Introduction
This document describes how the Challenge Handshake Authentication Protocol (CHAP) verifies the identity of a peer by means of a three-way handshake.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
-
How to enable PPP on the interface through the
encapsulation pppcommand. -
The
debug ppp negotiation -
How to troubleshoot when the Link Control Protocol (LCP) phase is not in the open state. This is because, the PPP authentication phase does not begin until the LCP phase is complete and is in the open state. If the
debug ppp negotiationcommand does not indicate that LCP is open, you need to troubleshoot this issue before you proceed.
Note: This document does not address MS-CHAP (Version 1 or Version 2).
Components Used
This document is not restricted to specific software and hardware versions.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Conventions
For more information on document conventions, see the Cisco Technical Tips Conventions.
Background Information
The Challenge Handshake Authentication Protocol (CHAP) (defined in RFC 1994 ) verifies the identity of the peer by means of a three-way handshake. These are the general steps performed in CHAP:
-
After the LCP (Link Control Protocol) phase is complete, and CHAP is negotiated between both devices, the authenticator sends a challenge message to the peer.
-
The peer responds with a value calculated through a one-way hash function (Message Digest 5 (MD5)).
-
The authenticator checks the response against its own calculation of the expected hash value. If the values match, the authentication is successful. Otherwise, the connection is terminated.
This authentication method depends on a «secret» known only to the authenticator and the peer. The secret is not sent over the link. Although the authentication is only one-way, you can negotiate CHAP in both directions, with the help of the same secret set for mutual authentication.
For more information on the advantages and disadvantages of CHAP, refer to RFC 1994.
Configure CHAP
The procedure to configure CHAP is fairly straightforward. For example, assume that you have two routers, left and right, connected across a network, as shown in Figure 1.
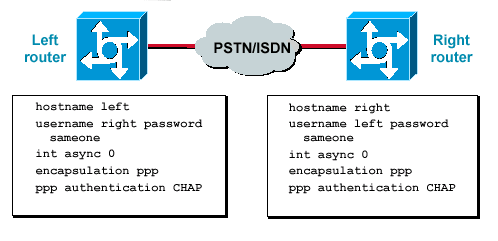
Figure 1 — Two Routers Connected Across a Network
To configure CHAP authentication, complete these steps:
-
On the interface, issue the encapsulation ppp command.
-
Enable the use of CHAP authentication on both routers with the
ppp authentication chapcommand. -
Configure the usernames and passwords. To do so, issue the
username username password passwordcommand, whereusernameis the hostname of the peer. Ensure that:-
Passwords are identical at both ends.
-
The router name and password are exactly the same, because they are case-sensitive.
-
Note: By default, the router uses its hostname to identify itself to the peer. However, this CHAP username can be changed through the ppp chap hostname command. Refer to PPP Authentication with the ppp chap hostname and ppp authentication chap callin Commands for more information.
One-Way and Two-Way Authentication
CHAP is defined as a one-way authentication method. However, you use CHAP in both directions to create a two-way authentication. Hence, with two-way CHAP, a separate three-way handshake is initiated by each side.
In the Cisco CHAP implementation, by default, the called party must authenticate the calling party (unless authentication is completely turned off). Therefore, a one-way authentication initiated by the called party is the minimum possible authentication. However, the calling party can also verify the identity of the called party, and this results in a two-way authentication.
One-way authentication is often required when you connect to non-Cisco devices.
For one-way authentication, configure the ppp authentication chap callincommand on the calling router.
Table 1 shows when to configure the callin option.
Table 1: When to Configure the Callin Option
| Authentication Type | Client (calling) | NAS (called) |
|---|---|---|
| One-way (unidirectional) | ppp authentication chap callin | ppp authentication chap |
| Two-way (bidirectional) | ppp authentication chap | ppp authentication chap |
Refer to PPP Authentication with the ppp chap hostname and ppp authentication chap callin Commands for more information.
CHAP Configuration Commands and Options
Table 2 lists the CHAP commands and options:
Table 2: CHAP Commands and Options
| Command | Description |
|---|---|
| ppp authentication {chap | ms-chap | ms-chap-v2 | eap |pap} [callin] | This command enables local authentication of the remote PPP peer with the specified protocol. |
| ppp chap hostnameusername | This command defines an interface-specific CHAP hostname. Refer to PPP Authentication with the ppp chap hostname and ppp authentication chap callin Commandsfor more information. |
| ppp chap passwordpassword | This command defines an interface-specific CHAP password. |
| ppp directioncallin | callout | dedicated | This command forces a call direction. Use this command when a router is confused as to whether the call is incoming or outgoing (for example, when connected back-to-back or connected by leased lines and the Channel Service Unit or Data Service Unit (CSU/DSU) or ISDN Terminal Adapter (TA) are configured to dial). |
| ppp chap refuse [callin] | This command disables remote authentication by a peer (default enabled). With this command, CHAP authentication is disabled for all calls, which means that all attempts by the peer to force the user to authenticate with the help of CHAP are refused. The callin option specifies that the router refuses to answer CHAP authentication challenges received from the peer, but still requires the peer to answer any CHAP challenges that the router sends. |
| ppp chap wait | This command specifies that the caller must authenticate first (default enabled). This command specifies that the router does not authenticate to a peer that requests CHAP authentication until after the peer has authenticated itself to the router. |
| ppp max-bad-auth value | This command specifies the allowed number of authentication retries (the default value is 0). This command configures a point-to-point interface not to reset itself immediately after an authentication failure, but instead to allow a specified number of authentication retries. |
| ppp chap splitnames | This hidden command allows different hostnames for a CHAP challenge and response (the default value is disabled). |
| ppp chap ignoreus | This hidden command ignores CHAP challenges with the local name (the default value is enabled). |
Transactional Example
The diagrams in this section show the series of events that occur during a CHAP authentication between two routers. These do not represent the actual messages seen in the debug ppp negotiationcommand output. For more information, refer to Understand debug ppp negotiation Output.
Call

Figure 2 — The Call Comes In
Figure 2 displays these steps:
-
The call comes in to 3640-1. The incoming interface is configured with the
ppp authentication chapcommand. -
LCP negotiates CHAP and MD5. For more information on how to determine this, refer to Understand debug ppp negotiation Output.
-
A CHAP challenge from 3640-1 to the calling router is required on this call.
Challenge
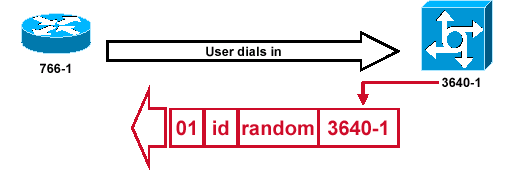
Figure 3 — A CHAP Challenge Packet is Built
Figure 3illustrates these steps in the CHAP authentication between the two routers:
-
A CHAP challenge packet is built with these characteristics:
-
01 = challenge packet type identifier.
-
ID = sequential number that identifies the challenge.
-
random = a reasonably random number generated by the router.
-
3640-1 = the authentication name of the challenger.
-
-
The ID and random values are kept on the called router.
-
The challenge packet is sent to the calling router. A list of outstanding challenges is maintained.
Response
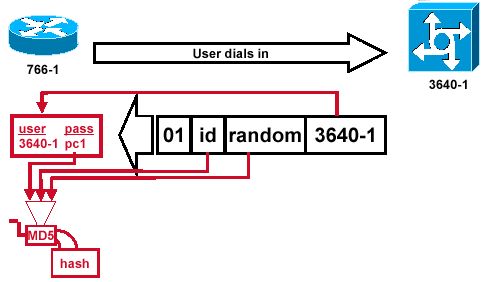
Figure 4 — Receipt and MD5 Processing of the Challenge Packet from the Peer
Figure 4 illustrates the how the challenge packet is received from the peer, and processed (MD5). The router processes the incoming CHAP challenge packet in this way:
-
The ID value is fed into the MD5 hash generator.
-
The random value is fed into the MD5 hash generator.
-
The name 3640-1 is used to look up the password. The router looks for an entry that matches the username in the challenge. In this example, it looks for:
username 3640-1 password pc1
4. The password is fed into the MD5 hash generator.
The result is the one-way MD5-hashed CHAP challenge that is sent back in the CHAP response.
Response (Continued)
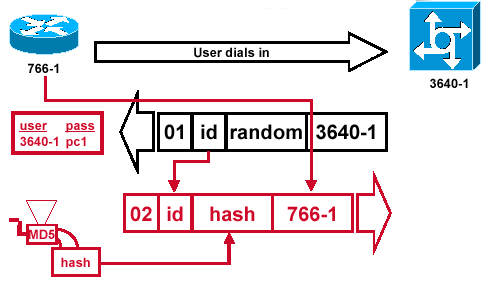
Figure 5 — The CHAP Response Packet Sent to the Authenticator is Built
Figure 5 illustrates how the CHAP response packet sent to the authenticator is built. This diagram shows these steps:
-
The response packet is assembled from these components:
-
02 = CHAP response packet type identifier.
-
ID = copied from the challenge packet.
-
hash = the output from the MD5 hash generator (the hashed information from the challenge packet).
-
766-1 = the authentication name of this device. This is needed for the peer to look up the username and password entry needed to verify identity (this is explained in more detail in the Verify CHAP section).
-
-
The response packet is then sent to the challenger.
Verify CHAP
This section provides tips on how to verify your configuration.
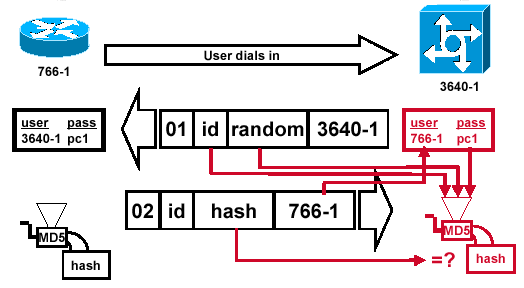
Figure 6 — The Challenger Processes the Response Packet
Figure 6 shows how the challenger processes the response packet. Here are the steps involved when the CHAP response packet is processed (on the authenticator):
-
The ID is used to find the original challenge packet.
-
The ID is fed into the MD5 hash generator.
-
The original challenge random value is fed into the MD5 hash generator.
-
The name 766-1 is used to look up the password from one of these sources:
-
Local username and password database.
-
RADIUS or TACACS+ server.
-
-
The password is fed into the MD5 hash generator.
-
The hash value received in the response packet is then compared with the calculated MD5 hash value. CHAP authentication succeeds if the calculated and the received hash values are equal.
Result
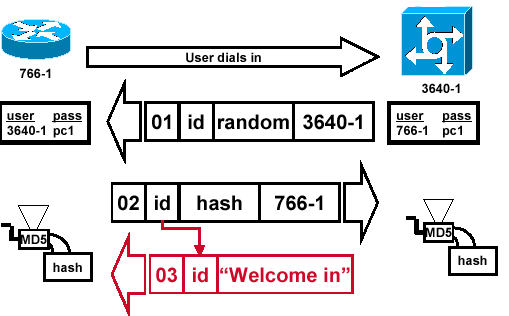
Figure 7 — Success Message is Sent to the Calling Router
Figure 7 illustrates the success message sent to the calling router. This involves these steps:
-
If authentication is successful, a CHAP success packet is built from these components:
-
03 = CHAP success message type.
-
ID = copied from the response packet.
-
«Welcome in» is simply a text message that provides a user-readable explanation.
-
-
If authentication fails, a CHAP failure packet is built from these components:
-
04 = CHAP failure message type.
-
ID = copied from the response packet.
-
«Authentication failure» or other text message, that provides a user-readable explanation.
-
-
The success or failure packet is then sent to the calling router.
Note: This example depicts a one-way authentication. In a two-way authentication, this entire process is repeated. However the calling router initiates the initial challenge.
Troubleshoot CHAP
Refer to Troubleshoot PPP (CHAP or PAP) Authentication for information on how to troubleshoot any issues.
Related Information
- Understand debug ppp negotiation Output
- PPP Authentication with the ppp chap hostname and ppp authentication chap callin Commands
- Cisco Technical Support & Downloads
В настоящее время, имея доступ к беспроводной сети, многие могут легко получить доступ к важной информации, поэтому важно выбрать правильный тип аутентификации для защиты вашей беспроводной сети. Ниже мы рассмотрим несколько типов протоколов аутентификации и рекомендации по выбору наиболее надежного варианта.
- Что такое PAP и CHAP
- Как выбрать тип аутентификации
- Какие протоколы аутентификации поддерживает PPP
- Почему медленный интернет на андроиде
- Советы по защите беспроводной сети
- Выводы
Что такое PAP и CHAP
PAP и CHAP — это два типа протоколов аутентификации для беспроводной сети. PAP (Password Authentication Protocol) — это основной и наименее защищенный способ аутентификации. Протокол PAP отправляет имя пользователя и пароль в открытом виде и криптографически не защищен, что делает его уязвимым к атакам и различным видам взлома паролей. CHAP (Challenge Handshake Authentication Protocol) более защищенный протокол, потому что он выполняет проверку подлинности внутрисквозной связи между оригинальным запросом и ответом клиента. CHAP чаще используется для безопасных подключений к серверам или VPN-сетям.
Как выбрать тип аутентификации
Наиболее надежным методом аутентификации сейчас считается WPA3, который обеспечивает более надежную защиту, чем WPA2. Однако, старые устройства не всегда поддерживают WPA3, поэтому для лучшей совместимости мы рекомендуем использовать смешанный режим WPA2/WPA3 — Personal. Если вам требуется высокий уровень защиты, выбирайте протокол CHAP.
Какие протоколы аутентификации поддерживает PPP
Microsoft PPP поддерживает следующие NCP:
- Internet Protocol Control Protocol (IPCP) для настройки IP.
- Internetwork Packet Exchange Control Protocol (IPXCP) для настройки IPX.
- AppleTalk Control Protocol (ATCP) для настройки AppleTalk.
Почему медленный интернет на андроиде
Медленный мобильный интернет на вашем Android-устройстве может быть вызван различными причинами, но чаще всего он связан с проблемами технического характера оператора связи или некачественным покрытием в зоне вашего местоположения. Также ресурсоемкие приложения могут расходовать трафик интернета и снижать скорость соединения. Если у вас возникли проблемы с медленным подключением, попробуйте перезагрузить ваше устройство или напишите в техническую поддержку вашего оператора связи.
Советы по защите беспроводной сети
- Используйте более надежный протокол WPA3;
- Обновляйте пароли и логины для доступа к сети;
- Никогда не будьте связаны со слабыми точками доступа, такими как открытые Wi-Fi-сети;
- Никогда не храните личные данные на общедоступной сети без защиты пароля;
- Периодически проверяйте свою сеть на наличие вторжений;
- Установите антивирусное программное обеспечение на все устройства, подключенные к беспроводной сети.
Выводы
Защита вашей беспроводной сети на самом деле может быть более важной, чем вы можете подумать. Надежное шифрование и правильный выбор протоколов аутентификации могут предотвратить нежелательные атаки на вашу сеть и сохранить важную информацию в безопасности. Следуя нашим приведенным выше советам, вы можете убедиться, что ваша беспроводная сеть защищена от внешних угроз.
Что такое аутентификации на телефоне
Аутентификация на телефоне — это способ подтверждения личности пользователя с помощью кода, который отправляется на его мобильное устройство по запросу. Этот метод является премиум-классом двухфакторной аутентификации, который обеспечивает высокую надежность и безопасность. Для выполнения аутентификации пользователь должен ввести свой номер телефона, после чего код будет отправлен на указанный номер. Затем пользователю необходимо ввести этот код для подтверждения своей личности. Такой подход повышает безопасность, так как требуется не только знание пароля, но и доступ к физическому устройству пользователя. Аутентификация по телефону широко применяется в системах интернет-банкинга, электронной почты и других онлайн-сервисах, где безопасность данных очень важна. Этот метод становится все более популярным благодаря своей простоте и надежности.
Что такое ошибка аутентификации в телефоне
Ошибка аутентификации в телефоне возникает, когда мы неправильно вводим пароль от Wi-Fi сети или настройки безопасности на маршрутизаторе заданы неверно. Как результат, телефон не может успешно подключиться к сети. Это проблема, которая может возникнуть как на смартфонах, так и на других устройствах с поддержкой Wi-Fi. Устранить ошибку можно путем проверки указанного пароля и исправления ошибок в настройках маршрутизатора. Также возможно перезагрузить маршрутизатор и смартфон, чтобы очистить временные данные и попытаться повторно подключиться. Если проблема сохраняется, стоит обратиться к провайдеру интернета или к специалисту, чтобы проверить настройки сети и найти решение проблемы. В целом, ошибка аутентификации в телефоне может быть разрешена путем правильной настройки подключения к Wi-Fi сети.
Какой APN у теле2
Название интернет-провайдера, который я хочу подключить, — Теле2. Прежде чем приступить к настройке, я хочу узнать, какой APN использовать. APN, или точка доступа, — это настройка, которая позволяет подключиться к интернету через мобильный оператор. После некоторого исследования мне удалось найти данные APN для Теле2. Имя APN — Tele2 Internet. APN самого провайдера — internet.tele2.ru. Тип играет важную роль в настройке APN и в данном случае тип APN — default, supl. Настройка APN необходима для правильной работы мобильного интернета на устройстве. Я собираюсь использовать эти данные для настройки подключения к интернету на своем устройстве и надеюсь, что все будет работать исправно.
Как прописать точку доступа теле2
Чтобы прописать точку доступа Теле2, нужно выполнить следующие действия:
- Зайдите в Настройки на своем устройстве.
- Выберите раздел «Беспроводные сети».
- Далее выберите «Мобильная сеть».
- Найдите пункт «Точки доступа (APN)» и выберите его.
- Нажмите на сенсорную клавишу Меню и выберите «Новая точка доступа».
- Введите имя точки доступа — TELE2 Internet.
- В поле APN введите internet.tele2.ru.
- Далее, в поле MCC введите 250, а в поле MNC введите 20.
- В поле «Тип APN» выберите значение «default».
- Протокол APN установите на IPv4.
- Остальные поля оставьте пустыми.
- Сохраните настройки.
Теперь точка доступа Теле2 должна быть прописана на вашем устройстве.
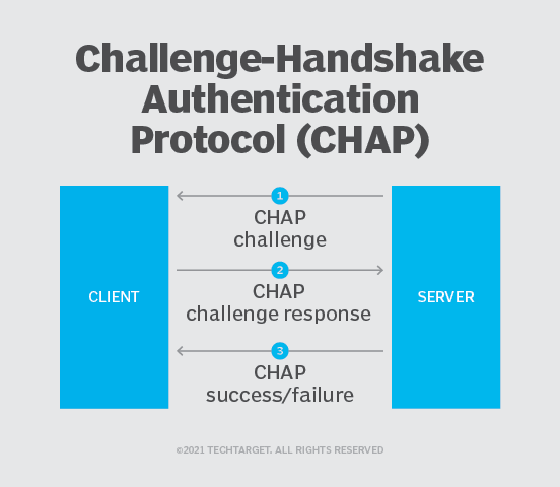
Challenge Handshake Authentication Protocol (CHAP) is a challenge-response identity authentication protocol. It depends on a combination of CHAP security credentials and a “shared secret” between the requestor (client) and the authenticator (server), and it does not expose a password. It requires both entities to prove their identity through a cryptographic exchange or a “three-way handshake”. When that is successful, authentication is complete.
Ongoing authentication requests from the server to the client continue on a regular basis after the initial handshake, which means the identifiers must change with every new authentication. This is one of the reasons why CHAP is more secure than Password Authentication Protocol (PAP).
How It Works
Before the handshake process can begin, the client and the server must have each other’s credentials, including their shared secret, on file. Once a Point-to-Point Protocol (PPP) link is established, the client nudges the server by sending only their username (not the password) across the connection.
-
At this point, the server responds to the client’s username with a CHAP challenge packet and asks the client for a shared secret. This is part one of the three-way handshake.
-
The client provides the server with a valid, encrypted answer that contains the shared secret. This is the second part of the three-way handshake.
-
If the client’s answer matches what the server expected, the server authenticates the client. This is the third and final part of the three-way handshake.
Below is a more detailed look at what happens at each step.
Both Entities Create and Share CHAP Credentials
As mentioned above, before a PPP link is established, the two entities must have each other’s CHAP credentials in their files. A CHAP credential consists of a CHAP username and a CHAP “secret.” A traditional password is not used or transmitted in CHAP.
A Link Is Established
With CHAP credentials in place, the initial PPP link can be activated. At this point, the client enters their username and password in the application or website. The username (not the password) is sent to the server to ask the server for a challenge packet.
CHAP Authentication Begins
SERVER: When the CHAP server receives the username from the client, it sends back a CHAP challenge packet that contains a random number and unique ID.
CLIENT: When the client receives the challenge, they must send back a calculation that contains the server’s random number and unique ID along with their own CHAP security credentials, which include the shared secret.
SERVER: If the client’s calculation matches the server’s calculation, the client is authenticated.
ONGOING AUTHENTICATION: After the initial authentication, while the client is still engaged in an online session, they’ll occasionally be re-authenticated by the server to make sure the connection remains safe and secure. Since these repeated challenges require a unique response from the client, it reduces the time of exposure to any single attack and lessens the threat of replay attacks.
PAP vs. CHAP
PAP is more susceptible to cyberattacks than CHAP because it doesn’t have the built-in safeguards that CHAP has. Specifically, CHAP doesn’t transmit passwords, has an ongoing authentication mechanism, and uses an encrypted calculation to help each entity verify the identity of the other.
Why CHAP Is One of the More Secure Forms of Authentication Available
One of the reasons CHAP is so secure is that it uses a challenge-response mechanism that requires the client and server to share a secret calculation before the user can be authenticated. No password is ever transferred, which reduces the likelihood of password breaches. In addition, ongoing authentication offers an extra layer of security because the client has to provide a new calculation for the server each time.
From Wikipedia, the free encyclopedia
In computing, the Challenge-Handshake Authentication Protocol (CHAP) is an authentication protocol originally used by Point-to-Point Protocol (PPP) to validate users. CHAP is also carried in other authentication protocols such as RADIUS and Diameter.
Almost all network operating systems support PPP with CHAP, as do most network access servers. CHAP is also used in PPPoE, for authenticating DSL users.
As the PPP sends data unencrypted and «in the clear», CHAP is vulnerable to any attacker who can observe the PPP session. An attacker can see the user’s name, CHAP challenge, CHAP response, and any other information associated with the PPP session. The attacker can then mount an offline dictionary attack in order to obtain the original password. When used in PPP, CHAP also provides protection against replay attacks by the peer through the use of a challenge which is generated by the authenticator, which is typically a network access server.
Where CHAP is used in other protocols, it may be sent in the clear, or it may be protected by a security layer such as Transport Layer Security (TLS). For example, when CHAP is sent over RADIUS using User Datagram Protocol (UDP), any attacker who can see the RADIUS packets can mount an offline dictionary attack, as with PPP.
CHAP requires that both the client and server know the clear-text version of the password, although the password itself is never sent over the network. Thus when used in PPP, CHAP provides better security as compared to Password Authentication Protocol (PAP) which is vulnerable for both these reasons.
Benefits of CHAP[edit]
When the peer sends CHAP, the authentication server will receive it, and obtain the «known good» password from a database, and perform the CHAP calculations. If the resulting hashes match, then the user is deemed to be authenticated. If the hashes do not match, then the users authentication attempt is rejected.
Since the authentication server has to store the password in clear-text, it is impossible to use different formats for the stored password. If an attacker were to steal the entire database of passwords, all of those passwords would be visible «in the clear» in the database.
As a result, while CHAP can be more secure than PAP when used over a PPP link, it prevents more secure storage «at rest» than with other methods such as PAP.
Variants[edit]
MS-CHAP is similar to CHAP but uses a different hash algorithm, and allows for each party to authenticate the other.
Working cycle[edit]
CHAP is an authentication scheme originally used by Point-to-Point Protocol (PPP) servers to validate the identity of remote clients. CHAP periodically verifies the identity of the client by using a three-way handshake. This happens at the time of establishing the initial link (LCP), and may happen again at any time afterwards. The verification is based on a shared secret (such as the client’s password).[1]
- After the completion of the link establishment phase, the authenticator sends a «challenge» message to the peer.
- The peer responds with a value calculated using a one-way hash function on the challenge and the secret combined.
- The authenticator checks the response against its own calculation of the expected hash value. If the values match, the authenticator acknowledges the authentication; otherwise it should terminate the connection.
- In PPP, the authenticator may send a new challenge at random intervals to the peer and repeats steps 1 through 3. However, when CHAP is used in most situations (e.g. RADIUS), this step is not performed.
CHAP packets[edit]
| Description | 1 byte | 1 byte | 2 bytes | 1 byte | Variable | Variable |
|---|---|---|---|---|---|---|
| Challenge | Code = 1 | ID | Length | Challenge length | Challenge value | Name |
| Response | Code = 2 | ID | Length | Response length | Response value | Name |
| Success | Code = 3 | ID | Length | Message | ||
| Failure | Code = 4 | ID | Length | Message |
The ID chosen for the random challenge is also used in the corresponding response, success, and failure packets. A new challenge with a new ID must be different from the last challenge with another ID. If the success or failure is lost, the same response can be sent again, and it triggers the same success or failure indication. For MD5 as hash the response value is MD5(ID||secret||challenge), the MD5 for the concatenation of ID, secret, and challenge.[2]
See also[edit]
- List of authentication protocols
- Password Authentication Protocol
- Challenge–response authentication
- Cryptographic hash function
References[edit]
- ^ Forouzan (2007). Data Communications & Networking 4E Sie. McGraw-Hill Education (India) Pvt Limited. pp. 352–. ISBN 978-0-07-063414-5. Retrieved 24 November 2012.
- ^ «Understanding and Configuring PPP CHAP Authentication». Cisco tech note. 2005. Retrieved 2011-08-14.
External links[edit]
- RFC 1994 PPP Challenge Handshake Authentication Protocol (CHAP)
- RFC 2865 Remote Authentication Dial In User Service (RADIUS): uses PAP or CHAP
- RFC 3748 Extensible Authentication Protocol (EAP): discusses CHAP
CHAP (Challenge-Handshake Authentication Protocol) is a challenge and response authentication method that Point-to-Point Protocol (PPP) servers use to verify the identity of a remote user. CHAP authentication begins after the remote user initiates a PPP link.
CHAP enables remote users to identify themselves to an authenticating system, without exposing their password. With CHAP, authenticating systems use a shared secret — the password — to create a cryptographic hash using the MD5 message digest algorithm.
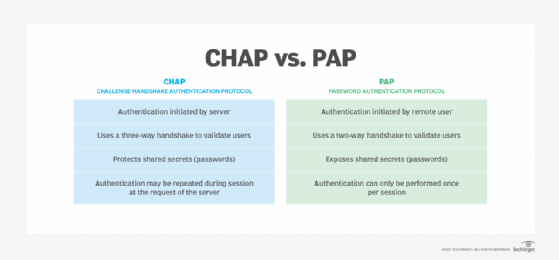
CHAP uses a three-way handshake to verify and authenticate the identity of the user, whereas the Password Authentication Protocol (PAP) uses a two-way handshake for authentication between the remote user and PPP server.
Designed to be used with PPP for authenticating remote users, CHAP is applied periodically during a remote session to reauthenticate the user. PAP and CHAP are primarily intended for remote connections over dial-up lines or switched circuits, as well as for dedicated links.
PAP and CHAP are commonly used for negotiating a network connection to an internet service provider. CHAP is specified in Request for Comments 1994.
How does CHAP work?
Here’s how CHAP works:
- After the link is made, the server sends a challenge message to the connection requestor.
- The requestor responds with a value obtained by using a one-way hash function known as MD5.
- The server checks the response by comparing it with its own calculation of the expected hash value. If the values match, the authentication is acknowledged; otherwise, the connection is usually terminated.
The server can send a new challenge to the requestor randomly during the session to reauthenticate the requestor. Steps 1 through 3 are then repeated.
At any time, the server can request the connected party to send a new challenge message. Because CHAP identifiers are changed frequently and authentication can be requested by the server at any time, CHAP provides more security than PAP.
Types of CHAP packets
PPP carries CHAP packets between the authenticator and the requestor. CHAP packets consist of a header, which includes the following:
- Code field, which contains an eight-bit code identifying the type of CHAP packet being sent — valid values are 1 to 4;
- Identifier field, which is an arbitrary eight-bit ID identifying the packet as belonging to an authentication sequence;
- Length field, which contains the number of bytes in the CHAP packet; and
- Data field, which includes any data being requested or submitted and values depending on the type of CHAP packet it is being carried in.
CHAP works with four different types of packet. Each packet is identified by the value of its Code field, as follows:
- The authenticating system — usually a network access server or switch — sends a CHAP Challenge packet to start the authentication process. After a PPP session is initiated, the system or network being accessed can demand that the remote user authenticate. The Challenge includes the authenticator’s host name.
- The remote user’s system must send a CHAP Response packet in response to a Challenge. The remote system sends a secure hash based on the remote user’s password in the Response packet. The authenticator compares the hash of the user’s password with the expected value. The remote user is authenticated if they match; otherwise, the authentication fails.
- The authenticating system — the network access server— sends a CHAP Success packet if the remote user’s hash matches the hash expected by the server.
- The authenticating system sends a CHAP Failure packet if the remote user’s password hash does not match the value sent by the user.
If the remote system fails to respond to a Challenge packet, the authenticator can repeat the process. The authenticator terminates the remote user’s access if they can’t authenticate.
CHAP vs. PAP
CHAP is a more secure procedure for connecting to a system than PAP.
The PAP and CHAP authentication schemes were both originally specified for authenticating remote users connecting to networks or systems using PPP. CHAP’s three-way handshake protocol provides stronger protection against password guessing and eavesdropping attacks than PAP’s two-way handshake.
Authenticating with PAP requires the remote user to submit their username and password, and the authenticating system then either permits or denies the user access based on those credentials.
CHAP secures the authentication process by using a more sophisticated protocol. CHAP implements a three-way handshake protocol to be used after the host establishes a PPP connection with the remote resource.
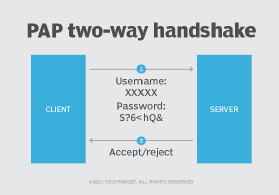
PAP defines a two-way handshake for a remote user to initiate remote access:
- The remote system sends a username and password, repeating the transmission until the network access server responds.
- The network access server transmits an authentication acknowledgement if the credentials are authenticated. If the credentials are not authenticated, the network access server sends a negative acknowledgment.
While PAP may be used as a bare minimum protocol to enable a remote user to initiate a network connection, CHAP provides a more secure authentication protocol.
This was last updated in September 2021
Continue Reading About CHAP (Challenge-Handshake Authentication Protocol)
- The top 7 identity and access management risks
- What is secure remote access in today’s enterprise?
- IPsec vs. SSL VPN: Comparing speed, security risks and technology
- Wireless network configuration basics: 5 steps to follow
- What are the most common digital authentication methods?
Dig Deeper on Identity and access management
-
Point-to-Point Protocol (PPP)
By: Andrew Froehlich
-
Use these 6 user authentication types to secure networks
By: Kyle Johnson
-
Layer Two Tunneling Protocol (L2TP)
By: Andrew Zola
-
RADIUS (Remote Authentication Dial-In User Service)
By: Peter Loshin