A Virtual Private Network (VPN) is used to securely create a tunnel for data between your local computer to a remote server. On Windows Server 2019, you can configure a VPN to provide network access to connected clients and allow connected devices to communicate securely.
This guide explains how to set up a fresh Windows Server 2019 as an L2TP over IPSec, or a PPTP VPN, using the routing and remote access feature. Layer 2 Tunneling Protocol (L2TP) with IPSec offers robust encryption for connections to the server. On the other hand, the Point to Point Tunneling Protocol (PPTP) is simple to deploy but not as secure.
To set up the VPN server, we shall use the built-in Routing and Remote access feature, which offers a graphic interface to configure remote networking features such as Dial-up, LAN routing, NAT, and VPN.
Requirements
-
Deploy a Windows Server 2019 Instance on Vultr
-
Remotely connect to the server and log in as an Administrator
Create a New VPN User
For the VPN service to work well, it must authenticate with a valid user account to the server. So, you need to create a new user on the server.
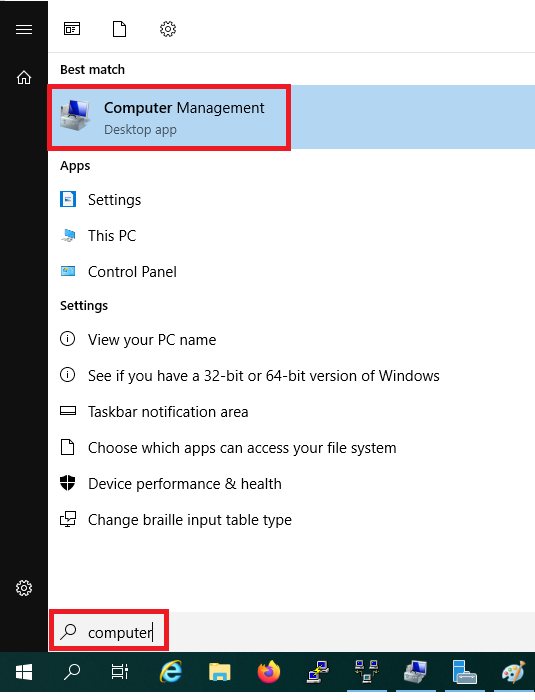
Click Tools under server manager and select Computer Management from the drop-down list to create a new user.
Once the computer management window pops up, expand Local Users and Groups from the left pane and right-click Users to select New User on the sub-menu.
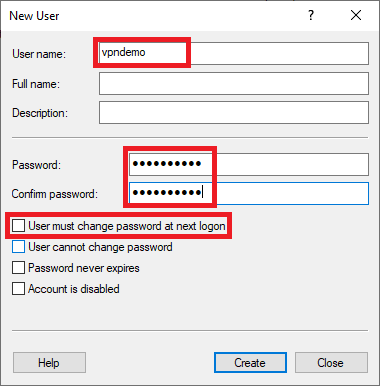
Under the New User dialog box, enter a username, full name, and password for the VPN user, then click create and close the window.
The new user will now be listed on the list of active server users, right-click on the new user and select properties.
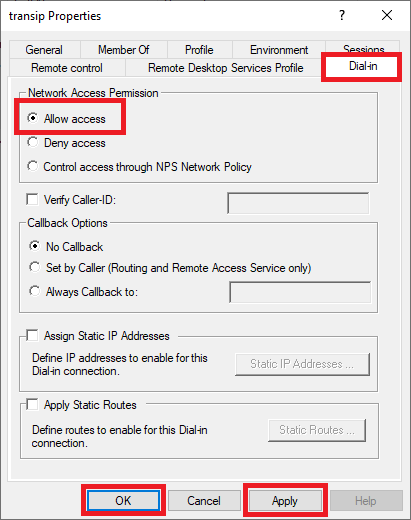
Under the user properties window, navigate to the Dial-in tab and click Allow access under Network Access Permission. Click OK for changes to take effect.
Install the Routing and Remote Access Features
Procedure 1: Through Server Manager
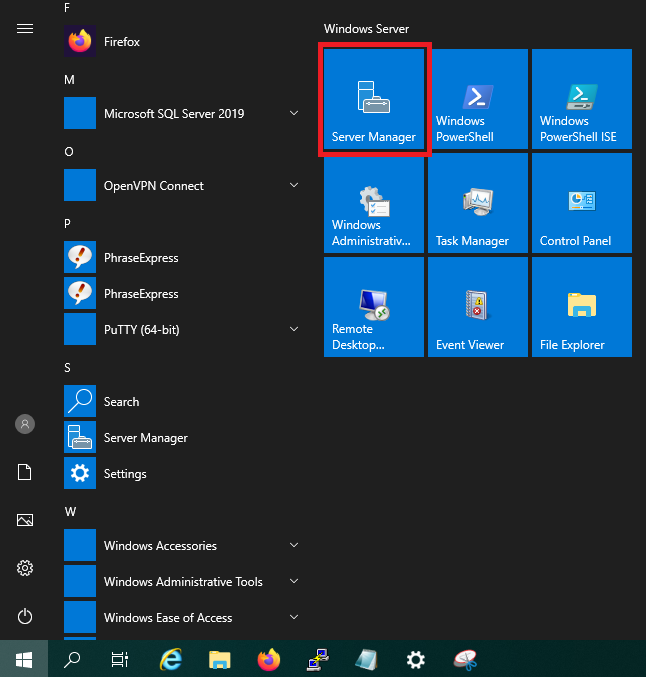
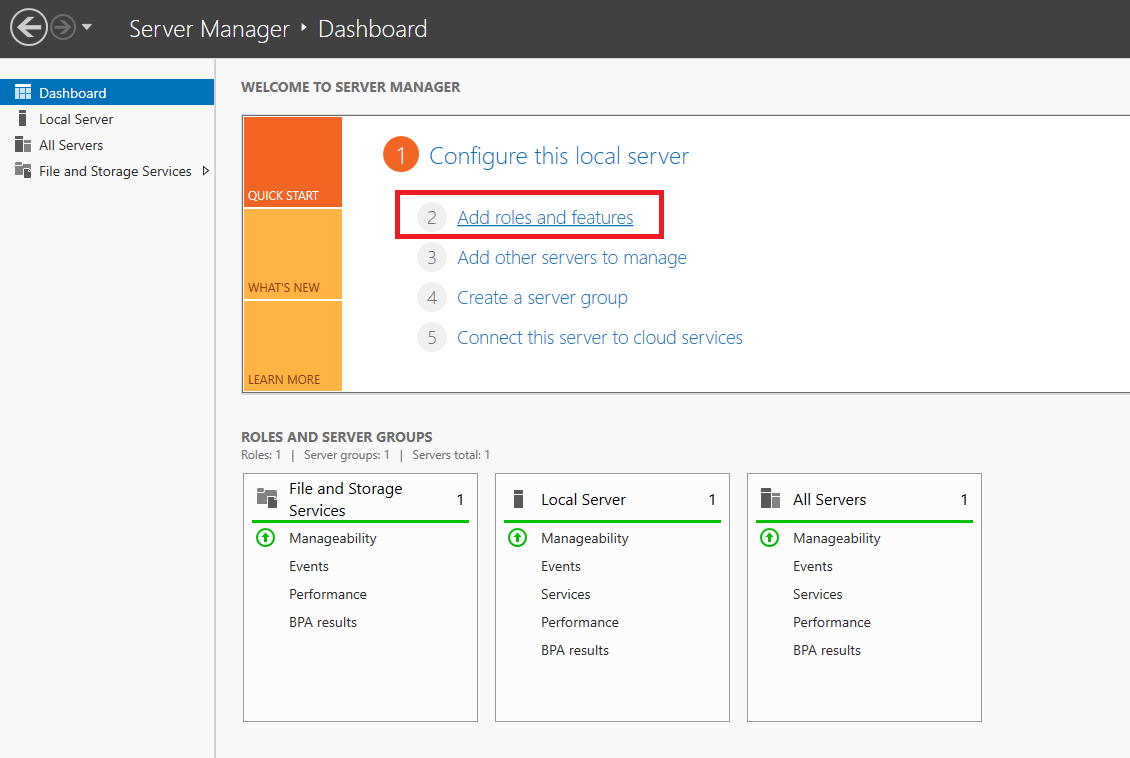
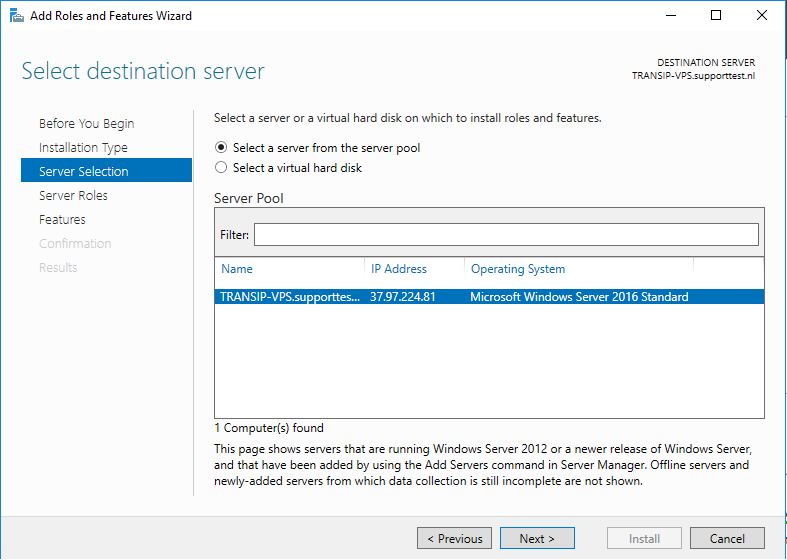
From the Windows start menu, open Server Manager, click Manage, then select Add Roles and Features from the drop-down list.
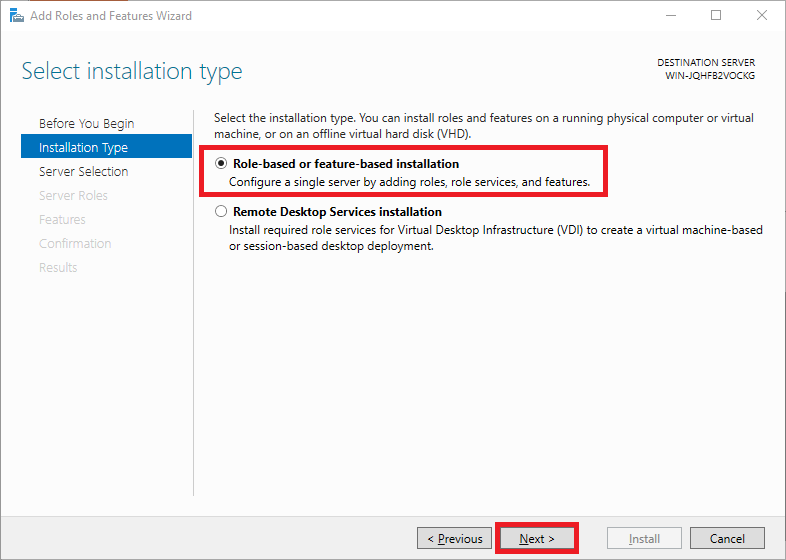
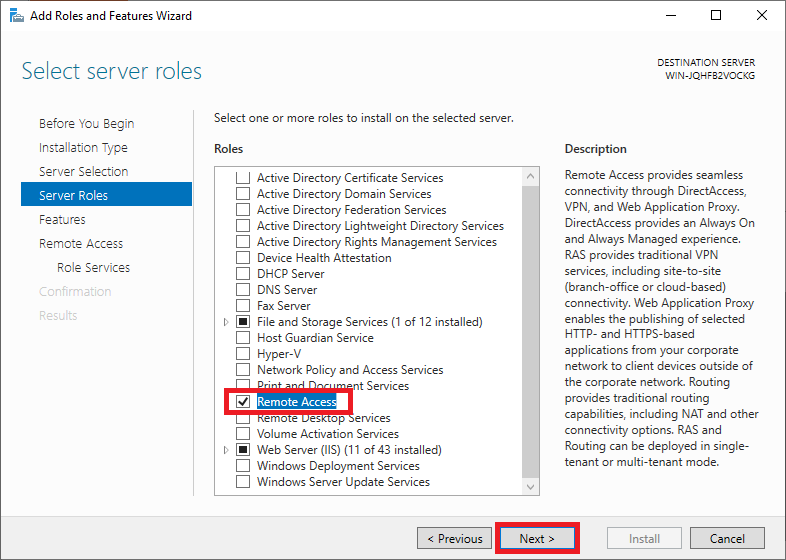
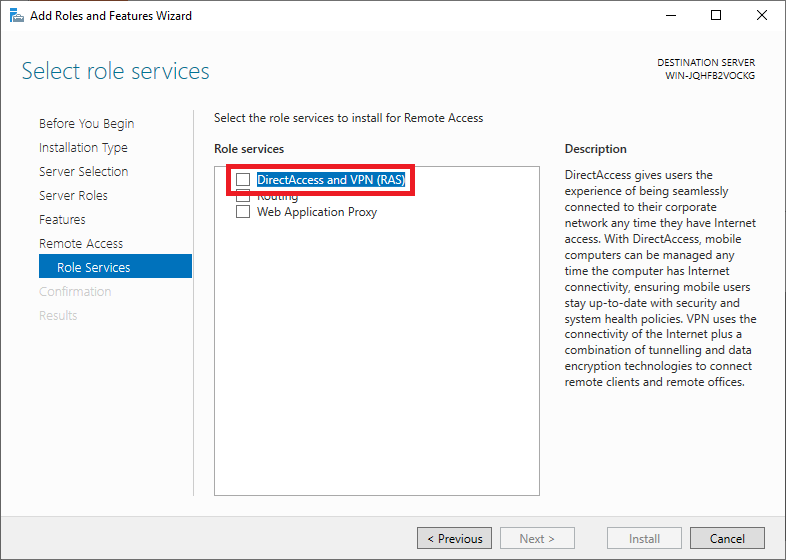
From the open window, click next and select Role-based or feature based installation, then select your server from the pool. Select Remote Access, Remote Access Administration from the list of server roles.
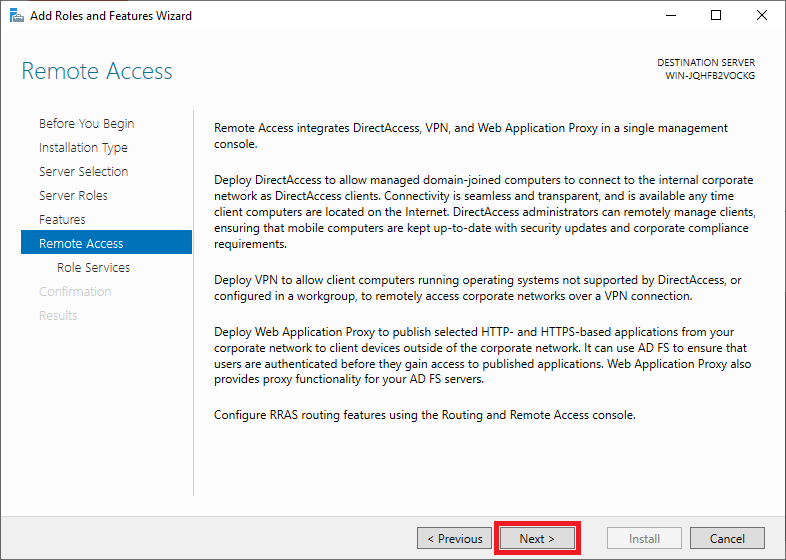
Next, select DirectAccess and VPN (RAS) and Routing from the features list, then click to Install IIS, which is required for remote access to work well.
Procedure 2: Using Windows PowerShell
You can also install Remote Access from Windows Powershell.
From the Windows start menu, open an Administrative Powershell, then install Remote access by pasting the following code to the console.
Install-WindowsFeature RemoteAccess
Install-WindowsFeature DirectAccess-VPN -IncludeManagementTools
Install-WindowsFeature Routing -IncludeManagementTools
Your output should be similar to:
PS C:UsersAdministrator> Install-WindowsFeature RemoteAccess
>> Install-WindowsFeature DirectAccess-VPN -IncludeManagementTools
>> Install-WindowsFeature Routing -IncludeManagementTools
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No Success {Remote Access}
True No Success {RAS Connection Manager Administration Kit...
True No Success {Routing}
Configure Routing and Remote Access
Open Server Manager and click Tools on the top toolbar. From the drop-down list, select Remote Access Management.
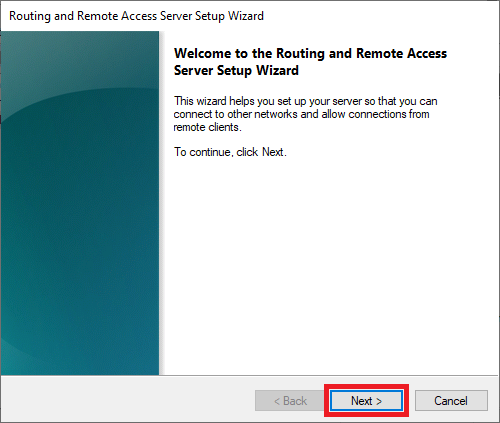
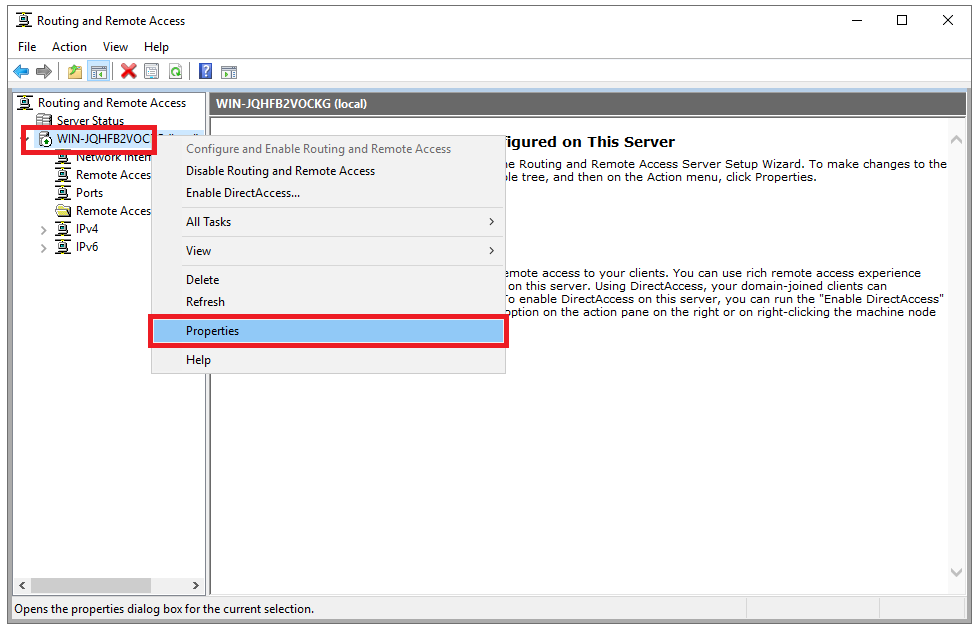
In the open Routing and Remote Access window, right click on your server name just below Server status, then select Configure and Enable Routing and Remote Access from the drop-down menu.
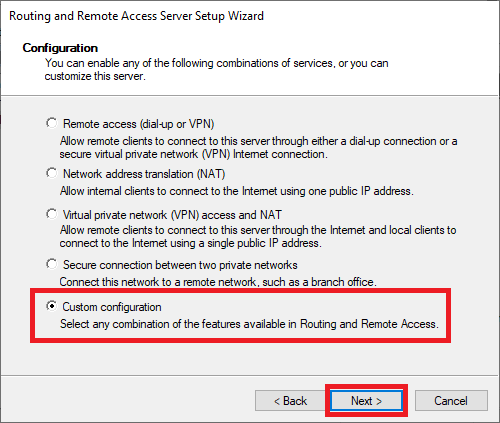
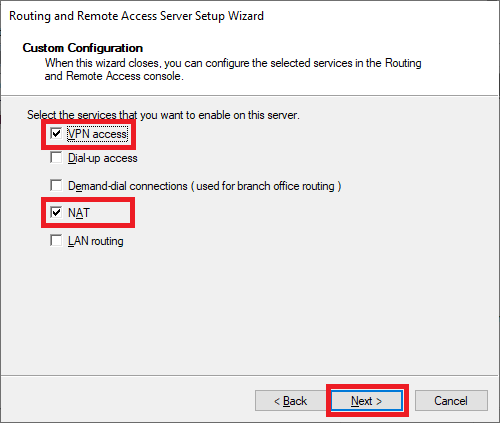
Now, select Custom configuration to configure remote access manually.
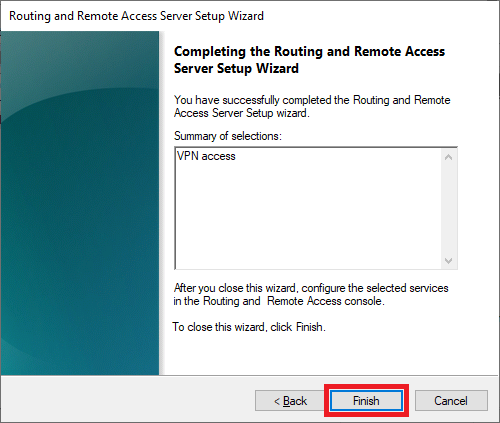
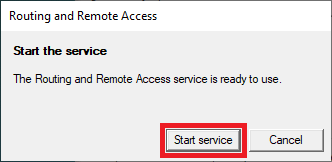
Select VPN Access and NAT as services you want to enable on your server, click next to finish the configuration, and start the service.
Setup a PPTP VPN
Now that Remote Access is running, you can set up your PPTP VPN. To get started, you must assign connected clients** static IP Addresses to avoid possible connection issues. To do this, right-click on your server under the Routing and Remote Access window and select Properties from the drop-down list.
Click IPV4 in the Open Window, then select Static address pool. Now, click Add to craft a new IP Address range from the open pop-up window. In this guide, we use the range 10.0.0.1 to 10.0.0.50, and the server will automatically calculate the number of available addresses.
Click OK to save your static IP Address configuration. You will be prompted to restart Routing and Remote Access for changes to apply; simply click OK.
Configure NAT and enable PPTP
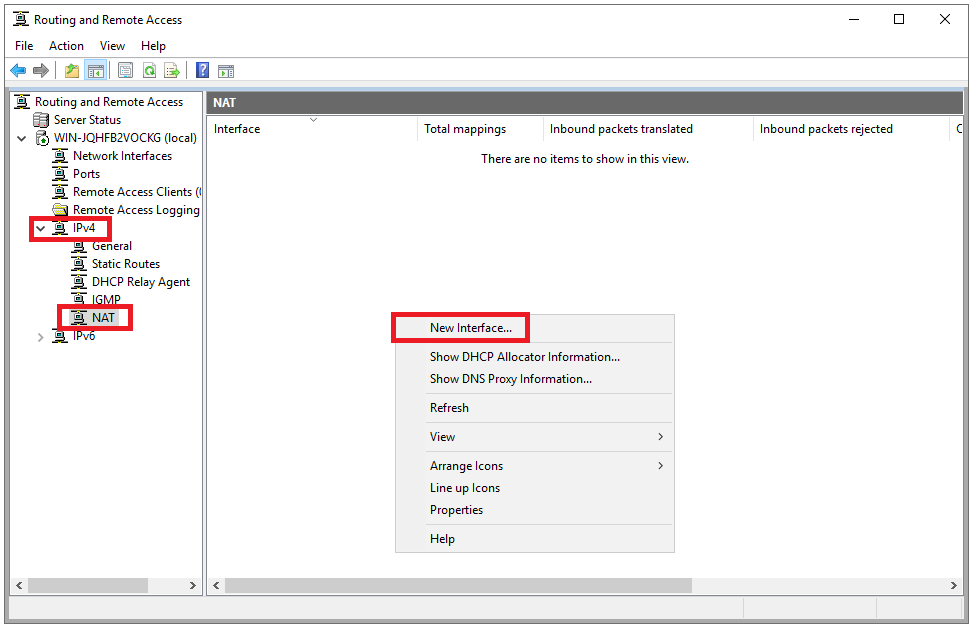
We need to configure Network Address Translation (NAT) for connected clients to use the Internet. On the left pane of the same routing and remote access window, expand the IPv4 options under your server. Right-click on NAT and select New Interface.
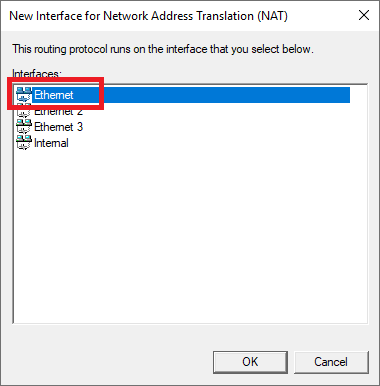
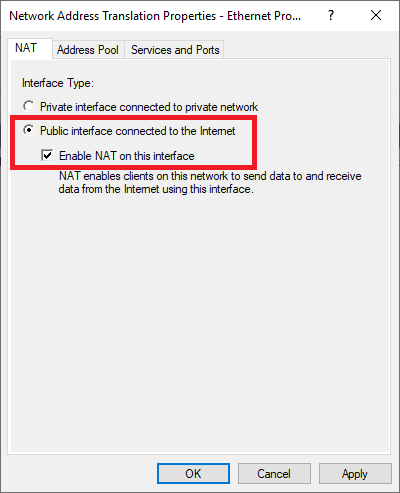
Under the open dialog window, select Public interface and enable NAT on the interface.
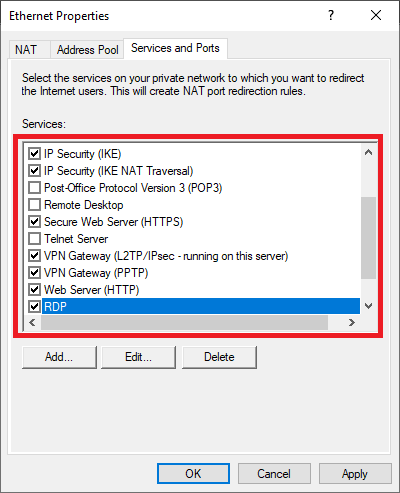
Next, navigate to Services and Ports and click VPN Gateway (PPTP) from the drop-down list.
Click Edit to set a Private address for the VPN service, change the current address 0.0.0.0 to 127.0.0.1, and click OK to save.
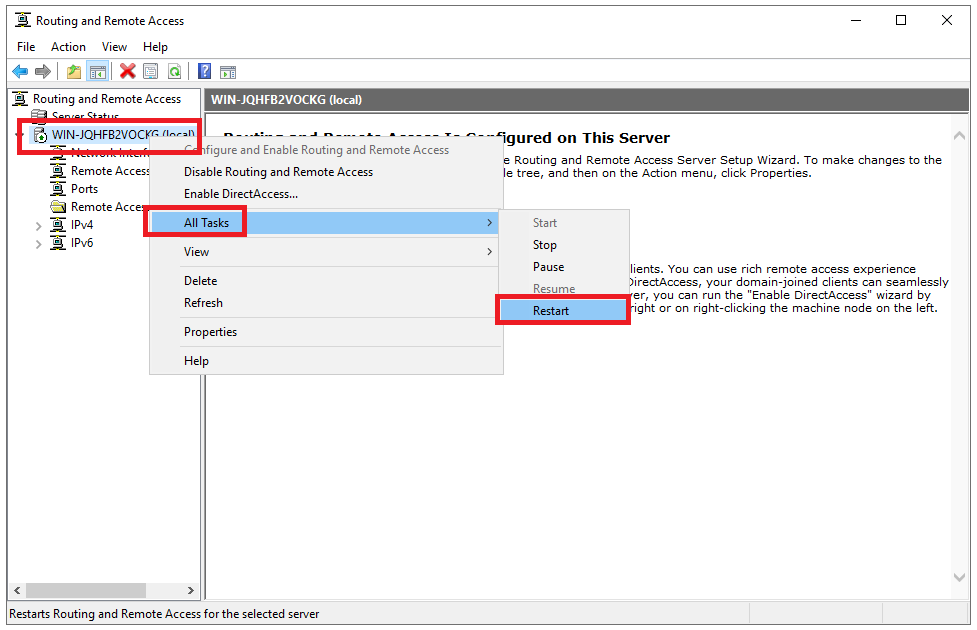
Finally, click OK to save all changes, then right-click on your server from the left pane and click Restart under the All Tasks sub-menu.
This will restart routing and remote access services making your server ready for incoming VPN connections.
Configure Windows Firewall to accept Incoming PPTP VPN Connections
Click Tools from the Windows server manager and select Windows Defender Firewall with Advanced Security from the drop-down list.
Under the open Windows Defender Firewall with Advanced Security window, select Inbound Rules on the left pane, then click New Rule on the right pane.
In the open new Inbound rule wizard, click Predefined and select Routing and Remote Access from the list.
Under predefined rules, choose Routing and Remote Access (PPTP-In), click next to allow the connection, then finish for the new Firewall rule to be applied and test your new PPTP VPN server.
Test your PPTP VPN
Using your personal computer (PC) or Smartphone, go to Networks, Add a new VPN and select PPTP as the VPN type. Then, enter the VPN username and password created earlier to connect.
In this guide, we cover and test the PPTP VPN on a Windows 10 PC. To get started, click the start menu and search for Control Panel, then, click Network and Internet.
Under Network and Internet, open the Network and Sharing Center and click Set up a new connection or network.
Under the open window, select Connect to a workplace and click Use my Internet connection (VPN).
Then, enter your server’s public IP Address (Check your Vultr server dashboard), assign the connection a name, and click create.
Now, on the left pane, click Change adapter settings, then right click your created VPN interface and select Properties.
Under the pop-up, click Security, then choose Point to Point Tunneling Protocol (PPTP) under Type of VPN.
Finally, under Allow these protocols, select CHAP and MS-CHAP v2, then click OK to apply changes.
Your new VPN is configured successfully. Click the network connection icon on the taskbar, select your VPN on the list and click Connect to enter the VPN username and password created earlier to establish a connection to your new PPTP VPN server.
Setup L2TP with IPSEC
Open server manager, click Tools, and open Remote Access Management, then right-click your server on the left pane to select Properties from the drop-down list.
Under server properties, navigate to the Security tab, and click Allow custom IPSec policy for L2TP/IKEv2 connection to enter your new pre-shared key.
In this guide, we use 12345678, choose something stronger, then navigate to IPV4 to set a static address pool and click OK to apply changes.
Keep note of the pre-shared key (PSK) since it will be required for every user establishing a connection to the VPN server.
From the left pane, expand the IPV4 sub-menu and right-click on NAT, then select New Interface. If you set PPTP earlier, click NAT and edit the existing interface you already created.
Navigate to the Services and Ports tab and select VPN Gateway [L2TP/IPSec], then click edit to change the private address from 0.0.0.0 to 127.0.0.1. Click OK to save changes and restart remote access from the left pane under All Tasks.
This will restart Routing and Remote Access, then save the applied L2TP configurations.
Allow L2TP Connections through Windows Firewall
Open Windows Defender with Firewall, select inbound rules and add a new rule. Select Predefined and from the list, choose Routing and remote access.
Under Predefined rules, select Routing and Remote Access [L2TP-In] and click next.
Finally, allow the connection and click Finish to apply the new Firewall rule.
Connect and Test Your L2TP VPN server
In this guide, we test the new L2TP with IPSec VPN on a mac. To get started, open System Preferencesand click Network.
Under the Network Preferences window, click the + sign and select VPN under the Interface dialog box. Then, choose L2TP with IPSec as the VPN Type and assign your connection a name.
Click create, then enter your public server IP Address (server address) and username (Account name). Next, click Authentication Settings to enter your account password and Pre-shared key (Shared secret) created earlier.
Next, click Advanced and select Send all Traffic over VPN Connection, then click Apply, and finally click Connect to establish a connection with your new L2TP VPN server.
Conclusion
You have set up a VPN on your Windows server 2019 instance; you can choose to create both PPTP and L2TP VPNs with different users connecting through your server without any limitations.
For every connected device, they will be able to access the Internet through your server and interact with other connected computers.
This blog post is a step by step guide how to install and configure VPN on Windows Server 2019. The blog post shows you how you can easily set up a VPN server for a small environment, branch office, or for a hosted server scenario. This VPN (Virtual Private Network) server allows you to connect from remote clients or firewalls to the Windows Server.
I already did a similar post for other versions of Windows
- How to Install VPN on Windows Server 2008 R2
- How to Install VPN on Windows Server 2012
- How to Install VPN on Windows Server 2012 R2
- How to Install VPN on Windows Server 2016
To install VPN access to a Windows Server 2019, simply follow this step by step guide:
Install Remote Access Role
First, install the “Remote Access” via Server Manager or PowerShell.
Open Server Manager and select Add Roles and Features
Select the Remote Access Role and click next through the wizard.
On the step Role Services, select the DirectAccess and VPN (RAS)
On the final step, select install to install the Remote Access role.
This might requires a reboot of the server.
Install and Configure VPN on Windows Server 2019
After you have successfully installed, now you can start the wizard to install and configure the VPN server in Windows Server 2019.
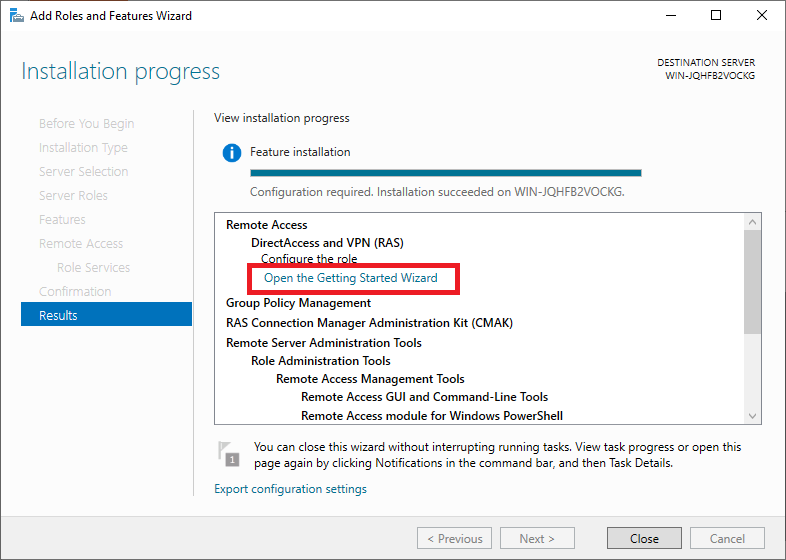
After the features are installed, which can take a while to finish, you see the link for the Getting Started Wizard. Click on “Open the Getting Started Wizard“.
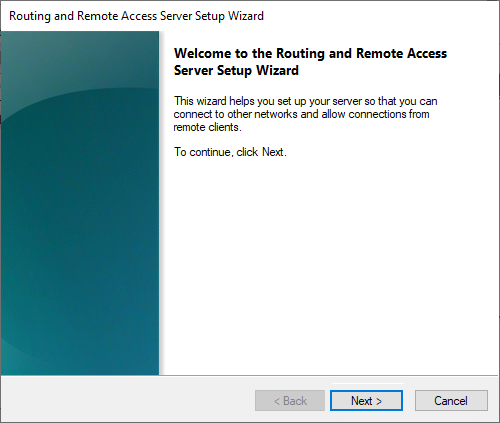
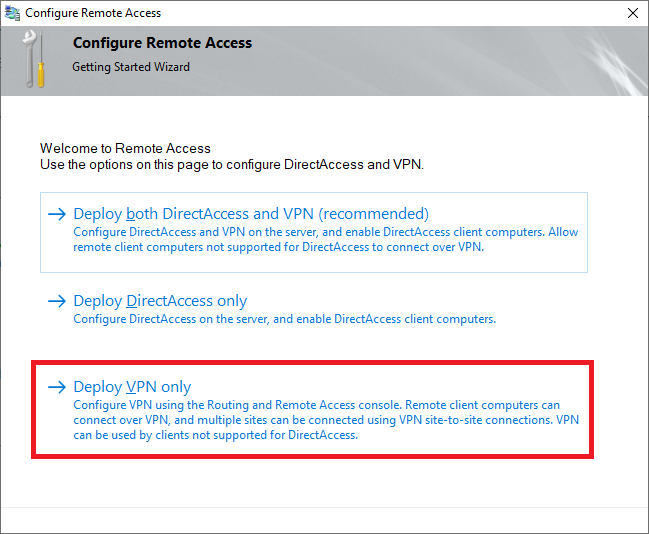
This opens a new wizard which will help you to configure the server. On the first screen, select “Deploy VPN only“.
This opens the Routing and Remote Access Management Console
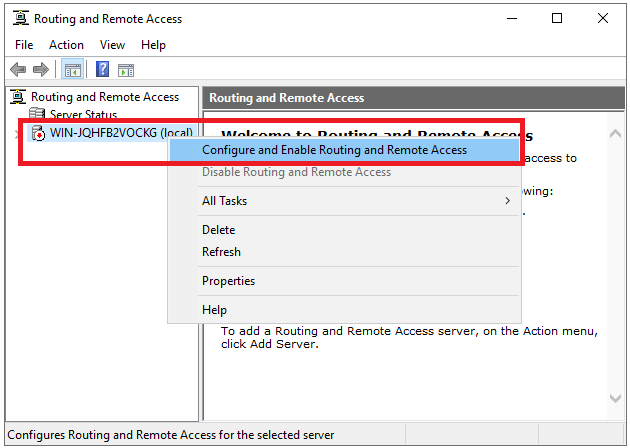
Right click on the Server name and click on “Configure and Enable Routing and Remote Access“.
On the new wizard select “Custom configuration“.
Select “VPN Access“.
After you have click finish, you can now start the Routing and Remote Access service.
Configure VPN Access Users and Network
If you have a firewall between the internet and your Windows Server you have to open the following Firewall port sand forward them to your Windows Server:
For PPTP: 1723 TCP and Protocol 47 GRE (also known as PPTP Pass-through)
For L2TP over IPSEC: 1701 TCP and 500 UDP
For SSTP: 443 TCP
After the installation Users have to be enabled for Remote Access to connect to your VPN Server. On a standalone server this can be done in the Computer Management MMC, in a domain environment this can be done in the user properties of an Active Directory user.
If you don’t have a DHCP Server in your environment, you have to add a static IP address pool. This is often needed if you have a single server hosted at a service provider. In the properties of your VPN server, you can click on the IPv4 tab and enable and configure the “Static address pool”.
You now have to add an IP address from the same subnet as your static address pool to the network interface of your server so that users can access the server.
I hope this helps you to set up a VPN server in a small environment, lab, or hosted server. You can find more information about Windows Server in the Microsoft Docs.
Tags: DirectAccess, Install VPN Server on Windows Server, Microsoft, Remote Access, Virutal Private Network, VPN, VPN Server, Windows Server, Windows Server 2019, Windows Server 2019 VPN, Windows VPN Last modified: July 7, 2019
About the Author / Thomas Maurer
Thomas works as a Senior Cloud Advocate at Microsoft. He engages with the community and customers around the world to share his knowledge and collect feedback to improve the Azure cloud platform. Prior joining the Azure engineering team, Thomas was a Lead Architect and Microsoft MVP, to help architect, implement and promote Microsoft cloud technology.
If you want to know more about Thomas, check out his blog: www.thomasmaurer.ch and Twitter: www.twitter.com/thomasmaurer
A Virtual Private Network (VPN) connection is a private network that connects multiple devices remotely through the Internet. Traffic over the VPN network is sent encrypted. With a VPN connection, you add an extra layer of security to your (company) network. For a more detailed explanation of VPN networks, see our in-depth blog post «What is a VPN connection?».
In this tutorial, we show you how to install a VPN server in Windows Server 2019 and make a VPN connection from another computer, for example, your computer at home.
The steps in this tutorial require an SSL certificate via IIS on your VPN server.
Installing a VPN server
Step 1
Connect to your Windows Server via Remote Desktop or the VPS console.
Step 2
Open the ‘Server Manager‘ via the Windows Start button > Server Manager.
Step 3
Click on ‘Add roles and features‘ in the dashboard of the Server Manager.
Step 4
You will now see the ‘Before You Begin‘ page. You can select not to see this page again when you add roles & features in the future. Click on ‘Next‘ after you have read the points under ‘before you continue‘.
Step 5
Under ‘Installation Type‘ you can choose between ‘Role-based or feature-based‘ and ‘Remote Desktop Services installation‘. Choose ‘Role-based or feature-based‘ and continue to the next step.
Step 6
Select the desired VPS on which you want to perform the installation. If you use an Active Directory and it contains several VPSs, these are listed in this overview. If you do not use Active Directory, you will see the VPS on which you go through this tutorial.
Step 7
On the next page, you can select a ‘Server Role‘. Select ‘Remote Access‘ (including responsible for VPN) and click on ‘Next‘. You do not have to adjust any other options already checked.
Step 8
You do not have to select or adjust features. Click immediately on ‘Next‘ to continue.
Step 9
You will see a description of the Remote Access role. Click on ‘Next‘ to continue.
Step 10
Then select the ‘role services‘ of the Remote Access role you want to use. Click here on ‘DirectAccess and VPN (RAS)‘.
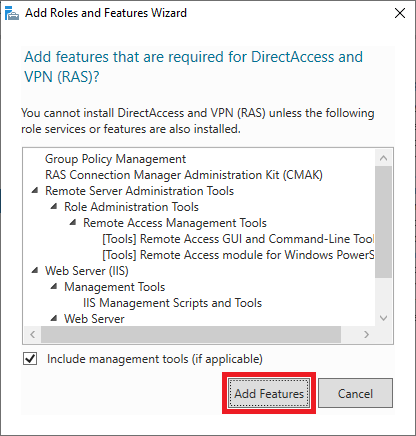
You should probably see a pop-up with an overview of role services and features that need to be added to use the DirectAccess and VPN (RAS). Click on ‘Add Features‘ to have it added automatically.
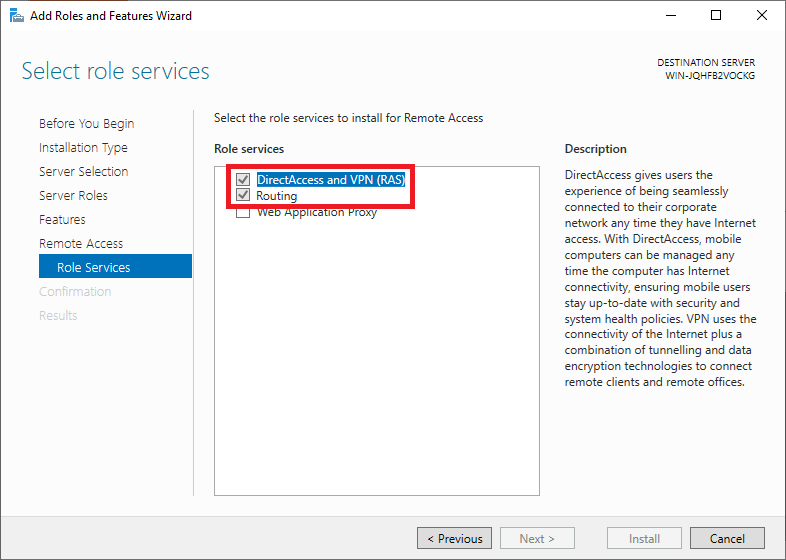
After this, you return to the ‘Role Services‘ screen and the option ‘DirectAccess and VPN (RAS)‘ is checked. Also, check the ‘Routing’ option and click ‘Next‘ to proceed to the next step.
Step 11
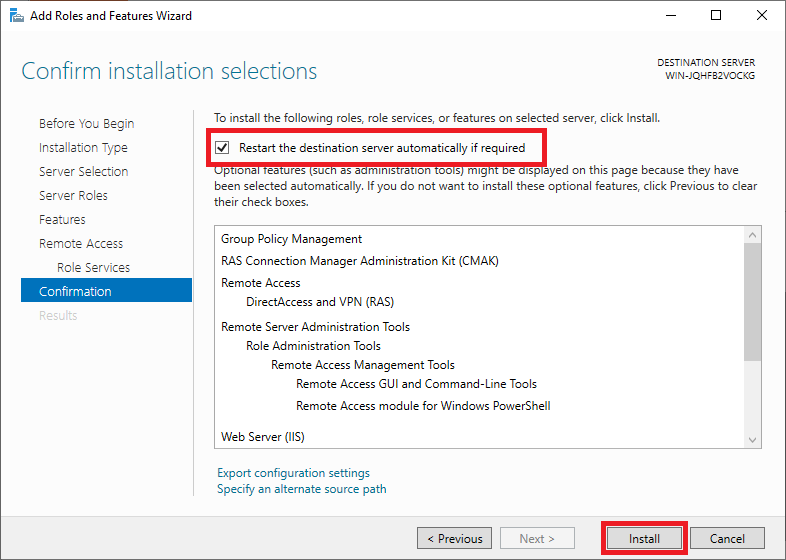
Before the installation starts, you will see a confirmation of the options you selected in the previous steps.
Check ‘Restart the destination server automatically if required‘: it is always important (if an installation requires it) to restart your server to ensure the proper functioning of the role/feature.
Finally, click on ‘Install‘. The installation itself takes a few minutes, so feel free to grab a cup of coffee before proceeding to the next step.
Step 12
Do notclose the confirmation screen after installation, but click on ‘Open the Getting Started Wizard‘. It may take a minute to open. If not, click in the Server Manager on ‘Tools‘> ‘Remote Access Management‘.
Step 13
You are greeted by the screen below. Before proceeding with the wizard, it is useful to first open the necessary ports in your firewall; otherwise, you will get an error after going through this wizard.
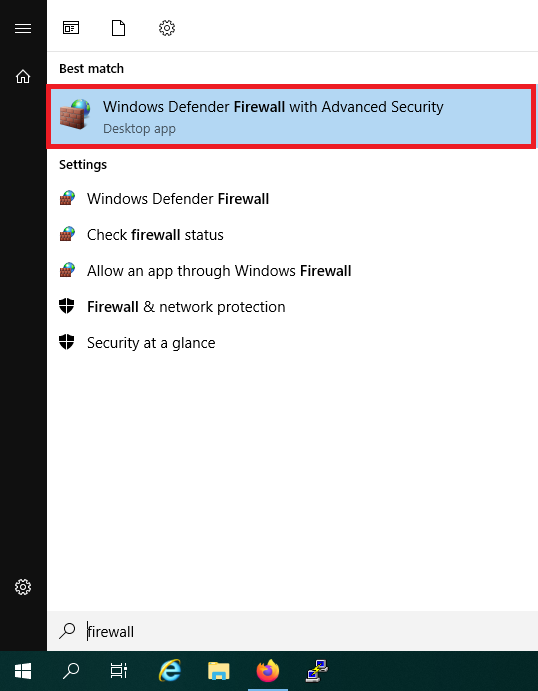
Do notclose the wizard and click the Windows Start button, type ‘firewall‘ and click ‘Windows Defender Firewall with Advanced Security‘ in the search results.
Step 14
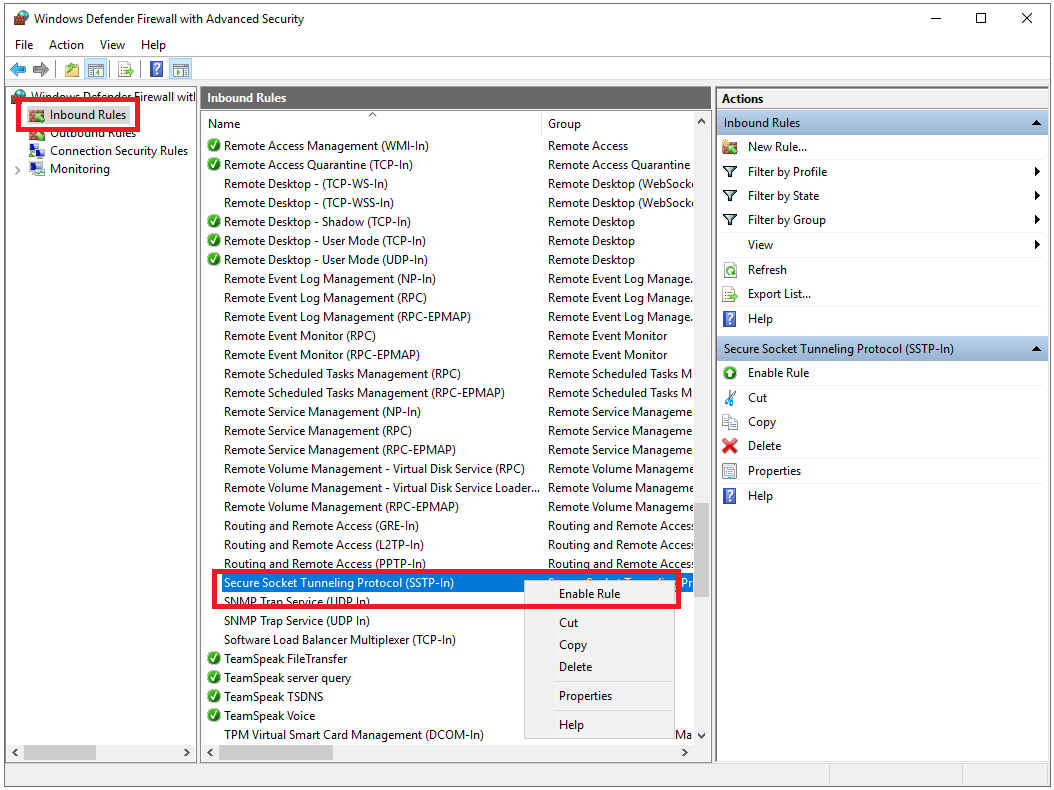
Click on ‘Inbound rules‘ and scroll down to the ‘Secure Socket Tunneling Protocol (SSTP-in)‘. This rule is probably already on. If not, right-click on the line and select ‘Enable rule‘.
There are several protocols you can use for a VPN server. For this tutorial, we choose the best of all worlds: a combination of security (256-bit encryption), stability and speed. The SSTP protocol using the HTTPS port 443 is the best fit, see this page for more information.
Step 15
Then close Windows Defender Firewall with Advanced Security and return to the ‘Remote Access Server Setup Wizard‘ and click ‘Next‘.
Step 16
Click on ‘Deploy VPN only‘.
Step 17
The ‘Routing and Remote Access Management Console‘ now opens. Right-click on the name of your VPS and click on ‘Configure and Enable Routing and Remote Access‘.
Step 18
Click on ‘Custom configuration‘> ‘Next‘ in the Configuration screen. This gives you the option to specifically configure a VPN server instead of installing services that you don’t need.
Step 19
Select ‘VPN Access‘ and ‘NAT‘ and click ‘Next‘.
Step 20
That brings you to the end of the configuration wizard. Click on ‘Finish‘ to complete the configuration.
Finally, you will be given the option to start your VPN server. Click here on ‘Start service‘.
Step 21
You are now back in the ‘Routing and Remote Access Management Console‘, see step 17. Right-click on your VPN server and then ‘Properties‘.
Step 22
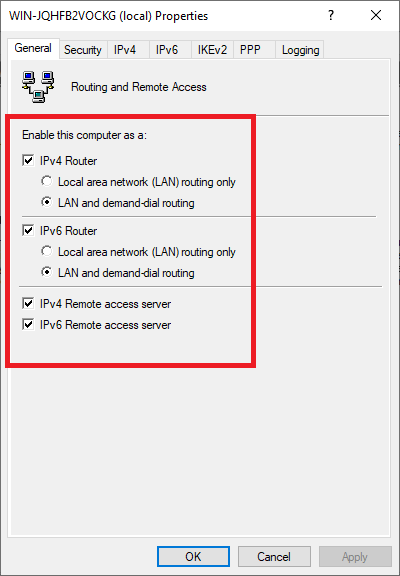
Check both ‘IPv4 Router’ and ‘IPv6 Router‘ with both the option ‘LAN and demand-dial routing‘ and the options ‘IPv4 Remote access server‘ and ‘IPv6 Remote access server‘.
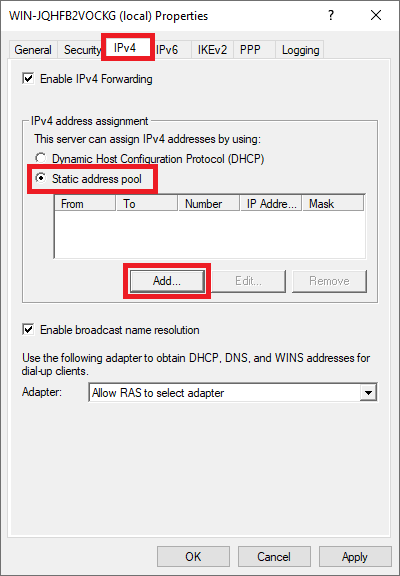
Then, click on the ‘IPv4‘ tab and select ‘Static address pool‘ > ‘Add‘.
Step 23
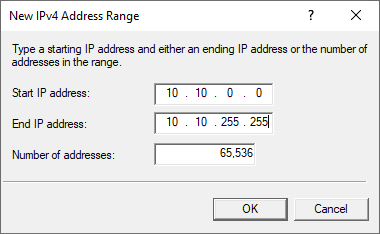
Enter the IP range for your VPN network, for example from 10.10.0.0 to 10.10.255.255 and click ‘OK‘ (a smaller range is of course also possible, such as 10.10.10.0 to 10.10.10.255).
Step 24
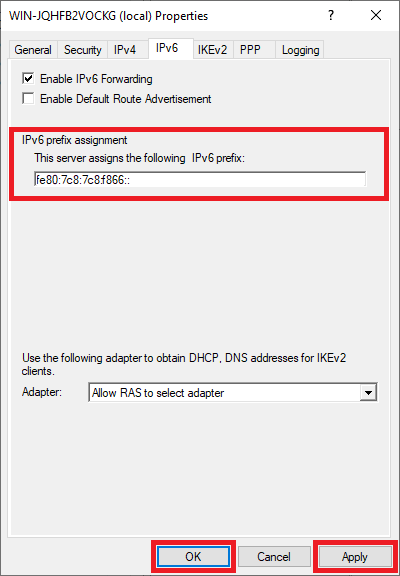
You will now return to the screen from the previous step. Now click on the ‘IPv6‘ tab and enter an IPv6 prefix assignment, for example, fe80: 7c8: 7c8: f866::
Then click ‘Apply‘ and ‘OK‘ to apply the changes.
You will probably now receive a message that RRAS (Routing and Remote Access) must restart. Allow this and after restarting proceed to the next step.
Step 25
Expand ‘IPv4‘ and select ‘NAT‘. Then right-click on an empty spot on the right side of the screen and select ‘New Interface …‘
Step 26
Select ‘Ethernet‘ as the interface for the routing protocol and click ‘OK‘.
Step 27
Double click on ‘Ethernet‘ and check ‘Enable NAT on this interface‘.
Step 28
Click on the ‘Services and Ports‘ tab and check the options below one by one. When you click on them, a pop-up will appear with information about the service. Adjust the ‘Private Address‘ value to 127.0.0.1 for:
- IP Security (IKE)
- IP Security (IKE NAT traversal)
- Remote Desktop
- Secure Web Server (HTTPS)
- VPN Gateway (L2TP / IPsec — running on this server)
- VPN Gateway (PPTP)
- Web Server (HTTP)
Do you use a custom port for Remote Desktop? Click on ‘Add‘ and add a TCP line for the correct port and also use 127.0.0.1 as a Private address.
Finally, click on ‘Apply‘ and ‘OK‘.
Step 29
You should now be prompted to restart RRAS. If not, right-click on your VPN server > ‘all tasks‘ > ‘restart‘ in the ‘Routing and Remote Access console‘ to process the changes.
Your VPN server is now ready to accept VPN connections. Great! but what next? In the following sections, we explain how to authorize users, connect to your VPN server and what you can use it for.
Step 1
Before a user can connect to your VPN server, that user must be authorized for Remote Access.
Not using Active Directory? Then click on the Windows start button, search for ‘computer‘ and click on ‘Computer Management‘ in the results.
Do you use an Active Directory? Then click on the Windows start button, search for ‘group‘ and click on ‘Group Policy Management‘ in the results.
Step 2
You are free to create a new user for your VPN connection or use an existing one. Click on ‘Local Users and Groups‘ > ‘Users‘.
- Existing user: Click on the name of the user
- New user: Right-click on an empty piece and then ‘New User‘. Enter the name of the new user, optionally disable ‘User must change password at next logon‘, and enter a password.
After creating the new user, close the ‘New User‘ screen and double click on the name of the account.
Step 3
Click on the ‘Dial-in‘ tab, under ‘Network Access Permission‘ check the option ‘Allow access‘ and finally click ‘Apply‘ and ‘OK‘ to confirm your changes.
That’s it! You can now connect to your VPN server. We explain how this works in the next section.
Connect to your VPN network
- This tutorial assumes a Windows computer/laptop. For MacOS, you can use this guide from Apple. To connect to your VPN server, enter the IP address of your VPS and as VPN type ‘SSTP‘.
- You go through the steps once per computer. You only need the last step to connect to your VPN server from now on.
Step 1
Now that your VPN server is ready and your user is authorized, it’s time to connect to your VPN server. First, you need to add the VPN connection to your (client) computer/laptop once.
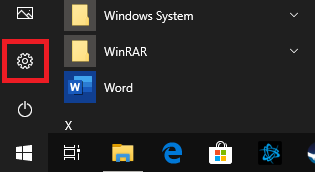
Click the Windows Start button and the Settings icon.
Step 2
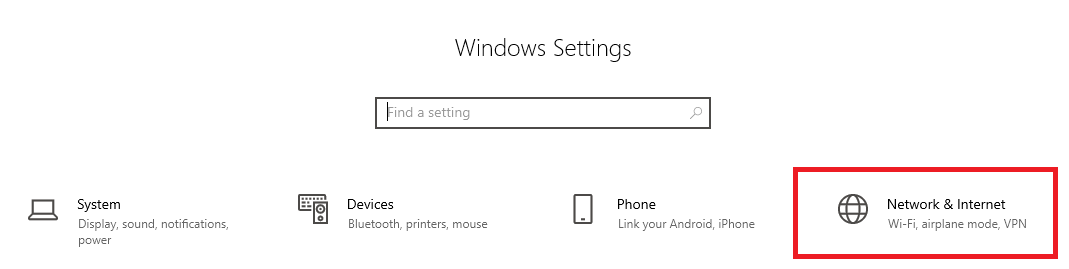
Then click on ‘Network & Internet‘.
Step 3
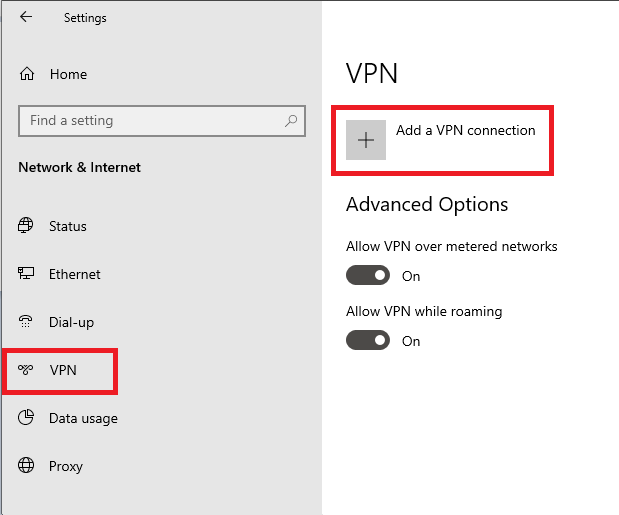
Click on ‘VPN‘ on the left and then on ‘Add a VPN connection‘.
Step 4
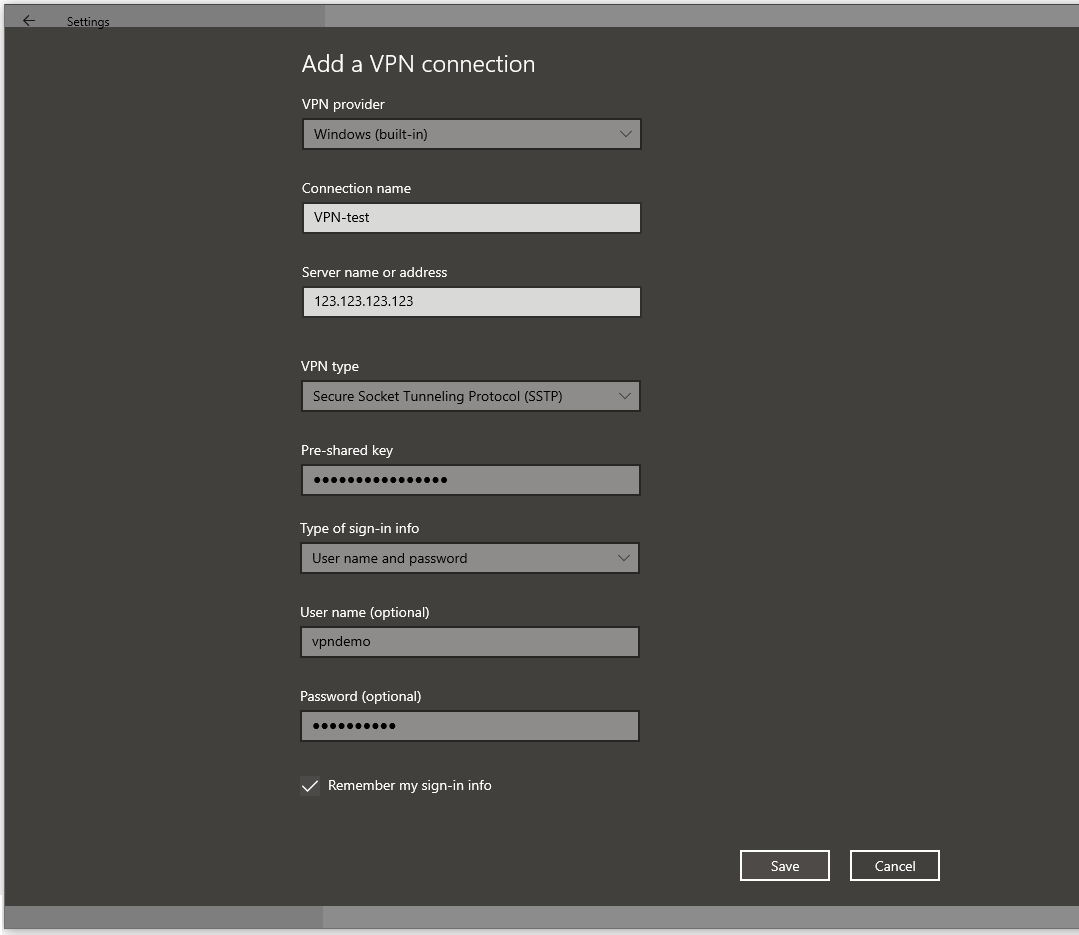
Enter the details on the ‘Add a VPN connection‘ screen that appears. Mind the following:
- Select ‘Windows (built-in)‘ as the VPN provider
- As ‘Server name or address‘, use the IPv4 address of your server, or a domain name that refers to your VPS.
- Choose as VPN type: ‘Secure Socket Tunneling Protocol (SSTP)‘.
Step 5
All your internet traffic is standard over the VPN and uses the default gateway of the VPN server. This means that if you navigate on a client computer in a browser, you are using the connection of your VPS.
We assume in this tutorial that for your regular internet traffic you would like to use your own connection (for example in connection with speed and the data traffic limit of your VPS). You can achieve this by setting your own connection as the default gateway for your VPN as follows:
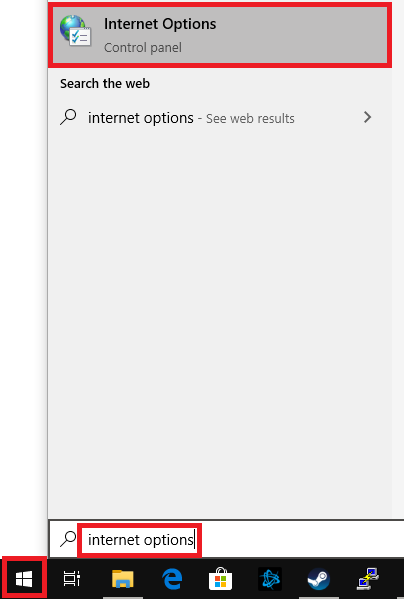
Click on the Windows Start button, type ‘Internet Options‘ and click on the top result.
Step 6
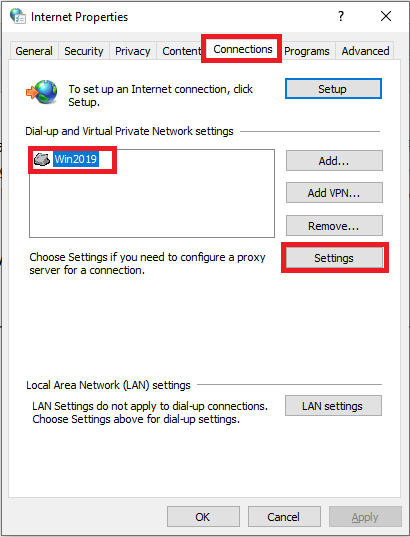
Go to the ‘Connections‘ tab, select your VPN connection and click ‘Settings‘.
Step 7
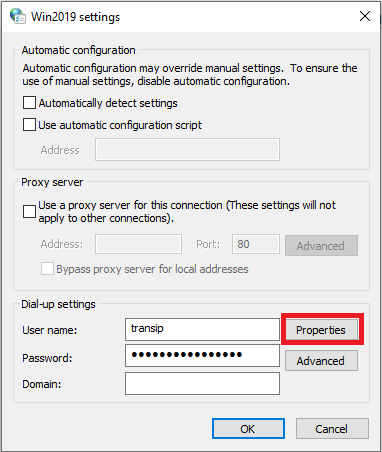
In the window that appears, click on ‘Properties‘.
Step 8
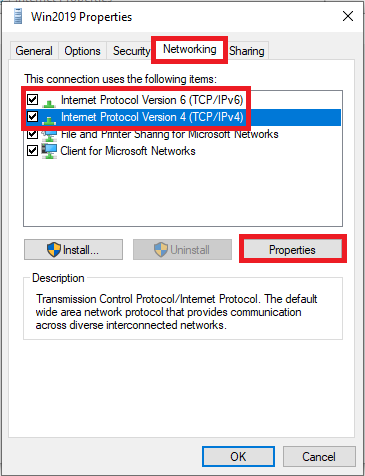
Go to the ‘Networking‘ tab and select ‘Internet Protocol Version 4 (TCP / IPv4)‘ followed by ‘Properties‘.
Step 9
Click on ‘Advanced‘.
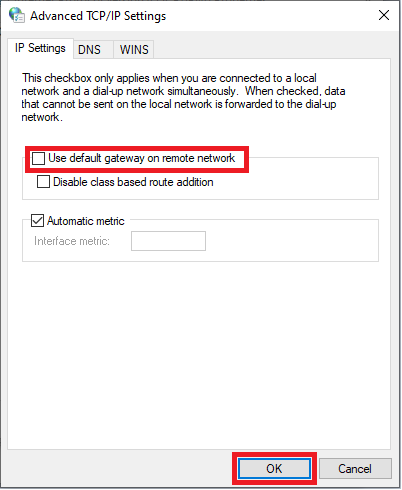
Step 10
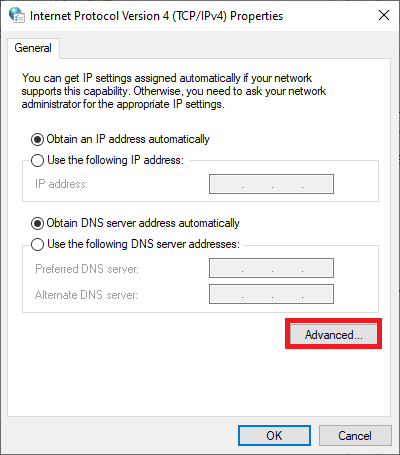
Uncheck ‘Use default gateway on remote network‘ and click ‘OK‘.
You will now return to the window from step 9. Click on ‘OK‘ there as well and repeat steps 8 to 10, but then for ‘Internet Protocol Version 6 (TCP / IPv6)‘.
Then click ‘OK‘ at each screen where you return until you return to the ‘Internet Properties‘ screen from step 6 and click ‘Apply‘ and ‘OK‘ there.
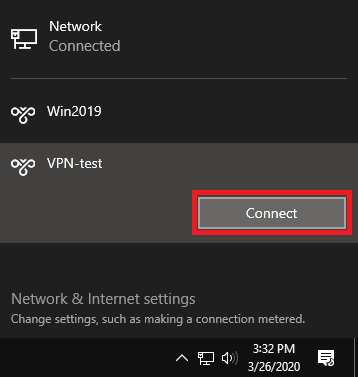
Step 11
Finally, click on the network icon at the bottom right of your screen and click on the name of your VPN connection, followed by ‘Connect‘. From now on, this is the only step you need to go through to reconnect to your VPN server.
Use Cases
Now that your VPN connection is working, you may be wondering what you can do with it. A VPN connection is powerful in combination with a firewall. You can set a scope for a rule in most firewall software, for example in Windows Defender Firewall with Advanced Security, see for example our tutorial on changing the Remote Desktop port.
By only allowing the range or specific addresses of your VPN connection as Remote IP address in the scope of your firewall rule, you limit access to the associated service to those IP addresses. Some examples of applications are:
- Restrict access to the Remote Desktop port to the IP range of your VPN network (10.10.0.0/24 for example).
- Restrict access to a website that you host on a server in your VPN network. This is useful, for example, for an internal administration system that can be reached via a web interface/website. You achieve this by limiting access to ports 80 and 443 on the server hosting your website to the IP range of your VPN network.
- Restrict access to an SMB server by restricting access to port 445 on the SMB server to the IP range of your VPN network.
That brings us to the end of this tutorial for setting up a VPN server in Windows Server 2019.
If you have any questions regarding this article, please do not hesitate to contact our support department. You can reach them via the button ‘Contact us‘ at the bottom of this page.
If you want to discuss this article with other users, please leave a message under ‘Comments‘.
In this article, we will learn the steps on How to Setup L2TP/IPsec VPN with a Pre-Shared key on Windows Server 2019.
What is a VPN?
A Virtual Private Network (VPN) is a secure network tunnel that allows you to connect to your private network from internet locations. So, you can access and use your internal resources based on assign permission.
Layer 2 Tunneling Protocol (L2TP):
L2TP is the industry standard when setting up secure VPN tunnels. L2TP supports either computer certificates or a Pre-shared key as the authentication method for IPsec. L2TP/IPsec VPN connections provide data confidentiality, data integrity, and data authentication.
Understanding the SSTP Test Lab:
- WS2K19-DC01: Domain Controller and DNS.
- WS2K19-VPN01: Member Server.
- WS10-CLI01: Windows 10 Client Machine.
Step:1 Install Remote Access Server role on Windows Server 2019:
1. The first step is the installation of the Remote Access Server role. Open Server Manager Console and start role and feature installation wizard. Select the Remote Access Server role.
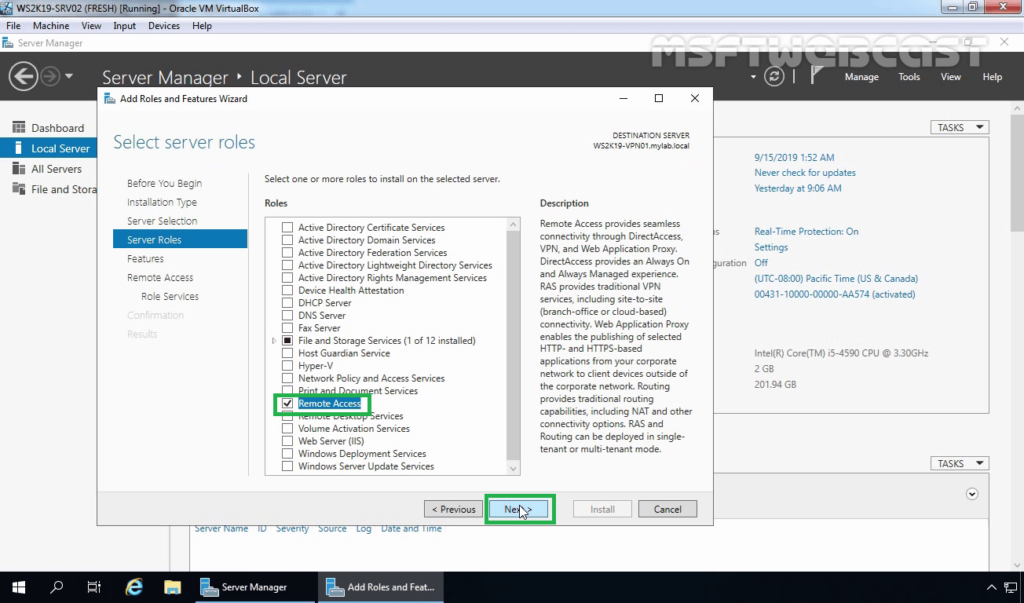
2. On select role services, select DirectAccess and VPN (RAS) role service. Click Next and finish the installation.
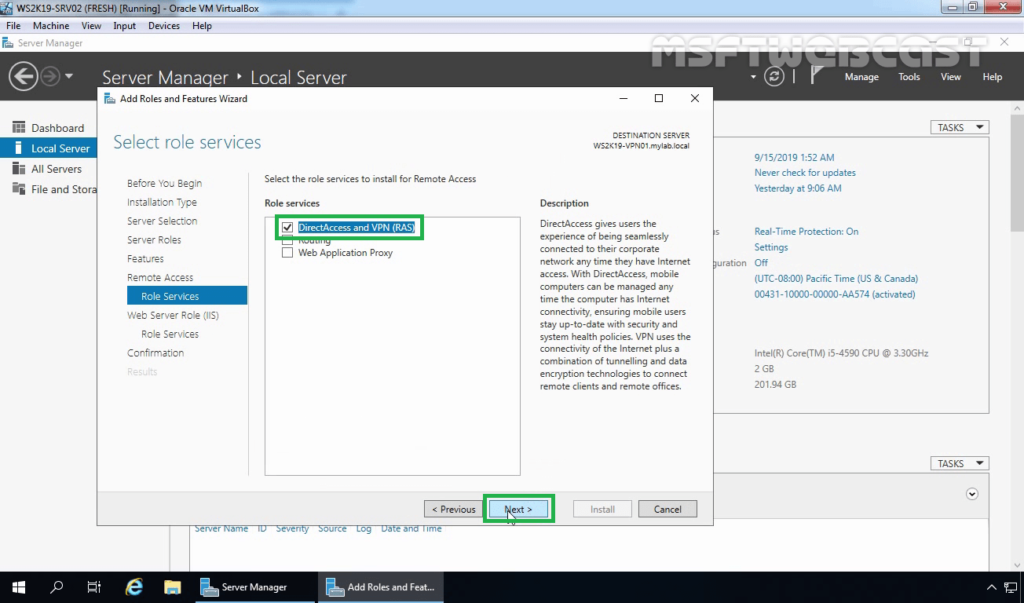
3. When the installation finished, click on close.
Step:2 Configure L2TP/IPsec VPN on Windows Server 2019:
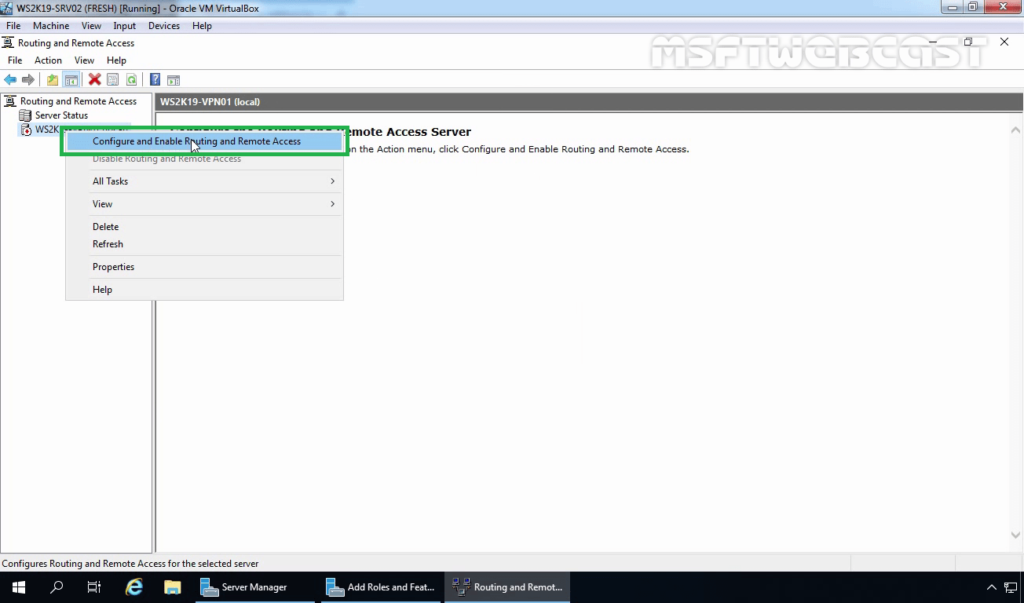
4. On Member Server, Open Server Manager. Click on Tools and select Routing and Remote Access Console.
5. Right-click on the Server name and select Configure and Enable Routing and Remote Access.
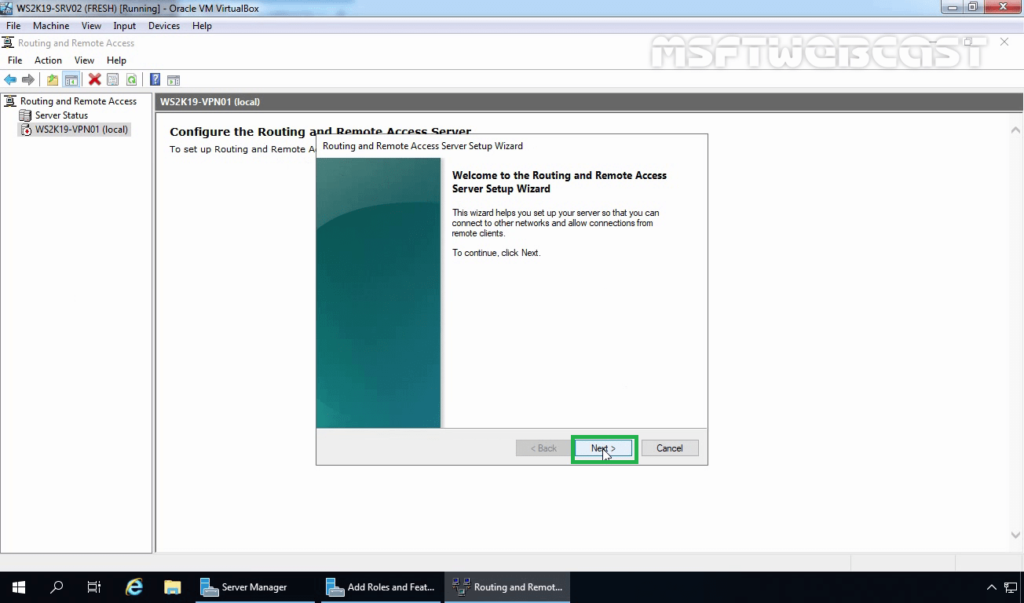
6. On Welcome screen, click Next.
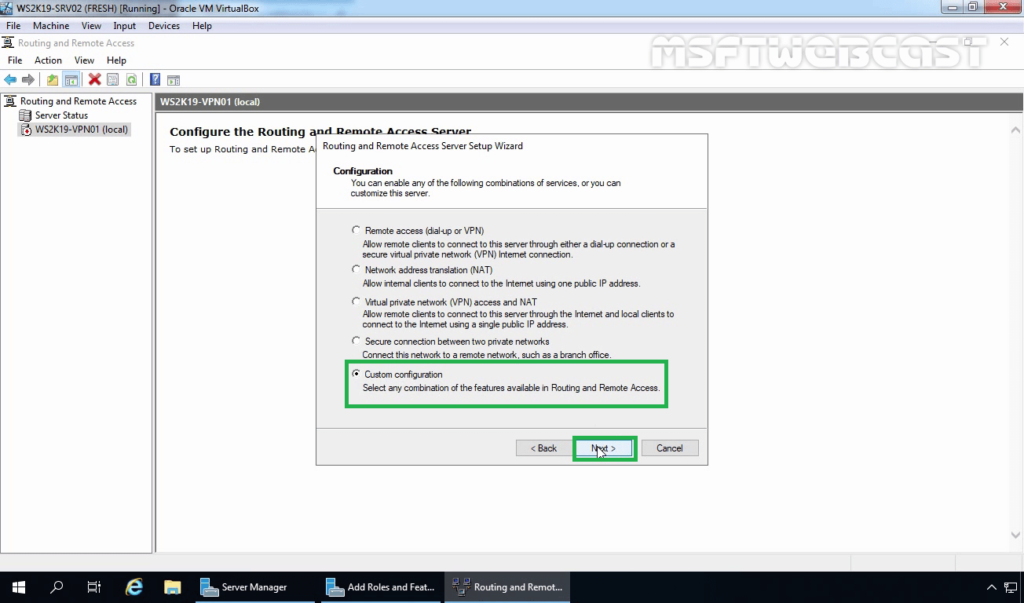
7. On the Configuration page, select the Custom configuration radio button. Click Next.
8. On select the service page, select VPN Access. Click Next.
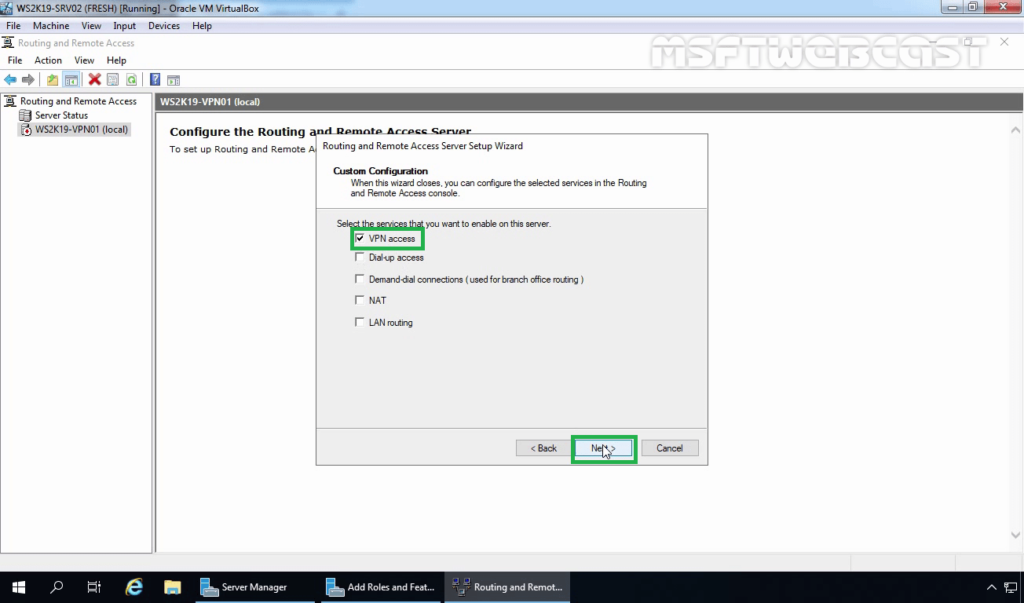
9. After clicking on the Finish, it will ask you to start the service. Click on Start service.
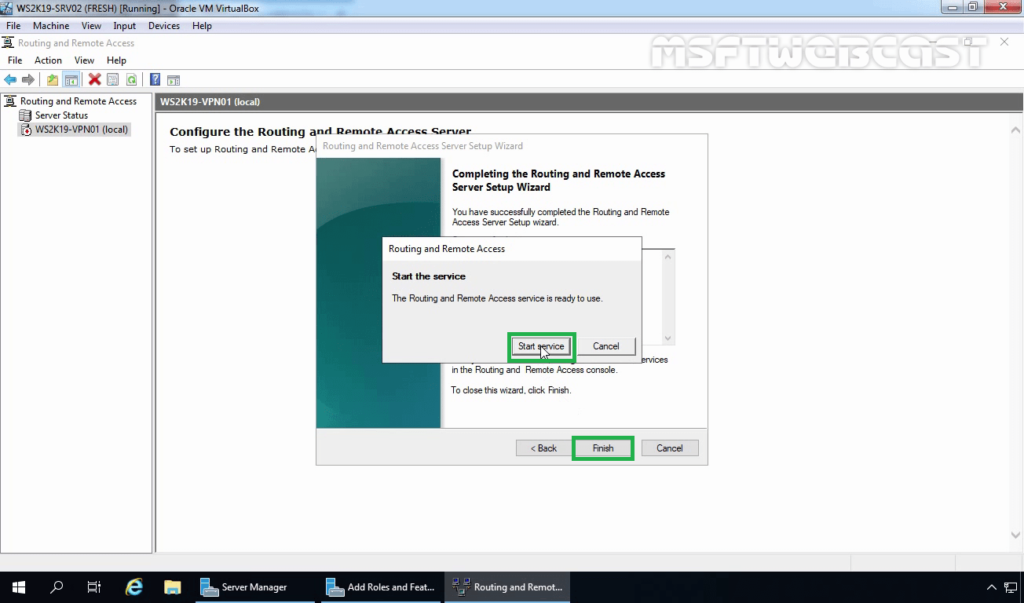
10. Now you will see a green up arrow beside your server name.
Step:3 Configure Pre-Shared Key for IPsec Authentication.
To configure the Pre-shared Key for L2TP/IPsec VPN, we need to set up specific settings in the VPN server’s properties section.
11. Right-click on the server name and click on Properties.
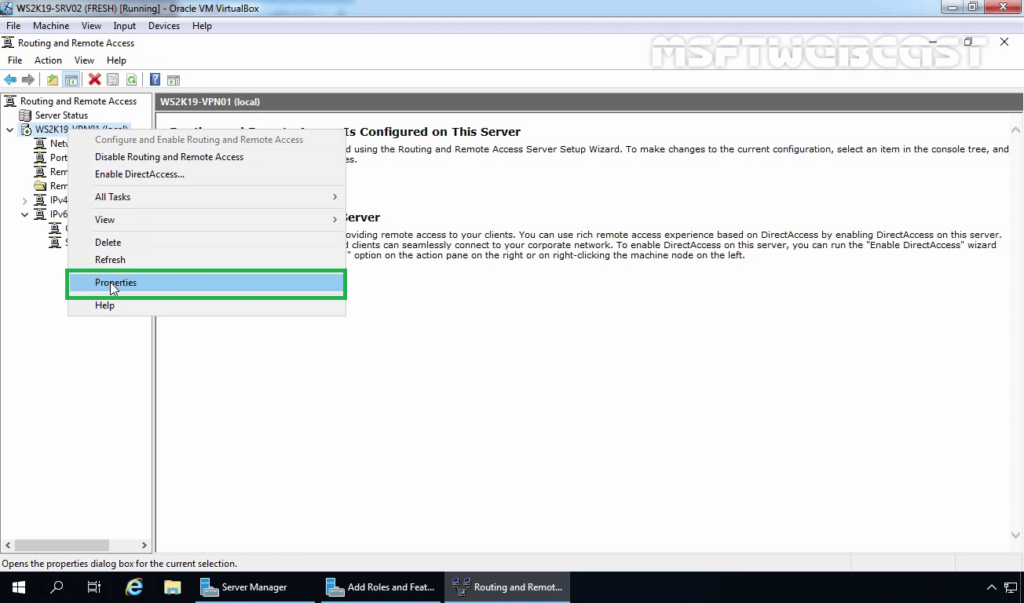
12. On the Security tab, select the checkbox Allow Custom IPsec Policy for L2TP/IKEv2 Connection. Specify a strong Pre-Shared Key for L2TP/IPsec VPN connection.
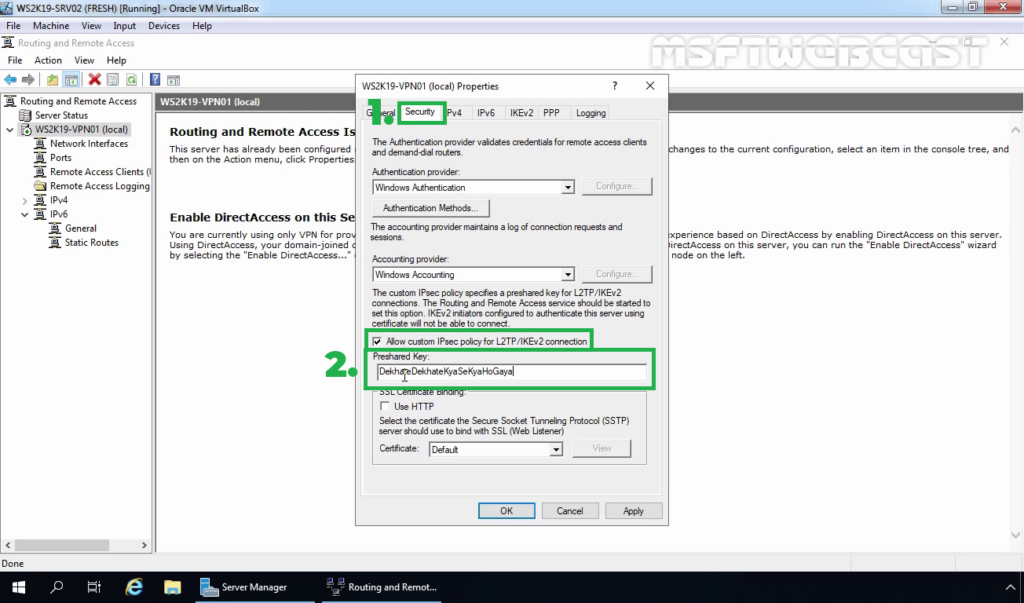
13. Click on IPv4 Tab. Select the Static Address Pool radio button. Click on Add button.
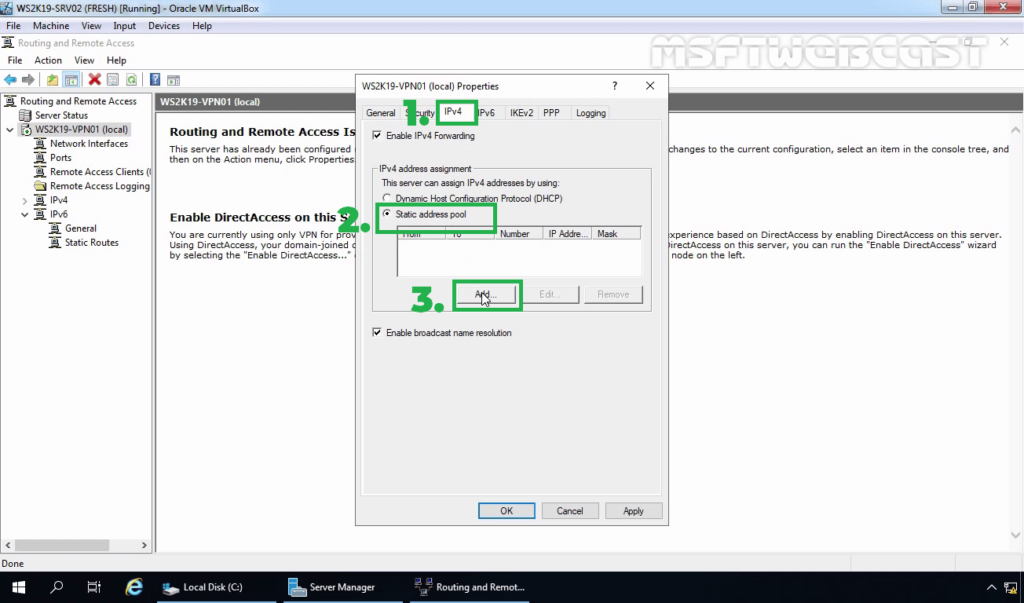
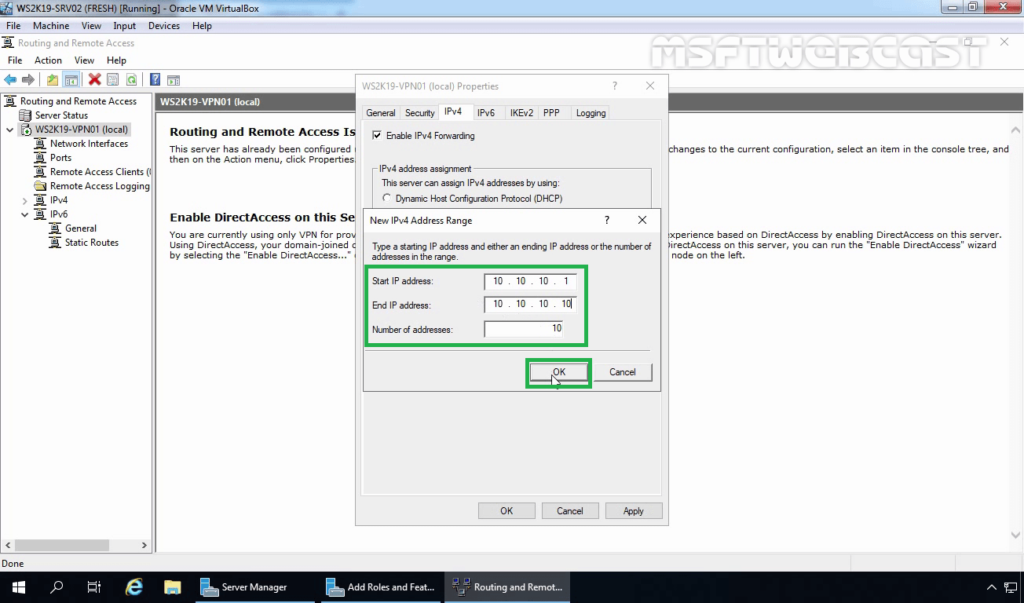
14. Specify the IP address range. Click on OK.
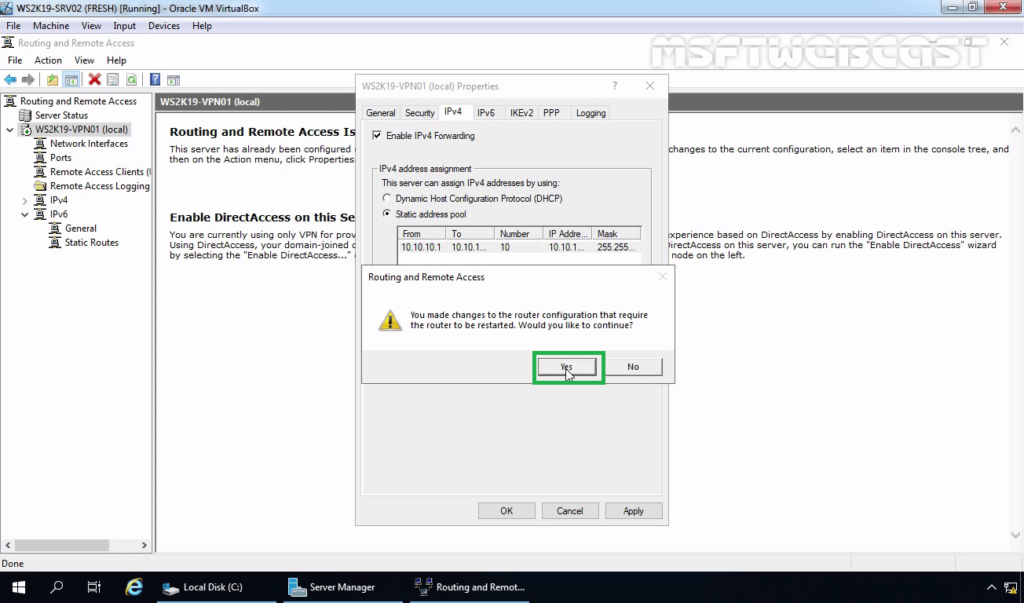
15. Click on Apply to save the changes to the VPN server. It will ask to restart the Routing and Remote Access service. Click on yes to do so.
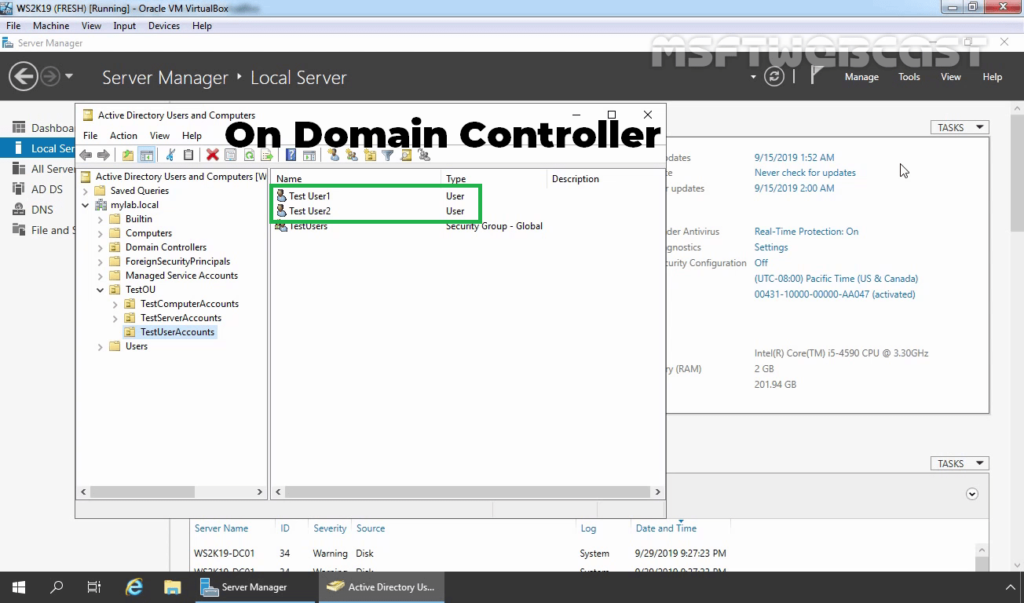
Step:4 Create AD User and allow dial-in access:
16. On Domain Controller, Open Active Directory Users and Computers snap-ins. Create AD users name Test User1 and Test User2.
17. Enable dial-in access for selected VPN users by opening the user properties and selecting Allow access on the tab Dial-in.
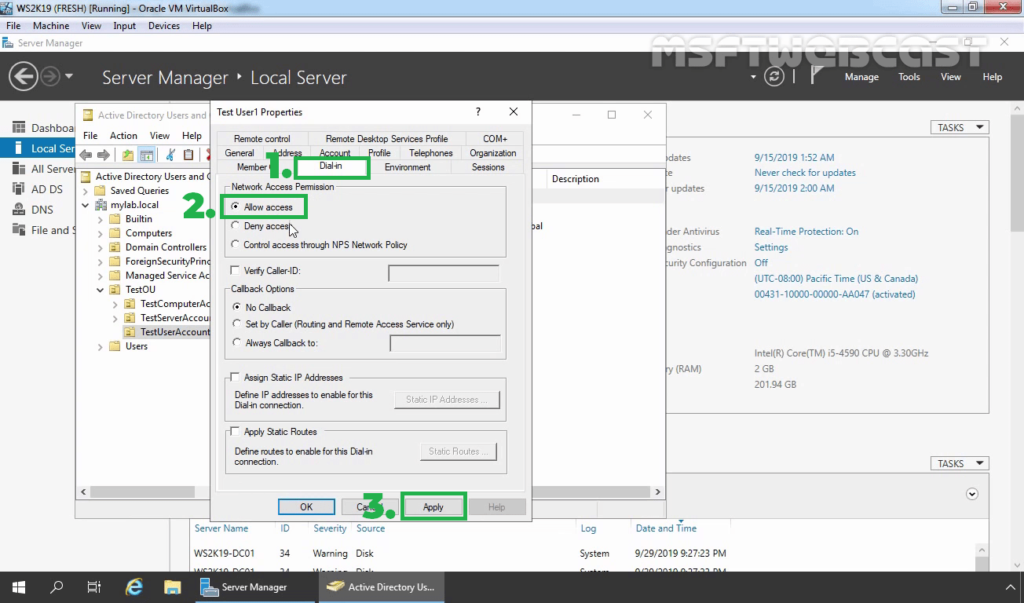
Note: If you want, you can configure Network Policy Server to allow VPN users to connect to the VPN server running on Windows Server 2019.
Step:5 Setup a VPN Connection for L2TP/IPsec VPN:
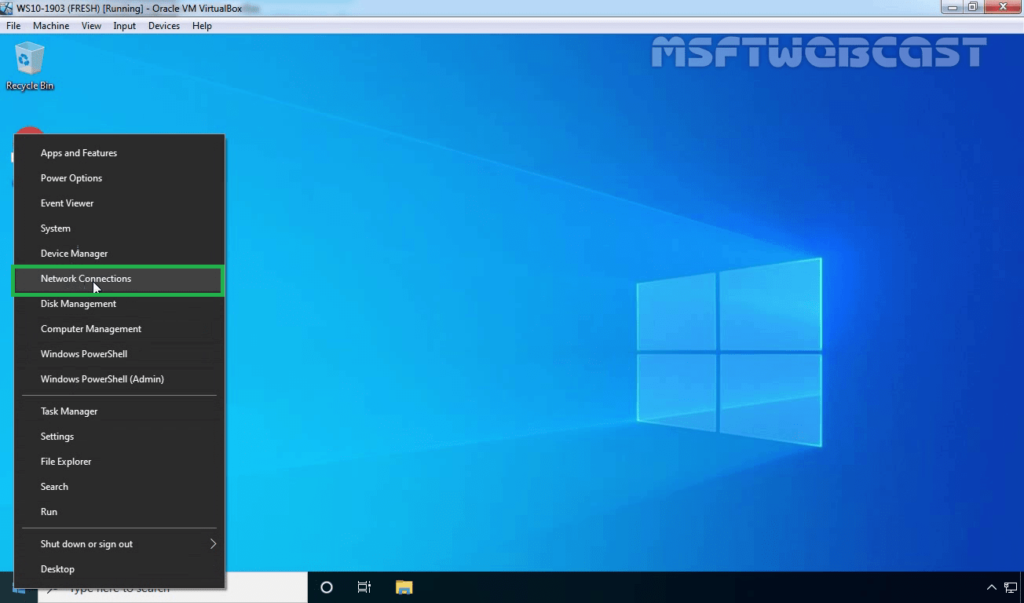
On Windows 10 client machine, we need to create a new VPN connection.
18. Right-click on the Start button and select Network Connections.
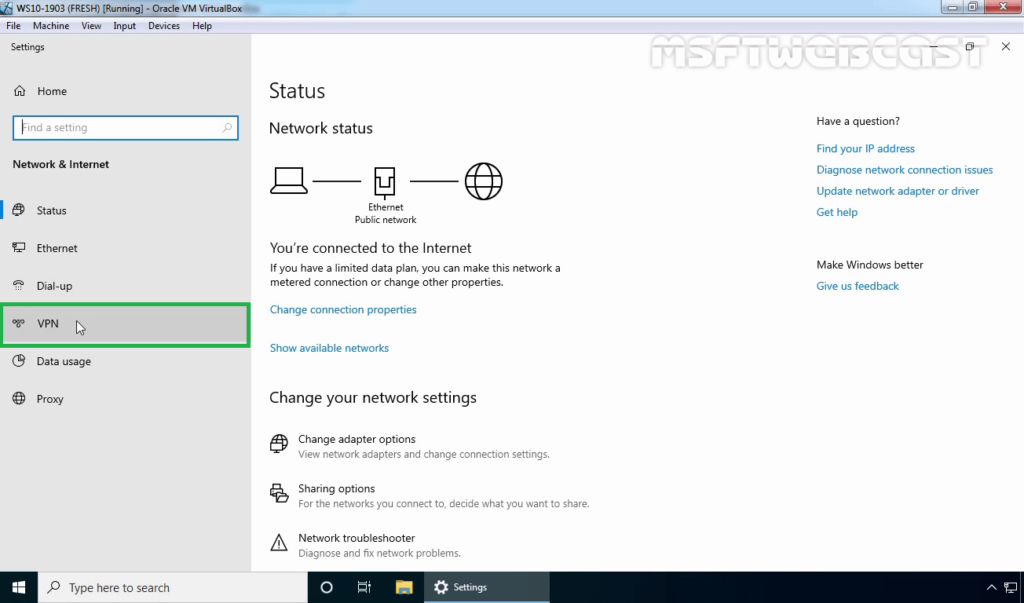
19. On left-pane, click on VPN.
20. Click on add a new VPN connection.
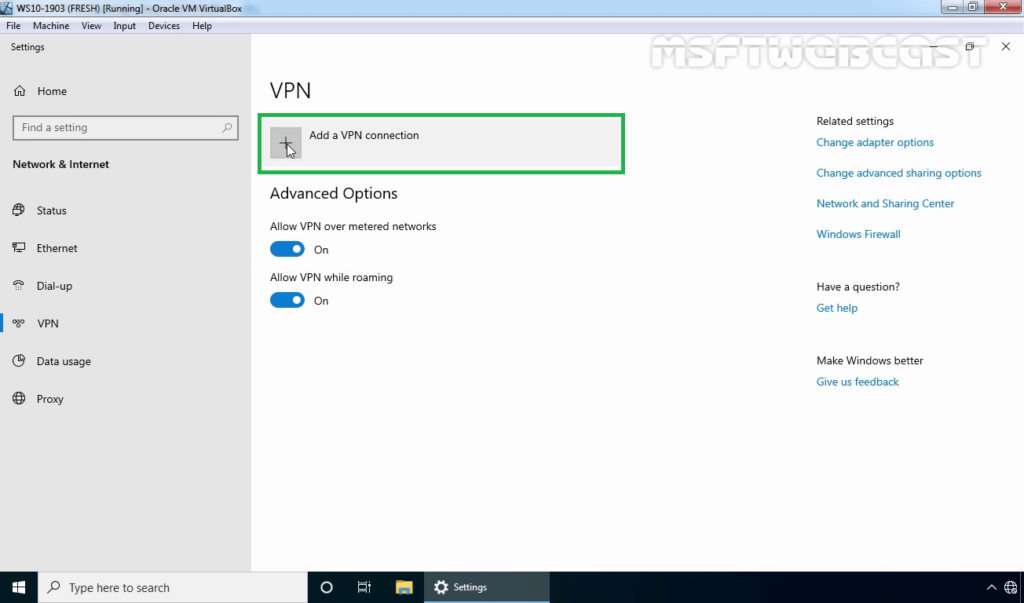
21. Specify the required information for the VPN connection.
- VPN Provider: Windows (Built-in)
- Connection Name: Name of your choice
- Server Name or IP Address: Public IP Address of VPN server
- VPN Type: L2TP/IPsec with Pre-shared key
- Pre-Shared Key: Specify the key which we had assign on VPN Server.
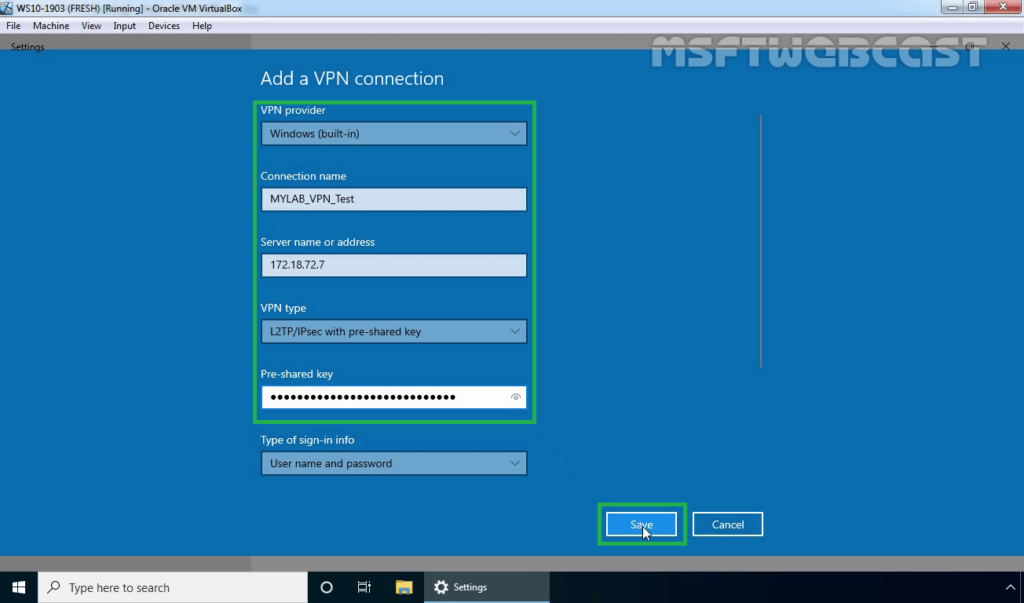
22. Click on Save.
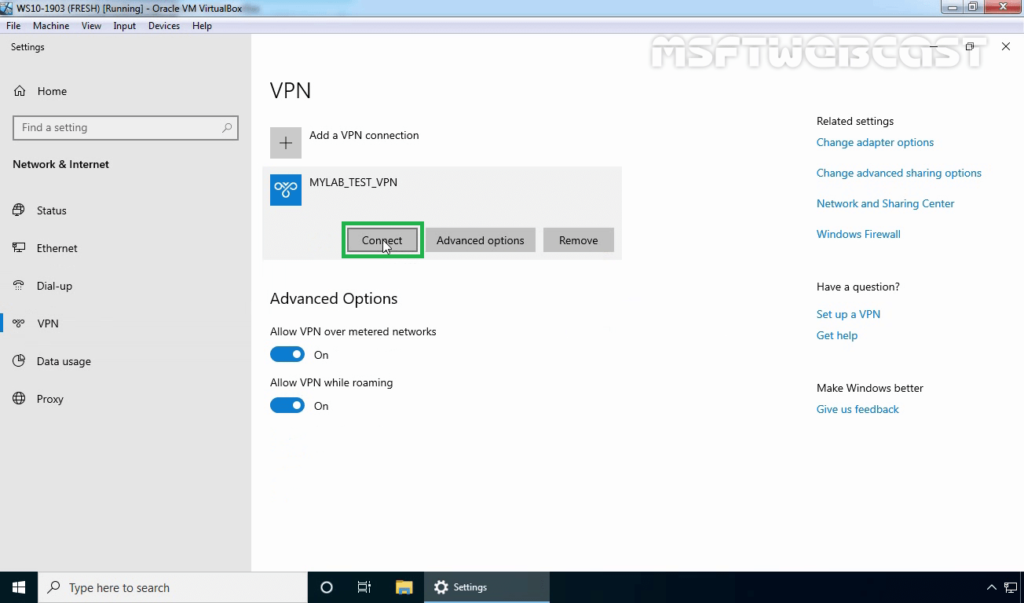
Step:6 Test L2TP/IPsec VPN Connection:
23. Click on VPN connection and select Connect.
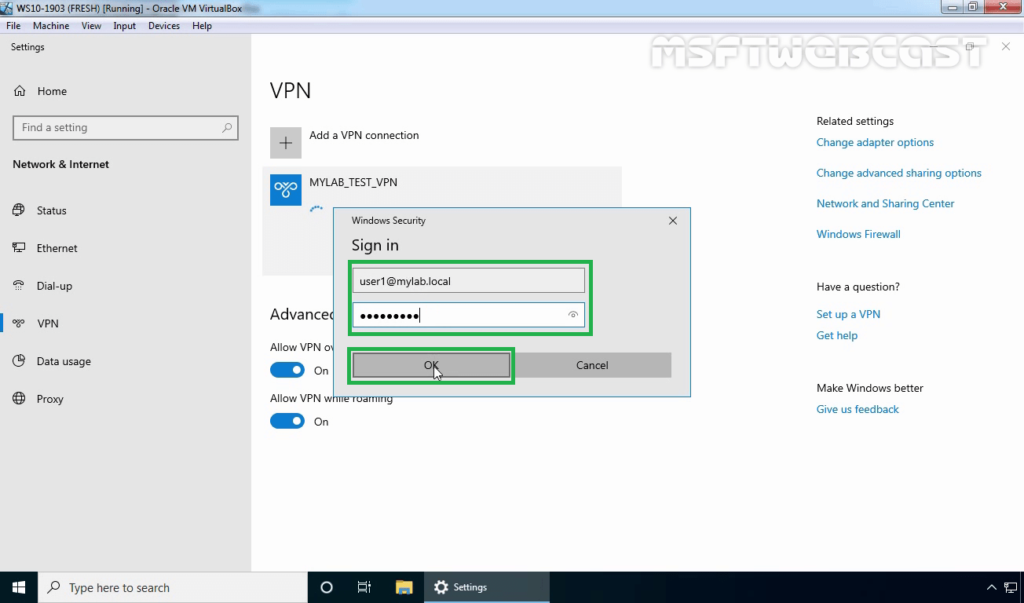
24. Specify a username and password to connect the VPN server. Click OK to connect.
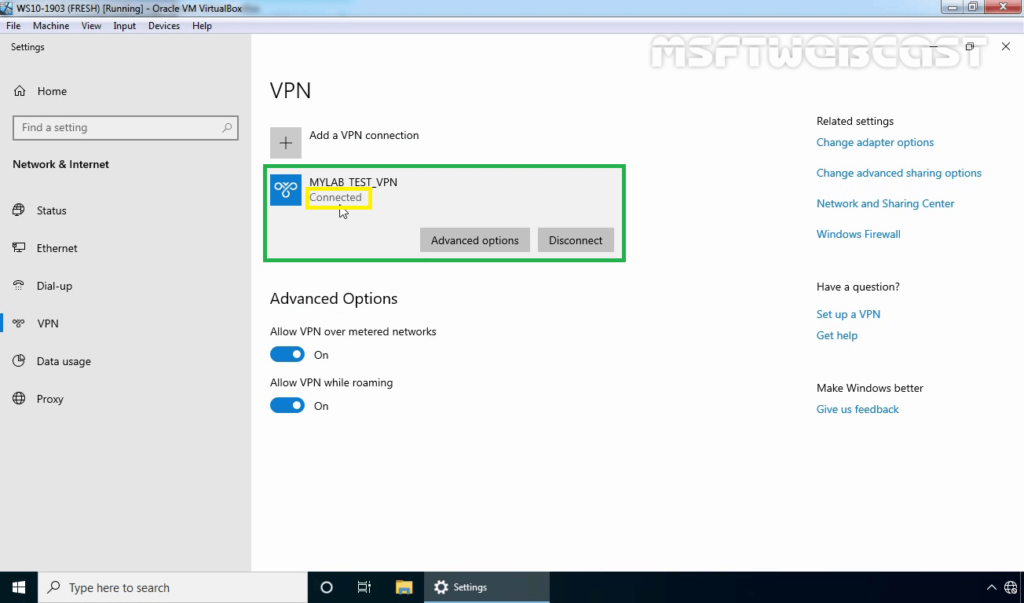
25. Verify the VPN connection is successfully connected with the VPN server using the L2TP/IPsec protocol.
Step:7 Monitor L2TP/IPsec VPN Connection:
On Windows 10 Client Machine:
26. Press Windows Key and R key together. At Run menu type ncpa.cpl and press enter to open Network Connection console.
27. Right-click on VPN connection and click on the Status button.
28. Click on details to see information about VPN connection like Authentication Method, Encryption Mod, etc.
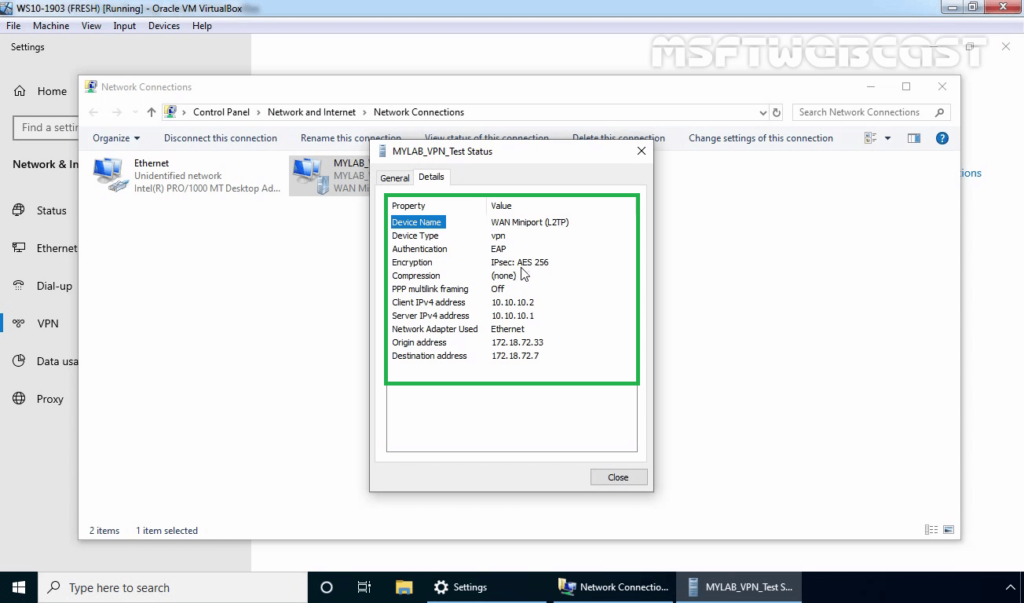
On VPN Server:
29. Press Windows Key and R key together. At Run menu type wf.msc and press enter to open Windows Defender Firewall and Advanced Security console.
30. Expand Monitoring, Expand Security Associations. Expand and Click on Main Mode.
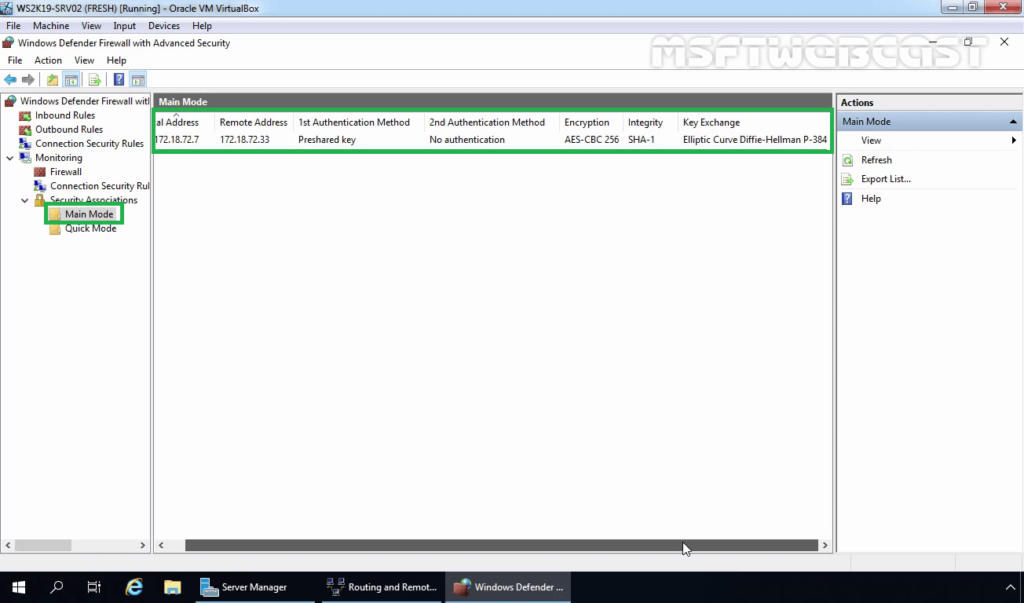
You can verify the authentication method and Encryption Standard for IPsec main mode connection.
- Authentication Method: Pre-Shared Key.
- Encryption Standard: AES-CBC 256 Bit
- Integrity Algorithm: SHA-1
- Key-Exchange Mode: Elliptic Curve Diffie-Hellman P-384.
31. Also, check Quick Mode Tunnel Information.
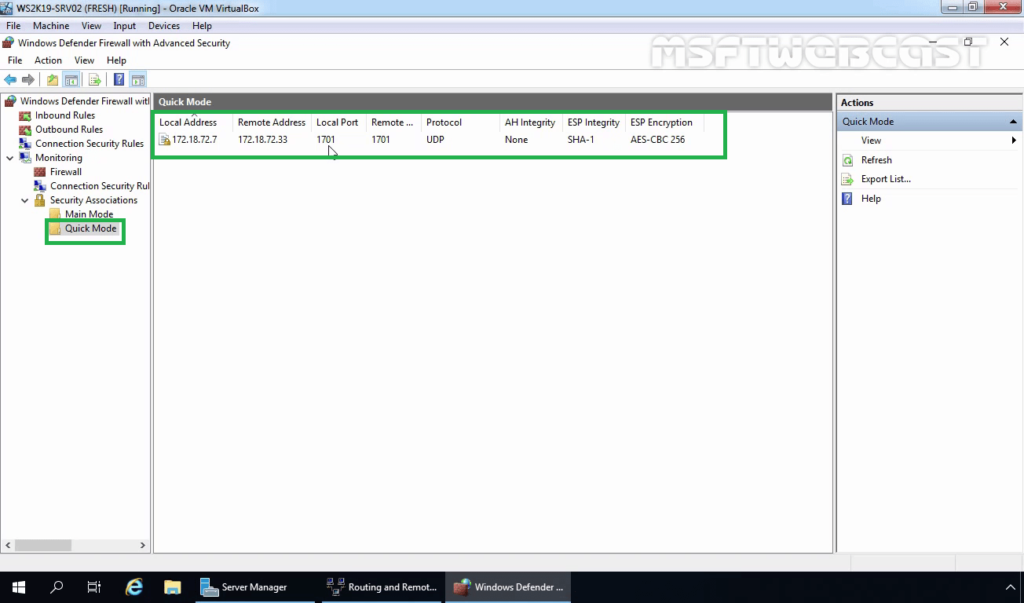
- Local Address: Local IP Address of VPN Server.
- Remote Address: VPN Client IP Address.
- Local Port: UDP 1701
- Remote Port: UDP 1701
- ESP Integrity Mode: SHA-1
- ESP Encryption Mode: AES -CBC 256 Bit
In this post, we have learned the steps to setup L2TP/IPsec VPN with a Pre-shared key on Windows Server 2019 and Windows 10.
Thank you for reading. Have a nice day.
Post Views: 4,895
A Virtual Private Network (VPN) is used to securely create a tunnel for data between your local computer to a remote server. On Windows Server 2019, you can configure a VPN to provide network access to connected clients and allow connected devices to communicate securely.
This guide explains how to set up a fresh Windows Server 2019 as an L2TP over IPSec, or a PPTP VPN, using the routing and remote access feature. Layer 2 Tunneling Protocol (L2TP) with IPSec offers robust encryption for connections to the server. On the other hand, the Point to Point Tunneling Protocol (PPTP) is simple to deploy but not as secure.
To set up the VPN server, we shall use the built-in Routing and Remote access feature, which offers a graphic interface to configure remote networking features such as Dial-up, LAN routing, NAT, and VPN.
Requirements
-
Deploy a Windows Server 2019 Instance on Vultr
-
Remotely connect to the server and log in as an Administrator
Create a New VPN User
For the VPN service to work well, it must authenticate with a valid user account to the server. So, you need to create a new user on the server.
Click Tools under server manager and select Computer Management from the drop-down list to create a new user.
Once the computer management window pops up, expand Local Users and Groups from the left pane and right-click Users to select New User on the sub-menu.
Under the New User dialog box, enter a username, full name, and password for the VPN user, then click create and close the window.
The new user will now be listed on the list of active server users, right-click on the new user and select properties.
Under the user properties window, navigate to the Dial-in tab and click Allow access under Network Access Permission. Click OK for changes to take effect.
Install the Routing and Remote Access Features
Procedure 1: Through Server Manager
From the Windows start menu, open Server Manager, click Manage, then select Add Roles and Features from the drop-down list.
From the open window, click next and select Role-based or feature based installation, then select your server from the pool. Select Remote Access, Remote Access Administration from the list of server roles.
Next, select DirectAccess and VPN (RAS) and Routing from the features list, then click to Install IIS, which is required for remote access to work well.
Procedure 2: Using Windows PowerShell
You can also install Remote Access from Windows Powershell.
From the Windows start menu, open an Administrative Powershell, then install Remote access by pasting the following code to the console.
Install-WindowsFeature RemoteAccess
Install-WindowsFeature DirectAccess-VPN -IncludeManagementTools
Install-WindowsFeature Routing -IncludeManagementTools
Your output should be similar to:
PS C:\Users\Administrator> Install-WindowsFeature RemoteAccess
>> Install-WindowsFeature DirectAccess-VPN -IncludeManagementTools
>> Install-WindowsFeature Routing -IncludeManagementTools
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No Success {Remote Access}
True No Success {RAS Connection Manager Administration Kit...
True No Success {Routing}
Configure Routing and Remote Access
Open Server Manager and click Tools on the top toolbar. From the drop-down list, select Remote Access Management.
In the open Routing and Remote Access window, right click on your server name just below Server status, then select Configure and Enable Routing and Remote Access from the drop-down menu.
Now, select Custom configuration to configure remote access manually.
Select VPN Access and NAT as services you want to enable on your server, click next to finish the configuration, and start the service.
Setup a PPTP VPN
Now that Remote Access is running, you can set up your PPTP VPN. To get started, you must assign connected clients** static IP Addresses to avoid possible connection issues. To do this, right-click on your server under the Routing and Remote Access window and select Properties from the drop-down list.
Click IPV4 in the Open Window, then select Static address pool. Now, click Add to craft a new IP Address range from the open pop-up window. In this guide, we use the range 10.0.0.1 to 10.0.0.50, and the server will automatically calculate the number of available addresses.
Click OK to save your static IP Address configuration. You will be prompted to restart Routing and Remote Access for changes to apply; simply click OK.
Configure NAT and enable PPTP
We need to configure Network Address Translation (NAT) for connected clients to use the Internet. On the left pane of the same routing and remote access window, expand the IPv4 options under your server. Right-click on NAT and select New Interface.
Under the open dialog window, select Public interface and enable NAT on the interface.
Next, navigate to Services and Ports and click VPN Gateway (PPTP) from the drop-down list.
Click Edit to set a Private address for the VPN service, change the current address 0.0.0.0 to 127.0.0.1, and click OK to save.
Finally, click OK to save all changes, then right-click on your server from the left pane and click Restart under the All Tasks sub-menu.
This will restart routing and remote access services making your server ready for incoming VPN connections.
Configure Windows Firewall to accept Incoming PPTP VPN Connections
Click Tools from the Windows server manager and select Windows Defender Firewall with Advanced Security from the drop-down list.
Under the open Windows Defender Firewall with Advanced Security window, select Inbound Rules on the left pane, then click New Rule on the right pane.
In the open new Inbound rule wizard, click Predefined and select Routing and Remote Access from the list.
Under predefined rules, choose Routing and Remote Access (PPTP-In), click next to allow the connection, then finish for the new Firewall rule to be applied and test your new PPTP VPN server.
Test your PPTP VPN
Using your personal computer (PC) or Smartphone, go to Networks, Add a new VPN and select PPTP as the VPN type. Then, enter the VPN username and password created earlier to connect.
In this guide, we cover and test the PPTP VPN on a Windows 10 PC. To get started, click the start menu and search for Control Panel, then, click Network and Internet.
Under Network and Internet, open the Network and Sharing Center and click Set up a new connection or network.
Under the open window, select Connect to a workplace and click Use my Internet connection (VPN).
Then, enter your server’s public IP Address (Check your Vultr server dashboard), assign the connection a name, and click create.
Now, on the left pane, click Change adapter settings, then right click your created VPN interface and select Properties.
Under the pop-up, click Security, then choose Point to Point Tunneling Protocol (PPTP) under Type of VPN.
Finally, under Allow these protocols, select CHAP and MS-CHAP v2, then click OK to apply changes.
Your new VPN is configured successfully. Click the network connection icon on the taskbar, select your VPN on the list and click Connect to enter the VPN username and password created earlier to establish a connection to your new PPTP VPN server.
Setup L2TP with IPSEC
Open server manager, click Tools, and open Remote Access Management, then right-click your server on the left pane to select Properties from the drop-down list.
Under server properties, navigate to the Security tab, and click Allow custom IPSec policy for L2TP/IKEv2 connection to enter your new pre-shared key.
In this guide, we use 12345678, choose something stronger, then navigate to IPV4 to set a static address pool and click OK to apply changes.
Keep note of the pre-shared key (PSK) since it will be required for every user establishing a connection to the VPN server.
From the left pane, expand the IPV4 sub-menu and right-click on NAT, then select New Interface. If you set PPTP earlier, click NAT and edit the existing interface you already created.
Navigate to the Services and Ports tab and select VPN Gateway [L2TP/IPSec], then click edit to change the private address from 0.0.0.0 to 127.0.0.1. Click OK to save changes and restart remote access from the left pane under All Tasks.
This will restart Routing and Remote Access, then save the applied L2TP configurations.
Allow L2TP Connections through Windows Firewall
Open Windows Defender with Firewall, select inbound rules and add a new rule. Select Predefined and from the list, choose Routing and remote access.
Under Predefined rules, select Routing and Remote Access [L2TP-In] and click next.
Finally, allow the connection and click Finish to apply the new Firewall rule.
Connect and Test Your L2TP VPN server
In this guide, we test the new L2TP with IPSec VPN on a mac. To get started, open System Preferencesand click Network.
Under the Network Preferences window, click the + sign and select VPN under the Interface dialog box. Then, choose L2TP with IPSec as the VPN Type and assign your connection a name.
Click create, then enter your public server IP Address (server address) and username (Account name). Next, click Authentication Settings to enter your account password and Pre-shared key (Shared secret) created earlier.
Next, click Advanced and select Send all Traffic over VPN Connection, then click Apply, and finally click Connect to establish a connection with your new L2TP VPN server.
Conclusion
You have set up a VPN on your Windows server 2019 instance; you can choose to create both PPTP and L2TP VPNs with different users connecting through your server without any limitations.
For every connected device, they will be able to access the Internet through your server and interact with other connected computers.
This blog post is a step by step guide how to install and configure VPN on Windows Server 2019. The blog post shows you how you can easily set up a VPN server for a small environment, branch office, or for a hosted server scenario. This VPN (Virtual Private Network) server allows you to connect from remote clients or firewalls to the Windows Server.
I already did a similar post for other versions of Windows
- How to Install VPN on Windows Server 2008 R2
- How to Install VPN on Windows Server 2012
- How to Install VPN on Windows Server 2012 R2
- How to Install VPN on Windows Server 2016
To install VPN access to a Windows Server 2019, simply follow this step by step guide:
Install Remote Access Role
First, install the “Remote Access” via Server Manager or PowerShell.
Open Server Manager and select Add Roles and Features
Select the Remote Access Role and click next through the wizard.
On the step Role Services, select the DirectAccess and VPN (RAS)
On the final step, select install to install the Remote Access role.
This might requires a reboot of the server.
Install and Configure VPN on Windows Server 2019
After you have successfully installed, now you can start the wizard to install and configure the VPN server in Windows Server 2019.
After the features are installed, which can take a while to finish, you see the link for the Getting Started Wizard. Click on “Open the Getting Started Wizard“.
This opens a new wizard which will help you to configure the server. On the first screen, select “Deploy VPN only“.
This opens the Routing and Remote Access Management Console
Right click on the Server name and click on “Configure and Enable Routing and Remote Access“.
On the new wizard select “Custom configuration“.
Select “VPN Access“.
After you have click finish, you can now start the Routing and Remote Access service.
Configure VPN Access Users and Network
If you have a firewall between the internet and your Windows Server you have to open the following Firewall port sand forward them to your Windows Server:
For PPTP: 1723 TCP and Protocol 47 GRE (also known as PPTP Pass-through)
For L2TP over IPSEC: 1701 TCP and 500 UDP
For SSTP: 443 TCP
After the installation Users have to be enabled for Remote Access to connect to your VPN Server. On a standalone server this can be done in the Computer Management MMC, in a domain environment this can be done in the user properties of an Active Directory user.
If you don’t have a DHCP Server in your environment, you have to add a static IP address pool. This is often needed if you have a single server hosted at a service provider. In the properties of your VPN server, you can click on the IPv4 tab and enable and configure the “Static address pool”.
You now have to add an IP address from the same subnet as your static address pool to the network interface of your server so that users can access the server.
I hope this helps you to set up a VPN server in a small environment, lab, or hosted server. You can find more information about Windows Server in the Microsoft Docs.
Tags: DirectAccess, Install VPN Server on Windows Server, Microsoft, Remote Access, Virutal Private Network, VPN, VPN Server, Windows Server, Windows Server 2019, Windows Server 2019 VPN, Windows VPN Last modified: July 7, 2019
About the Author / Thomas Maurer
Thomas works as a Senior Cloud Advocate at Microsoft. He engages with the community and customers around the world to share his knowledge and collect feedback to improve the Azure cloud platform. Prior joining the Azure engineering team, Thomas was a Lead Architect and Microsoft MVP, to help architect, implement and promote Microsoft cloud technology.
If you want to know more about Thomas, check out his blog: www.thomasmaurer.ch and Twitter: www.twitter.com/thomasmaurer