачу данных и удаленное управление, что делает ее удобным инструментом для системных администраторов и разработчиков.
OpenSSH for Windows
About OpenSSH for Windows
OpenSSH is a very popular suite of network utilities based on the SSH protocol (Secure Shell). Finding an installation tool for Windows is not very easy, since almost all Windows versions are portable. Update: Now with OpenSSH v8.6p1 and LibreSSL v3.3.3
An that is what OpenSSH for Windows does: installs a modern version of OpenSSH into your Windows system.
Installation instructions
Simply go to the releases tab and download the binary for your Windows architecture (modern PCs use x64).
Compilation instructions
| GitHub Actions | AppVeyor | Azure Pipelines | Travis CI | Codacy |
|---|---|---|---|---|
| ———- | ———- | ———- | ———- |
Requirements
- Inno Setup 6
- MSVC or MinGW with gcc and g++ support
Compilation steps
-
Download or
git clonethe repository. -
Open Developer Command Prompt (if you use MSVC) or Command Prompt if you use MinGW.
-
Go to the ISCompiler folder at the directory in which you have extracted the files.
-
Now run:
cl ISCompil.cppif you are using MSVC.g++ ISCompil.cpp -o ISCompil.exeif you are using MinGW.
-
After compiling
ISCompil.cpp, runISCompil.exe -
Finally, check
..\{WINDOWS ARCHITECTURE}folder forOpenSSHforWindows-Installer-{WINDOWS ARCHITECTURE}.exe -
Done! Now you can install OpenSSH for Windows correctly.
Uninstallation instructions
You can uninstall OpenSSH for Windows through Programs and Features in Control Panel.
Additional notes
OpenSSH for Windows’ binaries sources are available here.
Contributing to the project
If you want to contribute to the project, please open a Pull Request.
You can contribute with the following things:
- A new portable version of OpenSSH
- Code improvements
Please report bugs through the Issues tab.
Acknowledgements
I would like to thank OpenBSD, OpenSSH, PowerShell and Inno Setup for making this project possible, and you for choosing my software!
Copyrights
© 1996 — 2021, the OpenBSD project
© 1999 — 2021, the OpenSSH project
© 2006 — 2021, PowerShell and Microsoft Corporation
© 1997 — 2021, Jordan Russell’s Software
© 2020 — 2021, Lumito — www.lumito.net
Openssh (Open Secure Shell) — это набор программного обеспечения для безопасной удаленной работы с компьютером через сеть. Изначально разработанный для операционной системы Unix, он также доступен для Windows.
Openssh для Windows предоставляет возможность выполнения различных операций на удаленных серверах с использованием зашифрованных соединений. Благодаря применению криптографических алгоритмов, все данные, передаваемые по сети, защищены от несанкционированного доступа.
Использование Openssh для Windows имеет ряд преимуществ. Во-первых, он обеспечивает безопасную передачу данных между клиентом и сервером, защищая их от перехвата и вмешательства злоумышленников. Во-вторых, Openssh позволяет создавать туннелированные соединения, что особенно полезно при работе с удаленными ресурсами или доступе к локальным сервисам через интернет.
С помощью Openssh можно выполнять различные операции, такие как удаленное управление серверами, передача файлов, создание и монтирование зашифрованных туннелей и многое другое.
Внедрение Openssh в операционную систему Windows происходит путем установки отдельного пакета программ, которые затем можно использовать из командной строки или интерфейса командной оболочки. Openssh для Windows является свободно распространяемым программным обеспечением и находится на стадии активной разработки и поддержки.
Содержание
- Openssh for windows: что это и как установить
- Что такое Openssh for windows
- Преимущества использования Openssh for windows
Openssh for windows: что это и как установить
Для установки OpenSSH for Windows следуйте инструкциям ниже:
- Посетите официальный веб-сайт проекта OpenSSH для Windows.
- Найдите раздел загрузок и выберите последнюю версию OpenSSH для Windows.
- Скачайте установочный файл .exe для вашей версии Windows.
- Запустите установочный файл и следуйте инструкциям мастера установки.
- После установки откройте командную строку или PowerShell и введите команду
ssh, чтобы убедиться, что OpenSSH правильно установлен.
После успешной установки OpenSSH for Windows вы сможете использовать его для безопасного подключения к удаленным компьютерам, передачи файлов и выполнения команд на удаленном компьютере.
Заметьте, что для использования OpenSSH необходимо, чтобы удаленный компьютер также имел установленный и настроенный OpenSSH сервер.
Что такое Openssh for windows
OpenSSH for Windows обеспечивает защищенное соединение с помощью алгоритмов шифрования и аутентификации, таких как RSA, DSA, ECDSA и Ed25519. Это значит, что вы можете безопасно подключаться к удаленным серверам и передавать данные, не опасаясь их перехвата или изменения.
OpenSSH for Windows также предоставляет возможность создания и использования ssh-ключей, которые позволяют вам автоматизировать процесс аутентификации без ввода пароля. Это очень удобно при автоматическом выполнении команд на удаленных серверах или при синхронизации файлов.
Одна из основных функций OpenSSH for Windows – это возможность выполнения команд на удаленных серверах. Вы можете легко управлять удаленными машинами через командную строку, а также выполнять различные задачи, такие как копирование файлов, установка программ и многое другое.
Другая важная функция OpenSSH for Windows – это возможность передачи файлов между локальным и удаленным компьютером. Вы можете копировать файлы и папки, сохраняя при этом их целостность и конфиденциальность.
OpenSSH for Windows является мощным инструментом, который может быть использован как системными администраторами для удаленного управления серверами, так и разработчиками для загрузки и тестирования программ на удаленных машинах.
Преимущества использования Openssh for windows
Ниже перечислены основные преимущества использования Openssh for windows:
1. Безопасность: Openssh for windows обеспечивает высокий уровень безопасности при удаленном управлении компьютерами. Протокол SSH использует криптографические методы для защиты передаваемых данных, что делает невозможным перехват их злоумышленниками. Также Openssh for windows поддерживает различные методы аутентификации, включая публичные и приватные ключи, что позволяет установить двухфакторную аутентификацию.
2. Гибкость: Openssh for windows предоставляет широкие возможности для настройки и кастомизации. Он поддерживает различные алгоритмы шифрования и методы аутентификации, а также предлагает множество дополнительных функций, таких как туннелирование, проброс портов и сжатие данных. Это позволяет адаптировать использование Openssh for windows под различные сценарии и задачи.
3. Удобство использования: Openssh for windows имеет интуитивно понятный интерфейс командной строки, который делает работу с ним удобной и эффективной. Необходимый функционал доступен при помощи простых команд, что упрощает автоматизацию процессов и интеграцию с другими инструментами и программами.
4. Поддержка различных систем: Openssh for windows может работать как на серверах с операционной системой Windows, так и на клиентских компьютерах с другими операционными системами, такими как Linux или macOS. Это делает его универсальным инструментом для управления компьютерами разных типов и архитектур в единой сетевой среде.
5. Бесплатность и открытый исходный код: Openssh for windows распространяется бесплатно и имеет открытый исходный код. Это означает, что его можно свободно скачать, установить и модифицировать для адаптации под свои нужды.
Отмечая все эти преимущества, можно с уверенностью сказать, что использование Openssh for windows является надежным и эффективным решением для удаленного управления компьютерами под управлением Windows.
One of the biggest and most welcome changes to the Windows 10 1809 update and in Windows Server 2019 was the addition of the OpenSSH Client and OpenSSH Server features. It is now incredibly easy to SSH into a Windows Workstation/Server using native tools that are now builtin to the Operating System. In the past this was only possible by using complicated tools and odd workarounds in order to get an SSH-like implementation to work correctly. You can also use the SSH commands right from the Windows command line (CMD, PowerShell), without needing third-party tools or odd commands. This is a very nice change that Microsoft has added, since it is much easier to remotely manage a Windows through the Command Line instead of the GUI, and having the ability to use the same tools on both Windows and Linux is a big advantage.
Note: I have only tested this on Windows 10 Pro for Workstations (Version 1809 Build 17763.253) and on Windows Server 2019 Standard.
Table Of Contents
Installation
Installing the OpenSSH Client and OpenSSH Server options can be done through either the Settings app or through the Command Line.
GUI Installation
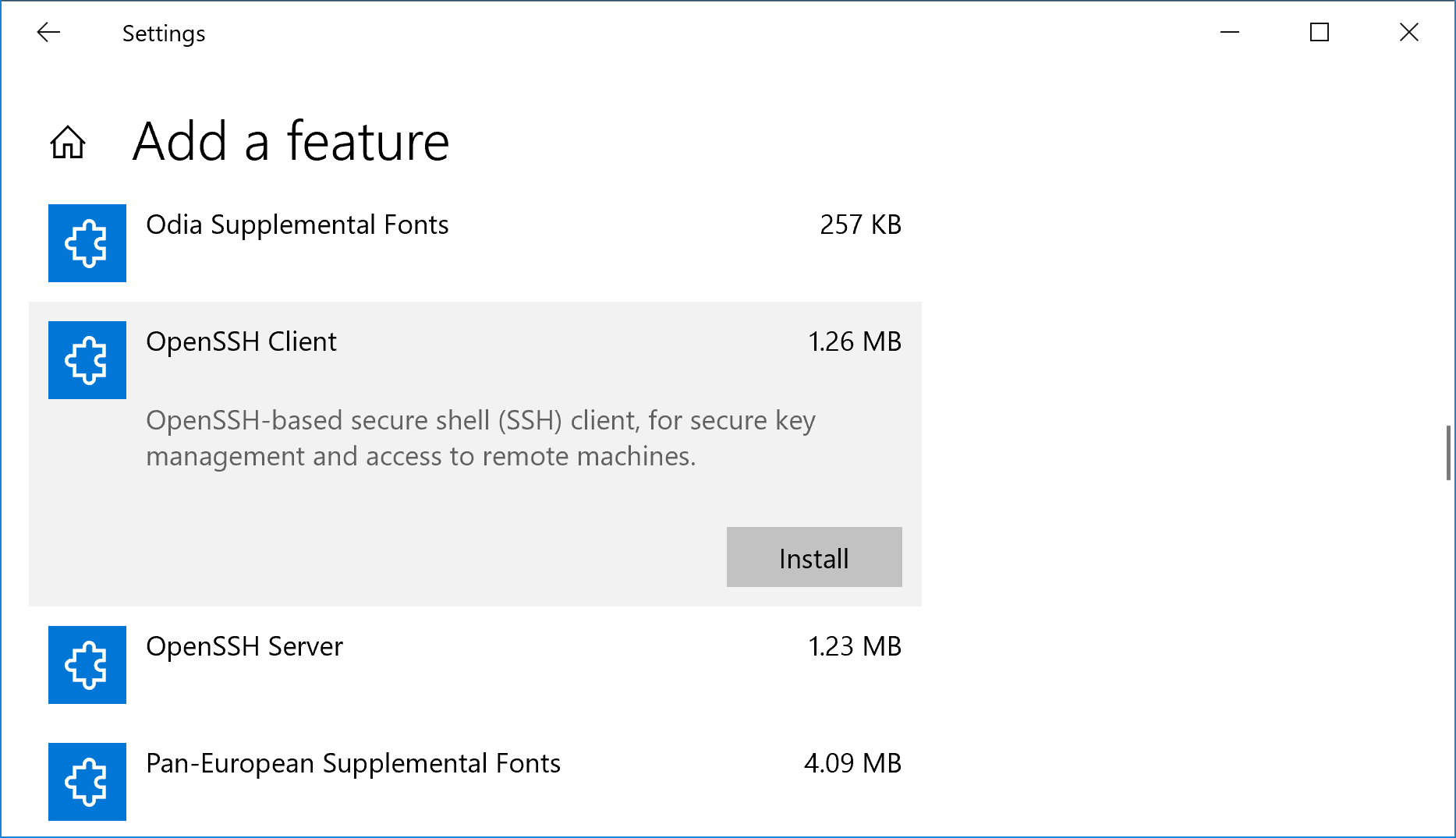
To install through the GUI, go to Settings -> Apps -> Apps & Features -> Manage optional features -> Add a feature. You should see the two options in the list of available features that can be installed:
- OpenSSH Client
- OpenSSH Server
Highlight each option and click the Install button to install the feature. If the options are missing, then you are not on the latest version/patch level of Windows 10 or Windows Server 2019. A restart should not be necessary after adding these features, but the newly installed services will need to be started and configured to automatically start at boot.
Command Line Installation
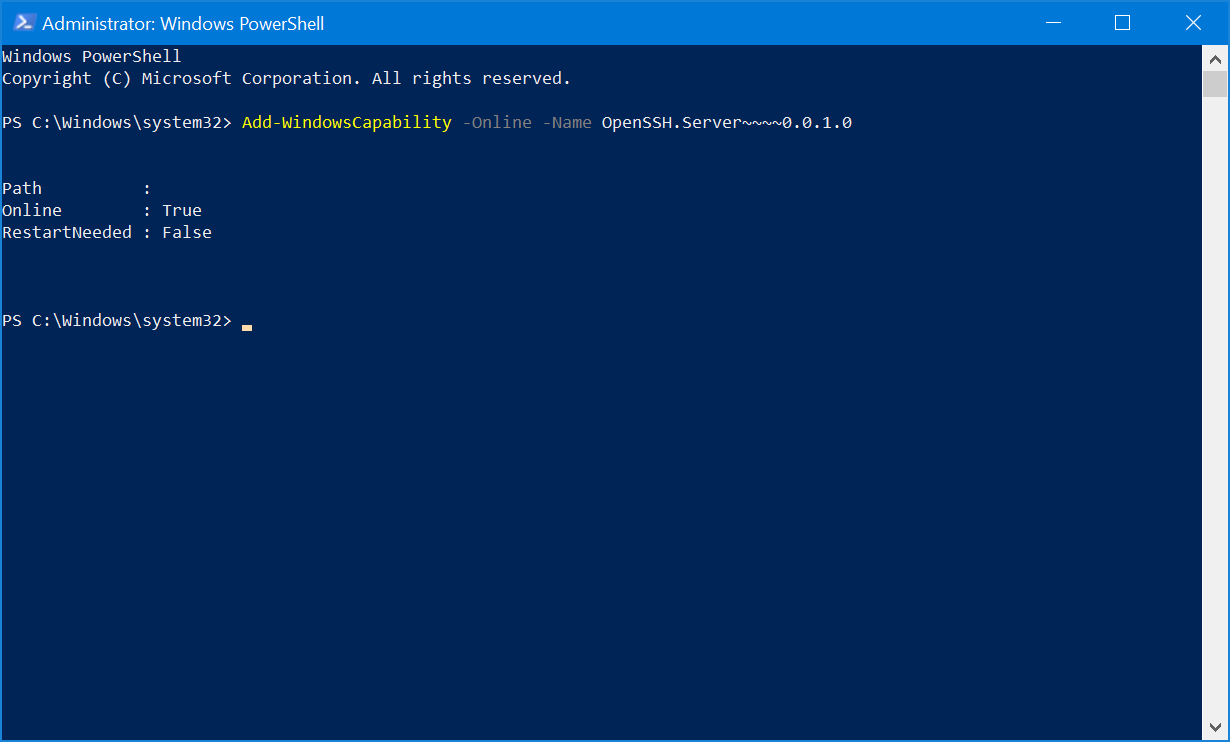
To install through the Command Line, open an elevated PowerShell console in order to proceed. To confirm that you are able to install the OpenSSH Client and OpenSSH Server features, run the following command:
Get-WindowsCapability -Online | findstr OpenSSH
Name : OpenSSH.Client~~0.0.1.0
Name : OpenSSH.Server~~0.0.1.0
If those two options are present, run the following two commands to install the features:
Add-WindowsCapability -Online -Name OpenSSH.Client~~~~0.0.1.0
Add-WindowsCapability -Online -Name OpenSSH.Server~~~~0.0.1.0
Like installing through the Settings app, a restart should not be necessary after adding these features. The newly installed services will need to be started and configured to automatically start at boot.
Services Start
In order to start using OpenSSH Server, the associated services will need to be started first. This can be done through either the Services MMC console or through the Command Line.
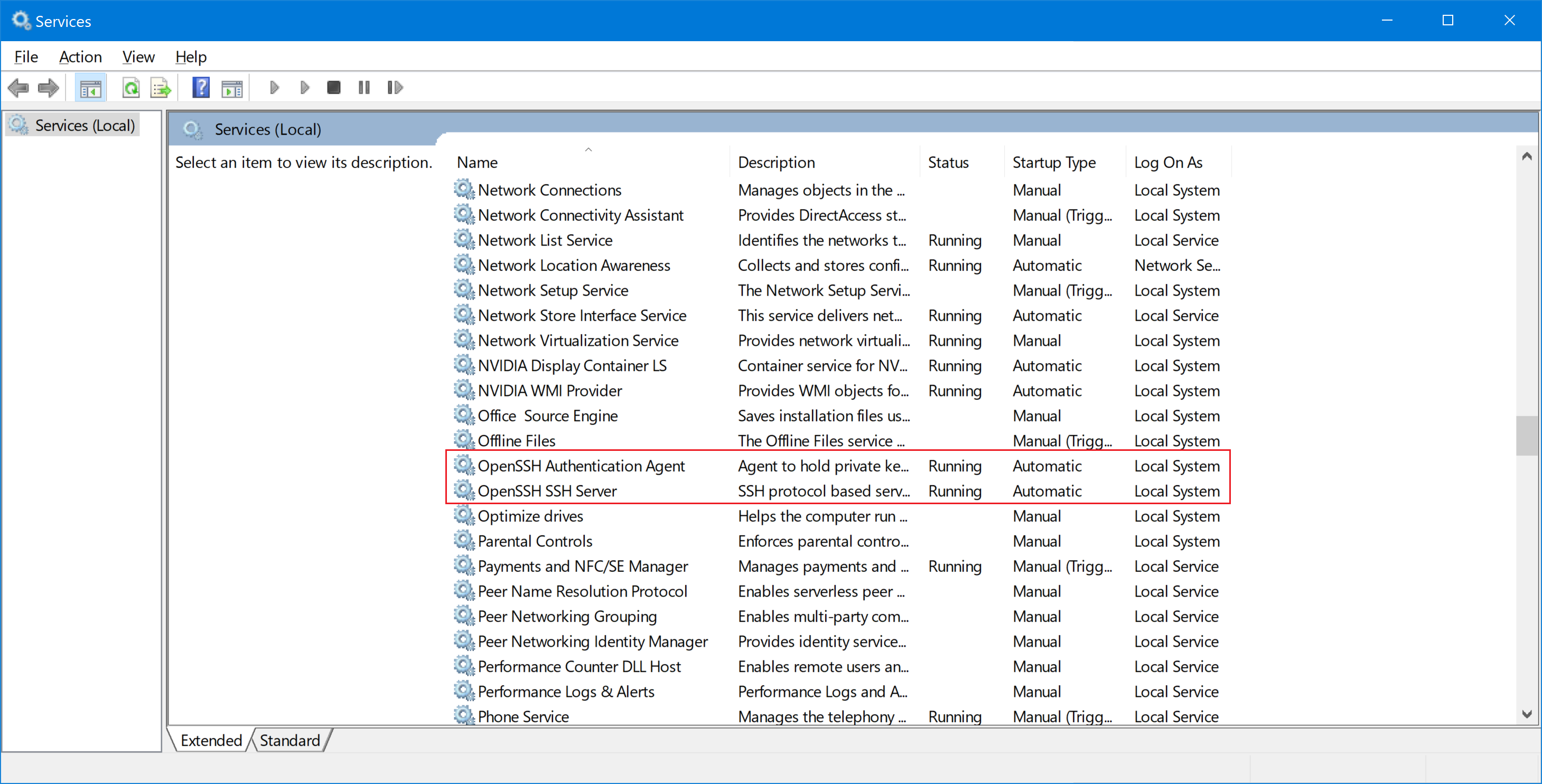
Services MMC Console
Open the Services MMC Console (Win + R, and type in services.mmc) and find the two Services that are related to OpenSSH Server:
- OpenSSH Authentication Agent
- OpenSSH Server
Right-click on each service and select Properties. Under Service Status, click the Start button to start the service. To configure the service to start automatically at boot, change the Startup Type drop-down menu to Automatic and click Apply.
Command Line Services
To start the OpenSSH Server services and enable them to run automatically, there are a few command that you will need to run. To do this, open an elevated PowerShell console and run the following commands to start the OpenSSH Server:
Start-Service sshd
Start-Service ssh-agent
To have these services start automatically at boot, there are two additional commands to run as well:
Set-Service sshd -StartupType Automatic
Set-Service ssh-agent -StartupType Automatic
After this has been completed, you should be able to connect to your Windows installation over SSH.
Using OpenSSH Client
The OpenSSH Client can be used exactly the same way as you would on any Linux/Unix host. It will work through the regular Command Line and in PowerShell:
PS C:\> ssh.exe
usage: ssh [-46AaCfGgKkMNnqsTtVvXxYy] [-B bind_interface]
[-b bind_address] [-c cipher_spec] [-D [bind_address:]port]
[-E log_file] [-e escape_char] [-F configfile] [-I pkcs11]
[-i identity_file] [-J [user@]host[:port]] [-L address]
[-l login_name] [-m mac_spec] [-O ctl_cmd] [-o option] [-p port]
[-Q query_option] [-R address] [-S ctl_path] [-W host:port]
[-w local_tun[:remote_tun]] destination [command]
Here is the same output from a Linux environment:
matthew@thinkpad / $ ssh
usage: ssh [-46AaCfGgKkMNnqsTtVvXxYy] [-b bind_address] [-c cipher_spec]
[-D [bind_address:]port] [-E log_file] [-e escape_char]
[-F configfile] [-I pkcs11] [-i identity_file]
[-J [user@]host[:port]] [-L address] [-l login_name] [-m mac_spec]
[-O ctl_cmd] [-o option] [-p port] [-Q query_option] [-R address]
[-S ctl_path] [-W host:port] [-w local_tun[:remote_tun]]
[user@]hostname [command]
I won’t go into the details on how to use any of these advanced options, there are very good tutorials on how to use the OpenSSH Client on other sites. The behaviour of OpenSSH Client on Windows should be almost exactly the same as on a Linux environment. So far I haven’t run into any issues with connectivity.
Connecting to OpenSSH Server
There is nothing special required to connect to a Windows host, it behaves exactly the same way as any other SSH host. There are a few different username formats that you can use:
user@windows-host (Local User Account)
user@domain.local@windows-host (Domain UPN)
domain\user@windows-host (Netbios)
One of the benefits is the ability to login with a Microsoft account if you are using that as your username. It is a bit unusual to see an e-mail address used this way, but I am glad that Microsoft made sure that this functionality worked correctly:
user@outlook.com@windows-host
There is nothing more to OpenSSH Server, you can manage your Windows host from the command line once you are logged in. If you want to do any further customization or need some basic troubleshooting, there is additional information below.
Change the Default Shell
By default when you login to a Windows installation with SSH, it defaults to the regular Command Prompt (cmd.exe). I prefer PowerShell for everyday usage, and it is easy to switch to PowerShell once you login, but you can change the default shell to save yourself some time if you are going to be using this feature often.
This is done through the Registry Editor, which will run with Administrator privileges. You need to navigate to the following key:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\OpenSSH
Create a new string called DefaultShell and give it the following value:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Restart the OpenSSH Server Service and the next time that you login with SSH, you should automatically go to PowerShell. I have tried making this work with Bash, but it doesn’t seem to be supported yet.
If you do want to use Bash, just type in bash.exe to switch to it.
Additional Settings
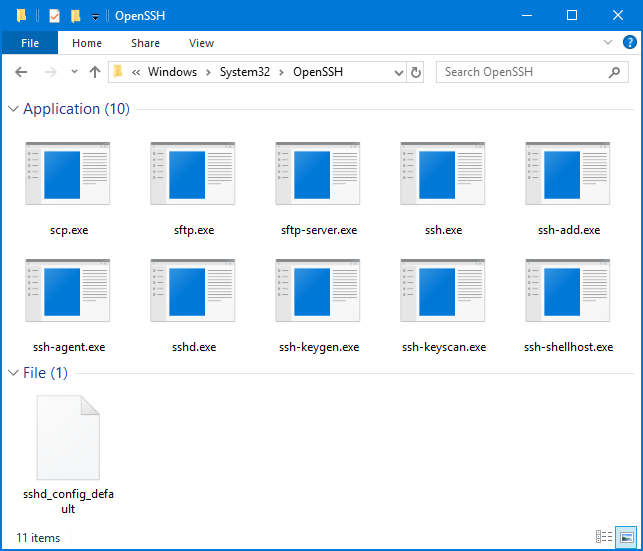
There are a few customizations that you can do to the OpenSSH Server service if needed. Since this is a port of the OpenSSH Server, the customization is done in a very similar way. To begin, the directory where all of the associated executable files are found is in the C:\Windows\System32\OpenSSH directory:
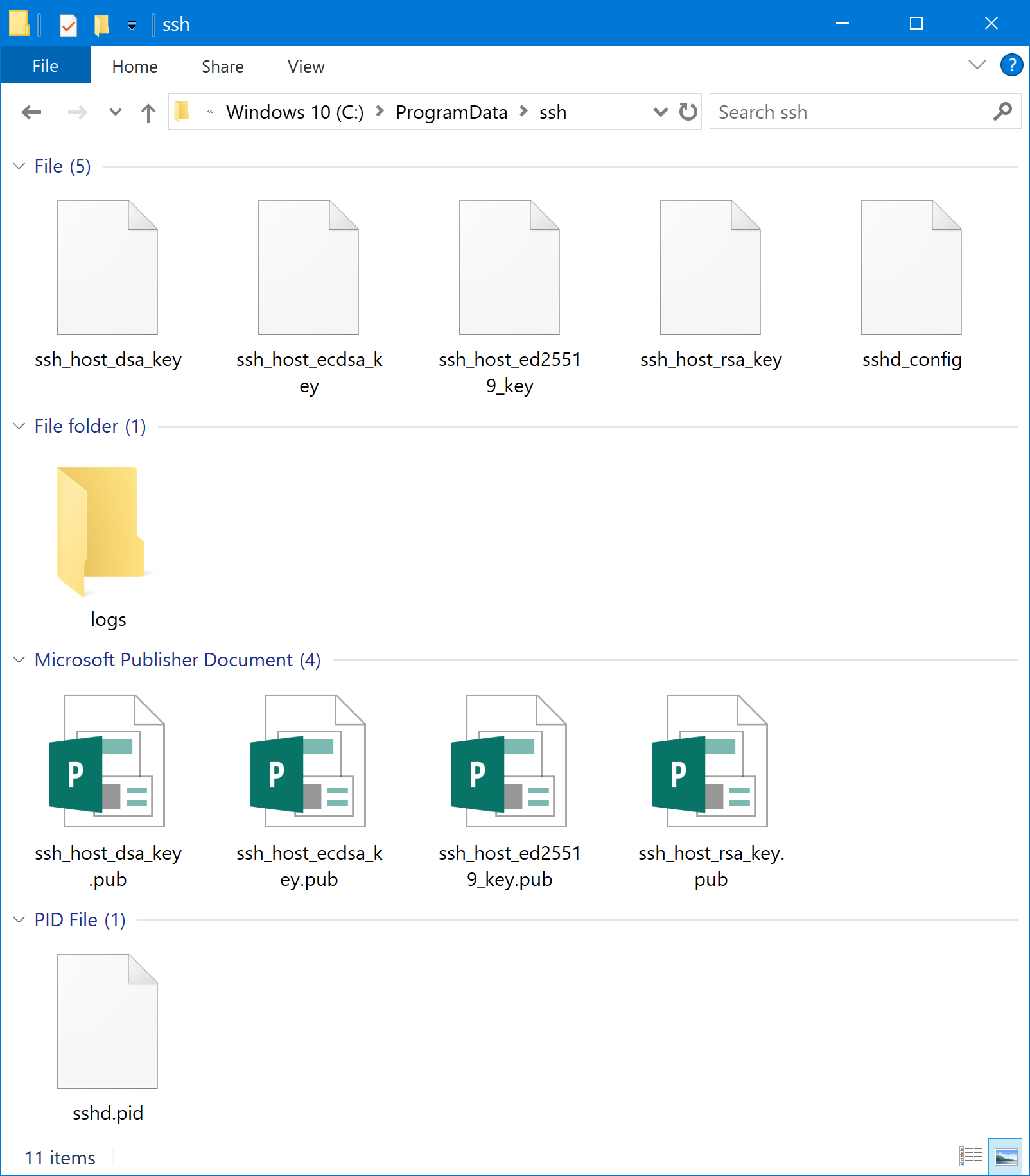
The other important directory for OpenSSH Server is the C:\ProgramData\ssh folder, which contains the configuration files and log files.
OpenSSH Server options, such as changing the login banner and locking down security options are done in the C:\ProgramData\ssh\sshd_config file.
Not all options can be used on a Windows host. For more information, you can refer to the official Wiki article on what options are supported:
https://github.com/PowerShell/Win32-OpenSSH/wiki/sshd_config
Troubleshooting
If you need to view the log file for OpenSSH Server, you need to make a quick change to the configuration file (C:\ProgramData\ssh\sshd_config) to enable logging:
# Logging
#SyslogFacility AUTH
#LogLevel INFO
Make the following change:
# Logging
SyslogFacility LOCAL0
LogLevel INFO
You will need to restart the OpenSSH Server service in order to apply the change. Once the change has been made, the log file (sshd.log) can be found in the C:\ProgramData\ssh\logs directory. When you are finished troubleshooting, you should revert this change to prevent unnecessary logging for the OpenSSH service.
Links
- SSH on Windows Server 2019
- Win32-OpenSSH