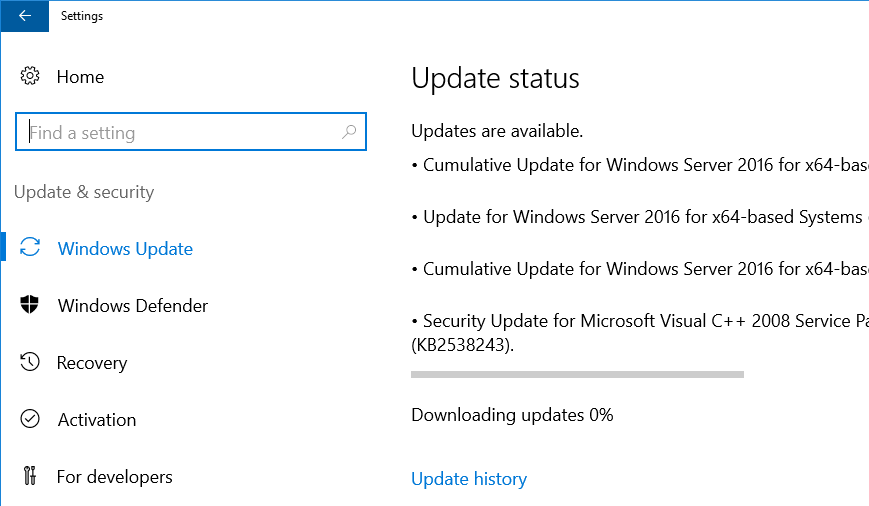
Обнаружил одну интересную особенность в службе обновлений Windows Server 2016. В том случае, если у вас не используется внутренний WSUS сервер, и ОС должна обновляться напрямую с серверов Windows Update в Интернет, то при использовании прокси-сервера для доступа наружу, при попытке загрузить обновления через центр обновлений, в Windows Server 2016 процесс загрузки зависает на этапе скачивания апдейтов на 0% (Downloading Updates 0%).
Что интересно, клиенту Windows Update удалось отправить/загрузить метаданные обновлений (список необходимых обновлений успешно сформировался), но ни одно из них не загружается.
Сформируем и откроем журнал WindowsUpdate.log с помощью командлета Get-WindowsUpdateLog.
2018/06/04 16:24:21.8312332 588 4116 DownloadManager BITS job initialized: JobId = {E3AA21C9B-4BC2-443E-2342-8F693CE1443E}
2018/06/04 16:24:21.8436054 588 4116 DownloadManager Downloading from http://download.windowsupdate.com/c/msdownload/update/software/defu/2017/09/nis_engine_1af0e4b80bf4028f8dac56ebf186b392e4e72486.exe to C:\Windows\SoftwareDistribution\Download\f71ddf93ec2d087c819cf75c55ddfda2\1af0e4b80bf4028f8dac56ebf186b392e4e72486 (full file)
2018/06/04 16:24:21.8452605 588 4116 DownloadManager New download job {E3AA21C9B-4BC2-443E-2342-8F693CE1443E} for UpdateId F608EDA4-2E84-433A-A8C9-8117411F91A8.200
2018/06/04 16:24:21.8545291 588 4116 DownloadManager Download job E3AA21C9B-4BC2-443E-2342-8F693CE1443E resumed.
2018/06/04 16:24:21.8734449 588 4116 DownloadManager Failed to connect to the DO service; (hr = 80040154)
2018/06/04 16:24:21.8734462 588 4116 DownloadManager GetDOManager() failed, hr=80246008, hrExtended=80040154
2018/06/04 16:24:21.8734472 588 4116 DownloadManager Failed creating DO job with hr 80246008
2018/06/04 16:24:21.8772521 588 4116 DownloadManager DO download failed with error 80246008[Extended: 80040154], falling back to BITS and retrying with new Download Job.
Как вы видите, BITS не может закачать файлы с ошибкой 80246008.
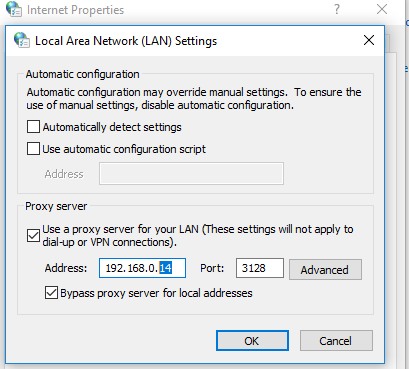
Как оказалось, простая установка параметров прокси-сервера для Internet Explorer в Windows Server 2016 RTM (10.0.14393) не работает так, как в предыдущих версиях Windows. Чтобы клиент Windows Update в Windows Server 2016 мог получать доступ в Интернет через прокси, нужно принудительно указать системный прокси для winhttp.
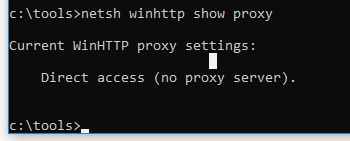
Выведем текущие настройки прокси-сервера для WinHTTP:
netsh winhttp show proxy
Current WinHTTP proxy settings:
Direct access (no proxy server).
Как вы видите, параметры прокси-сервера для WinHTTP не заданы указаны.
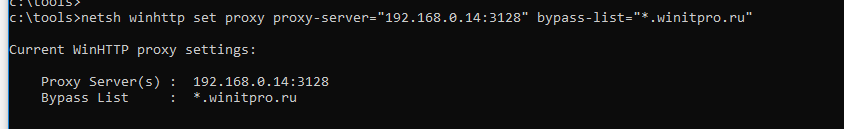
Задать настройки системного прокси для WinHTTP можно так:
netsh winhttp set proxy proxy-server="192.168.0.14:3128" bypass-list="*.winitpro.ru"
Или так, импортировав настройки из IE (настройки прокси в Internet Explorer нужно предварительно задать вручную или настроить через GPO):
netsh winhttp import proxy source=ie
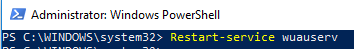
После изменения настроек прокси службу Windows Update нужно перезапустить:
Restart-service wuauserv
После того, как были указан прокси для WinHTTP, Windows Server 2016 начал закачивать обновления с узлов Windows Update.
Аналогичной проблеме подвержена RTM версия Windows 10.
Примечание. Если вручную скачать и установить последнее кумулятивное обновление из каталога обновлений Microsoft (вышедшее после ноября 2016 года), то обновления начинают устанавливаться нормально, даже если не указывать WinHTTP прокси. Судя по информации от Microsoft, этот баг был исправлен в версии агента обновления 10.0.14393.187 и выше.
Также не забудьте, что вы не сможете получать обновления через прокси сервер с авторизацией, т.к. клиент Windows Update не поддерживает возможность авторизации на прокси (в отличии от PowerShell). Чтобы корректно работала служба обновлений Windows, нужно на прокси сервере разрешить анонимный доступ к серверам обновлений Microsoft. Список URL указан ниже:
- update.microsoft.com
- * .update.microsoft.com
- download.windowsupdate.com
- * .download.windowsupdate.com
- download.microsoft.com
- * .download.microsoft.com
- windowsupdate.com
- * .windowsupdate.com
- ntservicepack.microsoft.com
- wustat.windows.com
- mp.microsoft.com
- * .mp.microsoft.com
-
Question
-
You can ignore the restart one. that’s fake news because it didn’t successfully install. The below has been occurring since last year
All replies
-
Hi,
Please click the Failed to install message of the screen you had posted, and provide me the detail error message/code of failed update.
Please try below steps to rename SoftwareDistribution folder:
net stop wuauserv
Ren %systemroot%\SoftwareDistribution SoftwareDistribution.old
net start wuauservThen, re-start system in Clean Boot with 3rd party process disabled, and try to check/install update again to check the result.
How to perform a clean boot in Windows:
https://support.microsoft.com/en-us/help/929135/how-to-perform-a-clean-boot-in-windowsBest Regards,
Eve Wang
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. -
The message does not say anything about why it failed…
A security issue has been identified in a Microsoft software product that could affect your system. You can help protect your system by installing this update from Microsoft. For a complete listing of the issues that are included
in this update, see the associated Microsoft Knowledge Base article. After you install this update, you may have to restart your system.I just manually updated by downloading the update from the updates download website. That works every time so the automatic way should too.
-
Hi,
If possible, when system built-in update failed again, please remember the error code:
there will be Retry icon for you once update installation failed, on top of the icon, there should a paragraph, and error code should be displayed at the end.It would be helpful for further identify.
Besides, please clear existing Windwsupdate.log, then, re-try system built-in update, if it fails again, provide me the widnowsupdate.log file.
How to read the Windowsupdate.log file:
https://support.microsoft.com/en-us/help/902093/how-to-read-the-windowsupdate-log-fileBest Regards,
Eve Wang
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. -
I’m having the exact same issue — the windows defender items update OK, but the cumulative updates have not updated automatically for quite a time. I’ve had to run wusa to install them manually each time.
The error code is 0x800705b4. Running the troubleshooter comes up with some items fixed, but «windows database error» is not fixed. I have run sfc and dism — they report no errors. I’ve stopped the services and renamed the softwaredistribution
and catroot2 directories, no fix.I’ve even followed the instructions here: http://www.thewindowsclub.com/manually-reset-windows-update-components, no fix (note some of the dll’s don’t seem to exist when I regsvr32 them)
I’ve included the last windowsupdate log file to see if it sheds some light on the issue.
2018/05/11 12:02:06.4805804 1184 6444 Shared * START * Service startup
2018/05/11 12:02:07.2120995 1184 6444 Agent WU client version 10.0.14393.2214
2018/05/11 12:02:07.2134706 1184 6444 Agent SleepStudyTracker: Machine is non-AOAC. Sleep study tracker disabled.
2018/05/11 12:02:07.2137723 1184 6444 Agent Base directory: C:\Windows\SoftwareDistribution
2018/05/11 12:02:07.2807160 1184 6444 Agent Datastore directory: C:\Windows\SoftwareDistribution\DataStore\DataStore.edb
2018/05/11 12:02:09.3872246 1184 6444 Shared UpdateNetworkState Ipv6, cNetworkInterfaces = 4.
2018/05/11 12:02:09.3873105 1184 6444 Shared UpdateNetworkState Ipv4, cNetworkInterfaces = 3.
2018/05/11 12:02:09.3895614 1184 6444 Shared Network state: Connected
2018/05/11 12:02:10.4752843 1184 6444 Misc LoadHistoryEventFromRegistry completed, hr = 8024000C
2018/05/11 12:02:10.5391706 1184 6444 Shared UpdateNetworkState Ipv6, cNetworkInterfaces = 4.
2018/05/11 12:02:10.5391926 1184 6444 Shared UpdateNetworkState Ipv4, cNetworkInterfaces = 3.
2018/05/11 12:02:10.5392134 1184 6444 Shared Power status changed
2018/05/11 12:02:10.5894833 1184 6444 Agent Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2018-05-11 21:33:37, not idle-only, not network-only
2018/05/11 12:02:10.6027019 1184 8636 Agent Initializing global settings cache
2018/05/11 12:02:10.6027037 1184 8636 Agent WSUS server: NULL
2018/05/11 12:02:10.6027048 1184 8636 Agent WSUS status server: NULL
2018/05/11 12:02:10.6027063 1184 8636 Agent Alternate Download Server: NULL
2018/05/11 12:02:10.6027070 1184 8636 Agent Fill Empty Content Urls: No
2018/05/11 12:02:10.6027088 1184 8636 Agent Target group: (Unassigned Computers)
2018/05/11 12:02:10.6027099 1184 8636 Agent Windows Update access disabled: No
2018/05/11 12:02:10.7994969 1184 6444 Agent Initializing Windows Update Agent
2018/05/11 12:02:10.8129206 1184 6444 DownloadManager Download manager restoring 0 downloads
2018/05/11 12:02:10.8950328 1184 6444 Agent CPersistentTimeoutScheduler | GetTimer, returned hr = 0x00000000
2018/05/11 12:02:16.3834091 1184 9604 DownloadManager PurgeExpiredFiles::Found 0 expired files to delete.
2018/05/11 12:02:17.2101591 1184 9604 DownloadManager PurgeExpiredUpdates::Found 30 non expired updates.
2018/05/11 12:02:17.3310634 1184 9604 DownloadManager PurgeExpiredUpdates::Found 0 expired updates.
2018/05/11 12:02:17.3651914 1184 9604 Shared Effective power state: AC
2018/05/11 12:02:17.3651939 1184 9604 DownloadManager Power state change detected. Source now: AC
2018/05/11 12:07:51.7848203 9924 3320 AppAU * START *
2018/05/11 12:07:51.7990969 9924 3320 AppAU * START * Finding app updates
1600/12/31 19:00:00.0000000 9800 8748 Unknown( 10): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 9800 8748 Unknown( 11): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 9800 9948 Unknown( 15): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 9800 9948 Unknown( 17): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 9800 8748 Unknown( 10): GUID=fe1b6309-dedb-392e-308c-ec757efded1a (No Format Information found).
2018/05/11 12:07:53.6006802 9924 3320 AppAU * END * Finding app updates, exit code = 0x00000000
2018/05/11 12:07:53.6020776 9924 3320 AppAU * END *, exit code = 0x00000000
2018/05/11 12:17:53.5208870 1184 7688 Agent Earliest future timer found:
2018/05/11 12:17:53.5209163 1184 7688 Agent Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2018-05-11 21:33:37, not idle-only, not network-only
2018/05/11 12:17:54.5414859 1184 6444 Agent Earliest future timer found:
2018/05/11 12:17:54.5415016 1184 6444 Agent Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2018-05-11 21:33:37, not idle-only, not network-only
2018/05/11 12:17:54.5670519 1184 6444 Misc CreateSessionStateChangeTrigger, TYPE:2, Enable:No
2018/05/11 12:17:54.5670621 1184 6444 Misc CreateSessionStateChangeTrigger, TYPE:4, Enable:No
2018/05/11 12:17:54.7457392 1184 6444 Handler CUHCbsHandler::CancelDownloadRequest called
2018/05/11 12:17:55.4934728 1184 6444 Shared * END * Service exit Exit code = 0x240001
2018/05/11 12:53:03.0561254 1184 7612 Shared * START * Service startup
2018/05/11 12:53:03.8542510 1184 7612 Agent WU client version 10.0.14393.2214
2018/05/11 12:53:03.8555906 1184 7612 Agent SleepStudyTracker: Machine is non-AOAC. Sleep study tracker disabled.
2018/05/11 12:53:03.8558594 1184 7612 Agent Base directory: C:\Windows\SoftwareDistribution
2018/05/11 12:53:03.8816766 1184 7612 Agent Datastore directory: C:\Windows\SoftwareDistribution\DataStore\DataStore.edb
2018/05/11 12:53:05.7460730 1184 7612 Shared UpdateNetworkState Ipv6, cNetworkInterfaces = 4.
2018/05/11 12:53:05.7461446 1184 7612 Shared UpdateNetworkState Ipv4, cNetworkInterfaces = 3.
2018/05/11 12:53:05.7478876 1184 7612 Shared Network state: Connected
2018/05/11 12:53:06.6616513 1184 7612 Misc LoadHistoryEventFromRegistry completed, hr = 8024000C
2018/05/11 12:53:06.8821078 1184 7612 Shared UpdateNetworkState Ipv6, cNetworkInterfaces = 4.
2018/05/11 12:53:06.8821290 1184 7612 Shared UpdateNetworkState Ipv4, cNetworkInterfaces = 3.
2018/05/11 12:53:06.8821487 1184 7612 Shared Power status changed
2018/05/11 12:53:06.8951036 1184 9092 Agent Initializing global settings cache
2018/05/11 12:53:06.8951054 1184 9092 Agent WSUS server: NULL
2018/05/11 12:53:06.8951065 1184 9092 Agent WSUS status server: NULL
2018/05/11 12:53:06.8951076 1184 9092 Agent Alternate Download Server: NULL
2018/05/11 12:53:06.8951087 1184 9092 Agent Fill Empty Content Urls: No
2018/05/11 12:53:06.8951102 1184 9092 Agent Target group: (Unassigned Computers)
2018/05/11 12:53:06.8951113 1184 9092 Agent Windows Update access disabled: No
2018/05/11 12:53:06.9485969 1184 7612 Agent Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2018-05-11 21:33:37, not idle-only, not network-only
2018/05/11 12:53:07.3000973 1184 7612 Agent Initializing Windows Update Agent
2018/05/11 12:53:07.3717867 1184 7612 DownloadManager Download manager restoring 0 downloads
2018/05/11 12:53:07.4788658 1184 7612 Agent CPersistentTimeoutScheduler | GetTimer, returned hr = 0x00000000
1600/12/31 19:00:00.0000000 1088 668 Unknown( 11): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 1088 2240 Unknown( 15): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 1088 2240 Unknown( 17): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 1088 668 Unknown( 10): GUID=fe1b6309-dedb-392e-308c-ec757efded1a (No Format Information found).
1600/12/31 19:00:00.0000000 1088 668 Unknown( 10): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 1088 668 Unknown( 11): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 1088 2240 Unknown( 15): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 1088 2240 Unknown( 17): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 1088 668 Unknown( 10): GUID=fe1b6309-dedb-392e-308c-ec757efded1a (No Format Information found).
1600/12/31 19:00:00.0000000 1088 8076 Unknown( 10): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 1088 8076 Unknown( 11): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 1088 2224 Unknown( 15): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 1088 2224 Unknown( 17): GUID=349c41a9-8927-3d50-ed8a-be0b57a7b6b2 (No Format Information found).
1600/12/31 19:00:00.0000000 1088 8076 Unknown( 10): GUID=fe1b6309-dedb-392e-308c-ec757efded1a (No Format Information found).
2018/05/11 12:54:29.8321341 1184 7780 Shared Effective power state: AC
2018/05/11 12:54:29.8321366 1184 7780 DownloadManager Power state change detected. Source now: AC
2018/05/11 13:12:26.4403640 1184 1336 Agent Earliest future timer found:
2018/05/11 13:12:26.4403937 1184 1336 Agent Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2018-05-11 21:33:37, not idle-only, not network-only
2018/05/11 13:12:27.4576229 1184 7612 Agent Earliest future timer found:
2018/05/11 13:12:27.4576518 1184 7612 Agent Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2018-05-11 21:33:37, not idle-only, not network-only
2018/05/11 13:12:27.7707115 1184 7612 Misc CreateSessionStateChangeTrigger, TYPE:2, Enable:No
2018/05/11 13:12:27.7707225 1184 7612 Misc CreateSessionStateChangeTrigger, TYPE:4, Enable:No
2018/05/11 13:12:28.5225259 1184 7612 Handler CUHCbsHandler::CancelDownloadRequest called
2018/05/11 13:12:30.7571203 1184 7612 Shared * END * Service exit Exit code = 0x240001
2018/05/11 14:02:07.7597008 1184 4464 Agent WU client version 10.0.14393.2214
2018/05/11 14:02:07.7613732 1184 4464 Agent SleepStudyTracker: Machine is non-AOAC. Sleep study tracker disabled.
2018/05/11 14:02:07.7616793 1184 4464 Agent Base directory: C:\Windows\SoftwareDistribution
2018/05/11 14:02:07.8425155 1184 4464 Agent Datastore directory: C:\Windows\SoftwareDistribution\DataStore\DataStore.edb
2018/05/11 14:02:09.6425395 1184 4464 Shared UpdateNetworkState Ipv6, cNetworkInterfaces = 4.
2018/05/11 14:02:09.6426101 1184 4464 Shared UpdateNetworkState Ipv4, cNetworkInterfaces = 3.
2018/05/11 14:02:09.6444042 1184 4464 Shared Network state: Connected
2018/05/11 14:02:09.8339210 1184 4464 Misc LoadHistoryEventFromRegistry completed, hr = 8024000C
2018/05/11 14:02:09.8789514 1184 4464 Shared UpdateNetworkState Ipv6, cNetworkInterfaces = 4.
2018/05/11 14:02:09.8789635 1184 4464 Shared UpdateNetworkState Ipv4, cNetworkInterfaces = 3.
2018/05/11 14:02:09.8789752 1184 4464 Shared Power status changed
2018/05/11 14:02:09.9252636 1184 4928 Agent Initializing global settings cache
2018/05/11 14:02:09.9252647 1184 4928 Agent WSUS server: NULL
2018/05/11 14:02:09.9252655 1184 4928 Agent WSUS status server: NULL
2018/05/11 14:02:09.9252658 1184 4928 Agent Alternate Download Server: NULL
2018/05/11 14:02:09.9252666 1184 4928 Agent Fill Empty Content Urls: No
2018/05/11 14:02:09.9252673 1184 4928 Agent Target group: (Unassigned Computers)
2018/05/11 14:02:09.9252680 1184 4928 Agent Windows Update access disabled: No
2018/05/11 14:02:09.9624536 1184 4464 Agent Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2018-05-11 21:33:37, not idle-only, not network-only
2018/05/11 14:02:10.2140472 1184 4464 Agent Initializing Windows Update Agent
2018/05/11 14:02:10.2344025 1184 4464 DownloadManager Download manager restoring 0 downloads
2018/05/11 14:02:10.2641782 1184 4464 Agent CPersistentTimeoutScheduler | GetTimer, returned hr = 0x00000000
2018/05/11 14:02:15.6761404 1184 10036 Shared Effective power state: AC
2018/05/11 14:02:15.6761430 1184 10036 DownloadManager Power state change detected. Source now: AC
2018/05/11 14:20:59.6613201 1184 9652 Agent Earliest future timer found:
2018/05/11 14:20:59.6613504 1184 9652 Agent Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2018-05-11 21:33:37, not idle-only, not network-only
2018/05/11 14:21:00.6726018 1184 4464 Agent Earliest future timer found:
2018/05/11 14:21:00.6726351 1184 4464 Agent Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2018-05-11 21:33:37, not idle-only, not network-only
2018/05/11 14:21:00.6976532 1184 4464 Misc CreateSessionStateChangeTrigger, TYPE:2, Enable:No
2018/05/11 14:21:00.6976627 1184 4464 Misc CreateSessionStateChangeTrigger, TYPE:4, Enable:No
2018/05/11 14:21:00.7159284 1184 4464 Handler CUHCbsHandler::CancelDownloadRequest called
2018/05/11 14:21:01.1417927 1184 4464 Shared * END * Service exit Exit code = 0x240001
2018/05/11 15:02:07.7888712 1184 3620 Shared * START * Service startup
2018/05/11 15:02:08.1791601 1184 3620 Agent WU client version 10.0.14393.2214
2018/05/11 15:02:08.1804817 1184 3620 Agent SleepStudyTracker: Machine is non-AOAC. Sleep study tracker disabled.
2018/05/11 15:02:08.1807363 1184 3620 Agent Base directory: C:\Windows\SoftwareDistribution
2018/05/11 15:02:08.2273546 1184 3620 Agent Datastore directory: C:\Windows\SoftwareDistribution\DataStore\DataStore.edb
2018/05/11 15:02:09.5964587 1184 3620 Shared UpdateNetworkState Ipv6, cNetworkInterfaces = 4.
2018/05/11 15:02:09.5965366 1184 3620 Shared UpdateNetworkState Ipv4, cNetworkInterfaces = 3.
2018/05/11 15:02:09.5983198 1184 3620 Shared Network state: Connected
2018/05/11 15:02:10.2887560 1184 3620 Misc LoadHistoryEventFromRegistry completed, hr = 8024000C
2018/05/11 15:02:10.3499061 1184 3620 Shared UpdateNetworkState Ipv6, cNetworkInterfaces = 4.
2018/05/11 15:02:10.3499273 1184 3620 Shared UpdateNetworkState Ipv4, cNetworkInterfaces = 3.
2018/05/11 15:02:10.3499471 1184 3620 Shared Power status changed
2018/05/11 15:02:10.4473908 1184 3620 Agent Initializing global settings cache
2018/05/11 15:02:10.4473919 1184 3620 Agent WSUS server: NULL
2018/05/11 15:02:10.4473927 1184 3620 Agent WSUS status server: NULL
2018/05/11 15:02:10.4473930 1184 3620 Agent Alternate Download Server: NULL
2018/05/11 15:02:10.4473938 1184 3620 Agent Fill Empty Content Urls: No
2018/05/11 15:02:10.4473945 1184 3620 Agent Target group: (Unassigned Computers)
2018/05/11 15:02:10.4473952 1184 3620 Agent Windows Update access disabled: No
2018/05/11 15:02:10.4659019 1184 8608 Agent Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2018-05-11 21:33:37, not idle-only, not network-only
2018/05/11 15:02:10.5844979 1184 8608 Agent Initializing Windows Update Agent
2018/05/11 15:02:10.5978378 1184 8608 DownloadManager Download manager restoring 0 downloads
2018/05/11 15:02:10.6383927 1184 8608 Agent CPersistentTimeoutScheduler | GetTimer, returned hr = 0x00000000
2018/05/11 15:02:14.7045245 1184 7808 Shared Effective power state: AC
2018/05/11 15:02:14.7045271 1184 7808 DownloadManager Power state change detected. Source now: AC
2018/05/11 15:20:59.9620133 1184 2388 Agent Earliest future timer found:
2018/05/11 15:20:59.9620422 1184 2388 Agent Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2018-05-11 21:33:37, not idle-only, not network-only
2018/05/11 15:21:00.9700571 1184 3620 Agent Earliest future timer found:
2018/05/11 15:21:00.9700860 1184 3620 Agent Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2018-05-11 21:33:37, not idle-only, not network-only
2018/05/11 15:21:01.0417952 1184 3620 Misc CreateSessionStateChangeTrigger, TYPE:2, Enable:No
2018/05/11 15:21:01.0418051 1184 3620 Misc CreateSessionStateChangeTrigger, TYPE:4, Enable:No
2018/05/11 15:21:01.0612498 1184 3620 Handler CUHCbsHandler::CancelDownloadRequest called
2018/05/11 15:21:01.4308539 1184 3620 Shared * END * Service exit Exit code = 0x240001
2018/05/11 15:46:45.2145025 1184 8916 Shared * START * Service startup
2018/05/11 15:46:45.2997503 1184 8916 Agent WU client version 10.0.14393.2214
2018/05/11 15:46:45.3009337 1184 8916 Agent SleepStudyTracker: Machine is non-AOAC. Sleep study tracker disabled.
2018/05/11 15:46:45.3012120 1184 8916 Agent Base directory: C:\Windows\SoftwareDistribution
2018/05/11 15:46:45.3032267 1184 8916 Agent Datastore directory: C:\Windows\SoftwareDistribution\DataStore\DataStore.edb
2018/05/11 15:46:45.7150617 1184 8916 Shared UpdateNetworkState Ipv6, cNetworkInterfaces = 4.
2018/05/11 15:46:45.7151330 1184 8916 Shared UpdateNetworkState Ipv4, cNetworkInterfaces = 3.
2018/05/11 15:46:45.7169699 1184 8916 Shared Network state: Connected
2018/05/11 15:46:45.8069233 1184 8916 Misc LoadHistoryEventFromRegistry completed, hr = 8024000C
2018/05/11 15:46:45.8194342 1184 8916 Shared UpdateNetworkState Ipv6, cNetworkInterfaces = 4.
2018/05/11 15:46:45.8194565 1184 8916 Shared UpdateNetworkState Ipv4, cNetworkInterfaces = 3.
2018/05/11 15:46:45.8194751 1184 8916 Shared Power status changed
2018/05/11 15:46:45.8521486 1184 8916 Agent Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2018-05-11 21:33:37, not idle-only, not network-only
2018/05/11 15:46:45.8652556 1184 7764 Agent Initializing global settings cache
2018/05/11 15:46:45.8652571 1184 7764 Agent WSUS server: NULL
2018/05/11 15:46:45.8652585 1184 7764 Agent WSUS status server: NULL
2018/05/11 15:46:45.8652596 1184 7764 Agent Alternate Download Server: NULL
2018/05/11 15:46:45.8652607 1184 7764 Agent Fill Empty Content Urls: No
2018/05/11 15:46:45.8652622 1184 7764 Agent Target group: (Unassigned Computers)
2018/05/11 15:46:45.8652633 1184 7764 Agent Windows Update access disabled: No
2018/05/11 15:46:45.9788966 1184 8916 Agent Initializing Windows Update Agent
2018/05/11 15:46:45.9798957 1184 8916 DownloadManager Download manager restoring 0 downloads
2018/05/11 15:46:45.9911486 1184 8916 Agent CPersistentTimeoutScheduler | GetTimer, returned hr = 0x00000000
1600/12/31 19:00:00.0000000 1184 7764 Unknown( 10): GUID=eb73583d-5481-33b4-202d-9bb270eddffa (No Format Information found).
1600/12/31 19:00:00.0000000 1184 7764 Unknown( 11): GUID=eb73583d-5481-33b4-202d-9bb270eddffa (No Format Information found).
2018/05/11 15:46:49.2723656 1184 7764 Agent * START * Queueing Finding updates [CallerId = UpdateOrchestrator Id = 1]
2018/05/11 15:46:49.2723814 1184 7764 Agent Added service 00000000-0000-0000-0000-000000000000 to sequential scan list
1600/12/31 19:00:00.0000000 1184 7764 Unknown( 12): GUID=eb73583d-5481-33b4-202d-9bb270eddffa (No Format Information found).
2018/05/11 15:46:49.2879423 1184 8760 Agent * END * Queueing Finding updates [CallerId = UpdateOrchestrator Id = 1]
2018/05/11 15:46:49.3028588 1184 8760 Agent * START * Finding updates CallerId = UpdateOrchestrator Id = 1
2018/05/11 15:46:49.3028614 1184 8760 Agent Online = Yes; AllowCachedResults = No; Ignore download priority = No
2018/05/11 15:46:49.3028643 1184 8760 Agent Criteria = IsInstalled=0 and DeploymentAction=’Installation’ or IsPresent=1 and DeploymentAction=’Uninstallation’ or IsInstalled=1 and DeploymentAction=’Installation’
and RebootRequired=1 or IsInstalled=0 and DeploymentAction=’Uninstallation’ and RebootRequired=1″»
2018/05/11 15:46:49.3028749 1184 8760 Agent ServiceID = {00000000-0000-0000-0000-000000000000} Third party service
2018/05/11 15:46:49.3028763 1184 8760 Agent Search Scope = {Machine}
2018/05/11 15:46:49.3028859 1184 8760 Agent Caller SID for Applicability: S-1-5-21-2520894800-3868199361-3526192511-1000
2018/05/11 15:46:49.3028870 1184 8760 Agent ProcessDriverDeferrals is set
2018/05/11 15:46:49.3028880 1184 8760 Agent RegisterService is set
2018/05/11 15:46:49.3442493 1184 8760 Misc Got 9482F4B4-E343-43B6-B170-9A65BC822C77 redir SecondaryServiceAuth URL: 117cab2d-82b1-4b5a-a08c-4d62dbee7782″»
2018/05/11 15:46:49.3481752 1184 8760 SLS CoCreateInstance Failed: hr = 0x80040154
2018/05/11 15:46:49.3481818 1184 8760 Agent Failed to retrieve SLS response data for service 117cab2d-82b1-4b5a-a08c-4d62dbee7782, error = 0x80040154
2018/05/11 15:46:49.3481895 1184 8760 Agent Caller Service Recovery failed to opt in to service 117cab2d-82b1-4b5a-a08c-4d62dbee7782, hr=0X80040154
2018/05/11 15:46:49.3499083 1184 8760 Misc Got 9482F4B4-E343-43B6-B170-9A65BC822C77 redir SecondaryServiceAuth URL: 7971f918-a847-4430-9279-4a52d1efe18d»» -
I’ve attached the log end of another failed upgrade. This time the CU showed up in WU and I clicked install. Again it failed with 0x800705b4.
2018/05/13 11:30:38.5417774 552 8820 Agent * START * Installing updates CallerId = UpdateOrchestrator
2018/05/13 11:30:38.5417796 552 8820 Agent Updates to install = 1
2018/05/13 11:30:38.5504154 552 8820 Agent Title = 2018-05 Cumulative Update for Windows Server 2016 for x64-based Systems (KB4103723)
2018/05/13 11:30:38.5504319 552 8820 Agent UpdateId = 99A0B90D-2519-4700-BE0C-E6C7B5BD04EC.202
2018/05/13 11:30:38.5504333 552 8820 Agent Bundles 1 updates:
2018/05/13 11:30:38.5504439 552 8820 Agent C168E41D-0CC8-49BD-8A93-47BB39206A1E.202
2018/05/13 11:30:41.8070529 552 8820 Handler Loaded state: cCompleteIterations: 1, pt: SelfContainedNoExpressPayload, nNextRequestID: 1.
2018/05/13 11:30:42.0552810 552 8820 DownloadManager Preparing update for install, updateId = {C168E41D-0CC8-49BD-8A93-47BB39206A1E}.202.
2018/05/13 11:30:42.5759887 1620 3956 Handler * START * CBS Install
2018/05/13 11:30:42.5780630 1620 3956 Handler Starting install of CBS update C168E41D-0CC8-49BD-8A93-47BB39206A1E
2018/05/13 11:30:42.6470358 1620 3956 Handler CBS session identity: 30665423_1522368624
2018/05/13 11:30:43.4494416 1620 3956 Handler CBS package identity: Package_for_RollupFix~31bf3856ad364e35~amd64~~14393.2248.1.5
2018/05/13 11:30:43.4673786 1620 3956 Handler Loaded state: cCompleteIterations: 1, pt: SelfContainedNoExpressPayload, nNextRequestID: 1.
2018/05/13 11:30:43.4706689 1620 3956 Handler Installing SelfContainedNoExpressPayload with source=C:\Windows\SoftwareDistribution\Download\cf74a5b09f19de7637d9c5aa90a0406d\Windows10.0-KB4103723-x64.cab,
workingdir=C:\Windows\SoftwareDistribution\Download\cf74a5b09f19de7637d9c5aa90a0406d\inst
2018/05/13 11:31:23.5090497 1620 6028 Handler CBS called Initiate
2018/05/13 11:31:23.5382004 1620 9912 Handler CBS called Progress with state=2, ticks=10, total=1000
1600/12/31 19:00:00.0000000 5648 5616 Unknown( 10): GUID=fe1b6309-dedb-392e-308c-ec757efded1a (No Format Information found).
1600/12/31 19:00:00.0000000 5648 5616 Unknown( 10): GUID=fe1b6309-dedb-392e-308c-ec757efded1a (No Format Information found).
2018/05/13 12:01:23.6382642 1620 8860 Handler CUHCbsHandler::Cancel called with fReleaseThreadNow=0 -
Hi,
>The error code is 0x800705b4. Running the troubleshooter comes up with some items fixed, but «windows database error» is not fixed.
Please try to use DISM.EXE to do a reparation and check the result.Fix Windows Update errors by using the DISM or System Update Readiness tool:
https://support.microsoft.com/en-us/help/947821/fix-windows-update-errors-by-using-the-dism-or-system-update-readinessBest Regards,
Eve Wang
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com.No improvement. I ran:
DISM.exe /Online /Cleanup-Image /RestoreHealth
DISM.exe /Online /Cleanup-Image /RestoreHealth /Source:H:\sources\install.wim:1/LimitAccess (H: is the installation DVD)
both reported «the restore operation completed successfully», no problems reported
sfc /scannow
It said it did not find any integrity violations
running windows update on the Cumulative Update again failed with 0x800705b4
-
Hi,
The error “0x800705b4” usually means “Timeout”. Please take the following steps to troubleshoot the issue.
1. If the Windows Update service has been configured in standalone mode, then the similar issue would occur. Please open an administrator command line and run the following command line to move WUA back into a shared svchost:
sc config wuauserv type= share2. Reconfigure the privileges on WUA so that the call to ZwOpenProcess() will be allowed.
sc privs wuauserv SeAssignPrimaryTokenPrivilege/SeAuditPrivilege/SeBackupPrivilege/SeChangeNotifyPrivilege/SeCreateGlobalPrivilege/SeCreatePagefilePrivilege/SeCreatePermanentPrivilege/SeCreateSymbolicLinkPrivilege/SeDebugPrivilege/SeImpersonatePrivilege/SeIncreaseBasePriorityPrivilege/SeIncreaseQuotaPrivilege/SeIncreaseWorkingSetPrivilege/SeLoadDriverPrivilege/SeLockMemoryPrivilege/SeManageVolumePrivilege/SeProfileSingleProcessPrivilege/SeRestorePrivilege/SeSecurityPrivilege/SeShutdownPrivilege/SeSystemEnvironmentPrivilege/SeSystemProfilePrivilege/SeSystemtimePrivilege/SeTakeOwnershipPrivilege/SeTcbPrivilege/SeTimeZonePrivilege/SeUndockPrivilege3. Perform a clean boot then install the update. If there is any third party antivirus software installed, we may consider to uninstall it completely temporarily
How to perform a clean boot in Windows:
https://support.microsoft.com/en-us/help/929135/how-to-perform-a-clean-boot-in-windows4. Try to increase the timeout of TrustedInstaller:
a. Open registry by run regedit.exe.
b. Navigate to HKLM\System\CurrentControlSet\Services\TrustedInstaller.
c. Right click it and export it for a backup.
d. Set this registry value: BlockTimeIncrement
to “2a30” (3 hours timeout).
e. You may receive error when you set this value, please right click the “TrustedInstaller” key and set the permission to “Full Control” to users.
f. Restart computer and install update again.If the issue persists, please help to take the following steps then upload the logs to OneDrive.
1. If the issue persists, please take the following steps to collect the related logs.
a. Stop the Windows Update service by running “net stop wuauserv” as administrator.
b. Backup the cbs.log (C:\Windows\Logs\CBS) and clear everything in it.
c. Install the latest update KB4103723 manually and restart the machine to reproduce the issue:
https://www.catalog.update.microsoft.com/Search.aspx?q=KB4103723
d. Export Event Viewer\Windows Logs\Applications, System, Setup.
e. Upload the CBS.log and event logs to
One Drive(https://onedrive.live.com/) and share the link here.Best Regards,
Eve Wang
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com.-
Proposed as answer by
Wednesday, May 23, 2018 9:08 AM
-
Proposed as answer by
-
Neither the windows update sc commands, nor increasing the timeout in trusted installer fixed the error 0x800705b4 in windows update.
I manually installed KB4103723 (it was successful) and then the latest defender update (via windows update) and have captured the CBS and event logs as requested in:
https://onedrive.live.com/?id=2DB94D83D2F570EB%21284&cid=2DB94D83D2F570EB
Since the cumulative update was installed manually, I won’t be able to repeat the windows update issue until the next cumulative update is released.
-
Hi,
According to the log, it seems that the updates have been installed correctly now.
I want to confirm with you if automatic update fails while update manually works? Please have an verification for next CU and check the result.
If system automatic Windows Update fails again, we could try to reset the windows update component:
https://gallery.technet.microsoft.com/scriptcenter/Reset-Windows-Update-Agent-d824badcBest Regards,
Eve Wang
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. -
I’m confirming that automatic updates failed in the past and manual updates always worked. I have installed four or more CUs manually that failed automatically.
I’ve already run the WU reset tool before posting my first message and it did not fix the automatic update.
I’ll resurrect this thread when the next CU is released and I confirm automatic update fails.
-
Hi,
Thank you for updating, if there is anything new, please feel free to let us know.
Best Regards,
Eve Wang
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. -
I have had the exact same problem as you with WSE 2016. Cumulative updates always fail, antivirus always installs along with any other smaller updates. When I run the standalone updater, the cumulative update will install. I have run
many of the same fixes listed above, but none has fixed this problem, which occurs each month when the CU is sent out. -
Hi,
@heythereyou
Have you tried to re-set Windows Update component? And try automatically update again?If manually installation works, please wait for next month CU, if problem happens again, please post a new thread on this forum, also, provides detail system information and WindowsUpdata.log file.
Best Regards,
Eve Wang
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. -
Hi,
Is there any update?
Please click “Mark as answer” if any of above reply is helpful. It would make this reply to the top and easier to be found for other people who has the similar problem.
Best Regards,
Eve Wang
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. -
I have had the exact same problem as you with WSE 2016. Cumulative updates always fail, antivirus always installs along with any other smaller updates. When I run the standalone updater, the cumulative update will install. I have
run many of the same fixes listed above, but none has fixed this problem, which occurs each month when the CU is sent out.lol ugh. Now even manual seems to not be working. Or just taking a real long time. It’s been an hour already
-
Actually, it updated. Just took almost two hours to update.
-
Hi,
Thank you for taking the time to have an update about the result.
Once problem happens again, please provide detail system information and relate log file as mentioned above. Post a new thread and we will try to find out more detail information about such problem.
Best Regards,
Eve Wang
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. -
I’m confirming that automatic updates failed in the past and manual updates always worked. I have installed four or more CUs manually that failed automatically.
I’ve already run the WU reset tool before posting my first message and it did not fix the automatic update.
I’ll resurrect this thread when the next CU is released and I confirm automatic update fails.
The next wave of updates are out. KB2267602, definition update for windows defender, and KB4132216 installed OK via windows update. CU KB4103720 failed with error 0x800705b4. I’ve uploaded msinfo.txt and windowsupdate.log to one-drive,
here:https://onedrive.live.com/?id=2DB94D83D2F570EB%21284&cid=2DB94D83D2F570EB
-
Hi,
I had downloaded your log files. you can delete them safely.
Besides, there should be a period of time for me the analyzing these logs. I will reply to you as soon as possible.
Best Regards,
Eve Wang
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. -
I have had the same issue
Physical server running Windows Server 2016 Standard with OS build 14393.1715 (September 12th 2017) and refusing to install later monthly cumulative updates with various error codes, but happily applying minor updates.
The physical server hosts a single HYPER-V server running Windows Server 2016 Standard which was happily installing the monthly cumulative updates.
Today I tried applying the updates to the physical server using the sconfig utility and rebooting and it worked!
So now both servers (physical and HYPER-V) are running Windows Server 2016 Standard with OS build 14393.2248 (May 8th 2018).
-
I have had the same issue
Physical server running Windows Server 2016 Standard with OS build 14393.1715 (September 12th 2017) and refusing to install later monthly cumulative updates with various error codes, but happily applying minor updates.
The physical server hosts a single HYPER-V server running Windows Server 2016 Standard which was happily installing the monthly cumulative updates.
Today I tried applying the updates to the physical server using the sconfig utility and rebooting and it worked!
So now both servers (physical and HYPER-V) are running Windows Server 2016 Standard with OS build 14393.2248 (May 8th 2018).
What did you actually do with sconfig? After giving it a quick glance at the tool, it seems like all you can do is change update settings.
-
I used option 6 ‘Download and Install Updates’ and then option 13 ‘Restart Server’
-
Edited by
Kayak2
Friday, June 8, 2018 4:13 PM
-
Edited by
-
I used option 6 ‘Download and Install Updates’ and then option 13 ‘Restart Server’
Ah ok. I missed that option. I’ll try it with next update
-
I had to download it manually again. Sconfig doesn’t work for me — it just opens and closes with no activity
-
Does sconfig display the options and then prompt you to enter one allowing you to type ‘6’ to select ‘Download and Install Updates’ ?
-
Dealing with a Hyper-V server, I followed your advice and modified «sc» configurations, rebooted and manually downloaded and installed the updates successfully. Thanks.
-
-
Edited by
El Dab67 plus
Monday, July 16, 2018 6:45 PM
additional info
-
Edited by
-
Does sconfig display the options and then prompt you to enter one allowing you to type ‘6’ to select ‘Download and Install Updates’ ?
Yeah, and it just reverts back to the cmd prompt window with the options. Nothing happens.
This is very frustrating. Still have to download updates manually. The delta package fails. The cumulative one takes hours to install. Takes some unknown time to then reboot as well.
-
We’ve been seeing the same growing problem with this since May, 2018. Generally it is Windows 2016 running on a VM hosted on older hardware. They timeout installing the cumulative security update no matter how high the max run time is set for the update.
Manual download and installation always works, although the installation times are excessively high. -
There are issues at least for me with downloads as well — deltas fail to install. need to install cumulative patches
-
So 10 weeks on from my first post (June 8th) with the virtual server still happily automatically updating I tried updating the physical server using Settings/Update & Security/ Windows Update. It tried to apply
2018-08 Cumulative Update for Windows Server 2016 for x64-based Systems (KB4343887)
this failed with error code 0x8024a105, however as before when I used sconfig with option 6 ‘Download and Install Updates’ and then option 13 ‘Restart Server’ the cumulative update was installed successfully.
-
Well, good that the option works for you but for some reason nothing happens for me when I try sconfig. Still doing it manually and it still takes half a day to install the patch. It’s pretty ridiculous but I don’t want to reformat / reinstall
server for this. I’ll just deal since obviously the issue will be ignored. -
Well, that’s a surprise. I haven’t tried in a while so maybe it was fixed earlier but the latest cumulative update did patch without having to do it manually. Here’s hoping the same for October
-
No solution for this and MS. is not able to fix it. I have the same problem. Server is not updated since September last year…it is just baloney.
Luka Radunovic
-
So approximately a year after my earlier posts I thought I would update this thread to say that updates to both the virtual and physical server are now being successfully applied without needing to resort to using sconfig.
Both servers (physical and HYPER-V) are running Windows Server 2016 Standard with OS build 14393.2999 and 14393.2972 respectively
-
Hello everyone. These are the steps that worked for me, and a little context:
— I received a HPE DL20 Gen9 server, compatible with Windows Server 2016 Standard according to HP.
— I had to manually update after the first clean installation of Windows Server 2016 Standard v1607 because updates just didn’t install automatically. The cumulative updates successfully applied were 2018-05 (kb4103720), 2018-11 (kb4467684) and 2019-03 (kb4489889).
— Servicing stack, Adobe flash, and other minor updates were also applied every month.
— It seemed Windows Update was working fine. But not with cumulative updates (same issues reported here and everywhere else).
— And sconfig utility didn’t even detect updates to download and install.
— So I used sconfig utility to set updates to ‘manual’ and then manually applied, in order, these cumulative updates: 2019-04 (kb4493470 and kb4493473), 2019-05 (kb4499177), 2019-06 (kb4503267). Success.
— What’s next? Manually install, in order, the next cumulative updates: 2019-06 (KB4503294 and KB4509475) and 2019-07 (KB4507460 and KB4507459)
All updates were manually downloaded from Microsoft Catalog. I always use this website to get important information: https://support.microsoft.com/en-us/help/4000825/windows-10-windows-server-2016-update-history.
It’s unbelievable I have to go through this nightmare AGAIN, after all these annoying, time-consuming, patience-testing type of issues with Windows 10 (since its first version). And this is an expensive Windows Server product, wich is supposed to fulfill
very important or even critical tasks. It’s been months and I can’t put this HP server to use.I’ll keep you posted.
Cesar.
-
OK but what’s next ?
Will you continue ton download and install manualy next cumulative updates ?
-
I had this same problem — spent most of the last 2 days researching this — here is what finally worked for me — perhaps this will help others — short answer is the System Reserved partition was full — here are the steps that I took to fix it
windows administrative tools — computer management — disk management
— right click on system reserved partition and go to properties — is free space at 0 (zero)? close window
— right click on system reserved partition and go to change drive letter and paths
— add a drive letter — I used Z
-click ok and close all windowscontrol panel — file explorer options — view tab
— select ‘Show hidden files, folders and drives’
— uncheck ‘Hide Protected Operating System Files’
— click ok and close all windowsstart — this PC — Z drive
— right click on system volume information — properties — security — advanced
— change owner to your admin user account and also replace owner on subcontainers and objectsstart — type cmd — right click on command prompt and run as administrator
— type these commands within the command prompt
— z:
— cd system volume information
— del *.logclose all windows and reboot server
after reboot
windows administrative tools — computer management — disk management
— right click on system reserved partition and go to properties — you should now have free space
— close all windowsstart — this PC — Z drive
— right click on system volume information — properties — security — advanced
— change owner back to the default System and also replace owner on all subcontainers and objectswindows administrative tools — computer management — disk management
— right click on system reserved partition and go to change drive letter and paths
— remove drive letter
-click ok and close all windowscontrol panel — file explorer options — view tab
— select ‘Don’t Show hidden files, folders and drives’
— check ‘Hide Protected Operating System Files’
— click ok and close all windowsclose all windows and reboot server
after reboot windows updates worked for me-
Edited by
pusaabq
Thursday, August 15, 2019 9:10 PM
-
Edited by
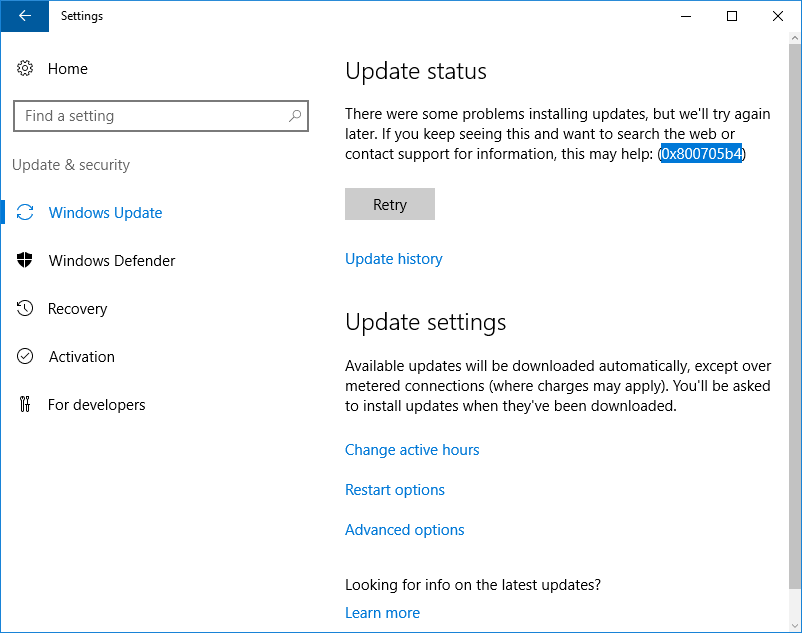
При обновлении Windows Server 2016 столкнулся с ошибкой 0x800705b4. Перепробовал несколько способов решения проблемы, один из них помог.
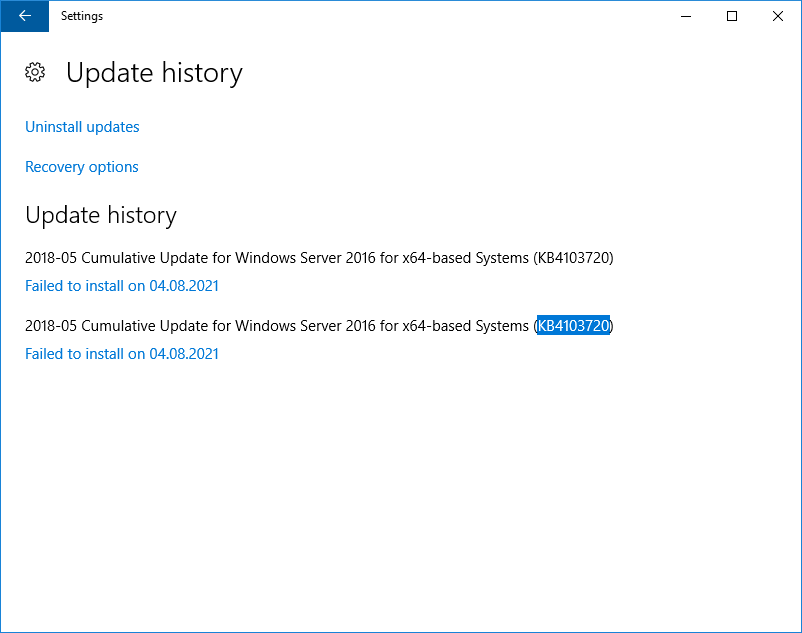
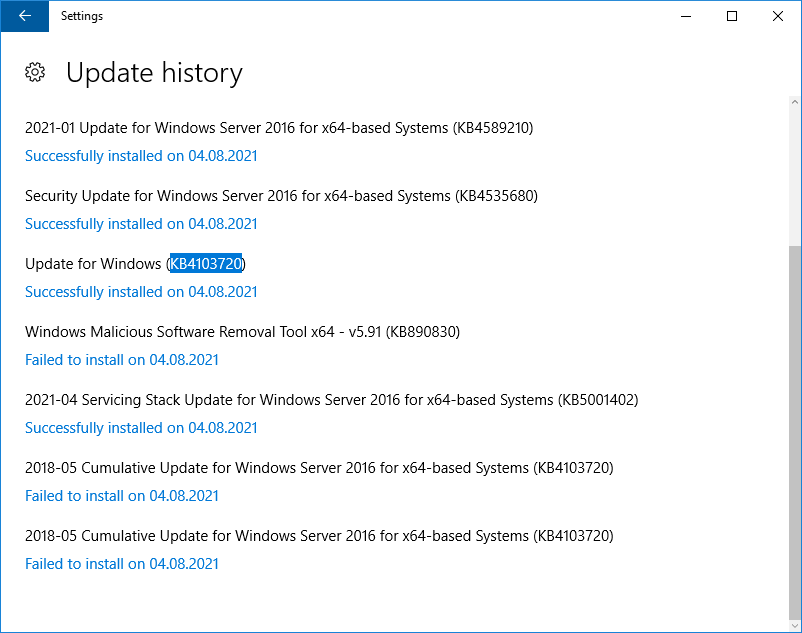
Если нажать кнопку Retry, то обновление снова завершается ошибкой. Накопительное обновление KB4103720 никак не хочет устанавливаться. Посмотреть какое обновление вызвало ошибку можно в журнале обновлений Update history.
Пошерстив Интернет, нашёл несколько советов, которые могут помочь в таком случае.
Аналогичная ошибка при установке обновлений:
- KB4103720
- KB4103723
Первый совет, который мне не помог
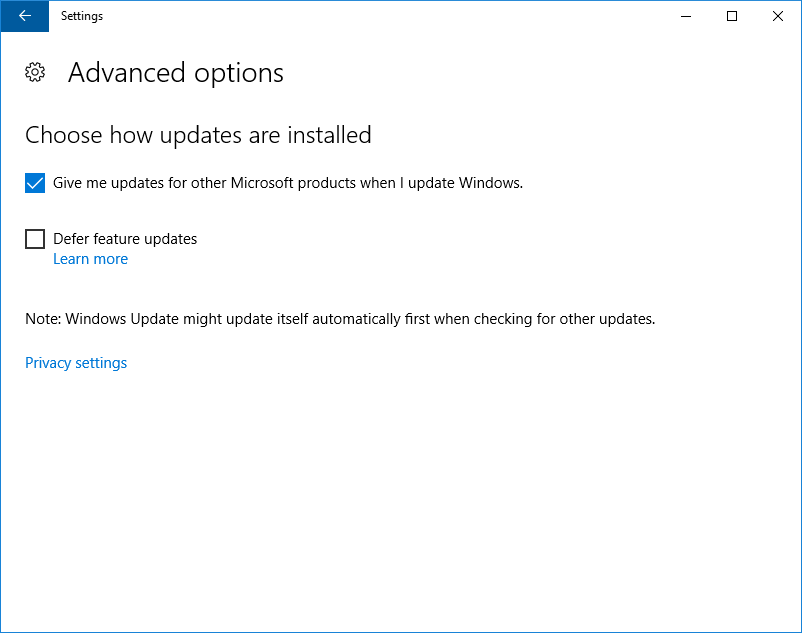
Установить опцию «При обновлении Windows получать обновления для других продуктов Майкрософт». Захожу в дополнительные настройки Advanced option и включаю «Give me updates for other Microsoft products when I update Windows».
Говорят, что обновление может не устанавливаться, если оно зависит от какого-то другого, необязательного обновления. Я, правда, в этом сомневаюсь.
Мне не помогло.
Второй совет, который мне не помог
Обновить вручную антивирус. Антивирусные базы должны обновляться автоматически, но из-за ошибки этого не происходит. Даже есть это не поможет, то хотя бы антивирус будет обновлён. Я в этом способе тоже сомневаюсь. Хотя, если у вас стоит какой-то другой антивирус, то он может мешать обновлениям, его можно попытаться отключить. У меня на сервере стоит только защитник Windows.
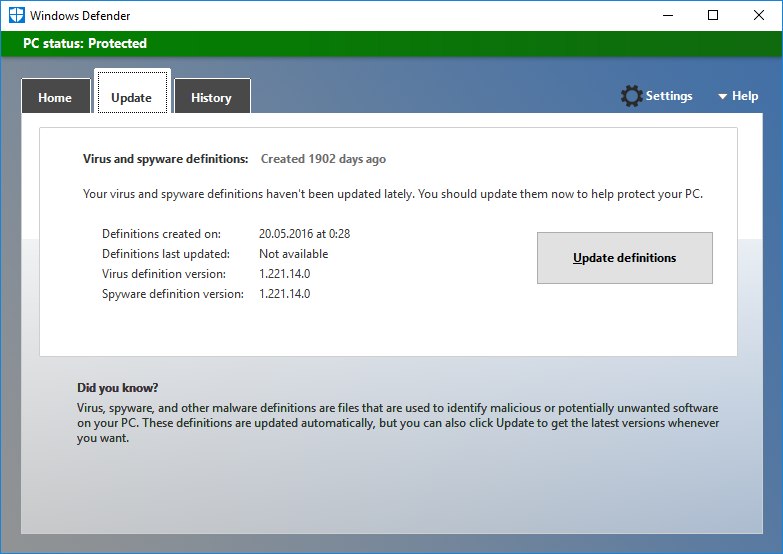
Запускаю Windows Defender. Да, базы не обновлены.
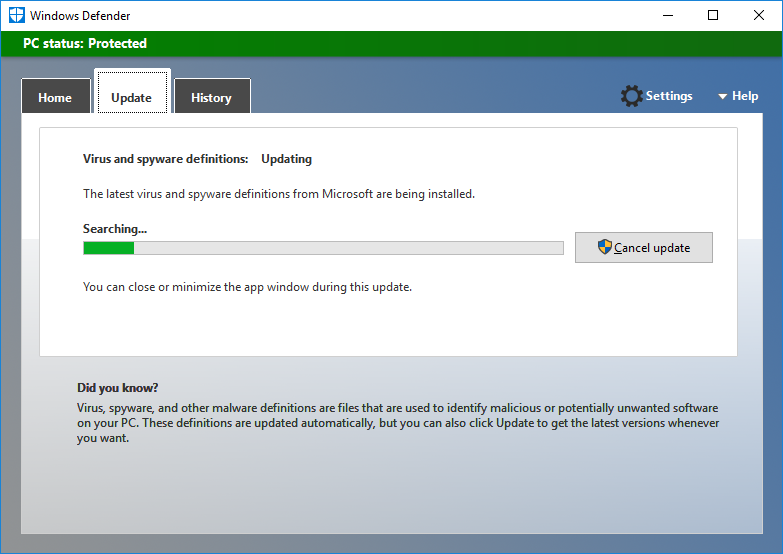
Нажимаю кнопку Update definitions.
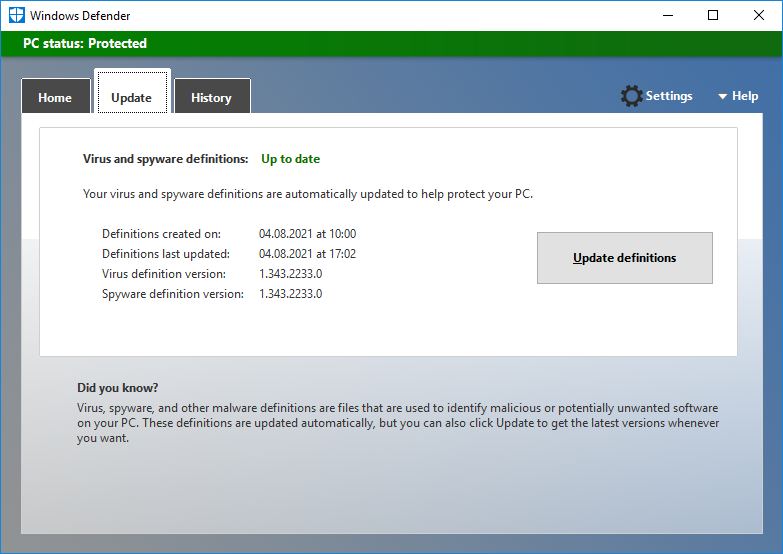
Антивирусные базы обновляются.
Мне не помогло.
Третий совет, который мне не помог
Если сервер находится в домене, то, возможно, обновление скачивается с WSUS. Оно может быть битым или вообще ненужным. Можно отключить обновление через WSUS, чтобы сервер скачал патч напрямую из Microsoft.
Я уже пользовался этим способом при ошибке 0x80244011.
Windows Server 2016 — отключаем обновление через WSUS
Мне не помогло.
Четвёртый совет, который мне не помог
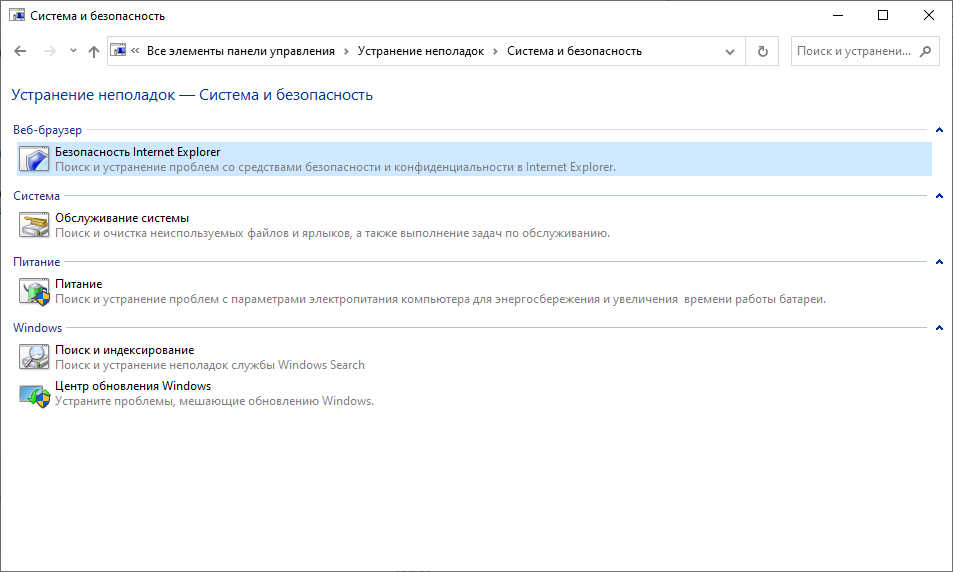
Через панель управления устраняем неполадки с центром обновления Windows.
Панель управления → Устранение неполадок → Система и безопасность → Центр обновления Windows.
Начинается поиск проблем, мешающим обновлению.
Найдена какая-то проблема и исправлена. Замечательно, но…
Мне не помогло.
Пятый совет, который мне не помог
Все обновления перед установкой скачиваются в директорию SoftwareDistribution. А подписи обновлений хранятся в папке catroot2. Эти папки можно почистить или удалить, но придётся остановить несколько служб.
Я воспользовался скриптом для командной строки:
Net Stop bits
Net Stop wuauserv
Net Stop appidsvc
Net Stop cryptsvc
Ren %systemroot%\SoftwareDistribution SoftwareDistribution.bak
Ren %systemroot%\system32\catroot2 catroot2.bak
Net Start bits
Net Start wuauserv
Net Start appidsvc
Net Start cryptsvcСкрипт останавливает несколько сервисов м переименовывает папки SoftwareDistribution и catroot2. Потом снова запускает остановленные службы.
Мне не помогло.
Шестой совет, который мне помог
Проблемное обновление можно скачать из каталога Windows и установить вручную.
https://www.catalog.update.microsoft.com/Home.aspx
Нахожу в каталоге проблемное накопительное обновление KB4103720 для Windows Server 2016. Скачиваю и запускаю.
Обновление успешно устанавливается.
После этого перезагружаю сервер и устанавливаю остальные обновления в обычном режиме.
Вместо заключения
Что-то мне подсказывает, что проблемы с установкой обновлений у всех могут быть разные. Если один из способов не помог, попробуйте другой.
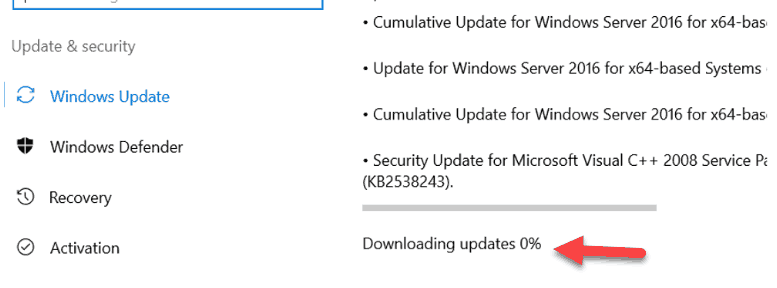
Sometimes the Windows update is a nightmare, especially on the business/work network. If you have direct internet without any proxy or WSUS servers, it is going to work without any issues most of the time. That is how it works on personal computers at home. But when there is a complicated setup in place with the different versions of servers, multiple Internet gateways, and proxy servers, then you will face random issues with Windows update. Recently I had a problem with Windows 2016 server where the Windows update stuck at 0% and did not move further.
In my case, it detected the available updates, but when it started downloading, it stuck at 0%. I thought that something was wrong with the Internet connectivity, but the Internet browsing worked fine on the same server. After finding several solutions online, only one worked for me. In this post, I’m going to share how to fix the Windows update stuck at 0% issue on Windows 2016 server. By the way, it is a virtual machine running on Hyper-V.
The below steps are applicable for Windows 2019 and 2022 server Operating Systems also if you face similar issues.
Let me add the solution first which worked for me after trying several steps. If this doesn’t work for you or your scenario is different, then proceed to other steps.
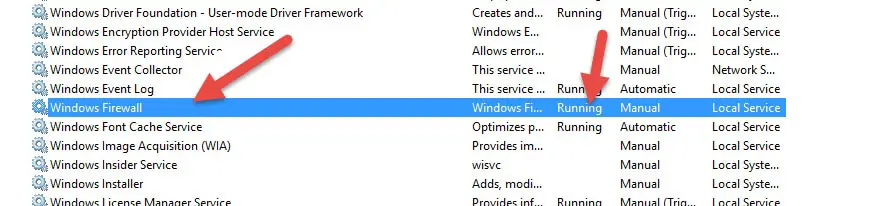
1) Check the Windows Firewall Service/status
In Windows 2016 (or 2019/2022 servers), the Windows firewall should be on and active to make Microsoft Updates work. In my case, I disabled the Windows firewall for some other purpose earlier. So, the update stuck at 0% without any progress.
Visit the Services under server manager, make sure that the Windows firewall service is running.
Once I started the service, the Windows update started downloading automatically.
If this step doesn’t fix the issue, go to the next steps.
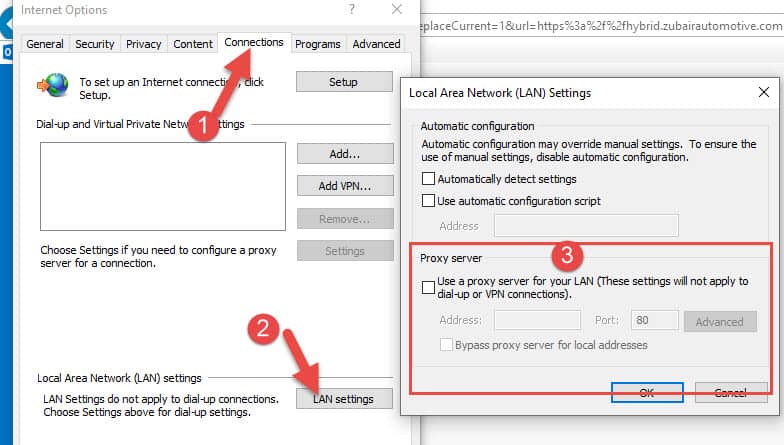
2) Check the Internet Proxy Settings
In most cases, Windows update can’t download the packages via the web proxy (though it depends on the authentication and security policy of the web proxy).
Check and confirm that there is no proxy setup on the web browser.
You should remove the proxy settings and provide direct internet to Windows servers to download Windows updates.
You can check the current and active proxy settings in the command prompt by the below input.
netsh winhttp show proxy3) Clean the Update Catalog Folder
There could be a reason that Windows update content folder/file/catalog is corrupted so the download is stuck at 0%. Cleaning up the folder may help to resume Windows updates successfully.
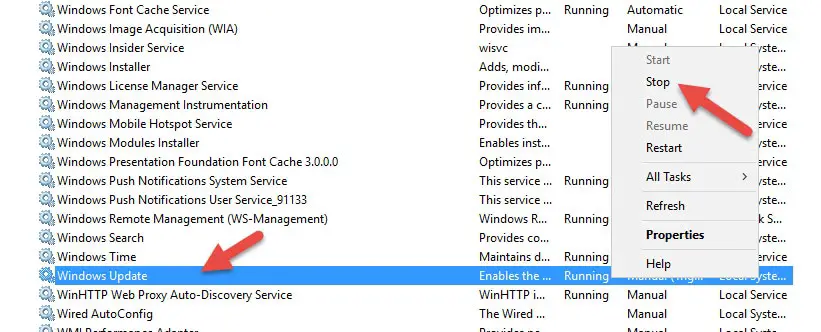
We need to stop the service before doing the cleanup,
Go to the Services and locate the Windows update service. Stop the service.
Once the service stopped successfully, navigate to the following folder location and delete all content (files and folders).
C:\Windows\SoftwareDistribution
This is the place where Windows OS downloads the updates. Cleaning up these files/folders and starting the service may help.
After deleting the files, start the same Windows Update service you stopped initially. This will restart the update service and download the updates that stuck at 0% on Windows 2016/2019 server earlier.
I tried steps 2 and 3 first, but it did not help in my case. My server never had a proxy server for Internet access. Deleting the content from the particular location and restarting the Windows Update service did not help either. Enabling the Windows firewall worked for me in the end. You can try these steps and share the outcome on which method helped to download the Windows updates from Windows 2016/2019 servers that stuck at 0%.
В Windows Server 2016 можно столкнуться с ситуацией, когда встроенный клиент Windows Update очень долго выполняет проверку обновлений. Характерно то, что проблема может проявляться плавающим образом и воспроизводиться не всегда. Замечено, что чаще всего проблема проявляется в случае, если система была недавно включена или перезагружена. В этой заметке мы поговорим о том, какие могут быть причины у такого поведения и как это можно попробовать исправить.
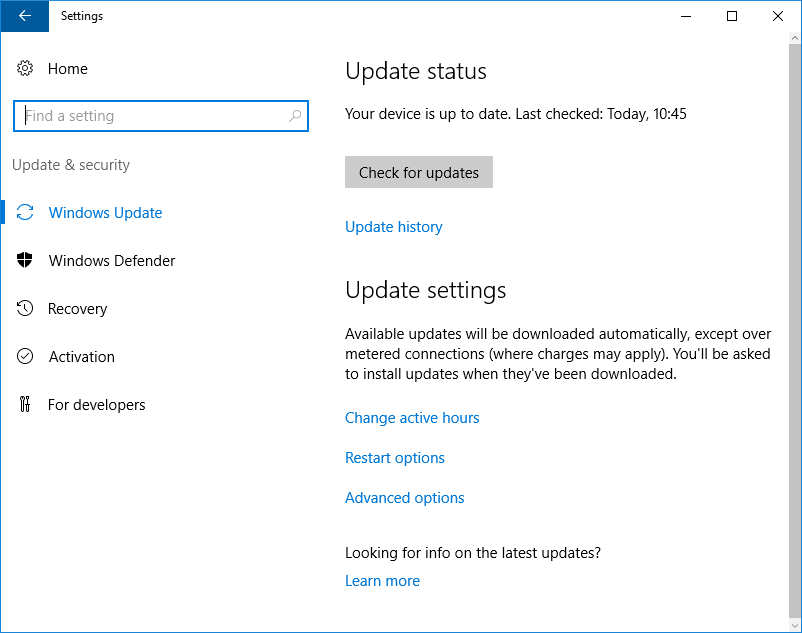
При попытке вызвать проверку обновлений из интерфейса настроек системы в Settings > Update & security > Windows Update мы можем столкнуться с длительным циклом ожидания в статусе «Checking for updates…»
Результатом такого ожидания может стать возникновение ошибки типа:
We couldn't connect to the update service. We'll try again later, or you can check now. If it still doesn't work, make sure you're connected to the Internet.
Это привносит проблемы и в других операциях обслуживания системы.
Отражение проблемы с Windows Update в Failover Cluster Manager
В качестве примера отрицательного влияния проблемной работы Windows Update можно привести мастер проверки конфигурации кластера, вызываемый из оснастки Failover Cluster Manager. В ходе выполнения валидации кластера, на этапе сбора информации об установленных на кластерных узлах обновлениях («List Software Updates«) мы можем получить состояние длительного ожидания.
В ходе изучения ситуации по следам «коллективного разума» я обнаружил, что самые разнообразные проблемы c Windows Update в Windows Server 2016 известны давно и с ними столкнулись многие:
- TechNet Forums : Windows Server 2016 Updates slow!
- Superuser : Windows Update stuck on Checking for updates
- Born’s Tech and Windows World : Windows Server 2016: Slow updates
Методом «а если попробовать…» было выявлено, что в качестве обходного решения в вышеописанной ситуации с Failover Cluster Manager, может быть простой перезапуск службы «Windows Update«.
Возможно, потребуется сделать лишь остановку этой службы, а запустится служба через несколько секунд автоматически. Если служба не остановилась с первого раза (остановка привела к ошибке), то пробуем выполнить остановку повторно. Выполнить остановку службы можно как через оснастку управления службами services.msc, так и через PowerShell.
Stop-Service "Windows Update"
Сразу после того, как служба будет остановлена (а затем сама автоматически запустится) мы увидим сдвиг в работе механизма проверки обновлений.
В случае с кластером, выполнить остановку/перезапуск службы «Windows Update» нам может потребоваться на всех узлах кластера, начиная с того, на котором запущен мастер проверки.
В попытках понять, что же не так с проверкой обновлений в Windows Server 2016 и проведения ряда экспериментов с видимыми настройками клиента Windows Update в графической среде, стало очевидно то, что наличие включённой опции «Defer feature updates» в Settings > Update & security > Windows Update > Advanced options явным образом влияет на воспроизведение проблемы.
То есть, как только мы отключаем данную опцию, включенную в Windows Server 2016 по умолчанию, то механизм проверки обновлений начинает работать так, как мы этого от него ожидаем при наличии сервера WSUS.
Дальнейшее изучение вопроса показало, что причиной странного поведения клиента Windows Update может являться механизм «Dual Scan» (подробней в статьях «Improving Dual Scan on 1607» и «Demystifying Dual Scan»), который заставляет при проверке обновлений в качестве источника использовать не только форсировано настроенный в доменных групповых политиках сервер WSUS в локальной сети, но и Интернет-службы Windows Update.
Соответственно, при условии, что компьютеры имеют ограниченный доступ в Интернет или не имеют его вовсе, может возникнуть эффект длительного ожидания с возникновением ошибок разного содержания.
Чтобы решить описанную проблему, нам потребуется провести настройку групповой политики Active Directory, с помощью которой настраиваются наши серверы на базе Windows Server 2016. Однако, как выяснилось, в этом вопросе всё не так очевидно, понятно и однозначно, как хотелось бы.
Варианты решения с готовыми политиками GPO (неработающие в нашем случае)
Примечание: Если важен только готовый рецепт и не интересны эксперименты по следам ранее предложенных в Интернете приёмов(которые в нашем случае не помогли), то можете смело пропустить этот раздел заметки и читать заключительный раздел.
В ранних выпусках Windows 10 (с версии 1607) и Windows Server 2016 за отключение попыток использования онлайн репозитория Windows Update отвечала политика:
«Do not allow update deferral policies to cause scans against Windows Update«
в разделе:
Computer Configuration > Administrative Templates > Windows Components > Windows Update.
В результате применения этой политики в системном реестре Windows появляется параметр DisableDualScan, установленный в 1:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate]
"DisableDualScan"=dword:00000001
И, судя по старым статьям, на более ранних версиях Windows 10 описанная политика могла быть полезна для решения проблемы.
Однако, в более поздних версиях Windows 10 (начиная с версии 2004), Windows 11, а так же, возможно, в более новых версиях Windows Server, данная политика была перенесена в подраздел Legacy Policies и была заменена новой политикой:
«Specify source service for specific classes of Windows Updates«
в разделе:
Computer Configuration > Administrative Templates > Windows Components > Windows Update > Manage updates offered from Windows Server Update Service.
Предполагается включение этой политики и выбор WSUS в качестве источника для всех предлагаемых типов обновлений.
В результате применения этой политики в системном реестре Windows появляется 4 параметра с соответствующими именами, установленных в 1:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate]
"SetPolicyDrivenUpdateSourceForFeatureUpdates"=dword:00000001
"SetPolicyDrivenUpdateSourceForQualityUpdates"=dword:00000001
"SetPolicyDrivenUpdateSourceForDriverUpdates"=dword:00000001
"SetPolicyDrivenUpdateSourceForOtherUpdates"=dword:00000001
Логично предполагать, что включать и настраивать данную политику резонно лишь для серверных систем, которые в локальных сетях, как правило, обновляются с сервера WSUS и имеют ограниченный доступ в Интернет. Для клиентских же систем, часть из которых может оказаться мобильными и периодически перемещающимися из локальной сети во внешние сети с доступом в Интернет, в некоторых ситуациях может оказаться логичней использовать настроенный по умолчанию механизм выбора источника (то есть, чтобы в качестве дополнительного источника мог выступать онлайн репозиторий Windows Update).
Эксперименты с двумя выше описанными политиками показали, что на данный момент времени сами по себе (ни по отдельности ни вместе) эти политики не решают проблему в нашем конкретном случае.
В ходе дальнейшего изучения опыта борьбы коллег со странностями работы Windows Update в Windows Server 2016 обнаружил статью «Windows admin blog : Некорректное отображение информации на WSUS | Проблемы обновления со WSUS (Dual Scan)», где в качестве одного из решений предложено включение «олдскульной» политики:
«Do not connect to any Windows Update Internet locations«
в разделе:
Computer Configuration > Administrative Templates > Windows Components > Windows Update > Manage updates offered from Windows Server Update Service.
В результате применения этой политики в системном реестре Windows появляется параметр DoNotConnectToWindowsUpdateInternetLocations, установленный в 1:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate]
"DoNotConnectToWindowsUpdateInternetLocations"=dword:00000001
Однако, практика показала, что применение данной политики может привести к появлению новой ошибки в ходе проверки обновлений:
There were some problems installing updates, but we'll try again later. If you keep seeing this and want to search the web or contact support for information, this may help: (0x8024500c)
Причём избавиться от этой ошибки не поможет ни перезапуск службы, ни перезагрузка системы, а по свидетельствам очевидцев, эта ошибка воспроизводится так же и на Windows 10.
Понимая то, что данная политика не решает проблемы, можно было бы не упоминать о ней в нашей заметке. Однако помимо того, что она не только не закрывает исходную проблему, но и может создать новую трудно интерпретируемую проблему, мы и упоминаем здесь о ней, как о неподходящем варианте решения.
Перебрав ряд других групповых политик, как по одиночке, так и в в разных комбинациях, мне так и не удалось найти решения на базе каких-либо готовых политик.
Отключение опции «Defer feature updates» с помощью GPP
В конечном итоге пришлось прибегнуть к помощи Group Policy Preferences (GPP) для управления опцией «Defer feature updates«, отображаемой в графической оболочке Windows Server 2016.
Отключение данной опции приводит к следующему изменению в системном реестре:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsUpdate\UX\Settings]
"DeferUpgrade"=dword:00000000
Соответственно, для настройки серверов с Windows Server 2016 на явное отключение данной опции мы можем создать в доменной групповой политике, применяемой к серверам, объект GPP, настраивающий параметр реестра DeferUpgrade.
С помощью Item-level targeting можем указать то, что данный параметр реестра будет обновляться только на системах семейства Windows Server 2016.
Для оперативной проверки результата выполняем на конечном сервере обновление групповых политик и инициируем процедуру проверки обновлений:
gpupdate /force
UsoClient.exe startscan
Убедимся в том, что после применения GPO в реестре на серверных системах с Windows Server 2016 применились изменения и в графической консоли настроек системы опция «Defer feature updates» отображается в выключенном состоянии.
Все последующие проверки обновлений Windows теперь должны начать работать напрямую с WSUS без длительных попыток обращения к Интернет-службам Windows Update.