When you startup a Windows NT, 2000 or XP based machine (which are all based on a similar set of code), the computer is loading and juggling many files in order to load the operating system. This is a basic breakdown of the NT/2000/XP startup process which comes in handy for troubleshooting startup problems.
The following files are loaded during the Windows NT/2000/XP startup process:
- Ntldr
- Boot.ini
- Bootsect.dos (for mutlibooting systems only)
- Ntbootdd.sys (loaded only if SCSI drives exist)
- Ntdetect.com
- Ntoskrnl.exe
- Hal.dll
- The Registry files in systemroot\System32\Config
- The Driver files in systemroot\System32\Drivers
The first part that is loaded is the Ntldr (NT Loader) which is started by the active partitions boot sector. It then changes the processor into protected mode, starts the file system and reads the contents of the boot.ini file. The boot.ini file determines startup options and the boot menu selections such as when you dual boot multiple OS’s.
If you are dual booting and you choose a non NT/2000/XP operation system (ie. Linux) then Bootsect.dos is loaded. If you are running any SCSI devices Ntbootdd.sys is loaded which contains the SCSI boot drivers.
Ntdetect.com gathers data regarding the current hardware configuration and passes this information to Ntldr. If your BIOS is ACPI compliant, Windows will use ACPI to initialize the devices. If the computer has multiple hardware profiles then Windows chooses the correct one based on the current hardware configuration.
The Windows kernel loads. Ntldr passes the information that was collected by Ntdetect.com to Ntoskrnl.exe. Ntoskrnl.exe then loads Windows kernel. Hal.dll (Hardware Extraction Layer) and the systems registry information. An indicator on the bottom of the screen (typically a green bar in XP) indicates the progress of this step.
The Windows drivers load and the user logs on. Networking components load such as TCP/IP along with other services and the Windows logon screen appears. After Windows loads successfully, Windows updates the “Last Known Good Configuration†option which you see when you press F8 during bootup to reflect the current configuration state.
Plug and Play detects and configures new devices found on the PC. If Windows finds new devices they are assigned system resources, Windows extracts the necessary drivers from a file called Driver.cab. If the correct driver file is not found in the Driver.cab archive then the user is prompted to provide them. This step occurs simultaneously with the Windows logon process.
In the event that your Windows computer does fail during bootup, you can press F8 on the screen just before the loading screen appears and choose “Enable Boot Logging†which will create a file called Ntbtlog.txt. This file will record all the events during bootup which can help you determine which part is not loading correctly.
Boot
sequence for Windows NT, 2000, XP and 2003:
BIOS: performs
Power On Self Test (POST)
BIOS: loads
MBR from the boot device specified/selected by the BIOS
MBR: contains
a small amount of code that reads the partition table, the first partition
marked as active is determined to be the system volume
MBR: loads
the boot sector from the system volume
BOOT
SECTOR: reads the root directory of the system volume at loads
NTLDR
NTLDR: reads
BOOT.INI from the system volume to determine the boot drive (presenting a menu
if more than 1 entry is defined)
NTLDR: loads
and executes NTDETECT.COM from the system volume to perform BIOS hardware
detection
NTLDR: loads
NTOSKRNL.EXE, HAL.DLL, BOOTVID.DLL (and KDCOM.DLL for XP upwards) from the boot
(Windows) volume
NTLDR: loads
\WINDOWS\SYSTEM32\CONFIG\SYSTEM which becomes the system hive
HKEY_LOCAL_MACHINE\System
NTLDR: loads
drivers flagged as “boot” defined in the system hive, then passes control to
NTOSKRNL.EXE
NTOSKRNL.EXE: brings
up the loading splash screen and initializes the kernel subsystem
NTOSKRNL.EXE: starts
the boot-start drivers and then loads & starts the system-start drivers
NTOSKRNL.EXE: creates
the Session Manager process (SMSS.EXE)
SMSS.EXE: runs
any programs specified in BootExecute (e.g. AUTOCHK, the native API version of
CHKDSK)
SMSS.EXE: processes
any delayed move/rename operations from hotfixes/service packs replacing in-use
system files
SMSS.EXE: initializes
the paging file(s) and the remaining registry hives
** before this step completes,
bugchecks will not result in a memory dump as we need a working page file on
the boot (Windows) volume **
SMSS.EXE: starts
the kernel-mode portion of the Win32 subsystem (WIN32K.SYS)
SMSS.EXE:
starts the user-mode portion of the Win32 subsystem (CSRSS.EXE)
SMSS.EXE: starts
WINLOGON.EXE
WINLOGON.EXE: starts
the Local Security Authority (LSASS.EXE)
WINLOGON.EXE: loads
the Graphical User Identification and Authentication DLL (MSGINA.DLL by
default)
WINLOGON.EXE: displays
the logon window
WINLOGON.EXE: starts
the services controller (SERVICES.EXE)
** at this point users can
logon **
SERVICES.EXE: starts
all services markes as automatic
———
NOTES:
The SYSTEM volume
is the partition from which the boot process starts, containing the MBR, boot
sector, NTLDR, NTDETECT.COM & BOOT.INI
The BOOT volume is
the partition which contains the Windows folder – this can be a logical
partition
Процесс запуска Windows NT — это процесс инициализации операционных систем Microsoft Windows NT, Windows 2000, Windows XP и Windows Server 2003. В Windows Vista процесс сильно изменён.
Фаза начальной загрузки[]
Шаблон:Details
Фаза начальной загрузки различается в зависимости от аппаратной платформы. Начиная с ранней фазы, не привязанной к ОС, началом процесса загрузки считается:
- Для x86 или x64: когда код сектора загрузочного раздела исполняется в реальном режиме и загружает NTLDR
- Для IA-64: когда исполняется программа IA64ldr.efi EFI (позднее называемая просто как IA64ldr)
От данной точки процесс загрузки продолжает выполнять следующее:
Файл NTLDR, размещенный в корневой папке загрузочного диска, состоит из двух частей. Первая — это модуль StartUp, после которого следует загрузчик ОС (osloader.exe), обе части хранятся в файле NTLDR. При загрузке NTLDR в память управление передается модулю StartUp, при этом центральный процессор работает в реальном режиме. Основная задача StartUp — перевод процессора в защищённый режим, что позволяет использовать 32-разрядную адресацию памяти, а также создать таблицу дескрипторов прерываний, таблицу глобальных дескрипторов, таблицу страниц и включение страничной работы с памятью. Это делается с использованием возможностей основного операционного окружения, на котором установлена операционная система. Затем модуль StartUp загружает и запускает загрузчик ОС.
Загрузчик ОС в NTLDR содержит основные функции для доступа к дискам IDE, отформатированным в файловых системах NTFS, FAT, CDFS (ISO 9660), ETFS или UDFS в новейших версиях операционных систем. Доступ к дискам производится через BIOS посредством встроенной программы ARC на системах с ARC или посредством сети, используя протокол TFTP. Помимо этой точки, все вызовы к BIOS проходят через виртуальный режим 8086, так как из защищённого режима невозможен прямой доступ к BIOS. Если загрузочный диск является SCSI и SCSI-контроллер не использует 13-ое прерывание реального режима, то для получения доступа к диску загружается дополнительный файл Ntbootdd.sys. Он является копией того же драйвера miniport для SCSI, который используется, когда запускается Windows.
Затем загрузчик считывает содержимое файла boot.ini для обнаружения информации о системном томе. Если такой файл отсутствует, то загрузчик пытается обнаружить информацию из стандартного установочного каталога. Для машин под Windows NT это каталог C:\WINNT. Для машин под Windows XP и 2003 загружается из C:\WINDOWS.
В этом месте экран очищается и в Windows 2000 и поздних версиях NTLDR и IA64ldr, которые поддерживают гибернацию системы, корневой каталог тома по умолчанию определён в boot.ini для поиска файла гибернации hiberfil.sys. Если этот файл найден и активная память работает, содержимое файла (который совпадает по размеру с физической памятью в машине) загружается в память и передаёт управление в ядро Windows с точки, с которой гибернация была восстановлена. После этого файл сразу же помечается как неактивный, так что повреждение или другие сбои не могут вызвать это (уже устаревшее) состояние памяти в виде повторной загрузки. Если возвращение состояния не удалось, то в следующий раз NTLDR спросит пользователя, надо ли снова пытаться восстанавливать или отменить обработку файла и произвести обычную загрузку.
Если boot.ini содержит запись более чем об одной операционной системе, то пользователю показывается меню загрузки, позволяющее выбрать, какую именно из операционных систем загружать. Если выбрана операционная система, не основанная на NT, подобно Windows 98, то NTLDR загружает соответствующий файл загрузочного сектора, указанный в списке в boot.ini (по умолчанию это bootsect.dos, если не задано иное имя файла) и контроль над выполнением переходит к нему. Если выбрана операционная система, основанная на NT, NTLDR запускает ntdetect.com, который собирает основную информацию об аппаратном обеспечении компьютера, сообщаемую BIOS‘ом.
В этой точке процесса загрузки NTLDR очищает экран и выводит псевдографический индикатор состояния (который часто не виден под системами XP или 2003 из-за их скорости инициализации); Windows 2000 также показывает текст «Starting Windows…». Если во время этой фазы пользователь нажмёт F8, то показывается расширенное меню загрузки, содержащее различные специальные режимы загрузки, включающие в себя безопасный режим с конфигурацией последней успешной загрузки, с включением отладки и (в случае серверных редакций) режим восстановления служб Директорий.
Загрузка продолжается, как только выбирается один из пунктов или если повторно нажимается F8.
Фаза загрузки ядра[]
- ntoskrnl.exe (ядро)
- hal.dll (тип абстрактного уровня аппаратного обеспечения)
- kdcom.dll (библиотека расширения ядра отладчика аппаратного обеспечения)
- bootvid.dll (для логотипа Windows и индикатора статуса загрузки)
- config\system — реестр
- HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\BootExecute
- процессы служб в порядке готовности
- *HKLM\SYSTEM\CurrentControlSet\Control\ServiceGroupOrder
Инициализация подсистемы ядра и подсистемы выполнения Windows делается за две фазы.
Во время первой фазы создаются базовые внутренние структуры памяти и инициализируется контроллер прерываний каждого процессора. Инициализируется менеджер памяти, создаются области для файлового кэша системы, страничных и нестраничных опросов памяти. Менеджер объектов[1] инициализирует токен безопасности для назначения первому процессу системы и менеджер процессов инициализирует сам себя. В этой точке также как системный процесс создаётся System Idle Process.
Второй этап предполагает инициализацию драйверов устройств, которые были определены NTLDR как системные драйверы.
Во время процесса загрузки драйверов устройств в нижней части экрана систем под Windows 2000 виден индикатор статуса; в Windows XP и Windows Server 2003 это было заменено анимированной полоской, которая не отражает реального времени процедуры. До Windows 2000 эта часть процесса загрузки занимала значительно больше времени, потому что драйверы инициализировались последовательно по одному. В Windows XP и Windows Server 2003 все драйверы инициализируются асинхронно.
См. также[]
- Архитектура Windows NT
- NTLDR
- Начальная загрузка компьютера
- Процесс загрузки Windows (Windows startup process)
- Процесс загрузки Vista (Windows Vista startup process)
- Процесс загрузки Linux
- Загрузчик операционной системы
- Мультизагрузка
- Главная загрузочная запись
- POST (аппаратное обеспечение)
- BootVis
Примечания[]
- ↑ Windows, NT Object Manager
Ссылки[]
- Шаблон:Cite book
- Troubleshooting the Startup Process. Windows XP Resource Kit. Microsoft Technet. Проверено 15 февраля 2006. Архивировано из первоисточника 3 апреля 2012.
- Mark Minasi, John Enck. Troubleshooting NT Boot Failures. Administrator’s Survival Guide: System Management and Security. Windows IT Library. Проверено 15 февраля 2006. Архивировано из первоисточника 3 апреля 2012.
- Microsoft KB Article 244036 on remote installation & booting
- Definition of the RunOnce Keys
- boot.ini switches
- Startup Applications List
- Troubleshooting Windows XP Startup Process
- AnVir Task Manager — утилита для анализа и редактирования программ автозагрузки Windows
| |
|
|---|---|
| Основные |
Aero • |
| Службы управления |
Архивация и восстановление • |
| Приложения |
Контакты • |
| Игры |
Chess Titans • |
| Ядро ОС |
Ntoskrnl.exe • |
| Службы |
Autorun.inf • |
| Файловые системы |
ReFS • |
| Сервер |
Active Directory • |
| Архитектура |
NT • |
| Безопасность |
BitLocker • |
| Совместимость |
Подсистема UNIX (Interix) • |
The booting process of Windows NT is the process run to start Windows NT. The process has been changed between releases, with the biggest changes being made with Windows Vista. In versions before Vista, the booting process begins when the BIOS loads the Windows NT bootloader, NTLDR. Starting with Vista, the booting process begins with either the BIOS or UEFI load the Windows Boot Manager, which replaces NTLDR as the bootloader. Next, the bootloader starts the kernel, which starts the session manager, which begins the login process. Once the user is logged in, File Explorer, the graphical user interface used by Windows NT, is started.
History[edit]
Windows Vista introduces a complete overhaul of the Windows operating system loader architecture.[1][2] The earliest known reference to this revised architecture is included within PowerPoint slides distributed by Microsoft during the Windows Hardware Engineering Conference of 2004 when the operating system was codenamed «Longhorn». This documentation mentions that the Windows operating system loader would be undergoing a significant restructuring in order to support EFI and to «do some major overhaul of legacy code».[3] The new boot architecture completely replaces the NTLDR architecture used in previous versions of Windows NT.[2]
Most of the steps that follow the NT kernel being loaded, including kernel initialization and user-space initialization, are kept the same as in earlier NT systems.[4] Refactoring in Winlogon resulted in GINA being completely replaced by Credential Providers and graphical components in Windows Vista and later.[5]
BIOS/UEFI[edit]
On systems with a BIOS, the BIOS invokes MBR boot code from a hard disk drive at startup. The MBR boot code and the VBR boot code are OS-specific. In Microsoft Windows, the MBR boot code tries to find an active partition (the MBR is only 512 bytes), then executes the VBR boot code of an active partition. The VBR boot code tries to find and execute NTLDR for Windows XP and earlier, or the Windows Boot Manager for Windows Vista and later, from an active partition.[6]
On systems with a UEFI, the UEFI invokes bootmgfw.efi from an EFI system partition at startup, starting the Windows Boot Manager.
Boot loader phase[edit]
The Windows NT startup process starts when the computer finds a Windows boot loader, a portion of the Windows operating system responsible for finding Microsoft Windows and starting it up. Prior to Windows Vista, the boot loader was NTLDR. Microsoft has also released operating systems for Intel Itanium processors which use IA-64 architecture. The boot loader of these editions of Windows is IA64ldr.efi (later referred as simply IA64ldr). It is an Extensible Firmware Interface (EFI) program.[7] Windows Vista and later use the Windows Boot Manager (bootmgr).
Operating system selection[edit]
The boot loader, once executed, searches for Windows operating systems. Windows Boot Manager does so by reading Boot Configuration Data (BCD), a complex firmware-independent database for boot-time configuration data. Its predecessor, NTLDR, does so by reading the simpler boot.ini. If the boot.ini file is missing, the boot loader will attempt to locate information from the standard installation directory. For Windows NT and 2000 machines, it will attempt to boot from C:\WINNT. For machines running Windows XP, 2003, and later, it will boot from C:\WINDOWS.
Both databases may contain a list of installed Microsoft operating systems that may be loaded from the local hard disk drive or a remote computer on the local network. NTLDR supports operating systems installed on disks whose file system is NTFS or FAT file systems, CDFS (ISO 9660) or UDFS.[8] Windows Boot Manager also supports operating systems installed inside a VHD file, stored on an NTFS disk drive.[9]
In Windows 2000 or in later versions of Windows in which hibernation is supported, the Windows boot loader starts the search for operating systems by searching for hiberfil.sys. NTLDR looks into the root folder of the default volume specified in boot.ini. Windows Boot Manager looks up the location of hiberfil.sys in BCD. If this file is found and an active memory set is found in it, the boot loader loads the contents of the file (which is a compressed version of a physical memory dump of the machine) into memory and restores the computer to the state that it was in prior to hibernation by running winresume.exe.
Next, the boot loader looks for a list of installed operating system entries. If more than one operating system is installed, the boot loader shows a boot menu and allow the user to select an operating system. If a non NT-based operating system such as Windows 98 is selected (specified by an MS-DOS style of path, e.g. C:\), then the boot loader loads the associated «boot sector» file listed in boot.ini or BCD (by default, this is bootsect.dos if no file name is specified) and passes execution control to it.
Otherwise, the boot process continues. For Windows Vista and after, this is done through a separate program, winload.exe.
Loading the Windows NT kernel[edit]
The operating system starts when certain basic drivers flagged as «Boot» are loaded into memory. The appropriate file system driver for the partition type (NTFS, FAT, or FAT32) which the Windows installation resides in is amongst them. At this point in the boot process, the boot loader clears the screen and displays a textual progress bar (which is often not seen due to the initialization speed); Windows 2000 also displays the text «Starting Windows…» underneath.
If the user presses F8 during this phase, the advanced options menu is displayed, containing various special boot modes including Safe mode, with the Last Known Good Configuration, with debugging enabled, and (in the case of Server editions) Directory Services Restore Mode. Starting with Windows Vista, this menu was changed significantly. Once a boot mode has been selected (or if F8 was never pressed) booting continues.
Hardware information about the computer is gathered by NTDETECT.COM in Windows XP and earlier or by winload.exe in later versions. This information is stored in the HKLM\HARDWARE\DESCRIPTION key in the Windows Registry.
Next the Windows NT kernel (Ntoskrnl.exe), the Hardware Abstraction Layer (hal.dll), kdcom.dll (Kernel Debugger HW Extension DLL), bootvid.dll (the Windows logo and side-scrolling bar), and config\system (one of the registry hives) are loaded.
For Windows XP and earlier, if multiple hardware configurations are defined in the Registry, the user is prompted at this point to choose one.
With the kernel in memory, boot-time device drivers are loaded (but not yet initialized). The required information (along with information on all detected hardware and Windows Services) is stored in the HKEY_LOCAL_MACHINE\SYSTEM portion of the registry, in a set of registry keys collectively called a Control Set. In Windows XP and earlier, multiple control sets are kept, in the event that the settings contained in the currently-used one prohibit the system from booting. HKEY_LOCAL_MACHINE\SYSTEM contains control sets labeled ControlSet001, ControlSet002, etc. Windows uses CurrentControlSet to read and write information, but the key is merely a synthesized link to one of the sets defined by HKLM\System\Select\Control; it does not exist in the Hive file.[10]
Windows now picks the «real» control set being used based on the values set in the HKEY_LOCAL_MACHINE\SYSTEM\Select registry key:
Defaultwill be the boot loader’s choice if nothing else overrides it.- If the value of the
Failedkey matchesDefault, then the boot loader displays an error message, indicating that the last boot failed, and gives the user the option to try booting anyway, or to use the «Last Known Good Configuration». - If the user chooses (or has chosen) Last Known Good Configuration, the control set indicated by the
LastKnownGoodkey is used instead ofDefault.
When a control set is chosen, the Current key gets set accordingly. The Failed key is also set to the same as Current until the end of the boot process. LastKnownGood is also set to Current if the boot process completes successfully.
Which services are started and the order which each group is started in are provided by the following keys:
HKLM\SYSTEM\CurrentControlSet\ServicesHKLM\SYSTEM\CurrentControlSet\Control\ServiceGroupOrder
For the purposes of booting, a driver may be one of the following:
- A «Boot» driver that is loaded by the boot loader prior to starting the kernel. «Boot» drivers are almost exclusively drivers for hard-disk controllers and file systems (ATA, SCSI, file system filter manager, etc.); in other words, they are the absolute minimum that the kernel will need to get started with loading other drivers, and the rest of the operating system.
- A «System» driver which is loaded and started by the kernel after the boot drivers. «System» drivers cover a wider range of core functionality, including the display driver, CD-ROM support, and the TCP/IP stack.
- An «Automatic» driver which is loaded much later when the GUI already has been started.
With this finished, control is then passed from the boot loader to the kernel.
Kernel phase[edit]
The initialization of the kernel subsystem and the Windows Executive subsystems is done in two phases.
During the first phase, basic internal memory structures are created, and each CPU’s interrupt controller is initialized. The memory manager is initialized, creating areas for the file system cache, paged and nonpaged pools of memory. The Object Manager,[11] initial security token for assignment to the first process on the system, and the Process Manager itself. The System idle process as well as the System process are created at this point.
The second phase involves initializing the device drivers which were identified by NTLDR as being system drivers.
Through the process of loading device drivers, a «progress bar» is visible at the bottom of the display on Windows 2000 systems; in Windows XP and Windows Server 2003, this was replaced by an animated bar which does not represent actual progress. Prior to Windows XP, this part of the boot process took significantly longer; this is because the drivers would be initialized one at a time. On Windows XP and Server 2003, the drivers are all initialized asynchronously.
Session manager[edit]
Once all the Boot and System drivers have been loaded, the kernel (system thread) starts the Session Manager Subsystem (smss.exe). The Session Manager stores its configuration at HKLM\SYSTEM\CurrentControlSet\Control\Session Manager. The exact operation of most of these items is based on the configuration set in the registry.[12]
The Session Manager creates the environment variables located at the registry entry HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Environment. It also creates additional paging files with configuration data from HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management.[13]
The Session Manager Subsystem is then responsible starting the Win32 subsystem. It starts the kernel-mode side of the subsystem implemented by win32k.sys.[13] Once this is done, Windows is able to switch into graphical mode as there is now enough infrastructure in place. The user-mode side of the subsystem, Client/Server Runtime Subsystem (csrss.exe), is also started.[13] This makes the Win32 subsystem available to user-mode applications.
The Session Manager Subsystem is also responsible for doing any operations that are requested to be done at the start of a session. Commands listed in HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\BootExecute, such as autochk and convert, are executed. These commands are run before services are loaded by later steps of the booting process.[13] Any rename operations queued at HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\PendingFileRenameOperations. This is used to allow previously in-use files (e.g. drivers) to be replaced as part of a reboot.[14]
autochk running on Windows 10.
autochk mounts all drives and checks them one at a time to see whether or not they were cleanly unmounted. If autochk determines one or more volumes are dirty, it will automatically run chkdsk and provides the user with a short window to abort the repair process by pressing a key within 10 seconds (introduced in Windows NT 4.0 Service Pack 4; earlier versions would not allow the user to abort chkdsk). Since Windows 2000, XP and 2003 show no text screen at that point (unlike NT 3.1 to 4.0, which displayed a blue text screen), the user will see a different background picture holding a mini-text-screen in the center of the screen and show the progress of chkdsk there.[15]
Starting with Windows Vista, the Session Manager Subsystem creates a temporary instance of itself that launches the Windows Startup Application (wininit.exe) and a second Client/Server Runtime Subsystem (csrss.exe) for Session 0, a session decided to system processes. From here, the Windows Startup Application starts the Service Control Manager (services.exe), which starts all the Windows services that are set to «Auto-Start» and sets the LastKnownGood to the current control set.[14] The application also starts the Local Security Authority Subsystem Service (lsass.exe). Before Windows Vista, these processes where started by Windows Logon instead of the Windows Startup Application, which didn’t exist. The dedicated session for system processes also didn’t exist.[16]
The Session Manager Subsystem now starts Winlogon (Windows Logon Application), which is responsible for handling interactive logons to a Windows system, either local or remote.[16]
Authentication[edit]
The authentication process is implemented by Winlogon. This program is responsible for responding to the secure attention sequence (SAS), loading the user profile on logon, and optionally locking the computer when a screensaver is running.
Winlogon checks if automatic logon is enabled, and if so, logs in to the specified account automatically.[17] If there is not automatic logon enabled, Winlogon starts the process to allow the user to logon. Before Windows Vista this was done by GINA,[18] but starting with Vista this is done by LogonUI. If configured, both of these programs display a prompt for the user to enter the Secure Attention Sequence (SAS) (Control-Alt-Delete). They then display the login dialog which prompts the user to enter their credentials. Once the user submits these credentials, they are passed to LSASS and any other additional network credential providers. This allows multiple network providers to authenticate the user at once during normal logon.[19][18]
LSASS first tries to use cached data in the LSA database, the SECURITY hive of the registry. If there is none, LSASS determines which account protocol is to be used by using the security packages listed in the key HKLM\SYSTEM\CurrentControlSet\Control\Lsa. There are two standard packages, msv1_0.dll, which implements the NTLM protocols, and Kerberos.dll, which provides remote login by using Active Directory. msv1_0.dll is used in stand-alone systems and domain-member systems for backward compatibility. If the user is trying to log into the local host then msv1_0.dll uses the Security Account Manager database located at HKLM/SAM. If the user is trying to log into another host then the NetLogon service is used to carry the data with the following sequence:
msv1_0.dll <-> netlogon <-> remote netlogon <-> remote msv1_0.dll <-> remote SAM
After the user is authenticated, LSASS enforces the local security policy (checking user permissions, creating audit trails, doling out security tokens, etc.) and passes control pack to Winlogon. Winlogon creates and opens an interactive windows station, WinSta0,[20] and creates three desktops, Winlogon, Default and ScreenSaver. Winlogon switches from the Winlogon desktop to the Default desktop when the shell indicates that it is ready to display something for the user, or after thirty seconds, whichever comes first. The system switches back to the Winlogon desktop if the user presses Control-Alt-Delete or when a User Account Control prompt is shown.[21] Winlogon now starts the program specified in the Userinit value which defaults to userinit.exe. This value supports multiple executables.[19]
Shell[edit]
Userinit is the first program that runs with the user credentials. It is responsible to start all the other programs that compose the user shell environment.
The shell program (typically Explorer.exe) is started from the registry entry Shell= pointed to by the same registry entry in key HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\system.ini\Boot; its default value is SYS:Microsoft\Windows NT\CurrentVersion\Winlogon, which evaluates to HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon.[22]
Userinit starts by loading the user profile. There are a few types of user profiles and it can be local or remote. This process can be very slow if the user profile is of the «roaming» type. User and Computer Group Policy settings are then applied and user scripts, machine scripts, and proquota.exe are run. Startup programs are started and then the shell configured in registry, which defaults to explorer.exe. Now Userinit exits and the shell program continues running without a parent process.
Userinit runs startup programs from the following locations:[13]
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceHKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\RunHKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunHKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows\LoadHKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows\RunHKCU\Software\Microsoft\Windows\CurrentVersion\RunHKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce%ALLUSERSPROFILE%\Start Menu\Programs\Startup\(this path is localized on non-English versions of Windows before Vista)%USERPROFILE%\Start Menu\Programs\Startup\(this path is localized on non-English versions of Windows before Vista)
Advanced options[edit]
With the advent of the new boot manager in Windows Vista, many components have been changed; one is the Advanced Boot Options menu that provides options for advanced boot modes (e.g., Safe Mode). Due to the implementation of fast startup in Windows 8 and up, access to the Advanced Boot Options menu has been disabled by default. However, access is still possible with a BCD modification. These are the possible boot modes:
- Repair Your Computer — Boots Windows Recovery Environment (WinRE or Windows RE)
- Safe Mode — Loads Safe Mode, a boot mode with minimal drivers and resources intended for malware removal or replacing faulty drivers.
- Safe Mode with Networking — Loads Safe Mode along with the network drivers.
- Safe Mode with Command Prompt — Loads Safe Mode with the Command Prompt as the shell instead of Windows Explorer. Windows Explorer can still be loaded by typing
explorerat the command prompt. - Enable Boot Logging — Enables writing of
ntbtlog.txt, a file that will log the boot process; listing drivers that loaded and drivers that did not. - Enable low resolution video — Disables the default graphics driver and uses the standard VGA driver. Intended in case the user changed the resolution to an unusable level (i.e. 320×200 at low refresh rates <24 Hz, 60 Hz>)
- Last Known Good Configuration — Loads configuration based on the last successful boot process. Intended for Registry corruptions. This mode is removed in Windows 8 and later versions of Windows.
- Directory Services Restore Mode — Boot mode used to reboot the Domain Controller in case it is not working as intended.
- Debugging Mode — Boots while loading the kernel debugger.
- Disable automatic restart on system failure — Disables the auto-reboot function after a Blue Screen of Death is experienced.
- Disable early launch anti-malware driver — ELAM prechecks boot required drivers for signatures and tampering. Disabling ELAM is intended to allow booting on false positive driver checks but could also allow a tampered driver to load.[23]
- Disable Driver Signature Enforcement — Disables the kernel setting that prohibits unsigned drivers from loading.
- Start Windows Normally
The ABO menu is accessible by rapidly pressing or holding the F8 key before Windows boots. Starting from Windows 8 on UEFI, it can only be accessed by clicking Restart while holding the Shift key.
Remote booting and installation[edit]
To successfully boot, the client must support PXE booting and the Windows Deployment Services (WDS) component must be installed on the server. It is not installed by default. WDS is the successor of Remote Installation Services (RIS).
The PXE program is found on the BIOS or on a ROM chip on the network card.
PXE booting is not a technology specific to Windows and can also be used to start a Linux system. In fact, a Linux system can act as a server to service DHCP or TFTP.
PXE can be used to start Windows Setup to install the system on the client computer or to run the operating system from RAM. The latter, called Remote Boot, was introduced by Windows XP Embedded SP1[24] and is only available for this flavor of Windows.[25]
The general process for both methods is as follows:
- PXE boots
- DHCP request broadcast
- Optionally DHCP router redirects to the server
- The server sends the Network Bootstrap Program (NBP) (
PXEboot.com)[26] through TFTP - The NBP program downloads the required files through the BINL protocol
The Boot Information Negotiation Layer (BINL) is a Windows 2000 service running on the server that communicates with the client after the NBP was already loaded by the PXE.
See also[edit]
- Architecture of Windows NT
- Windows Setup
- Booting process of Windows NT Setup before Vista
- Booting process of DOS-based Windows
- Booting process of Linux
- Master boot record
- Power-on self-test
- BootVis
References[edit]
- ^ «Inside the Windows Vista Kernel – Startup Processes». Microsoft. Retrieved October 1, 2010.
- ^ a b Microsoft (February 4, 2008). «Boot Configuration Data in Windows Vista» (DOCX). Retrieved April 18, 2015.
- ^ Ritz, Andrew (2004). «EFI and Windows ‘Longhorn’«. Microsoft. Archived from the original (PPT) on June 9, 2004. Retrieved April 18, 2015.
- ^ de Boyne Pollard, Jonathan. «The Windows NT 6 boot process». Frequently Given Answers.
- ^ «Winlogon and GINA». MSDN. Microsoft. Retrieved December 4, 2014.
- ^ «Boot Sequence of Windows Multi-Boot — Multibooters.com». www.multibooters.com. Retrieved November 19, 2020.
- ^ «In Windows Server 2003, you may not be able to start a computer from a GPT disk when the computer has an Itanium processor (Revision: 2.2)». Microsoft Support. Microsoft Corporation. Retrieved October 29, 2011.
- ^ «Unified Extended Firmware Interface support in Windows Vista (Revision: 1.5)». Microsoft Support. Microsoft Corporation. October 26, 2007. Retrieved October 30, 2011.
- ^ «Boot from VHD in Win7». TechNet Edge. Microsoft Corporation. February 20, 2009. Retrieved October 30, 2011.
- ^ «What are Control Sets? What is CurrentControlSet?». Microsoft Support. Archived from the original on February 17, 2015.
- ^ «Windows, NT Object Manager». Channel 9. Microsoft Corporation. June 3, 2005. Retrieved October 24, 2011.
- ^ «Registry: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager». renenyffenegger.ch. Retrieved May 13, 2023.
- ^ a b c d e «Troubleshooting the Startup Process». Windows XP Resource Kit. Microsoft Technet. November 3, 2005. Retrieved October 24, 2011.
- ^ a b Ionescu, Alex; Russinovich, Mark; Solomon, David A. (2012). Windows internals, Part 2 (6th ed.). Redmond, Wash.: Microsoft. pp. 522–527. ISBN 978-0735665873.
- ^ «Resource Kit». Microsoft Corporation. Archived from the original on March 11, 2007.
- ^ a b Archiveddocs. «Windows Administration: Inside the Windows Vista Kernel: Part 2». learn.microsoft.com. Retrieved May 13, 2023.
- ^ Deland-Han. «Configure Windows to automate logon — Windows Server». learn.microsoft.com. Retrieved May 13, 2023.
- ^ a b Russinvoich, Mark E.; Solomon, David (2005). Microsoft Windows Internals (4th ed.). Redmond, Washington: Microsoft Press. p. 81. ISBN 978-0735619173.
- ^ a b Ionescu, Alex; Russinovich, Mark; Solomon, David A. (2012). Windows internals, Part 1 (6th ed.). Redmond, Wash.: Microsoft Press. p. 77. ISBN 978-0735648739.
- ^ «Window Stations». MSDN. Microsoft Corporation. Retrieved April 19, 2014.
- ^ «Desktops». MSDN. Microsoft Corporation. Retrieved April 19, 2014.
- ^ «Different Shells for Different Users». Microsoft Corporation. Retrieved March 16, 2014.
- ^ QuinnRadich. «Early launch antimalware — Win32 apps». docs.microsoft.com. Retrieved December 14, 2021.
- ^ «Deploying Windows XP Embedded Remote Boot». MSDN. Microsoft Corporation. Retrieved April 18, 2014.
- ^ «Remote Boot Overview». MSDN. Microsoft Corporation. Retrieved April 19, 2014.
- ^ «Managing Network Boot Programs». TechNet. Microsoft Corporation. Retrieved April 18, 2014.
Further reading[edit]
- Russinovich, Mark; Solomon, David A. (2005). «Startup and Shutdown». Microsoft Windows Internals (4th ed.). Microsoft Press. pp. 251–273. ISBN 0-7356-1917-4.
- Minasi, Mark; Enck, John (June 1998). «Troubleshooting NT Boot Failures». Administrator’s Survival Guide: System Management and Security. Windows IT Library. ISBN 1-882419-88-X. Retrieved February 15, 2006.
- «Description of PXE Interaction Among PXE Client, DHCP, and RIS Server (Revision 2.4)». Microsoft Support. Microsoft Corporation. February 28, 2007. Retrieved October 24, 2011.
- «Definition of the RunOnce Keys in the Registry (revision 2.3)». Microsoft Support. Microsoft Corporation. January 19, 2007. Retrieved October 24, 2011.
- «Available switch options for the Windows XP and the Windows Server 2003 Boot.ini files (revision 6.3)». Microsoft Support. Microsoft Corporation. November 28, 2007. Retrieved October 24, 2011.
External links[edit]
- Startup Applications List
- How to edit SETUPAPI.DLL Archived January 6, 2019, at the Wayback Machine
An Examination of the
Windows 2000 ( NT5.0 )
and
Windows XP ( NT5.1 )
MBR ( Master Boot Record )
[ Embedded in DMADMIN.EXE,
SPCMDCON.SYS or various other
System files; see Introduction ]
Web Presentation and Text are
Copyright©2003, 2007 by Daniel B. Sedory
NOT to be reproduced in any form without Permission of the Author !
This page examines the Windows™ 2000 MBR code introduced in
1999 when Microsoft finally released what was supposed to be version 5.0 of their NT OS; which was still being called
NT4. Instead, they renamed it to Windows™ 2000; most likely an effort to refocus customer recognition once again on their more
solid Windows™ trademark rather than the «New Technology» (NT) name.
This MBR code is installed on blank hard drives when Disk
Management is used by a Windows™ 2000, XP or 2003 OS. [When
dealing with Dynamic Disks, the partition type is set to 42h and the data in the
Partition Table may become useless!]
Note: Like all other code presented in this series, this MBR code could still be used
to boot any OS on an x86 PC if it meets the conditions listed here*.
- Introduction
- A View of the Win2k/XP MBR in a Disk Editor
- Summary of Code and Data Sections within the MBR
- Message Offset Bytes (for Error Messages)
- Disk Signatures in the Registry
- An Examination of the (Assembly) Code
- Data Strings
- Error Messages/Message Offsets in Memory
- Serial Number/Partition Table in Memory
- Interpreting a Sample Partition Table (on the Standard MBR page).
Other Microsoft MBR pages:
An Examination of the Standard
MBR created by MS-DOS FDISK
The MBR created by MS-Windows 95B/98/98SE and
ME‘s FDISKAnd Microsoft OS Volume Boot Records:
An Examination of the MS-Windows 95B/98/98SE/Me OS Boot Record (MSWIN4.1)
An Examination of the MS-Windows 2000/XP OS Boot Record (NTFS)Confused? Send me an email if you have a specific question about the MBR or any Boot
Records…
IMPORTANT: One of the first things that any PC user should do after setting up
a new hard disk (or creating a new partition with a utility such as Partition Magic) is to make a copy of its MBR; especially if
you have more than one partition on the disk! Why? If you accidentally overwrite this sector, or are infected by a Boot sector virus,
you may never be able to access some or even all of your disk again! Even the most expensive HD utility might not correctly restore
the Partition Table of a multi-partitioned hard disk!
Some advice: Save the Partition Table data on floppy disks or write it down on
paper(!); it does no good to have the data you need to access your HD on the un-accessible HD itself! There are many ways you can do
this… See the MBR Tools Page. Any good Disk Editor will allow you to manually enter data you’ve
written down under an easy to use Partition Table View, or you can use Power Quest’s excellent little utility program «MBRutil» (under any version of Windows!) and «MBRUTILD» (under DOS)
to save the binary data to a file on a floppy diskette and later restore the MBR from the saved file.
____________
| * |
NOTE: Windows NT/2000/XP can also boot multiple OSs There have been many MBRs or IPLs (Initial Program Loaders) created for booting an OS and even for |
Introduction
This page examines the MBR code most likely to be found in a Microsoft®
Windows™ 2000, XP or 2003 installation. All of these operating systems contain the same exact MBR code embedded in files such as
DMADMIN.EXE (there are a few more places we didn’t list above where either the MBR code or Boot Records can be found; if you’re interested in that, read our
“Where’s the
code?” page). This code will be written to Cylinder 0, Head 0, Sector 1 of a
Hard Drive by various OS routines, such as the Disk Management Console, if the drive does not already have an existing MBR sector
(recognized by Windows®) when it is installed. [Note: These OSs will still write data to the MBR sector when required (see our Disk Signature comments below).]
For Windows™ XP (SP2 and SP3), the MBR code is contained inside the
file:
C:\WINNT\system32\dmadmin.exeThis file which is «224,768 bytes»
and has a Modification Date of «Wednesday, August 04, 2004, 4:00:00 AM« (for SP3: Same size, but dated
«Monday, April 14, 2008, 7:00:00 AM») is described as the «Logical Disk Manager service process» with «File version: 2600.2180.503.0» («2600.5512.503.0» for SP3) and:
«Copyright © 1985-2000 Microsoft Corporation. All rights reserved.
Portions Copyright © 1997-2000 Veritas Software. All rights reserved.»
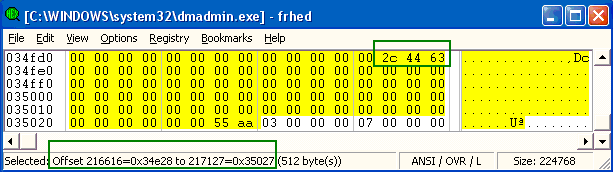
The MBR code itself is found between offsets 34E28h through 35027h (of which only
the last 80 bytes are shown here):
Figure 1. Note that the bytes «2c 44 63″are part of the
MBR’s image file in dmadmin.exe
Under the original Windows™ XP, the MBR code was in the same file, but
at offsets 2FFF8h (196,600) through 301F7h
(197,111) for its August 23, 2001 5:00:00 AM
version of 204,800 bytes. And unlike the very first file under Windows 2000 [see below], its copyright was changed to: «Copyright © 1985-2000 Microsoft Corporation» and only «Portions Copyright © 1997-2000 Veritas Software«; so it appears that Veritas got an offer from
Microsoft® they couldn’t refuse!
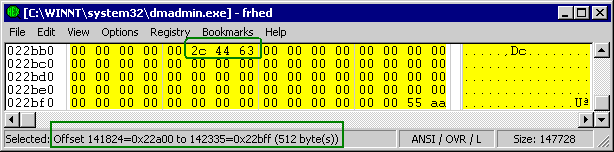
For Windows™ 2000 (with SP3), the MBR code is contained inside the file C:\WINNT\system32\dmadmin.exe This file which is «147,728 bytes» and has a Modification Date of «Monday, July 22, 2002, 12:05:04
PM» is also described as a «Logical Disk Manager service process»; interestingly enough this file is «Copyright © VERITAS Software 1997» and not Microsoft. The MBR code itself is found between
offsets 22A00h through 22BFFh
(of which only the last 80 bytes are shown in this Hex editor window):
Figure 2. The bytes «2c 44 63″have always been part of this
MBR’s image file for English.
The following is a disk editor view of how the bytes in this
MBR are stored on your hard drive’s first sector; that’s Absolute (or Physical) Sector 0, or CHS 0,0,1. (See Examination of the Code below to find out where this data ends up in Memory when it’s executed.)
Absolute Sector 0 (Cylinder 0, Head 0, Sector 1)
0 1 2 3 4 5 6 7 8 9 A B C D E F
0000 33 C0 8E D0 BC 00 7C FB 50 07 50 1F FC BE 1B 7C 3.....|.P.P....|
0010 BF 1B 06 50 57 B9 E5 01 F3 A4 CB BD BE 07 B1 04 ...PW...........
0020 38 6E 00 7C 09 75 13 83 C5 10 E2 F4 CD 18 8B F5 8n.|.u..........
0030 83 C6 10 49 74 19 38 2C 74 F6 A0 B5 07 B4 07 8B ...It.8,t.......
0040 F0 AC 3C 00 74 FC BB 07 00 B4 0E CD 10 EB F2 88 ..<.t...........
0050 4E 10 E8 46 00 73 2A FE 46 10 80 7E 04 0B 74 0B N..F.s*.F..~..t.
0060 80 7E 04 0C 74 05 A0 B6 07 75 D2 80 46 02 06 83 .~..t....u..F...
0070 46 08 06 83 56 0A 00 E8 21 00 73 05 A0 B6 07 EB F...V...!.s.....
0080 BC 81 3E FE 7D 55 AA 74 0B 80 7E 10 00 74 C8 A0 ..>.}U.t..~..t..
0090 B7 07 EB A9 8B FC 1E 57 8B F5 CB BF 05 00 8A 56 .......W.......V
00A0 00 B4 08 CD 13 72 23 8A C1 24 3F 98 8A DE 8A FC .....r#..$?.....
00B0 43 F7 E3 8B D1 86 D6 B1 06 D2 EE 42 F7 E2 39 56 C..........B..9V
00C0 0A 77 23 72 05 39 46 08 73 1C B8 01 02 BB 00 7C .w#r.9F.s......|
00D0 8B 4E 02 8B 56 00 CD 13 73 51 4F 74 4E 32 E4 8A .N..V...sQOtN2..
00E0 56 00 CD 13 EB E4 8A 56 00 60 BB AA 55 B4 41 CD V......V.`..U.A.
00F0 13 72 36 81 FB 55 AA 75 30 F6 C1 01 74 2B 61 60 .r6..U.u0...t+a`
0100 6A 00 6A 00 FF 76 0A FF 76 08 6A 00 68 00 7C 6A j.j..v..v.j.h.|j
0110 01 6A 10 B4 42 8B F4 CD 13 61 61 73 0E 4F 74 0B .j..B....aas.Ot.
0120 32 E4 8A 56 00 CD 13 EB D6 61 F9 C3 49 6E 76 61 2..V.....a..Inva
0130 6C 69 64 20 70 61 72 74 69 74 69 6F 6E 20 74 61 lid partition ta
0140 62 6C 65 00 45 72 72 6F 72 20 6C 6F 61 64 69 6E ble.Error loadin
0150 67 20 6F 70 65 72 61 74 69 6E 67 20 73 79 73 74 g operating syst
0160 65 6D 00 4D 69 73 73 69 6E 67 20 6F 70 65 72 61 em.Missing opera
0170 74 69 6E 67 20 73 79 73 74 65 6D 00 00 00 00 00 ting system.....
0180 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0190 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
01A0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
01B0 00 00 00 00 00 2C 44 63 A8 E1 A8 E1 00 00 80 01 .....,Dc........
01C0 01 00 07 7F BF FD 3F 00 00 00 C1 40 5E 00 00 00 ......?....@^...
01D0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
01E0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
01F0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 55 AA ..............U.
0 1 2 3 4 5 6 7 8 9 A B C D E F
The first 300 bytes (000h through 12Bh) of this 512-byte sector are executable code and the next 80 bytes (12Ch through 17Bh) contain error messages. The last 66
bytes of the sector contain the 64-byte Partition Table (1BEh through 1FDh); data in the Table area will depend
upon the size, structure and file systems on each hard disk. The sector ends with the Word-sized signature ID of AA55h (often called the sector’s Magic number); on PCs using an Intel (or x86 compatible) CPU, hex Words are stored with
the Low-byte first and the High-byte last.
The remaining 66 bytes (between the Error
Messages and the Partition Table; 17Ch through 1BDh) begin as padding (which are first filled with all zero-bytes by Win
2000/XP); with the exception of the three bytes (2C 44 63) at 1B5h through 1B7h
(described in detail below) that are actually part of the dmadmin.exe file (see
Figures 1 and 2 above). However, after a drive has any of the NT-type Operating Systems installed and running, they will write a Disk
Signature in the MBR. The four bytes from offsets 1B8h through 1BBh are called the Windows™ 2000/XP Disk Signature or NT Drive Serial Number (The digits shown in the disk editor view above
are only an example and could be anything; but we’ve noticed a high tendency under Windows 2000/XP for the first and third
and the second and fourth bytes to be the same digits, as in the example above: A8 E1 A8 E1. In other NT-type MBRs, we’ve observed signatures such as these: «87 04 88 04» and «6B 40 6C 40» and «84 1A 85 1A«. So there’s a high
probability that at least the 2nd and 4th bytes will almost always be the same and that some kind of algorithm is being applied by the
OS to create these digit patterns. However, we’ve also seen NT-type MBRs with no discernible pattern at all, such as:
«ED 19 EB BF» and «80 EF A0 FB,» so we have no idea exactly how these OSs ‘decide’ to write these kind of Disk Signature
digits versus those having patterns as seen above.) See here for details on Disk Signature use in the Registry!
The three bytes at offsets 1B5h through 1B7h («2C 44 63«) are used by Microsoft Windows™ for a very specific purpose; for English versions of Windows
2000/XP, you’ll always see these same Hex values («2C 44 63») in the MBR. They’re
used by the MBR code to display Error Messages on your
screen. But for those using Windows™ with a different language, their
MBRs may have different values in the second and third bytes
depending upon how many characters are in the error messages. If
you look in the code section below, starting at offset 063Ah
(instruction: «MOV AL,[07B5]»), you’ll see these three
bytes are used to reference the offset in Memory of the first
byte of each Error Message that can be displayed on screen at boot
up: 072Ch,
0744h
and 0763h.
Since the code will always be the same, the first offset (072Ch)
should never change. If you had the German (Deutsch)
version of Windows™ 2000 or XP, your error messages
and message offsets would look like this:
0120 32 E4 8A 56 00 CD 13 EB D6 61 F9 C3 55 6E 67 81 2..V.....a..Ungü 0130 6C 74 69 67 65 20 50 61 72 74 69 74 69 6F 6E 73 ltige Partitions 0140 74 61 62 65 6C 6C 65 00 46 65 68 6C 65 72 20 62 tabelle.Fehler b 0150 65 69 6D 20 4C 61 64 65 6E 20 64 65 73 20 42 65 eim Laden des Be 0160 74 72 69 65 62 73 73 79 73 74 65 6D 73 00 42 65 triebssystems.Be 0170 74 72 69 65 62 73 73 79 73 74 65 6D 20 6E 69 63 triebssystem nic 0180 68 74 20 76 6F 72 68 61 6E 64 65 6E 00 00 00 00 ht vorhanden.... 0190 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 01A0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 01B0 00 00 00 00 00 2C 48 6E .....,Hn 0 1 2 3 4 5 6 7 8 9 A B C D E F
Now that you know what the bytes at offsets 1B5h through 1B7h are
used for, you could change these error messages to display whatever you wish (as long as they all fit into the space between offsets
12Ch and 1B4h) by counting their character lengths and using a disk editor on the MBR sector to make the appropriate changes.
[ Note: If you ever used PhysTechSoft’s old
«BootWizard» program, these bytes had a completely different meaning! The first byte was an MBR checksum value, and the next
two bytes were a two-byte Hex Word for what it called the structure size. Since the free Disk Editor program PTS-DE (on our Free Tools page) came from PhysTechSoft, it will display these bytes under its
«Partition Table View« as if
they were from the old «Boot Wizard» software; so keep that in mind if you use the PTS-Disk Editor! ]
Disk Signatures in the Registry
Searching for my Disk Signature in the Registry (both as «a8 e1 a8 e1» and
«e1 a8 e1 a8»; endianness often matters, as well as without any spaces between the bytes, taught me a valuable lesson:
You cannot trust Microsoft’s Registry Editor will find all the data you search for. Why? Because much of
what is stored in the Registry is binary (hex) data, and the Registry Editor’s search function cannot find binary values or REG_DWORD entries! This
is rather important for us here, because the Disk Signature of any drive connected to your PC is clearly displayed under this Key:
HKEY_LOCAL_MACHINE\SYSTEM\MountedDevices
which also contains information (in the form of GUIDs) to
reference all logical drives ever connected to the computer! This includes removable
storage such as USB devices; which may contain their actual physical
serial numbers (see: USB
Serials in Registry).
However, the Disk Signature (or NT Serial Number) as a
four-byte Hex Word («E1A8E1A8» hex, see example Signature above) can be found with the Registry Editor in these keys:HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\STORAGE\Volume
and even
HKLM\SYSTEM\ControlSet001\Control\DeviceClasses\{53f5630d-b6bf-11d0-94f2-00a0c91efb8b}
among many others. Keys using Disk Signatures contain a wealth of information about your hard disk’s
partitions!
For example, one of the “SymbolicLink” Key Name’s value (that begins with “ \\?\STORAGE#Volume#1& ”)
continues as:30a96598&0&SignatureE1A8E1A8Offset7E00Length1AE735E00#
followed by the GUID {53f5630d-b6bf-11d0-94f2-00a0c91efb8b} which you’ll see in most of these key values. I’m not exactly sure how the digits in red are used, but I did find them as the Key Value for the Name
ParentIdPrefix under the Key:
HKLM\SYSTEM\CurrentControlSet\Enum\Root\ftdisk\0000.
Interpreting the
Data: The «Signature » value should be obvious. The «Offset » value is the
hexadecimal equivalent of the number of bytes before the beginning of this partition; thus,
7E00h is 32,256 bytes or 63 sectors (at 512 bytes/sector) which also means this is
the first partition on the disk (every Basic Disk leaves the first track unused; except for the MBR sector, so its first partition always begins at
CHS 0,1,1), and the «Length» value is the exact number of bytes in the whole partition
(1AE735E00h = 7,221,763,584 bytes for about a 6.7 GiB partition size).
After executing the POST (Power-On Self Test), the BIOS loads this sector into memory at
0000:7C00 (as it does any MBR) then transfers control to this code.
Unlike an OS boot sector though, this code must first copy itself into another area of Memory. This is necessary because
the code must also load the Boot Sector of the Active Partition into the same area of Memory that it was first loaded into! But just as we saw
for the Windows 98 MBR, this code doesn’t copy any bytes it has already executed before jumping to the new location in Memory; it copies only the 485 bytes
from 7C1Bh through 7DFFh to Memory locations 0000:061B through 0000:07FF, rather than simply copying the whole block of 512 bytes to
0000:0600 and following as the the old Standard MBR code did! For the first 25 instructions, this code is quite similar to that of a Windows 98
(FAT32) MBR, but then diverges into completely new routines.
An Examination of the Assembly Code
You can learn a great deal about the instructions used here by obtaining the x86 Opcode
Windows Help file and Ralf Brown’s Interrupt List from our Intro to Assembly page.
Here’s a Listing of the disassembled code (; with comments) after first being loaded into
Memory at 0000:7C00 by the BIOS (all Memory locations listed below are in Segment 0000:). If you see an asterisk (*) next to an
instruction, it means that MS-DEBUG can not disassemble that code.
7C00 33C0 XOR AX,AX ; Zero out the Accumulator and 7C02 8ED0 MOV SS,AX ; Stack Segment register. 7C04 BC007C MOV SP,7C00 ; Set Stack Pointer to 0000:7C00 7C07 FB STI ; Enable Interrupts 7C08 50 PUSH AX ; (AX=0 at this time) 7C09 07 POP ES ; Zero-out Extra Segment 7C0A 50 PUSH AX ; (AX=0 at this time) 7C0B 1F POP DS ; Zero-out Data Segment 7C0C FC CLD ; Clear Direction Flag 7C0D BE1B7C MOV SI,7C1B ; Source Index: Copy from here... 7C10 BF1B06 MOV DI,061B ; Destination Index: Copy to here: ; Code will begin at: 0000:061B 7C13 50 PUSH AX ; Set up Segment(AX) and Offset(DI) 7C14 57 PUSH DI ; for jump to 0000:061B. 7C15 B9E501 MOV CX,01E5 ; Set up Counter (CX) to copy ; (1E5h) 485 bytes of code. 7C18 F3 REP ; REPeat the following MOVSB ; instruction for 'CX' times. 7C19 A4 MOVSB ; Copy one byte at a time. 7C1A CB RETF ; Use RETF to do Jump to where we ; copied the code: 0000:061B. ; Since the preceding routine copies the remainder of the code to 0000:061B ; through 0000:07FF and continues its execution there, the following ; addresses have been changed to reflect the code's actual location in ; memory at the time of execution. ; This next section of code tries to find an ACTIVE (i.e., bootable) ; entry in the Partition Table. The first byte of an entry indicates ; if it's bootable(an 80h) or not(a 00h); any other values in these ; locations means the Table is invalid! If none of the four entries ; in the Table is active, the 'Invalid' error message is displayed. ; [Previous Microsoft MBR code used the SI register here rather than ; BP which can be seen at offsets 061B, 0620 and 0627 below.] 061B BDBE07 MOV BP,07BE ; Location of first entry ; in the partition table ; (see Sample Table here). 061E B104 MOV CL,04 ; Maximum of four entries. 0620 386E00 CMP [BP+00],CH ; CH=0 (from Counter decrement ; above), so CoMPare first byte ; of entry [BP+00] to Zero. Any- ; thing else will be 'less than'. 0623 7C09 JL 062E ; Found a possible boot entry ; let's check it out more at 062E ; or keep searching here... 0625 7513 JNZ 063A ; -> "Invalid partition table" 0627 83C510 ADD BP,+10 ; Checking the next entry... ; (10h = 16 bytes per entry) 062A E2F4 LOOP 0620 ; Go back & check next Entry... ; unless CL=0 (tried all four). 062C CD18 INT 18 ; Checked all 4; NONE of them ; were bootable, so start ; ROM-BASIC (only available on ; some IBM machines!) Many BIOS ; simply display "PRESS A ; KEY TO REBOOT" when an ; Interrupt 18h is executed. ; An Active partition was found, but we must check all other entries ; for being non-bootable (first byte = 00h), or there's an error! ; (Only one entry in the Partition Table can be marked as 'Active.') 062E 8BF5 MOV SI,BP ; Copy Base Pointer value of 07BE ; into Source Index Register; use 0630 83C610 ADD SI,+10 ; SI,+10 (16 bytes) to see if any ; more partitions are left. 0633 49 DEC CX ; If CX=0, then we're done here, 0634 7419 JZ 064F ; so Jump to ID-type checking! 0636 382C CMP [SI],CH ; Compare entry's first byte [SI] 0638 74F6 JZ 0630 ; to Zero (CH=0). If it's not ; zero, we immediately fall into ; the following error routine: ; Note: When the last character of any Error Message has been displayed ; on screen, the instructions at offsets 0642 and 0644 lock computer's ; execution into an infinite loop! You must reboot the machine. Int 10, ; Function 0Eh (Teletype Output) is used to display the characters. ; 063A A0B507 MOV AL,[07B5] ;[7B5]=2C Together with the '07' 063D B407 MOV AH,07 ; in AH, this gives us an offset 063F 8BF0 MOV SI,AX ; of 72C in the Source Index Reg. ; -> "Invalid partition table" 0641 AC LODSB ; Load character into AL from [SI]. 0642 3C00 CMP AL,00 |; Have we reached end of message |; marker?(00) If so, then lock 0644 74FC JZ 0642 |; execution into infinite loop. 0646 BB0700 MOV BX,0007 ; Display page 0, normal white on ; black characters. 0649 B40E MOV AH,0E ; Teletype Output.. displays only 064B CD10 INT 10 ; one character at a time. 064D EBF2 JMP 0641 ; Go back for another character! The following code is still missing some detailed
comments: 064F 884E10 MOV [BP+10],CL 0652 E84600 CALL 069B ; Load 1st sector of boot ; partition into Memory. 0655 732A JNB 0681 ; (jae short 0681) 0657 FE4610 INC BYTE PTR [BP+10] 065A 807E040B CMP BYTE PTR [BP+04],0B 065E 740B JZ 066B 0660 807E040C CMP BYTE PTR [BP+04],0C 0664 7405 JZ 066B 0666 A0B607 MOV AL,[07B6] ; [7B6] = 44 + 700 -> 744 0669 75D2 JNZ 063D ; Display: "Error loading ; operating system" 066B 80460206 ADD BYTE PTR [BP+02],06 066F 83460806 ADD WORD PTR [BP+08],+06 0673 83560A00 ADC WORD PTR [BP+0A],+00 0677 E82100 CALL 069B 067A 7305 JNB 0681 ; (jae short 0681) 067C A0B607 MOV AL,[07B6] ; [7B6] = 44 + 700 -> 744 067F EBBC JMP 063D ; Display: "Error loading ; operating system" 0681 813EFE7D55AA CMP WORD PTR [7DFE],AA55 ; Check for "Magic Number" 0687 740B JZ 0694 ; at end of sector and ; jump to Boot Record... 0689 807E1000 CMP BYTE PTR [BP+10],00 068D 74C8 JZ 0657 068F A0B707 MOV AL,[07B7] ; [7B7] = 63 + 700 -> 763 0692 EBA9 JMP 063D ; Display: "Missing ; operating system" ========================================================================== ; Set up the CS and IP Registers for Jumping to the Volume Boot Record ; loaded into Memory at 0000:7C00 using a FAR Return instruction (which ; takes IP and then CS off the STACK before jumping to CS:IP); a RETF ; was already used at 7C10 through 7C1A above. 0694 8BFC MOV DI,SP ; STACK Pointer is still 7C00. 0696 1E PUSH DS ; DS is 0000 at this time. 0697 57 PUSH DI ; SP --> DI (now 7C00). 0698 8BF5 MOV SI,BP ; BP (still 07BE) -> SI for ; use by OS Boot Record. 069A CB RETF ; Jumps to VBR at 0000:7C00 ;========================================================================== ; S U B R O U T I N E S for Reading Sectors into Memory ;========================================================================== ; The following code first performs an INT 13 Function 08 BIOS routine ; called "Get Drive Parameters" (if successful, there will be no Carry Flag ; and AH will be zero); returns Max. Head number in DH and the number of ; drives in DL. The Max. Cylinder number must be calculated from bits 7 and ; 6 of CL (two high bits) and CH (low eight bits) to form a 10-bit number; ; thus it can be no larger than 3FFh (or 1023). Bits 5 thru 0 of CL are the ; Max. Sector number -> 3Fh (or 63) is the largest value we can have there. 069B BF0500 MOV DI,0005 ;(Set 'Try Count' to 5 times!) 069E 8A5600 MOV DL,[BP+00] ;| 80 -> DL (First Hard Drive) 06A1 B408 MOV AH,08 ;| INT 13, Function 08 06A3 CD13 INT 13 ;| "Get Drive Parameters" 06A5 7223 JB 06CA 06A7 8AC1 MOV AL,CL 06A9 243F AND AL,3F ; Gives Max. Sectors (bits 5-0) 06AB 98 CBW ; Convert Byte to Word. 06AC 8ADE MOV BL,DH ; Max. Head value -> BL 06AE 8AFC MOV BH,AH 06B0 43 INC BX ; Gives Max. Heads 06B1 F7E3 MUL BX ; AX <- (Max. Heads x Sectors ; = Max. Sectors per Cylinder.) 06B3 8BD1 MOV DX,CX 06B5 86D6 XCHG DL,DH 06B7 B106 MOV CL,06 06B9 D2EE SHR DH,CL 06BB 42 INC DX 06BC F7E2 MUL DX 06BE 39560A CMP [BP+0A],DX 06C1 7723 JA 06E6 ; Check for Extended INT 13. 06C3 7205 JB 06CA 06C5 394608 CMP [BP+08],AX 06C8 731C JNB 06E6 ; Check for Extended INT 13. ; Extended Read Functions not available, so use INT 13 Fundtion 02 : ;======================================================================= 06CA B80102 MOV AX,0201 ;| INT 13, Function 2 06CD BB007C MOV BX,7C00 ;| (ES):BX = Memory Buffer 06D0 8B4E02 MOV CX,[BP+02] ;/ Cyl., Sector, Head & Drive 06D3 8B5600 MOV DX,[BP+00] ;\ values set from code above. 06D6 CD13 INT 13 ;| "Read 1 Sector into Memory" 06D8 7351 JNB 072B ; If CF not set (CF=0), then ; it's a good read, so return! 06DA 4F DEC DI ;/ CF was set, so decrease the ;| 'Try Count' and try again; 06DB 744E JZ 072B ;| unless it's been 5 times! ;| (Note: Calling code is not ;| alerted of any bad reads!) 06DD 32E4 XOR AH,AH ;| INT 13, Function 0 06DF 8A5600 MOV DL,[BP+00] ;| DL=Drive Number 06E2 CD13 INT 13 ;| "Reset DISK System" first 06E4 EBE4 JMP 06CA ;\ Go back and try again... ; The following code is the "INT 13 Extensions Installation Check" : 06E6 8A5600 MOV DL,[BP+00] ;| DL = Drive Number. 06E9 60 * PUSHA ; PUSH all Registers onto Stack. 06EA BBAA55 MOV BX,55AA ;| BX must be set to 55AAh or the ;| Function won't work! 06ED B441 MOV AH,41 ;| INT 13 Function 41h. 06EF CD13 INT 13 ;| "Check for INT 13 Extensions" 06F1 7236 JB 0729 ; Was operation successful? ; If not, Return (with CF set)! 06F3 81FB55AA CMP BX,AA55 ; The contents of BX are changed ; into AA55h if EXTs installed! 06F7 7530 JNZ 0729 ; Are they installed? ; If not, Return (with CF set)! 06F9 F6C101 TEST CL,01 06FC 742B JZ 0729 ; Return (with Carry Flag set)! 06FE 61 * POPA ; POP all Registers from Stack. ; Extended READ Sectors from HDD (Function 42h) follows. To use this function, ; the code must push what's called a "Disk Address Packet" onto the Stack in ; reverse order of how Function 42h will read the 'Packet' data from it, so ; the 00h (Reserved) and 10h bytes are the last to be pushed onto the Stack ; (see instruction at memory location 0711 below): ; ; Offset Size Description of DISK ADDRESS PACKET's Contents ; ------ ----- ------------------------------------------------------------ ; 00h BYTE Size of packet (10h = 16 bytes, or 18h=24 bytes). ; 01h BYTE Reserved (00). ; 02h WORD Number of blocks to transfer (Only 1 sector for this code). ; 04h DWORD Points to -> Transfer Buffer (0000 7C00 for this code). ; 08h QWORD Starting Absolute Sector (get from Partition Table entry: ; (00000000 + DWORD PTR [BP+08]). Remember, the Partition ; Table 'Preceding Sectors' entry can only be a max. of 4 bytes! 06FF 60 * PUSHA ; PUSH all Registers onto Stack. 0700 6A00 * PUSH 0000 ; Push 4 zero-bytes onto Stack to 0702 6A00 * PUSH 0000 ; pad VBR's Starting Sector. 0704 FF760A PUSH [BP+0A] ; High 2 bytes and then the Low 2 0707 FF7608 PUSH [BP+08] ; bytes = Location of VBR Sector. 070A 6A00 * PUSH 0000 ; \ Segment then Offset parts, so: 070C 68007C * PUSH 7C00 ; / Copy to 0x7c00 in Memory. 070F 6A01 * PUSH 0001 ; Copy only 1 sector. 0711 6A10 * PUSH 0010 ; Reserved and Packet Size (16 bytes). 0713 B442 MOV AH,42 ;| INT 13 Function 42h 0715 8BF4 MOV SI,SP ;| (DS):SI = Disk Address Packet ;| which was PUSHed onto STACK ;| to use with this function! 0717 CD13 INT 13 ;| Extended READ of drive sector. ; If successful, CF (Carry Flag) is cleared (0) and AH set to 00h. ; If any errors, CF is set to 1 and AH = error code. In either ; case, DAP's block count field is set to number of blocks actually transferred. 0719 61 * POPA ; POP all Packet values from Stack. 071A 61 * POPA ; POP all Registers from Stack. 071B 730E JNB 072B ; Read OK, so return without Disk Reset. 071D 4F DEC DI ; Error occurred, so try again after Disk Reset: 071E 740B JZ 072B ; If tried 5 times, give up! 0720 32E4 XOR AH,AH ;| INT 13 Function 0 0722 8A5600 MOV DL,[BP+00] ;| DL=Drive Number 0725 CD13 INT 13 ;| "Reset DISK System" 0727 EBD6 JMP 06FF 0729 61 * POPA ; If here, then Extensions Check ; failed, so clean up and return: 072A F9 STC ; SET Carry Flag 072B C3 RET
Location of Error
Messages and
Message Offsets in Memory
C D E F 072C 49 6E 76 61 Inva 0730 6C 69 64 20 70 61 72 74 69 74 69 6F 6E 20 74 61 lid partition ta 0740 62 6C 65 00 45 72 72 6F 72 20 6C 6F 61 64 69 6E ble.Error loadin 0750 67 20 6F 70 65 72 61 74 69 6E 67 20 73 79 73 74 g operating syst 0760 65 6D 00 4D 69 73 73 69 6E 67 20 6F 70 65 72 61 em.Missing opera 0770 74 69 6E 67 20 73 79 73 74 65 6D 00 00 00 00 00 ting system..... 0780 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0790 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 07A0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 07B0 00 00 00 00 00 2C 44 63 .....,Dc 0 1 2 3 4 5 6 7 8 9 A B C D E F
Location of Sample
Disk Signature
and Partition Table in Memory
8 9 A B C D E F
07B8 A8 E1 A8 E1 00 00 80 01 ........
07C0 01 00 07 7F BF FD 3F 00 00 00 C1 40 5E 00 00 00 ......?....@^...
07D0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
07E0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
07F0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 55 AA ..............U.
0 1 2 3 4 5 6 7 8 9 A B C D E F
Last Update: March 26, 2018. (26.03.2018)
Updated: 25 May 2007 (25.05.2007); 10 APR 2009 (10.04.2009); 1 AUG 2009 (01.08.2009); 10 OCT 2010 (10.10.2010); 24 May 2017 (24.05.2017); 23 MAR 2018
(23.03.2018).