В операционной системе Windows 10 настроить VPN-подключение по протоколу L2TP не составит большого труда — достаточно выполнить все действия, как показано на картинках, и уже через минуту вы сможете анонимно посещать любые сайты, обойти блокировку Вконтакте, безопасно использовать бесплатный Wi-Fi.
1
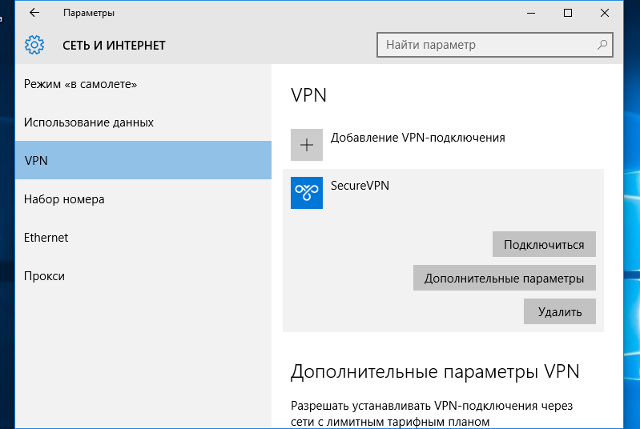
Кликнуть на иконке сетевого подключения в системном трее, и в появившемся окне выбрать Сетевые параметры.
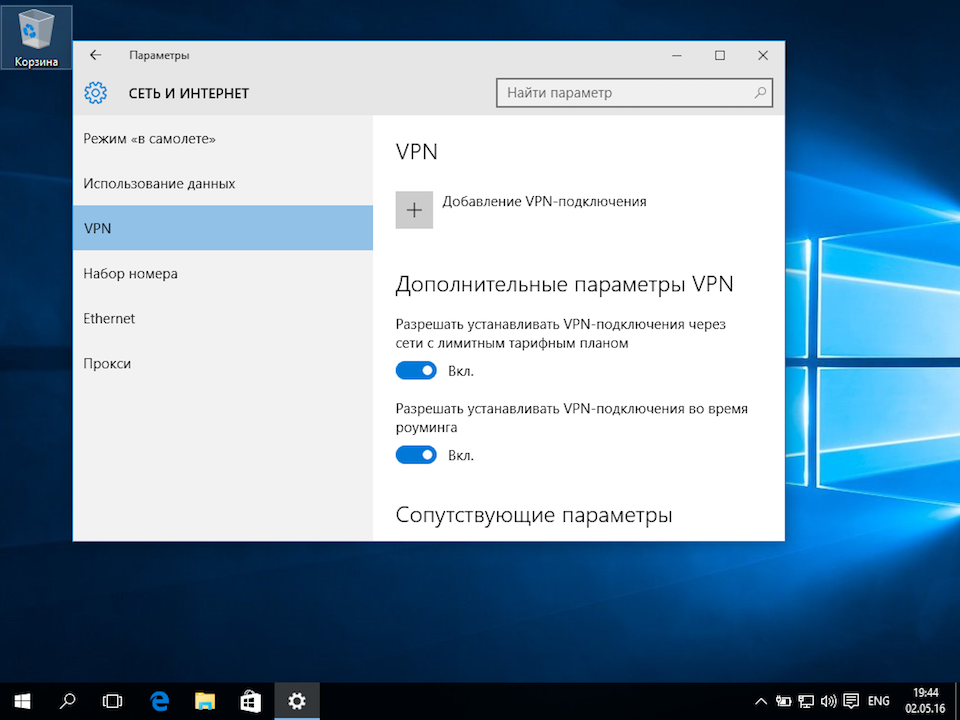
Далее
4
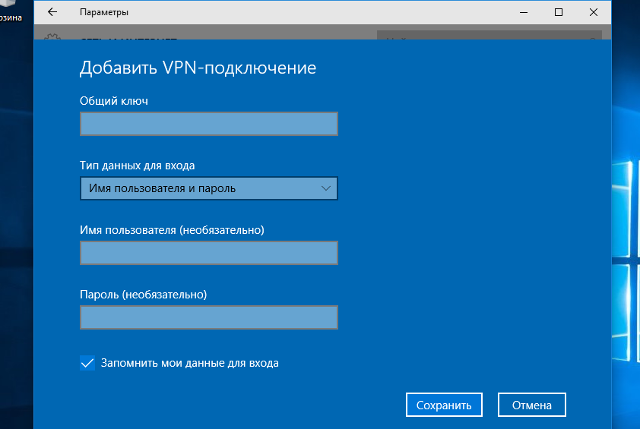
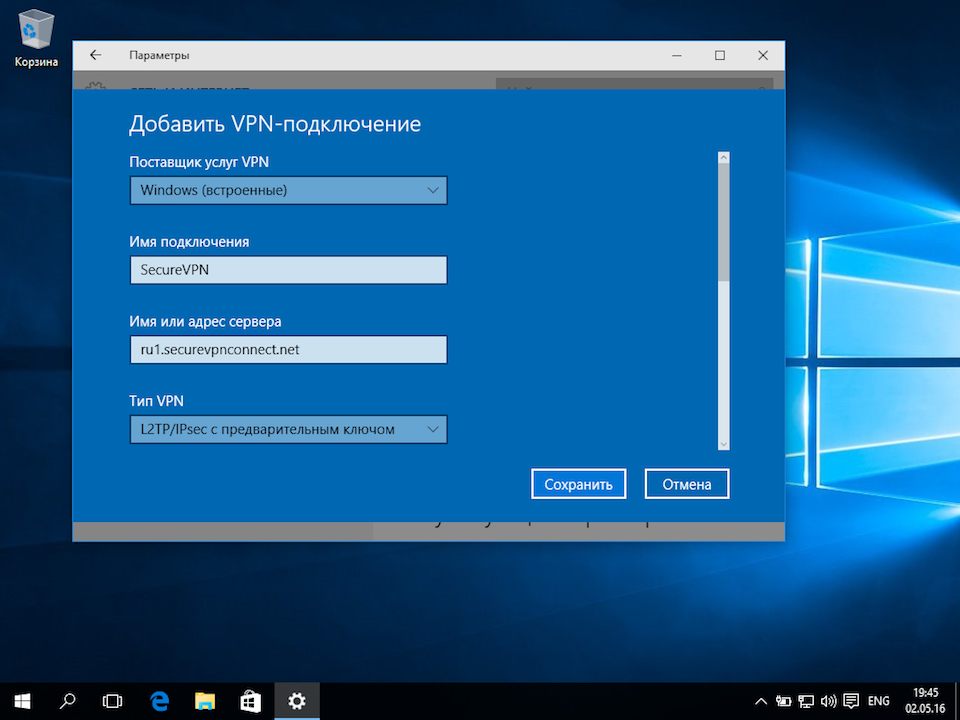
Указать идентификационные данные:
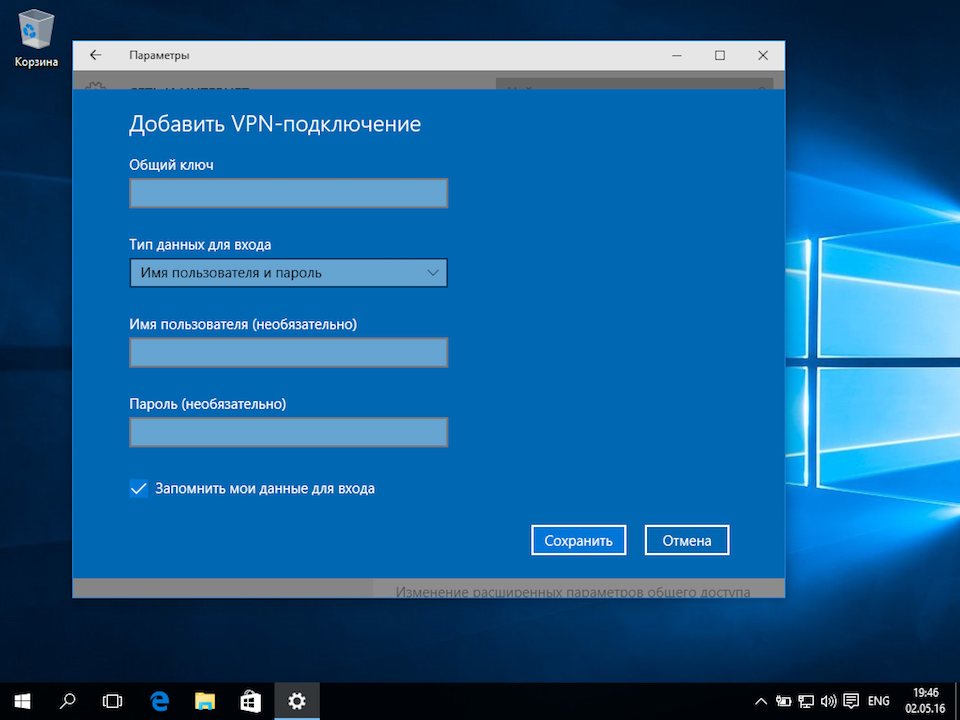
- Общий ключ — a-secure-psk
- Тип данных для входа — Имя пользователя и пароль
- Имя пользователя — username
- Пароль — password
Для завершения настройки нажать Сохранить.
Важное замечание: имя пользователя и пароль находятся в файле readme.txt, отправленном на Вашу почту после заказа подписки.
Далее
a-secure-psk
username
password
5
Для подключения выбрать только что созданное соединение, и нажать кнопку Подключиться.
Далее
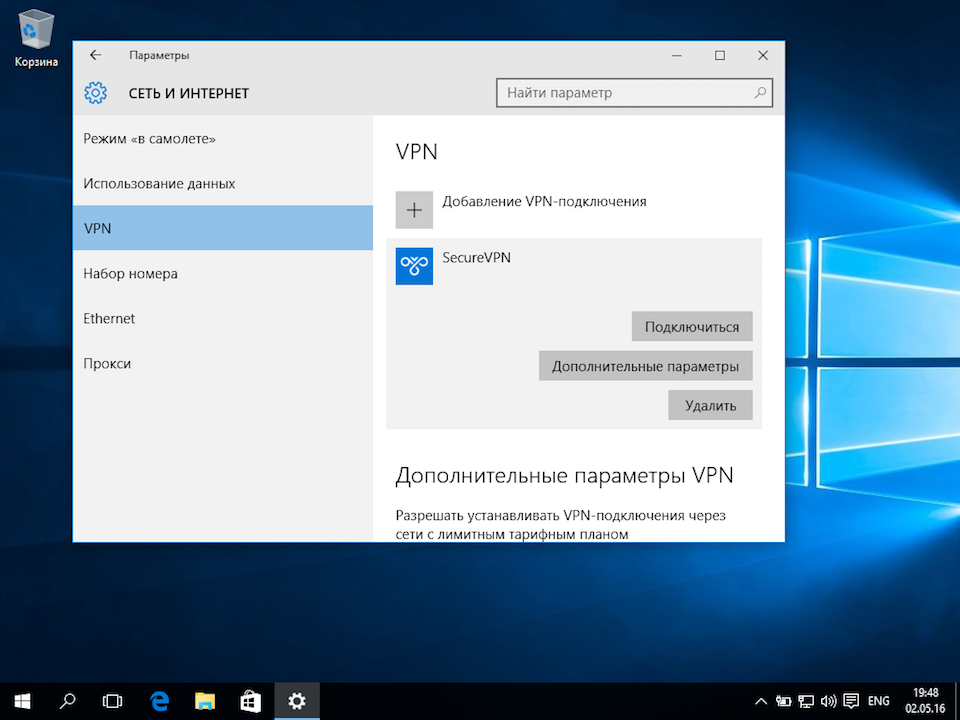
6
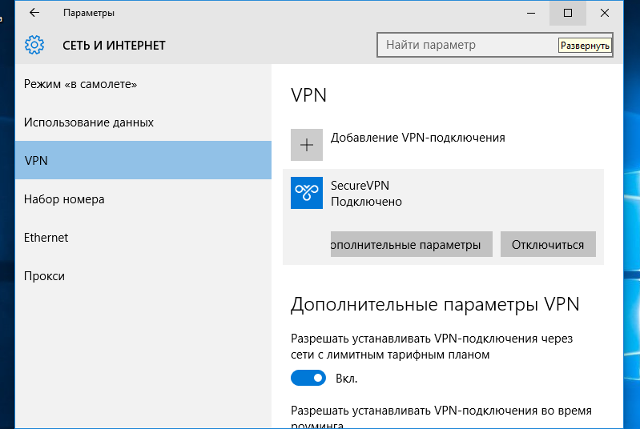
Соединение будет установлено через некоторое время. Для отключения нажать Отключиться.
Далее
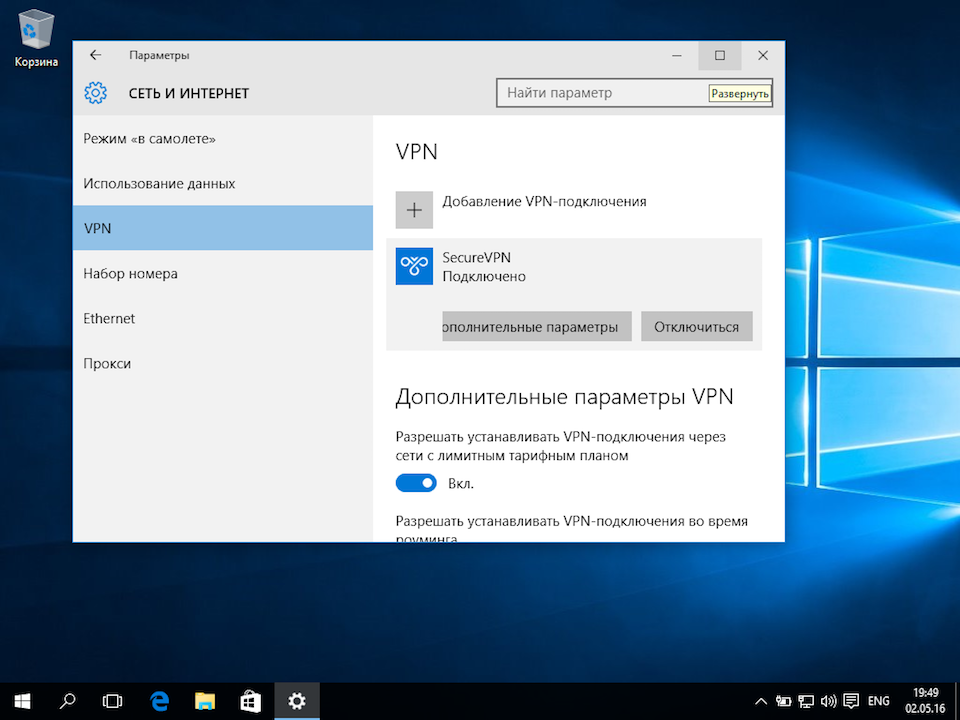
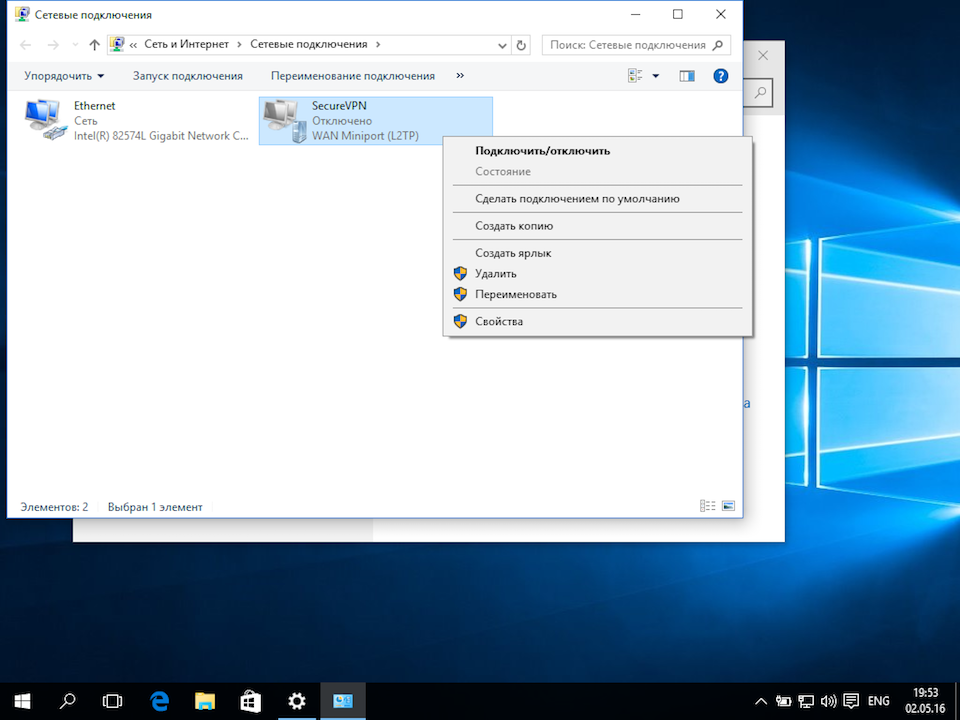
8
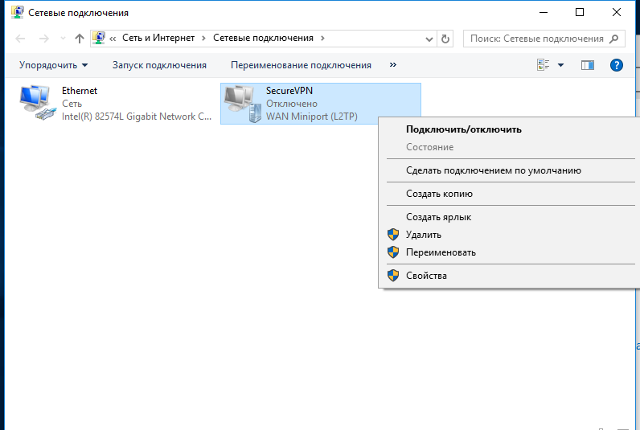
В открывшемся окне Сетевые подключения кликнуть правой кнопкой на созданном подключении, и выбрать Свойства.
Далее
ADEO Imaging OÜ
The cloud spirit…
Setup and configure L2TP/IPSec-PSK VPN on Windows 10
Attention! In order to get L2TP/IPSec working correctly with Windows, it is necessary to make changes to the registry (add a parameter). This problem is listed on the official Microsoft website https://support.microsoft.com/en-us/kb/926179. This procedure will be described below in (1) of this manual. If you are not ready to make changes to the Windows registry, then you can set up VPN with PPTP protocol (see PPTP settings here), which not required the modification of the registry.
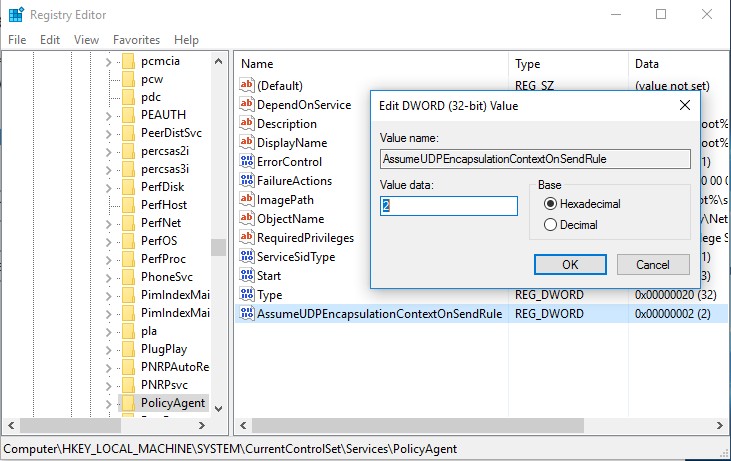
1. Making changes to the Windows registry (Administrative rights):
1) Run regedit with administrative privileges and locate the section HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PolicyAgent
2) Create DWORD (32 bit) parameter AssumeUDPEncapsulationContextOnSendRule and set value 2 for it.
3). Restart Windows!!!
2. After registry has been modified and computer was restarted, we can start to configure L2TP/IPSec connection. Click «Start» button and select «Settings» icon:
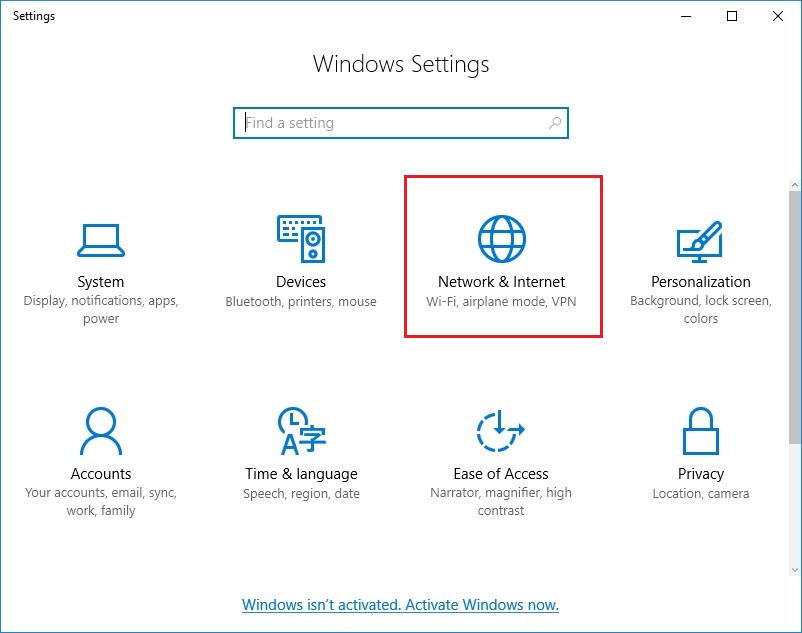
3. Click «Network & Internet»:
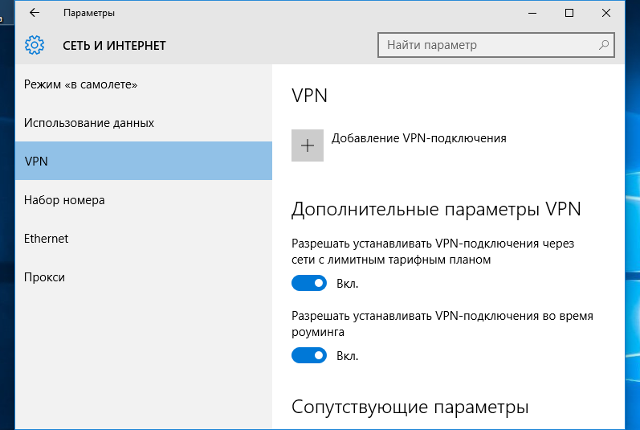
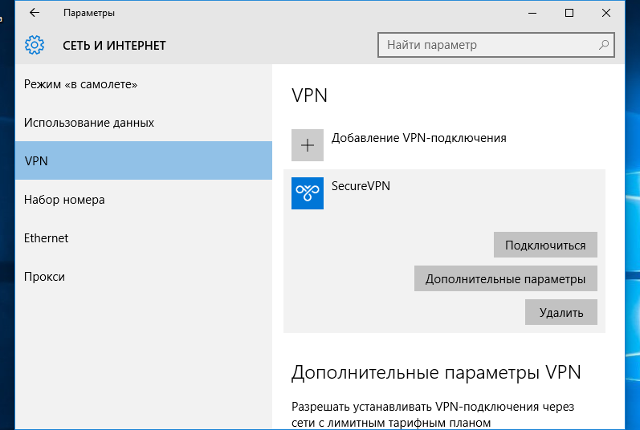
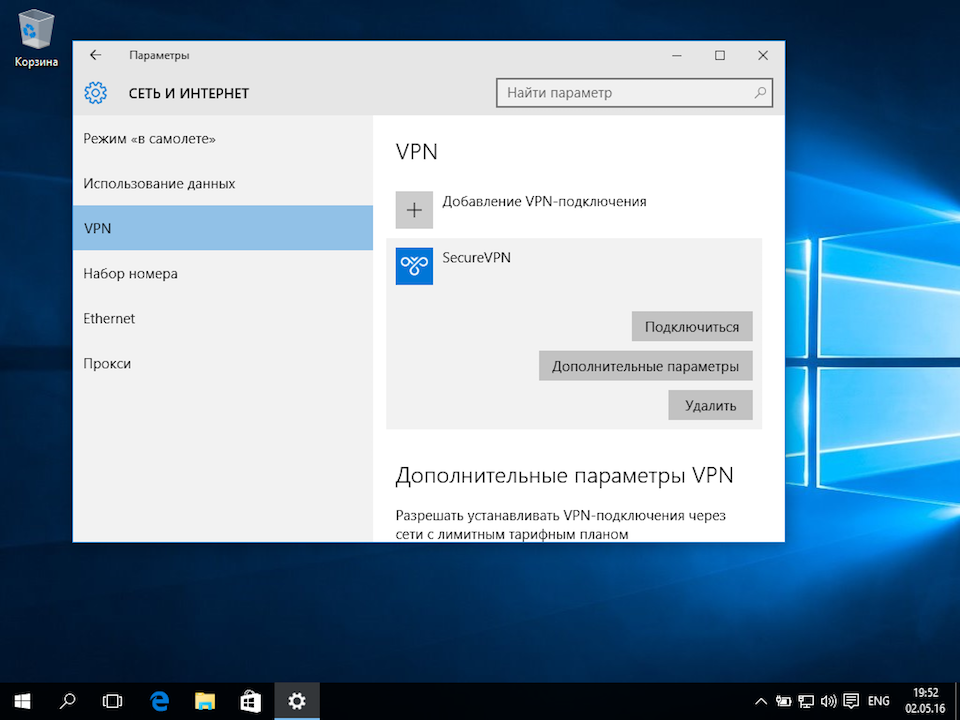
4. Click «VPN»:
5. Click «Add a VPN connection»:
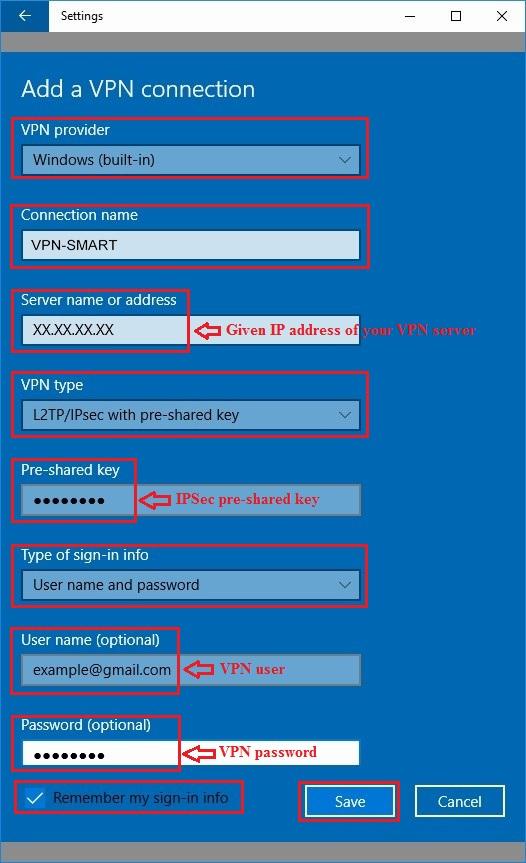
6. On the next page:
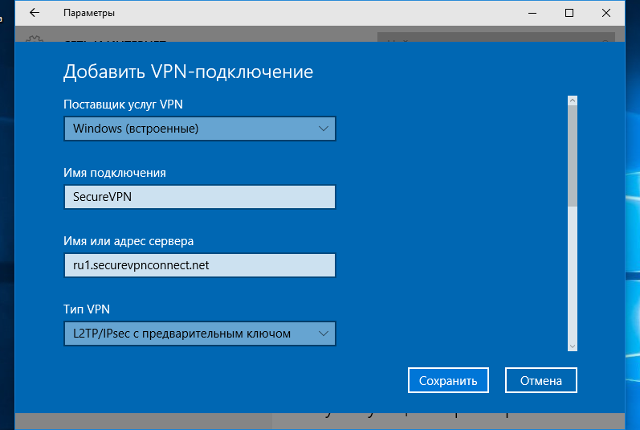
* in the list «VPN provider» select «Windows (built-in)»
* in the «Connection name» field, enter the name of the connection, for example, «VPN-SMART»
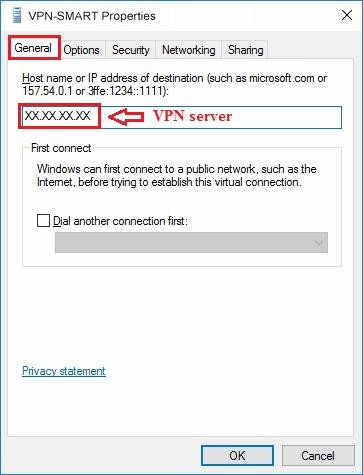
* in the field «Server name or address» enter given ip-address of your VPN server
* in the list «VPN type» select «L2TP/IPSec with pre-shared key»
* in the field «Pre-shared key» enter given IPSec pre-shared key
* in the list «Type of sign-in info» select «User name and password»
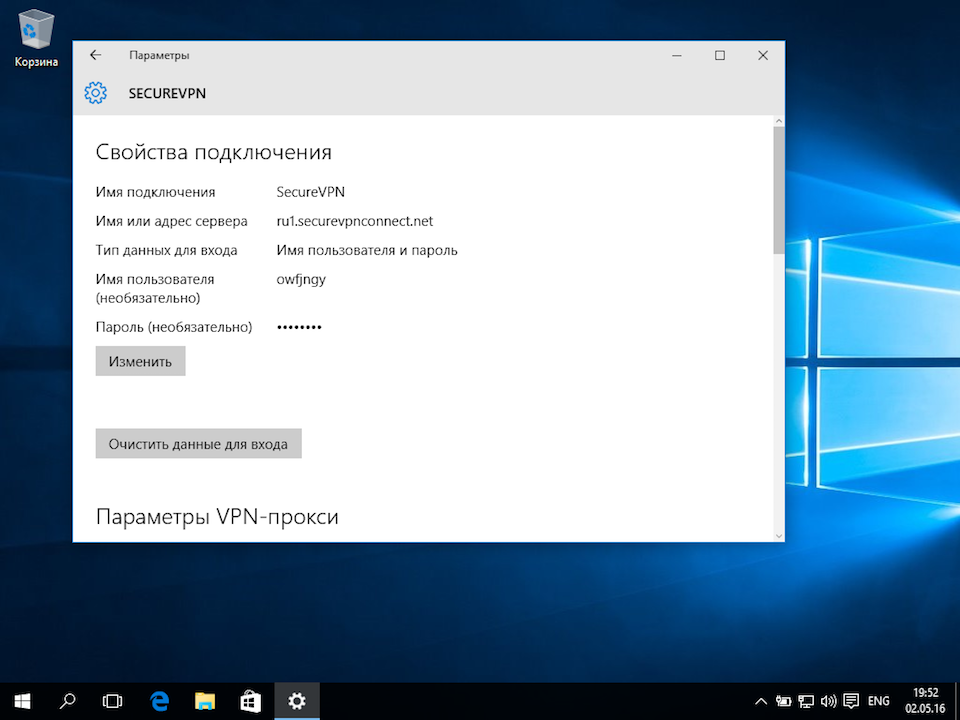
* in fields «User name (optional)» and «Password (optional)» enter given VPN user name (e-mail) and VPN password
* Check «Remember my sign-in info» checkbox and click «Save» button:
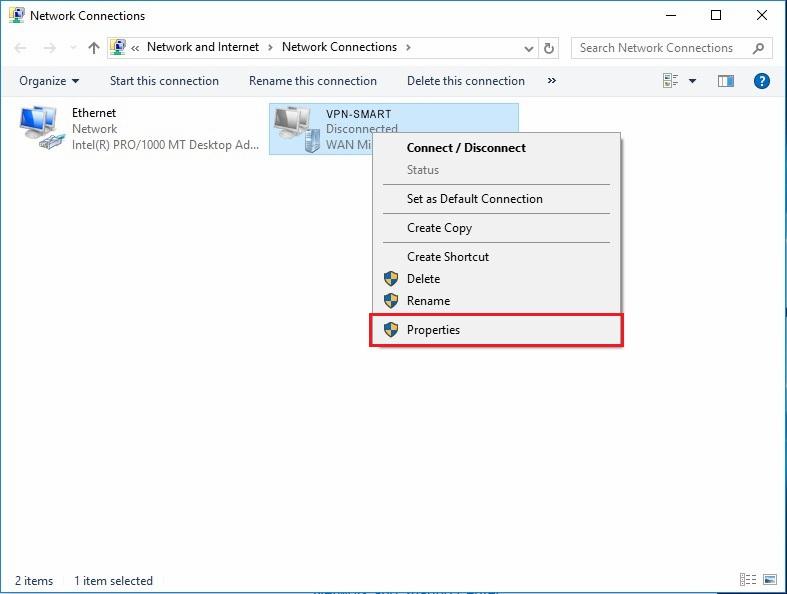
7. At this stage, a newly created connection VPN-SMART is ready, but network adapter is not yet configured. Do not connect now, please click «Change adapter options»:
8. In context menu of a newly created connection VPN-SMART click «Properties»:
9. Check again the given ip-address of your VPN Server on «General» tab:
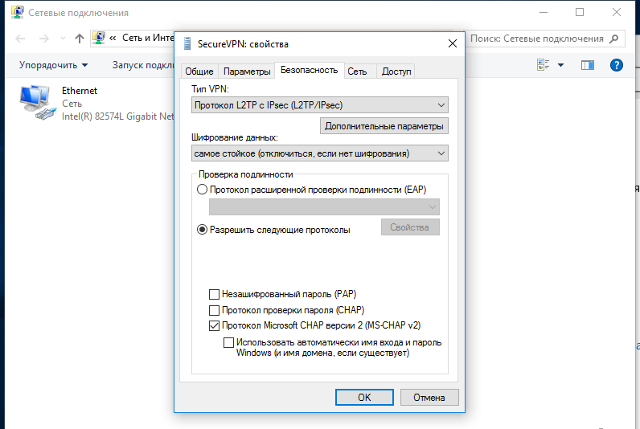
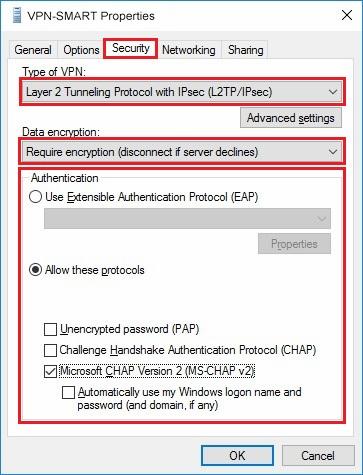
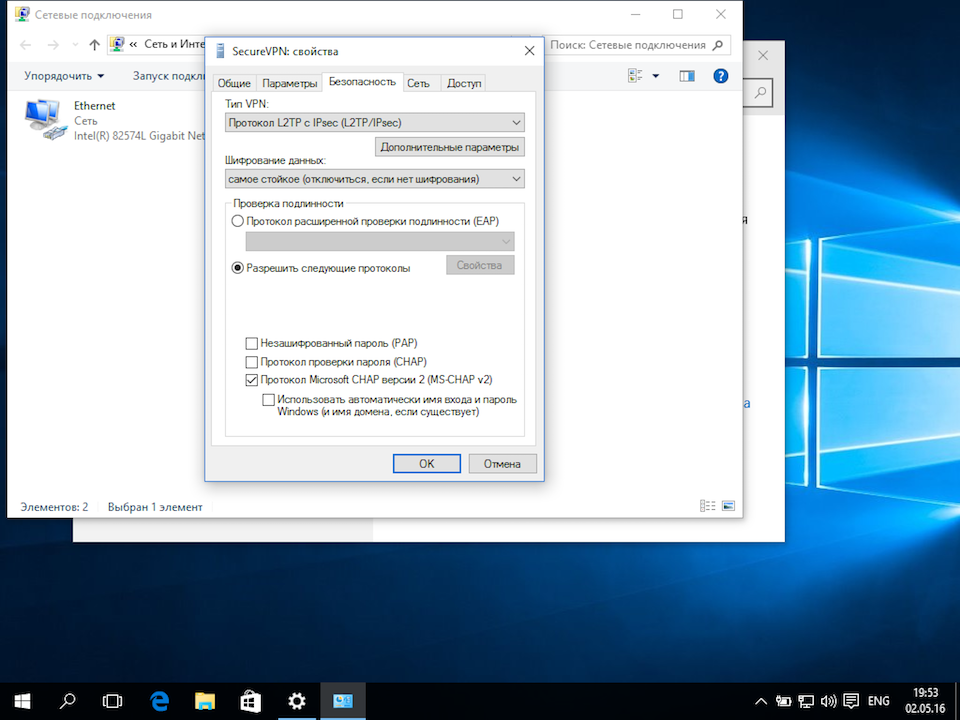
10. Go to «Security» tab. Set Type of VPN as «Layer 2 Tunneling Protocol with IPsec (L2TP/IPSec)» and Data encryption as «Require encryption (disconnect if server declines)». Then check «Microsoft CHAP version 2 (MS-CHAP v2)» checkbox and click «ОК». Also close the previous «Network Connections» window:
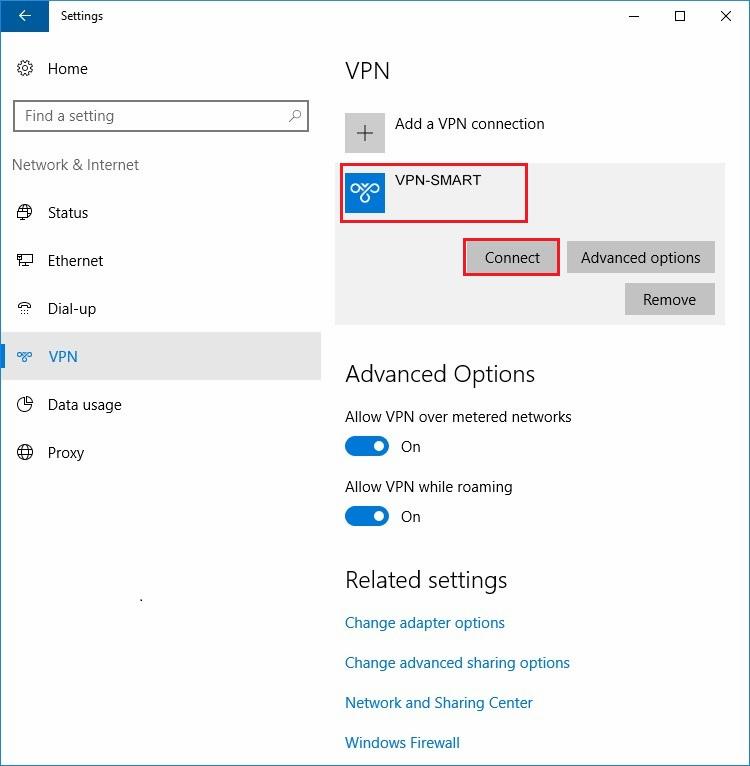
11. Now everything is ready. You can connect to VPN server. To get connected please click «Connect» button in the window «Settings->Network & Internet». If buttons Connect, Advanced Options and Remove are not visible then click «VPN-SMART» to display them:
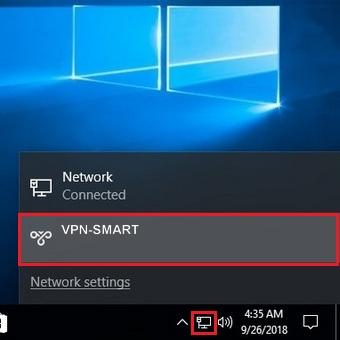
From now, after VPN-connection has already been created, it can be turned on/off from «Network» icon:
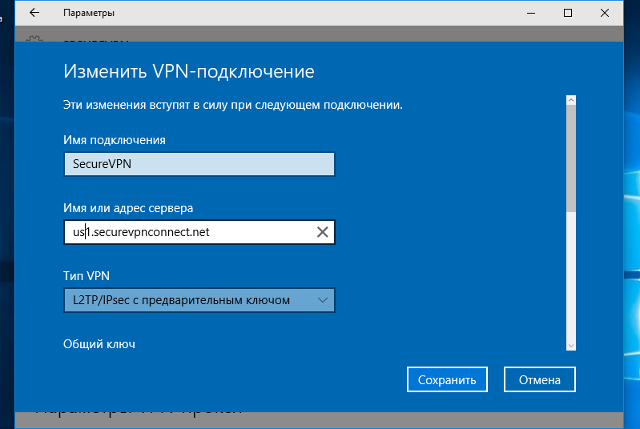
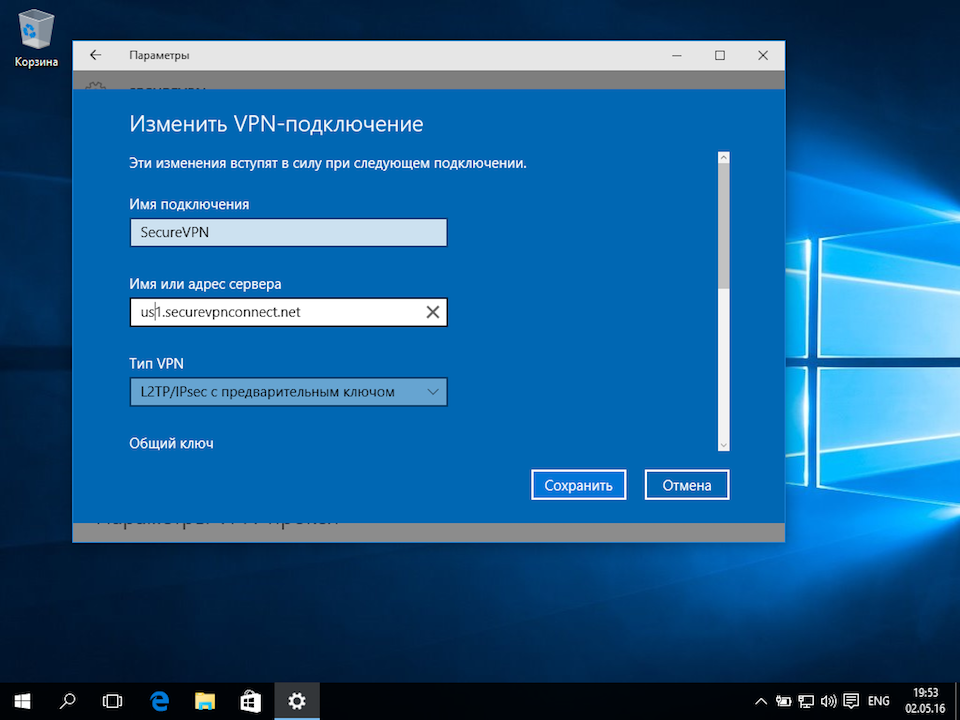
Для L2TP/IPsec с общим ключом
Важно: L2TP IPsec клиенты, находящиеся за одним NAT’ом, могут испытывать проблемы подключения если их более одного. Решить проблему может помочь
инструкция
. Рекомендуем вместо L2TP IPsec использовать IKEv2 IPsec.
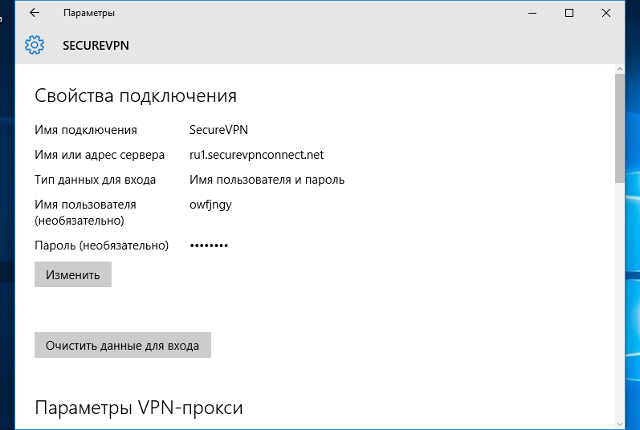
Имя подключения — название создаваемого подключения;
-
Имя или адрес сервера — адрес VPN-сервера;
-
Тип VPN — Протокол L2TP/IPsec с общим ключом;
-
Общий ключ — значение строки PSK в разделе Пользователи -> VPN-подключение -> Основное -> Подключение по L2TP/IPsec;
-
Тип данных для входа — Имя пользователя и пароль;
-
Имя пользователя — имя пользователя, которому разрешено подключение по VPN;
-
Пароль — пароль пользователя.
При настройке подключения по VPN из сети Интернет, в свойствах VPN-подключения нужно указать следующие параметры:
-
Перейдите в Настройки параметров адаптера;
-
Нажмите на созданное подключение правой кнопкой мыши и выберите Свойства;
-
Перейдите во вкладку Безопасность и установите:
-
Шифрование данных — обязательное (отключиться, если нет шифрования)
-
Протокол расширенной проверки подлинности (EAP) — Microsoft защищенный пароль (EAP MSCHAPV2)
-
Если создается VPN-подключение к UTM через проброс портов, рекомендуем выполнить следующие действия:
-
1.
Откройте Редактор реестра;
-
2.
Перейдите в
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PolicyAgentи создайте DWORD-параметр с именем AssumeUDPEncapsulationContextOnSendRule и значением2;
-
1.
Неправильно указан логин или пароль пользователя. Часто при повторном соединении предлагается указать домен. Старайтесь создавать цифро-буквенные пароли, желательно на латинице для учетных записей. Если есть сомнения в этом пункте, то временно установите логин и пароль пользователю «user» и «123456».
-
2.
Для того, чтобы пакеты пошли через VPN-туннель, надо убедиться, что в настройках этого подключения стоит чекбокс Использовать основной шлюз в удалённой сети в разделе Настройка параметров адаптера -> Правой кнопкой мыши по подключению -> Свойства -> Сеть -> Свойства опции «Протокол Интернета версии 4 (TCP/IPv4)» ->Дополнительно. Если же маршрутизировать все пакеты в этот интерфейс не обязательно, то маршрут надо писать вручную.
-
3.
Подключение происходит через DNAT, т.е. внешний интерфейс Ideco UTM не имеет «белого» IP-адреса, а необходимые для работы порты (500 и 4500) «проброшены» на внешний интерфейс устройства, расположенного перед Ideco UTM и имеющего «белый» IP-адрес. В данном случае VPN-подключение либо вообще не будет устанавливаться, либо будут периодические обрывы. Решение — исключить устройство перед Ideco UTM и указать на внешнем интерфейсе Ideco UTM «белый» IP-адрес, к которому в итоге и будут осуществляться L2TP/IPsec-подключения. Либо используйте протокол SSTP, потому что его проще опубликовать с помощью проброса портов.
-
4.
Если в OC Windows 10 повторно подключиться по L2TP, но при этом использовать невалидный ключ PSK (введя его в дополнительных параметрах (скриншот ниже)), подключение все равно будет установлено успешно. Это связано с особенностями работы ОС.
Убедитесь, что локальная сеть (или адрес на сетевой карте) на удалённой машине не пересекается с локальной сетью организации. Если пересекается, то доступа к сети организации не будет (трафик по таблице маршрутизации пойдёт в физический интерфейс, а не в VPN). Адресацию необходимо менять.
Configure IPsec/L2TP VPN Clients
IPsec/L2TP is natively supported by Android, iOS, OS X, and Windows. There is no additional software to install. Setup should only take a few minutes. In case you are unable to connect, first check to make sure the VPN credentials were entered correctly.
- Platforms
- Windows
- OS X (macOS)
- Android
- iOS (iPhone/iPad)
- Chromebook
- Linux
- Troubleshooting
Windows
Windows 10 and 8.x
- Right-click on the wireless/network icon in your system tray.
- Select Open Network and Sharing Center. Or, if using Windows 10 version 1709 or newer, select Open Network & Internet settings, then on the page that opens, click Network and Sharing Center.
- Click Set up a new connection or network.
- Select Connect to a workplace and click Next.
- Click Use my Internet connection (VPN).
- Enter
Your VPN Server IPin the Internet address field. - Enter anything you like in the Destination name field, and then click Create.
- Return to Network and Sharing Center. On the left, click Change adapter settings.
- Right-click on the new VPN entry and choose Properties.
- Click the Security tab. Select «Layer 2 Tunneling Protocol with IPsec (L2TP/IPSec)» for the Type of VPN.
- Click Allow these protocols. Check the «Challenge Handshake Authentication Protocol (CHAP)» and «Microsoft CHAP Version 2 (MS-CHAP v2)» checkboxes.
- Click the Advanced settings button.
- Select Use preshared key for authentication and enter
Your VPN IPsec PSKfor the Key. - Click OK to close the Advanced settings.
- Click OK to save the VPN connection details.
Note: A one-time registry change is required before connecting. See details below.
Alternatively, instead of following the steps above, you may create the VPN connection using these Windows PowerShell commands. Replace Your VPN Server IP and Your VPN IPsec PSK with your own values, enclosed in single quotes:
# Disable persistent command history Set-PSReadlineOption –HistorySaveStyle SaveNothing # Create VPN connection Add-VpnConnection -Name 'My IPsec VPN' -ServerAddress 'Your VPN Server IP' -L2tpPsk 'Your VPN IPsec PSK' -TunnelType L2tp -EncryptionLevel Required -AuthenticationMethod Chap,MSChapv2 -Force -RememberCredential -PassThru # Ignore the data encryption warning (data is encrypted in the IPsec tunnel)
Windows 7, Vista and XP
- Click on the Start Menu and go to the Control Panel.
- Go to the Network and Internet section.
- Click Network and Sharing Center.
- Click Set up a new connection or network.
- Select Connect to a workplace and click Next.
- Click Use my Internet connection (VPN).
- Enter
Your VPN Server IPin the Internet address field. - Enter anything you like in the Destination name field.
- Check the Don’t connect now; just set it up so I can connect later checkbox.
- Click Next.
- Enter
Your VPN Usernamein the User name field. - Enter
Your VPN Passwordin the Password field. - Check the Remember this password checkbox.
- Click Create, and then Close.
- Return to Network and Sharing Center. On the left, click Change adapter settings.
- Right-click on the new VPN entry and choose Properties.
- Click the Options tab and uncheck Include Windows logon domain.
- Click the Security tab. Select «Layer 2 Tunneling Protocol with IPsec (L2TP/IPSec)» for the Type of VPN.
- Click Allow these protocols. Check the «Challenge Handshake Authentication Protocol (CHAP)» and «Microsoft CHAP Version 2 (MS-CHAP v2)» checkboxes.
- Click the Advanced settings button.
- Select Use preshared key for authentication and enter
Your VPN IPsec PSKfor the Key. - Click OK to close the Advanced settings.
- Click OK to save the VPN connection details.
Note: This one-time registry change is required if the VPN server and/or client is behind NAT (e.g. home router).
To connect to the VPN: Click on the wireless/network icon in your system tray, select the new VPN entry, and click Connect. If prompted, enter Your VPN Username and Password, then click OK. You can verify that your traffic is being routed properly by looking up your IP address on Google. It should say «Your public IP address is Your VPN Server IP«.
If you get an error when trying to connect, see Troubleshooting.
OS X
- Open System Preferences and go to the Network section.
- Click the + button in the lower-left corner of the window.
- Select VPN from the Interface drop-down menu.
- Select L2TP over IPSec from the VPN Type drop-down menu.
- Enter anything you like for the Service Name.
- Click Create.
- Enter
Your VPN Server IPfor the Server Address. - Enter
Your VPN Usernamefor the Account Name. - Click the Authentication Settings button.
- In the User Authentication section, select the Password radio button and enter
Your VPN Password. - In the Machine Authentication section, select the Shared Secret radio button and enter
Your VPN IPsec PSK. - Click OK.
- Check the Show VPN status in menu bar checkbox.
- (Important) Click the Advanced button and make sure the Send all traffic over VPN connection checkbox is checked.
- Click the TCP/IP tab, and make sure Link-local only is selected in the Configure IPv6 section.
- Click OK to close the Advanced settings, and then click Apply to save the VPN connection information.
To connect to the VPN: Use the menu bar icon, or go to the Network section of System Preferences, select the VPN and choose Connect. You can verify that your traffic is being routed properly by looking up your IP address on Google. It should say «Your public IP address is Your VPN Server IP«.
If you get an error when trying to connect, see Troubleshooting.
Android
- Launch the Settings application.
- Tap More… in the Wireless & Networks section.
- Tap VPN.
- Tap Add VPN Profile or the + icon at top-right of screen.
- Enter anything you like in the Name field.
- Select L2TP/IPSec PSK in the Type drop-down menu.
- Enter
Your VPN Server IPin the Server address field. - Enter
Your VPN IPsec PSKin the IPSec pre-shared key field. - Tap Save.
- Tap the new VPN connection.
- Enter
Your VPN Usernamein the Username field. - Enter
Your VPN Passwordin the Password field. - Check the Save account information checkbox.
- Tap Connect.
Once connected, you will see a VPN icon in the notification bar. You can verify that your traffic is being routed properly by looking up your IP address on Google. It should say «Your public IP address is Your VPN Server IP«.
If you get an error when trying to connect, see Troubleshooting.
iOS
- Go to Settings -> General -> VPN.
- Tap Add VPN Configuration….
- Tap Type. Select L2TP and go back.
- Tap Description and enter anything you like.
- Tap Server and enter
Your VPN Server IP. - Tap Account and enter
Your VPN Username. - Tap Password and enter
Your VPN Password. - Tap Secret and enter
Your VPN IPsec PSK. - Make sure the Send All Traffic switch is ON.
- Tap Done.
- Slide the VPN switch ON.
Once connected, you will see a VPN icon in the status bar. You can verify that your traffic is being routed properly by looking up your IP address on Google. It should say «Your public IP address is Your VPN Server IP«.
If you get an error when trying to connect, see Troubleshooting.
Chromebook
- If you haven’t already, sign in to your Chromebook.
- Click the status area, where your account picture appears.
- Click Settings.
- In the Internet connection section, click Add connection.
- Click Add OpenVPN / L2TP.
- Enter
Your VPN Server IPfor the Server hostname. - Enter anything you like for the Service name.
- Make sure Provider type is L2TP/IPSec + pre-shared key.
- Enter
Your VPN IPsec PSKfor the Pre-shared key. - Enter
Your VPN Usernamefor the Username. - Enter
Your VPN Passwordfor the Password. - Click Connect.
Once connected, you will see a VPN icon overlay on the network status icon. You can verify that your traffic is being routed properly by looking up your IP address on Google. It should say «Your public IP address is Your VPN Server IP«.
If you get an error when trying to connect, see Troubleshooting.
Linux
Ubuntu Linux
Ubuntu 18.04 (and newer) users can install the network-manager-l2tp-gnome package, then configure the IPsec/L2TP VPN client using the GUI. Ubuntu 16.04 and 14.04 users may need to add the nm-l2tp PPA, read more here.
- Go to Settings -> Network -> VPN. Click the + button.
- Select Layer 2 Tunneling Protocol (L2TP).
- Enter anything you like in the Name field.
- Enter
Your VPN Server IPfor the Gateway. - Enter
Your VPN Usernamefor the User name. - Right-click the ? in the Password field, select Store the password only for this user.
- Enter
Your VPN Passwordfor the Password. - Leave the NT Domain field blank.
- Click the IPsec Settings… button.
- Check the Enable IPsec tunnel to L2TP host checkbox.
- Leave the Gateway ID field blank.
- Enter
Your VPN IPsec PSKfor the Pre-shared key. - Expand the Advanced section.
- Enter
aes128-sha1-modp2048!for the Phase1 Algorithms. - Enter
aes128-sha1-modp2048!for the Phase2 Algorithms. - Click OK, then click Add to save the VPN connection information.
- Turn the VPN switch ON.
Once connected, you can verify that your traffic is being routed properly by looking up your IP address on Google. It should say «Your public IP address is Your VPN Server IP«.
Fedora and CentOS
Fedora 28 (and newer) and CentOS 7 users can connect using the faster IPsec/XAuth mode.
Other Linux
First check here to see if the network-manager-l2tp and network-manager-l2tp-gnome packages are available for your Linux distribution. If yes, install them (select strongSwan) and follow the instructions above. Alternatively, you may configure Linux VPN clients using the command line.
Troubleshooting
- Windows Error 809
- Windows Error 628
- Windows 10 upgrades
- Windows 8/10 DNS leaks
- macOS VPN traffic
- iOS/Android sleep mode
- Android 6 and above
- Chromebook issues
- Other errors
- Additional steps
Windows Error 809
The network connection between your computer and the VPN server could not be established because the remote server is not responding.
To fix this error, a one-time registry change is required because the VPN server and/or client is behind NAT (e.g. home router). Download and import the .reg file below, or run the following from an elevated command prompt. You must reboot your PC when finished.
-
For Windows Vista, 7, 8.x and 10 (download .reg file)
REG ADD HKLM\SYSTEM\CurrentControlSet\Services\PolicyAgent /v AssumeUDPEncapsulationContextOnSendRule /t REG_DWORD /d 0x2 /f -
For Windows XP ONLY (download .reg file)
REG ADD HKLM\SYSTEM\CurrentControlSet\Services\IPSec /v AssumeUDPEncapsulationContextOnSendRule /t REG_DWORD /d 0x2 /f
Although uncommon, some Windows systems disable IPsec encryption, causing the connection to fail. To re-enable it, run the following command and reboot your PC.
-
For Windows XP, Vista, 7, 8.x and 10 (download .reg file)
REG ADD HKLM\SYSTEM\CurrentControlSet\Services\RasMan\Parameters /v ProhibitIpSec /t REG_DWORD /d 0x0 /f
Windows Error 628
The connection was terminated by the remote computer before it could be completed.
To fix this error, please follow these steps:
- Right-click on the wireless/network icon in system tray, select Open Network and Sharing Center.
- On the left, click Change adapter settings. Right-click on the new VPN and choose Properties.
- Click the Security tab. Select «Layer 2 Tunneling Protocol with IPsec (L2TP/IPSec)» for Type of VPN.
- Click Allow these protocols. Make sure the «Challenge Handshake Authentication Protocol (CHAP)» checkbox is checked.
- Click the Advanced settings button.
- Select Use preshared key for authentication and enter
Your VPN IPsec PSKfor the Key. - Click OK to close the Advanced settings.
- Click OK to save the VPN connection details.
Windows 10 upgrades
After upgrading Windows 10 version (e.g. from 1709 to 1803), you may need to re-apply the fix above for Windows Error 809 and reboot.
Windows 8/10 DNS leaks
Windows 8.x and 10 use «smart multi-homed name resolution» by default, which may cause «DNS leaks» when using the native IPsec VPN client if your DNS servers on the Internet adapter are from the local network segment. To fix, you may either disable smart multi-homed name resolution, or configure your Internet adapter to use DNS servers outside your local network (e.g. 8.8.8.8 and 8.8.4.4). When finished, clear the DNS cache and reboot your PC.
In addition, if your computer has IPv6 enabled, all IPv6 traffic (including DNS queries) will bypass the VPN. Learn how to disable IPv6 in Windows.
macOS VPN traffic
OS X (macOS) users: If you can successfully connect using IPsec/L2TP mode, but your public IP does not show Your VPN Server IP, read the OS X section above and complete this step: Click the Advanced button and make sure the Send all traffic over VPN connection checkbox is checked. Then re-connect the VPN.
iOS/Android sleep mode
To save battery, iOS devices (iPhone/iPad) will automatically disconnect Wi-Fi shortly after the screen turns off (sleep mode). As a result, the IPsec VPN disconnects. This behavior is by design and cannot be configured. If you need the VPN to auto-reconnect when the device wakes up, try OpenVPN instead, which has support for options such as «Reconnect on Wakeup» and «Seamless Tunnel».
Android devices will also disconnect Wi-Fi shortly after entering sleep mode, unless the option «Keep Wi-Fi on during sleep» is enabled. This option is no longer available in Android 8 (Oreo). Alternatively, you may try enabling the «Always-on VPN» option to stay connected. Learn more here.
Android 6 and above
If you are unable to connect using Android 6 or above:
- Tap the «Settings» icon next to your VPN profile. Select «Show advanced options» and scroll down to the bottom. If the option «Backward compatible mode» exists (see image below), enable it and reconnect the VPN. If not, try the next step.
- Edit
/etc/ipsec.confon the VPN server. Findsha2-truncbug=yesand replace it withsha2-truncbug=no. Save the file and runservice ipsec restart(Ref).
Chromebook issues
Chromebook users: If you are unable to connect, try these steps: Edit /etc/ipsec.conf on the VPN server. Find the line phase2alg=... and append ,aes_gcm-null at the end. Save the file and run service ipsec restart.
Other errors
If you encounter other errors, refer to the links below:
- http://www.tp-link.com/en/faq-1029.html
- https://documentation.meraki.com/MX-Z/Client_VPN/Troubleshooting_Client_VPN#Common_Connection_Issues
- https://blogs.technet.microsoft.com/rrasblog/2009/08/12/troubleshooting-common-vpn-related-errors/
Additional steps
Please try these additional troubleshooting steps:
First, restart services on the VPN server:
service ipsec restart service xl2tpd restart
If using Docker, run docker restart ipsec-vpn-server.
Then reboot your VPN client device, and retry the connection. If still unable to connect, try removing and recreating the VPN connection, by following the instructions in this document. Make sure that the VPN credentials are entered correctly.
Check the Libreswan (IPsec) and xl2tpd logs for errors:
# Ubuntu & Debian grep pluto /var/log/auth.log grep xl2tpd /var/log/syslog # CentOS & RHEL grep pluto /var/log/secure grep xl2tpd /var/log/messages
Check status of the IPsec VPN server:
ipsec status ipsec verify
Show current established VPN connections:
ipsec whack --trafficstatus
Configure Linux VPN clients using the command line
Instructions below are based on the work of Peter Sanford. Commands must be run as root on your VPN client.
To set up the VPN client, first install the following packages:
# Ubuntu & Debian apt-get update apt-get -y install strongswan xl2tpd # CentOS & RHEL yum -y install epel-release yum --enablerepo=epel -y install strongswan xl2tpd # Fedora yum -y install strongswan xl2tpd
Create VPN variables (replace with actual values):
VPN_SERVER_IP='your_vpn_server_ip' VPN_IPSEC_PSK='your_ipsec_pre_shared_key' VPN_USER='your_vpn_username' VPN_PASSWORD='your_vpn_password'
Configure strongSwan:
cat > /etc/ipsec.conf <<EOF # ipsec.conf - strongSwan IPsec configuration file # basic configuration config setup # strictcrlpolicy=yes # uniqueids = no # Add connections here. # Sample VPN connections conn %default ikelifetime=60m keylife=20m rekeymargin=3m keyingtries=1 keyexchange=ikev1 authby=secret ike=aes128-sha1-modp2048! esp=aes128-sha1-modp2048! conn myvpn keyexchange=ikev1 left=%defaultroute auto=add authby=secret type=transport leftprotoport=17/1701 rightprotoport=17/1701 right=$VPN_SERVER_IP EOF cat > /etc/ipsec.secrets <<EOF : PSK "$VPN_IPSEC_PSK" EOF chmod 600 /etc/ipsec.secrets # For CentOS/RHEL & Fedora ONLY mv /etc/strongswan/ipsec.conf /etc/strongswan/ipsec.conf.old 2>/dev/null mv /etc/strongswan/ipsec.secrets /etc/strongswan/ipsec.secrets.old 2>/dev/null ln -s /etc/ipsec.conf /etc/strongswan/ipsec.conf ln -s /etc/ipsec.secrets /etc/strongswan/ipsec.secrets
Configure xl2tpd:
cat > /etc/xl2tpd/xl2tpd.conf <<EOF [lac myvpn] lns = $VPN_SERVER_IP ppp debug = yes pppoptfile = /etc/ppp/options.l2tpd.client length bit = yes EOF cat > /etc/ppp/options.l2tpd.client <<EOF ipcp-accept-local ipcp-accept-remote refuse-eap require-chap noccp noauth mtu 1280 mru 1280 noipdefault defaultroute usepeerdns connect-delay 5000 name $VPN_USER password $VPN_PASSWORD EOF chmod 600 /etc/ppp/options.l2tpd.client
The VPN client setup is now complete. Follow the steps below to connect.
Note: You must repeat all steps below every time you try to connect to the VPN.
Create xl2tpd control file:
mkdir -p /var/run/xl2tpd touch /var/run/xl2tpd/l2tp-control
Restart services:
service strongswan restart service xl2tpd restart
Start the IPsec connection:
# Ubuntu & Debian ipsec up myvpn # CentOS/RHEL & Fedora strongswan up myvpn
Start the L2TP connection:
echo "c myvpn" > /var/run/xl2tpd/l2tp-control
Run ifconfig and check the output. You should now see a new interface ppp0.
Check your existing default route:
Find this line in the output: default via X.X.X.X .... Write down this gateway IP for use in the two commands below.
Exclude your VPN server’s IP from the new default route (replace with actual value):
route add YOUR_VPN_SERVER_IP gw X.X.X.X
If your VPN client is a remote server, you must also exclude your Local PC’s public IP from the new default route, to prevent your SSH session from being disconnected (replace with actual value):
route add YOUR_LOCAL_PC_PUBLIC_IP gw X.X.X.X
Add a new default route to start routing traffic via the VPN server:
route add default dev ppp0
The VPN connection is now complete. Verify that your traffic is being routed properly:
wget -qO- http://ipv4.icanhazip.com; echo
The above command should return Your VPN Server IP.
To stop routing traffic via the VPN server:
route del default dev ppp0
To disconnect:
# Ubuntu & Debian echo "d myvpn" > /var/run/xl2tpd/l2tp-control ipsec down myvpn # CentOS/RHEL & Fedora echo "d myvpn" > /var/run/xl2tpd/l2tp-control strongswan down myvpn
| Description |
This article describes how to configure FortiGate so Microsoft’s L2TP/IPSec VPN client configured on Windows 10 PC will have access to the network(s) behind FortiGate in a secure manner. When deploying L2TP/IPSec VPN between Windows 10 PC and FortiGate, it’s possible to run into issues (where the tunnel failed to come up), if not using ‘VPN Proposals’ supported by Windows 10. |
| Scope |
FortiGate v6.2, FortiGate v6.4, FortiGate v7.0. |
| Solution |
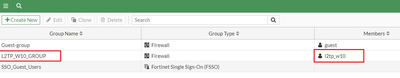
L2TP over IPSec can be deployed on FortiGate through CLI or GUI, it is advisable to follow the GUI configuration template on FortiGate (Under VPN -> IPSec Wizard -> VPN Setup). Configuring L2TP over IPSec (GUI). Step 1: Create a User Account: A ‘user account’ is required on FortiGate for ‘L2TP over IPSec’ deployment.
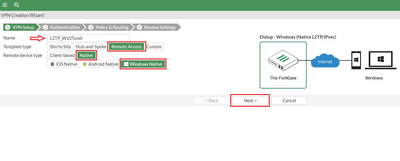
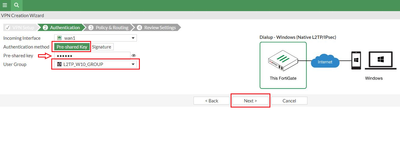
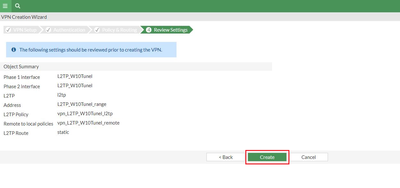
Step 2: Create the VPN. Go to CUI Interface, VPN -> IPsec Wizard -> VPN Setup -> Remote Access -> Native -> Windows Native (fill in required information) and select ‘Next’.
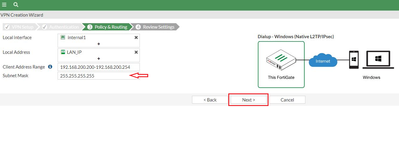
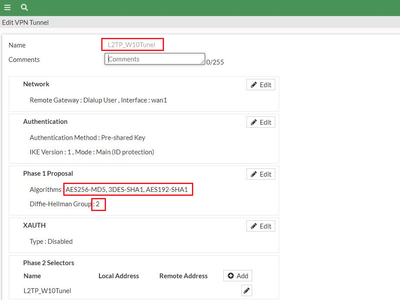
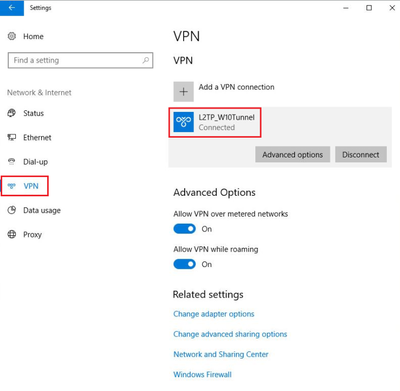
Note: Do not change the ‘Subnet Mask’ leave it as default. Review the newly created VPN and once okay, select ‘Create’. VPN Summary: Note: The proposal used in phase1 (and phase 2) by FortiGate wizard, should be supported by Windows. The deployment will NOT work if a proposal not supported by Windows 10 (or other Windows) L2TP/IPSec is choosen. Step 3: Create L2TP/IPSec on Windows 10. On Windows, select Start -> Settings -> Network & Internet -> VPN -> Add a VPN connection. Fill in the ‘Add a VPN connection’ tab using below screenshot as a guide. Select ‘save’ once done. Note: ‘Server name or address’, is the IP address of the FortiGate WAN Interface. Verification: Select connect under the newly created VPN, and it should connect and access the network behind FortiGate if everything is configured correctly. Note that the IP specified under the Client Address Range of FortiGate is assigned to the PC. |