Во время работы или при включении компьютера внезапно может появиться так называемый «синий экран смерти». Если вчитаться в текст, написанный поверх, то там будет указана причина сбоя – некорректная работа файла Ntoskrnl.exe. Этот элемент очень важен для функционирования ОС, и когда с ним что-то происходит, пользоваться ПК становится невозможно.
Что такое Ntoskrnl.exe
Когда вы включаете компьютер, запускается целый ряд служб, в том числе, Ntoskrnl.exe, который подготавливает к работе драйверы и визуализирует изображение на экране. При этом может произойти ошибка, что влечет за собой остановку процесса. Данная служба обычно располагается на диске «С» вместе с другими компонентами системы и занимает несколько папок: System32, Driver Cache и т. п.
Причины неисправности
Ошибка ntoskrnl.ехе может возникать по целому ряду причин:
- Некорректный оверклокинг и андервольтинг, приведший к перегреву.
- Физическое удаление файла (вообще-то это достаточно трудно сделать, но возможно, если использовать ПО, влияющее на системные элементы).
- Повреждение/замена файла вирусом.
- Повреждение записей в реестре.
- Наличие проблемных или старых драйверов.
- Внутренний системный сбой.
- Сбой в работе винчестера.
- ОС не обновлена до актуальной версии.
- Повреждение или сбой в работе ОЗУ.
Возможные решения
Ошибка ntoskrnl.exe – это серьёзно, но не всегда фатально, и сейчас мы расскажем, как её исправить.
- Для начала нужно добраться до «Десктопа» и получить доступ к функциям ПК, так как, синий экран закрывает собой все пространство.
- Для этого выполните перезагрузку, и нажимайте клавишу F2 или Del (иногда бывают и другие варианты, это зависит от внутренней структуры системы ввода-вывода).
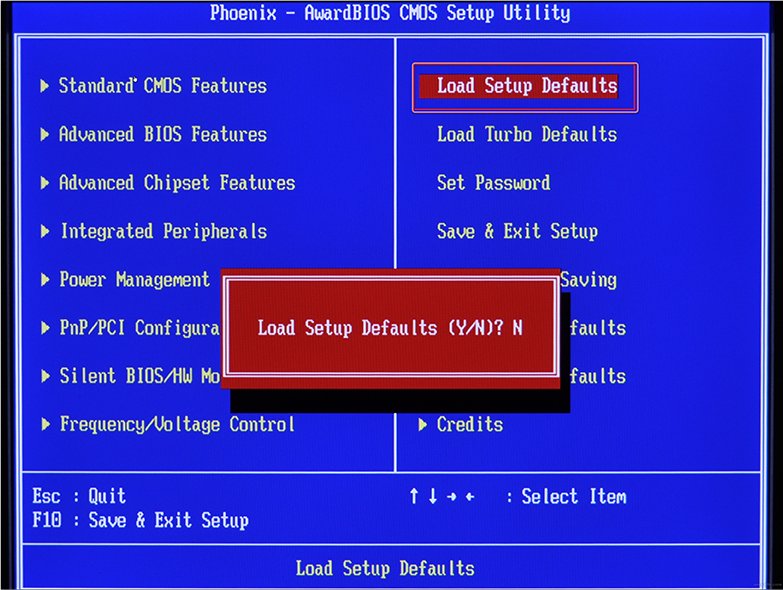
- Перед вами развернутся опции БСВВ.
- Выберите пункт Load setup defaults («Загрузить настройки по умолчанию»).
- Кликните по F10, чтобы подтвердить выбор.
- Снова перезапустите ПК – синий экран исчезнет, и можно будет переходить к исправлению ошибки.
Очистка реестра
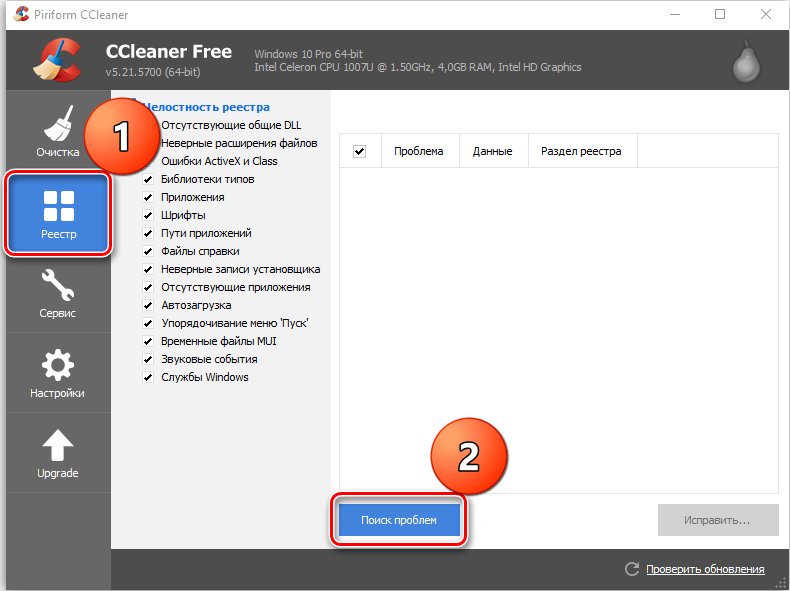
Пока не вернулась ошибка ntoskrnl.exe с синим экраном (кстати, чаще всего она возникает на windows 7), нужно начать действовать. Первым делом попробуйте почистить реестр от неправильно выполненных и устаревших записей. Удобнее и безопаснее всего делать это с помощью специальных утилит, например, небезызвестной CCleaner.
- Скачайте программу и установите её.
- Откройте окно и слева в списке найдите главу «Очистка реестра».
- Нажмите «Анализ» и дождитесь обнаружения всех проблемных записей.
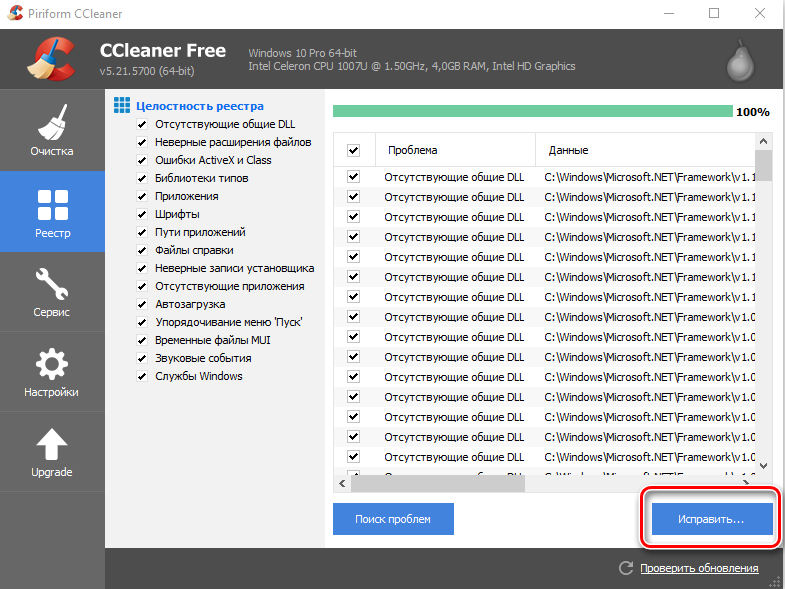
- Вверху укажите «Выделить все» и «Исправить выделенное».
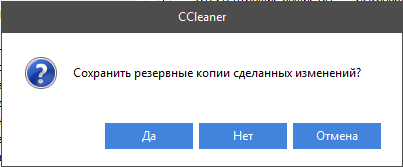
- Программа предложит сделать копию реестра – соглашайтесь, только сохраняйте ее не в «Документы» на диске «С», как указано по умолчанию, а в отдельную папку на диске «D».
- После очистки запустите «Анализ» ещё раз – и так до тех пор, пока список повреждённых элементов не останется пустым.
Исправление диска
Далее нужно проверить системный диск и исправить кое-какие ошибки, если они будут обнаружены. Для этого:
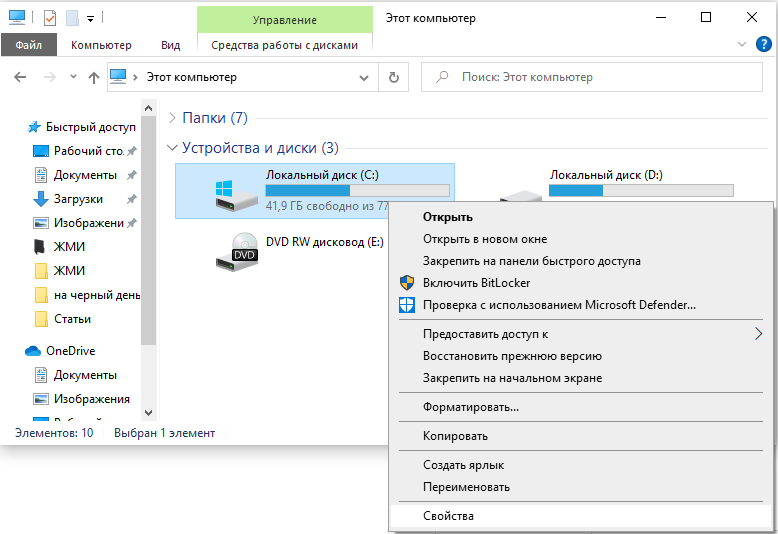
- Найдите значок «Компьютер» и разверните содержимое.
- Дважды щелкните ПКМ по диску «С» (у вас он может называться как-нибудь еще – главное, помните, что нам нужен раздел, где хранится ОС);
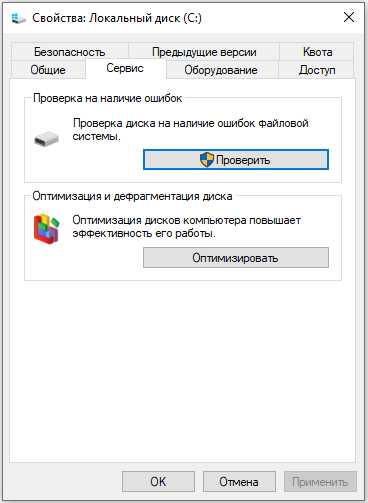
- Выберите последний пункт «Свойства», а затем подпункт «Сервис» и запустите проверку.
- Компьютер может несколько раз перезагрузиться в процессе – это нормально, не волнуйтесь.
Для этих же целей проверяем внутренние системные файлы и исправляем неполадки следующим образом:
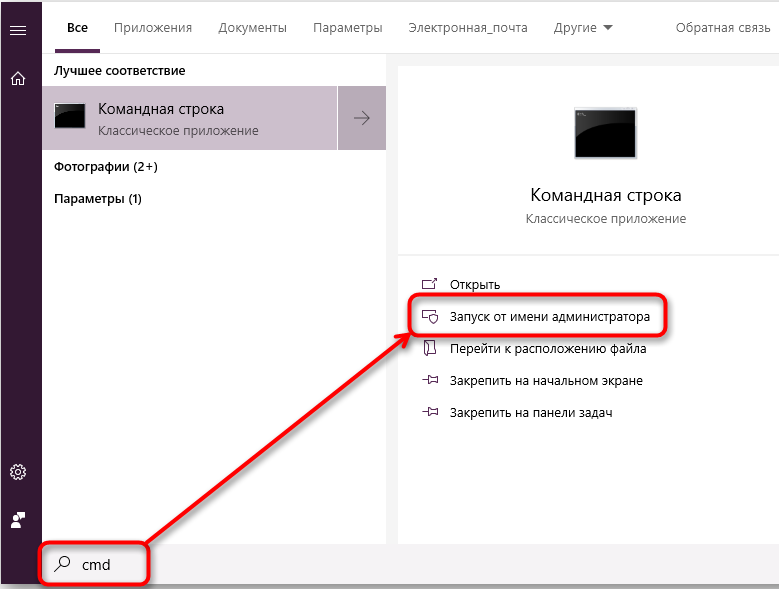
- Нажмите Win+R и дождитесь появления небольшого окошка со строкой ввода.
- Впишите в нее «cmd».
- Теперь появится окно с черным полем, куда нужно ввести: «sfc/scannow» и нажать «Интер».
- Также можно задать команду «chkdsk».
Подождите, пока не появится сообщение об успешном выполнении операции, а потом перезагрузите ПК.
Проверка на вирусы
Нередко причиной остановки запуска Windows бывают вирусы, которые удаляют файл Ntoskrnl.exe из корневой папки Winnt_root\System32. Не сбрасывайте со счетов такую возможность и обязательно проверьте систему:
- Установите какой-нибудь хороший антивирус: Касперского, «Доктор веб», «Эсет» и т. п.
- Запустите полную проверку всех дисков.
- Дождитесь окончания процедуры (это может занять много времени, можно оставить на ночь).
- Удалите все вредоносные файлы или переместите в карантин – лучше поступить так, как рекомендует антивирус.
- Проверьте файловую систему на ошибки и восстановите все поврежденное, как это было описано выше.
Если вирус занесен какой-то программой, ее необходимо деинсталлировать. Скорее всего, добровольно удаляться она не захочет – тогда вам поможет деинсталлятор (например, Uninstall Tool) и опция «принудительное удаление».
Обновление ОС и драйверов
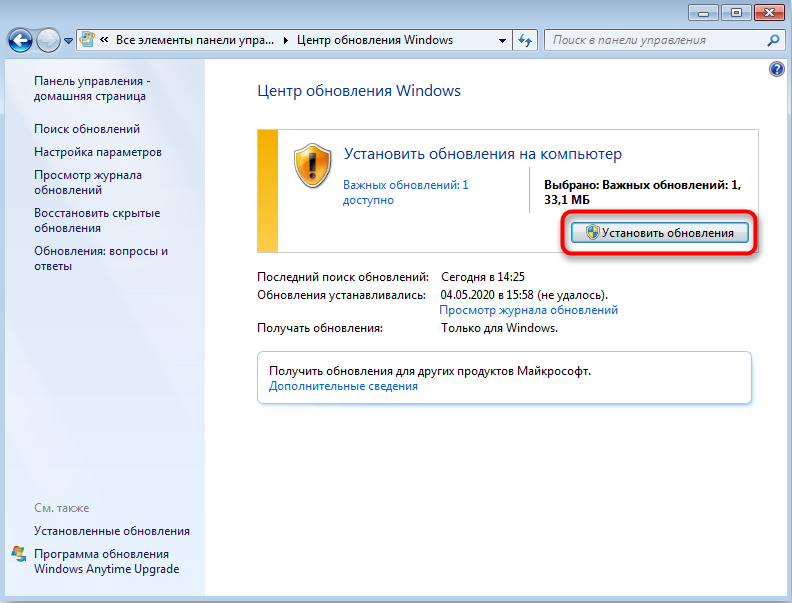
Иногда проблемы с ntoskrnl.exe и синий экран возникают из-за того, что система давно не обновлялась: в Windows 10 сложно отключить автоматическую установку пакетов, но в седьмой версии такое часто происходит – просто зайдите в Update Center и запустите обновления, а для драйверов оборудования скачайте их отдельно (только обращайте внимание на разрядность: x64 или х86 для 64-bit систем). Удалите все драйвера старого, не используемого оборудования: принтеров, графических планшетов, сканеров, МФУ и т.п. («Панель управления» — «Диспетчер устройств» — клик правой кнопкой по устаревшему устройству – команда «Удалить»).
Восстановление системы
И, наконец, если все предыдущие шаги не увенчались успехом, можно восстановить систему до того состояния, когда все нормально работало. Чтобы сделать это, нужно:
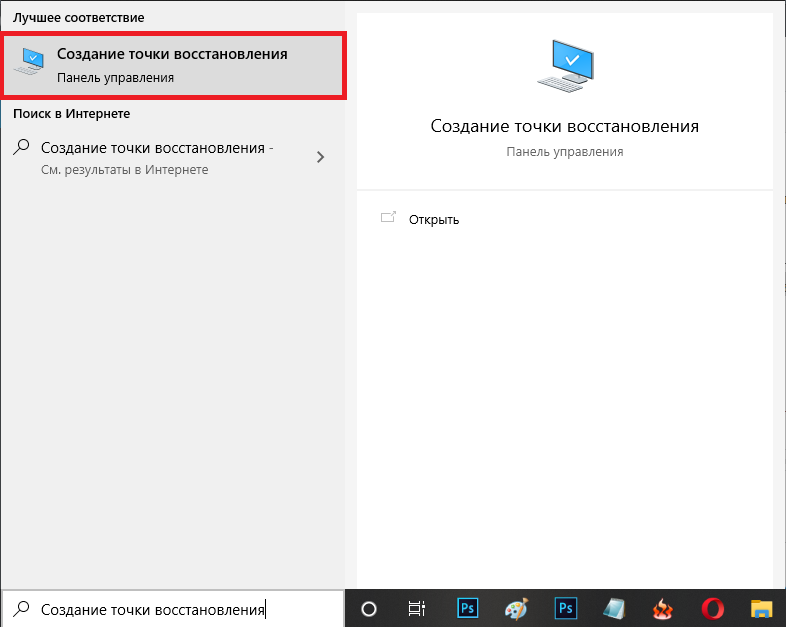
- На Windows 7 последовательно открываем: «Пуск» – «Все программы» – «Стандартные» – «Служебные» – «Восстановление системы», на Windows 10 в «Поиск» наберите «Создание точки восстановления» и откройте соответствующий значок.
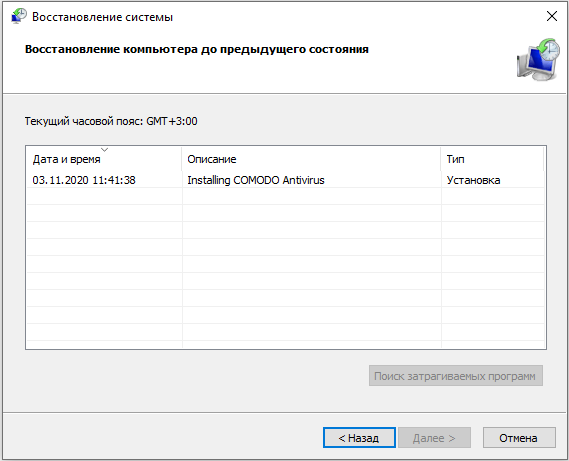
- Нажмите «Далее» в появившемся окне и выбираем «Показать точки восстановления».
- Выберите дату, когда компьютер стабильно работал.
- Нажмите «Готово».
Дождитесь окончания процесса – ни в коем случае не выключайте компьютер из сети и позаботьтесь о том, чтоб у ноутбука не села батарея.
This article is about a computer file that contains a part of Windows kernel, among other things. For the Windows NT kernel itself, see Architecture of Windows NT.
ntoskrnl.exe (short for Windows NT operating system kernel executable), also known as the kernel image, contains the kernel and executive layers of the Microsoft Windows NT kernel, and is responsible for hardware abstraction, process handling, and memory management. In addition to the kernel and executive mentioned earlier, it contains the cache manager, security reference monitor, memory manager, scheduler (Dispatcher), and blue screen of death (the prose and portions of the code).[1]
Overview
Edit
x86 versions of ntoskrnl.exe depend on bootvid.dll, hal.dll and kdcom.dll (x64 variants of ntoskrnl.exe have these dlls embed into the kernel to increase performance). However, it is not a native application. In other words, it is not linked against ntdll.dll. Instead, ntoskrnl.exe containing a standard «start» entry point that calls the architecture-independent kernel initialization function. Because it requires a static copy of the C Runtime objects, the executable is usually about 10 MB in size.
In Windows XP and earlier, the Windows installation source ships four kernel image files to support uniprocessor systems, symmetric multiprocessor (SMP) systems, CPUs with PAE, and CPUs without PAE. Windows setup decides whether the system is uniprocessor or multiprocessor, then, installs both the PAE and non-PAE variants of the kernel image for the decided kind. On a multiprocessor system, Setup installs ntkrnlmp.exe and ntkrpamp.exe but renames them to ntoskrnl.exe and ntkrnlpa.exe respectively.
| Filename | Supports SMP |
Supports PAE |
|---|---|---|
ntoskrnl.exe
|
No | No |
ntkrnlmp.exe
|
Yes | No |
ntkrnlpa.exe
|
No | Yes |
ntkrpamp.exe
|
Yes | Yes |
Starting with Windows Vista, Microsoft began unifying the kernel images as multi-core CPUs took to the market and PAE became mandatory.
Routines in ntoskrnl use prefixes on their names to indicate in which component of ntoskrnl they are defined.
Since not all functions are being exported by the kernel, function prefixes ending in i or p (such as Mi, Obp, Iop) are internal and not supposed to be accessed by the user. These functions contain the core code and implements important checks, such as for vulnerabilities, missing arguments and exception handling.
The following table lists some of them.
| Prefix | Meaning |
|---|---|
Cc |
File system cache[2] |
Cm |
Configuration Manager, the kernel mode side of Windows Registry |
Csr |
Functions used to communicate with the Win32 subsystem process, csrss.exe (csrss stands for client/server runtime sub-system) |
Dbg |
Debugging aid functions, such as a software break point |
Ex |
Windows executive, an «outer layer» of Ntoskrnl.exe |
Exp |
Windows executive private (routines intended for the internal use of Windows Executive) |
FsRtl |
File system runtime library[3] |
Io |
I/O manager[4] |
Iop
|
Internal and base code for the I/O Manager |
Ke |
Core kernel routines[5] |
Ki |
Internal core routines |
Kx |
Interrupt handling, semaphores, spinlocks, multithreading and context switching functions |
Ky
|
Internal and stub functions that generate a trap frame and call Kx-prefixed functions |
Ks |
Kernel streaming |
Kx
|
Internal functions for acquiring spinlock and semaphore implementations |
Ldr |
NT’s PE Executables loader |
Ldrp
|
Internal base code for the PE Loader, usually just PE relocate implementation. |
Lpc |
Local Procedure Call, an internal, undocumented, interprocess or user/kernel message passing mechanism |
Lsa |
Local Security Authority |
Mm |
Memory management |
Mi |
Memory management routines not exported for call outside the memory manager (i = internal) |
Nls |
Nls for Native Language Support (similar to code pages). |
Ob |
Object Manager |
Obp
|
Internal base code for the Object Manager |
Pfx |
Prefix handling |
Po |
Plug-and-play and power management[6] |
Ps |
Process and thread management (task management) |
Psp
|
Internal base code for the Task manager |
Rtl |
Runtime library, i.e., many utility functions that can be used by native applications, yet don’t directly involve kernel support |
Rtlp |
Runtime library private (for internal use only) |
Se |
Security Manager, access token for the Win32 API |
Sep
|
Internal base code for the Security Manager |
Vf |
Driver Verifier |
Vi |
Driver Verifier routines not exported for call outside the driver verifier |
Zw |
Nt or Zw are system calls declared in ntdll.dll and ntoskrnl.exe. When called from ntdll.dll in user mode, these groups are almost exactly the same; they trap into kernel mode and call the equivalent function in ntoskrnl.exe via the SSDT. When calling the functions directly in ntoskrnl.exe (only possible in kernel mode), the Zw variants ensure kernel mode, whereas the Nt variants do not.[7] |
Initialization
Edit
When the kernel receives control, it gets a struct-type pointer from bootloader. The pointer’s destination contains information about the hardware, the path to the Windows Registry file, kernel parameters containing boot preferences or options that change the behavior of the kernel, path of the files loaded by the bootloader (SYSTEM Registry hive, nls for character encoding conversion, and vga font).[8] The definition of this structure can be retrieved by using the kernel debugger or downloading it from the Microsoft symbol database.[9][page needed]
In the x86 architecture, the kernel receives the system already in protected mode, with the GDT, IDT and TSS ready.[further explanation needed] But since it does not know the address of each one, it has to load them one by one to fill the PCR structure.[jargon]
The main entry point of ntoskrnl.exe performs some system dependent initialization then calls a system independent initialization then enters an idle loop.[contradictory]
Interrupt handling
Edit
This article is about NT implementation of interrupt handlers. For other uses, see Interrupt handling.
Modern operating systems use interrupts instead of I/O port polling to wait for information from devices.
In the x86 architecture, interrupts are handled through the Interrupt Dispatch Table (IDT). When a device triggers an interrupt and the interrupt flag (IF) in the FLAGS register is set, the processor’s hardware looks for an interrupt handler in the table entry corresponding to the interrupt number to which in turn has been translated from IRQ by PIC chips, or in more modern hardwares, APIC. Interrupt handlers usually save some subset of the state of registers before handling it and restore them back to their original values when done.
The interrupt table contains handlers for hardware interrupts, software interrupts, and exceptions. For some IA-32 versions of the kernel, one example of such a software interrupt handler (of which there are many) is in its IDT table entry 2E16 (hexadecimal; 46 in decimal), used in assembly language as INT 2EH for system calls. In the real implementation the entry points to an internal subroutine named (as per symbol information published by Microsoft) KiSystemService. For newer versions, different mechanisms making use of SYSENTER instruction and in x86-64 SYSCALL instruction are used instead.
One notable feature of NT’s interrupt handling is that interrupts are usually conditionally masked based on their priority (called «IRQL»), instead of disabling all IRQs via the interrupt flag. This permits various kernel components to carry on critical operations without necessarily blocking services of peripherals and other devices.[10]
Memory manager
Edit
This article is about NT implementation of a memory manager. For other uses, see memory management.
The entire physical memory (RAM) address range is broken into many small blocks also called pages, 4KB in size each, and mapped to virtual addresses. A few of the properties of each block are stored in structures called page table entries, which are managed by the OS and accessed by the processor’s hardware. Page tables are organized into a tree structure, and the physical page number of the top-level table is stored in control register 3 (CR3).
Microsoft Windows divides virtual address space into two regions. The lower part, starting at zero, is instantiated separately for each process and is accessible from both user and kernel mode. Application programs run in processes and supply code that runs in user mode.
The upper part is accessible only from kernel mode, and with some exceptions, is instantiated just once, system-wide. Ntoskrnl.exe is mapped into this region, as are several other kernel mode components. This region also contains data used by kernel mode code, such as the kernel mode heaps and the file system cache.
| Arch | MmHighestUserAddress | MmSystemRangeStart |
|---|---|---|
| x86[a] | 0x7fffffff |
0x80000000
|
| ARM | 0x7fffffff |
0x80000000
|
| x86-64 | 0x000007ff'ffffffff |
0xffff8000'00000000
|
Registry
Edit
Windows Registry is a repository for configuration and settings information for the operating system and for other software, such as applications. It can be thought of as a filesystem optimized for small files.[11] However, it is not accessed through file system-like semantics, but rather through a specialized set of APIs, implemented in kernel mode and exposed to user mode.
The registry is stored on disk as several different files called «hives.» One, the System hive, is loaded early in the boot sequence and provides configuration information required at that time. Additional registry hives, providing software-specific and user-specific data, are loaded during later phases of system initialization and during user login, respectively.
Drivers
Edit
The list of drivers to be loaded from the disk are retrieved from the Services key of the current control set’s key in the SYSTEM registry hive. That key stores device drivers, kernel processes and user processes. They are all collectively called «services» and are all stored mixed on the same place.
During initialization or upon driver load request, the kernel traverses that tree looking for services tagged as kernel services.
See also
Edit
- Architecture of Windows NT
- Windows NT Startup Process
Notes
Edit
- ^ Tunable via
/uservaor/3gbswitch.
References
Edit
- ^ Russinovich, M: Systems Internals Tips and Trivia, SysInternals Information
- ^ Microsoft Corporation (2009). «Cache Manager Routines». Microsoft Corporation. Retrieved 2009-06-13.
- ^ Microsoft Corporation (2009). «File System Runtime Library Routines». Microsoft Corporation. Retrieved 2009-06-13.
- ^ Microsoft Corporation (2009). «I/O Manager Routines». Microsoft Corporation. Retrieved 2009-06-13.
- ^ Microsoft Corporation (2009). «Core Kernel Library Support Routines». Microsoft Corporation. Retrieved 2009-06-13.
- ^ Microsoft Corporation (2009). «Power Manager Routines». Microsoft Corporation. Retrieved 2009-06-13.
- ^ The NT Insider (August 27, 2003). «Nt vs. Zw — Clearing Confusion On The Native API». OSR Online. OSR Open Systems Resources. 10 (4). Retrieved 2013-09-16.
- ^ «struct LOADER_PARAMETER_BLOCK». www.nirsoft.net.
- ^ a b Practical Reverse Engineering Using X86, X64, Arm, Windows Kernel, and Reversing Tools. John Wiley & Sons Inc. 2014. ISBN 978-1118787311.
- ^ CC Hameed (January 22, 2008). «What is IRQL and why is it important? | Ask the Performance Team Blog». Microsoft Corporation. Retrieved 2018-11-11.
- ^ Tanenbaum, Andrew S. (2008). Modern operating systems (3rd ed.). Upper Saddle River, N.J.: Pearson Prentice Hall. p. 829. ISBN 978-0136006633.
Further reading
Edit
- Tanenbaum, Andrew S. (2008). Modern Operating Systems (3rd ed.). Upper Saddle River, N.J.: Pearson Prentice Hall. p. 829. ISBN 978-0136006633.
- Bruce Dang; Alexandre Gazet; Elias Bachaalany (2014). Practical Reverse Engineering: x86, x64, ARM, Windows Kernel, Reversing Tools, and Obfuscation. Wiley. p. 384. ISBN 978-1118787311.
External links
Edit
- Inside the Windows Vista Kernel (TechNet Magazine)
- struct LOADER_PARAMETER_BLOCK
- Driver Development Part 1: Introduction to Drivers

Никогда в Диспетчере задач просто так не завершайте процессы! Дело в том, что в отличии от Windows XP, начиная с Windows 7 некоторые системные процессы настолько важны, что система может тупо вырубится, если вы какой-то не тот процесс завершите, у самого такое было! С тех пор я никогда не завершаю процессы методом тыка
Лично у себя я его нашел в папке C:\Windows\System32 и это нормально, и он у меня точно не вирус (это Windows 10 64 bit версия LTSB), единственное что немного меня удивило — это размер, привык что исполняемые файлы в папке System32 куда меньше, ну да ладно, главное что это не вирус:
В общем как оказывается, это очень важный процесс, который запускается загрузчиком ядра NTLDR в безопасном режиме, хотя это наверно вам не особо интересно.
Самое главное — это ядро Windows, это системный файл, удалять его нельзя и ни в коем случае не завершать его работу!
Бывает такое, что ntoskrnl.exe грузит систему, что в таком случае делать? Главное — не паниковать, тут может быть конфликт с какой-то программой, которую вы ставили недавно. Вспомните что вы устанавливали и удалите, посмотрите, будут ли глюки дальше.
Также была отмечена такая нагрузка при установке виртуальной среды VMWare, а точнее конфликт был с виртуальными сетевыми адаптерами.
Покопавшись в интернете, обнаружил баг, что ntoskrnl.exe грузит систему через процесс System, при этом вешает так что даже печатать невозможно, и что интересно именно в Windows 8.1, в Windows 8 такого не замечено:
Мне стало самому интересно, хотя я у себя на Windows 10 такого бага не замечаю, тем не менее скорее всего сам ntoskrnl.exe не грузит систему, тут может быть файл подкачки активно используется, а к этому может привести например Google Chrome, который любит кушать оперативку.
В общем почитал я, почитал, и пришел к выводу что эти баги Windows 8/8.1 до сих пор так и не устранены (некоторые пользователи проводили тесты и баг появляется даже после чистой установки Windows 8/8.1!), если у вас вдруг такая же Windows стоит и вы уже не знаете что делать, чтобы как-то убрать эти тормоза, то обрадовать мне вас нечем. Скорее всего их не убрать, однако тут есть несколько советов, чтобы уменьшить глюки, хотя потом все равно тормоза вернутся.
Ладно, я надеюсь что вы просто интересовались вопросом ntoskrnl.exe — что это за процесс, а так, все с Windows у вас нормуль
Однако все же если вы думаете, что это у вас может быть вирус — то да, такое действительно может быть, вирусы просто маскируются под системные процессы, чтобы вам было сложнее понять где нормальный процесс, а где вирусняк сидит! В общем вот проверенные временем утилиты, это Dr.Web CureIt!, Kaspersky Virus Removal Tool, Kaspersky Security Scan, они помогут вам если что очистить комп от вирусов!
На главную!
19.04.2016
From Wikipedia, the free encyclopedia
This article is about a computer file that contains a part of Windows kernel, among other things. For the Windows NT kernel itself, see Architecture of Windows NT.
ntoskrnl.exe (short for Windows NT operating system kernel executable), also known as the kernel image, contains the kernel and executive layers of the Microsoft Windows NT kernel, and is responsible for hardware abstraction, process handling, and memory management. In addition to the kernel and executive mentioned earlier, it contains the cache manager, security reference monitor, memory manager, scheduler (Dispatcher), and blue screen of death (the prose and portions of the code).[1]
Overview[edit]
x86 versions of ntoskrnl.exe depend on bootvid.dll, hal.dll and kdcom.dll (x64 variants of ntoskrnl.exe have these dlls embed into the kernel to increase performance). However, it is not a native application. In other words, it is not linked against ntdll.dll. Instead, ntoskrnl.exe containing a standard «start» entry point that calls the architecture-independent kernel initialization function. Because it requires a static copy of the C Runtime objects, the executable is usually about 10 MB in size.
In Windows XP and earlier, the Windows installation source ships four kernel image files to support uniprocessor systems, symmetric multiprocessor (SMP) systems, CPUs with PAE, and CPUs without PAE. Windows setup decides whether the system is uniprocessor or multiprocessor, then, installs both the PAE and non-PAE variants of the kernel image for the decided kind. On a multiprocessor system, Setup installs ntkrnlmp.exe and ntkrpamp.exe but renames them to ntoskrnl.exe and ntkrnlpa.exe respectively.
| Filename | Supports SMP |
Supports PAE |
|---|---|---|
ntoskrnl.exe
|
No | No |
ntkrnlmp.exe
|
Yes | No |
ntkrnlpa.exe
|
No | Yes |
ntkrpamp.exe
|
Yes | Yes |
Starting with Windows Vista, Microsoft began unifying the kernel images as multi-core CPUs took to the market and PAE became mandatory.
Routines in ntoskrnl use prefixes on their names to indicate in which component of ntoskrnl they are defined.
Since not all functions are being exported by the kernel, function prefixes ending in i or p (such as Mi, Obp, Iop) are internal and not supposed to be accessed by the user. These functions contain the core code and implements important checks, such as for vulnerabilities, missing arguments and exception handling.
The following table lists some of them.
| Prefix | Meaning |
|---|---|
Cc |
File system cache[2] |
Cm |
Configuration Manager, the kernel mode side of Windows Registry |
Csr |
Functions used to communicate with the Win32 subsystem process, csrss.exe (csrss stands for client/server runtime sub-system) |
Dbg |
Debugging aid functions, such as a software break point |
Ex |
Windows executive, an «outer layer» of Ntoskrnl.exe |
Exp |
Windows executive private (routines intended for the internal use of Windows Executive) |
FsRtl |
File system runtime library[3] |
Io |
I/O manager[4] |
Iop
|
Internal and base code for the I/O Manager |
Ke |
Core kernel routines[5] |
Ki |
Internal core routines |
Kx |
Interrupt handling, semaphores, spinlocks, multithreading and context switching functions |
Ky
|
Internal and stub functions that generate a trap frame and call Kx-prefixed functions |
Ks |
Kernel streaming |
Kx
|
Internal functions for acquiring spinlock and semaphore implementations |
Ldr |
NT’s PE Executables loader |
Ldrp
|
Internal base code for the PE Loader, usually just PE relocate implementation. |
Lpc |
Local Procedure Call, an internal, undocumented, interprocess or user/kernel message passing mechanism |
Lsa |
Local Security Authority |
Mm |
Memory management |
Mi |
Memory management routines not exported for call outside the memory manager (i = internal) |
Nls |
Nls for Native Language Support (similar to code pages). |
Ob |
Object Manager |
Obp
|
Internal base code for the Object Manager |
Pfx |
Prefix handling |
Po |
Plug-and-play and power management[6] |
Ps |
Process and thread management (task management) |
Psp
|
Internal base code for the Task manager |
Rtl |
Runtime library, i.e., many utility functions that can be used by native applications, yet don’t directly involve kernel support |
Rtlp |
Runtime library private (for internal use only) |
Se |
Security Manager, access token for the Win32 API |
Sep
|
Internal base code for the Security Manager |
Vf |
Driver Verifier |
Vi |
Driver Verifier routines not exported for call outside the driver verifier |
Zw |
Nt or Zw are system calls declared in ntdll.dll and ntoskrnl.exe. When called from ntdll.dll in user mode, these groups are almost exactly the same; they trap into kernel mode and call the equivalent function in ntoskrnl.exe via the SSDT. When calling the functions directly in ntoskrnl.exe (only possible in kernel mode), the Zw variants ensure kernel mode, whereas the Nt variants do not.[7]
|
Initialization[edit]
When the kernel receives control, it gets a struct-type pointer from bootloader. The pointer’s destination contains information about the hardware, the path to the Windows Registry file, kernel parameters containing boot preferences or options that change the behavior of the kernel, path of the files loaded by the bootloader (SYSTEM Registry hive, nls for character encoding conversion, and vga font).[8] The definition of this structure can be retrieved by using the kernel debugger or downloading it from the Microsoft symbol database.[9][page needed]
In the x86 architecture, the kernel receives the system already in protected mode, with the GDT, IDT and TSS ready.[further explanation needed] But since it does not know the address of each one, it has to load them one by one to fill the PCR structure.[jargon]
The main entry point of ntoskrnl.exe performs some system dependent initialization then calls a system independent initialization then enters an idle loop.[contradictory]
Interrupt handling[edit]
This article is about NT implementation of interrupt handlers. For other uses, see Interrupt handling.
Modern operating systems use interrupts instead of I/O port polling to wait for information from devices.
In the x86 architecture, interrupts are handled through the Interrupt Dispatch Table (IDT). When a device triggers an interrupt and the interrupt flag (IF) in the FLAGS register is set, the processor’s hardware looks for an interrupt handler in the table entry corresponding to the interrupt number to which in turn has been translated from IRQ by PIC chips, or in more modern hardwares, APIC. Interrupt handlers usually save some subset of the state of registers before handling it and restore them back to their original values when done.
The interrupt table contains handlers for hardware interrupts, software interrupts, and exceptions. For some IA-32 versions of the kernel, one example of such a software interrupt handler (of which there are many) is in its IDT table entry 2E16 (hexadecimal; 46 in decimal), used in assembly language as INT 2EH for system calls. In the real implementation the entry points to an internal subroutine named (as per symbol information published by Microsoft) KiSystemService. For newer versions, different mechanisms making use of SYSENTER instruction and in x86-64 SYSCALL instruction are used instead.
One notable feature of NT’s interrupt handling is that interrupts are usually conditionally masked based on their priority (called «IRQL»), instead of disabling all IRQs via the interrupt flag. This permits various kernel components to carry on critical operations without necessarily blocking services of peripherals and other devices.[10]
Memory manager[edit]
This article is about NT implementation of a memory manager. For other uses, see memory management.
The entire physical memory (RAM) address range is broken into many small blocks also called pages, 4KB in size each, and mapped to virtual addresses. A few of the properties of each block are stored in structures called page table entries, which are managed by the OS and accessed by the processor’s hardware. Page tables are organized into a tree structure, and the physical page number of the top-level table is stored in control register 3 (CR3).
Microsoft Windows divides virtual address space into two regions. The lower part, starting at zero, is instantiated separately for each process and is accessible from both user and kernel mode. Application programs run in processes and supply code that runs in user mode.
The upper part is accessible only from kernel mode, and with some exceptions, is instantiated just once, system-wide. Ntoskrnl.exe is mapped into this region, as are several other kernel mode components. This region also contains data used by kernel mode code, such as the kernel mode heaps and the file system cache.
| Arch | MmHighestUserAddress | MmSystemRangeStart |
|---|---|---|
| x86[a] | 0x7fffffff |
0x80000000
|
| ARM | 0x7fffffff |
0x80000000
|
| x86-64 | 0x000007ff'ffffffff |
0xffff8000'00000000
|
Registry[edit]
Windows Registry is a repository for configuration and settings information for the operating system and for other software, such as applications. It can be thought of as a filesystem optimized for small files.[11] However, it is not accessed through file system-like semantics, but rather through a specialized set of APIs, implemented in kernel mode and exposed to user mode.
The registry is stored on disk as several different files called «hives.» One, the System hive, is loaded early in the boot sequence and provides configuration information required at that time. Additional registry hives, providing software-specific and user-specific data, are loaded during later phases of system initialization and during user login, respectively.
Drivers[edit]
The list of drivers to be loaded from the disk are retrieved from the Services key of the current control set’s key in the SYSTEM registry hive. That key stores device drivers, kernel processes and user processes. They are all collectively called «services» and are all stored mixed on the same place.
During initialization or upon driver load request, the kernel traverses that tree looking for services tagged as kernel services.
See also[edit]
- Architecture of Windows NT
- Windows NT Startup Process
Notes[edit]
- ^ Tunable via
/uservaor/3gbswitch.
References[edit]
- ^ Russinovich, M: Systems Internals Tips and Trivia, SysInternals Information
- ^ Microsoft Corporation (2009). «Cache Manager Routines». Microsoft Corporation. Retrieved 2009-06-13.
- ^ Microsoft Corporation (2009). «File System Runtime Library Routines». Microsoft Corporation. Retrieved 2009-06-13.
- ^ Microsoft Corporation (2009). «I/O Manager Routines». Microsoft Corporation. Retrieved 2009-06-13.
- ^ Microsoft Corporation (2009). «Core Kernel Library Support Routines». Microsoft Corporation. Retrieved 2009-06-13.
- ^ Microsoft Corporation (2009). «Power Manager Routines». Microsoft Corporation. Retrieved 2009-06-13.
- ^ The NT Insider (August 27, 2003). «Nt vs. Zw — Clearing Confusion On The Native API». OSR Online. OSR Open Systems Resources. 10 (4). Retrieved 2013-09-16.
- ^ «struct LOADER_PARAMETER_BLOCK». www.nirsoft.net.
- ^ a b Practical Reverse Engineering Using X86, X64, Arm, Windows Kernel, and Reversing Tools. John Wiley & Sons Inc. 2014. ISBN 978-1118787311.
- ^ CC Hameed (January 22, 2008). «What is IRQL and why is it important? | Ask the Performance Team Blog». Microsoft Corporation. Retrieved 2018-11-11.
- ^ Tanenbaum, Andrew S. (2008). Modern operating systems (3rd ed.). Upper Saddle River, N.J.: Pearson Prentice Hall. p. 829. ISBN 978-0136006633.
Further reading[edit]
- Tanenbaum, Andrew S. (2008). Modern Operating Systems (3rd ed.). Upper Saddle River, N.J.: Pearson Prentice Hall. p. 829. ISBN 978-0136006633.
- Bruce Dang; Alexandre Gazet; Elias Bachaalany (2014). Practical Reverse Engineering: x86, x64, ARM, Windows Kernel, Reversing Tools, and Obfuscation. Wiley. p. 384. ISBN 978-1118787311.
External links[edit]
- Inside the Windows Vista Kernel (TechNet Magazine)
- struct LOADER_PARAMETER_BLOCK
- Driver Development Part 1: Introduction to Drivers
The ntoskrnl.exe is a kernel image of the Windows operating system which is responsible for numerous system services such as process, memory management, and hardware virtualization. The cache manager, executive, kernel, security reference monitor, and scheduler are all part of the ntoskernel.exe.
The default driver in Windows rarely causes a ntoskrnl.exe BSOD (Blue Screen of Death). However, if a custom, overclocked or obsolete driver corrupts the memory unit used by ntoskrnl.exe, the OS will blame it and display a BSOD to prevent the computer from further damage.
So, if we get any errors related to ntoskernel.exe, our first priority should be to check our memory module and uninstall any third-party driver.
Note: The ntoskrnl.exe file is located in C:\Windows\System32.
Table of Contents
What Causes ntoskrnl.exe BSOD?
We have listed a few reasons your computer runs into ntoskrnl.exe Blue Screen of Death Error.
- Faulty memory modules
- Outdated driver
- Overclocked memory
- XMP (Extreme Memory Profile) enabled
Why Does ntoskrnl.exe Take a Lot of Memory?
The OS uses ntoskrnl.exe for any process that requires disk activity. Also, when communicating with devices and drivers, ntoskrnl.exe uses RAM to store the data.
Therefore, if we have a corrupted driver, there may be a memory management issue, consuming a high memory.
All ntoskrnl.exe BSOD Errors
The computer might run into many ntoskrnl.exe Blue Screen of Death errors. Although most of them are related to issues with memory management and driver problems, some errors may be caused by other factors.
- driver_irql_not_less_or_equal ntoskrnl.exe
- system_service_exception ntoskrnl.exe
- irql_not_less_or_equal ntoskrnl.exe
- page_fault_in_nonpaged_area ntoskrnl.exe
- memory_management ntoskrnl.exe
- kmode_exception_not_handled ntoskrnl.exe
- unexpected_kernel_mode_trap ntoskrnl.exe
- Critical_process_died ntoskrnl.exe
- apc_index_mismatch ntoskrnl.exe
- ntoskrnl.exe missing or corrupt
- bad_pool_header ntoskrnl.exe
How to Fix ntoskrnl.exe Blue Screen of Death in Windows
Here is a list of solution that you can try to fix any issue with ntoskrnl.exe BSOD.
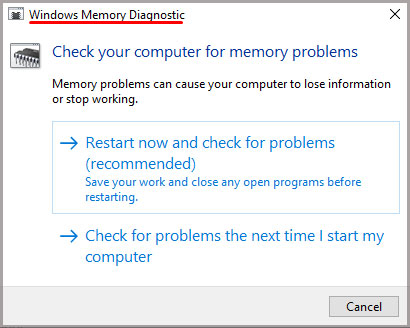
Run Windows Memory Diagnostic Tool
The Windows Diagnostic tool in Windows checks the memory modules for any fault. So, if your computer suffers from a constant Blue Screen of Death, you can run the Windows Memory Diagnostic Tool to find out any errors in your RAM sticks.
Follow these steps to start the Windows Memory Diagnostic Tool.
- Press the Windows key + R.
- Type “
mdsched.exe” and press Enter. - Click Restart now and check for problems (recommended).
Once the computer restarts, the system will run the Windows Memory Diagnostic. During the diagnostic process, the computer will show you the detailed report of your memory module. However, you can also use the Event Viewer feature to view the Windows log folder.
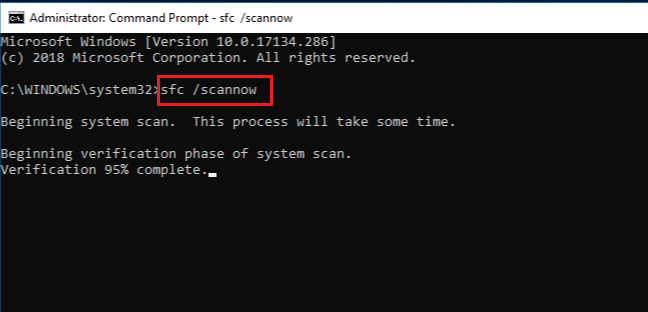
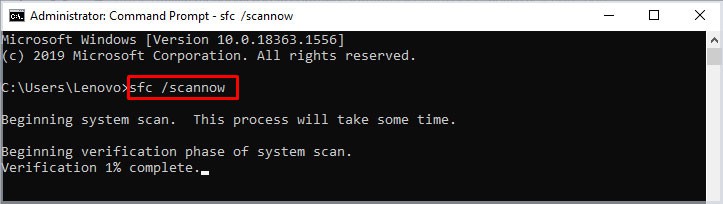
Run SFC and DISM Command
The System File Checker (SFC) is a command which allows you to repair any corrupted system files. If the computer gets the ntoskrnl.exe BSOD with a corrupted Windows NT OS Kernel file, the SFC command will correct them.
Follow these steps to run the System File Checker command.
- Press the Windows key + R.
- Type “cmd” without the quotation mark and press Ctrl + Shift + Enter to run Command Prompt as an administrator.
- In command, type
sfc /scannowand press Enter. - The SFC feature will check for any corrupted Windows system files and repair them.
Note: System files are those files located inside System32.
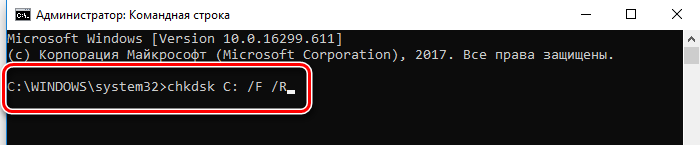
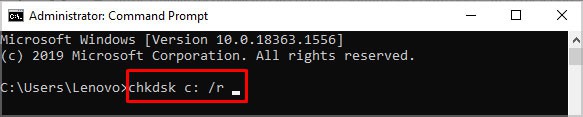
If the SFC report says it could not fix some issues, the chkdsk command may resolve the issue. Follow these steps to run the chkdsk command
- Run Command Prompt as administrator.
- Type “
chkdsk C: /r” without the quotation mark and press Enter. - Press Y if the command asks again for permission.
- Once the process is complete, restart the computer and run SFC again.
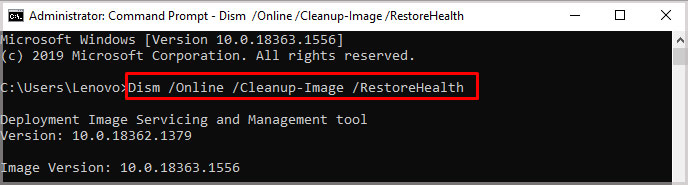
Once we run the SFC command, we need to run the DISM (Deployment Image Servicing and Management) command to manage both Windows Online and Offline Images. Follow these steps to run the DISM command.
- Run Command Prompt as administrator.
- Type the following Command:
DISM.exe /Online /Cleanup-Image /Restorehealth - This command performs a cleanup and recovery operation on corrupted system Files.
Once you complete both SFC and DISM operations, restart your computer.
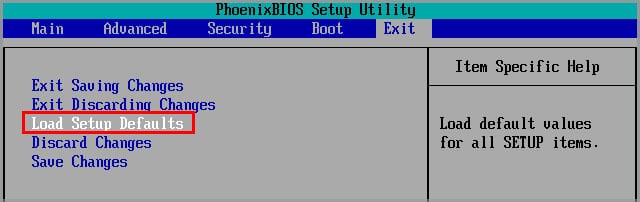
Revert Overclocked Hardware
Overclocked computer components are also known to cause ntoskrnl.exe Blue Screen of Death error. If a computer has overclocked RAM and it constantly turns off due to the BSOD, it is best to reset the BIOS settings. Therefore, resetting the BIOS setting will revert all overclocked devices to normal speed.
Follow these steps to reset your BIOS.
- Enter the BIOS of your motherboard.
- Search for an option like Load Setup Defaults (depends on motherboard manufacturer).
- Press Enter and Save Changes.
Once the changes are saved, the computer will restart.
Uninstall Third-Party Drivers
The computer may also get the ntoskrnl.exe BSOD due to unofficial drivers. If these drivers use the memory address allocated to ntoskrnl.exe, the OS forces the computer to the Blue Screen of Death to prevent any memory issue.
Try uninstalling any third-party drivers or recently installed applications to fix this issue.
Restore the Registry
Before starting this solution, this process requires a backup of the Windows Registry before the computer gets constant BSOD. You can skip this process if you do not have the backup file.
The registry contains the data of Windows information and settings. Therefore, if a computer starts to turn off randomly (or malfunction), we can use the backup of the registry to roll back the Windows settings. So, it is always recommended to make a backup of the Windows Registry every month.
Follow these steps to restore the registry.
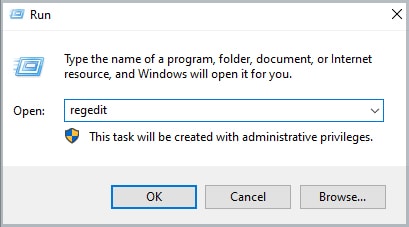
- Press the Windows + R key.
- Type “regedit” without the quotation mark.
- The Registry Editor dialog box will open.
- Go to Files > Import.
- Here, Browse the backup of your Registry.
- Click Open and restart the computer.
Fix the Issue With Android Emulators
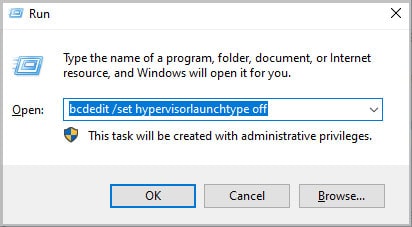
If you run an emulator software, you may get the ntoskrnl.exe BSOD error. Most android emulators require a Virtual Machine (VM) to give users a better gaming experience. However, Microsoft’s virtual machine can cause some memory issues when running the android emulator.
Therefore, we either need to uninstall the emulator app or disable and restart Microsoft’s Virtual Machine to fix the ntoskrnel.exe BSOD issue.
To disable Microsoft’s VM, run the command as administrator and run the following command:
bcdedit /set hypervisorlaunchtype off
If this does not fix the issue, then uninstall the emulator.
Update Drivers
As we discussed, most of the ntoskrnl.exe BSOD error arises due to driver issues. Therefore, it is only ideal to update your drivers to fix this issue. However, some drivers like the Realtek Audio Drivers are known to cause the BSOD due to some unknown issues.
To update your driver, Press the Windows + X key and click on Device Manager. Here, expand the list. Right-click the driver you want to update and click on Update. Now, Click on Search automatically for drivers.
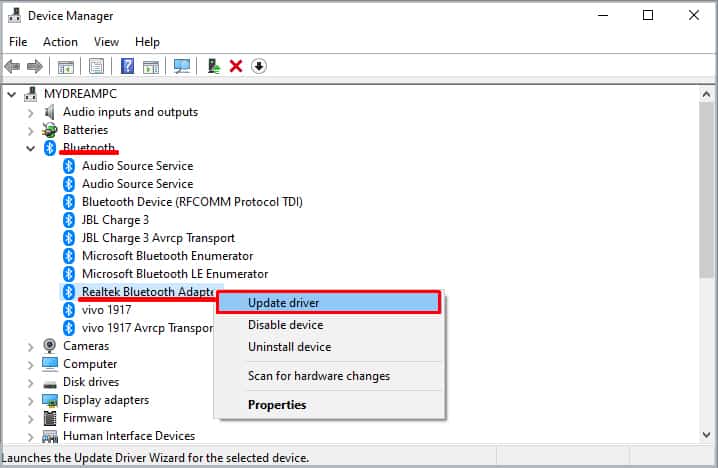
Once the update is complete, click on close.
You can also update all your drivers at once using the Windows Update feature. Go to Settings > Windows Update (Security & update > Windows Update for Windows 10). Click on Check for Updates.
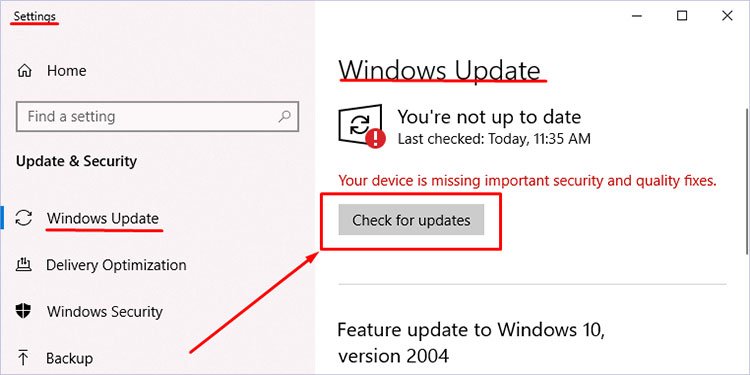
Once the download is complete, restart your computer to install the updates.
Note: Whether or not the Realtek Audio Drivers cause BSOD, it is ideal to uninstall and reinstall this driver.
Remove Faulty Memory Modules
A faulty RAM stick is the most common reason for a Blue Screen of Death. However, in this case, memory leak or poor memory management may also cause the Blue Screen of Death. Whatever may be the reason, we cannot rule out the fact that the memory module is faulty.
If the computer is running on dual memory, take one out of the slot to check if the computer still suffers from BSOD. If it does not, then the memory you just took out is the faulty one, causing your computer to crash constantly. Repeat this process for both memory sticks.
However, if you are running on a single memory stick, try using another RAM stick.
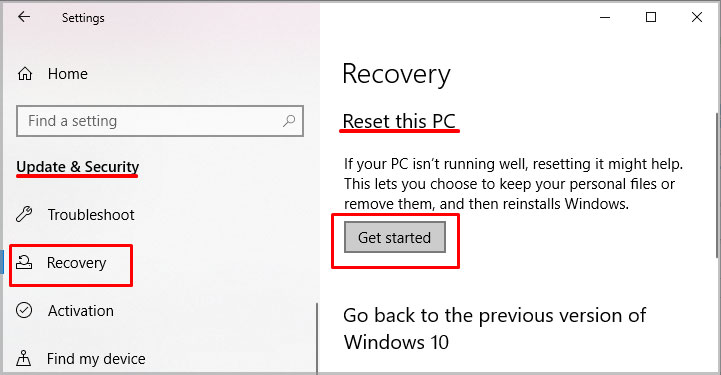
Reset Windows
If none of the above solutions fix the BSOD, we can try resetting the OS. Resetting the Windows can fix the BSOD errors like ntoskrnl.exe missing or corrupt as it will reinstall everything, including the system files.
Follow these steps to reset Windows.
- Click on the Start menu.
- Go to Settings > System > Recovery.
- Click on Reset this PC.
- The Windows will ask you a series of questions like whether to keep files or remove everything. Choose according to your will.
- The reset will take a few minutes to complete.
Once the computer starts, the computer should be free from the constant shutdown.
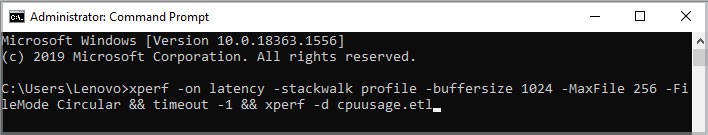
Using Windows Performance Tool-kit
In order to use this, you need to have installed Windows ADK, which can be downloaded from official Microsoft’s website.
- Open Run and type in “CMD.” Then press Ctrl + Shift + Enter to start command prompt with administrator privileges.
- Paste the following command in the prompt:
xperf -on latency -stackwalk profile -buffersize 1024 -MaxFile 256 -FileMode Circular && timeout -1 && xperf -d cpuusage.etl - The code will run for 60 seconds and revert to default directory.
- A log file named
cpuusage.etlwill have been created in C:\Windows\system32. - From this diagnostic file, details regarding the files and application causing the memory dump can be identified. Once the process has been identified, you can proceed to terminate or uninstall the application as required.
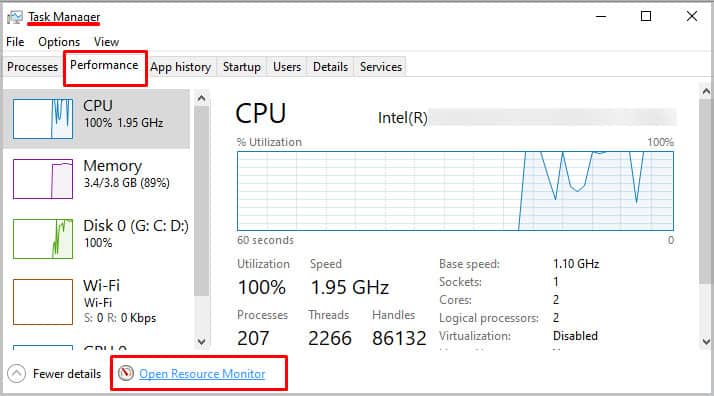
Resource Monitor Utility
The resource monitor utility is a crucial feature in Windows OS that lists CPU, disk, network and memory usage of all the process that are running. Using this feature, we can check if the ntoskrnl.exe file is performing smoothly.
Follow these steps to view Resource Monitor Utility.
- Press Ctrl + Alt + Del Key simultaneously.
- Select Task Manager and go to Performance tab.
- Now, click on Open Resource Monitor to open the Resource Monitor dialog box.
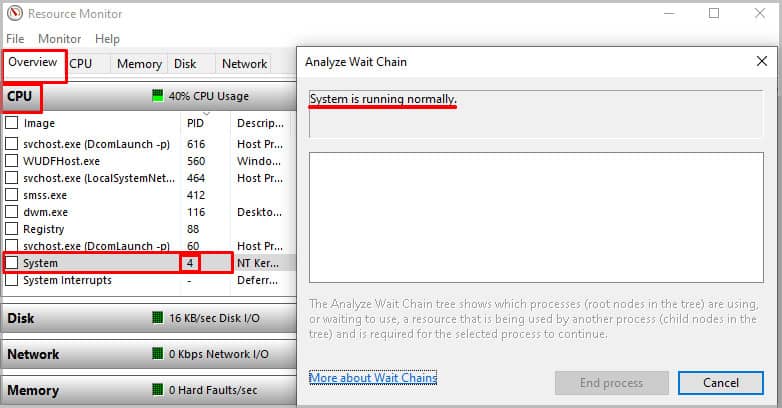
- On Overview tab, Under CPU, you can see all the process and their details. Here, click on PID (Process ID) until all process are displayed in ascending order.
- Locate The Process ID 4 which is the PID of ntoskrnl.exe and will be indicated as System under Image.
- Right-click on System and click on Analyze Wait Chain…. It must read System is running normally.
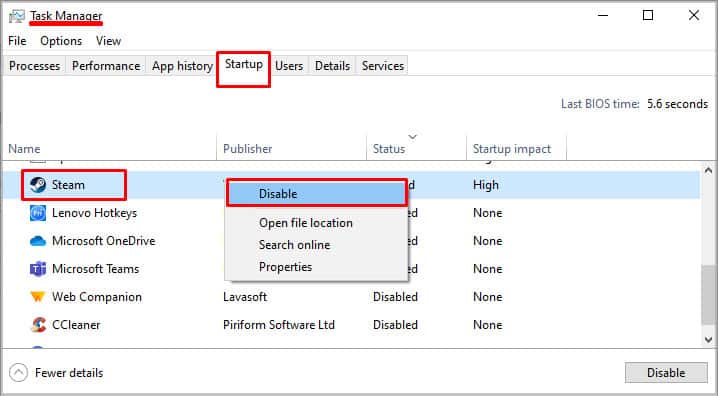
Disable Startup Process
Some application process may run automatically when the computer starts. If these startup application, for unknown reason, uses the same memory address causing a conflict. This will result in a ntoskrnl.exe Blue Screen of Death.
Therefore, we need to disable any unnecessary startup process from the task manager. To disable start up process, follow these steps.
- Press Ctrl + Alt + Del key.
- Click on Task Manager. Then, click on More details.
- Here, you will see all the process running in the background.
- Click on the Startup tab.
- Right-click on any process that you do not need during startup and select Disable.
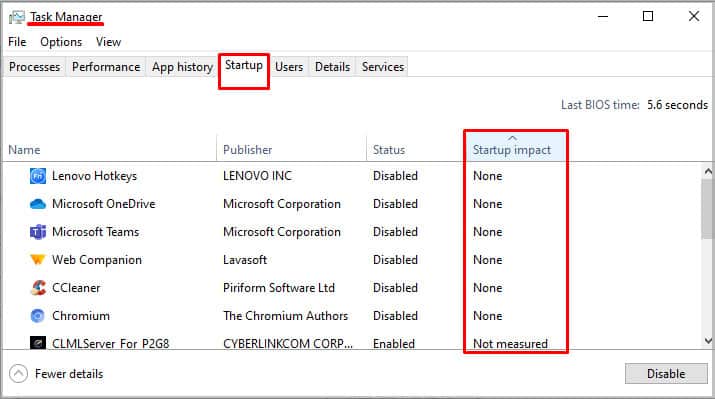
- It is recommended to check the Startup impact as well. Remove any process from startup with Startup impact Low or None.
Malware Issue
Malicious software and virus can attack the system files on our computer. This may cause a system file to corrupt or the computer may not detect them at all. When a computer does not detect a system files (files inside System32), it cannot function. This will result in constant Blue Screen of Death.
You can also look for the process in task manager. If the PID of the process consuming your CPU is 4, the process is authentic and belongs to the OS. But, if the PID is something different than it can be assured that the process has been infected by malware and causing the crash.
Use Antivirus software to detect and remove any malicious software and virus from your computer.
How to Reinstall ntoskrnl.exe File?
The computer will not boot if it does not find the ntoskrnl.exe file. Therefore, there is no way you can reinstall the file as the computer will not boot at all. We can only solve a ntoskrnl.exe file missing issue by reinstalling the OS itself.
Reinstalling the OS from scratch will install all its system files, including the Windows NT Operating System Kernel file.