This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Hello, Chris here from Directory Services support team with part 3 of the series.
With the November 2022 security update, some things were changed as to how the Kerberos Key Distribution Center (KDC) Service on the Domain Controller determines what encryption types are supported by the KDC and what encryption types are supported by default for users, computers, Group Managed Service Accounts (gMSA), and trust objects within the domain.
It is strongly recommended that you read the following article before going forward if you are not certain about Kerberos Encryption types are nor what is supported by the Windows Operating System:
Understanding Kerberos encryption types: https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/decrypting-the-selection-of-supported-kerberos-encryption-types/ba-p/1628797
Before we dive into what all has changed, note that there were some unexpected behaviors with the November update:
November out-of-band announcement: https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/november-2022-out-of-band-update-released-take-action/ba-p/3680144
Kerberos changes related to Encryption Type: https://support.microsoft.com/en-us/topic/kb5021131-how-to-manage-the-kerberos-protocol-changes-related-to-cve-2022-37966-fd837ac3-cdec-4e76-a6ec-86e67501407d
November out-of-band guidance: https://learn.microsoft.com/en-us/windows/release-health/windows-message-center#2961
After installing Windows Updates released on November 8, 2022 on Windows domain controllers, you might have issues with Kerberos authentication.
This specific failure is identified by the logging of Microsoft-Windows-Kerberos-Key-Distribution-Center Event ID 14 in the System event log of DC role computers with this unique signature in the event message text:
While processing an AS request for target service <service>, the account <account name> did not have a suitable key for generating a Kerberos ticket (the missing key has an ID of 1). The requested etypes : <etype numbers >. The accounts available etypes : <etype numbers>. Changing or resetting the password of <account name> will generate a proper key.
Where (a.) “the missing key has an ID 1” and (b.) «4» is not listed in the «requested etypes» or «account available etypes» fields.
You need to read the links above. If you are experiencing this signature above, Microsoft strongly recommends installing the November out of band patch (OOB) which mitigated this regression. The OOB should be installed on top of or in-place of the Nov 8 update on DC Role computers while paying attention to special install requirements for Windows Updates on pre-WS 2016 DCs running on the Monthly Rollup (MR) or SO (Security only) servicing branches.
Note that this out-of-band patch will not fix all issues. You should keep reading. If you tried to disable RC4 in your environment, you especially need to keep reading.
There was a change made to how the Kerberos Key Distribution Center (KDC) Service determines what encryption types are supported and what should be chosen when a user requests a TGT or Service Ticket.
Prior to the November 2022 update, the KDC made some assumptions:
- If the User’s/GMSA’s/Computer’s/Service account’s/Trust object’s msDS-SupportedEncryptionTypes attribute was NULL (blank) or a value of 0, the KDC assumes account only supports RC4_HMAC_MD5.
- If the Windows Kerberos Client on workstations/Member Servers and KDCs are configured to ONLY support either one or both versions of AES encryption, the KDC would create an RC4_HMAC_MD5 encryption key as well as create AES Keys for the account if msDS-SupportedEncryptionTypes was NULL or a value of 0. This meant you could still get AES tickets.
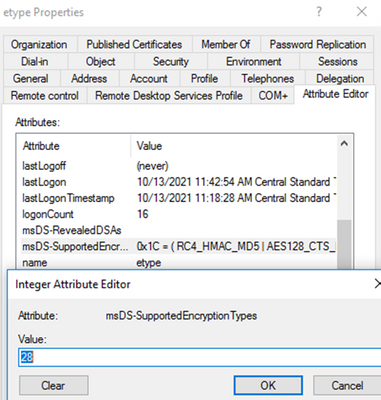
- Configurations where FAST/Windows Claims/Compound Identity/Disabled Resource SID Compression were implemented had no impact on the KDC’s decision for determining Kerberos Encryption Type. See below screen shot of an example of a user account that has these higher values configured but DOES NOT have an encryption type defined within the attribute.
After November 2022 Update the KDC Makes the following decisions:
- If the User’s/GMSA’s/Computer’s/Service account’s/Trust object’s msDS-SupportedEncryptionTypes attribute was NULL (blank) or a value of 0, it defaults to an RC4_HMAC_MD5 encrypted ticket with AES256_CTS_HMAC_SHA1_96 session keys if the DefaultDomainSupportedEncTypes registry value is not configured on the KDC. If this value IS configured, then it uses the value defined in the registry.
- If the User’s/GMSA’s/Computer’s/Service account’s/Trust object’s msDS-SupportedEncryptionTypes attribute is NOT NULL nor a value of 0, it will use the most secure intersecting (common) encryption type specified. If the KDC’s Kerberos client is NOT configured to support any of the encryption types configured in the account’s msDS-SupportedEncryptionTypes attribute then the KDC will NOT issue a TGT or Service Ticket as there is no common Encryption type between the Kerberos Client, Kerberos enabled service, or the KDC.
As explained above, the KDC is no longer proactively adding AES support for Kerberos tickets, and if it is NOT configured on the objects then it will more than likely fail if RC4_HMAC_MD5 has been disabled within the environment. This literally means that the authentication interactions that worked before the 11b update that shouldn’t have, correctly fail now.
On top of that, if FAST, Compound Identity, Windows Claims, or Resource SID Compression has been enabled on accounts that don’t have specific encryption types specified within the environment, it also will cause the KDC to NOT issue Kerberos tickets as the attribute msDS-SupportedEncryptionTypes is no longer NULL or a value of 0. These technologies/functionalities are outside the scope of this article. You can read more about these higher bits here: FAST, Claims, Compound auth and Resource SID compression.
Steps to address the issues:
So now that you have the background as to what has changed, we need to determine a few things.
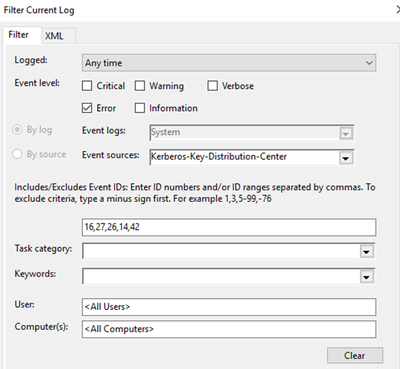
If the November 2022/OOB updates have been deployed to your domain controller(s), determine if you are having problems with the inability for the domain controllers (KDC) to issue Kerberos TGT’s or Service tickets. This can be done by Filtering the System Event log on the domain controllers for the following:
Event Log: System
Event Source: Kerberos-Key-Distribution-Center
Event IDs: 16,27,26,14,42
NOTE: If you want to know about the detailed description, and what it means, see the section later in this article labeled: Kerberos Key Distribution Center Event error messages.
If any of these have started around the same time as the November security update being installed, then we already know that the KDC is having issues issuing TGT or Service tickets.
First, we need to determine if your environment was configured for Kerberos FAST, Compound Identity, Windows Claims or Resource SID Compression. This can be easily done one of two ways:
- Running the following Windows PowerShell command to show you the list of objects in the domain that are configured for these.
Get-ADObject -Filter "msDS-supportedEncryptionTypes -bor 0xf0000 -and -not msDS-supportedEncryptionTypes -bor 0x1c"
- Running the 11B checker (see sample script at the end of the article) and checking the list of accounts under the section, “There are X objects that have msDS-SupportedEncryptionTypes configured, but no encryption protocol is allowed.”
If any objects are returned, then the supported encryption types will be REQUIRED to be configured on the object’s msDS-SupportedEncryptionTypes attribute. If the script returns a large number of objects in the Active Directory domain, then it would be best to add the encryption types needed via another Windows PowerShell command below:
Set-ADUser [sAMAccountName] -KerberosEncryptionType [CommaSeparatedListOfEtypes]
Set-ADComputer [sAMAccountName] -KerberosEncryptionType [CommaSeparatedListOfEtypes]
Set-ADServiceAccount [sAMAccountName] -KerberosEncryptionType [CommaSeparatedListOfEtypes]
Supported values for ETypes: DES, RC4, AES128, AES256
NOTE: The value “None” is also supported by the PowerShell Cmdlet, but will clear out any of the supported encryption types.
If no objects are returned via method 1, or 11B checker doesn’t return any results for this specific scenario, it would be easier to modify the default supported encryption type for the domain via a registry value change on all the domain controllers (KDCs) within the domain. This is done by adding the following registry value on all domain controllers.
HKLM\System\CurrentControlSet\Services\KDC
Value Type: REG_DWORD
Value Name: DefaultDomainSupportedEncTypes
The value data required would depend on what encryption types that are required to be configured for the domain or forest for Kerberos Authentication to succeed again.
Some of the common values to implement are:
For AES128_CTS_HMAC_SHA1_96 and AES256_CTS_HMAC_SHA1_96 support, you would set the value to: 0x18. This will exclude use of RC4 on accounts with msDS-SupportedEncryptionTypes value of NULL or 0 and require AES.
For RC4_HMAC_MD5, AES128_CTS_HMAC_SHA1_96 and AES256_CTS_HMAC_SHA1_96 support, you would set the value to: 0x1C. This will allow use of both RC4 and AES on accounts when msDS-SupportedEncryptionTypes value of NULL or 0. Note: This will allow the use of RC4 session keys, which are considered vulnerable.
If you want to include an AES256_CTS_HMAC_SHA1_96_SK (Session Key), then you would add 0x20 to the value. So, if with the above examples 0x18 would be 0x38, and 1C would be 0x3C.
More information about the supported encryption type bit flags can be found here:
https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-kile/6cfc7b50-11ed-4b4d-846d-6f08f0812919
The KDC registry value can be added manually on each domain controller, or it could be easily deployed throughout the environment via Group Policy Preference Registry Item deployment.
Mismatched Kerberos Encryption Types
The next issue needing attention is the problem of mismatched Kerberos Encryption Types and missing AES keys. You can leverage the same 11b checker script mentioned above to look for most of these problems.
Here’s an example of an environment that is going to have problems with explanations in the output (Note: This script does not make any changes to the environment. It just outputs a report to the screen):
*****************************************
Legacy OS detected: CN=F42003,CN=Computers,DC=contoso,DC=com
This OS is not compatible with the new default behavior, and authentication to this computer will fail after the DC is upgraded to 11B/11OOB
Explanation: This computer is running an unsupported Operating System that requires RC4 to be enabled on the domain controller.
There are 2 objects that do not have msDS-SupportedEncryptionTypes configured.
When authenticating to this target, Kerberos will default to the setting of DefaultDomainSupportedEncTypes registry on the authenticating DC.
This defaults to a value of 0x27, which means 'use AES for session keys and RC4 for ticket encryption'
If this target service does not support AES, please set msDS-SupportedEncryptionTypes to 4 on this object so that only RC4 is used.
CN=alice,CN=Users,DC=contoso,DC=com
CN=bob,CN=Users,DC=contoso,DC=com
Explanation: If you have disabled RC4, you need to manually set these accounts accordingly, or leverage DefaultDomainSupportedEncTypes. If you still have RC4 enabled throughout the environment, no action is needed.
======================================
There are 1 objects that have msDS-SupportedEncryptionTypes configured, but no encryption protocol is allowed.
This can cause authentication to/from this object to fail.
Please either delete the existing msDS-SupportedEncryptionTypes settings, or add supported etypes.
Example: Add 0x1C to signify support for AES128, AES256, and RC4
CN=server12,CN=Users,DC=contoso,DC=com
Explanation: The fix action for this was covered above in the FAST/Windows Claims/Compound Identity/Resource SID compression section.
======================================
There are 2 computers/services that are configured for RC4/DES only
If you have any clients or DCs that are configured to only support AES, authentication will fail
Here is the list of objects that are RC4/DES only:
CN=computer4,CN=Users,DC=contoso,DC=com
CN=Stefan,CN=Users,DC=contoso,DC=com
Explanation: If are trying to enforce AES anywhere in your environments, these accounts may cause problems. You need to investigate why they have been configured this way and either reconfigure, update, or replace them.
A common scenario where authentication fails after installing November update on DCs in this condition is if DCs are configured to only support AES
Example: Setting the 'Configure encryption types allowed for Kerberos' policy to AES only on DCs
Here are the DCs configured for AES only:
CN=DC1,OU=Domain Controllers,DC=contoso,DC=com
Explanation: This is warning you that RC4 is disabled on at least some DCs. You’ll need to consider your environment to determine if this will be a problem or is expected.
Want more Information about Windows OS and Kerberos?
Attribute msDS-SupportedEncryptionTypes
To avoid redundancy, I will briefly cover a very important attribute called msDS-SupportedEncryptionTypes on objectClasses of User. For our purposes today, that means user, computer, and trustedDomain objects. Here’s an example of that attribute on a user object:
If you haven’t patched yet, you should still check for some issues in your environment prior to patching via the same script mentioned above.
If you have already patched, you need to keep an eye out for the following Kerberos Key Distribution Center events. If you see any of these, you have a problem.
Event ID 14 Description: While processing an AS request for target service krbtgt/contoso.com, the account Client$ did not have a suitable key for generating a Kerberos ticket (the missing key has an ID of 5). The requested etypes : 18 17 23 3 1. The accounts available etypes : 23. Changing or resetting the password of krbtgt will generate a proper key.
Translation: The krbtgt account has not been reset since AES was introduced into the environment.
Resolution: Reset the krbtgt account password after ensuring that AES has not been explicitly disabled on the DC.
Event ID 42 Description: The Kerberos Key Distribution Center lacks strong keys for account krbtgt. You must update the password of this account to prevent use of insecure cryptography.
Translation: The krbtgt account has not been reset since AES was introduced into the environment.
Resolution: Reset the krbtgt account password after ensuring that AES has not been explicitly disabled on the DC.
Event ID 26 Description: While processing an AS request for target service krbtgt/CONTOSO.COM, the account Client$ did not have a suitable key for generating a Kerberos ticket (the missing key has an ID of 3). The requested etypes were 18. The accounts available etypes were 23 18 17.
Translation: The DC, krbtgt account, and client have a Kerberos Encryption Type mismatch.
Resolution: Analyze the DC and client to determine why the mismatch is occurring.
Event ID 16 Description: While processing a TGS request for the target server http/foo.contoso.com, the account admin@contoso.com did not have a suitable key for generating a Kerberos ticket (the missing key has an ID of 8). The requested etypes were 18 17 23 24 -135. The accounts available etypes were 23 18 17. Changing or resetting the password of <account name> will generate a proper key.
Translation: The encryption types specified by the client do not match the available keys on the account or the account’s encryption type configuration.
Resolution: Reset <account name’s>password after ensuring that AES has not been explicitly disabled on the DC or ensure that the client’s and service account’s encryption types have a common algorithm.
Event ID 27 Description: While processing a TGS request for the target server http/foo.contoso.com, the account admin@CONTOSO.COM did not have a suitable key for generating a Kerberos ticket (the missing key has an ID of 9). The requested etypes were 23 3 1. The accounts available etypes were 23 18 17.
Translation: The encryption types configured on the service account for foo.contoso.com are not compatible with the encryption types specific by the DC. (Another Kerberos Encryption Type mismatch)
Resolution: Analyze the DC, the service account that owns the SPN, and the client to determine why the mismatch is occurring.
All of the events above would appear on DCs. There is one more event I want to touch on, but would be hard to track since it is located on the clients in the System event log.
Event log: System
Source: Security-Kerberos
Event ID: 4
Description: The Kerberos client received a KRB_AP_ERR_MODIFIED error from the server ADATUMWEB$. The target name used was HTTP/adatumweb.adatum.com. This indicates that the target server failed to decrypt the ticket provided by the client. This can occur when the target server principal name (SPN) is registered on an account other than the account the target service is using. Ensure that the target SPN is only registered on the account used by the server. This error can also happen if the target service account password is different than what is configured on the Kerberos Key Distribution Center for that target service. Ensure that the service on the server and the KDC are both configured to use the same password. If the server name is not fully qualified, and the target domain (ADATUM.COM) is different from the client domain (CONTOSO.COM), check if there are identically named server accounts in these two domains, or use the fully-qualified name to identify the server.
Possible problem: Account hasn’t had its password reset (twice) since AES was introduced to the environment or some encryption type mismatch.
Translation: There is a mismatch between what the requesting client supports and the target service account.
Resolution: Analyze the service account that owns the SPN and the client to determine why the mismatch is occurring.
By now you should have noticed a pattern. Things break down if you haven’t reset passwords in years, or if you have mismatched Kerberos Encryption policies. Keep in mind the following rules/items:
- If you have still pre Windows 2008/Vista Servers/Clients:
Such devices may still obtain Kerberos tickets, but cannot decrypt tickets with AES session keys generated by November patched DCs. Pre 2008 devices do support the msDS-SupportedEncryptionTypes attribute. Upgrade these server to a supported version of Windows. IT Admins and CTOs should reread the Sarbanes–Oxley Act of 2002.
-
If you have other third-party Kerberos clients (Java, Linux, etc.) systems that are currently using RC4 or DES:
Contact the third-party vendor to see if the device/application can be reconfigured or updated to support AES encryption, otherwise replace them with devices/applications that support AES encryption and AES session keys.
To run a command on Linux to dump the supported encryption types for a keytab file:
klist -kte /var/kerberos/krb5/user/KeyTabFileName
To analyze a KeyTab file on Windows, you can use the following command to find out the encryption types configured in the file:
KTPass /in KeyTabFileName
- An entire forest and all trusts should have a common Kerberos encryption type to avoid a likely outage. You must ensure that msDS-SupportedEncryptionTypes are also configured appropriately for the configuration you have deployed
- If your security team gives you a baseline image or a GPO that has RC4 disabled, and you haven’t finished prepping the entire environment to solely support AES, point them to this article. Make sure they accept responsibility for the ensuing outage.
- You’ll want to leverage the security logs on the DC throughout any AES transition effort looking for RC4 tickets being issued. You need to enable auditing for «Kerberos Authentication Service» and «Kerberos Service Ticket Operations» on all Domain Controllers. Events 4768 and 4769 will be logged that show the encryption type used. The field you’ll need to focus on is called «Ticket Encryption Type» and you’re looking for 0x17. 0x17 indicates RC4 was issued. This XML query below can be used to filter for these:
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">*[EventData[Data[@Name='TicketEncryptionType'] and (Data='0x17')]]
</Select>
</Query>
</QueryList>
- You need to evaluate the passwordLastSet attribute for all user accounts (including service accounts) and make sure it is a date later than when Windows Server 2008 (or later) DCs were introduced into the environment.
- Previous guidance said “Do not wait for AES to be enforced on you.” This guidance stands.
Happy Hunting,
Sample Script
Import-Module ActiveDirectory
$noSET = New-Object -TypeName ‘System.Collections.ArrayList’
$badSET = New-Object -TypeName ‘System.Collections.ArrayList’
$rc4only = New-Object -TypeName ‘System.Collections.ArrayList’
$AESonlyDC = New-Object -TypeName ‘System.Collections.ArrayList’
$NoAESKeys = New-Object -TypeName ‘System.Collections.ArrayList’
$computers = Get-ADComputer -filter * -Properties msDS-SupportedEncryptionTypes, operatingSystem, operatingSystemVersion, userAccountControl, passwordLastSet
$users = Get-ADUser -Filter * -Properties msDS-supportedEncryptionTypes, servicePrincipalName, passwordLastSet
$dateAESadded = (Get-ADGroup «Read-only Domain Controllers» -Properties WhenCreated).WhenCreated
foreach ($computer in $computers) {
if (!$computer.Enabled) { continue }
#Look for legacy Windows OS’s (pre 2008/Vista)
if ($computer.operatingSystem -match «Windows») {
[int]$version = ($computer.OperatingSystemVersion.Split(«.»))[0]
if ($version -lt 6) {
Write-Host «*****************************************»
Write-Host «Legacy OS detected: » -NoNewline -ForegroundColor Red
Write-Host $computer
Write-Host «This OS is not compatible with the new behavior, and authentication to this computer will fail after installing Windows Update released on November 2022 or newer on DCs.»
continue
}
}
#Look for computer objects with msDS-SupportedEncryptionTypes not configured
if (!$computer.’msDS-SupportedEncryptionTypes’) {
$noSET.Add($computer) | Out-Null
}
else {
$set = $computer.’msDS-SupportedEncryptionTypes’
#Look for computer objects with msDS-SupportedEncryptionTypes configured but no etype enabled
#Example: only CompoundIdentity is set
if (($set -band 0x1F) -eq 0) {
$badSET.Add($computer) | Out-Null
}
#Keep track of objects where AES is disabled
elseif (($set -band 0x18) -eq 0) {
$rc4only.Add($computer) | Out-Null
}
#Look for DCs with msDS-SupportedEncryptionTypes RC4 disabled
if ($computer.’userAccountControl’ -band 0x2000 -and ($set -band 0x4) -eq 0) {
$AESonlyDC.Add($computer) | Out-Null
}
}
if ($computer.passwordlastset -le $dateAESadded) {
$NoAESKeys.Add($computer)
}
}
foreach ($user in $users) {
if (!$user.Enabled) { continue }
if ($user.servicePrincipalName) {
#ignore krbtgt
if ($user.Name -match «krbtgt») { continue }
#This is most likely a service account
#Look for objects with msDS-SupportedEncryptionTypes not configured
if (!($user.’msDS-SupportedEncryptionTypes’)) {
$noSET.Add($user) | Out-Null
}
else {
$set = $user.’msDS-SupportedEncryptionTypes’
#Look for objects with msDS-SupportedEncryptionTypes configured but no etype enabled
if (($set -band 0x1F) -eq 0) {
$badSET.Add($user) | Out-Null
}
#Keep track of objects where AES is disabled
elseif (($set -band 0x18) -eq 0) {
$rc4only.Add($user) | Out-Null
}
}
}
if ($user.passwordlastset -le $dateAESadded) {
$NoAESKeys.Add($user)
}
}
Write-Host «======================================»
if ($noSET.Cout -ne 0) {
Write-Host «There are $($noSET.Count) objects that do not have msDS-SupportedEncryptionTypes configured.» -ForegroundColor Red
Write-Host «When authenticating to this target, Kerberos will use the setting of DefaultDomainSupportedEncTypes registry on the authenticating DC to determinte supported etypes.»
Write-Host «This defaults to a value of 0x27, which means ‘use AES for session keys and RC4 for ticket encryption'»
Write-Host «If this target server does not support AES, please set msDS-SupportedEncryptionTypes to 4 on this object so that only RC4 is used.»
foreach ($obj in $noSET) {
Write-Host «`t»$obj
}
}
else {
Write-Host «There were no objects with msDS-SupportedEncryptionTypes not configured.»
Write-Host «During Kerberos authentication, supported etypes will be determined based on the value of msDS-SupportedEncryptionTypes»
}
Write-Host «======================================»
if ($badSET.Count -ne 0) {
Write-Host «There are $($badSET.Count) objects that have msDS-SupportedEncryptionTypes configured, but no encryption protocol is allowed.» -ForegroundColor Red
Write-Host «This can cause authentication to/from this object to fail.»
Write-Host «Please either delete the existing msDS-SupportedEncryptionTypes settings, or add supported etypes.»
Write-Host «Example: Add 0x1C to signify support for AES128, AES256, and RC4»
foreach ($obj in $badSET) {
Write-Host «`t»$obj
}
}
else {
Write-Host «There were no objects with msDS-SupportedEncryptionTypes configured without any etypes enabled.»
}
Write-Host «======================================»
if ($NoAESKeys.Count -ne 0) {
Write-Host «There are $($NoAESKeys.Count) objects that do not have AES Keys generated.» -ForegroundColor Red
Write-Host «This can occur if the account’s password has not been changed after adding Server 2008 or newer DCs»
Write-Host «Authentication to this target can fail if AES is required by either the client or the KDC.»
Write-Host «Please change/reset the accounts’ password, and AES keys will be automatically generated.»
foreach ($obj in $NoAESKeys) {
Write-Host «`t»$obj
}
}
else {
Write-Host «There were no accounts whose passwords predate AES capabilities.»
}
Write-Host «======================================»
if ($rc4only.Count -ne 0) {
Write-Host «There are $($rc4only.Count) computers/services that are configured for RC4/DES only.» -ForegroundColor Red
Write-Host «Authentication to this target can fail if AES is required by either the client or the KDC.»
Write-Host «Here is the list of objects that are RC4/DES only:»
foreach ($obj in $rc4only) {
Write-Host «`t»$obj
}
Write-Host «`nA common scenario where authentication fails after installing November 2022 update or newer on DCs in this condition is if DCs are configured to only support AES»
Write-Host «Example: Setting the ‘Configure encryption types allowed for Kerberos’ policy to AES only on DCs»
if ($AESonlyDC.Count -eq 0) {
Write-Host «No DCs were detected that are configured for AES only»
}
else {
Write-Host «Here are the DCs configured for AES only:»
foreach ($obj in $AESonlyDC) {
Write-Host «`t»$obj
}
}
}
if ($badSET.Count -eq 0 -and $noSET.Count -eq 0 -and $NoAESKeys.Count -eq 0 -and $rc4only.Count -eq 0) {
Write-Host «======================================»
Write-Host «Configurations known to cause Kerberos authentication failures after installing November 2022 update or newer on DCs were not detected.» -ForegroundColor Green -BackgroundColor Black
Write-Host «Pleae contact Microsoft Support if you do see any failures.»
}
Introduction to this blog series: https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/having-issues-since-deploying…
Part 2 of this blog series: https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/so-you-say-your-dc-s-memory-is-getting-all-used-up-after/ba-p/3696318
After downloading cumulative updates issued on this month’s Patch Tuesday, business domain controllers may encounter Kerberos sign-in failures and other authentication issues.
Microsoft is looking into this new known issue. On all Windows versions above Windows 2000, the Kerberos protocol has taken the place of the NTLM protocol as the default authentication protocol for domain-connected devices.
The November updates, according to MS “break Kerberos in situations where you have set the ‘This account supports Kerberos AES 256 bit encryption’ or ‘This account supports Kerberos AES 128 bit encryption’ Account Options set” (i.e., the msDS-SupportedEncryptionTypes attribute on user accounts in AD).
Any Kerberos authentication situation inside impacted business setups can be impacted by the known problem, which Microsoft is currently investigating.
You can have Kerberos authentication problems on Windows Servers with the Domain Controller role after installing updates issued on November 8, 2022 or later, according to Microsoft.
You can see a Microsoft-Windows-Kerberos-Key-Distribution-Center Event ID 14 error event in the System section of your Domain Controller’s Event Log with the following language when this problem arises.
The phrase “the missing key has an ID of 1” will be used to identify errors that are recorded in the system event logs of impacted systems. The account “account name” didn’t have an appropriate key for producing a Kerberos ticket while processing an AS request for the target service “service,” and the missing key has an ID of 1, according to the reported problems. The following examples of Kerberos authentication situations are just a few.
- Signing in as a domain user might fail. Authentication with Active Directory Federation Services (AD FS) may potentially be impacted by this.
- It’s possible for Group Managed Service Accounts (gMSA) to have authentication issues when used with services like Internet Information Services (IIS Web Server).
- Domain user remote desktop connections might not succeed.
- Shared folders on workstations and file shares on servers may not be accessible.
- Printing operations that need domain
So, that’s all in this blog. I will meet you soon with next stuff .Have a nice day !!
Recommended content
How to Check the Active Directory Database Integrity
Disabling and Enabling the Outbound Replication
DFS Replication Service Stopped Replication
Repadmin Replsummary
How to prevent lingering objects replication in active directory
AD replication process overview
Guys please don’t forget to like and share the post. You can also share the feedback on below windows techno email id.
If you have any question feel free to contact us on [email protected] also follow us on facebook@windowstechno to get updates about new blog posts.

He is an Active Directory Consultant. He has been working in IT industry for more than 10 years. He is dedicated and enthusiastic information technology expert who always ready to resolve any technical problem. If you guys need any further help on subject matters, feel free to contact us on [email protected] Please subscribe our Facebook page as well website for latest article. https://www.facebook.com/windowstechno
Event Id 11 Microsoft-Windows-Kerberos-Key-Distribution-Center. Sep 08, 2020 · 8 (decimal) or 0x8 (hexadecimal): The duplicate name is %1 (of type %2).
You may also see a kdc 11 error for a duplicate spn in the systemevent log:
In this situation, the criteria 1 is satisfied by rc4 encryption, and the criteria 2 is satisfied by des encryption. See full list on docs.microsoft.com We strongly recommend that you check whether des encryption is still required in the environment or check whether specific services require only des encryption. See full list on docs.microsoft.com
Location:
To continually increase the information security of on-premises Domain Controllers, Microsoft provides new functionality to Windows Server and Active Directory. Sometimes, the new security measures affect backward compatibility. In this knowledgebase article, I’ll discuss such a measure.
The situation
You run Active Directory with Domain Controllers on one or more of the below Windows Server Operating Systems:
- Windows Server 2008
- Windows Server 2008 R2
- Windows Server 2012
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server 2019
- Windows Server 2022
You have not reset the password for the krbtgt account in Active Directory since upgrading the Active Directory Domain Functional Level (DFL) to Windows Server 2008, or beyond, or your DFL still runs Windows Server 2003.
You have not configured the Network Security: Configure encryption types allowed for Kerberos setting in a Group Policy object targeting the domain or the Domain Controllers OU, or have it configured to still allow RC4_HMAC_MD5 explicitly.
The issue
Suddenly, you start experiencing errors in the System log of your Domain Controllers. These errors have Event ID 42 and source Kdcsvc.
The Kerberos Key Distribution Center lacks strong keys for account: accountname. You must update the password of this account to prevent use of insecure cryptography. See https://go.microsoft.com/fwlink/?linkid=2210019 to learn more.
End users in the environment do not experience any issues signing in or signing out and any services that run with the credentials of domain user objects do not experience issues.
The cause
These errors occur because the November 2022 or newer cumulative updates for Windows Server are installed on Domain Controllers.
Since the November 2022 updates, the Advanced Encryption Standard (AES) is configured as the default encryption type for session keys on user objects that are not marked with a default encryption type.
After applying the updates, the above error is triggered on Domain Controllers, in either or both of the following two scenarios:
- A person signs in with a user object that is explicitly configured to use RC4 and is allowed to do so, because the Network Security: Configure encryption types allowed for Kerberos Group Policy setting allows it.
- The password for the krbtgt account was last reset when the Active Directory domain ran in the Windows Server 2003 Domain Functional Level (or before).
Since Windows Server 2008, the krbtgt account supports AES-encrypted session keys, but only when the password on the password for this account is reset after the Active Directory Domain Functional Level (DFL) was upgraded to Windows Server 2008.
The error indicates that the affected user objects are insecurely configured and should be configured to use the Advanced Encryption Standard (AES) instead of legacy RC4 encryption to encrypt session keys. The affected user objects are vulnerable in the context of CVE-2022-37966.
The solution
There are two ways to solve these errors:
Reset the password for the krbtgt account, have affected people change their passwords and have them sign out and sign in again
Perform these steps:
Step 1
If the Active Directory Domain Functional Level (DFL) is set to Windows Server 2003, upgrade it to Windows Server 2008, or up. In the process, the password for the krbtgt account is reset, so do not reset the password for the krbtgt account as part of step 2 (within a week’s time span). Skip to step 3.
Step 2
To reset the password for the krbtgt account, use Microsoft’s New-KrbtgtKeys.ps1 PowerShell script from Github and run it on the Domain Controller holding the Primary Domain Controller Emulator (PDCE) Flexible Single Master Operations (FSMO) role.
Step 3
Configure the affected user object(s) to no longer explicitly use RC4_HMAC_MD5.
When people sign out and sign in again after they’ve changed their passwords, their session keys will be AES encrypted and no longer be vulnerable in the context of CVE-2022-37966. When RC4 is needed for the account, turn to Step 3 of the below alternative method.
Step 4
Optionally, when no new errors with event ID 42 occur, configure the Network Security: Configure encryption types allowed for Kerberos setting in a Group Policy object targeting the domain to explicitly disable the DES_CBC_CRC, DES_CBC_MD5 and RC4_HMAC_MD5 encryption types and explicitly enable the AES128_HMAC_SHA1, AES256_HMAC_SHA1 and Future encryption types.
Reset the password for the krbtgt account, apply a registry key to update explicitly set encryption defaults and have affected people sign out and sign in again
Perform these steps:
Step 1
If the Active Directory Domain Functional Level (DFL) is set to Windows Server 2003, upgrade it to Windows Server 2008, or up. In the process, the password for the krbtgt account is reset, so do not reset the password for the krbtgt account as part of step 2 (within a week’s time span). Skip to step 3.
Step 2
To reset the password for the krbtgt account, use Microsoft’s New-KrbtgtKeys.ps1 PowerShell script from Github and run it on the Domain Controller holding the Primary Domain Controller Emulator (PDCE) Flexible Single Master Operations (FSMO) role.
Step 3
Apply the following line of PowerShell to all Domain Controllers and domain-joined devices:
New-ItemProperty -Path «HKLM:\System\CurrentControlSet\Services\KDC» -Name DefaultDomainSupportedEncTypes -Value 0X27 -PropertyType DWORD –Force
This registry key re-enables the DES_CBC_CRC, DES_CBC_MD5 and RC4_HMAC_MD5 encryption types as supported encryption types for Kerberos.
Step 4
Work with the vendor of any third-party Domain Controllers, devices and/or applications to remove dependencies on the RC4_HMAC_MD5 encryption for Kerberos session tickets.
Step 5
After remediating these situations, change the password for the affected user object(s), have people sign out and sign in again or restart the affected service run by the affected user object(s), and disable the outdated encryption types again by removing the DefaultDomainSupportedEncTypes registry key.
Step 6
Optionally, when no new errors with event ID 42 occur, configure the Network Security: Configure encryption types allowed for Kerberos setting in a Group Policy object targeting the domain to explicitly disable the DES_CBC_CRC, DES_CBC_MD5 and RC4_HMAC_MD5 encryption types and explicitly enable the AES128_HMAC_SHA1, AES256_HMAC_SHA1 and Future encryption types.
После установки обновлений, выпущенных 8 ноября 2022 г. или позже, на серверах Windows с ролью контроллера домена могут возникнуть проблемы с аутентификацией Kerberos. Эта проблема может повлиять на любую аутентификацию Kerberos в вашей среде. Некоторые сценарии, которые могут быть затронуты:
• Вход пользователя домена может завершиться сбоем. Это также может повлиять на аутентификацию Active Directory Federation Services (AD FS);
• Group Managed Service Accounts (gMSA), используемые для таких служб, как Internet Information Services (IIS Web Server), могут не пройти аутентификацию;
• Подключения Remote Desktop с помощью пользователей домена могут не подключиться;
• Возможно, вам не удастся получить доступ к общим папкам на рабочих станциях и общим файлам на серверах;
• Печать, требующая аутентификации пользователя домена, может завершиться сбоем;
При возникновении этой проблемы вы можете получить Microsoft-Windows-Kerberos-Key-Distribution-Center Event ID 14 error event в разделе «Система» журнала событий на контроллере домена с текстом ниже. Примечание: затронутые события будут иметь «отсутствующий ключ имеет идентификатор 1»:
While processing an AS request for target service , the account did not have a suitable key for generating a Kerberos ticket (the missing key has an ID of 1). The requested etypes : 18 3. The accounts available etypes : 23 18 17. Changing or resetting the password of will generate a proper key.
Примечание: Эта проблема не является ожидаемой частью усиления безопасности для Netlogon и Kerberos, начиная с обновления безопасности за ноябрь 2022 года. Вам по-прежнему необходимо будет следовать указаниям в этих статьях даже после того, как эта проблема будет решена.
Устройства Windows, используемые потребителями дома, или устройства, не являющиеся частью локального домена, не затронуты этой проблемой. Среды Azure Active Directory, которые не являются гибридными и не имеют локальных серверов Active Directory, не затрагиваются.
Решение: Эта проблема была решена во внеплановых обновлениях, выпущенных 17 ноября 2022 г. для установки на все контроллеры домена (DCs) в вашей среде. Вам не нужно устанавливать какие-либо обновления или вносить какие-либо изменения в другие сервера или клиентские устройства в вашей среде, чтобы решить эту проблему. Если вы использовали какой-либо обходной путь или смягчения для этой проблемы, они больше не нужны, и Microsoft рекомендует вам их удалить.
Чтобы получить автономный пакет для этих внеплановых обновлений, найдите номер KB в
Microsoft Update Catalog
. Вы можете вручную импортировать эти обновления в Windows Server Update Services (WSUS) и Microsoft Endpoint Configuration Manager. Инструкции по WSUS см. в статье
WSUS and the Catalog Site
. Инструкции по Configuration Manger см. в статье
Import updates from the Microsoft Update Catalog
. Примечание: Указанные ниже обновления недоступны из Центра обновления Windows и не устанавливаются автоматически.
Накопительные обновления:
• Windows Server 2022:
KB5021656
;
• Windows Server 2019:
KB5021655
;
• Windows Server 2016:
KB5021654
;
Примечание: Перед установкой этих накопительных обновлений не требуется применять какое-либо предыдущее обновление. Если вы уже установили обновления, выпущенные 8 ноября 2022 г., вам не нужно удалять затронутые обновления перед установкой любых более поздних обновлений, включая обновления, перечисленные выше.
Автономные обновления:
• Windows Server 2012 R2:
KB5021653
;
• Windows Server 2012:
KB5021652
;
• Windows Server 2008 R2 SP1: Это обновление пока недоступно. Пожалуйста, проверьте здесь на следующей неделе для получения дополнительной информации;
• Windows Server 2008 SP2:
KB5021657
;
Примечание: Если вы используете только обновления безопасности для этих версий Windows Server, вам нужно установить эти автономные обновления только за ноябрь 2022 года. Только обновления безопасности не являются накопительными, и вам также потребуется установить все предыдущие только обновления безопасности, чтобы они были полностью актуальными. Ежемесячные накопительные обновления являются накопительными и включают в себя обновления безопасности и все обновления качества. Если вы используете ежемесячные накопительные обновления, вам потребуется установить как перечисленные выше автономные обновления, чтобы решить эту проблему, так и установить ежемесячные накопительные пакеты, выпущенные 8 ноября 2022 г., чтобы получить обновления качества за ноябрь 2022 г. Если вы уже установили обновления, выпущенные 8 ноября 2022 года, вам не нужно удалять затронутые обновления перед установкой любых более поздних обновлений, включая обновления, перечисленные выше.
Затронутые платформы:
• Client: Windows 11, версия 22H2; Windows 10, версия 22H2; Windows 11, версия 21H2; Windows 10, версия 21H2; Windows 10, версия 21H1; Windows 10, версия 20H2; Windows 10 Enterprise LTSC 2019; Windows 10 Enterprise LTSC 2016; Windows 10 Enterprise 2015 LTSB; Windows 8.1; Windows 7 SP1;
• Server: Windows Server 2022; Windows Server 2019; Windows Server 2016; Windows Server 2012 R2; Windows Server 2012; Windows Server 2008 R2 SP1; Windows Server 2008 SP2;