I’m trying to install and run the nmap tool to test my server, but it keeps saying
Note: Host seems down. If it is really up, but blocking our ping probes, try -P0
and showing all the server ports are closed. Which is not true — the server is up and has lots of open ports. Any ideas?
UPDATE: Just to clarify — the server can be pinged and port-scanned fine by other programs. It’s juts nmap that does not work. Even «google.com» seems to be down for nmap.
asked Apr 4, 2011 at 17:36
jitbitjitbit
4072 gold badges6 silver badges18 bronze badges
3
If you have two NICs on your computer, nmap sometimes picks up the wrong routing information (for Windows, different from what route PRINT would output, compare with nmap --iflist)
You can see which interface it is picking with the -d option
The solution is to specify the correct interface with the -e option, for instance if nmap is picking eth1 whereas it should have picked eth2 you would write nmap -e eth2 ...
answered Aug 6, 2012 at 8:21
KaanKaan
3581 gold badge3 silver badges10 bronze badges
1
As I have the same problem on my Win 7 64-bit machine and managed to fix it, I thought I should contribute so that it could be searchable for other users.
Step 1:
Do a nmap --iflist which will show you the device IP address (if any) and MAC address
From there, select the interface that you will use e.g.eth2
Step 2:
Then you are ready to run your scan by running:
nmap -v -O -e eth2 somehost.com
growse
8,02013 gold badges74 silver badges115 bronze badges
answered May 20, 2013 at 7:58
Blue TongueBlue Tongue
1072 gold badges3 silver badges8 bronze badges
I have nmap working perfectly on my Windows 7 Professional 64 bit machine, so I do not believe it is the OS that is preventing nmap from properly scanning your server. Either it’s a problem with your system configuration, server configuration, or network configuration.
I would recommend as a first step trying to figure out where the problem lies (workstation, network, or server). Running some form of network sniffer (e.g.: wireshark, tcpdump) on your workstation and server while the nmap scan is running might be a good first step. This will help you determine whether the network traffic from nmap is even leaving the workstation or arriving at the server. Obviously the nmap program thought it executed the scan without error, so it must have received TCP traffic back from somewhere.
Again, this is only a first step to get you going. I don’t know very much about your setup to be able to make further recommendations. Good luck.
answered Apr 4, 2011 at 19:47
Some random thoughts:
I always forget that my local firewall can block outbound traffic. I think I hit this same issue with nmap. Try disabling your local firewall or creating a policy that allows all traffic out which originates from localhost.
If that isn’t it then forget nmap and focus solely on getting ping to work. If ping currently doesn’t work then this will help you find the point of failure.
The ports on the server might be open, but are they exposed to your source IP or network segment? They might be open only for localhost. Disable the firewall on the server for a minute to see if that helps you find where the blocking is occurring.
You said the ports on the server were open. I’m assuming you have tested this. Try a netstat -an on the server just to be certain that it’s actually listening on those ports.
Is there any potential for blocking inbetween the devices? Does your traffic traverse a router, other firewall, etc?
One other random potential issue: Sometimes my apps just don’t work on Win7x64 unless they’re running as Admin. Even if I launch them under an account that has admin privs, I still occasionally have to right click on them and run them as administrator. Perhaps…
As @Ryan said; map out the potential choke points for your traffic and starting testing each one.
answered Apr 5, 2011 at 18:24
For anyone who’s still stumbled upon this problem:
The above answer(Kaan’s) works, but only in some case. There are cases I met where the default route is binded to the wrong interface, hence some will see a «cannot route» message.
Just for anyone that’s getting this problem, the best course is to get the newest version (At the time of this post it is 6.25 (link), which seemed to have fixed the problem).
answered Dec 8, 2012 at 9:13
You must log in to answer this question.
Not the answer you’re looking for? Browse other questions tagged
.
Not the answer you’re looking for? Browse other questions tagged
.
@therealkenc ty for the interesting remark: «WSL’s focus is on development related scenarios, not enterprise scenarios (for some definition of either category).»
TL;DR: Is there a blog post that describes this distinction in more detail, perhaps with more compelling use cases than https://msdn.microsoft.com/en-us/commandline/wsl/faq ?
Detailed comments, questions;
I’ve been really excited by WSL and am trying to figure out for myself how /when I can use it. (I have a windows machine I love, but my current shop is mac based. ) I already think Powershell’s Bash sugar support is terrific.
Perhaps this is really a marketing / product placement question that apparently many of us share. If so , maybe you all can clarify and show us the win(s).
The idea of WSL focusing on dev not enterprise scenarios confuses me.
- For pure ‘development,’ ie writing code, I can do that almost anywhere with a text editor nowadays.
- For certain coding, like simple bash scripts, windows powershell already provides some interop with linux — no WSL required, right? (or maybe it is/was?)
- The FAQ for WSL, above, references MS’s desire to support dev on ruby stacks that use long filepaths and such. Are those scenarios satisfactorily solved without networking, ie this ticket nmap not working #1349 , fully supported? [1]
- The WSL FAQ states an intent not to support server tasks and references other tools like Docker, but aren’t alot of the complex ruby programs related to server usage? In fact, isn’t it exactly Linux’s ‘free enterprise services’ such as nmap, tcpdump, etc that got it into the market(s) (of RubyRails hosting for ex.)? As one anonymous poster wrote on the UserVoice, above, November 24, 2017 17:43 «we use linux because we are nerds; dev nerds, infra nerds, network nerds, or all of the above. » That rings true to me, and I’m wondering what dev projects I should/not think of with WSL.
Your complaint is well taken that Uservoice is lacking and ‘ absent a single: «In my development workflow I do , but I am unable to to because there is no AF_PACKET support in WSL». In this context is a development goal you are trying to achieve, not «run native Linux wireshark» (which is a means not a goal). ‘
I checked and found the most substantial comments were:
- James commented July 30, 2017 22:54 Pls support, don’t want to have to run a VM to get these tools to work, kinda meant to be able to replace the need to have a VM to get a real Linux CLI… => this is the same concern as on this issue ticket, ie we thought WSL would replace needing also to have a VM. But here James doesn’t say why he wants to use it.
- Anonymous March 19, 2017 12:12 Yes, +1. Every few months I try out the latest Linux subsystem on my wifes laptop to see if it can replace my MacBook for mobile development. As of now, it can’t. I develop apps that use libpcap and/or netmap on Linux. The great thing is, they compile and I can read from pcap files files. Its just when I want to do a «live » test it fails.
Some thoughts as an observer about the use case are above, but also once there are daemons [2], how about this scenario;
- I start my dev ruby rails server on my linux box, it runs in background after I hide wsl
- now periodically I want to check its network performance.
- would I not need nmap etc on WSL to do so?
- Similarly, or for the same scenario, if the website/process is a dockerized container , wouldn’t I need these tools?
Since the FAQ seems to say I should never do this, I want the FAQ to specify more of the advantages of MS’s proposed division of labor.
thank you for the project! I am definitely speaking as an amateur / explorer here so all/any resources appreciated.
Anne
Notes
[1] NB: Right now 2017-12-06 those scenarios might have some trouble as well , iff the files-intermittently-missing is not fixed completely by the latest update. I am not sure if it is — maybe no per #2712 but maybe yes per #2448 .
[2] Server work likely wouldn’t make sense before getting background processes going, https://wpdev.uservoice.com/forums/266908-command-prompt-console-bash-on-ubuntu-on-windo/suggestions/13653522-consider-enabling-cron-jobs-daemons-and-backgroun
//edit; add TLDR , reorg
I’m trying to install and run the nmap tool to test my server, but it keeps saying
Note: Host seems down. If it is really up, but blocking our ping probes, try -P0
and showing all the server ports are closed. Which is not true — the server is up and has lots of open ports. Any ideas?
UPDATE: Just to clarify — the server can be pinged and port-scanned fine by other programs. It’s juts nmap that does not work. Even «google.com» seems to be down for nmap.
asked Apr 4, 2011 at 17:36
jitbitjitbit
4072 gold badges6 silver badges18 bronze badges
3
If you have two NICs on your computer, nmap sometimes picks up the wrong routing information (for Windows, different from what route PRINT would output, compare with nmap --iflist)
You can see which interface it is picking with the -d option
The solution is to specify the correct interface with the -e option, for instance if nmap is picking eth1 whereas it should have picked eth2 you would write nmap -e eth2 ...
answered Aug 6, 2012 at 8:21
KaanKaan
3581 gold badge3 silver badges10 bronze badges
1
As I have the same problem on my Win 7 64-bit machine and managed to fix it, I thought I should contribute so that it could be searchable for other users.
Step 1:
Do a nmap --iflist which will show you the device IP address (if any) and MAC address
From there, select the interface that you will use e.g.eth2
Step 2:
Then you are ready to run your scan by running:
nmap -v -O -e eth2 somehost.com
growse
8,02013 gold badges74 silver badges115 bronze badges
answered May 20, 2013 at 7:58
Blue TongueBlue Tongue
1072 gold badges3 silver badges8 bronze badges
I have nmap working perfectly on my Windows 7 Professional 64 bit machine, so I do not believe it is the OS that is preventing nmap from properly scanning your server. Either it’s a problem with your system configuration, server configuration, or network configuration.
I would recommend as a first step trying to figure out where the problem lies (workstation, network, or server). Running some form of network sniffer (e.g.: wireshark, tcpdump) on your workstation and server while the nmap scan is running might be a good first step. This will help you determine whether the network traffic from nmap is even leaving the workstation or arriving at the server. Obviously the nmap program thought it executed the scan without error, so it must have received TCP traffic back from somewhere.
Again, this is only a first step to get you going. I don’t know very much about your setup to be able to make further recommendations. Good luck.
answered Apr 4, 2011 at 19:47
Some random thoughts:
I always forget that my local firewall can block outbound traffic. I think I hit this same issue with nmap. Try disabling your local firewall or creating a policy that allows all traffic out which originates from localhost.
If that isn’t it then forget nmap and focus solely on getting ping to work. If ping currently doesn’t work then this will help you find the point of failure.
The ports on the server might be open, but are they exposed to your source IP or network segment? They might be open only for localhost. Disable the firewall on the server for a minute to see if that helps you find where the blocking is occurring.
You said the ports on the server were open. I’m assuming you have tested this. Try a netstat -an on the server just to be certain that it’s actually listening on those ports.
Is there any potential for blocking inbetween the devices? Does your traffic traverse a router, other firewall, etc?
One other random potential issue: Sometimes my apps just don’t work on Win7x64 unless they’re running as Admin. Even if I launch them under an account that has admin privs, I still occasionally have to right click on them and run them as administrator. Perhaps…
As @Ryan said; map out the potential choke points for your traffic and starting testing each one.
answered Apr 5, 2011 at 18:24
For anyone who’s still stumbled upon this problem:
The above answer(Kaan’s) works, but only in some case. There are cases I met where the default route is binded to the wrong interface, hence some will see a «cannot route» message.
Just for anyone that’s getting this problem, the best course is to get the newest version (At the time of this post it is 6.25 (link), which seemed to have fixed the problem).
answered Dec 8, 2012 at 9:13
You must log in to answer this question.
Not the answer you’re looking for? Browse other questions tagged
.
Not the answer you’re looking for? Browse other questions tagged
.
-
B правой части каждого сообщения есть стрелки ⇧ и ⇩. Не стесняйтесь оценивать ответы. Чтобы автору вопроса закрыть свой тикет, надо выбрать лучший ответ. Просто нажмите значок ✔ в правой части сообщения.
-
#1
Всем привет, у меня перестал работать Nmap, он не сканирует
Вот к примеру я попытался просканировать vk.com(так со всеми хостами):
Код:
Starting Nmap 7.80 ( Nmap: the Network Mapper - Free Security Scanner ) at 2020-07-05 15:01 +06
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 3.12 seconds
вот еще вывод команды nmap --script-updatedb:
Starting Nmap 7.80 ( Nmap: the Network Mapper - Free Security Scanner ) at 2020-07-05 14:52 +06
NSE: Updating rule database.
NSE: Failed to load /usr/local/bin/../share/nmap/scripts//http-vuln-cve2014-3704.nse:
...al/bin/../share/nmap/scripts//http-vuln-cve2014-3704.nse:8: module 'openssl' not found:
NSE failed to find nselib/openssl.lua in search paths.
no field package.preload['openssl']
no file '/usr/local/share/lua/5.3/openssl.lua'
no file '/usr/local/share/lua/5.3/openssl/init.lua'
no file '/usr/local/lib/lua/5.3/openssl.lua'
no file '/usr/local/lib/lua/5.3/openssl/init.lua'
no file './openssl.lua'
no file './openssl/init.lua'
no file '/usr/local/lib/lua/5.3/openssl.so'
no file '/usr/local/lib/lua/5.3/loadall.so'
no file './openssl.so'
stack traceback:
[C]: in function 'require'
...al/bin/../share/nmap/scripts//http-vuln-cve2014-3704.nse:8: in function <...al/bin/../share/nmap/scripts//http-vuln-cve2014-3704.nse:1>
NSE: failed to initialize the script engine:
/usr/local/bin/../share/nmap/nse_main.lua:614: could not load script
stack traceback:
[C]: in function 'error'
/usr/local/bin/../share/nmap/nse_main.lua:614: in field 'new'
/usr/local/bin/../share/nmap/nse_main.lua:1294: in main chunk
[C]: in ?
QUITTING!ранее прописывал apt autoremove
Последнее редактирование модератором:
-
#2
Всем привет, у меня перестал работать Nmap, он не сканирует
Вот к примеру я попытался просканировать vk.com(так со всеми хостами):Starting Nmap 7.80 (
Ссылка скрыта от гостей
) at 2020-07-05 15:01 +06
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 3.12 secondsвот еще вывод команды nmap —script-updatedb:
Starting Nmap 7.80 (
Ссылка скрыта от гостей
) at 2020-07-05 14:52 +06
NSE: Updating rule database.
NSE: Failed to load /usr/local/bin/../share/nmap/scripts//http-vuln-cve2014-3704.nse:
…al/bin/../share/nmap/scripts//http-vuln-cve2014-3704.nse:8: module ‘openssl’ not found:
NSE failed to find nselib/openssl.lua in search paths.
no field package.preload[‘openssl’]
no file ‘/usr/local/share/lua/5.3/openssl.lua’
no file ‘/usr/local/share/lua/5.3/openssl/init.lua’
no file ‘/usr/local/lib/lua/5.3/openssl.lua’
no file ‘/usr/local/lib/lua/5.3/openssl/init.lua’
no file ‘./openssl.lua’
no file ‘./openssl/init.lua’
no file ‘/usr/local/lib/lua/5.3/openssl.so’
no file ‘/usr/local/lib/lua/5.3/loadall.so’
no file ‘./openssl.so’
stack traceback:
[C]: in function ‘require’
…al/bin/../share/nmap/scripts//http-vuln-cve2014-3704.nse:8: in function <…al/bin/../share/nmap/scripts//http-vuln-cve2014-3704.nse:1>
NSE: failed to initialize the script engine:
/usr/local/bin/../share/nmap/nse_main.lua:614: could not load script
stack traceback:
[C]: in function ‘error’
/usr/local/bin/../share/nmap/nse_main.lua:614: in field ‘new’
/usr/local/bin/../share/nmap/nse_main.lua:1294: in main chunk
[C]: in ?QUITTING!
ранее прописывал apt autoremove
Опцию -Pn пробовали добавлять?
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
-
#3
Опцию -Pn пробовали добавлять?
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
пробовал, ничего не выводит
-
#4
Покажи полную команду которую пытаешься запустить.
От рута запускаешь?
-
#5
А ранее nmap работал?
Может nmap-у Firewall мешает?
Как вариант можно запустить ну скажем Wireshark и посмотреть что происходит с пакетами.
autoremove удаляет только не используемые зависимости и не должен был как то повлиять.
-
#6
Проверь, что у тебя есть все необходимые компоненты OpenSSL. В выводе явно указано, что их не хватает для работы скрипта http-vuln-cve2014-3704.nse.
И судя по выводу, так же не хватает вот этих файлов:
no field package.preload[‘openssl’]
no file ‘/usr/local/share/lua/5.3/openssl.lua’
no file ‘/usr/local/share/lua/5.3/openssl/init.lua’
no file ‘/usr/local/lib/lua/5.3/openssl.lua’
no file ‘/usr/local/lib/lua/5.3/openssl/init.lua’
no file ‘./openssl.lua’
no file ‘./openssl/init.lua’
no file ‘/usr/local/lib/lua/5.3/openssl.so’
no file ‘/usr/local/lib/lua/5.3/loadall.so’
no file ‘./openssl.so’
ПРоверь что они есть по указанным путям. Если нет, то загугли как их залить/установить.
-
#7
А ранее nmap работал?
Может nmap-у Firewall мешает?
Как вариант можно запустить ну скажем Wireshark и посмотреть что происходит с пакетами.
autoremove удаляет только не используемые зависимости и не должен был как то повлиять.
Ранее работал, и можете подсказать как файрвол выключить
P.S. Только не пишите пожалуйста что то вроде «УУ даже таких элементарных вещей незнаешь»
А ранее nmap работал?
Может nmap-у Firewall мешает?
Как вариант можно запустить ну скажем Wireshark и посмотреть что происходит с пакетами.
autoremove удаляет только не используемые зависимости и не должен был как то повлиять.
Кстати попробовал на термуксе, тоже не работает
А ранее nmap работал?
Может nmap-у Firewall мешает?
Как вариант можно запустить ну скажем Wireshark и посмотреть что происходит с пакетами.
autoremove удаляет только не используемые зависимости и не должен был как то повлиять.
в wireshark первый(nmap) отправленный пакет(icmp) и последний(nmap), пишет no response found
-
#8
У тебя сломан openssl.
Проверь, установлен-ли он и переставь nmap, возможно он зависимости нормально подтянет.
-
#9
dc
У тебя сломан openssl.
Проверь, установлен-ли он и переставь nmap, возможно он зависимости нормально подтянет.
все равно нет, ксати, я переустановил линукс, и все тоже самое кроме ошибок про openssl
-
#10
все равно нет, ксати, я переустановил линукс, и все тоже самое кроме ошибок про openssl
Покажи полную команду и её вывод.
-
#11
dc
все равно нет, ксати, я переустановил линукс, и все тоже самое кроме ошибок про openssl
А какой именно линукс?
-
#12
А curl-ом пробовал до этих же хостов достучаться? А в браузере пашет (если да, то какой и какая версия)?
Как у тебя устроена сеть (vpn->tor->vpn, vpn->tor, tor->vpn, tor, vpn)?
С термукса и с линукса по одному и тому же каналу выход идёт?
В Wireshark только по одному пакету прошло? Другой трафик в Wireshark-е летает?
Про firewall (если используешь iptables):
список правил
iptables -L
очистить правила
iptables -F
iptables -X
разрешить любой трафик
iptables -P INPUT ACCEPT
iptables -P FORWARD ACCEPT
iptables -P OUTPUT ACCEPT
-
#13
А curl-ом пробовал до этих же хостов достучаться? А в браузере пашет (если да, то какой и какая версия)?
Как у тебя устроена сеть (vpn->tor->vpn, vpn->tor, tor->vpn, tor, vpn)?
С термукса и с линукса по одному и тому же каналу выход идёт?
В Wireshark только по одному пакету прошло? Другой трафик в Wireshark-е летает?Про firewall (если используешь iptables):
список правил
iptables -Lочистить правила
iptables -F
iptables -Xразрешить любой трафик
iptables -P INPUT ACCEPT
iptables -P FORWARD ACCEPT
iptables -P OUTPUT ACCEPT
файрвол настроил и все заработало, спасибо
Обучение наступательной кибербезопасности в игровой форме. Начать игру!
- Nmap Network Scanning
- Chapter 2. Obtaining, Compiling, Installing, and Removing Nmap
- Windows
While Nmap was once a Unix-only tool, a Windows version was
released in 2000 and has since become the second most popular Nmap
platform (behind Linux). Because of this popularity and the fact that
many Windows users do not have a compiler, binary executables are
distributed for each major Nmap release. We support Nmap on Windows 7
and newer, as well as Windows Server 2008 and newer. We also maintain
a guide for users
who must run Nmap on earlier Windows releases. While it has improved dramatically, the Windows port is not
quite as efficient as on Unix. Here are the known limitations:
-
Nmap only supports ethernet interfaces (including most
802.11 wireless cards and many VPN clients) for raw packet scans.
Unless you use the-sT -Pnoptions, RAS connections
(such as PPP dialups) and certain VPN clients are not supported. This
support was dropped when Microsoft removed raw TCP/IP socket support
in Windows XP SP2. Now Nmap must send lower-level ethernet frames
instead. -
When using Nmap without Npcap, you cannot
generally scan your own machine from itself (using a
loopback IP such as 127.0.0.1 or any of its
registered IP addresses). This is a Windows limitation that we
have worked around in Npcap, which is included in the Windows self-installer.
Users stuck without a Npcap installation can use a TCP
connect scan without pinging (-sT -Pn) as that uses
the high level socket API rather than sending raw
packets.
Scan speeds on Windows are generally comparable to those on
Unix, though the latter often has a slight performance edge. One
exception to this is connect scan (-sT), which is
often much slower on Windows because of deficiencies in the Windows
networking API. This is a shame, since that is the one TCP scan that
works over all networking types (not just ethernet, like the raw packet scans).
Connect scan performance can be
improved substantially by applying the Registry changes in the
nmap_performance.reg file included with Nmap. By default these changes are applied for you by the Nmap executable installer. This registry file
is in the nmap-<version>
directory of the Windows binary zip file, and
nmap-<version>/mswin32
in the source tarball (where <version> is the
version number of the specific release). These changes increase
the number of ephemeral ports reserved for user applications (such as
Nmap) and reduce the time delay before a closed connection can
be reused. Most people simply check the box to apply these changes in the executable Nmap installer, but you can also apply them by double-clicking on
nmap_performance.reg, or by running the command
regedt32 nmap_performance.reg. To make the changes by hand, add these three Registry DWORD values to
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters:
- MaxUserPort
-
Set a large value such as 65534 (0x0000fffe). See MS KB 196271.
- TCPTimedWaitDelay
-
Set the minimum value (0x0000001e). See MS KB 149532.
- StrictTimeWaitSeqCheck
-
Set to 1 so TCPTimedWaitDelay is checked.
Windows users have three choices for installing
Nmap, all of which are available from the
download page at https://nmap.org/download.html.
Windows Self-installer
Every Nmap release includes a Windows
self-installer named
nmap-<version>-setup.exe
(where <version> is the version number of the
specific release). Most Nmap users choose this option since it is so
easy. Another advantage of the self-installer is that it provides the option to install the Zenmap GUI and other tools. Simply run the installer file and let it walk you through
panels for choosing an install path and installing Npcap. The
installer was created with the open-source Nullsoft Scriptable
Install System. After it completes, read the section called “Executing Nmap on Windows” for instructions on executing Nmap on the
command-line or through Zenmap.
Command-line Zip Binaries
![[Note]](https://nmap.org/book/images/note.png) |
Note |
|---|---|
|
Most users prefer installing Nmap with the self-installer discussed previously. |
Every stable Nmap release comes with Windows
command-line binaries and associated files in a Zip archive. No
graphical interface is included, so you need to run
nmap.exe from a DOS/command window. Or you can
download and install a superior command shell such as those included
with the free
Cygwin
system available from https://www.cygwin.com. Here are the step-by-step instructions for installing and executing the Nmap .zip binaries.
Installing the Nmap zip binaries
-
Download the .zip binaries from
https://nmap.org/download.html. -
Extract the zip file into the directory you want
Nmap to reside in. An example would beC:\Program. A directory called
Files
nmap-should be created, which includes<version>
the Nmap executable and data files. -
For improved performance, apply the Nmap Registry
changes discussed previously. -
Nmap requires the free Npcap packet capture library.
We include a recent Npcap installer which is available in the zip file
asnpcap-,<version>.exe
where<version>is the Npcap version rather
than the Nmap version. Alternatively, you can obtain and install
the latest version fromhttps://npcap.com. -
Due to the way Nmap is compiled, it requires the
Microsoft Visual C++ Redistributable Package of runtime
components. Many systems already have this installed from other
packages, but you should runVC_redist.x86.exe
from the zip file just in case you need it.
Pass the/qoption to run these installers in quiet (non interactive) mode. -
Instructions for executing your compiled Nmap are
given in the section called “Executing Nmap on Windows”.
Compile from Source Code
Most Windows users prefer to use the Nmap binary self-installer,
but compilation from source code is an option, particularly if you plan to help with Nmap development. Compilation requires
Microsoft Visual C++ 2019, which is part of their commercial Visual Studio
suite. Any of the Visual Studio 2019 editions should work, including the free
Visual Studio 2019 Community.
Some of Nmap’s dependencies on Windows are inconvenient to build. For
this reason, precompiled binaries of the dependencies are stored in
Subversion, in the directory /nmap-mswin32-aux.
When building from source, whether from a source code release or from
Subversion, check out /nmap-mswin32-aux as
described below.
Compiling Nmap on Windows from Source
-
Download the Windows dependencies from Subversion with the command
svn checkout https://svn.nmap.org/nmap-mswin32-aux.
The build files are configured to look for dependencies in this
checked-out directory. If you want to build the dependencies yourself
instead, you will have to reconfigure the Visual Studio project files to
point to the alternate directory. -
Decide whether to obtain the Nmap source code by downloading the latest release from nmap.org, or using a Subversion client to retrieve even newer (but less tested) code from our repository. These instructions are for the web download approach, but using Subversion instead is straightforward (see the section called “Obtaining Nmap from the Subversion (SVN) Repository”).
-
Download the latest Nmap source distribution from
https://nmap.org/download.html. It has the name
nmap-or<version>.tar.bz2
nmap-. Those are the same tar file compressed using bzip2 or gzip, respectively. The bzip2-compressed version is smaller.<version>.tgz -
Uncompress the source code file you just downloaded. The
source code directory and thenmap-mswin32-auxmust
be in the same parent directory.
Recent releases of the free Cygwin distribution can handle both the.tar.bz2and.tgzformats. Use the command tar xvjf nmap-version.tar.bz2 or tar xvzf nmap-version.tgz, respectively. Alternatively, the common WinZip application can decompress these files. -
Open Visual Studio and the Nmap solution file (
nmap-).<version>/mswin32/nmap.sln -
Right click on
Solution 'nmap'in the Solution Explorer sidebar and choose “Configuration Manager”. Ensure that the active solution configuration isReleaseand then close the Configuration Manager. -
Build Nmap by pressing F7 or choosing “Build
Solution” from the GUI. Nmap should begin compiling, and
end with the line “-- Done --” saying
that all projects built successfully and there were zero
failures. -
The executable and data files can be found in
nmap-. You can copy them to a preferred directory as long as they are all kept together.<version>/mswin32/Release/ -
Ensure that you have Npcap installed. You can obtain it by
installing our binary self-installer or executing
npcap-from<version>.exe
our zip package. Alternatively, you can obtain the official installer at
https://npcap.com. -
Instructions for executing your compiled Nmap are
given in the next section.
If you wish to build an Nmap executable Windows
installer or Zenmap executable,
see docs/win32-installer-zenmap-buildguide.txt in the Nmap SVN repository.
Many people have asked whether Nmap can be compiled with the
gcc/g++ included
with Cygwin or other compilers. Some users have reported success with
this, but we don’t maintain instructions for building Nmap under
Cygwin.
Executing Nmap on Windows
Nmap releases now include the
Zenmap graphical user interface for Nmap.
If you used the Nmap installer and left the Zenmap field checked,
there should be a new Zenmap entry on your desktop and Start Menu.
Click this to get started. Zenmap is fully documented in
Chapter 12, Zenmap GUI Users’ Guide. While many users love Zenmap, others prefer
the traditional command-line approach to executing Nmap. Here are
detailed instructions for users who are unfamiliar with command-line
interfaces:
-
Make sure the user you are logged in as has
administrative privileges
on the computer (user should be a member of theadministratorsgroup). -
Open a command/DOS Window. Though it can be found in
the program menu tree, the simplest approach is to choose “Start”
-> “Run” and type cmd<enter>. Opening a Cygwin window (if you installed it) by clicking on the Cygwin icon on the desktop works too, although the necessary commands differ slightly from those shown here. -
Change to the directory you installed Nmap into. You can skip this step if Nmap is already in your command path (the Zenmap isntaller adds it there by default). Otherwise, type the following commands.
c:cd "\Program Files (x86)\Nmap"On Windows releases prior to Windows 7, specify
\Program Files\Nmapinstead. The directory will also be different if you chose to install Nmap in a non-default location. -
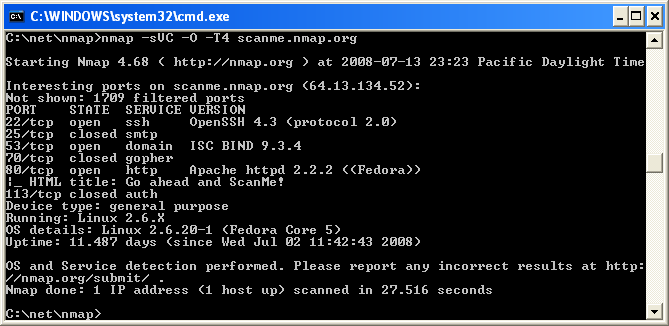
Execute nmap.exe. Figure 2.1 is a screen shot showing a simple example.
Figure 2.1. Executing Nmap from a Windows command shell
If you execute Nmap frequently, you can add the Nmap directory
(c:\Program Files (x86)\Nmap by default) to your command execution path:
-
Open the System Properties window to the Advanced tab by running
SystemPropertiesAdvanced.exe. -
Click the “Environment
Variables” button. -
Choose
Pathfrom the
System variablessection, then hit
edit. -
Add a semi-colon and then your Nmap directory (e.g.
c:\Program Files (x86)\Nmap) to the end of the value. -
Open a new command prompt and you should be able to execute a
command such as nmap scanme.nmap.org from any directory.