The OpenVPN community project team is proud to release OpenVPN 2.6.6. This is a small bugfix release.
For details see Changes.rst
User visible changes:
- OCC exit messages are now logged more visibly See GH #391.
- OpenSSL error messages are now logged with more details (for example, when loading a provider fails, which .so was tried, and why did it fail) See GH #361.
- print a more user-friendly message when tls-crypt-v2 client auth fails
- packaging now includes all documentation in the source tarball
New features:
- set WINS server via interactive service — this adds support for «dhcp-option WINS 192.0.2.1» for DCO + wintun interfaces where no DHCP server is used. See GH #373.
Windows MSI changes since 2.6.5:
- Included openvpn-gui updated to 11.44.0.0
- MSIs now use OpenSSL 3.1.2
For Community-maintained packages for Linux distributions see OpenvpnSoftwareRepos
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.6-I001-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.6-I001-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.6-I001-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.6.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.4. This is a small bugfix release.
For details see Changes.rst
Note:
- License amendment: all new commits fall under a modified license that explicitly permits linking with Apache2 libraries (mbedTLS, OpenSSL) — see COPYING for details. Existing code will fall under the new license as soon as all contributors have agreed to the change — work ongoing.
Feature changes:
- DCO: support kernel-triggered key rotation (avoid IV reuse after 232 packets). This is the userland side, accepting a message from kernel, and initiating a TLS renegotiation. As of 2.6.4 release, only implemented in FreeBSD kernel.
Windows MSI changes since 2.6.3:
- Rebuilt included tap-windows driver with the correct version of the old Windows 7 driver, removing a warning about unsigned driver on Windows 7 installation. See GH openvpn-build#365.
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.4-I001-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.4-I001-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.4-I001-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.4.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.3. This is a small bugfix release.
For details see Changes.rst
Feature changes:
- Windows: support setting DNS domain in configurations without GUI and DHCP (typically wintun or windco drivers), see GH openvpn#306.
Windows MSI changes since 2.6.2:
- Several Windows-specific issues fixed:
- ensure interactive service stays enabled after silent reinstall, see GH openvpn-build#348, openvpn-build#349 and openvpn-build#351
- repair querying install path info for easyrsa-start.bat on some Windows language versions, see GH openvpn-build#352.
- MSIs are now built against OpenSSL 3.1.0.
- Update included openvpn-gui to 11.41.0.0
- This update removes the ability to change the password of a private key from the GUI. This was a niche feature which caused a direct dependency of GUI on OpenSSL. Use openssl.exe directly if you need to edit a private key.
Note: Windows MSI was updated to I003 on April 26th. Changes in I003:
- The GPG subkey for creating the .asc files for the downloads has been updated. You might need to re-download or update the GPG key if verifying the signatures.
- Fix the encoding of some documentation/sample files included in the installer. See GH openvpn-build#358
- Update include tap-windows6 driver to 9.25.0
- Fixes a problem with sending small non-IP packets (e.g. PPPoE) over the VPN connection. See GH tap-windows6#158
- Note: The new driver is only used on Windows 10 and newer. We can’t rebuild drivers for Windows 7/8 since Microsoft doesn’t support the signing mechanism anymore. We include the previous driver version to still allow installation on Windows 7/8.
- Update included openvpn-gui to 11.42.0.0
- Fixes a problem with passphrase prompt was sometimes not displayed. See GH openvpn-gui#619
- Adds «Password Reveal» feature which allows you to see passwords while entering them.
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.3-I003-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.3-I003-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.3-I003-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.3.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.2. This is mostly a bugfix release with some improvements.
For details see Changes.rst
Feature changes:
- implement byte counter statistics for DCO Linux (p2mp server and client)
- implement byte counter statistics for DCO Windows (client only)
--dns server <n> address ...now permits up to 8 v4 or v6 addresses
Important note for Linux DCO users:
- New control packets flow for data channel offloading on Linux: 2.6.2+ changes the way OpenVPN control packets are handled on Linux when DCO is active, fixing the lockups observed with 2.6.0/2.6.1 under high client connect/disconnect activity. This is an INCOMPATIBLE change and therefore an ovpn-dco kernel module older than v0.2.20230323 (commit ID 726fdfe0fa21) will not work anymore and must be upgraded. The kernel module was renamed to «ovpn-dco-v2.ko» in order to highlight this change and ensure that users and userspace software could easily understand which version is loaded. Attempting to use the old ovpn-dco with 2.6.2+ will lead to disabling DCO at runtime.
Windows MSI changes since 2.6.1:
- Update included openvpn-gui to 11.39.0.0
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.2-I001-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.2-I001-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.2-I001-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.2.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.1. This is mostly a bugfix release with some improvements.
For details see Changes.rst
Feature changes:
- Dynamic TLS Crypt: When both peers are OpenVPN 2.6.1+, OpenVPN will dynamically create a tls-crypt key that is used for renegotiation. This ensure that only the previously authenticated peer can do trigger renegotiation and complete renegotiations.
- CryptoAPI (Windows): support issuer name as a selector. Certificate selection string can now specify a partial issuer name string as
«—cryptoapicert ISSUER:<string>» where <string> is matched as a substring of the issuer (CA) name in the certificate.
Note: configure now enables DCO build by default on FreeBSD and Linux. On Linux this brings in a new default dependency for libnl-genl (for Linux distributions that are too old to have a suitable version of the library, use «configure —disable-dco»)
Windows MSI changes since 2.6.1:
- Update included ovpn-dco-win driver to 0.9.2
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.1-I001-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.1-I001-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.1-I001-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.1.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.0. This is a new stable release with some major new features.
For details see: Changes.rst
The Changes document also contains a section with workarounds for common problems encountered when using OpenVPN with OpenSSL 3.
New features and improvements in 2.6.0 compared to 2.5.8:
- Data Channel Offload (DCO) kernel acceleration support for Windows, Linux, and FreeBSD.
- OpenSSL 3 support.
- Improved handling of tunnel MTU, including support for pushable MTU.
- Outdated cryptographic algorithms disabled by default, but there are options to override if necessary.
- Reworked TLS handshake, making OpenVPN immune to replay-packet state exhaustion attacks.
- Added —peer-fingerprint mode for a more simplistic certificate setup and verification.
- Added Pre-Logon Access Provider support to OpenVPN GUI for Windows.
- Improved protocol negotiation, leading to faster connection setup.
- Included openvpn-gui updated to 11.37.0.0. See CHANGES.rst.
- Updated easy-rsa3 bundled with the installer on Windows.
- Various bug fixes.
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.0-I005-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.0-I005-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.0-I005-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.0.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.5.4. This release include a number of fixes and small improvements. One of the fixes is to password prompting on windows console when stderr redirection is in use — this breaks 2.5.x on Win11/ARM, and might also break on Win11/amd64. Windows executable and libraries are now built natively on Windows using MSVC, not cross-compiled on Linux as with earlier 2.5 releases. Windows installers include updated OpenSSL and new OpenVPN GUI. The latter includes several improvements, the most important of which is the ability to import profiles from URLs where available. Installer version I602 fixes loading of pkcs11 files on Windows. Installer version I603 fixes a bug in the version number as seen by Windows (was 2.5..4, not 2.5.4). Installer I604 fixes some small Windows issues.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.4.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.4.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.4.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.4-I604-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.4-I604-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.5.4-I604-arm64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.3. Besides a number of small improvements and bug fixes, this release fixes a possible security issue with OpenSSL config autoloading on Windows (CVE-2021-3606). Updated OpenVPN GUI is also included in Windows installers.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.3.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.3.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.3.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.3-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.3-I601-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.5.3-I601-arm64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.2. It fixes two related security vulnerabilities (CVE-2020-15078) which under very specific circumstances allow tricking a server using delayed authentication (plugin or management) into returning a PUSH_REPLY before the AUTH_FAILED message, which can possibly be used to gather information about a VPN setup. In combination with «—auth-gen-token» or a user-specific token auth solution it can be possible to get access to a VPN with an otherwise-invalid account. OpenVPN 2.5.2 also includes other bug fixes and improvements. Updated OpenSSL and OpenVPN GUI are included in Windows installers.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.2.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.2.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.2.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.2-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.2-I601-amd64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.1. It includes several bug fixes and improvements as well as updated OpenSSL and OpenVPN GUI for Windows.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.1.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.1.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.1.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.1-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.1-I601-amd64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.0 which is a new major release with many new features.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.0.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.0.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.0.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.0-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.0-I601-amd64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.4.11. It fixes two related security vulnerabilities (CVE-2020-15078) which under very specific circumstances allow tricking a server using delayed authentication (plugin or management) into returning a PUSH_REPLY before the AUTH_FAILED message, which can possibly be used to gather information about a VPN setup. This release also includes other bug fixes and improvements. The I602 Windows installers fix a possible security issue with OpenSSL config autoloading on Windows (CVE-2021-3606). Updated OpenSSL and OpenVPN GUI are included in Windows installers.
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.11.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.11.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.11.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.11-I602-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.11-I602-Win10.exe |
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
This is primarily a maintenance release with bugfixes and small improvements. Windows installers include the latest OpenSSL version (1.1.1i) which includes security fixes.
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.10.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.10.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.10.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.10-I601-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.10-I601-Win10.exe |
Instructions for verifying the signatures are available here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with bugfixes and improvements. This release also fixes a security issue (CVE-2020-11810, trac #1272) which allows disrupting service of a freshly connected client that has not yet not negotiated session keys. The vulnerability cannot be used to inject or steal VPN traffic.
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. We are moving to MSI installers in OpenVPN 2.5, but OpenVPN 2.4.x will remain NSIS-only.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.9.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.9.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.9.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.9-I601-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.9-I601-Win10.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with bugfixes and improvements. The Windows installers (I601) have several improvements compared to the previous release:
- New tap-windows6 driver (9.24.2) which fixes some suspend and resume issues
- Latest OpenVPN-GUI
- Considerable performance boost due to new compiler optimization flags
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. We are moving to MSI installers in OpenVPN 2.5, but OpenVPN 2.4.x will remain NSIS-only.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.8.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.8.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.8.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.8-I602-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.8-I602-Win10.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with bugfixes and improvements. One of the big things is enhanced TLS 1.3 support. A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. We are moving to MSI installers in OpenVPN 2.5, but OpenVPN 2.4.x will remain NSIS-only.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer will not work on Windows 7/8/8.1/Server 2012r2. This is because Microsoft’s driver signing requirements and tap-windows6. For the same reason you need to use an older installer with Windows Server 2016. This older installer has a local privilege escalation vulnerability issue which we cannot resolve for Windows Server 2016 until tap-windows6 passes the HLK test suite on that platform. In the meanwhile we recommend Windows Server 2016 users to avoid installing OpenVPN/tap-windows6 driver on hosts where all users can’t be trusted. Users of Windows 7-10 and Server 2012r2 are recommended to update to latest installers as soon as possible.
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.7.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.7.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.7.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.7-I607-Win7.exe |
Windows 10 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.7-I607-Win10.exe |
Windows Server 2016 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.7-I603.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with minor bugfixes and improvements, and one security relevant fix for the Windows Interactive Service. Windows installer includes updated OpenVPN GUI and OpenSSL. Installer I601 included tap-windows6 driver 9.22.1 which had one security fix and dropped Windows Vista support. However, in installer I602 we had to revert back to tap-windows 9.21.2 due to driver getting reject on freshly installed Windows 10 rev 1607 and later when Secure Boot was enabled. The failure was due to the new, more strict driver signing requirements. The 9.22.1 version of the driver is in the process of getting approved and signed by Microsoft and will be bundled in an upcoming Windows installer.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. Our long-term plan is to migrate to using MSI installers instead.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developha er IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.6.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.6.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.6.zip |
Windows installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.6-I602.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
You can download Windows developments snapshots (MSI installers) from here (Index of /downloads/snapshots/github-actions/openvpn2/ ). Those are automatically built from commits to OpenVPN master branch and include functionality which will be available in the next release. Development snapshots are less stable than releases, so use at your own risk.
Official OpenVPN Connect client program
This is the official OpenVPN Connect client software for Windows workstation platforms developed and maintained by OpenVPN Inc. This is the recommended client program for the OpenVPN Access Server to enable VPN for Windows. The latest version of OpenVPN for Windows is available on our website.
If you have an OpenVPN Access Server, it is recommended to download the OpenVPN Connect client software directly from your own Access Server, as it will then come pre configured for use for VPN for Windows. The version available here contains no configuration to make a connection, although it can be used to update an existing installation and retain settings.
Download OpenVPN Connect v3
sha256 signature: 81c97d2a482f8e0062f3e58d22dafedfcd973332f5e62d2511419a42cd9aa9d4
For Windows 7, 8, 10, and 11.
A 32 bits version is also available:
Download OpenVPN Connect v3 for 32 bits
sha256 signature: 7f80d6ef9818ba854c6b379381d51d1b8b4735acdad4b27f661b4e52ff69855d
Previous generation OpenVPN Connect V2 is available here:
Download OpenVPN Connect v2.7.1
sha256 signature: f65dd0ea784dd63632be64f89b1f83d51c199fd7319888883780cb9e975c325a
For Windows 7, 8, and 10.
The Interface
Our latest line of OpenVPN for Windows (OpenVPN Connect) software available for the major platforms features a new and improved user interface, making the experience of installing and using the OpenVPN for Windows software a snap. With an easy to use import feature you can import profiles straight from your OpenVPN Access Server or just import a saved profile from disk.
Frequently Asked Questions
Yes, you may continue to use both v2 and v3 on the same connect device and import the profiles desired into each. If you like, you can run either one or both.
No, the client cannot connect to multiple servers at once. It does support multiple connection profiles, giving you the option to switch easily from one server to the next, but you can only be connected to one at a time. This is by design, to prevent unexpected traffic paths when connecting to multiple VPN servers at the same time. If you are a system administrator and you require a complex setup where multiple connections are active at the same time, there is the option to use the open source community OpenVPN client software available from our website.
The OpenVPN client v1 was called “OpenVPN Desktop Client” and is no longer available. It is also not safe to use this anymore as it hasn’t been maintained for many years. It was replaced with the OpenVPN client v2. The OpenVPN client v2 is called “OpenVPN Connect Client” and has been in use for many years. It is still available from our website. You can download it from the direct link new the top of this page. The OpenVPN client v3 is called “OpenVPN Connect” and is the latest generation of our software. You can download it with the link above. It is also offered in the OpenVPN Access Server client web interface itself.
This is the official OpenVPN Connect software for Windows workstation platforms developed and maintained by OpenVPN Inc. This is the recommended client program for the OpenVPN Access Server. The latest versions are available on our website. If you have an OpenVPN Access Server, you can download the OpenVPN Connect client software directly from your own Access Server, and it will then come pre-configured for use. The version available here contains no configuration to make a connection, although it can be used to update an existing installation and retain settings.
- Download the MSI file
- Open and start the setup wizard.
- Give permissions to install on your Windows OS.
- Complete the OpenVPN Connect Setup Wizard.
- The OpenVPN logo displays in your tray (bottom right) with DISCONNECTED status.
- Click on the icon to start the Onboarding Tour.
- Review how to import a profile from a server by entering the Access Server Hostname and credentials or uploading a profile from your computer.
- Agree to the data collection use and retention policies after reviewing them.
- Import a profile, either from the server or from file.
- Navigate to your OpenVPN Access Server client web interface.
- Login with your credentials.
- Select ‘OpenVPN Connect for Windows’.
- Wait until the download completes, and then open it (specifics vary depending on your browser).
- Click Run to start the installation process.
- Click Yes to approve the privilege escalation request.
- Wait until the installation process completes.
- In the system tray, the OpenVPN Connect Client is now ready for use.
- From the OpenVPN Connect UI, choose “Import from Server”.
- Enter your Access Server Hostname, Title, Port (optional), and your credentials—username and password.
- Click Add.
- If you choose to Import autologin profile, it is less secure, but you won’t need to re-enter credentials.
- Choose “Import from File”.
- Drag and drop a .OVPN file or click on Browse to navigate to the location on your computer.
- The message displays that the profile is successfully imported and displays the hostname and the title. You can change the title if desired.
- Click on Add to complete the import.
Layer 2 bridging (TAP) is no longer supported. Switch over to TUN Mode to resolve this issue.
OpenVPN Access Server starts with a self-signed certificate. With this, you will receive warnings from your web browser about the site not being secure as well as a certificate error when importing a profile with the Connect Client. You can simply override the warnings or add an exception for your web browser. To resolve this, you can set up a DNS host name that resolves to the public address of your Access Server and install a valid SSL certificate that corresponds to that DNS host name. Going forward, you would use that hostname to access your server instead of the IP address. This is also the recommended method as validated SSL certificates can only ever function with a valid public DNS hostname.
Your Access Server Hostname is the address at which your Access Server can be reached. For example it could be https://vpn.yourcompany.com/. If a DNS hostname is not set up, it is also possible to specify the IP address where your Access Server. For example: https://55.193.55.55 Your credentials are your username and password. You may need to get that information from your Access Server administrator if you don’t know it.
Title is the name for the profile. It is automatically defined as the username with the hostname or IP address(example: user1@hostname). It differentiates between multiple profiles. You can define it manually as well. The title can be anything you want just so you can see which profile is which.
Choosing this option allows you to import an autologin profile with the address and credentials for your Access Server, then simply start the connection with the tap of a button. You would not need to re-enter credentials each time you connect. The autoprofile itself contains an embedded secure certificate that identifies and authorizes your connection automatically. It is an optional setting on the OpenVPN Access Server that the administrator of the server can choose to make available to you. If you find you cannot import the autologin profile, your administrator may not have allowed autologin through user permissions.
During investigation of a vulnerability called VORACLE, it was found that using compression to make the data that goes through the VPN tunnel smaller, and thus faster, has an adverse effect on security. To learn more about this see our security notification on our website regarding the VORACLE attack vulnerability. In order to protect our customers, we are disabling compression by default. Some servers of the open source variety can be configured in such a way that the client must do compression, or else the client may not connect successfully. In such a case, you should get the server updated to disable compression. But we understand that this is not always possible, and you may need to be able to connect to such a server. In that event you can go into the settings and re-enable compression.
- OpenVPN Connect v3 supports Windows 7, Windows 8, Windows 10, and Windows 11.
- OpenVPN Connect v2 supports Windows Vista, Windows 7, Windows 8, and Windows 10.
- For Windows XP, you’ll need to get an open source client from the Open Source Community.
Downloading and installing
OpenVPN для Windows 10
|
|
|
| Версия | Платформа | Язык | Размер | Формат | Загрузка |
|---|---|---|---|---|---|
|
OpenVPN 2.4.6 |
Windows 10 |
Русский | 3.9MB | .exe |
Скачать бесплатно |
|
OpenVPN для Android для Android |
Android | Русский | 16.4MB | .apk |
Скачать бесплатно |
|
OpenVPN последняя версия |
Windows | Русский | 5.9MB | .exe |
Скачать бесплатно |
|
OpenVPN русская версия |
Windows | Русский | 5.9MB | .exe |
Скачать бесплатно |
|
OpenVPN x64 |
Windows | Русский | 5.9MB | .exe |
Скачать бесплатно |
|
OpenVPN x32 |
Windows | Русский | 5.9MB | .exe |
Скачать бесплатно |
|
OpenVPN x86 |
Windows | Русский | 5.9MB | .exe |
Скачать бесплатно |
|
OpenVPN 2022 |
Windows | Русский | 5.9MB | .exe |
Скачать бесплатно |
|
OpenVPN 2021 |
Windows | Русский | 5.9MB | .exe |
Скачать бесплатно |
|
OpenVPN 2020 |
Windows | Русский | 5.9MB | .exe |
Скачать бесплатно |
| * скачайте бесплатно OpenVPN для Windows, файл проверен! |
Обзор OpenVPN
OpenVPN – бесплатный сервис с открытым кодом для создания зашифрованных каналов доступа. Позволяет устанавливать безопасное сетевое соединение между компьютерами, клиентами и серверами.
Читать Далее »
OpenVPN скачать бесплатно для windows
Если у вас так и не получилось создать VPN-подключение для Windows 10, то велика вероятность что ваш провайдер блокирует протокол PPTP, который широко используется на всех операционных системах.
В этом случае, чтобы обойти блокировку провайдера лучше всего использовать бесплатный OpenVPN клиент для Windows 10. Эта программа с открытым исходным кодом и считается самой безопасной из подобных ей программ.
Для использования данной программы также понадобится готовая конфигурация и комплект сертификатов, которые помогут подключаться к VPN через протоколы TCP и UDP. Также необходимо будет установить виртуальный Tun/Tap сетевой адаптер, который использует OpenVPN в Windows 10.
Скачать данную программу, Tap-драйвер и комплект сертификатов можно бесплатно. О том, где это сделать, и как настроить бесплатный OpenVPN для Windows 10 я постараюсь подробно рассказать и показать на скриншотах в данной статье.
OpenVPN – это лучшее и наиболее рекомендуемое во всем мире программное обеспечение VPN с открытым исходным кодом, которое обеспечивает безопасное соединение VPN.
Для того, чтобы скачать клиент OpenVPN, необходимо зайти в браузер, в котором уже работает VPN, так как сайт, о котором дальше пойдет речь заблокирован в России по понятным причинам.
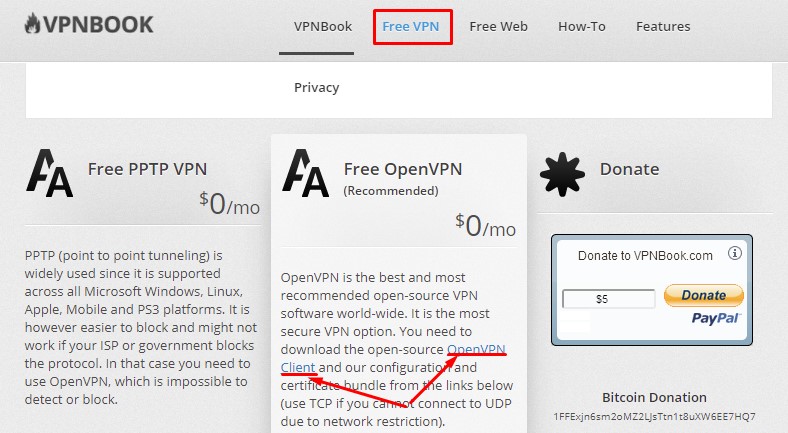
Я рекомендую вам на время установить расширение «Avira Phantom VPN», позволяющие использовать VPN в Яндекс Браузере или Google Chrome. Это позволит вам зайти на сайт «VPNBOOK» и скачать оттуда клиент OpenVPN и комплект сертификатов для настройки подключения.
После того как вы подключили VPN в своем браузере, перейдите на страницу сайта VPNBOOK: https://www.vpnbook.com/freevpn и кликните по ссылке «OpenVPN Client» во втором рекомендуемом вертикальном разделе.
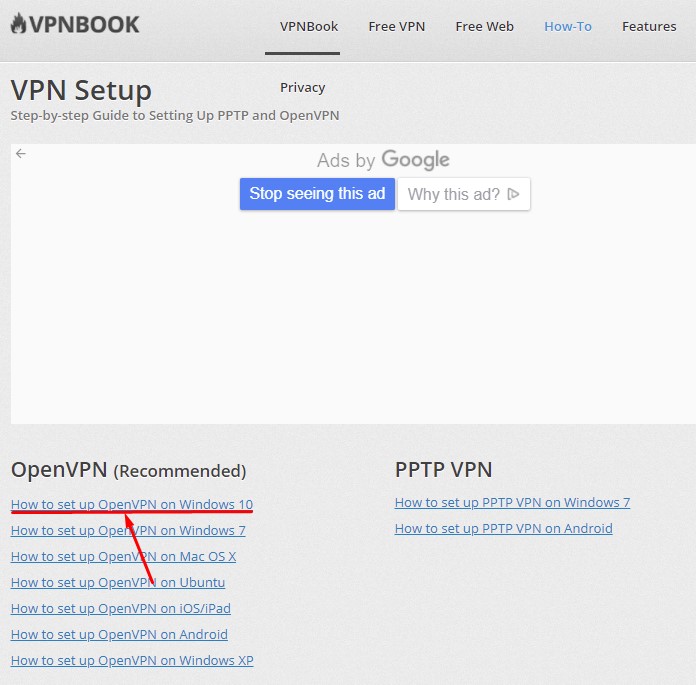
На открывшейся странице перейдите по ссылке «How to set up OpenVPN on Windows 10».
У вас откроется страница в виде слайдов на английском языке, где вы увидите пошаговую инструкцию по скачиванию, установке и настройке клиента OpenVPN. Вы можете ей воспользоваться и сами все настроить. Но если вам что-то не понятно, то читайте дальше я все подробно расскажу.
Кликните на стрелочку вправо на слайдере.
На слайде 1-го шага вы увидите ссылку для скачивания клиента OpenVPN для Windows 10. Кликните по данной ссылке.
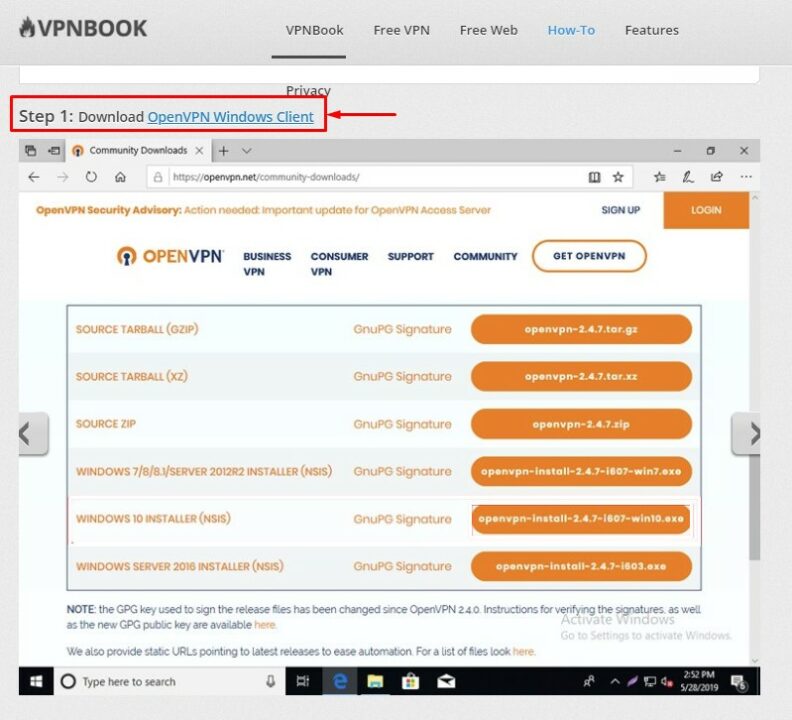
Внимание! После первого перехода по данной ссылке у вас может открыться страница конфиденциальности. В этом случае вернитесь назад стрелочкой в браузере и снова перейдите по данной ссылке.
У вас откроется страница сайта, где можно будет скачать клиент OpenVPN. В зависимости от разрядности вашей системы выберите установочный пакет.
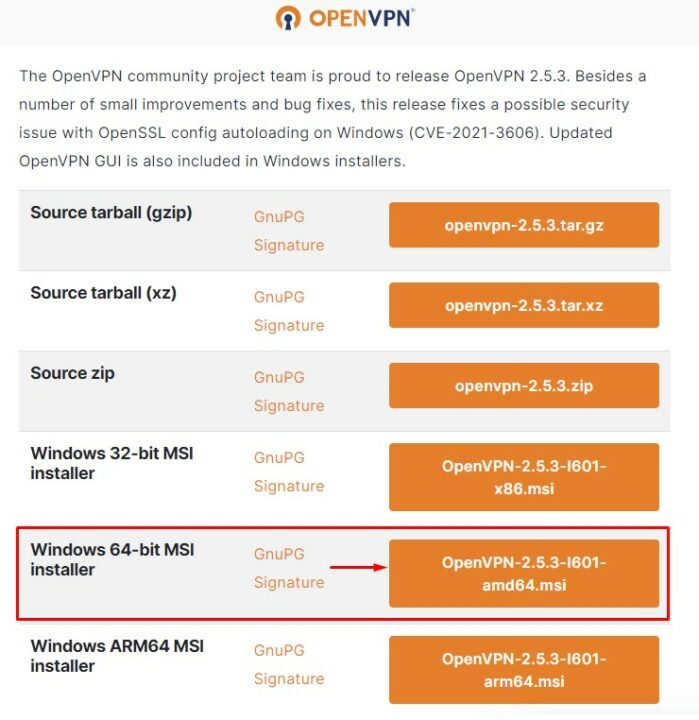
Сохраните файл в удобное для вас место. (я сохранил в папку «Загрузки»). Затем запустите двойным кликом левой кнопки мыши данный установщик и в открывшемся окне нажмите кнопку «Install Now».
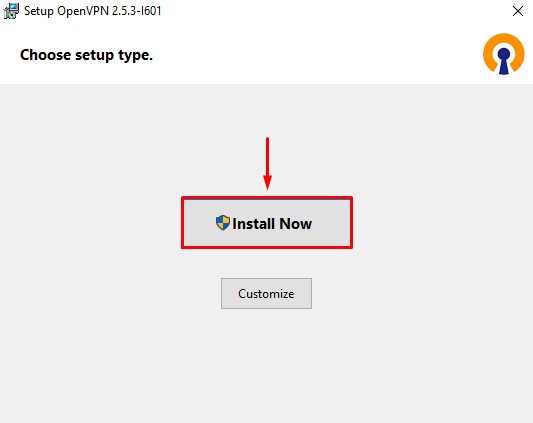
Дождитесь завершения установки и закройте окно, нажав на кнопку «Close». После этого у вас запуститься окно и появится сообщение, в котором будет написано, что файлы конфигурации не найдены.
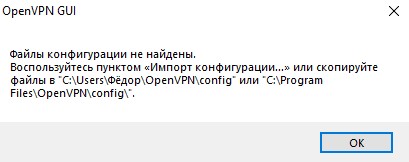
Это те самые сертификаты, которые необходимо скачать и добавить в папку с файлами конфигурации.
Закройте это окно, и переходите ко второй части инструкции. Скачиванию и установке Tap-драйвера.
Установка виртуального Tun/Tap сетевого адаптера
Для того, чтобы установить виртуальный Tun/Tap сетевой адаптер, который необходим для работы программы OpenVPN, необходимо скачать Tap-драйвер с официального репозитория OpenVPN и запустить его установку с правами администратора.
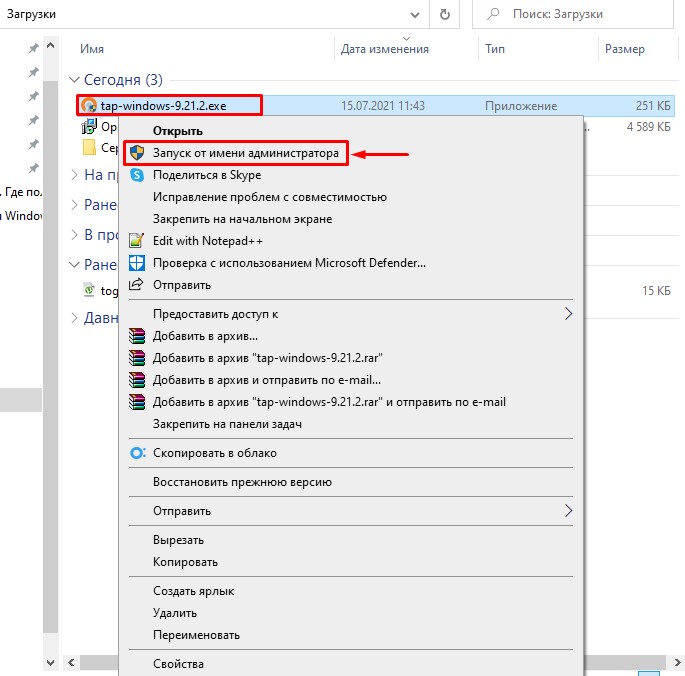
При установке ничего не меняйте и со всем соглашайтесь.
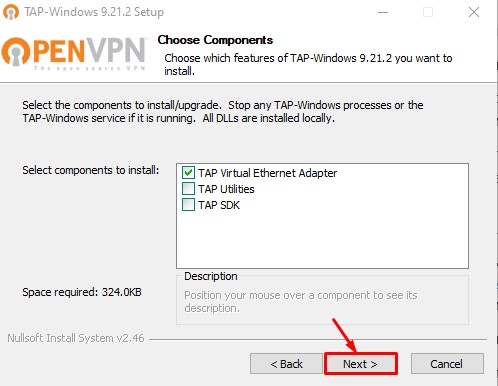
В конце нажмите «Finish». И на этом установка Tap-драйвера будет завершена.
Теперь переходите к третьей завершающей части инструкции в которой необходимо будет скачать сертификаты с VPN, установить их и подключиться к VPN.
Пошаговое руководство по настройке OpenVPN в Windows 10
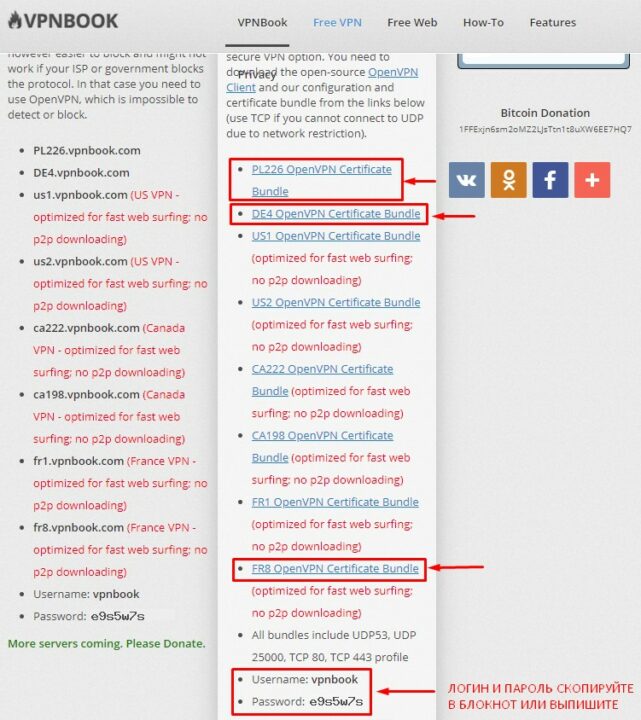
Для того, чтобы настроить OpenVPN в Windows 10 необходимо скачать комплекты сертификатов, а также выписать в блокнот логин и пароль для их подключения.
Вернитесь на страницу сайта VPNBOOK на вкладку меню Free VPN. И поочередно скачайте сертификаты с VPN тех стран, которыми вы планируете пользоваться.
К примеру, я выбрал для себя: Польшу, Германию и Францию. Также скопируйте или выпишите в блокнот логин и пароль, который подходит для всех VPN-подключений.
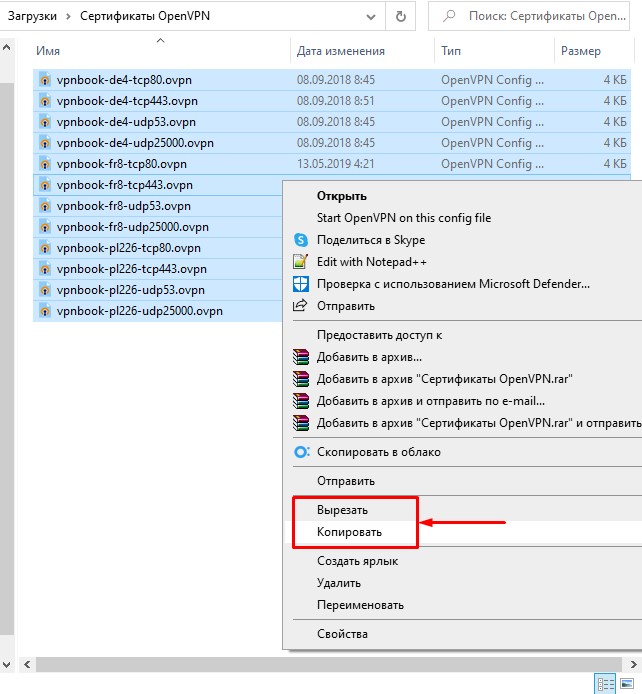
После скачивания архивов с комплектами сертификатов, извлеките их из архива, а сами архивы можете удалить. Затем выделите их все, кликните по ним правой кнопкой мыши и выберите «Копировать» или «Вырезать».
Откройте папку «config» там, где установилась программа OpenVPN, и кликнув правой кнопкой мыши, выберите «Вставить». У меня это выглядит так.
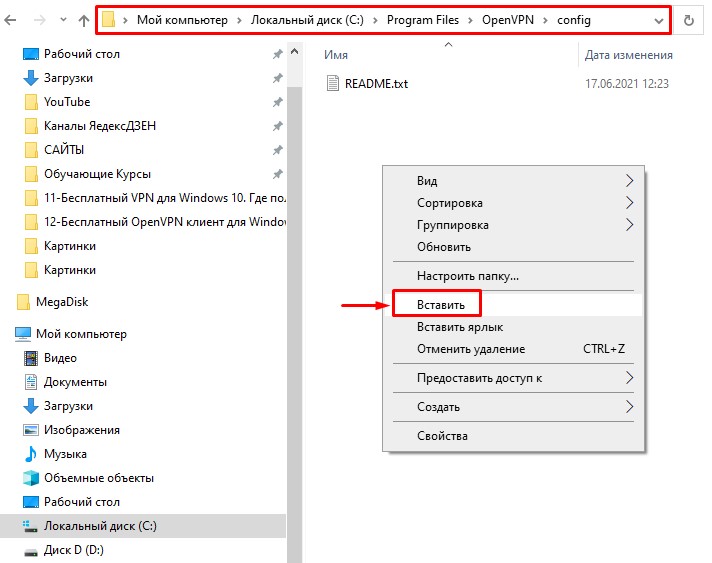
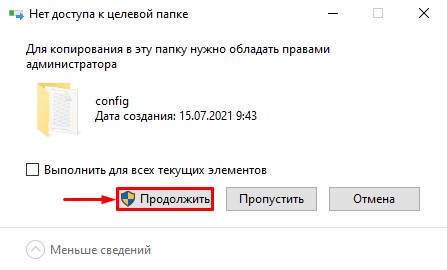
Если у вас откроется окошко, требующее прав администратора, то поставьте галочку «Выполнить для всех текущих элементов» и нажмите «Продолжить».
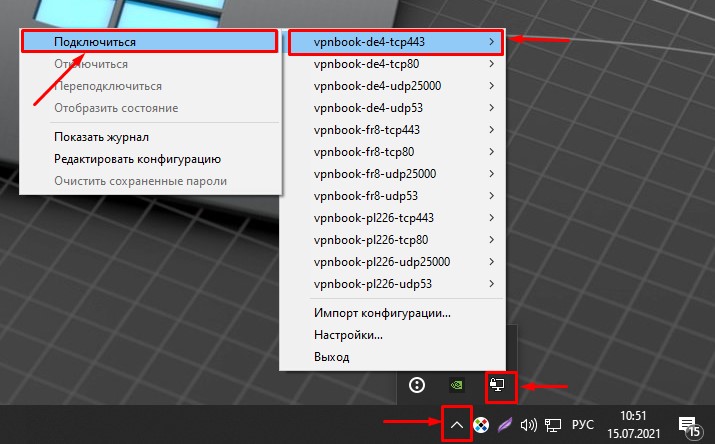
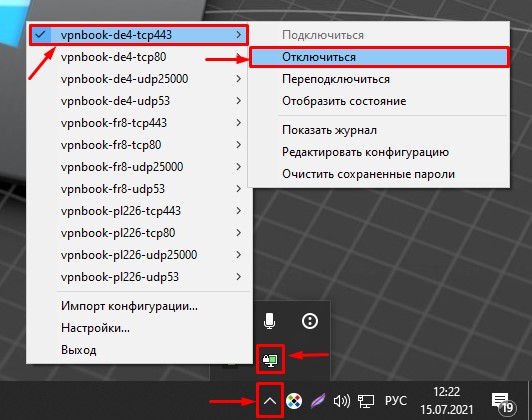
После установки программы OpenVPN, и если она запущена, нажмите на стрелочку «Отображать скрытые значки» и кликните правой кнопкой мыши по иконке программы (монитор с замочком). Выберите любое подключение и нажмите «Подключиться».
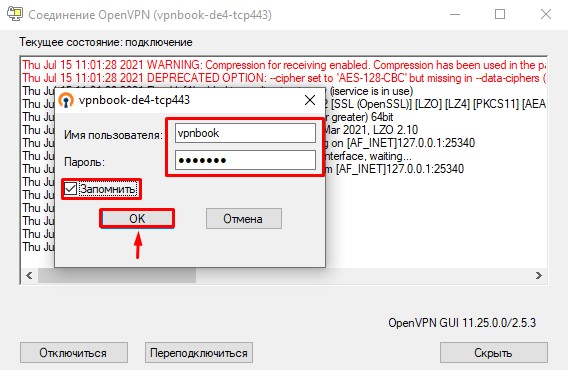
В открывшемся окне введите, ранее выписанные логин и пароль, установите галочку «Запомнить», и нажмите «ОК».
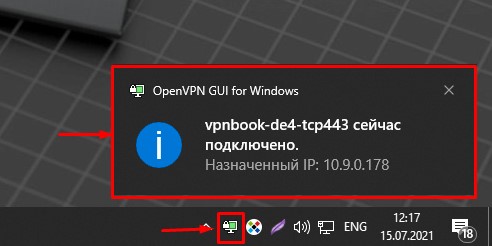
Если вы все сделали правильно и нигде не ошиблись, то у вас выйдет сообщение об успешном подключении, а иконка приобретет светло-зеленый цвет.
Чтобы отключиться, кликните по этой же иконке правой кнопки мыши, выберите ваше VPN-подключение и нажмите «Отключиться».
Видео. Бесплатный OpenVPN клиент для Windows 10. Поможет если ваш VPN блокирует Провайдер!
На этом все! Ваш бесплатный OpenVPN клиент для Windows 10 установлен и настроен. Теперь можете проверить свой ip-адрес и убедиться, что он изменился. Все заблокированные в России сайты доступны для вас.
Надеюсь вам помогла данная статья. Буду вам очень благодарен если вы поделитесь ей в социальных сетях и оставите свой отзыв в комментариях.
OpenVPN
для Windows
OpenVPN — кроссплатформенный инструмент для безопасного туннелирования IP-сетей через единственный UDP или TCP-порт с поддержкой аутентификации сессий и обмена ключами на основе SSL/TLS, шифрования, аутентификации и сжатия пакетов. Поддерживается широкий спектр конфигураций, динамических IP-адресов и NAT, присутствует возможность настраивать удаленный доступ, VPN-соединения типа «точка-точка» и пр.
Основные возможности OpenVPN:
- Поддержка прокси серверов, включая HTTP, SOCKS, NAT и сетевые фильтры.
- Сетевые операции через TCP или UDP транспорт.
- Туннелирования IP-сетей через единственный UDP или TCP-порт с поддержкой аутентификации сессий.
- Эффективное сжатие трафика.
- Поддержка нескольких протоколов шифрования (MD5-HMAC, RSA) и 2048-битного ключа.
- Возможность настраивать удаленный доступ.
- Поддержка динамических IP-адресов и NAT.
- VPN-соединения типа «точка-точка».
ТОП-сегодня раздела «Анонимайзеры, VPN»
Tor Browser 12.5.6
Предоставляет надежную защиту персональной информации и конфиденциальности, которая…
Planet VPN 2.1.19.1
Бесплатный VPN с возможностями, функционалом и защищенностью на уровне топовых платных…
AdGuard VPN 2.1.0
Удобный инструмент для интернет-безопасности и защиты конфиденциальности в Сети,…
Windscribe 2.6.14
Удобное решение, которое представляет собой набор инструментов, которые работают вместе…
DNS Jumper 2.2
DNS Jumper — небольшое бесплатное приложение для быстрого переключения DNS на ПК для повышения уровня безопасности или увеличения скорости работы в Интернете…
Отзывы о программе OpenVPN
Сергей про OpenVPN 2.5.7 [12-07-2022]
OpenVPN-2.5.7-I602-arm64 Win10 очень классная программа, бесплатная и работает на все100%
7 | 13 | Ответить
Валерий про OpenVPN 2.5.6 [24-03-2022]
Хрень, полная ни фига эта прога не меняет ваш регион и ип. Зря качал.
6 | 39 | Ответить
Алексей в ответ Валерий про OpenVPN 2.5.7 [18-01-2023]
Ну если не знать для чего существует данная программа, то хаять конечно же проще.
Свою задачу она выполняет на все 100%
7 | 8 | Ответить



