Overview
This article describes a set of commands used for configuration management.
Configuration Undo and Redo
Any action done in GUI or any command executed from the CLI is recorded in /system history. You can undo or redo any action by running undo or redo commands from the CLI or by clicking on Undo, and Redo buttons from the GUI.
A simple example to demonstrate the addition of the firewall rule and how to undo and redo the action:
[admin@v7_ccr_bgp] /ip/firewall/filter> add chain=forward action=drop [admin@v7_ccr_bgp] /ip/firewall/filter> print Flags: X - disabled, I - invalid; D - dynamic 0 X chain=input action=drop protocol=icmp src-address=10.155.101.1 log=no log-prefix="" 1 chain=forward action=drop [admin@v7_ccr_bgp] /ip/firewall/filter> /system/history/print Flags: U - undoable, R - redoable, F - floating-undo Columns: ACTION, BY, POLICy ACTION BY POLIC F filter rule added admin write U --- write [admin@v7_ccr_bgp] /ip/firewall/filter>
We have added a firewall rule and in /system history we can see all that is being done.
Let’s undo everything:
[admin@v7_ccr_bgp] /ip/firewall/filter> /undo [admin@v7_ccr_bgp] /ip/firewall/filter> print Flags: X - disabled, I - invalid; D - dynamic 0 X chain=input action=drop protocol=icmp src-address=10.155.101.1 log=no log-prefix="" [admin@v7_ccr_bgp] /ip/firewall/filter>
As you can see firewall rule disappeared.
Now redo the last change:
[admin@v7_ccr_bgp] /ip/firewall/filter> /redo [admin@v7_ccr_bgp] /ip/firewall/filter> print Flags: X - disabled, I - invalid; D - dynamic 0 X chain=input action=drop protocol=icmp src-address=10.155.101.1 log=no log-prefix="" 1 chain=forward action=drop [admin@v7_ccr_bgp] /ip/firewall/filter>
System history is capable of showing exact CLI commands that will be executed during Undo or Redo actions even if we perform the action from GUI, for example, detailed history output after adding TCP accept rule from WinBox:
[admin@v7_ccr_bgp] /system/history> print detail
Flags: U - undoable, R - redoable, F - floating-undo
F redo=
/ip firewall filter add action=accept chain=forward disabled=no log=no \
log-prefix="" protocol=tcp
undo=/ip firewall filter remove *4 action="filter rule added" by="admin"
policy=write time=oct/10/2019 18:51:05
F redo=/ip firewall filter add action=accept chain=forward
undo=/ip firewall filter remove *3 action="filter rule added" by="admin"
policy=write time=oct/10/2019 18:49:03
U redo="" undo="" action="---" by="" policy=write time=sep/27/2019 13:07:35
[admin@v7_ccr_bgp] /system/history>
Safe Mode
It is sometimes possible to change router configuration in a way that will make the router inaccessible (except from local console). Usually, this is done by accident, but there is no way to undo the last change when the connection to the router is already cut. Safe mode can be used to minimize such risk.
The «Safe Mode» button in the Winbox GUI allows you to enter Safe Mode, while in the CLI, you can access it by either using the keyboard shortcut F4 or pressing [CTRL]+[X]. To exit without saving the made changes in CLI, hit [CTRL]+[D].
[admin@MikroTik] ip route>[CTRL]+[X] [Safe Mode taken] [admin@MikroTik] ip route<SAFE>
Message Safe Mode taken is displayed and prompt changes to reflect that session is now in safe mode. All configuration changes that are made (also from other login sessions), while the router is in safe mode, are automatically undone if the safe mode session terminates abnormally. You can see all such changes that will be automatically undone and tagged with an F flag in the system history:
[admin@MikroTik] /ip/route> [Safe Mode taken] [admin@MikroTik] /ip/route<SAFE> add [admin@MikroTik] /ip/route<SAFE> /system/history/print Flags: U, F - FLOATING-UNDO Columns: ACTION, BY, POLICY ACTION BY POLICY F route 0.0.0.0/0 added admin write
Now, if the telnet connection (or winbox terminal) is cut, then after a while (TCP timeout is 9 minutes) all changes that were made while in safe mode will be undone. Exiting session by [Ctrl]+[D] also undoes all safe mode changes, while /quit does not.
If another user tries to enter safe mode, he’s given the following message:
[admin@MikroTik] > Hijacking Safe Mode from someone - unroll/release/don't take it [u/r/d]:
- [u] — undoes all safe mode changes, and puts the current session in safe mode.
- [r] — keeps all current safe mode changes, and puts the current session in a safe mode. The previous owner of safe mode is notified about this:
[admin@MikroTik] ip firewall rule input [Safe mode released by another user]
- [d] — leaves everything as-is.
If too many changes are made while in safe mode, and there’s no room in history to hold them all (currently history keeps up to 100 most recent actions), then the session is automatically put out of the safe mode, and no changes are automatically undone. Thus, it is best to change the configuration in small steps, while in safe mode. Pressing [Ctrl]+[X] twice is an easy way to empty safe mode action list.
System Backup and Restore
System backup is the way to completely clone router configuration in binary format.
More information about Backup and Restore is found here.
Configuration Export and Import
RouterOS allows exporting and importing parts of the configuration in plain text format. This method can be used to copy bits of configuration between different devices, for example, clone the whole firewall from one router to another.
An export command can be executed from each individual menu (resulting in configuration export only from this specific menu and all its sub-menus) or from the root menu for complete config export and is available for CLI only.
The Export command does not export system user passwords, installed certificates, SSH keys, Dude, or a User-manager database.
Installed certificates, SSH keys, Dude, and User-manager databases must be manually exported and imported into a new device.
System user passwords can not be exported.
During config import, we suggest using the same RouterOS version used during config export to prevent cases when some of the commands do not exist in one or another RouterOS version.
Configuration Export
The following command parameters are accepted:
| Property | Description |
|---|---|
| compact | Output only modified configuration, the default behavior |
| file | Export configuration to a specified file. When the file is not specified export output will be printed to the terminal |
|
show-sensitive (yes|no; Default: no). RouterOS version 7 only hide-sensitive (yes|no; Default: yes). RouterOS version 6 only |
Show sensitive information, like passwords, keys, etc. Hide sensitive information, like passwords, keys, etc. |
| terse | With this parameter, the export command will output only configuration parameters, without defaults. |
| verbose |
With this parameter, the export command will output whole configuration parameters and items including defaults. |
For example, export configuration from /ip address the menu and save it to a file:
[admin@MikroTik] > /ip address print
Flags: X - disabled, I - invalid, D - dynamic
# ADDRESS NETWORK BROADCAST INTERFACE
0 10.1.0.172/24 10.1.0.0 10.1.0.255 bridge1
1 10.5.1.1/24 10.5.1.0 10.5.1.255 ether1
[admin@MikroTik] > /ip address export file=address
[admin@MikroTik] > /file print
# NAME TYPE SIZE CREATION-TIME
0 address.rsc script 315 dec/23/2003 13:21:48
[admin@MikroTik] >
By default, export command writes only user-edited configuration, RouterOS defaults are omitted.
For example, the IPSec default policy will not be exported, and if we change one property then only our change will be exported:
[admin@rack1_b4] /ip ipsec policy> print
Flags: T - template, X - disabled, D - dynamic, I - inactive, * - default
0 T * group=default src-address=::/0 dst-address=::/0 protocol=all
proposal=default template=yes
[admin@rack1_b4] /ip ipsec policy> export
# apr/02/1970 17:59:14 by RouterOS 6.22
# software id = DB0D-LK67
#
[admin@rack1_b4] /ip ipsec policy> set 0 protocol=gre
[admin@rack1_b4] /ip ipsec policy> export
# apr/02/1970 17:59:30 by RouterOS 6.22
# software id = DB0D-LK67
#
/ip ipsec policy
set 0 protocol=gre
Note:
The * flag, it indicates that the entry is system default and cannot be removed manually.
Here is the list of all menus containing default system entries
| Menu | Default Entry |
|---|---|
| /interface wireless security-profiles | default |
| /ppp profile | «default», «default-encryption» |
| /ip hotspot profile | default |
| /ip hotspot user profile | default |
| /ip ipsec policy | default |
| /ip ipsec policy group | default |
| /ip ipsec proposal | default |
| /ip ipsec mode-conf | read-only |
| /ip smb shares | pub |
| /ip smb users | guest |
| /ipv6 nd | any |
| /mpls interface | all |
| /routing bfd interface | all |
| /routing bgp instance | default |
| /routing ospf instance | default |
| /routing ospf area | backbone |
| /routing ospf-v3 instance | defailt |
| /routing ospf-v3 area | backbone |
| /snmp community | public |
| /tool mac-server mac-winbox | all |
| /tool mac-server | all |
| /system logging | «info», «error», «warning», «critical» |
| /system logging action | «memory», «disk», «echo», «remote» |
| /queue type | «default», «ethernet-default», «wireless-default», «synchronous-default», «hotspot-default», «only-hardware-queue», «multi-queue-ethernet-default», «default-small» |
If some specific menu will not be able to respond to the export command, starting from the RouterOS v7.11, error message will be printed out in the export command output after a timeout («#error exporting «/xxx» (timeout)») and the process will move on to the next menu.
Configuration Import
Root menu command import allows running configuration script from the specified file. Script file (with extension «.rsc») can contain any console command including complex scripts.
For example, load saved configuration file
[admin@MikroTik] > import address.rsc Opening script file address.rsc Script file loaded and executed successfully [admin@MikroTik] >
Import command allows to specify the following parameters:
| Property | Description |
|---|---|
| from-line | Start executing the script from the specified line number |
| file-name | Name of the script (.rsc) file to be executed. |
| verbose | Reads each line from the file and executes individually, allowing to debug syntax or other errors more easily. |
In the event that the device has a default or existing configuration that requires replacement, it is necessary to initiate a configuration reset.
This involves applying a clean, empty configuration using the command /system/reset-configuration no-defaults=yes, followed by a device reboot.
Auto Import
It is also possible to automatically execute scripts after uploading to the router with FTP or SFTP. The script file must be named with the extension *.auto.rsc. Once the commands in the file are executed, a new *.auto.log file is created which contains import success or failure information.
«.auto.rsc» in the filename is mandatory for a file to be automatically executed.
Import troubleshooting
Configuration parts to watch out for in exported .rsc files
Things that should be removed from export files that were created with «/export», before attempting import on a new device.
- Interface renaming is in conflict with the default ethernet naming scheme.
/interface ethernet set [ find default-name=ether5 ] auto-negotiation=no name=ether1-gateway set [ find default-name=ether6 ] name=ether2 set [ find default-name=ether7 ] name=ether3 set [ find default-name=ether8 ] name=ether4 set [ find default-name=ether1 ] name=ether5 set [ find default-name=ether2 ] name=ether6 set [ find default-name=ether3 ] name=ether7 set [ find default-name=ether4 ] name=ether8
- In older version exports default entries might show with «add» instead of the «set» command. That should be edited before import to avoid errors.
- Check if the total number of physical interfaces count matches the new and old devices. If there will some missing that will end up in error during .rsc import.
In case of problematic import, attempt the following:
- Reset the configuration on that device.
- Run the import command again with the «verbose=yes» argument. It will stop also stop the import process on a problem that you already encountered, but will also show the place where the export failed. This way shows you the place where things need to be edited in the .rsc import file.
Startup delay
If your configuration relies on interfaces that might not yet have started up upon command execution, it is suggested to introduce delays or to monitor until all needed interfaces are available. This example script allows you to set how many interfaces you are expecting, and how long to wait until they become available:
{
:local i 0
#Number of interfaces. It is necessary to reconfigure this number for each device (/interface print count-only)
:local x 10
#Max time to wait
:local t 30
while ($i < $t && [:len [/interface find]] < $x) do={
:put $i
:set $i ($i + 1)
:delay 1
}
if ($i = $t) do={
:log warning message="Could not load all physical interfaces"
} else={
#Rest of your script
}
}
The above script will wait until there are 10 interfaces visible, or 30 seconds. If there are no 10 interfaces at this time, it will put a message in the log. Modify the variables according to your needs.
Configuration Reset
RouterOS allows resetting configuration with /system reset-configuration command
This command clears all configuration of the router and sets it to the factory defaults including the login name and password (‘admin’ with an empty password or, for some models, check user and wireless passwords on the sticker). For more details on the default configuration see the list.
After the configuration reset command is executed router will reboot and load the default configuration.
The backup file of the existing configuration is stored before reset. That way you can easily restore any previous configuration if the reset is done by mistake.
If the router has been installed using Netinstall and had a script specified as the initial configuration, the reset command executes this script after purging the configuration. To stop it from doing so, you will have to reinstall the router.
It is possible to override the default reset behavior with the parameters below:
| Property | Description |
|---|---|
| keep-users | Do not remove existing users from the configuration |
| no-defaults | Do not load the default configuration, just clear the configuration |
| skip-backup | Skip automatic backup file generation before reset |
| run-after-reset | Run specified .rsc file after reset. That way you can load your custom configuration. |
If a specific .rsc file execution takes more than 2 minutes, a script will fail, and LOG will contain a «runtime limit exceeded» error.
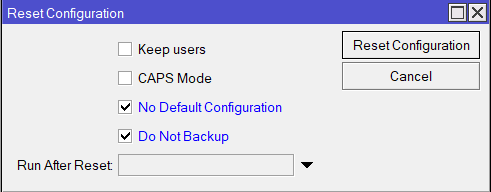
For example hard reset configuration without loading default config and skipping backup file:
[admin@MikroTik] > /system reset-configuration no-defaults=yes skip-backup=yes Dangerous! Reset anyway? [y/N]: y
And the same using Winbox:
Contents
Introduction
This document describes how to migrate a configuration from a current router to a new router.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics and have the required accesses:
-
Access to a Trivial File Transfer Protocol (TFTP) or File Transfer Protocol (FTP) server.
-
Connectivity — Routers must be able to access the FTP or TFTP server. Use thepingcommand to verify connectivity.
Components Used
This document is not restricted to specific software and hardware versions.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Conventions
Refer toCisco Technical Tips Conventionsfor more information on document conventions.
Make a Backup of the Configuration
There are several methods to choose from in order to back up and restore a configuration:
-
Use a TFTP server
-
Use an FTP server
-
Use a Terminal Emulation Program
-
Automatic Backup of Configuration with the Kron Method
-
Backup Configuration to a TFTP Server
Use a TFTP Server to Backup and Restore a Configuration
This is a step-by-step approach to copy a configuration from a router to a TFTP server, and back to another router. Before you proceed with this method, make sure you have a TFTP server on the network to which you have IP connectivity.
-
At theRouter>prompt, issue theenablecommand, and provide the required password when prompted.
The prompt changes toRouter#, which indicates that the router is now in privileged mode.
-
Copy this configuration file to the TFTP server:
CE_2#copy running-config tftp: Address or name of remote host []? 10.104.207.171 Destination filename [ce_2-confg]? backup_cfg_for_my_router !! 1030 bytes copied in 2.489 secs (395 bytes/sec) CE_2#
-
Open the configuration file with a text editor. Search for and remove any line that starts with «AAA».
Note: This step is to remove any security commands that can lock you out of the router.
-
Copy the configuration file from the TFTP server to a new router in privileged (enable) mode which has a basic configuration.
Router#copy tftp: running-config Address or name of remote host []? 10.104.207.171 Source filename []? backup_cfg_for_my_router Destination filename [running-config]? Accessing tftp://10.66.64.10/backup_cfg_for_my_router... Loading backup_cfg_for_router from 10.104.207.171 (via FastEthernet0/0): ! [OK - 1030 bytes] 1030 bytes copied in 9.612 secs (107 bytes/sec) CE_2#
Use an FTP Server to Backup and Restore a Configuration
In this procedure, an FTP server can be used in place of a TFTP server.
-
At theRouter>prompt, issue theenablecommand, and provide the required password when prompted.
The prompt changes toRouter#, which indicates that the router is now in privileged mode.
-
Configure the FTP username and password.
CE_2#configure terminal CE_2(config)#ip ftp username cisco CE_2(config)#ip ftp password cisco123 CE_2(config)#end CE_2#
-
Copy the configuration to the FTP server.
CE_2#copy running-config ftp: Address or name of remote host []? 10.66.64.10 Destination filename [ce_2-confg]? backup_cfg_for_router Writing backup_cfg_for_router ! 1030 bytes copied in 3.341 secs (308 bytes/sec) CE_2#
-
Open the configuration file with a text editor. Search for and remove any line that starts with «AAA».
Note: This step is to remove any security commands that can lock you out of the router.
-
Copy the configuration file from the FTP server to a router in privileged (enable) mode which has a basic configuration.
Router#copy ftp: running-config Address or name of remote host [10.66.64.10]? Source filename [backup_cfg_for_router]? Destination filename [running-config]? Accessing ftp://10.66.64.10/backup_cfg_for_router... Loading backup_cfg_for_router ! [OK - 1030/4096 bytes] 1030 bytes copied in 13.213 secs (78 bytes/sec) CE_2#
Use a Terminal Emulation Program to Backup and Restore a Configuration
A terminal emulation program can be used to back up and restore a configuration. This is a description of the procedure with Microsoft HyperTerminal Emulation software, but you can use the concept and follow this example with the Terminal Emulation software of your preference:
-
If the configuration needs to be copied from another router, connect to that router through the console or Telnet.
-
At theRouter>prompt, issue theenablecommand, and provide the required password when prompted.
The prompt changes toRouter#, which indicates that the router is now in privileged mode.
-
Issue theterminal length 0command in order to force the router to return the entire response at once, rather than one screen at a time.
This allows you to capture the configuration without extraneous—more—prompts generated when the router responds one screen at a time.
-
On the HyperTerminal menu, chooseTransfer > Capture Text.
The Capture Text window appears.
-
Name this file «config.txt.»
-
ClickStartin order to dismiss the Capture Text window and begin the capture.
-
Issue theshow running-configcommand and allow time for the router to complete its response. You can see:
Building configuration...
followed by the configuration.
-
On the HyperTerminal menu, chooseTransfer > Capture Text > Stopin order to end the screen capture.
-
Open the config.txt file you created in any text editor, such as Notepad or WordPad.
-
Search for and remove any line that starts with «AAA».
Note: This step is to remove any security commands that can lock you out of the router.
-
Save the file.
-
Connect to the router that needs the configuration.
-
Open the config.txt file.
-
Highlight the entire contents of the config.txt file.
To do this, highlight the entire contents with your left mouse button. Alternatively, if you use Notepad, you can chooseEdit > Select Allfrom the menu.
-
Copy the selected text to the Windows clipboard.
You can either chooseEdit > Copyfrom the text editor menu or hold down theCTRLkey and simultaneously press theCkey in order to perform the copy.
-
Switch to the HyperTerminal window and issue theconfigure terminalcommand at theRouter#prompt. Then pressEnter.
-
Paste the configuration file into the router withEdit > Paste to Hoston the HyperTerminal menu.
-
After the configuration has finished pasting and the router brings you back to the configuration prompt, issue thecopy running-config startup-configcommand in order to write the configuration into memory.
-
Issue theexitcommand in order to return to theRouter#prompt.
Automatic Backup of Configuration with the Kron Method
In order to get a router to copy the running-config to startup-config, for example every Sunday at 23:00, complete these steps:
-
Create a kron policy list—This is the script that lists what commands the router must run at the scheduled time.
Router(config)#kron policy-list SaveConfig Router(config-kron-policy)#cli write Router(config-kron-policy)#exit-
cli—Specifies EXEC CLI commands within a Command Scheduler policy list.
-
Policy-list—Specifies the policy list associated with a Command Scheduler occurrence.
Note: The reason whywritewas used rather thancopy running-config startup-configis because kron does not support interactive prompts and thecopy running-config startup-configcommand requires interaction. It is important to remember this when you create commands. Also, note that kron does not support configuration commands.
-
-
Create a kron occurrence—This informs the router when and how often the policy must run.
Router(config)#kron occurrence SaveConfigSchedule at 23:00 Sun recurring Router(config-kron-occurrence)#policy-list SaveConfig
-
SaveConfigSchedule—This is the name of occurrence. Length of occurrence-name is from 1 to 31 characters. If the occurrence-name is new, an occurrence structure can be created. If the occurrence-name is not new, the current occurrence can be edited.
-
at—Identifies that the occurrence is to run at a specified calendar date and time.
-
recurring—Identifies that the occurrence is to run on a recurring basis.
-
-
Verify the kron configuration with theshowcommand.
Router#show kron schedule Kron Occurrence Schedule SaveConfigSchedule inactive, can run again in 1 days 12:37:47 at 23:00 on Sun
-
inactive—Means that kron is not running the command(s) at present.
-
Active—Means that kron is running the current command(s).
Router#show running-configuration kron occurrence SaveConfigSchedule at 23:00 Sun recurring policy-list SaveConfig kron policy-list SaveConfig cli write
-
Backup Configuration to a TFTP Server
This example is to save the current config to a TFTP server (10.1.1.1) every Sunday at 23:00:
Router(config)#kron policy-list Backup Router(config-kron-policy)#cli show run | redirect tftp://10.1.1.1/test.cfg Router(config-kron-policy)#exit ! Router(config)#kron occurrence Backup at 23:00 Sun recurring Router(config-kron-occurrence)#policy-list Backup
Verify
Use theshow running-configcommand to confirm that the configuration file has been copied to the destination router.
Related Information
- Cisco Support & Downloads
Есть в маршрутизаторах компании Tp-Link такая полезная функция, как сохранение и восстановление настроек. Сейчас мы рассмотрим как это сделать. Зачем вообще сохранять настройки? На самом деле, это очень удобно. Например, вы хотите поэкспериментировать с какими-то настройками на роутере, и боитесь что-то сделать не так. Просто делаем резервную копию настроек и можем спокойно что-то менять.
Но, я думаю, что эта возможность будет особенно полезна в двух случаях:
- При обновлении прошивки на маршрутизаторе. Мы уже знаем, что после обновления прошивки на Wi-Fi роутере Tp-Link, все настройки будут сброшены к заводским. И его нужно заново настраивать. Намного проще перед прошивкой сохранить все настройки в файл, а затем, после прошивки их восстановить.
- Бывает, что приходится делать сброс настроек маршрутизатора: при проблемах в работе, частых сбоях и т. п. Что бы потом не мучатся с настройкой, просто делаем backup.
Все делается очень просто и быстро!
Как сохранить настройки роутера Tp-Link в файл?
Подключитесь к своему маршрутизатору. Можно по кабелю, или по Wi-Fi.
Откройте браузер, и в строке, где вводим адрес сайтов, вводим IP-адрес роутера: 192.168.1.1, или 192.168.0.1.
Вводим логин и пароль. Если вы их не меняли, то это admin и admin (эта информация есть на самом маршрутизаторе).

Перейдите на вкладку System Tools — Backup & Restore (в русской прошивке: Системные инструменты — Резервная копия и Восстановление).
Для сохранения настроек нажмите на кнопку Backup (Резервная копия). Сохраните файл в формате .bin. Например, на рабочий стол.

Восстанавливаем настройки на маршрутизатор
Все на той же вкладке System Tools — Backup & Restore нажмите на кнопку Выберите файл. Выберите файл настроек, который вы сохранили ранее на свой компьютер. Нажмите на кнопку Restore (Восстановить).

Советую вам после успешной настройки маршрутизатора создать такой резервный файл настроек и сохранить его в надежное место. В случае какой-то ошибки (бывает, что настройки сами слетают), вы сможете за несколько секунд их восстановить.
Step 1. Open up a web browser and type in the IPaddress of the DSL-G624M (default is 192.168.1.1). PressEnter.
Step 2. Type in the username and password(default is admin/admin). Press OK.
Step 3. Click on Tools tab atthe top and then click on System on theleft.
Step 4. To save the configuration settings ofyour wireless router, click the Save button nextto Save Settings To Local Hard Drive.
To load a previously saved configuration file, click theBrowse… button next to Load Settings FromLocal Hard Drive. Once you have located the file (backup.cfg)on your hard drive, click the OK button and thenclick Load.
NOTE: If the firmware on your wireless router hasbeen upgraded/downgraded, do not load configuration files that weresaved using a different version of firmware then you currently haveinstalled. This will not work and could damage the unit.
Порой оптимальные настройки на роутере подбираются не один день. Особенно, это касается конфигурации WAN, чтобы добиться максимально возможной скорости Интернета. Очень досадно, если после этого настройки случайно сбрасываются. Поэтому, мы настоятельно рекомендуем нашим читателям пользоваться функцией экспорта конфигурации в файл. Такая функция имеется во всех современных роутерах, DSL-модемах и подобном оборудовании. Файл с настройками можно сохранить на жёсткий диск, флешку или куда угодно ещё. При необходимости вы в любой момент можете импортировать настройки из файла и применить их к роутеру. А если вы хотите заменить неисправный роутер на новый (идентичной марки и модели), то в этом случае процедура импорта-экспорта будет просто незаменимой.
Как сохранить настройки роутера
Обычно такие функции как импорт\экспорт находятся в разделе Обслуживание. На иллюстрации показан веб-интерфейс роутера D-Link DIR-300. Здесь нужно войти в раздел Maintenance, выбрать страницу Save and Restore и в поле Save Settings To Local Drive нажать кнопку Save:
После этого произойдёт обычное скачивание файла с экспортированными параметрами роутера:
Переместите этот файл в надежное место и храните.
Как восстановить настройки роутера
Для восстановления предыдущего состояния устройства вам понадобится нажать кнопку Выберите файл в блоке под названием Load Settings From Local Drive :
открыть файл конфигурации роутера с расширением .bin :
и нажать кнопку Upload Settings для импорта параметров:
После перезагрузки роутер восстановит те параметры, которые были установлены до сброса.