If you are a pen-tester, cracking passwords is something you will be doing on a daily basis. This can include login passwords, file passwords, and almost anything that is protected using a password.
John the Ripper (JtR) is a popular password-cracking tool. John supports many encryption technologies for Windows and Unix systems (Mac included).
One remarkable feature of John is that it can autodetect the encryption for common formats. This will save you a lot of time in researching the hash formats and finding the correct tool to crack them.
John is also a dictionary-based tool. This means that it works with a dictionary of common passwords to compare it with the hash in hand. Here is a common password list called rockyou.txt.
While you can use popular wordlists like RockYou, John also has its own set of wordlists with thousands of common passwords. This makes John very effective when cracking systems with weak passwords.
This is how John works by default:
- recognize the hash type of the current hash
- generate hashes on the fly for all the passwords in the dictionary
- stop when a generated hash matches the current hash.
This is not the only way John finds a password. You can also customize John based on your requirements. For example, you can specify the password format using the — — format flag.
In this article, we will first install John followed by a walkthrough of the different modes you can use. We will then use John to crack passwords for three different use cases — a Windows password, a Linux password, and a zip file password.
A quick disclaimer before we get started: do not use this tool for nefarious purposes. This is meant to be an educational tutorial to help you protect yourself and your clients or team from password attacks. Use this information responsibly and safely!
Let’s get cracking.
If you are using Kali Linux, John is pre-installed. You can use John by typing the following command:
$ johnFor Ubuntu/Debian, you can get John from the apt source. Here is the command to install John in Ubuntu:
$ apt install JohnIn Mac, you can find John in Homebrew:
$ brew install johnFor windows and other operating systems, you can find the binaries here.
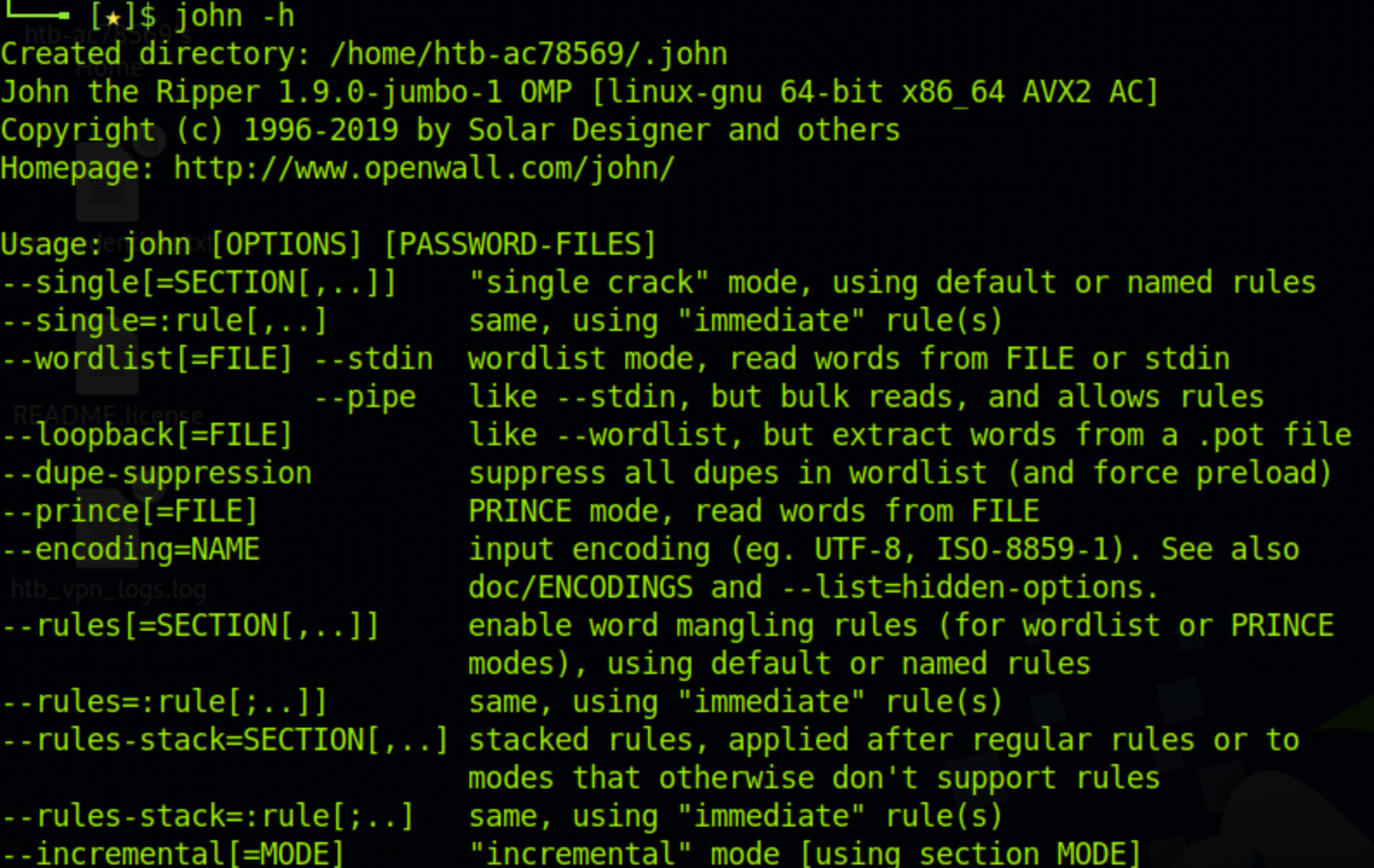
Once you have installed John, try the help command to make sure your installation is working. The help command can also be used as a reference when working with John.
$ john -hHere is the output of the help command:
How to Use John the Ripper
Now that we know what John is, let’s look at the three modes it offers you. You will be using one of these three for most of your use cases.
- Single crack mode
- Wordlist mode
- Incremental mode
Let’s look at each one of them in detail.
What is Single Crack Mode?
In single-crack mode, John takes a string and generates variations of that string in order to generate a set of passwords.
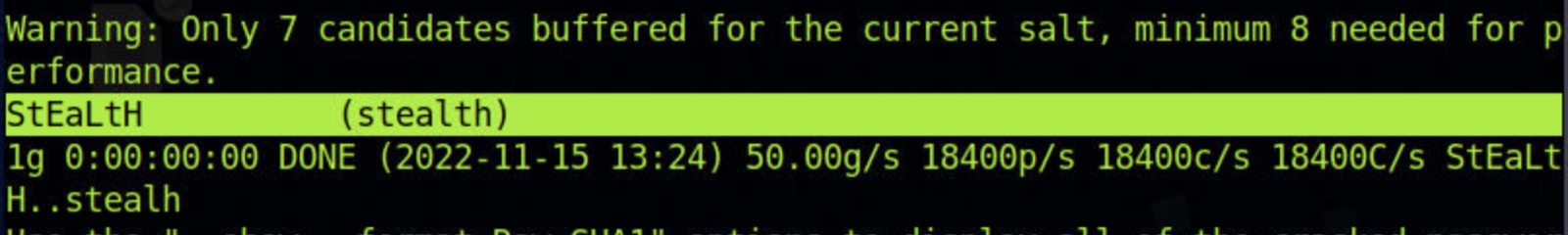
For example, if our username is “stealth” and the password is “StEaLtH”, we can use the single mode of John to generate password variations (STEALTH, Stealth, STealth, and so on).
We use the “format” flag to specify the hash type and the “single” flag to let John know we want to use the single crack mode. We will also create a crack.txt file which will contain the username and the hash value of the password.
stealth:d776dd32d662b8efbdf853837269bd725203c579Now we can use the following command to use John’s single crack mode:
$ john --single --format=raw-sha1 crack.txtAnd here is the result. You can see that John has successfully found the correct password “StEaLtH”.
That was fun, wasn’t it? Now let’s look at the dictionary mode to crack more complicated passwords.
What is Dictionary Mode?
In dictionary mode, we will provide John with a list of passwords. John will generate hashes for these on the fly and compare them with our password hash.
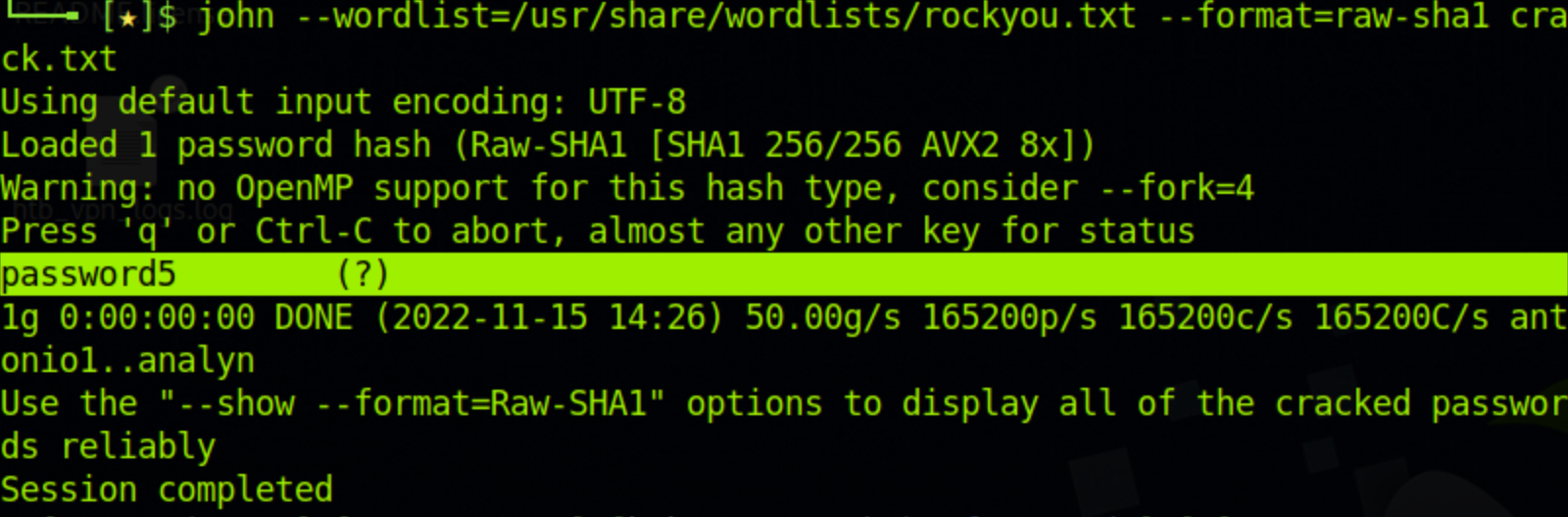
For this example, we will use the RockYou wordlist. If you are using Kali, you can find it at /usr/share/wordlists/rockyou.txt. We will also have a crack.txt file with just the password hash.
edba955d0ea15fdef4f61726ef97e5af507430c0Here is the command to run John in dictionary mode using the wordlist.
$ john --wordlist=/usr/share/wordlists/rockyou.txt --format=raw-sha1 crack.txtAnd John finds the password pretty quickly.
The weaker the password is, the quicker John can figure it out. This is why it is always recommended to have strong passwords.
What is Incremental Mode?
Incremental mode is the most powerful mode provided by John. It tries all possible character combinations as passwords.
This sounds great, but there is a problem. The cracking can go on for a long time if the password is too long or if it’s a combination of alphanumeric characters and symbols.
You will rarely use this mode unless you have no other option. In typical cases, a combination of Social Engineering attacks and wordlist mode will help you crack most of the hashes.
If you would like to try the incremental mode, here is the syntax.
$ john -i:digits passwordfile.txtHere, the -i flag tells John that we want to use the increment mode. The “digits” placeholder can be used to set the maximum number of digits in the password.
You can also add the “format” option to make it easier for John to start cracking.
Use Cases for John the Ripper
Now that you understand the different modes of John, let’s look at a few use cases.
We will use John to crack three types of hashes: a windows NTLM password, a Linux shadow password, and the password for a zip file.
How to Crack a Windows Password
Let’s start with Windows. In Windows, the password hashes are stored in the SAM database. SAM uses the LM/NTLM hash format for passwords, so we will be using John to crack one.
Getting passwords from the SAM database is out of scope for this article, but let’s assume you have acquired a password hash for a Windows user.
Here is the command to crack it:
$ john --format=lm crack.txtThe crack.txt will contain the password hash. If John is unable to crack the password using its default wordlist, you can use the RockYou wordlist using the — — wordlist flag.
How to Crack a Linux Password
Now, let’s crack a Linux password. In Linux, there are two important files saved in the /etc folder: passwd and shadow.
- /etc/passwd -> stores information like username, user id, login shell, and so on.
- /etc/shadow -> contains password hash, password expiry, and so on.
In addition to the “john” command, John comes with a few other utilities. One of them is called “unshadow”.
The unshadow command combines the passwd and shadow files together into a single file. This can then be used by John to crack passwords.
Here is how we use the unshadow command:
$ unshadow /etc/passwd /etc/shadow > output.dbThis command will combine the files together and create an output.db file. We can now crack the output.db file using John.
$ john output.dbJohn tries to find the password for all the users in the passwd file and generates the output with the list of cracked passwords. Again, you can use custom wordlists via the — — wordlist flag.
How to Crack a Zip File Password
Finally, let’s crack a zip file password. To do that, we first have to get the hash of the zip file’s password.
Like unshadow, John has another utility called zip2john. zip2john helps us to get the hash from zip files. If you are cracking a .rar file, you can use the rar2john utility.
Here is the syntax to get the password hash of a zip file:
$ zip2john file.zip > zip.hashesThe above command will get the hash from the zip file and store it in the zip.hashes file. You can then use John to crack the hash.
$john zip.hashesJohn also has several other functionalities that will help you crack a variety of passwords. You can find the complete documentation for John here.
How to Defend Against Password Attacks
So far we have seen how to crack passwords with John the Ripper. But how do we defend against these types of brute-force attacks?
The simplest way to defend against password attacks is to set a strong password. The stronger the password is, the harder it is to crack.
The second step is to stop using the same passwords for multiple sites. If one site gets hacked, your password will be exposed to the internet. A hacker can then use the email/password combination to test your credentials across other sites. You can check if your password is on the internet here.
The final step would be to generate random passwords and use a password manager. There are a variety of options including the Chrome built-in Google password manager. If you use a strong password for each site you use, it becomes extremely hard to crack your password.
Summary
John is a popular and powerful password-cracking tool. It is often used by both penetration testers and black hat hackers for its versatility and ease of use.
From automated hash discovery to dictionary-based attacks, John is a great tool to have in your pentesting toolkit.
Hope this article helped you to understand John the Ripper in detail. You can connect with me here or visit my blog here.
Learn to code for free. freeCodeCamp’s open source curriculum has helped more than 40,000 people get jobs as developers. Get started
Are you looking for a secure and reliable way to protect your Windows 10 system from malicious attacks? John the Ripper is a powerful tool used to detect weak passwords and make it more difficult for hackers to gain access to your system. In this guide, we’ll take you through how to correctly install and use John the Ripper on Windows 10 to secure your system and keep your data safe.
John the Ripper is a free and open-source password cracking tool available for Windows 10. It uses a combination of techniques to detect weak passwords. To use John the Ripper on Windows 10, here are the steps:
- Download the latest version of John the Ripper from the official website.
- Extract the ZIP file and copy the John folder to the C:\ drive.
- Open a command prompt as administrator and navigate to the C:\John directory.
- Run the command john –test to test your computer’s capabilities.
- Create the password file to use with John the Ripper by running the command john .
- Run the command john –format=format to crack the passwords.
- Once John the Ripper has finished, use the command john –show to see the cracked passwords.
What Is John The Ripper?
John The Ripper is a free and open-source software program used for password cracking. It is designed to identify weak passwords that can be easily guessed or cracked with the help of a dictionary attack. It is a cross-platform tool that can be used on different operating systems, including Windows 10.
John The Ripper is a powerful tool for recovering lost passwords, as well as for testing password strength. It is a popular choice among security professionals and ethical hackers for its simplicity and ability to identify weak passwords quickly.
Downloading and Installing John The Ripper
The first step in using John The Ripper on Windows 10 is to download and install the latest version of the software. The latest version can be found on the official John The Ripper website. Once the download is complete, double-click on the downloaded file to begin the installation process.
The installation process is straightforward and will guide you through each step. Once the installation is complete, you will be able to launch John The Ripper and start using it to crack passwords.
Using John The Ripper
John The Ripper can be used in a variety of ways to crack passwords. The most common use is a dictionary attack, which is a method of cracking a password by trying thousands of common words and phrases. This type of attack is useful for cracking simple passwords that are easy to guess.
John The Ripper can also be used for brute-force attacks, which involve trying all possible combinations of characters to crack a password. This type of attack is more time-consuming but can be used to crack complex passwords.
Creating a Password List
Before using John The Ripper, you need to create a password list that contains all of the words and phrases that you want to use in your attack. It is important to include as many words and phrases as possible in the list to ensure that the attack is successful.
The password list can be created in a text editor, such as Notepad, or using a dedicated password list generator. Once the list is complete, save it in a text file and make sure to store it in a secure location.
Performing the Attack
Once the password list is ready, you can begin the attack. To do this, open John The Ripper and select the type of attack you want to perform. If you are performing a dictionary attack, you will need to select the dictionary option and then enter the path to the password list you created.
For a brute-force attack, you will need to enter the character set and the length of the passwords you want to crack. Once all of the options have been entered, click “Start” to begin the attack.
Analyzing the Results
When the attack is complete, John The Ripper will display the results. If the attack was successful, the passwords that were cracked will be displayed in the results. It is important to analyze the results carefully and make sure that the passwords are secure.
It is also important to note that John The Ripper is not guaranteed to crack every password. If the attack was unsuccessful, you may need to try a different type of attack or increase the length of the character set.
Security Considerations
John The Ripper is a powerful tool for recovering lost passwords, but it can also be used for malicious purposes. It is important to use the software responsibly and never attempt to crack passwords without the owner’s consent.
It is also important to keep in mind that John The Ripper is not a substitute for strong passwords. It is still important to use strong passwords and to change them regularly to ensure the security of your accounts.
Conclusion
John The Ripper is a powerful and popular tool for password cracking. It can be used to identify weak passwords and recover lost passwords, but it is important to use the software responsibly and to remember that strong passwords are still the best defense against malicious attacks.
Related FAQ
What is John the Ripper?
John the Ripper is a free, open-source password cracking tool that can be used to recover lost or forgotten passwords. It can be used to crack passwords on Windows, Linux, and OS X systems. The tool is written in the C programming language and utilizes a variety of password cracking algorithms. It is highly effective and can be used to crack passwords quickly and efficiently.
How does John the Ripper work?
John the Ripper works by taking a list of passwords and running a series of algorithms to try and match each password with an existing hash. If a match is found, the password is then revealed. John the Ripper also includes a number of built-in rules that can be used to optimize the process of guessing passwords, such as replacing certain characters with other characters or appending characters to the end of passwords.
What are the benefits of using John the Ripper?
John the Ripper has a number of benefits over other password cracking tools, such as its speed and efficiency. It is also highly configurable, allowing users to customize the tool to their needs. Additionally, John the Ripper is a free and open source tool, which makes it accessible to anyone.
How do I use John the Ripper on Windows 10?
In order to use John the Ripper on Windows 10, you will first need to download the John the Ripper software and install it on your system. Once it is installed, you can then create a text file containing the list of passwords that you wish to crack. You can then run John the Ripper, providing the path to the text file containing the passwords, and it will attempt to crack each password.
Are there any risks associated with using John the Ripper?
Yes, there are some risks associated with using John the Ripper, particularly if the passwords being cracked are associated with sensitive information. Therefore, it is important to ensure that only authorized personnel have access to the tool and that the passwords being cracked are not associated with any sensitive information.
Is John the Ripper easy to use?
Yes, John the Ripper is relatively easy to use. The tool includes a user-friendly graphical user interface (GUI) which makes it easy to select the passwords that you wish to crack and configure the settings. Additionally, the tool includes a number of built-in rules and settings which can be used to optimize the process of guessing passwords.
How to install John The Ripper tool in Windows 10 || Easy To use || Environment Variable
John the Ripper is a powerful and useful tool for those who need to secure their Windows 10 system from malicious attackers. It is easy to use and provides comprehensive protection against various threats. With its advanced features, John the Ripper is a great choice for Windows 10 users who want to protect their system from any potential harm. By following the steps outlined in this article, you can easily and quickly use John the Ripper to secure your system against malicious attacks.
Время на прочтение
6 мин
Количество просмотров 33K
На данный момент хэш можно вскрыть пятью способами: грубый перебор (брутфорс), подбор по словарю, по словарю с правилами (гибридная атака), rainbow таблицы (радужные таблицы) и криптоатака. Сами хэши можно разделить на обычные хэши, и хэши с солью (salt, «затравка»). Эта статья посвящена программам john и mdcrack. На их примере, также рассмотрим основные методы для реализации брутфорса.
john
John the Ripper password cracker предназначен для вскрытия различных типов хэшей, которые применяются во множестве ПО и ОС, от MySQL до OpenBSD. В программе реализованы возможности: брутфорс пароля, подбор пароля по словарю и гибридная атака. А также signle и external способы подбора пароля, специфичные для этой программы. О всех способах будет рассказано ниже.
В программе имеется возможность восстанавливать процесс подбора после его прерывания.
Одной из особенностей программы является тот факт, что при вскрытии большого количества паролей «за раз», велика возможность того, что они вскроются быстрее, чем бы вскрылись по отдельности. А также инкремент пароля производится «интеллектуально», о чём будет сказано ниже.
В программе имеются два ограничения: john может вскрывать хэши только с солью — для вскрытия обычных хэшей вам потребуется соответствующий патч или готовая спец. сборка программы; можно брутфорсить пароль длиной не более 8-ми символов (но при атаке по словарю такого лимита нет).
Salt (соль, «затравка») — это метод усложнения вычисления хэша. К примеру, во FreeBSD, при вычислении хэша от пароля, сначала генерируются два случайных символа, которые конкатенируются к паролю, от полученной строки вычисляется хэш, и к полученному хэшу прибавляются эти два символа, давая результирующий хэш.
Для тестирования скорости программы на вашем компьютере, запустите её с флагом ‘—test’. Результат будет выдан в c/s, т.е. в символах в секунду, а не в h/s (хэш в секунду), как это принято в других программах этого типа. Но каждый следующий символ образует новый пароль. А значит, перебирая, к примеру, 3500 символов в секунду, мы генерируем 3500 новых паролей в секунду. Следовательно, цифры, которые даёт команда john —test — это и есть хэши в секунду.
Для начала работы программы, запишите вскрываемый хэш в файл: user:hash, где user — это любая строка, и hash — вскрываемый вами хэш. Если вам требуется вскрыть сразу несколько хэшей, то нужно записать их всех в один файл. Как сказано выше, велика вероятность того, что так все хэши вскроются быстрее, чем если бы они были записаны в разные файлы по отдельности. Например, создадим файл bla.pass такого содержания:
user1:$1$yHJlM1Y9$lzO5yVj6Drepbz6xje0wq0
user2:$1$RDBUtZMr$z8acZKa5XzY0vQuUwG6Un1
user3:$1$EP5lm7ex$poOrQvYoH78Bc63nhXx1p1
user4:$1$ths1/RY5$CUR32fPoOr/UcjeBpD4fx0
Что бы начать перебор, дайте команду john bla.pass. Программа скажет о количестве загруженных хэшей, о количестве различных salt-ов (в старых unix-системах salt был фиксированным, т.е. одинаковым у всех паролей) и о типе хэшей. Тип хэша может определится не верно. Так, если попытаться вскрыть обычный md5_128bit (без salt), то рассматриваемая в этой статье версия john-а определит этот хэш как NT LM DES, и начнёт подбор пароля, заведомо безрезультатно.
После начала перебора, может пройти вечность до того, как пароль вскроется. Что бы попытаться вскрыть пароль в разумные сроки, у john-а есть целый арсенал различных типов подбора (режимов работы), правил, фильтров и гибкий файл конфигурации. Далее будут коротко рассмотрены режимы работы john-а. Дополнительную информацию читайте в документации к программе.
Итого, john имеет 4 режима работы, т.е. 4 способа вскрытия пароля: single crack, wordlist, incremental и external.
Single crack mode
— поиск пароля по косвенным уликам. Первыми кандидатами в пароли становятся имя пользователя, «GECOS», «Full Name» — поля его учётной записи и название домашней директории пользователя. А также используются правила (гибридная атака) для полученных данных, и возможных паролей становиться больше. Но не так много как в прилагаемом к программе словаре. Поэтому это самый быстрый способ. Он завершает свою работу (перебирает все возможные этим способы варианты паролей) за несколько секунд.
В GECOS-поле пользователь может записать дополнительные данные о себе, такие как номер телефона, дату рождения и т.п.
Wordlist
— подбор пароля по словарю. Основной словарь весит более чем 600 Mb, распространяется на двух дисках. В нём собраны наиболее употребляемые пароли более чем на 20 языках. Стоит этот сборник паролей 28.25$. Также доступен малый сборник паролей размером 11 Mb. Эффективность этого сборника сомнительна, поскольку он также содержит пароли на более чем 20 языках. У режима wordlist есть «подрежим»: wordlist с правилами (rulets). Это гибридный вид подбора пароля. Набор применяемых правил можно изменять и дополнять своими. Правила описаны в файле конфигурации спецсимволами и специальными флагами, которые читает и обрабатывает john-овский препроцессор правил.
Вы можете скачать некоторые очень полезные словари с сайта passwords.ru
Incremental — грубый перебор, т.е. брутфорс. Настройки перебора хранятся в файле конфигурации. При переборе, программа равномерно распределяет частоту инкремента по длине пароля и набору символов (That’s one reason why this mode deals with trigraph frequencies, separately for each character position and for each password length, to crack as many passwords as possible within a limited time). Есть пять подрежимов инкрементного режима: «All», «Alnum», «Alpha», «Digits» и «LanMan». К примеру «Digits» будет перебирать лишь цифры, «Alpha» — лишь строчные латинские буквы. Также есть возможность создания своего подрежима инкрементного режима. Подробнее — в документации.
External — этот режим даёт возможность применять «фильтры», описанные в файле конфигурации на языке Си с использованием четырёх callback-функций. С помощью этого можно написать свой алгоритм перебора. Но несколько основных уже написаны в файле конфигурации, и ими можно пользоваться.
Все режимы можно совмещать. По дефолту (если не указывать режим и ничего не менять в конфигах) программа сначала отработает single-режим, затем попытается подобрать пароль по словарю, прилагаемому к программе (всего лишь 3108 паролей), затем начнёт перебор паролей (перейдёт в инкрементный режим) длиной от 0 до 8 с азбукой в 96 символов (латинские строчные, латинские заглавные, цифры и символы).
Практический совет: пробуйте сначала те режимы и подрежимы, которые заканчивают свою работу (в случае неудачи) быстрее всех. После завершения работы в режимах single, wordlist и wordlist with rulets, вы, вероятно, начнёте брутфорсить пароль в подрежиме «All». Это может оказаться вашей большой ошибкой, которая отнимет у вас слишком много времени. Вместо этого, сначала попробуйте более быстрые подрежимы в порядке возрастания количества символов: «Digits» (10 цифр), «Alpha» (26 латинских строчных букв), «Alnum» (36 символов — буквы + цифры) и т.п. Поскольку пользователи часто используют простые пароли, сперва следует попробовать более быстрые подрежимы инкрементного перебора. Это может значительно сэкономить вам время.
mdcrack
Программа нацелена на достижение максимальной скорости перебора пароля. Версия программы 1.2 имеет открытый исходный код, но поддерживает всего лишь три вида хэшей: MD4, MD5 и NTLM1. Программа версии 1.5 и 1.7 поддерживает большее число хэшей, в том числе и md5_freebsd, но исходный код в открытом виде не предоставляется. Программу mdcrack удобно использовать для брутфорса, когда стандартная сборка программы john вам не подошла, т.е. когда вам необходимо вскрыть хэш без соли (без salt).
Пример вызова программы mdcrack:
mdcrack -s qwertyuiopasdfghjklzxcvbnm -S 7 c8e5b031cee3fe69955e63f8c5e11509.
После этой команды создастся «сессия», и если вы прервёте перебор, дайте команду mdcrack (без параметров) для возврата к прерванной сессии. Для удаления сессии, дайте команду mdcrack -d.
По завершению или после прерывания работы программы, она выдаёт информацию о производительности компьютера (среднее количество хэшей в секунду).
Флаг -W используется для создания файла предварительно рассчитанных пар pass:hash. Для чтения такого файла используется флаг -R. Для более быстрой работы чтения/записи используется флаг -F.
Флаги -b и -e используются для указания challegne-значения. В некоторых протоколах передачи данных, передаваемый хэш пароля шифруется (вычисляется хэш от передаваемого хэша). Пароль, на который он шифруется в данном контексте называется challegne.
Стоит отметить, что программа mdcrack ищет в хэше коллизии. Дело в том, что одному хэшу может соответствовать несколько паролей (но вероятность этого очень мала), причём разной длины. Если пользователь задал пароль из 9 символов, при подборе такого пароля может выясниться, что другой, более короткий пароль, к примеру из двух символом, имеет точно такой же хэш. И если его ввести атакуемой системе — он будет воспринят как правильный.
Тематические ссылки
- Статья «Заметки: какой брутер выбрать?»: forum.antichat.ru/showthread.php?t=37651
- Словари для вскрытия хэша, и не только: www.passwords.ru
На чтение 2 мин Опубликовано
Приложение John the Ripper или Джон Потрашитель мы уже рассматривали в статье, в составе Kali Linux.
1. Извлечем хэш из Windows
Диспетчер учетных записей (SAM) – файл базы данных в Windows 10/8/7/XP, который хранит пользовательские пароли в зашифрованном виде, который в свою очередб расположен в следующем каталоге:
C:\Windows\system32\config
Первая вещь, которую мы должны сделать – заполучить хэши пароля от файла SAM.
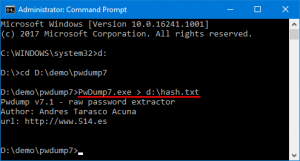
Просто загрузите бесплатное программное обеспечение PwDump7 и разархивируйте его на вашем локальном PC.
Откройте командную строку.
Переместитесь в папку, где вы извлекли приложение PwDump7, и затем вводите следующую команду:
# PwDump7.exe > d:\hash.txt

Как только вы нажмете [ Enter ] PwDump7 получит хэши паролей системы и сохранит их в файл d:\hash.txt.
2. Взлом пароля с John the Ripper
Поскольку вы видите, что хэши пароля все еще нечитабельны – мы должны взломать их используя John the Ripper.
John the Ripper – один из самых популярных инструментов взламывания пароля, который может работать на Windows, Linux и Mac OS x.
Просто загрузите бинарники для Windows John the Ripper и распакуйте содержимое.
Откройте командную строку и смените каталог, куда распаковали John the Ripper и затем выполните:
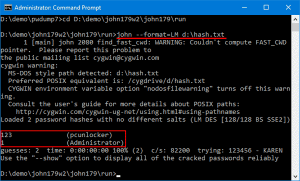
# john --format=LM d:\hash.txt
Теперь мы можем увидеть связки пароль + логин для пользователей Windows.
Примечание: Информация для исследования, обучения или проведения аудита. Применение в корыстных целях карается законодательством РФ.
Пожалуйста, не спамьте и никого не оскорбляйте.
Это поле для комментариев, а не спамбокс.
Рекламные ссылки не индексируются!
Perhaps you need a quick overview on how to use the password-cracking tool John the Ripper, or you may be a beginner and wondering why you haven’t been able to get it to work. If that’s you, you’ve come to the right place. We’ve prepared a straightforward tutorial on how to use John the Ripper for you.
A must-have in the pentester’s toolkit, John the Ripper cracks passwords using a rainbow table approach: comparing them with an inbuilt table of hashes. We’ll review John the Ripper’s three major password-cracking modes and several usage examples, with short exercises for those new to this ruthless tool.
But be warned: We don’t condone using John the Ripper for malicious purposes. With great power comes great responsibility.
Without further ado, let’s get cracking.
Table Of Contents
- What Is John the Ripper?
- John the Ripper Command Generator
- Modes for Cracking Passwords
- Cracking Passwords With John the Ripper
- Other Useful Commands
- Conclusion
- Frequently Asked Questions
What Is John the Ripper?
Jack the Ripper was a murderer in 1888 in London, England. Just as people exposed to Jack the Ripper died, passwords exposed to John the Ripper are no longer secret.
You can deploy John the Ripper inside Kali Linux with the following terminal command instantly:
john
Hence, for simplicity, we’ll call John the Ripper “John” from this point onward. John’s various options help you customize your experience uncovering passwords:
john -h
John the Ripper Command Generator
Say goodbye to the hassle of trying to remember the exact syntax for your John the Ripper commands! With our John the Ripper Command Generator, you can simply say what you need John the Ripper to do, and we will generate the command for you.
Modes for Cracking Passwords
John the Ripper offers three main password-cracking modes: Single, Wordlist, and Incremental.
Single Crack Mode
Our example here is a username-password pair based on the 1986 Tom Cruise movie, which released its sequel in 2022.
In Single Crack Mode, John takes a string and generates variations of that string to generate a set of passwords. For example, you can use this Mode to generate password variations of the username “topgun” with the corresponding password “Topgun” (or TopGun, ToPgUn, tOpGuN, and so on).
Use the --format flag to specify the hash type and the --single (-si) flag to let John know we want to use the Single Crack Mode.
Afterward, we’ll crack more complex passwords with John’s Wordlist Mode.
Try this exercise
- Designate a short string (
topgun) as a username and variations on its capitalization as the password (such as Topgun). - Show the output of the SHA-256-hashed password:
echo -n 'Topgun' | sha256sum - Create a new text file (
simple.txt) to store the username and the password hash value from prior steps:echo -n 'topgun:4558ce5abe3b1e70bbadc3b95f2ff84f54d0a5c30fb524ceebfd401f8233fda7' > simple.txt - Run
simple.txtthrough John the Ripper’s Single Crack Mode (change the--formatargument as you see fit):john --single --format=raw-sha256 simple.txt - Get results.
A self-contained tutorial on generating a password for Single Crack Mode
Oops: If you hash your desired password with the following wrong command instead, you’ll hash an unintended line break at the end:
echo Topgun | sha256sum # wrong command
Wordlist Mode
In Wordlist Mode, we’ll provide John with a list of passwords. John will generate hashes for them in real-time and compare them with our password hash. In this example, we will use the well-known RockYou wordlist, which you can preview at
cat /usr/share/wordlists/rockyou.txt | less
Feel free to copy it to your current working directory to simplify the commands using the --wordlist (-w) flag:
cp /usr/share/wordlists/rockyou.txt rockyou
Now let’s pass text files containing password hashes through John:
john --wordlist=rockyou --format=raw-sha256 crack.txt
john -w=rockyou --format=raw-sha256 crack.txt
Try this exercise
- Pipe a hash based on one or more dictionary words (optionally with numbers) to SHA-256:
echo -n 'password1234' | sha256sum - Write your username, a colon (:), and the hash as a single long string into a new text file
(crack.txt): echo user01:b9c950640e1b3740e98acb93e669c65766f6670dd1609ba91ff41052ba48c6f3>>crack.txt - Repeat Steps 1 and 2 to generate as many username-password pairs as desired and append them to
crack.txt. - Run
crack.txtthrough John the Ripper’s Wordlist Mode:john --wordlist=rockyou --format=raw-sha256 crack.txt - Get results.
Left: John the Ripper Wordlist Mode in action
Right: Generating hashes for three simple passwords
John finds these three passwords rapidly. The weaker the password is, the faster John cracks them.
Let’s move on to John’s final Incremental Mode.
Incremental Mode
In Incremental Mode, John tries all possible character combinations as passwords. This process can be time-consuming if the password is too long or if alphanumeric characters and symbols comprise the password.
You won’t use this Mode unless you don’t have any other options. Typically, a combination of social engineering attacks and Wordlist Mode will help you uncover most passwords.
The syntax for Incremental Mode is:
john --incremental --incremental-charcount=N --format=FORMAT passwords_to_crack.txt
john -inc --incremental-charcount=N --format=FORMAT passwords_to_crack.txt
Let’s break down each flag:
Incremental Mode flags
- The
--incremental (-inc)flag tells John to use the Incremental Mode. - The
--incremental-charcount=Nflag, where N is a positive integer, is for setting the maximum number of digits in the password. - The
--formatoption tells John the hash type of your passwords.
Try this exercise
- Pipe a hash on a simple alphanumeric password to SHA-256:
echo -n 'passw0rd' | sha256sum - Write your username, a colon (:), and the hash as a single long string into a new text file
(inc.txt): echo user02:8f0e2f76e22b43e2855189877e7dc1e1e7d98c226c95db247cd1d547928334a9>>inc.txt - Run inc.txt through John the Ripper’s Wordlist Mode:
john --incremental --format=raw-sha256 inc.txt - Get results.
Generated password hashes
Cracking password hashes in Incremental Mode
Now that we know how to use John the Ripper, we shall move on to specific use cases.
Cracking Passwords With John the Ripper
Now that we know the different modes, let’s examine some real-world examples of when and how to crack passwords with John.
Choosing a Wordlist
John’s default Wordlist is a file located in /usr/share/john/password.lst in Kali Linux, but its power is finite compared with custom wordlists such as those found by John’s developer OpenWall https://www.openwall.com/wordlists/.
Apart from RockYou, the Wordlists all.lst (downloadable as all.gz) and huge.lst are good candidates for the --wordlist flag.
Edit the Wordlist by amending the following line in /usr/share/john/john.conf:
Wordlist = $JOHN/password.lst
To make John work more efficiently, remove duplicate entries from and sort the contents of your chosen Wordlist file.
Cracking ZIP files
John has a utility called zip2john. zip2john helps us to get the hash from zip files. Other “2john” utilities exist, such as the rar2john utility for cracking a RAR file.
To crack a password-protected ZIP file, we first get the hash of the ZIP file’s password:
zip2john file.zip > zip.hashes
This command gets the hash from the ZIP file and stores it in the zip.hashes file.
Now you can crack the hash with John:
john zip.hashes # Single Crack Mode
john --wordlist=rockyou zip.hashes # Using the RockYou wordlist
Try this exercise
- Create a password-protected ZIP archive (
classified.zip) on Kali Linux: right click on a file/folder, select “Create Archive…”, choose “ZIP” as the compression method, expand “Other options” to give it a weak password, and click “Create.” - Export the ZIP hash to
zip.hashes: zip2john classified.zip > zip.hashes - Run
zip.hashesthrough John the Ripper:john zip.hashes - Get results.
Step 1: Create a password-protected ZIP archive on Kali Linux
Steps 2 to 4: zip2john followed by John the Ripper usage

Cracking SSH Keys
The ssh2john utility creates a hash from your private key file. If your private key file path is /home/kali/.ssh/id_rsa, and you want to store the hash as myHash.txt, the syntax is:
ssh2john /home/kali/.ssh/id_rsa > myHash.txt
Try this exercise
- Use the following command to generate an RSA key pair with a passphrase:
ssh-keygen - Export the hashed private key file to a new file
(myHash.txt): ssh2john /home/kali/.ssh/id_rsa > myHash.txt - Run
myHash.txtthrough John the Ripper:john --wordlist=rockyou myHash.txt - Get results
Step 1: Demo of ssh-keygen

Cracking Linux Passwords
Linux stores password data in two files:
/etc/passwdstores information such as username, user id, and login shell;/etc/shadowis the password file containing data such as hash and expiry date.
A utility bundled with John the Ripper called unshadow can combine both files for cracking. Here, we’ll name the combined file lin.txt:
unshadow /etc/passwd /etc/shadow > lin.txt
Cracking Linux hashes is tricky; Kali Linux’s John the Ripper doesn’t readily detect the hash type of Linux (crypt), where the --wordlist flag is optional. If you omit the --format flag below, John won’t crack anything at all:
Once John has uncovered the passwords, you may view them using the command below:
john --show --format=crypt lin.txt
Try this exercise
- Create a new user on Kali Linux:
sudo useradd user1 - Give the new user a weak password:
sudo passwd user1 - Repeat steps 1 and 2 as desired to create two more new user accounts
user2anduser3with weak passwords. - Unshadow the Linux password hashes for all users:
unshadow /etc/passwd /etc/shadow > lin.txt - Export only the usernames and passwords of the three new users to a new file
(lin3.txt): tail -n -3 lin.txt > lin3.txt - Run it through John the Ripper:
john --format=crypt --wordlist=rockyou lin3.txt - Get results.

Cracking Windows Passwords
Windows stores hashed passwords in the SAM database. SAM uses the LM/NTLM hash format for passwords. As getting passwords from the SAM database is beyond the scope of this article, we suggest generating your own LM/NTLM hashes to test out this functionality and echo them to a text file, say win.txt, as shown in the demonstration:
The syntax for cracking this file containing the LM/NTLM hashes is the following, where the --wordlist flag is optional:
john --format=LM [--wordlist=rockyou] win.txt
Once John has uncovered the passwords, you may view them using the command below:
john --show --format=LM win.txt
Try this exercise
- Designate a short string (
topgun) as a username and variations on its capitalization as the password (such asTopgun). - Pass the password from step 1 into an LM/NTLM hash function, such as via a website as shown below.
- Create a new text file (
ntlm.txt) to store the username and the password hash value from prior steps:echo -n 'topgun::0BA224CF1C751F31AAD3B435B51404EE:D66B0428599B168372A76C8AB73A76A2:::' > ntlm.txt - Run
ntlm.txtthrough John the Ripper’s Single Crack Mode (change the--formatargument as you see fit):john --format=LM --single ntlm.txt - Get results. The capitalization of the cracked password may differ from what you’ve intended.
Step 2:
Step 3 and 4:

Choosing Specific Hashes to Crack
If you want to override John’s behavior of discovering the hash independently, you may tell John which hash type you’re looking for using the --format=HASH_TYPE flag. Choices for HASH_TYPE include Raw-MD (MD5), Raw-SHA1 (SHA-1), Raw-SHA256 (SHA-256), SSH, RADIUS, TACACS-Plus (TACACS+), ZIP, and RAR.
You can find all hash formats John supports using the following commands:
john --list=formats
john --list=subformats
Other Useful Commands
Here is a brief cheat sheet of John the Ripper commands:
| Flag | Description |
|---|---|
--show FILE |
Show cracked passwords based on hashes from FILE |
--rules, -ru |
Enable word-mangling rules to teach John the Ripper how to generate passwords |
--status |
Print the status of an interrupted or running session |
--session=NAME |
Give a new John the Ripper session a NAME, to which John will form the session file name NAME.rec; useful for running multiple instances of John in parallel or to be able to recover later a session other than the last one you interrupt |
--restore[=NAME] |
Continue an interrupted cracking session, reading state information from the specified session file or the default session at the file path $JOHN/john.rec |
--save-memory=LEVEL |
Enable memory saving at LEVEL 1, 2, or 3. Level 1 tells John not to waste memory on login names, and may speed things up. Levels 2 and 3 reduce John’s use of performance optimizations involving large lookup tables and thus may impact performance negatively. |
--test[=TIME] |
Run tests (and benchmarks, unless TIME is explicitly 0), each spanning TIME seconds |
& |
This symbol only applies to Kali Linux and other Unix-based operating systems. When you put this symbol at the end of a John the Ripper command, you run it in the background. |
--format=NAME |
Specify the hash type for John the Ripper to detect |
--list=formats, --list=subformats |
Reveal the hash types John the Ripper supports |
--single, -si |
Enable Single Crack Mode |
--wordlist=FILE, -w=FILE |
Enable Wordlist Mode, specifying a Wordlist (dictionary attack) |
--incremental, -inc |
Enable Incremental Mode |
Find the complete official documentation for John the Ripper here.
Conclusion
We hope learning how to use John the Ripper helps you, whether you’re exploring cyber security or aiming to become a professional hacker or penetration tester. For more resources, read our blog posts on hacking and check out our courses below:
Frequently Asked Questions
What can I crack with John the Ripper?
You can crack popular hash formats such as MD5, SHA-1, several DES variants, and Blowfish. Get the full list using the command john --list=formats on the Linux terminal.
How long should John the Ripper take?
Single Crack Mode usually runs for under a second to about a day, depending on the hash type and password length. The more complex your passwords are, the longer it takes; it may take years to crack certain passwords. You may find a detailed answer to this question in the FAQ on John the Ripper’s official documentation.
How does John the Ripper guess passwords?
John the Ripper uses a rainbow table approach: it hashes the guessed password and compares it to the list of password hashes you feed into it. If the hashes match, John remembers the plaintext password associated with it and can return that to the attacker.
Where can I find John cracked passwords?
Use the --show flag and an additional --format flag denoting the hash type if necessary. Example: john --show --format=raw-sha256 crack.txt
Does John the Ripper cost money?
No. It comes free with Kali Linux or as a standalone downloadable utility.
What are the alternatives to John the Ripper?
Another well-known password cracker is Hashcat.
When should I use John the Ripper vs. Hashcat?
Hashcat can do complex cracking using a GPU, but you must adjust its settings to identify the hash yourself. It also requires OpenCL to work. On the other hand, John the Ripper optimizes CPU usage. It seeks quick wins, detects your hash type, and excels in simpler jobs. Experientially it’s also a better choice for cracking SSH keys.
Level Up in Cyber Security: Join Our Membership Today!
-
Cassandra is a writer, artist, musician, and technologist who makes connections across disciplines: cyber security, writing/journalism, art/design, music, mathematics, technology, education, psychology, and more. She’s been a vocal advocate for girls and women in STEM since the 2010s, having written for Huffington Post, International Mathematical Olympiad 2016, and Ada Lovelace Day, and she’s honored to join StationX. You can find Cassandra on LinkedIn and Linktree.
View all posts