by Elena Constantinescu
Elena started writing professionally in 2010 and hasn’t stopped exploring the tech world since. With a firm grasp of software reviewing and content editing, she is always trying… read more
Updated on
- VPN services are exceptional for online security and privacy, as well as for remote connections. But they’re prone to errors, like any other piece of software.
- Use 5 very different ways to monitor your Windows 10 VPN connection. You can detect packet loss and other issues, view connected users, and more.
- If you’re an entrepreneur interested in virtual private networks, visit our Business VPN section.
- Once you identify the VPN connection issue, find its solution in our VPN Troubleshooting Hub.
A VPN is a must-have tool for anyone concerned about online security and privacy. It can change your IP address and geo-location, encrypt all data, access blocked sites, and bypass censorship.
Virtual private network solutions also help employees remotely access the workplace and use the company’s internal resources by connecting two networks.
However, if the VPN connection is faulty, those security features won’t matter anymore. That’s why it’s a good idea to track the VPN connection on your PC.
We listed 5 very different ways to monitor a Windows 10 VPN connection, depending on the type of information that interests you.
How we test, review and rate?
We have worked for the past 6 months on building a new review system on how we produce content. Using it, we have subsequently redone most of our articles to provide actual hands-on expertise on the guides we made.
For more details you can read how we test, review, and rate at WindowsReport.
Make sure you’re connected to the VPN before proceeding.
How do I monitor my Windows 10 VPN connection?
View the VPN connection properties
- Right-click the Windows 10 Start button.
- Go to Network Connections.
- Click Change adapter options.
- Double-click the VPN connection.
It might seem like a rudimentary method to monitor your Windows 10 VPN connection, but you can view the total sent and received bytes this way.
Enable debugging and inspect logs
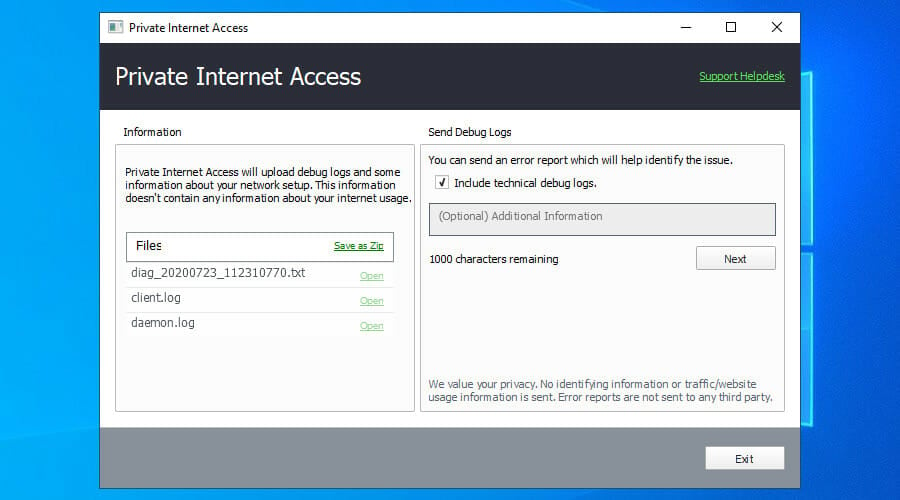
- Sign up for a PIA subscription plan.
- Download and install PIA.
- Connect to a VPN server.
- Right-lick PIA’s icon in the systray.
- Go to Settings > Help.
- Check Enable Debug Logging.
- Click Submit Debug Logs.
- Click Open next to a log file to open its location in Windows Explorer.
This method gives you complete, raw data about the VPN connection. We chose Private Internet Access in this example because it’s the best VPN for Windows 10. It’s a fast and secure VPN service operated by Kape Technologies.

Private Internet Access
Enable debug logging in PIA to find out exactly what happens with your VPN connection.
Use pathping
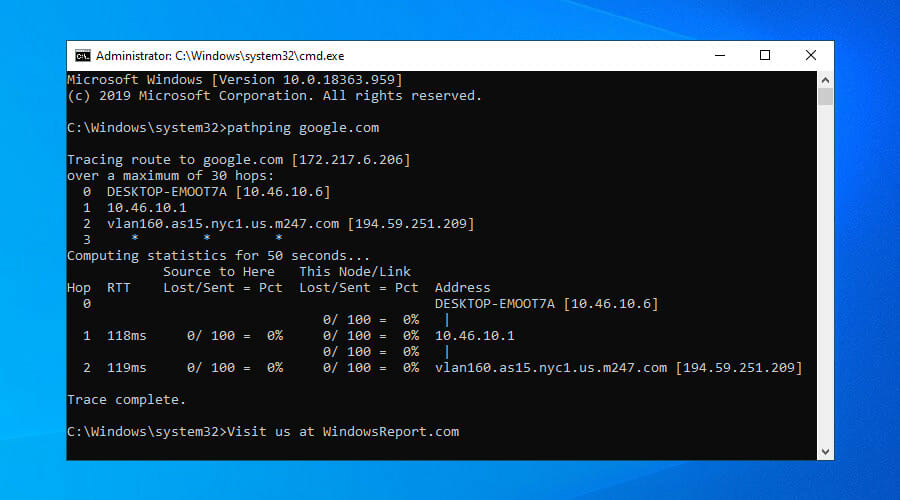
- Launch Command Prompt as admin.
- Type pathping and the IP address or hostname of the remote PC.
- You can also use arguments, as detailed in our pathping guide.
Pathping is a combination of ping and traceroute, which checks the route between your PC and a remote server. It sends the ping command every hop of the way, making it an excellent tool to monitor your Windows 10 VPN connection and check for packet loss.
Use NetworkTrafficView
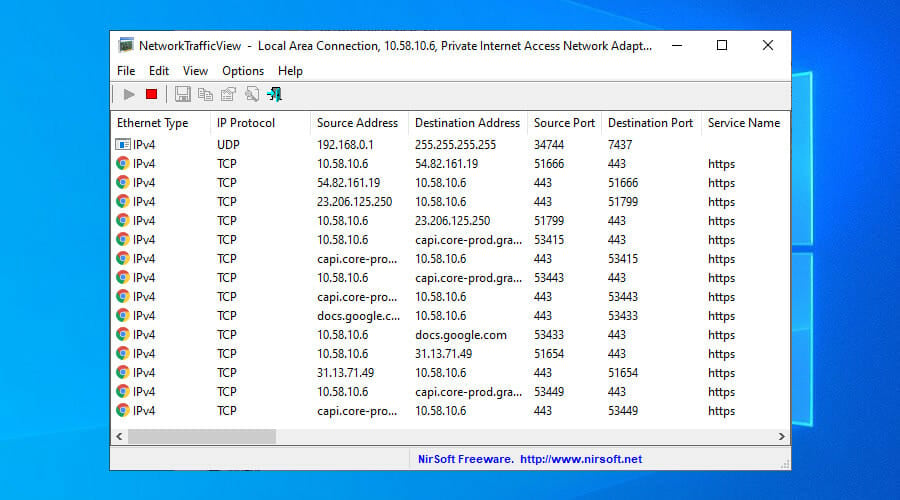
- Download NetworkTrafficView and unpack the ZIP file.
- Run the tool as admin.
- Set the VPN connection as your network adapter.
- Click the start button.
NetworkTrafficView is a free-to-use packet sniffer that lets you choose the network adapter to keep track of all Internet-enabled processes. You can use it to monitor your VPN connection in Windows 10 and view detailed information, such as data speed, last packet time, and latency.
Check out other free tools like Performance Monitor (built into Windows 10) or Microsoft Network Monitor.
Use PRTG Network Monitor
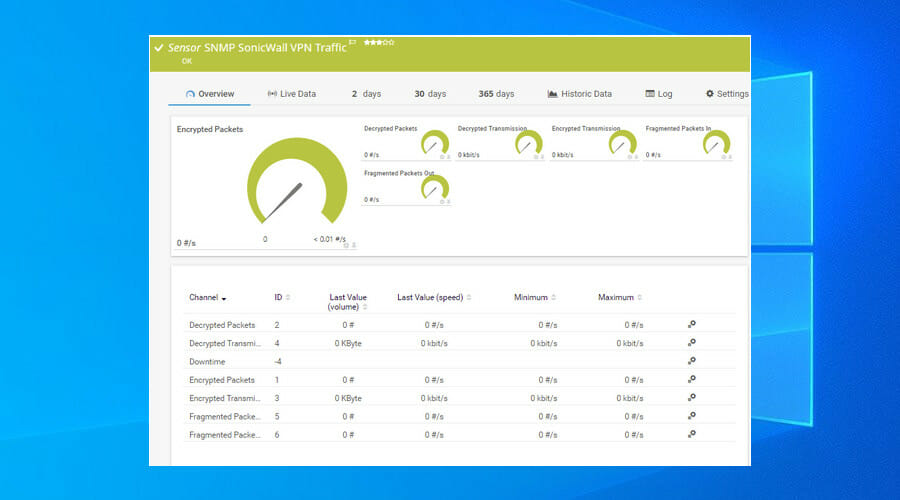
- Download PRTG Network Monitor.
- Install and launch the application.
- Log in to the web interface with the default credentials.
- Open the Sensors menu and click Add Sensor.
- Select Add sensor to a device and click Probe Device.
- Click Continue.
- In the search box, type VPN.
- Click on the preferred sensor type.
- Set a Sensor Name and click Create.
- Click the sensor to view VPN-related data.
PRTG Network Monitor is a network traffic inspection tool for corporations that want to monitor VPN connections on Windows 10 and Windows Server. It can be used to keep track of the activity of remote connections.
You can detect VPN connection issues and suspicious traffic, get notified on critical events, generate reports, and more. Currently, PRTG Network Monitor supports SNMP Cisco ASA VPN connections, traffic and users, together with SNMP SonicWall VPN traffic.
In conclusion, these 5 solutions can help you monitor your VPN connections on Windows 10 computers. As you can see, they show various information, from simple data like total sent and received data packets to more elaborate details like currently connected employees.
If you’re dealing with a specific VPN error, make sure to visit our VPN Troubleshooting Hub.
I have a friend who is quitting their job.
He is owed overtime, but the workplace has been casual about recording hours.
He regularly signs out a work laptop, and will work from home via VPN.
Is there a way to retrieve log files for this person, despite the fact they use a different computer for the majority of the time that he could copy as an aid to his claim for overtime hours?
Normally, if it was a everyday computer, I would check some common log files, eventvwr.msi etc.
Thoughts?
asked Apr 2, 2015 at 0:54
1
There are relevant log files in \WINDOWS\system32\LogFiles that may help. There is also system information available from the Event Viewer (Run > eventvwr.exe OR Control Panel > Admin Tools > Event Viewer) and look for System logs.
However, both these locations could be empty depending on local settings.
One can configure Windows firewall to log VPN connections but that is not a default. Check Control Panel > Windows Firewall > [Advanced tab], the default location is C:\WINDOWS\pfirewall.log for the log file.
Specific applications used may have preserved log data. If you know the IP address connected to you could do a general search for files containing that IP address (but that wouldn’t find compressed logs or non-ASCII log data).
answered Apr 2, 2015 at 12:22
pbhjpbhj
1362 silver badges14 bronze badges
Expanding on @pbhj’s answer, I successfully found logs following these instructions, summarized here:
Navigate through the Start menu to get to the event Viewer: Start >
Control Panels > Administrative Tools > Event Viewer.In the Actions
pane, select Create Custom View or Filter Current Customer View.Select the event severities (e.g., Critical, Warning, Error,
Information, etc.) listed under the Event level option.Click the
Event sources pull-down menu and select the event sources that you
would like to see, for example: VPN Client — vpnagent, vpnui; DHCP —
DHCP-Client; Native VPN — RasMan, RasClient, Remote Access.Save the
filter to Custom View.Select the log event in the event browser page
(top).Event Properties in the middle pane has the log details for an
event. Double-click an event to bring up a new Event Properties window
in addition to the Event Properties pane.
I used specifically «RasClient», and found this Error level log in the Custom view:
CoId={53F1C7C6-B011-4453-B2D5-C0F82ED8E590}: The user {domain}{username} dialed
a connection named {target VPN connection} which has failed. The error code
returned on failure is 789.
(Note I was looking for logs because my VPN errored, not because I wanted to see my VPN history as in OP’s question)
Codebling
7241 gold badge6 silver badges19 bronze badges
answered May 18, 2017 at 17:31
I found these event IDs:
- Connect Event: RasMan 20267
- Disconnect Event: RasMan 20268
- General Details: «RasClient» logging
You can use several tools to filter for these events.
Try FullEventLogView
Try Nirsoft’s fulleventlogview.exe. It will show connect/disconnect events.
- Open
Advanced Options - OPTIONAL:
Show only events from the last...1 Days (or however many you want) Show only the specified providers (comma-delimited list, wildcard allowed): RasClient,RasMan
Or try Custom View
Do to the same thing inside the regular Windows Event Viewer do this.
- Save this text here as
eventvwr.custom-view.RAS.xml:
<ViewerConfig>
<QueryConfig>
<QueryParams>
<Simple>
<Channel>Application,System</Channel>
<RelativeTimeInfo>0</RelativeTimeInfo>
<Source>RasClient,Rasman</Source>
<BySource>True</BySource>
</Simple>
</QueryParams>
<QueryNode>
<Name>RAS</Name>
<QueryList>
<Query Id="0" Path="Application">
<Select Path="Application">*[System[Provider[@Name='RasClient' or @Name='Rasman']]]</Select>
<Select Path="System">*[System[Provider[@Name='RasClient' or @Name='Rasman']]]</Select>
</Query>
</QueryList>
</QueryNode>
</QueryConfig>
</ViewerConfig>
- Start => Run… => eventvwr.msc Enter
- Event Viewer (Local) => Custom Views => right-click => Import Custom View…
answered Mar 15, 2022 at 10:48
StackzOfZtuffStackzOfZtuff
1,4931 gold badge15 silver badges23 bronze badges
You must log in to answer this question.
Not the answer you’re looking for? Browse other questions tagged
.
Not the answer you’re looking for? Browse other questions tagged
.
Advertisement
The goal of this article is to educate the new and non-IT expert VPN service users about the logging part of VPN both by the VPN service providers and the local computer. To reach that goal, in this article, we will cover the basics around the VPN Logs and explain phrases such as Zero Logging VPN, No Logging VPN. Also, we will give a real-life example of using a Windows client of a paid VPN service on Windows 10 to demonstrate the procedure to check the VPN log on the local computer.
VPN created with virtual point-to-point, virtual tunneling protocols, traffic encryption etc. Traditional VPNs use point-to-point topology and Microsoft Windows NetBIOS may not be fully working. Virtual Private LAN Service (VPLS), Layer 2 Tunnelling Protocols (L2TP) does not have such limitations. We can classify the VPN systems by tunneling protocol, tunnel’s termination point location, type of topology of connections, levels of security, OSI layer they present to the connecting network, number of simultaneous connections etc.
- 1 Introduction
- 2 Basic of VPN Logs
- 3 Zero Logging VPN for Windows 10
- 4 Infographics
- 5 Check VPN Log of VPN Client Applicatio
- 6 Conclusion
Virtual private network practically a proxy just like we set up Nginx server to listen to another server’s IPv4 server. Of course, the protocol is different for VPN than used for Nginx server but the basic is the same. That is the simplest way to explain the mechanism of how a VPN service works. On the main server’s log file, we can see the IPv4 connections from the main server and on the Nginx server’s log, we will obtain the real IPs, the user agent of the traffic requesting a request of URL etc. VPN logs from VPN service provider’s side are somewhat comparable to the above example. As a user, we have absolutely no way to verify at what level a VPN provider logs their users and how much data they are retaining. The above example with Nginx server clarifies that for server administration and to avoid any legal trouble, many VPN services will need to retain log at least for a few hours. Some VPN providers can keep log files for several weeks or even months, others keep for several hours.
Operating a VPN is quite an expensive matter. From our example of using simple Nginx reverse proxy, it will be obvious that for a just reverse proxy set up of that kind, we need two servers. VPN service provider company employs highly qualified network engineers to set up, configure, monitor the servers. Not to forget the cost of bandwidth. For a high-end professional service, we cannot expect to have just two virtual servers in their set up unlike our example with a reverse proxy. Cheaper VPN services, however, use virtual private servers. More servers on their network make their set up and logging much more complex. If a VPN service provider is providing free VPN service then they are getting the money from running the infrastructure from somewhere else. One such way is serving to advertise. Advertising means, that they are collecting user information to know some facts – like the user is not a bot and serve the users relevant ads specific to gender and age. It is meaningless for an ad serving company to deliver an advert for a fast sports car to an older person. The chance to purchase a sports card by an older person is lesser. If a VPN service is free, then they are either not anonymous by any means or has some crippling limitations like speed restrictions or some other limits.
There may be different logs stored by the VPN service providers, most trusted providers probably do not store logs for a longer period. Full traffic log VPN logging is like our example of Nginx Proxy with logging enabled – they store all the data like connected real IP to their server(s), user agent, URL surfed etc. Metadata logs VPN logging does not store the URL accessed but stores all other data like in case of full traffic log. No logs VPN or zero logs VPN claimed to store no data at all. No logs VPN or zero logs VPN technically not impossible to set up. However, Govts of UK, Europe, Australia and US forces to store some data of the users. So, probably you’ll need to do a research to find possible safe VPN. There is VPN service where police made a raid in their datacentre and found no logs, that fact came into the news. In other words, the claim of no logging by VPN service provider actually exists but sadly not possible to verify without a police raid!
It is important to understand that modern tracking is not like just old days’ IP tracking systems. Modern tracking involves carrier-grade NAT and probably backdoors at OS and hardware level to detect the signature of the machine.
Zero Logging VPN for Windows 10
In the context of Windows 10, the phrase VPN logging bears an apparent dual meaning to the new users. The common meaning is the logging by the VPN service provider in the way described above.
We use VPNs not only to conceal our IP address. There are some use cases where we might need to use a VPN. For example, when we are using a possible known-hostile network like a public airport WiFi access point, or using an ISP that is known to use MITM then we can use a VPN service or we can use to bypass basic governmental screening. For example, it is safe to SSH with a good VPN with a dedicated IP. VPN logging is an important matter even for such use cases. When we are accessing our servers via SSH or (s)FTP, then for security reasons it is better to use VPN with zero logging or no logging. Because if VPN service provider’s server is compromised, IP and open port of the servers become obvious. That information may help to somewhat easily intrude a server than without any information.
We also use the phrase VPN logging for logging by our Windows computers. This two logging are separate events and this later one is under control of the user. However, checking VPN logging on Windows operating system is not that easy to a new user, but such logging may be a wanted feature to a particular user group. The phrase VPN logging on Windows often confusing with VPN logging on the servers of the service provider.
How to Check VPN Log of VPN Client Application
Now, we need to clarify the VPN logging system on the local computer running Microsoft Windows. We can provide an example such as the usage of SurfShark VPN for our office usage and their Windows client application. Instead of SuftShark, it could be some other VPN service. In any case first, we need to be their client. Then we should follow their instruction to setup VPN on Microsoft Windows. Then, as for SurfShark we will download VPN app for Windows and install. SurfShark claims to be a strict no-logs VPN service provider and is affordable for our sysadmin works. In an ideal situation, SurfShark will have no logging on their servers. However, the Windows operating system itself has own way of VPN logging which may be turned on or off with checking an option. A VPN client software may also control that option. This VPN log is better to be referred as VPN client log. The logs for the VPN Client on Microsoft Windows are viewable via Computer Management. To access Computer Management, we need to navigate to the Windows start menu, search and open Event Viewer. Within the Event Viewer program, there will be a pane named Actions. In that Actions pane, we can click select Create Custom View or Filter Current Customer View. Then we can select the event severities option listed under the Event level option. Then we will click the Event sources pull-down menu. Thereafter we can select the event sources to investigate what sources we would like to view. For our example, the name of the event sources can be VPN Client or vpnagent or vpnui or DHCP – DHCP-Client or some name indicating SurfShark application. The name under event sources depends on the version of the VPN client application. Now, we will save the filter as Custom View. Then we will select the log event in the event browser page located at the top. The Event Properties clickable option in the middle of the pane has the log details for an event. We can double-click an event to bring up a new Event Properties window.
Conclusion
We believe that this article has covered the basics around VPN Logs and Zero Logging VPN with the example of checking logs using Windows client application. Also, we have clarified the VPN logging on servers and VPN logging on users’ computer. The use case of VPN varies. VPN no way a measure of complete “no tracking” but mostly protects from various malicious intruders via known and unknown loopholes of the servers of ISP.
Tagged With windows 10 vpn logs , zero log VPN , free non logging vpn for windows , windows 10 vpn log , vpn logging windows 10 , windows vpn log , vpn logs windows 10 , VPN log windows 10 , enable vpn client windows event viewer , Microsoft VPN logs
В составе VPNKI существует много систем, которые формируют журналы событий. Часть из этих журналов доступно и пользователям.
Здесь мы кратко расскажем про журналы, которые:
1. относятся к VPN подключениям и доступны в личном кабинете. Это «События безопасности» и «События авторизации».
2. относятся к VPN подключению по протоколу OpenVPN. Высылается по почте.
3. относятся к услугам «Публикация URL» и «Проброс TCP порта». Они высылаются по электронной почте.
Журналы VPN подключений и логи системы удаленного доступа
Журналы VPN соединений доступы в личном кабинете.
- В лог «События безопасности» заносятся важные технические действия в пользовательском аккаунте. Например создание и удаление туннелей, включение или выключение услуги. Также и часть информации о подключении.
- В лог «События авторизации» заносятся только события проверки имени пользователя и пароля туннеля.
Как читать логи системы удаленного доступа
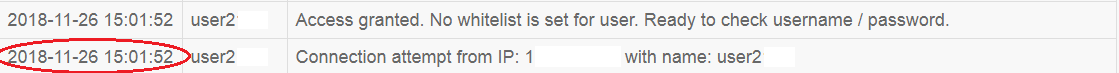
1. При установлении соединения, но еще до проверки имени пользователя и пароля, наша система проверяет наличие адреса, с которого идет подключение, в «белом списке».
Поэтому первые данные о подключении записываются в лог «События безопасности».
Connection attempt from IP: 1x.xx.xx.xx with name: user2xx . Это попытка установления соединения пользователя user2xx c IP адреса 1x.xx.xx.xx.
Access granted. No whitelist is set for user. Ready to check username / password. Нет установленного «белого списка», доступ разрешен. Готов к проверке имени/пароля.
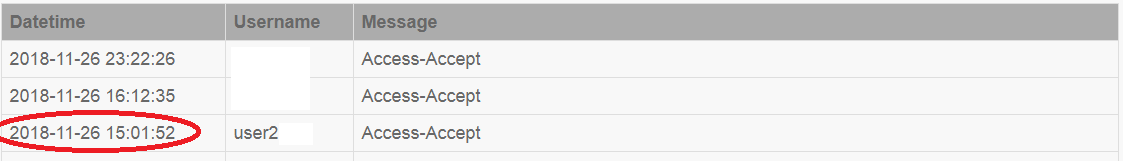
2. После этого начинается работа системы аутентификации и авторизации. Это можно увидеть в логе «События авторизации».
Access-Accept. Это ответ системы аутентификации о том, что доступ разрешен. Проверка имени пользователя и пароля VPN туннеля прошли успешно.
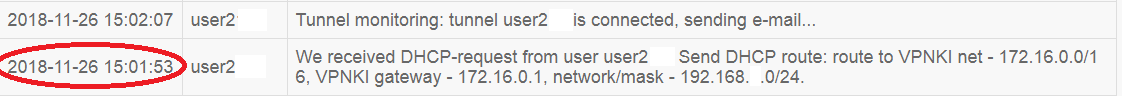
3. Затем можно вернуться к логу «События безопасности». Далее мы можем увидеть, что после успешной аутентификации система получила DHCP запрос от клиентского оборудования на выдачу IP адресов и маршрутов.
We received DHCP-request from user user2xx. Send DHCP route: route to VPNKI net — 172.16.0.0/16, VPNKI gateway — 172.16.0.1, network/mask — 192.168.1.0/24.
Если такой запрос приходит, то сервер VPNKI выдает информацию.
Последним сообщением в логе «События безопасности», касающимся этого соединения идет сообщение о том, что пользователь активировал услугу по почтовому информированию о подключении туннеля.
Tunnel monitoring: tunnel user2xx is connected, sending e-mail… Эта запись говорит об отправке почтового сообщения пользователю.
О проблеме с PPTP и GRE
Как известно, многие провайдеры в силу технических ограничений не всегда корректно пропускают трафик протокола GRE. Этот протокол необходим для работы PPTP. Если вы столкнулись с тем, что соединение PPTP не устанавливается, то имеет смысл заглянуть в логи VPNKI.
В этом случае, в «Событиях безопасности» может присутствовать информация о попытке установления соединения с вашего IP адреса. Однако информации об авторизации в журнале «События авторизации» не будет вовсе.
Это говорит о том, что при установлении соединения дело до проверки имени и пароля не дошло. Вероятная причина этому в отсутствии соединения по протоколу GRE.
Надеемся что эта короткая информация поможет вам в поиске неисправности.
Журнал подключений по OpenVPN
Журнал подключений высылается по электронной почте пользователя со страницы настройки туннелей. В архиве zip находится текстовый файл, содержащий лог обращений из Интернет. Период времени, за который сформирована выгрузка — чуть больше суток.
Журналы «Публикации URL» и «Проброса TCP порта»
Журнал этих услуг высылаются по электронной почте пользователя со страницы настройки соответствующей услуги. В архиве zip находится текстовый файл, содержащий лог обращений из Интернет. Период времени, за который сформирована выгрузка — чуть больше суток.
Публикация URL
Пример записи:
Mar 17 23:48:03 [6997]: 112.19.11.122:57692 [17/Mar/2021:23:48:03.563] http-in~ Octopus-raspberry/Octopus-raspberry 167/0/56/64/295 200 3496 — — —- 106/26/0/1/0 0/0 «GET / HTTP/1.1«
- Mar 17 23:48:03 — дата записи в логе.
- [6997] — номер процесса на сервере.
- 112.19.11.122:57692 — адрес источника:порт источника.
- [17/Mar/2021:23:48:03.563] — дата обращения.
- http-in~ — логическое имя на сервере.
- Octopus-raspberry/Octopus-raspberry — логическое имя получателя (пользователя).
- 167/0/56/64/295 — служебные данные сервера.
- 200 — код статуса HTTP обращения (200 — OK).
- 3496 — количество байт переданных в сторону пользователя, включая заголовки HTTP.
- 106/26/0/1/0 0/0 — служебные данные сервера.
- GET / HTTP/1.1 — HTTP запрос.
В этом примере, статус 200 означает, что сервер успешно выполнил HTTP запрос GET / — то есть получение главной страницы ресурса.
Из часто встречающихся статусов:
- 503 означает, что серверу VPNKI не удалось связаться с вашим ресурсом. Причиной этого может быть отсутствие VPN соединения в этот момент. Или что-то пошло не так с маршрутами к серверу.
- 404 означает, что запрошенный документ на сервере отсутствует.
Проброс TCP порта
Пример записи.
Mar 17 23:48:04 [6997]: 112.19.11.122:58428 [17/Mar/2021:23:46:27.455] direct-26153-Octopus direct-26153-Octopus/direct-Octopus 1/82/96593 2248 — 105/79/79/79/0 0/0
- Mar 17 23:48:04 — дата записи в логе.
- [6997] — номер процесса на сервере.
- 112.19.11.122:58428 — адрес источника:порт источника.
- [17/Mar/2021:23:46:27.455] — дата обращения.
- direct-26153-Octopus — логическое имя на сервере.
- direct-26153-Octopus/direct-Octopus — логическое имя получателя (пользователя).
- 1/82/96593 — служебные данные сервера.
- 2248 — количество байт переданных в сторону пользователя.
- 105/79/79/79/0 0/0 — служебные данные сервера.
Дополнительно стоит отметить, что при использовании «Публикации URL» наша система передает в сторону вашего оборудования заполненное поле HTTP заголовка X-Forwarded-For. Чуть больше информации здесь.
*** Если вдруг что-то не получилось, обращайтесь на Форум.
ЕЩЕ О ВОЗМОЖНОСТЯХ СИСТЕМЫ
Кроме работы системы иногда мы публикуем различные материалы об ИТ для дома в разделе «Блог ДОИТ». Вы можете ознакомиться с настройками оборудования и VPN соединений для решения различных задач. Например:
- Немного более подробно про IP адрес можно прочитать в разделе «О технологиях» на нашем сайте.
- Про VPN и протоколы.
- Про видеонаблюдение на даче можно почитать в Блоге блоге нашего сайта.
- Про использование нейросети на базе Tensorflow для видеоаналитики на даче можно почитать в блоге нашего сайта.
- Про удаленный доступ к компьютеру.
- Про удаленный доступ к камере.
With the VPN client, you must use the Event Viewer to read Microsoft VPN logs.
- Click the “Start” button on your Windows desktop and right-click “Computer.”
- Click the “Manage” option.
- Click “Event Viewer.”
- Click the “Windows Logs” entry, then click “Application” in the panel on the right.
How do I get VPN logs?
Collect VPN Logs
- Right click on the Receiver icon and go to Advance Preferences:
- Right click on Netscaler Gateway Settings and hit open:
- Go to Configuration and enable debug logging and hit save.
- Now Connect to the VPN and duplicate the issue you are facing.
What do VPN logs show?
VPN logs are data that providers store about the way you use their VPN service. They can either be usage logs which really violate your privacy, or connection logs which might put your privacy at risk if they store your IP address. Overall, it’s best to use a service with no VPN logging.
Where are routing and remote access logs?
RRAS log files are written to the %windir%\tracing folder. Use this procedure to control the amount of detail that RRAS writes to the log files. Membership in the local Administrators group, or equivalent, is the minimum required to complete this procedure.
Where are AnyConnect logs?
Session Logs
- From the Applications folder, click the AnyConnect VPN icon to open the user interface. A new pane labeled Cisco Anyconnect VPN Client will pop up.
- Select Connection log.
How do I find my VPN log on Windows 10?
To do so:
- Right-click the Dialup Networking folder, and then click Properties.
- Click the Networking tab, and then click to select the Record a log file for this connection check box.
Where are VPN logs stored?
There are relevant log files in \WINDOWS\system32\LogFiles that may help. There is also system information available from the Event Viewer ( Run > eventvwr.exe OR Control Panel > Admin Tools > Event Viewer ) and look for System logs.
Do VPNS have to keep logs?
Most VPN providers claim they don’t keep logs — but that’s impossible to test without risking your security. If you find out the VPN you’re testing does keep logs after you sign up, it already has your data on file.
Is VPN traceable?
Yes. VPN’s (most) keep records of all your traffic (even though many claim they don’t, laws in many nations prohibit them from destroying them). Not to mention if malware is placed on your machine then your real IP is easily gained which the VPN cannot do anything about.
Can a VPN be traced back to me?
Can I be tracked if I use a VPN? No, your web traffic and IP address can’t be tracked anymore. A premium quality VPN encrypts data and hides your IP address by routing your activity through a VPN server; even if someone tries to track you, all they’ll see is the VPN server’s IP address and complete gibberish.
Where are VPN logs in Event Viewer?
What is Ras log?
The RAS log contains error, trace, and informational records , which are referred to as RAS messages. RAS messages for daemons that are down and jobs that are being rejected or vacated are always logged. These trace and informational messages are also logged in the RAS log.
How to read Microsoft VPN logs on Windows 10?
With the VPN client, you must use the Event Viewer to read Microsoft VPN logs. Click the “Start” button on your Windows desktop and right-click “Computer.” Click the “Manage” option. Click “Event Viewer.” Click the “Windows Logs” entry, then click “Application” in the panel on the right. Locate the source entries for the “RASClient” in the list.
How do I configure a VPN on a Windows Server?
Click Start, point to Administrative Tools, and then click Routing and Remote Access. Double-click the server object, right-click Ports, and then click Properties. In the Ports Properties dialog box, click WAN Miniport (PPTP) > Configure. In the Maximum ports box, type the number of VPN connections that you want to permit.
Where can I find the PPP log file for Windows 10?
Right-click the Dialup Networking folder, and then click Properties. Click the Networking tab, and then click to select the Record a log file for this connection check box. The PPP log file is C:\\Windows\\Ppplog.txt. It’s located in the C:\\Program Files\\Microsoft IPSec VPN folder.
How do I allow multiple VPN connections on a Windows Server?
Double-click the server object, right-click Ports, and then click Properties. In the Ports Properties dialog box, click WAN Miniport (PPTP) > Configure. In the Maximum ports box, type the number of VPN connections that you want to permit. Click OK > OK, and then close Routing and Remote Acces s.