Ранее мы уже рассказывали про Hashcat в статье «Использовании Hashcat на Kali Linux». Сегодня покажу, как установить и использовать Hashcat на Windows. Будем взламывать хеш пароля в MD5, MD4, SHA1, SHA3 и коснемся других способов взлома хешей.
Еще по теме: Создание флешки Kali Linux (быстрый способ)
Hashcat — самый быстрый инструментом для взлома паролей. Он кроссплатформенный и доступен для Windows, macOS и Linux. Взломщик паролей поддерживает большое количество алгоритмов хеширования, включая LM Hash, NT hash, MD4, MD5, SHA-1 и 2 и многие другие. На сегодняшний день поддерживает 237 различных типов хешей.
Как пользоваться Hashcat на Windows
Рассмотрим команду использования Hashcat в Windows:
|
.\hashcat —m 0 —a 0 .\crackme.txt .\rockyou.txt |
.\hashcat -m 0 -a 0 .\файл_хешей.txt .\словарь.txt
- -m (тип хеша) — Например, MD5, SHA1 и т. д. В этом примере мы будем использовать
—m 0 для MD5. - -a (тип атаки) — Указывает Hashcat, каким методом взламывать пароль. Например, с использованием словаря слов, или перебора, или знаменитой комбинированной атаки. В этом примере мы будем использовать
—a 0 для атаки по словарю. - [файл_хешей.txt] — Задает расположение файла, содержащего хеш-коды, которые вы собираетесь взломать. В примере я использовал
crackme.txt. - [словарь.txt | маска | каталог] — Задает используемый словарь (список слов), маску или каталог. В этом примере мы будем использовать словарь для брута
rockyou.txt.
Установка и настройка Hashcat в Windows
Зайдите на сайт Хешкэт и скачайте бинарник (версию для Windows).
Запустите командную строку и с помощью команды
cd перейдите в папку с извлеченным из архива Hashcat.
Убедитесь, что находитесь в папке Hashcat введя hashcat.exe.
Создайте новый текстовый документ внутри папки hashcat, где будут хранятся хеши ваших паролей, в моем случае — это файл crackme.txt. Ниже приведен список тестовых хэшей, которые вы можете использовать.
|
6c569aabbf7775ef8fc570e228c16b98 e10adc3949ba59abbe56e057f20f883e 25f9e794323b453885f5181f1b624d0 5f4dcc3b5aa765d61d8327deb882cf9 d8578edf8458ce06fbc5bb76a58c5ca4 fcea920f7412b5da7be0cf42b8c93759 96e79218965eb72c92a549dd5a330112 25d55ad283aa400af464c76d713c07ad e99a18c428cb38d5f260853678922e03 7c6a180b36896a0a8c02787eeafb0e4c 3f230640b78d7e71ac5514e57935eb69 f6a0cb102c62879d397b12b62c092c06 |
Добавьте не менее 5 хешей.
Можете сгенерировать свои собственные хэши каким-нибудь онлайн-сервисом.
Теперь создайте словарь для брута. Hashcat имеет свой словарь example (файл DICT), но лучше использовать словарь Kali Linux rockyou.txt или свой словарь.
Использование Hashcat в Windows
Откройте командную строку и убедитесь, что находитесь в папке Hashcat.
Для справки введите команду:
Большой выбор алгоритмов хеширования:
Для взлома наших хешей используем атаку по словарю
—a 0 на хеш MD5
—m 0.
Как можно видеть на скрине ниже, Хешкэт взломал несколько хешей.
Hashcat добавляет все взломанные пароли в файл potfile и сохраняет в своей папке.
На этом все. Теперь вы знаете как пользоваться мощным инструментом Хешкэт, для взлома паролей.
ПОЛЕЗНЫЕ ССЫЛКИ:
- Лучшие словари для Hashcat
- Актуальные методы взлома паролей
- Брут секретного ключа JWT с помощью Hashcat
Step 1 – Install .NET 4 framework – Stand alone installer
https://www.microsoft.com/en-sg/download/details.aspx?id=17718
http://filehippo.com/download_dotnet_framework_4/
Step 2 – Download OCL Hashcat 1.36 for Windows
http://hashcat.net/oclhashcat/
Step 3 – Download Hashcat Gui for Windows
http://hashkiller.co.uk/hashcat-gui.aspx
***
Step 4 – Watch the video regarding rulesets and wordlists
Hashcat options.
This is background information so that you can adapt your attack for windows hashes or unix hashes etc.
hashcat –help
-m = hash type (the hash varies by operating system)
-a = Attack Mode (we’ll use both Straight and Combination Attack)
-r = rules file (look for xyz.rule)
****
Questions to ask
1. What hash algorithm is being used? MD5 or NTLM?
2. What wordlists do you want to use?
The rockyou database is one of the best, with 14 million unique passwords.
3. What rulesets do you want to use?
Straight through or Combinator?
Step 5 – Collect Password Dictionaries
https://github.com/danielmiessler/SecLists/tree/master/Passwords
The 2 major cracking dictionaries are Rockyou, and CrackStation.
Rockyou contains 14 million unique passwords.
CrackStation. For MD5 and SHA1 hashes, there is a 190GB, 15-billion-entry lookup table, and for other hashes, they offer a 19GB 1.5-billion-entry lookup table.
Download CrackStation by Torrent:
https://crackstation.net/buy-crackstation-wordlist-password-cracking-dictionary.htm
Some hashes will fail to be cracked, this is due to several reasons, it may not be a md5 hash, it may not be in your password list etc.
Hashes are case sensitive, so Password1 is not the same as password1.
oclHashcat-Plus uses your GPU rather than your CPU to crack passwords. Graphics cards are MUCH faster as an attack tool, than a CPU… MANY times faster.
*****
Reference
https://www.amazon.co.uk/s/ref=nb_sb_noss_2?url=search-alias%3Daps&field-keywords=hashcat
KALI – How to crack passwords using Hashcat – The Visual Guide
KALI – How to crack passwords using Hashcat – The Visual Guide
BRUTE FORCE HACKING – Brute force Calculator – A Visual Guide
https://uwnthesis.wordpress.com/2014/04/18/bruteforce-hacking-bruteforce-calculator-a-visual-guide/
How to write a password that takes over 35 quadrillion years to crack (but is easy to remember)
https://uwnthesis.wordpress.com/2016/03/27/how-to-write-a-password-that-takes-over-35-quadrillion-years-to-crack-but-is-easy-to-remember/
This Is A Quick Tutorial On How To Use The Hashcat GUI By Blandyuk Done By Giveen.
Hashcat Is The World’s Fastest And Most Advanced Password Recovery Utility, Supporting Five Unique Modes Of Attack For Over 200 Highly-Optimized Hashing Algorithms. Hashcat Currently Supports Cpus, Gpus, And Other Hardware Accelerators On Linux, Windows, And Macos, And Has Facilities To Help Enable Distributed Password Cracking. Examples of Hashcat Supported Hashing Algorithms Are Microsoft LM Hashes, MD4, MD5, SHA-Family, UNIX Crypt Formats, Mysql, and Cisco PIX.
GPU Driver requirements:
- AMD GPUs on Linux require «Radeon Open Compute (ROCm)» Software Platform (1.6.180 or later)
- AMD GPUs on Windows require «AMD Radeon Software Crimson Edition» (15.12 or later)
- Intel CPUs require «OpenCL Runtime for Intel Core and Intel Xeon Processors» (16.1.1 or later)
- Intel GPUs on Linux require «OpenCL 2.0 GPU Driver Package for Linux» (2.0 or later)
- Intel GPUs on Windows require «OpenCL Driver for Intel Iris and Intel HD Graphics»
- NVIDIA GPUs require «NVIDIA Driver» (367.x or later)
Check Out All Features Here :- https://hashcat.net/hashcat/
Tutorial 1 Provided By Giveen :- https://www.youtube.com/watch?v=Tj-U5hQSy_E
Tutorial 2 Provided By Giveen :- https://www.youtube.com/watch?v=hdWGcbS1Gv8
Download Hashcat GUI :- HashcatGUI_1.00r3.zip — v1.00r3 [6.33MB]
Download Hashcat Binaries :- hashcat-4.0.1.7z
Included
- hashcat-utils-1.0
- cap2hccap
Requirements:
- OS: Windows Only
- dotNET Framework: v4
- hashcat binaries
1. Your Folder Structure Should Look Like Below Image.
2. Extract The Hashcat Apps Into Folders Within The Hashcat GUI Directory.
SHARE BY GK
If you want to use Hashcat for password cracking, you’ve come to the right place.
Hashcat is a great tool for cracking passwords offline using the power of your graphics processor unit computational power. It can process an astounding number of password guesses per second, cutting down the time it takes to crack password hashes.
In this article, we will show you how to use Hashcat. We will discuss password lists, and running Hashcat in different environments, be it on a local machine, a virtual environment, or even in the cloud.
Finally, we’ll provide hands-on demonstrations to show you how to deploy Hashcat to crack some of the most commonly encountered hashes.
What Is Hashcat?
Let’s look at what Hashcat is and how it can use the power of the graphics processing unit (GPU) to crack hashes.
Hashcat
Hashcat is a popular open-source software for cracking passwords that can crack various hashes using various attack modes.
It takes advantage of hardware acceleration from the GPU, which can perform computational tasks more efficiently than a general-purpose CPU could.
The speed of a GPU directly affects the cracking speed because a faster GPU can process more password guesses simultaneously, significantly reducing the time required to find the correct password.
Depending on the type of hash, the complexity of the password, and the GPU being used, Hashcat can test up to millions of password combinations per second during a brute force attack, greatly beyond the capacity of a CPU.
What’s a Hash?
A hash is a fixed-length string representation created from the password using a hash function.
Simply put, a hash function takes input data and returns a fixed-length string through mathematical computations. Once the data has been hashed, there is no way to reverse the process and retrieve the original data from the hash.
Here is an example of an MD5 hash of the password “password123”.
And here is the MD5 hash of the password “password1234”.
As you can see, even though we only added a single number to the end of “password123”, it created a completely unique hash.
Websites create a hash of the password as a measure of security to protect users’ sensitive data. When a user logs in, the password entered is hashed, and if this hash matches the hash stored in the database, the user is logged in.
Now that you understand Hashcat and password hashes, let’s look at where we can find password lists to use with it.
Password Lists In Kali
Kali comes pre-packaged with wordlists that can be used for cracking passwords. The wordlist files are in the /usr/share/wordlists directory.
The one that is used the most, especially when doing a CTF (capture the flag), is the rockyou.txt file. This file is massive, It contains over fourteen million user passwords.
The rockyou.txt file comes from the over 32 million user credentials exposed due to a data breach in 2009 on the social media platform RockYou. These passwords were kept in plain text, not hashed or otherwise obfuscated.
Other Locations for Password Lists
Another great resource for passwords is SecLists on GitHub. This list contains many password lists, including “500-worst-passwords.txt” and “darkweb2017-top10000.txt.” The password lists are collections of commonly used, default, or leaked passwords.
The right wordlist for Hashcat can significantly boost the effectiveness of password cracking by being tailored to the organization or demographic being tested.
It should be comprehensive yet specific and consider common weak passwords, organization-specific terms, language and localization, and common password mutations.
Hashcat in Virtual Machine, Host Machine, or the Cloud?
Now let’s discuss three options for running Hashcat.
Hashcat in a Virtual Machine
Hashcat can be run inside a virtual machine such as Kali Linux, however it will not use the GPU but the CPU instead, making it much slower.
If you’re looking to install Kali Linux in a virtual machine, we have two great articles on installing it on VirtualBox and VMware.
It can have both advantages and disadvantages. Here’s a quick rundown:
Pros:
Environment Isolation: Running Hashcat in a VM keeps your main OS separate from your Host OS
Ease of Setup: Hashcat is already installed on Kali, making it easier to get up and running without installation or configuration.
Testing and Experimentation: Using Hashcat in a VM allows you to test and experiment without affecting your host OS.
Cons:
Performance Overhead: Running Hashcat in a VM is slower than running it on native hardware, especially due to its GPU-intensive tasks, because of the additional layer of abstraction provided by the VM.
Hardware Access: While most VM solutions support passing through USB devices to the guest operating system, GPU passthrough (beneficial for a tool like Hashcat) can be complex and may only be supported on some systems or with some VM software.
Resource Allocation: VMs require a portion of your system’s resources. Running intensive applications in a VM could impact the performance of the host system.
Hashcat on Host Machine
The decision to run Hashcat directly on the host OS versus in a VM depends on your specific needs and resources. Running Hashcat natively on the host operating system like Windows has its own set of pros and cons.
Pros:
Performance: Running Hashcat on the host OS performs better than running it inside a VM. This is because there are no additional layers of abstraction between the application and the hardware.
Simplicity: It might be simpler to install and run for users who are more comfortable working in a Windows environment than a Linux one or for those unfamiliar with setting up VMs.
Cons:
Resource Consumption: Hashcat is designed to use as much of your system’s resources as possible to perform its tasks quickly. While running, your computer might be slow to respond to other tasks.
System Compatibility: While Hashcat is built to be compatible with a wide range of systems and hardware, there can always be unforeseen compatibility issues or bugs that could impact its performance or stability on some systems.
Installing Hashcat on Windows
Let’s walk you through installing Hashcat on a Windows system.
The first step is to download the binary from the Hashcat site.
Once downloaded, you will need to extract the 7Zip file, we put ours in the C:\Hashcat folder, but you can put yours wherever makes the most sense for you.
To start using Hashcat in Windows, head to the command line and move into the directory you saved it. Next, you need to load hashcat.exe and any options you want to run. We’ll discuss these in another section.
Hashcat in the Cloud
Running Hashcat in the cloud, like on AWS, Azure, or Google Cloud, also comes with its own set of advantages and disadvantages:
Pros:
Scalability: Cloud platforms offer the ability to easily scale up your resources. If you need more computing power quickly, you can start a powerful GPU instance, run your task, and shut it down when you’re done.
Cost-Effectiveness: You only pay for what you use. This can be much more cost-effective than buying expensive hardware, particularly if you only need it occasionally.
Access from Anywhere: Your cloud environment can be accessed from anywhere, which can be beneficial if you work from different locations or collaborate with others.
Cons:
Price: While cloud services can be cost-effective, the costs can also add up quickly if you’re running powerful instances for long periods of time. GPU instances can be particularly expensive.
Complexity: While cloud platforms can offer a lot of flexibility, they can also be complex to set up and manage, particularly if you’re unfamiliar with the particular service.
Legal and Ethical Considerations: Using cloud resources for cracking passwords might violate the provider’s terms of service. Be sure to verify this before proceeding.
If you’re interested in setting up resources in the cloud to perform your cracking, we recommend checking out a few resources:
Cracking With Hashcat in the Cloud
Good cloud GPU providers?
Now that you’ve seen the pros and cons of running Hashcat on a VM, host machine, or in the cloud, the choice ultimately depends on your specific requirements, resource availability, and the level of risk you’re willing to accept.
Cracking Hashes With Hashcat
Now that you’re ready to crack hashes with Hashcat, let’s talk about the different hashes you may encounter and how to identify them. Then, we’ll show you this tool in action.
Hashes Available in Hashcat
The Hashcat Wiki has a great resource for finding all the hashes that work with the program. It gives you a table view of hashes.
You can easily search through this with the find command in your browser. This will help you find which hash mode to use with the hash you need to crack.
You can also view the list of hashes from the command line using --help.
And scroll down a little until you see the section titled “Hash modes.”
On a Linux system, you can also use the grep command to search quickly for a specific hash, such as hashcat --help | grep md5.
Popular Hashes Used
Here are some hash types you may see as a penetration tester or ethical hacker.
SHA-256 (Secure Hash Algorithm 256-bit): This is part of the SHA-2 family and is widely used in cryptographic applications and protocols, including TLS and SSL, PGP, SSH, and Bitcoin, among others.
Here is an example of an SHA-256 hash:
f2881bb653e5a11780fad1b3a7ef2d4fd10f1cced3d71c76443d7670aa0257d8
AS-REP (Authentication Service Response): This hash is part of the Kerberos protocol used for network authentication, including in Windows Active Directory domains and some Unix environments. This hash is acquired through AS-REP roasting, which extracts users’ password hashes with the activated «Do not require Kerberos preauthentication» setting.
Here is an example of a Kerberos AS-REP hash:
$krb5asrep$23$auston@xyz.local:3171EA207B3A6FDAEE52BA247C20362E$56FE7DC0CABA8CB7D3A02A140C612A917DF3343C01BCDAB0B669EFA15B29B2AEBBFED2B4F3368A897B833A6B95D5C2F1C2477121C8F5E005AA2A588C5AE72AADFCBF1AEDD8B7AC2F2E94E94CB101E27A2E9906E8646919815D90B4186367B6D5072AB9EDD0D7B85519FBE33997B3D3B378340E3F64CAA92595523B0AD8DC8E0ABE69DDA178D8BA487D3632A52BE7FF4E786F4C271172797DCBBDED86020405B014278D5556D8382A655A6DB1787DBE949B412756C43841C601CE5F21A36A0536CFED53C913C3620062FDF5B18259EA35DE2B90C403FBADD185C0F54B8D0249972903CA8FF5951A866FC70379B9DA
NTLM Hash: The NTLM hash is utilized in older Microsoft systems and applications, notably in workgroup environments and for local authentication on non-domain controllers. While it remains in use, more secure protocols like Kerberos are favored. NTLM support remains across all Windows systems to maintain compatibility with older server and client setups.
Here is an example of an NTLM hash:
58A478135A93AC3BF058A5EA0E8FDB71
Identify Hashes
If you come across a hash and aren’t sure what hashing algorithm is being used, some tools can help you identify them, such as Hash-Identifer or hashID.
hashID replaces Hash-Identifier, although it can still be used and is installed by default on Kali.
hashID can be installed from the command line using the following.
pip install hashid
Once installed, you simply type hashid -m and the hash you need to be identified, as seen below. This will show the corresponding Hashcat mode alongside the potential hash. Let’s take the following hash and put it into hashID.
7eb126739275d3717e981a78311dbdf6f71b7a74
The hash is identified as being a SHA-1 hash.
These tools do their best at guessing the correct hash but may not be able to accurately identify all hashes you input. Understanding the technology you are working with will go a long way in knowing which hash is being used.
Using Hashcat
Now we will show you how to crack multiple hashes using Hashcat.
Hashcat can run different attacks, such as a dictionary, combination, mask, and hybrid, but we will use the dictionary attack for our demo.
In dictionary attacks, each word in the password file is hashed and compared with the target hashes. If the hashes match, then the original password has been found.
You can run a basic Hashcat dictionary attack using the following command.
hashcat -m 0 -a 0 hash.txt wordlist.txt
- hashcat: This is the main command to run the Hashcat program (on Windows, use hashcat.exe).
- -m 0: This is the option for the hash type. In this case, 0 represents MD5. The value here would change depending on the hash type you are trying to crack. For instance, -m 1000 would be used for NTLM hashes.
- -a 0: This is the attack mode. In this case, 0 stands for «straight» mode, a dictionary attack.
- hash.txt: This file contains the hash or hashes you’re trying to crack. It should be a text file with one hash per line.
- wordlist.txt: This is your dictionary or list of potential passwords. Like the hash file, this should be a text file with one entry per line.
Hahscat can be used with other options, depending on what you need. Here are some examples:
- -r: This option allows you to specify a rules file. Rules in Hashcat allow you to modify the words from your wordlist in certain ways, which can greatly expand the number of potential passwords you’re testing. For example, a rule could be to try the word in lowercase and uppercase or to append certain numbers to the end of the word.
- —debug: This option enables debug mode. In debug mode, Hashcat will provide additional output to help you troubleshoot issues. For instance, if you’re using a rules file, debug mode can show you exactly how the rules modify the words from your wordlist.
- —force: This option forces Hashcat to start even if it detects that your system might not be capable of running it correctly. Using this option’s generally only recommended if you know what you’re doing, as it could lead to incorrect results or even damage your hardware.
Let’s try to crack two of the hashes from our popular hashes section. We will be using the rockyou.txt as our wordlist file.
This demonstration will show you how to run Hashcat in Windows, but it’s the same syntax when you run this in Linux. Ensure that you save the hash as a .txt file.
Our first hash is the Kerberos AS-Rep one shown in the previous section.
hashcat.exe -m 18200 asrep.txt -a 0 rockyou.txt
And we’ve cracked the password in only two seconds. As you can see, the weaker the password, the easier for Hashcat to crack.
You’re likely to encounter the NTLM hash, our second hash type, quite frequently if you’re pursuing a career as a penetration tester or interested in learning to attack Active Directory. The NTLM hash is still frequently used today in Windows operating systems.
The syntax you need to use is:
hashcat.exe -m 1000 ntlmhash.txt -a 0 rockyou.txt
This time we have the password cracked in only three seconds.
Conclusion
Hashcat is a potent tool that can be deployed to crack a diverse range of hashed passwords, from SHA-256 to NTLM and Kerberos. Hashcat can swiftly crack many passwords by harnessing your GPU’s power using a dictionary attack.
You’ve now learned how Hashcat works and how to use it. Additionally, you’ve discovered that Hashcat can run in various environments, including in a virtual machine (VM) or the cloud, expanding its versatility.
If you’re ready to level up your skills, join our VIP section for a massive selection of courses.
Frequently Asked Questions
What is password hashing?
Password hashing transforms a password by passing it through a hashing function, resulting in some fixed-length string. An example of the MD5 hash of the password “MyPassword” is 48503dfd58720bd5ff35c102065a52d7. Each password will have a unique string.
Can I use Hashcat without GPU?
Yes, you can use Hashcat without a GPU. In this case, Hashcat will default to using the CPU for processing, but be aware that this will result in significantly slower performance compared to using a GPU.
Is Hashcat better than John the Ripper?
If you’re cracking common hashes and speed is your primary concern, Hashcat is typically the better choice. However, if you’re dealing with a wider variety of hashes or non-standard hashes, John the Ripper may be more suitable. It ultimately depends on your specific requirements and resources.
How do you use Hashcat on Windows?
To use Hashcat on Windows, you need to download the binary, extract the 7zip file and then run it in the command line from the folder you installed it in. Such as hashcat.exe -m 1000 hash.txt -a 0 wordlist.txt
Level Up in Cyber Security: Join Our Membership Today!
-
Richard is a cyber security enthusiast, eJPT, and ICCA who loves discovering new topics and never stops learning. In his home lab, he’s always working on sharpening his offensive cyber security skills. He shares helpful advice through easy-to-understand blog posts that offer practical support for everyone. Additionally, Richard is dedicated to raising awareness for mental health. You can find Richard on LinkedIn, or to see his other projects, visit his Linktree.
View all posts
Hashcat is my favorite password cracker. You can use it on any operating system or distribution, but it’s often easier to use Windows to avoid drivers issues (especially with a recent GPU). Anyway, I will explain how to install it on Windows in this tutorial.
Hashcat is officially supported on Windows, binaries files can be downloaded on the official website directly. Once the files extracted, Hashcat can be used directly in the command prompt, there is no installation required.
If you are new to this, it might not be obvious to you, but don’t worry, I’ll explain everything in this step-by-step tutorial.
Hide your IP address and location with a free VPN:
Try it for free now, companies are paying for you.
1500 servers in 120 countries. It’s free. Forever. No email required.
Here are the required steps to install Hashcat on Windows:
- Download the latest Hashcat version from the official website.
- Extract the files on your computer.
- Open a command prompt and run hashcat in command line.
I will now explain each step in details.
Download Hashcat
The first step is to download the latest Hashcat version. It’s available on their official website:
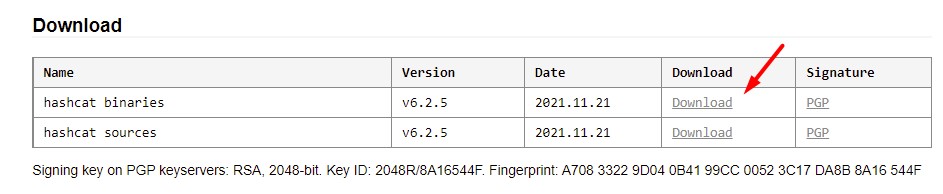
- Go to the Hashcat website homepage.
- Find the binaries and click on “Download” to get the archive on your computer.
The file is an archive, so the next step will be to extract the files before using them.
Extract the files
The files are compressed with 7zip. If you can’t open the archive, you might need to install it first:
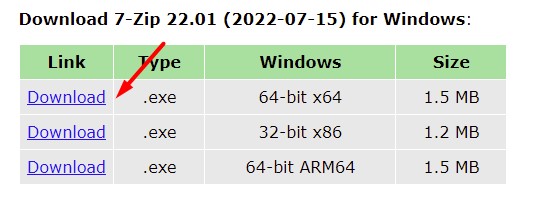
- Go to the 7zip website.
- Download the file corresponding to your operating system (the first link should be fine if your computer is recent, or use the 32-bit version if you have any doubt).
- Once downloaded, double-click on the file to install 7zip on your computer.
Follow the installation wizard, keep the default options.
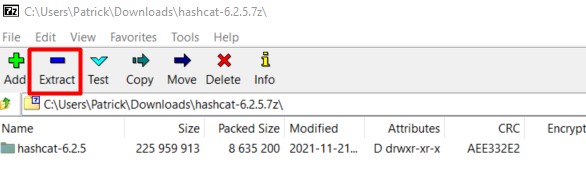
Once done, you should be able to open the Hashcat archive and extract the files.
Click on the “Extract” button in the top bar:
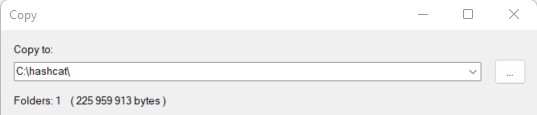
I recommend choosing a different path for the extract location. I don’t know you, but in my case, I tend to delete everything in the “Downloads” folder from time to time, and if I keep hashcat there, I will need to reinstall it eventually.
So, for the example, I’m extracting the files to C:\hashcat, but you can put them wherever you want:
Remember the files location, as you’ll have to go to this path on the next step.
Ethical Hacking Course
Learn Ethical Hacking From Scratch
Become an ethical hacker that can hack computer systems like black hat hackers and secure them like security experts.
Learn more
Run Hashcat for the first time
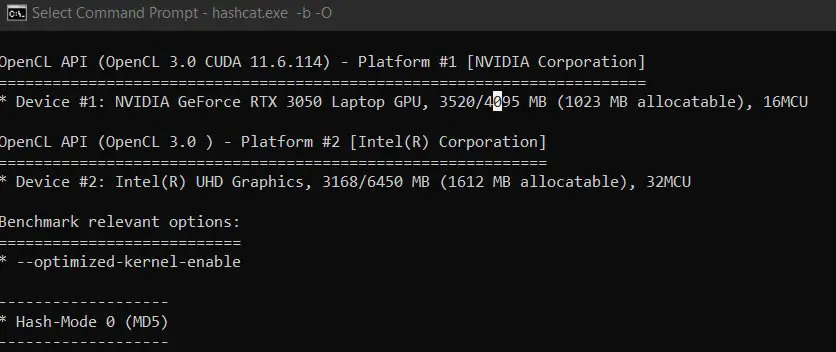
We are almost done, we’ll just make sure everything is working as expected:
This command will run a benchmark of your system, telling you the decryption rate you can expect on this computer, but also showing errors if there is something misconfigured on your system (like missing GPU drivers).
How to use Hashcat on Windows
If the benchmark command is working correctly, you can now use Hashcat on your Windows computer with the same commands as on Linux. It’s the same thing.
I already have several tutorials on this topic on the website, so I won’t repeat myself here, but if you need further assistance, feel free to read these tutorials:
- Is MD5 Easy to Crack? (and how long does it really takes)
- How to Brute Force a Password? (MD5 Hash)
- How to Install and Use Hashcat to Decrypt MD5? (Tutorial)
Hashcat FAQ
Is there a GUI for Hashcat?
Hashcat doesn’t include a graphic interface by default, but a few projects exist with the goal to add an interface to it, like the hashcat GUI toolkit (Windows interface) or Crackerjack (web interface).
Is Hashcat cross-platform?
Hashcat can run on most operating systems (Linux, Windows and macOS). The installation is slightly different on each system, but the command usage is the same on all platforms.
You can find my guide on how to install Hashcat on Ubuntu there.
How to install OpenCL on Windows?
Running hashcat on Windows require the latest drivers for your OpenCL device (your GPU). AMD and Nvidia official drivers include OpenCL by default, and for Intel GPU you have to install an additional package (link here).
If you experience any issue, make sure you installed the latest version of your graphic card driver, downloading it from the official website.
Installing this on Linux could be a nightmare with some distributions and hardware, but on Windows it’s pretty straightforward (in theory).