Search code, repositories, users, issues, pull requests…
Provide feedback
Saved searches
Use saved searches to filter your results more quickly
Sign up
| Operating Systems |
Windows 2008 R2 and 7
Windows 2012 R2 and 8.1 Windows 2016 and 10 Windows Server 2019 and 2022 |
|
Category • Subcategory |
Logon/Logoff • Logon |
| Type | Failure |
|
Corresponding events in Windows 2003 and before |
529 , 530 , 531 , 532 , 533 , 534 , 535 , 536 , 537 , 539
|
4625: An account failed to log on
On this page
- Description of this event
- Field level details
- Examples
- Discuss this event
- Mini-seminars on this event
This is a useful event because it documents each and every failed attempt to logon to the local computer regardless of logon type, location of the user or type of account.
Free Security Log Resources by Randy
- Free Security Log Quick Reference Chart
- Windows Event Collection: Supercharger Free Edtion
- Free Active Directory Change Auditing Solution
- Free Course: Security Log Secrets
Description Fields in
4625
Subject:
Identifies the account that requested the logon — NOT the user who just attempted logged on. Subject is usually Null or one of the Service principals and not usually useful information. See New Logon for who just logged on to the system.
- Security ID
- Account Name
- Account Domain
- Logon ID
Logon Type:
This is a valuable piece of information as it tells you HOW the user just logged on: See 4624 for a table of logon type codes.
Account For Which Logon Failed:
This identifies the user that attempted to logon and failed.
- Security ID: The SID of the account that attempted to logon. This blank or NULL SID if a valid account was not identified — such as where the username specified does not correspond to a valid account logon name.
- Account Name: The account logon name specified in the logon attempt.
- Account Domain: The domain or — in the case of local accounts — computer name.
Failure Information:
The section explains why the logon failed.
- Failure Reason: textual explanation of logon failure.
- Status and Sub Status: Hexadecimal codes explaining the logon failure reason. Sometimes Sub Status is filled in and sometimes not. Below are the codes we have observed.
| Status and Sub Status Codes | Description (not checked against «Failure Reason:») |
| 0xC0000064 | user name does not exist |
| 0xC000006A | user name is correct but the password is wrong |
| 0xC0000234 | user is currently locked out |
| 0xC0000072 | account is currently disabled |
| 0xC000006F | user tried to logon outside his day of week or time of day restrictions |
| 0xC0000070 | workstation restriction, or Authentication Policy Silo violation (look for event ID 4820 on domain controller) |
| 0xC0000193 | account expiration |
| 0xC0000071 | expired password |
| 0xC0000133 | clocks between DC and other computer too far out of sync |
| 0xC0000224 | user is required to change password at next logon |
| 0xC0000225 | evidently a bug in Windows and not a risk |
| 0xc000015b | The user has not been granted the requested logon type (aka logon right) at this machine |
Process Information:
- Caller Process ID: The process ID specified when the executable started as logged in 4688.
- Caller Process Name: Identifies the program executable that processed the logon. This is one of the trusted logon processes identified by 4611.
Network Information:
This section identifies where the user was when he logged on. Of course if logon is initiated from the same computer this information will either be blank or reflect the same local computers.
- Workstation Name: The computer name of the computer where the user is physically present in most cases unless this logon was initiated by a server application acting on behalf of the user. Workstation may also not be filled in for some Kerberos logons since the Kerberos protocol doesn’t really care about the computer account in the case of user logons and therefore lacks any field for carrying workstation name in the ticket request message.
- Source Network Address: The IP address of the computer where the user is physically present in most cases unless this logon was initiated by a server application acting on behalf of the user. If this logon is initiated locally the IP address will sometimes be 127.0.0.1 instead of the local computer’s actual IP address. This field is also blank sometimes because Microsoft says «Not every code path in Windows Server 2003 is instrumented for IP address, so it’s not always filled out.»
- Source Port: Identifies the source TCP port of the logon request which seems useless since with most protocols’ source ports are random.
Detailed Authentication Information:
- Logon Process: (see 4611)
- Authentication Package: (see 4610 or 4622)
- Transited Services: This has to do with server applications that need to accept some other type of authentication from the client and then transition to Kerberos for accessing other resources on behalf of the client. See http://msdn.microsoft.com/msdnmag/issues/03/04/SecurityBriefs/
- Package name: If this logon was authenticated via the NTLM protocol (instead of Kerberos for instance) this field tells you which version of NTLM was used. See security option «Network security: LAN Manager authentication level»
- Key Length: Length of key protecting the «secure channel». See security option «Domain Member: Require strong (Windows 2000 or later) session key». If value is 0 this would indicate security option «Domain Member: Digitally encrypt secure channel data (when possible)» failed
Supercharger Free Edition
Your entire Windows Event Collection environment on a single pane of glass.
Free.
Examples of 4625
An account failed to log on.
Subject:
Security ID: NULL SID
Account Name: —
Account Domain: —
Logon ID: 0x0
Logon Type: 3
Account For Which Logon Failed:
Security ID: NULL SID
Account Name: asdf
Account Domain:
Failure Information:
Failure Reason: Unknown user name or bad password.
Status: 0xc000006d
Sub Status: 0xc0000064
Process Information:
Caller Process ID: 0x0
Caller Process Name: —
Network Information:
Workstation Name: WIN-R9H529RIO4Y
Source Network Address: 10.42.42.201
Source Port: 53176
Detailed Authentication Information:
Logon Process: NtLmSsp
Authentication Package: NTLM
Transited Services: —
Package Name (NTLM only): —
Key Length: 0
This event is generated when a logon request fails. It is generated on the computer where access was attempted.
The Subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The Logon Type field indicates the kind of logon that was requested. The most common types are 2 (interactive) and 3 (network).
The Process Information fields indicate which account and process on the system requested the logon.
The Network Information fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The authentication information fields provide detailed information about this specific logon request.
- Transited services indicate which intermediate services have participated in this logon request.
- Package name indicates which sub-protocol was used among the NTLM protocols
- Key length indicates the length of the generated session key. This will be 0 if no session key was requested
Top 10 Windows Security Events to Monitor
Free Tool for Windows Event Collection
- How to Detect 2 Computers on Your Network Talking to Each Other for the First Time and Why It Matters
- Top 5 Ways for Analyzing Entitlements and Identifying High-Risk
- Top 12 Events to Monitor in the Windows Server Security Log
- How to Analyze Logon Attacks with the Windows Security Logs
- Anatomy of an Attack: How Password Spraying Exploits Weak Passwords So Effectively
- Correlating DHCP, DNS and Active Directory data with Network Logs for User Attribution
- 4 Threat Detections using Active Directory Authentication Events from the Windows Security Log
- Dabble or Deep Dive: 7 Different Threat Hunts You Can Do With Available Resources
- Auditing Active Directory Changes with the Windows Security Log
- Using Honeypot Accounts and Hashes in Active Directory to Detect Pass-the-Hash & Credential Theft
- Top 10 Event Categories to Monitor in the Windows Server Event Log
- Security Log Deep Dive: Mapping Active Directory Authentication and Account Management Events to MITRE ATT&CK TTPs
- Understanding Logon Events in the Windows Server 2022 Security Log
- Top 6 Security Events You Only Detect by Monitoring Workstation Security Logs
- Remove From My Forums
-
Question
-
Windows 2008 R2 server has over 3000 audit failures in the last hour with the following description. Any help would be appreciated.
An account failed to log on.
Subject:
Security
ID:
SYSTEM
Account
Name:
PHS-AERO$
Account
Domain:
PUSD
Logon
ID:
0x3e7Logon Type:
8Account For Which Logon Failed:
Security
ID:
NULL SID
Account
Name:
Administrator
Account
Domain:
PUSD.localFailure Information:
Failure
Reason:
Unknown user name or bad password.
Status:
0xc000006d
Sub
Status:
0xc000006aProcess Information:
Caller
Process ID:
0x4b4
Caller
Process Name:
C:\Windows\System32\svchost.exeNetwork Information:
Workstation
Name:
PHS-AERO
Source
Network Address:
—
Source
Port:
—Detailed Authentication Information:
Logon
Process:
Advapi
Authentication
Package:
Negotiate
Transited
Services:
—
Package
Name (NTLM only):
—
Key
Length:
0This event is generated when a logon request fails. It is generated on the computer where access was attempted.
The Subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The Logon Type field indicates the kind of logon that was requested. The most common types are 2 (interactive) and 3 (network).
The Process Information fields indicate which account and process on the system requested the logon.
The Network Information fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The authentication information fields provide detailed information about this specific logon request.
—
Transited services indicate which intermediate services have participated in this logon request.
—
Package name indicates which sub-protocol was used among the NTLM protocols.
—
Key length indicates the length of the generated session key. This will be 0 if no session key was requested.
Answers
-
looks like you have either deleted the computer account for machine PHS-AERO.
or the machine has corrupted its «secure-channel» with the DC — meaning the machine’s password that the computer is trying to use against the DC is diffrent from the password (hash) that is stored on the DC in question. This can happen either by some corruption
of the local computer registry on the PHS-AERO machine, or maybe AD restore. Or the most probable reason is that the machine PHS-AERO has just changed its computer password (happens every 30 days) on a different DC and the change has not yet replicated to
the DC with the errors.You can check the machine’s PHS-AERO health by using:
NLTEST /SC_VERIFY:domain-name
and if the result is SUCCESS, you can also try NLTEST /SC_RESET:domain-name several times to see what happens. The SC_RESET command forces the machine to select a new DC to authneticate against and you should see a random switching between your DCs. This
should go smoothly when you reset several times. If the problem was only temporary due to the replication latency, you should not see any further errors on the machine nor on any DC.ondrej.
-
Marked as answer by
Wednesday, February 29, 2012 2:46 AM
-
Marked as answer by
What is Event ID 4625: An Account Failed to Log On. Are you seeing a lot of event ID 4625 (An account failed to log on) in your Domain Controller’s Security logs and unsure what it means or how to resolve it? Well, in this article, we explains everything you need to know about this Active Directory security event log and how to fix the issue that triggers it.

First, we discuss the causes and various properties of Event ID 4625. This security event log provides information about the type of logon attempt, user account information, logon process, failure reason, client address, and event status and sub-status codes.
Next, we explain how to interpret these properties and use them to determine the root cause of the error that triggered the event log. This involves checking the username and password, account status, group membership, network connectivity, and related security events.
Once you have identified the problem, we also provide some general steps to fix event ID 4625. This may involve resetting passwords, re-enabling disabled accounts, adjusting group policies, troubleshooting network connectivity, or scanning for malware.
So, if you’re seeing a lot of event ID 4625 in your Domain Controller Security logs and want to fix the issue, keep reading to find out how!
Potential Causes of Event ID 4625: An Account Failed to Log On
The first step to troubleshooting and fixing the cause of event ID 4625 is to understand the possible things that could stop a user, service, or computer account from failing to log on. Here are the top reasons that may generate event ID 4625:
- Incorrect username or password: if a user enters a wrong password, the account cannot log in. This makes the computer the user attempt to sign in to log event ID 4625.
Moreover, if the password in a service account is wrong, it fails when the service account tries to authenticate to AD, and the Domain Controller also registers this event log.
- The user account has expired: when an admin creates an AD account, they set it to expire at a specified date.
If an Active Directory user attempts to use an expired account to sign in to AD, the user is denied access. Then, the Domain Controller logs an event ID 4625.
- The account that attempted login has been disabled.
- The user is restricted from logging in to a computer: did you know that as an admin, you use group policy to prevent a user or group from logging in to a computer?
This is done using the “Deny log on locally” policy. If this policy is applied to a user and they try to log in to the computer, they are denied access.
When this happens, the computer registers event ID 4625 in its local Security event log when a user is denied access due to the policy.
Understanding the Properties of Event ID 4625: An Account Failed to Log On
When this event is logged in the Security event log, it typically includes information about the user account that failed to log on, the type of login attempt, and the reason for the failure. This information helps troubleshoot the issue and determines the appropriate action to fix the problem.
However, to use the information in the event log, you need to understand the relevant properties of the event ID and what they mean.
Note that this event has numerous properties, but we discuss the properties you must learn to fix why an account failed to log on to the domain.
Event ID 4625 Logon Type

The event type is your starting point to determine why AD denied a user or service login access (more on how to use this information in the next section).
Get the event Logon Type by looking into the details of the event log.
Unfortunately, as shown in the highlighted portion of the screenshot above, the Windows Event log records Logon Types as a numerical value. So, for this information to be useful for troubleshooting, you must figure out what the numbers mean.
Fortunately, Microsoft has a page for this event log – 4625(F): An account failed to log on – that explains the logon types and their meaning.
For example, my screen above shows that Logon Type 5 triggered the event ID 4625. From the Microsoft page, this means a service account initiated the logon that triggered the event.
Event ID 4625 User Account Information
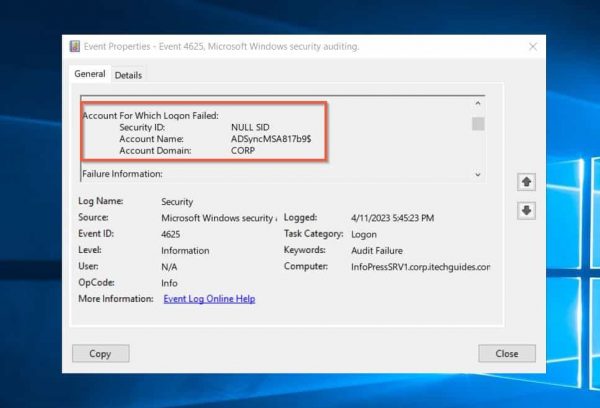
Once you have identified the Logon Type of the event that triggered the Event ID 4625, the next crucial information in the event log is the user information. Locate this information in the “Account For Which Logon Failed:” section of the event log.
In this section, you find 3 pieces of information, but the most important one is the Account Name. If you are managing a multi-domain AD Forest, it is also essential to take note of the Account Domain. By keeping track of these details, you are better equipped to troubleshoot failed logon attempts.
Try our Active Directory & Office 365 Reporting & Auditing Tools
Try us out for Free. 100’s of report templates available. Easily customise your own reports on AD, Azure AD & Office 355.
Event ID 4625 Failure Information

The Failure information property of event ID 4625 has 3 sub-properties: Failure Reason, Status Code, and Sub Status Code. While the “Failure Reason” gives you superficial information, for example, “Unknown user name or bad password,” the status code provides a specific reason for the failure.
This information is essential because “Unknown user name or bad password” may not necessarily mean the user entered an incorrect user name or password.
However, as shown in the highlighted part of the above screenshot, the status code is some code that you must interpret before using it. To learn about the status codes and their meaning, visit the event ID 4625 status codes link.
Based on Microsoft’s information in the previous link, the status code in my screenshot – 0xC000006D – means “The attempted logon is invalid. This is either due to a bad username or authentication information.”
This info is still ambiguous. For a more specific reason for the log-on failure, check the meaning of the event ID’s sub-status code.
Read about the sub status codes in the same link I provided earlier – event ID 4625 status codes. When I looked up the sub status code shown in my event 4625, it says “The specified account does not exist.”
Much better!
There we have my answer, the account the user attempted to log in with does not exist in Active Directory.
How to Troubleshoot and Fix Event ID 4625
To address the issue, you need to take a systematic approach to troubleshoot the root cause of the failed logon attempts.
Follow the general guidelines below to troubleshoot and fix the event ID 4625: An Account Failed to Log On.
Step 1: Review the Information in the Event Log
By following the 3 steps I discussed in the last section, get the following information from the event log:
Logon Type, The Account For Which Logon Failed, Failure Reason, Status, and Sub Status codes and their meaning.
In my case, we record the following:
Logon Type: 5 – a service account initiated the logon that triggered the event.
The Account For Which Logon Failed: ADSyncMSA817b9$
Failure Reason: Unknown user name or bad password.
Status and Meaning: 0xC000006D – The attempted logon is invalid. This is either due to a bad username or authentication information.
Sub Status and Meaning: 0xC0000064 – The specified account does not exist.
Step 2: Take Appropriate Steps to Resolve the Cause of Event ID 4625
Now that you have identified the account that caused the DC to record Event ID 4625, it’s time to take action and resolve the issue. For instance, in the case where a service account such as ADSyncMSA817b9$ is attempting to authenticate to the AD domain but the account does not exist, there are several steps to fix the problem.
Firstly, identify the service that uses this account and then create the missing account in the AD. Once you have created the account, enter the necessary details in the application that is making the authentication request. This allows the service to authenticate to the AD domain without issues.
General Guidelines to Fixing Event ID 4625
Here are some specific situations that could trigger Event ID 4625, along with some recommended actions to fix the problem:
1. Event log 4625 indicates that the failed logon attempt was due to an incorrect username or password: you should double-check the username used for logging on. If the username is correct, try resetting the user’s password and attempting to log in again.

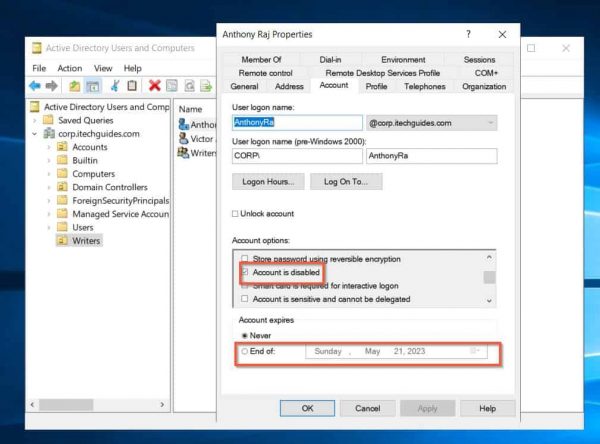
2. The event log indicates that the user account is disabled or expired: check the account status in Active Directory Users and Computers or use another suitable AD tool. If the account is disabled, re-enable it.
If the account is expired, extend the expiration date or create a new account for the user.
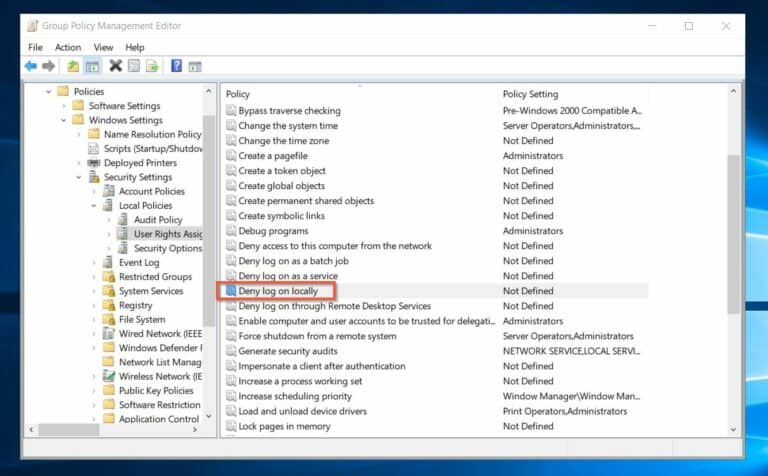
3. Event log 4625 shows that the user is not permitted to logon into a computer: firstly, remove them from that group.
Alternatively, adjust the group policy to allow login access to the group.
4. The event log indicates that the failed logon attempt was due to network connectivity issues: Troubleshoot any network connectivity issues (firewalls or network routing problems).
5. Check the event logs for related events, such as authentication failures or security events, that might provide additional information about the failed logon attempt.
6. If there are multiple failed logon attempts from the same user account, it could be a sign of a hacking attempt or malware infection. Perform a full malware scan and investigate further.
What is Event ID 4625: An Account Failed to Log On Conclusion
In general, fixing Event ID 4625 requires careful analysis of the information provided in the event log and a systematic approach to troubleshooting the issue. Following the steps discussed in this article, you should be able to successfully troubleshoot and fix event ID “4625: An Account Failed to Log On” event log issues.
By doing so, you improve the security of your Active Directory infrastructure and prevent further failed logon attempts.
Try InfraSOS for FREE
Invite your team and explore InfraSOS features for free
-
Free 15-Days Trial - SaaS Reporting & Auditing Solution
- Full Access to All Features
Время на прочтение
4 мин
Количество просмотров 262K
Рэнди Франклин Смит (CISA, SSCP, Security MVP) имеет в своем арсенале очень полезный документ, рассказывающий о том, какие события (event IDs) обязательно должны отслеживаться в рамках обеспечения информационной безопасности Windows. В этом документе изложена крайне полезная информация, которая позволит Вам “выжать” максимум из штатной системы аудита. Мы подготовили перевод этого материала. Заинтересованных приглашаем под кат.
О том, как настроить аудит, мы уже обстоятельно писали в одном из наших постов. Но из всех event id, которые встречаются в журналах событий, необходимо остановить свое внимание на нескольких критических важных. На каких именно – решать каждому. Однако Рэнди Франклин Смит предлагает сосредоточить внимание на 10 важных событиях безопасности в Windows.
Контроллеры доменов
Event ID — (Категория) — Описание
1) 675 или 4771
(Аудит событий входа в систему)
Событие 675/4771 на контроллере домена указывает на неудачную попытку войти через Kerberos на рабочей станции с доменной учетной записью. Обычно причиной этого является несоответствующий пароль, но код ошибки указывает, почему именно аутентификация была неудачной. Таблица кодов ошибок Kerberos приведена ниже.
2) 676, или Failed 672 или 4768
(Аудит событий входа в систему)
Событие 676/4768 логгируется для других типов неудачной аутентификации. Таблица кодов Kerberos приведена ниже.
ВНИМАНИЕ: В Windows 2003 Server событие отказа записывается как 672 вместо 676.
3) 681 или Failed 680 или 4776
(Аудит событий входа в систему)
Событие 681/4776 на контроллере домена указывает на неудачную попытку входа в систему через
NTLM с доменной учетной записью. Код ошибки указывает, почему именно аутентификация была неудачной.
Коды ошибок NTLM приведены ниже.
ВНИМАНИЕ: В Windows 2003 Server событие отказа записывается как 680 вместо 681.
4) 642 или 4738
(Аудит управления учетными записями)
Событие 642/4738 указывает на изменения в указанной учетной записи, такие как сброс пароля или активация деактивированной до этого учетной записи. Описание события уточняется в соответствие с типом изменения.
5) 632 или 4728; 636 или 4732; 660 или 4756
(Аудит управления учетными записями)
Все три события указывают на то, что указанный пользователь был добавлен в определенную группу. Обозначены Глобальная (Global), Локальная (Local) и Общая (Universal) соответственно для каждого ID.
6) 624 или 4720
(Аудит управления учетными записями)
Была создана новая учетная запись пользователя
7) 644 или 4740
(Аудит управления учетными записями)
Учетная запись указанного пользователя была заблокирована после нескольких попыток входа

(Аудит системных событий)
Указанный пользователь очистил журнал безопасности
Вход и выход из системы (Logon/Logoff)
Event Id — Описание
528 или 4624 — Успешный вход в систему
529 или 4625 — Отказ входа в систему – Неизвестное имя пользователя или неверный пароль
530 или 4625 Отказ входа в систему – Вход в систему не был осуществлен в течение обозначенного периода времени
531 или 4625 — Отказ входа в систему – Учетная запись временно деактивирована
532 или 4625 — Отказ входа в систему – Срок использования указанной учетной записи истек
533 или 4625 — Отказ входа в систему – Пользователю не разрешается осуществлять вход в систему на данном компьютере
534 или 4625 или 5461 — Отказ входа в систему – Пользователь не был разрешен запрашиваемый тип входа на данном компьютере
535 или 4625 — Отказ входа в систему – Срок действия пароля указанной учетной записи истек
539 или 4625 — Отказ входа в систему – Учетная запись заблокирована
540 или 4624 — Успешный сетевой вход в систему (Только Windows 2000, XP, 2003)
Типы входов в систему (Logon Types)
Тип входа в систему — Описание
2 — Интерактивный (вход с клавиатуры или экрана системы)
3 — Сетевой (например, подключение к общей папке на этом компьютере из любого места в сети или IIS вход — Никогда не заходил 528 на Windows Server 2000 и выше. См. событие 540)
4 — Пакет (batch) (например, запланированная задача)
5 — Служба (Запуск службы)
7 — Разблокировка (например, необслуживаемая рабочая станция с защищенным паролем скринсейвером)
8 — NetworkCleartext (Вход с полномочиями (credentials), отправленными в виде простого текст. Часто обозначает вход в IIS с “базовой аутентификацией”)
9 — NewCredentials
10 — RemoteInteractive (Терминальные службы, Удаленный рабочий стол или удаленный помощник)
11 — CachedInteractive (вход с кешированными доменными полномочиями, например, вход на рабочую станцию, которая находится не в сети)
Коды отказов Kerberos
Код ошибки — Причина
6 — Имя пользователя не существует
12 — Ограничение рабочей машины; ограничение времени входа в систему
18 — Учетная запись деактивирована, заблокирована или истек срок ее действия
23 — Истек срок действия пароля пользователя
24 — Предварительная аутентификация не удалась; обычно причиной является неверный пароль
32 — Истек срок действия заявки. Это нормальное событие, которое логгируется учетными записями компьютеров
37 — Время на рабочей машины давно не синхронизировалось со временем на контроллере домена
Коды ошибок NTLM
Код ошибки (десятичная система) — Код ошибки (16-ричная система) — Описание
3221225572 — C0000064 — Такого имени пользователя не существует
3221225578 — C000006A — Верное имя пользователя, но неверный пароль
3221226036 — C0000234 — Учетная запись пользователя заблокирована
3221225586 — C0000072 — Учетная запись деактивирована
3221225583 — C000006F — Пользователь пытается войти в систему вне обозначенного периода времени (рабочего времени)
3221225584 — C0000070 — Ограничение рабочей станции
3221225875 — C0000193 — Истек срок действия учетной записи
3221225585 — C0000071 — Истек срок действия пароля
3221226020 — C0000224 — Пользователь должен поменять пароль при следующем входе в систему
Еще раз продублируем ссылку на скачивание документа на сайте Рэнди Франклина Смита www.ultimatewindowssecurity.com/securitylog/quickref/Default.aspx. Нужно будет заполнить небольшую форму, чтобы получить к нему доступ.
P.S. Хотите полностью автоматизировать работу с журналами событий? Попробуйте новую версию NetWrix Event Log Manager 4.0, которая осуществляет сбор и архивирование журналов событий, строит отчеты и генерирует оповещения в режиме реального времени. Программа собирает данные с многочисленных компьютеров сети, предупреждает Вас о критических событиях и централизованно хранит данные обо всех событиях в сжатом формате для удобства анализа архивных данных журналов. Доступна бесплатная версия программы для 10 контроллеров доменов и 100 компьютеров.