If the program whose memory was swapped to disk needs that data or code back, Windows allocates real RAM for it and swaps another application’s memory to disk. If any application (16- or 32-bit) needs additional memory space, it sends a request to Windows, which checks to see how much memory is available.
Contents
- 1 How does Windows operating system work?
- 2 Does it cost money to use Windows?
- 3 What is Windows and its features?
- 4 What are the 5 operating system?
- 5 What are the 10 OS?
- 6 Why is Windows so expensive?
- 7 Is there a monthly fee for Windows 10?
- 8 Do you have to buy Windows 10 every year?
- 9 What is window Short answer?
- 10 What is the difference between window and Windows?
- 11 What are the main functions of Windows 10?
- 12 What does GUI stand for?
- 13 Which software starts first on a computer?
- 14 What is deadlock OS?
- 15 Which is best Linux or Windows?
- 16 Which is better DOS or Windows?
- 17 Which is the fastest OS?
- 18 Why do most companies use Windows?
- 19 When did Windows 11 come out?
- 20 Will there be a Windows 11?
How does Windows operating system work?
The operating system’s job
The operating system (OS) manages all of the software and hardware on the computer. It performs basic tasks such as file, memory and process management, handling input and output, and controlling peripheral devices such as disk drives and printers.
Does it cost money to use Windows?
Microsoft allows anyone to download Windows 10 for free and install it without a product key. It’ll keep working for the foreseeable future, with only a few small cosmetic restrictions. And you can even pay to upgrade to a licensed copy of Windows 10 after you install it.
What is Windows and its features?
Windows is a graphical operating system developed by Microsoft. It allows users to view and store files, run the software, play games, watch videos, and provides a way to connect to the internet. It was released for both home computing and professional works. Microsoft introduced the first version as 1.0.
What are the 5 operating system?
For the most part, the IT industry largely focuses on the top five OSs, including Apple macOS, Microsoft Windows, Google’s Android OS, Linux Operating System, and Apple iOS.
What are the 10 OS?
10 Best Operating Systems in Market
- MS-Windows.
- Ubuntu.
- Mac OS.
- Fedora.
- Solaris.
- Free BSD.
- Chrome OS.
- CentOS.
Why is Windows so expensive?
A Lot Of Companies Use Windows 10
Companies purchase software in bulk, so they aren’t spending as much as the average consumer would.Thus, the software becomes more expensive because it’s made for corporate use, and because companies are accustomed to spending a lot on their software.
Is there a monthly fee for Windows 10?
Microsoft is finally going to start charging for Windows 10 subscriptions, providing only the most basic features for free. Anyone who wants more than bare-bones functionality will have to pay.
Do you have to buy Windows 10 every year?
Windows 10 is available for free to most computers out there.Even after it’s been a year, your Windows 10 installation will continue working and receiving updates as normal. You won’t have to pay for some sort of Windows 10 subscription or fee to continue using it, and you’ll even get any new features Microsft adds.
What is window Short answer?
A window is a separate viewing area on a computer display screen in a system that allows multiple viewing areas as part of a graphical user interface ( GUI ).On today’s multitasking operating systems, you can have a number of windows on your screen at the same time, interacting with each whenever you choose.
What is the difference between window and Windows?
Understand how Windows works, with our easy to understand answers about Windows interview questions.
What is the difference between window and windows?
| S.no | WINDOW | WINDOWS |
|---|---|---|
| 1. | Refers to a single work box on the computer screen. | Refers to the whole operating system on which applications and programs run |
What are the main functions of Windows 10?
Top 10 New Windows 10 Features
- Start Menu Returns. It’s what Windows 8 detractors have been clamoring for, and Microsoft has finally brought back the Start Menu.
- Cortana on Desktop.
- Xbox App.
- Project Spartan Browser.
- Improved Multitasking.
- Universal Apps.
- Office Apps Get Touch Support.
- Continuum.
What does GUI stand for?
GUI (Graphical User Interface) A graphics-based operating system interface that uses icons, menus and a mouse (to click on the icon or pull down the menus) to manage interaction with the system. Developed by Xerox, the GUI was popularized by the Apple Macintosh in the 1980s.
Which software starts first on a computer?
operating system
The “operating system” of a computer is like a first, supervisory program that begins running when the computer first starts up (“boots up”). The operating system plays an invisible administrative and bookkeeping role behind the scenes.
What is deadlock OS?
In an operating system, a deadlock occurs when a process or thread enters a waiting state because a requested system resource is held by another waiting process, which in turn is waiting for another resource held by another waiting process.
Which is best Linux or Windows?
Linux offers great speed and security, on the other hand, Windows offers great ease of use, so that even non-tech-savvy people can work easily on personal computers. Linux is employed by many corporate organizations as servers and OS for security purpose while Windows is mostly employed by business users and gamers.
Which is better DOS or Windows?
Window has no full form but it is widely used operating system than DOS operating system. It consumes more memory and power than DOS operating system.
Difference between DOS and Windows.
| S.NO | DOS | WINDOW |
|---|---|---|
| 1. | DOS is single tasking operating system. | While windows are multitasking operating systems. |
| 2. | It consumes low power. | While windows consume high power. |
Which is the fastest OS?
The latest version of Ubuntu is 18 and runs Linux 5.0, and has no obvious performance weaknesses. The kernel operations seem to be the fastest across all operating systems. The graphical interface is roughly on par or faster than other systems.
Why do most companies use Windows?
Partnerships and business deals don’t need the annoying stress of incompatible files and mismatched functionality. Without a doubt, Windows has the biggest selection of software available for its platform than any other operating system. The benefit of this is that users get to choose from a wider variety of options.
When did Windows 11 come out?
5 October
After months under testing, Microsoft’s Windows 11 operating system (OS) started rolling out to mainstream personal computers (PCs) on 5 October.
Will there be a Windows 11?
Windows 11 is here, and if you own a PC, you might be wondering whether it’s time to upgrade your operating system. After all, you are likely to get this new software free. Microsoft first revealed its new operating system in June, its first major software upgrade in six years.
Lesson 8: Understanding Operating Systems
/en/computerbasics/mobile-devices/content/
What is an operating system?
An operating system is the most important software that runs on a computer. It manages the computer’s memory and processes, as well as all of its software and hardware. It also allows you to communicate with the computer without knowing how to speak the computer’s language. Without an operating system, a computer is useless.
Watch the video below to learn more about operating systems.
Looking for the old version of this video? You can still view it here.
The operating system’s job
Your computer’s operating system (OS) manages all of the software and hardware on the computer. Most of the time, there are several different computer programs running at the same time, and they all need to access your computer’s central processing unit (CPU), memory, and storage. The operating system coordinates all of this to make sure each program gets what it needs.
Types of operating systems
Operating systems usually come pre-loaded on any computer you buy. Most people use the operating system that comes with their computer, but it’s possible to upgrade or even change operating systems. The three most common operating systems for personal computers are Microsoft Windows, macOS, and Linux.
Modern operating systems use a graphical user interface, or GUI (pronounced gooey). A GUI lets you use your mouse to click icons, buttons, and menus, and everything is clearly displayed on the screen using a combination of graphics and text.
Each operating system’s GUI has a different look and feel, so if you switch to a different operating system it may seem unfamiliar at first. However, modern operating systems are designed to be easy to use, and most of the basic principles are the same.
Microsoft Windows
Microsoft created the Windows operating system in the mid-1980s. There have been many different versions of Windows, but the most recent ones are Windows 10 (released in 2015), Windows 8 (2012), Windows 7 (2009), and Windows Vista (2007). Windows comes pre-loaded on most new PCs, which helps to make it the most popular operating system in the world.
Check out our tutorials on Windows Basics and specific Windows versions for more information.
macOS
macOS (previously called OS X) is a line of operating systems created by Apple. It comes preloaded on all Macintosh computers, or Macs. Some of the specific versions include Mojave (released in 2018), High Sierra (2017), and Sierra (2016).
According to StatCounter Global Stats, macOS users account for less than 10% of global operating systems—much lower than the percentage of Windows users (more than 80%). One reason for this is that Apple computers tend to be more expensive. However, many people do prefer the look and feel of macOS over Windows.
Check out our macOS Basics tutorial for more information.
Linux
Linux (pronounced LINN-ux) is a family of open-source operating systems, which means they can be modified and distributed by anyone around the world. This is different from proprietary software like Windows, which can only be modified by the company that owns it. The advantages of Linux are that it is free, and there are many different distributions—or versions—you can choose from.
According to StatCounter Global Stats, Linux users account for less than 2% of global operating systems. However, most servers run Linux because it’s relatively easy to customize.
To learn more about different distributions of Linux, visit the Ubuntu, Linux Mint, and Fedora websites, or refer to our Linux Resources. For a more comprehensive list, you can visit MakeUseOf’s list of The Best Linux Distributions.
Operating systems for mobile devices
The operating systems we’ve been talking about so far were designed to run on desktop and laptop computers. Mobile devices such as phones, tablet computers, and MP3 players are different from desktop and laptop computers, so they run operating systems that are designed specifically for mobile devices. Examples of mobile operating systems include Apple iOS and Google Android. In the screenshot below, you can see iOS running on an iPad.
Operating systems for mobile devices generally aren’t as fully featured as those made for desktop and laptop computers, and they aren’t able to run all of the same software. However, you can still do a lot of things with them, like watch movies, browse the Web, manage your calendar, and play games.
To learn more about mobile operating systems, check out our Mobile Devices tutorials.
/en/computerbasics/understanding-applications/content/
What happens when the computer is thrashing?
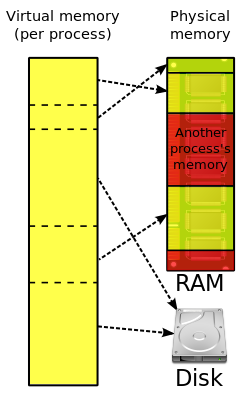
With a computer, thrashing or disk thrashing describes when a hard drive is being overworked by moving information between the system memory and virtual memory excessively.
When thrashing occurs, you will notice the computer hard drive always working, and a decrease in system performance.
What does the booting process do?
Booting a computer refers to the process of powering on the computer and starting the operating system. The operating system is the program that makes all your software applications and hardware work together, so you can do the work you want to do. Once you hit the power button, it’s all automatic from there.
What type of operating system allows two or more programs?
Multi-user: Allows two or more users to run programs at the same time. Some operating systems permit hundreds or even thousands of concurrent users. Multiprocessing : Supports running a program on more than one CPU. Multitasking : Allows more than one program to run concurrently.
Is a cold boot faster than a warm boot?
It is often used in contrast to a warm boot, which refers to restarting a computer once it has been turned on. A cold boot is typically performed by pressing the power button on the computer. Both a cold boot and warm boot clear the system RAM and perform the boot sequence from scratch.
How can operating systems prevent thrashing?
To resolve thrashing you can do any of the suggestions below :
- Increase the amount of RAM in the computer.
- Decrease the number of programs being run on the computer.
- Adjust the size of the swap file.
How does the system detect thrashing?
Thrashing is caused by under allocation of the minimum number of pages required by a process, forcing it to continuously page fault. The system can detect thrashing by evaluating the level of CPU utilization as compared to the level of multiprogramming. It can be eliminated by reducing the level of multiprogramming.
What are the two types of booting in a computer?
booting. Restarting a computer or its operating system software. It is of two types (1) Cold booting: when the computer is started after having been switched off. (2) Warm booting: when the operating system alone is restarted (without being switched off) after a system crash or ‘freeze.’
What is Bootrom?
Bootrom (or Boot ROM) is a small piece of mask ROM or write-protected flash embedded inside the processor chip. It contains the very first code which is executed by the processor on power-on or reset. Sometimes it may contain additional functionality, possibly usable by user code during or after booting.
What is the boot process of a typical computer?
Boot sequence is the order in which a computer searches for nonvolatile data storage devices containing program code to load the operating system (OS). Typically, a Macintosh structure uses ROM and Windows uses BIOS to start the boot sequence.
Is an operating system a utility program?
System software includes operating systems, utility software, device drivers and firmware. Operating systems control the computer hardware and act as an interface with application programs. Utility software helps to manage, maintain and control computer resources.
What is another term for an Internet peer to peer network?
Stands for “Peer to Peer.” In a P2P network, the “peers” are computer systems which are connected to each other via the Internet. Files can be shared directly between systems on the network without the need of a central server. Common P2P software programs include Kazaa, Limewire, BearShare, Morpheus, and Acquisition.
Is the core of an operating system that manages memory and devices?
The core of an operating system that manages memory and devices, maintains the computer’s clock, starts programs, and assigns the computer’s resources. Remaining in memory while a computer is running. multiprocessing. In reference to operating systems, supports two or more processors running programs at the same time.
Which power control option performs a warm boot?
On PCs, you can perform a warm boot by pressing the Control, Alt, and Delete keys simultaneously. On Macs, you can perform a warm boot by pressing the Restart button. Contrast with cold boot, turning a computer on from an off position.
What is the difference between cold booting and warm booting a computer?
The main difference between cold and warm booting is that the cold booting is the process of starting up the computer that is turned off while warm booting is the process of restarting the computer without interrupting power.
What is cool booting in computer?
Alternatively referred to as a cold start, hard boot, and hard start, cold boot is a term used to describe the process of turning on the computer after it has been powered off. For example, when you first turn your computer on after being off for the night you are cold booting the computer.
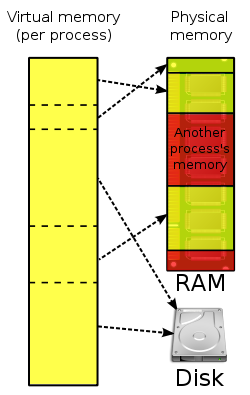
What is paging in OS?
Paging is a method of writing data to, and reading it from, secondary storage for use in primary storage, also known as main memory. In a memory management system that takes advantage of paging, the OS reads data from secondary storage in blocks called pages, all of which have identical size.
What is thrashing operating system?
In a virtual storage system (an operating system that manages its logical storage or memory in units called pages), thrashing is a condition in which excessive paging operations are taking place. A system that is thrashing can be perceived as either a very slow system or one that has come to a halt.
What is thrashing and how do you handle it?
Operating System | Techniques to handle Thrashing
- Thrashing is a condition or a situation when the system is spending a major portion of its time in servicing the page faults, but the actual processing done is very negligible.
- Locality Model – A locality is a set of pages that are actively used together.
- Techniques to handle:
Why are page size always power of 2 in OS?
Why are page sizes always powers of 2? Recall that paging is implemented by breaking up an address into a page and offset number. Because each bit position represents a power of 2, splitting an address between bits results in a page size that is a power of 2.
How thrashing can be prevented?
When this swapping activity is occurring such that it is the major consumer of the CPU time, then you are effectively thrashing. You prevent it by running fewer programs, writing programs that use memory more efficiently, adding RAM to the system, or maybe even by increasing the swap size.
What is computer threshing?
In computer science, thrashing occurs when a computer’s virtual memory resources are overused, leading to a constant state of paging and page faults, inhibiting most application-level processing. This causes the performance of the computer to degrade or collapse.
What are the 3 most common operating systems for personal computers?
The three most common operating systems for personal computers are Microsoft Windows, Mac OS X, and Linux.
The Windows operating system (Windows OS) for desktop PCs are more formally called Microsoft Windows and is actually a family of operating systems for personal computers. Windows provides a graphical user interface (GUI), virtual memory management, multitasking, and support for many peripheral devices.
What happens when computer starts?
Booting is what happens when a computer starts. This happens when the power is turned on. It is called “reboot” if it happens at other times. When you boot a computer, your processor looks for instructions in system ROM (the BIOS) and executes them.
Содержание
- What are the features of Microsoft Windows?
- Control Panel
- Cortana
- Desktop
- Device Manager
- Disk Cleanup
- Event Viewer
- File Explorer
- Internet browser
- Microsoft Paint
- Notepad
- Notification area
- Power User Tasks Menu
- Registry Editor
- Settings
- Start and Start menu
- System Information
- Taskbar
- Task Manager
- Windows search box
- OPERATING SYSTEMS AND UTILITIES
- Помогите с вопросами по информатике.
- Understanding Operating Systems
- Computer Basics: Understanding Operating Systems
- Lesson 8: Understanding Operating Systems
- What is an operating system?
- The operating system’s job
- Types of operating systems
- Microsoft Windows
- macOS
- Linux
- Operating systems for mobile devices
- Видео
What are the features of Microsoft Windows?
Microsoft Windows includes a wide array of features, tools, and applications to help get the most out of Windows and your computer.
To learn more about the features included in Microsoft Windows, click a link below.
Control Panel
The Control Panel is a collection of tools to help you configure and manage the resources on your computer. You can change settings for printers, video, audio, mouse, keyboard, date and time, user accounts, installed applications, network connections, power saving options, and more.
In Windows 10, the Control Panel is located in the Start menu, under Windows System.
Many of the Control Panel settings are also accessible in the Windows 10 Settings menu.
Cortana
Cortana is a virtual assistant introduced in Windows 10 that accepts voice commands. Cortana can answer questions, search your computer or Internet, set appointments and reminders, perform online purchases, and more. Cortana has similarities to other voice-activated services, such as Siri, Alexa, or Google Assistant, with the added benefit that it can search the information on your computer.
Desktop
The desktop is a fundamental part of the default GUI (graphical user interface) in Windows. It is a space where you can organize applications, folders, and documents, which appear as icons. Your desktop is always in the background, behind any other applications you’re running.
When you power on your computer and log in to Windows, the first thing you see is your desktop background, icons, and the taskbar. From here, you can access the installed programs on your computer from the Start menu, or by double-clicking any application shortcuts you may have on your desktop.
You can access your desktop at any time by pressing Windows key + D to minimize any running applications.
With the release of Windows 8 in 2012, the desktop was no longer the default GUI, replaced by the Start Screen. This change was short-lived, and the desktop returned as the default GUI in Windows 10.
Device Manager
The Device Manager lists the hardware devices installed in a computer. It allows users to see what hardware is installed, view and update hardware drivers, and uninstall hardware through the Device Manager.
Disk Cleanup
The Disk Cleanup utility helps increase free disk space on your computer by removing temporary or unnecessary files. Running Disk Cleanup helps improve your computer’s performance, and create additional space to store your downloads, documents, and programs.
You can access Disk Cleanup from the File Explorer.
Event Viewer
The Event Viewer is an administrator tool displays errors and important events that happen on your computer. It helps troubleshoot advanced problems in your Windows system.
File Explorer
The File Explorer, also called Windows Explorer, provides you with a view of the files and folders on the computer. You can browse the contents of your SSD, hard drive, and attached removable disks. You can search for files and folders, and open, rename, or delete them from the File Explorer.
Internet browser
Your Internet browser is one of the most important applications on your computer. You can use it to find information on the Internet, view web pages, shop and buy merchandise, watch movies, play games, and more. Microsoft Edge is the default browser in Windows 10. Internet Explorer is included as the default browser in previous versions of Windows, from Windows 95 to Windows 8.1.
To open a new Edge browser window in Windows 10, open the Start menu and scroll down to Microsoft Edge.
Microsoft Paint
Included in Windows since November 1985, Microsoft Paint is a simple image editor that you can use to create, view, and edit digital images. It provides basic functionality to draw and paint pictures, resize and rotate photographs, and save pictures as different file types.
Notepad
Notepad is a simple text editor. You can use it to create, view, and edit text files. For instance, you can use Notepad to write a batch file, or a web page written in HTML.
Notification area
The notification area, also known as the system tray, displays the date and time, and shows icons of programs that are started with Windows. It also provides your Internet connection’s status and a speaker icon for adjusting sound volume.
Available in Windows 8 and Windows 10, the Power User Tasks Menu provides quick access to helpful and important Windows utilities. From this menu, you can open the Control Panel, Device Manager, File Explorer, Task Manager, and more.
Registry Editor
The Registry Editor allows you to view the Windows system registry, and edit registry keys. Computer technicians may use the Registry Editor to fix problems with the Windows operating system or installed software.
Making changes to the registry can cause your applications or system to stop functioning correctly. Don’t edit the registry if you’re not sure what your changing and always back up your registry by exporting it to a file before making changes.
Settings
Available in Windows 8 and Windows 10, Settings allows you to change many aspects of Windows. You can change the desktop background, adjust power settings, review options for external devices, and more.
Start and Start menu
The Start menu is a list of applications and utilities installed on your computer. You can open it by clicking Start on the left side of your taskbar.
System Information
The System Information utility provides information about the computer, including hardware and Windows details. You can find out details about your computer’s hardware, including processor, memory, video card, and sound card. You can also view and configure environment variables, device drivers, services, and more.
Taskbar
The Windows taskbar shows programs that are currently open, and a Quick Launch area that allows quick access to launch specific programs. The notification area is on the right side of the taskbar, showing the date and time, and programs running in the background.
Task Manager
The Task Manager gives you an overview of what’s running on your computer. You can see how much of your system resources is used by each application (task), sorting by CPU, RAM, and disk I/O usage. If a program is frozen or not responding, you can right-click it in Task Manager and end the task, forcing it to quit.
Windows search box
The Windows search box is a convenient way to search for documents, pictures, videos, applications, and more. In Windows 10, the search box is also integrated with Cortana. The feature first appeared in Windows Vista.
The search box is on your taskbar by default. In Windows 10, if you don’t see the search box, right-click the taskbar and select Taskbar settings. Make sure Use small taskbar buttons is Off. Then, right-click the taskbar again, and select Cortana, Show search box.
Источник
OPERATING SYSTEMS AND UTILITIES
Operating system overview
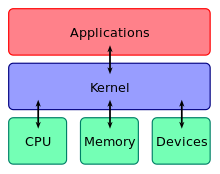
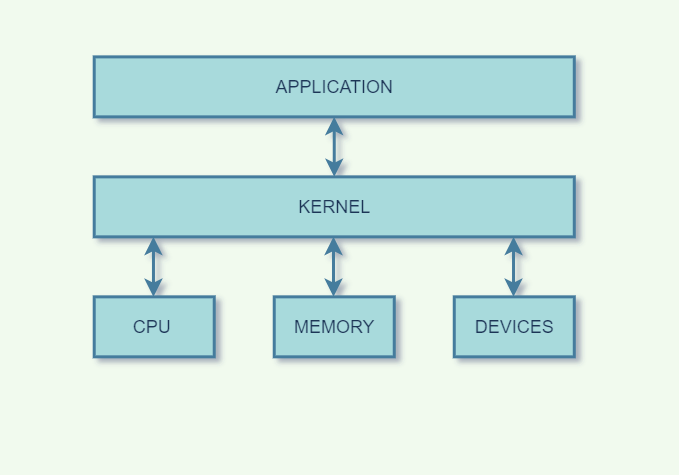
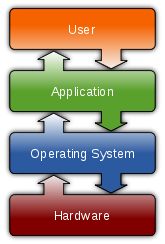
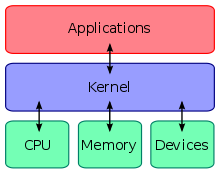
An operating system (abbreviated OS) is a type of system software that acts as a mast controller for all the activities that take place within a computer system. It is one of the factors that determine your computer compatibilityand platform. The operating system interactswith application software, device drivers, and hardware to manage a computer’s resources. The term resource refers to any component that is required to perform work. For example, the processor is a resource. RAM, storage space, and peripherals are also resources.
Operating system manages different tasks:
— Managememory. OS allocates a specific area of RAM for each program that is open and running. OS is itself a program, so it requires RAM space too. A microprocessor works with data and executes instructions stored in RAM – one of your computer’s most important resources. When you want to run more than one program at a time, the OS has to allocate specific areas of memory for each program. When multiple programs are running, the OS must ensurethat instructions and data from one area of memory do not “leak” into an area allocated to another program. If an OS falls down on the job and fails to protect each program’s memory area, data can get corrupted, programs can “crash”, and your computer displays error messages.
— Manage processor resources. The operating system also controls the microprocessor – just at a slightly higher level. Every cycle of a computer’s microprocessor is a resource for accomplishing tasks. Many activities – called “processes” – compete for the attention of your computer’s microprocessor. OS must ensure that each activity “process” receives its share of microprocessor cycles. A computer can take advantage of performance-enhancing technologies such as multitasking,multithreading,multiprocessing,dual coreormultiple processors.
— Keep track of storage resources. OS stores and retrieves files from your disks and CDs. It remembers the names and locations of all your files and keeps track of empty spaces where new files can be stored.
— Ensure that input and output proceed in an orderly manner. OS communicates with device driver software so that data can travel smoothlybetween the computer and these peripheral resources. OS uses ‘buffers’ to collect and hold data while the computer is busy with other tasks.
— Establish basic elements of the user interface. A user interface can be definedas the combination of hardware and software that helps people and computers communicate with each other. Your computer’s user interface includes a display device, mouse, and keyboard that allow you to view and manipulate your computer environment. It also includes software elements, such as menus and toolbar buttons. A graphical user interface (GUI)features menus and icons that you can manipulate with the click of a mouse. A command-line interface requires you to memorize and type commands.
For nearly all PCs, servers, workstations, mainframes, and supercomputers, the operating system program is quite large, so most of it is stored on a hard disk. The operating system’s small bootstrap program is stored in ROM and supplies the instructions needed to load the operating system’s core into memory when the system boots. This core part of OS called the kernelprovides the most essential operating system services, such as memory management and file access. The kernel always stays in RAM all the time your computer is on. Other parts of OS, such as customization utilities, are loaded into RAM as they are needed.
Many operating systems provide helpful tools, called operating system utilities, that you can use to control and customize your computer equipment and work environment. They are typically accessed by using a GUI, such as the familiar Windows desktop. The most popular are: launch programs, manage files, get help, customize the user interface, and configure equipment.
One operating system might be better suited to some computing tasks than others. To provide clues to their strengths and weaknesses, operating systems are informally categorized using one or more of the following terms:
A single-user operating system expects to deal with one set of input devices – those that can be controlled by one user only.
A multiuser operating systemallows a single computer to deal with simultaneousinput, output, and processing requests from many users. One of its most difficult responsibilities is to schedule all the processing requests that a centralized computer must perform.
A network operating system provides communications and routing services that allow computers to share data, programs, and peripheral devices. The main difference between network OS and multiuser OS is that multiuser operating systems schedule requests for processing on a centralized computer, whereas a network operating system simply routes data and programs to each user’s local computer, where the actual processing takes place.
A desktop operating system is one that is designed for a personal computer. Typically, these operating systems are designed to accommodate a single user, but might also provide network capability.
Windows is the best-selling operating system. The number and variety of programs that run on Windows are unmatched by any other operating system, a fact that contributes to its dominant position as the most widely used desktop operating system.
Utility software is a type of system software that is designed to perform a specialized task, such as system maintenance or security. Utility software that does not come packaged with an operating system is often referred to as a third-party utility. In past years, antivirus software was a popular category of third-party utilities. With the recent influx of nuisance ads, intrusion attempts, and spam, utilities such as ad blockers, personal firewalls, and spam filters have also become best sellers. Filtering software is used by parents to block their children from objectionable Websites. Another popular category of utility software is system utilities. These utilities track down and fix disk errors, repair corrupted files, and give your PC a performance – enhancing tune-up.
A final group of utilities worth mentioning is designed for backing upand cleaning up hard disks, and shreddingfiles so they can’t be recovered. They can help you recover files deleted by mistake.
Comprehension check. Indicate the paragraph where the following ideas are found in the text.
1. Operating system’s main purpose is to control what happens behind the scene.
2. Your PC can sometimes recover from memory leak problems if you use the Ctl+Alt+Del key sequence to close the corrupted program.
3. The operating system must ensure that the microprocessor does not “spin its wheels” waiting for input while it could be working on some other processing projects.
4. Windows is installed on more than 80 % of the world’s personal computers.
5. The term “buffer” is a technical jargon for a region of memory that holds data waiting to be transferred from one device to another.
6. Many operating systems provide helpful tools, called operating system utilities, that you can use to control and customize your computer equipment and work environment.
Vocabulary practice
1. In the text find the opposites to the given words.
roughly shred disorganize monopolize stop succeed break
2. Fill in the blanks choosing from the variants given.
1. An operating system … a computer’s resources, such as Ram, storage space, and peripherals.
a) allocates b) defines c) manages d) accommodates
2. To … more than one program at a time, the operating system must allocate specific areas of Ram for each program.
a) store b) install c) fix d) run
3. A graphical user-interface provides a way to point and click a mouse to … menu options and manipulate objects that appear on the screen.
a) feature b) deal with c) select d) manage
4. Handheld devices, such as PDAs and smartphones typically … single-user operating systems.
a) feature b) retrieve c) include d) establish
5. OS communicates with device driver software so that data can travel … between the computer and peripheral resources.
a) roughly b) smoothly c) simultaneously d) primary
a) variety b) security c) capability d) compatibility
3. Make three-word combinations using the words in columns and then fill in the gaps in the following sentences.
A: multiuser B: operating C: system
third user technologies
desktop enhancing interface
graphical operating system
performance party utilities
3. A … features menus and icons that you can manipulate with a click of a mouse.
4. A …, such as Windows, is designed for personal computers.
5. WinZip, WinAce are … that offer a variety of compression options.
4. Fill in the gaps in the text.
___ (computer/application) software tells the operating system what to do. The operating system tells the ___ (device/tool) drivers, device drivers tell the ___ (software/hardware), and the hardware actually does the work. The operating system___ (interacts/competes) with application software, device drivers, and hardware to ___ (manage/define) a computer’s ___ (resources/compatibility).
The core part of an operating system is called the ___ (kernel/cycle). In addition to this core, many operating systems ___ (provide/schedule) helpful tools, called ___ (utilities/capabilities).
Speaking. Discuss the following questions.
1. What is an operating system?
2. What does an operating system do?
3. How does an operating system manage processor resources?
4. Why does an operating system manage memory?
5. Where is the operating system stored?
6. What are utilities? What are the most popular ones?
7. How does the operating system affect the user interface?
Text C
Reading. Read the text and try to guess the meaning of the words in bold. Check your variants in the dictionary.
APPLICATION SOFTWARE
Most computers include some basic word processing, e-mail, and Internet access software, but computer owners want additional software to increase their computer’s productivity, business, learning, or entertainment capabilities.
Источник
Помогите с вопросами по информатике.
1. Видеокарта, процессор, мат. плата, оперативка, жёсткий диск, блок питания, сетевая карта. Перифирия: монитор, мышка, клавиатура, колонки. Видеокарта может быть встроенна в процессор, сетевая карта в мат. плату.
2. Форм-фактор компьютера это размеры материнской платы + корпуса ради компактности будущего компа. Форм фактор имеет стандарты mini-ATX например.
3. Да это универсальная игровая платформа с огромными возможностями и такой компьютер может быть и для бизнеса и даже как сервер, что даёт область применения в бизнесе онлайн компьютерных игр или аренды как хоста, так и VPS сервера.
4. Наличие умений выбора у выбирающего, связь видеокарты + процессора что есть основа как под цену компьютера, так и под требуемые задачи. Это начало.
5. Новые платформы снабжаются одними и теми же процессорами на 2016 год от Intel, что позволяет запускать на Mac платформе виртуальные ОС windows. Можно совместить платформы с наличием в новых Mac платформах UEFI поставив 2 операционные системы 64-х битную Windows и оставив Mac. Так что можно, но не легко.
6. Устаревший это примерно на 2016 год 2009, очень сильные модели и для игр подойдут, но апгрейд ради игр хорошая идея, ибо это не замена компьютера с нуля.
7. Текстовые процессоры, графические профессиональные редакторы, мессенджеры и браузеры, почтовые программы.
8.What basic utilities are included with Windows and Mac operating systems?
Windows содержит простые утилиты как простой графический редактор, просмотр картинок, базовые возможности просмотра видео/музыки, калькулятор и настройка за программным обеспечением, где есть так же защита и много сетевых утилит для соединения например жёстких дисков разных компьютеров.
__________
Mac да хрен его знает никогда им не пользовался!
__________
9.How do iPhones provide adaptive utilities for people who can’t see the screen?
х. й знает
__________
iPhone да хрен его знает никогда им не пользовался!
__________
10.Why is it important to know where to locate the version numbers for device drivers?
что бы знать пора ли их обновить ради улучшенной поддержки устройства.
11.How can word processing software help improve your writing?
Исправляя синтаксические ошибки он является как бы проверочным редактором перед выпуском с удобством исправления, базой слов и просмотром и редактированием тех же текстов.
12.How does spreadsheet software work?
Табличное программное обеспечение работает сохраняя важные данные в свои ячейки в которых очень высокая скорость поиска, а так же большие возможности сортировки и вывода информации по строкам и таблицам, примеры тому очень популярные MySQL, Excel.
Источник
Understanding Operating Systems
Computer Basics: Understanding Operating Systems
Lesson 8: Understanding Operating Systems
What is an operating system?
An operating system is the most important software that runs on a computer. It manages the computer’s memory and processes, as well as all of its software and hardware. It also allows you to communicate with the computer without knowing how to speak the computer’s language. Without an operating system, a computer is useless.
Watch the video below to learn more about operating systems.
Looking for the old version of this video? You can still view it here.
The operating system’s job
Your computer’s operating system (OS) manages all of the software and hardware on the computer. Most of the time, there are several different computer programs running at the same time, and they all need to access your computer’s central processing unit (CPU), memory, and storage. The operating system coordinates all of this to make sure each program gets what it needs.
Types of operating systems
Operating systems usually come pre-loaded on any computer you buy. Most people use the operating system that comes with their computer, but it’s possible to upgrade or even change operating systems. The three most common operating systems for personal computers are Microsoft Windows, macOS, and Linux.
Modern operating systems use a graphical user interface, or GUI (pronounced gooey). A GUI lets you use your mouse to click icons, buttons, and menus, and everything is clearly displayed on the screen using a combination of graphics and text.
Each operating system’s GUI has a different look and feel, so if you switch to a different operating system it may seem unfamiliar at first. However, modern operating systems are designed to be easy to use, and most of the basic principles are the same.
Microsoft Windows
Microsoft created the Windows operating system in the mid-1980s. There have been many different versions of Windows, but the most recent ones are Windows 10 (released in 2015), Windows 8 (2012), Windows 7 (2009), and Windows Vista (2007). Windows comes pre-loaded on most new PCs, which helps to make it the most popular operating system in the world.
Check out our tutorials on Windows Basics and specific Windows versions for more information.
macOS
macOS (previously called OS X) is a line of operating systems created by Apple. It comes preloaded on all Macintosh computers, or Macs. Some of the specific versions include Mojave (released in 2018), High Sierra (2017), and Sierra (2016).
According to StatCounter Global Stats, macOS users account for less than 10% of global operating systems—much lower than the percentage of Windows users (more than 80%). One reason for this is that Apple computers tend to be more expensive. However, many people do prefer the look and feel of macOS over Windows.
Check out our macOS Basics tutorial for more information.
Linux
Linux (pronounced LINN-ux) is a family of open-source operating systems, which means they can be modified and distributed by anyone around the world. This is different from proprietary software like Windows, which can only be modified by the company that owns it. The advantages of Linux are that it is free, and there are many different distributions—or versions—you can choose from.
According to StatCounter Global Stats, Linux users account for less than 2% of global operating systems. However, most servers run Linux because it’s relatively easy to customize.
To learn more about different distributions of Linux, visit the Ubuntu, Linux Mint, and Fedora websites, or refer to our Linux Resources. For a more comprehensive list, you can visit MakeUseOf’s list of The Best Linux Distributions.
Operating systems for mobile devices
Operating systems for mobile devices generally aren’t as fully featured as those made for desktop and laptop computers, and they aren’t able to run all of the same software. However, you can still do a lot of things with them, like watch movies, browse the Web, manage your calendar, and play games.
To learn more about mobile operating systems, check out our Mobile Devices tutorials.
Источник
Видео
Intermediate Class for Mac OS (Operating System) «Utilities»
MacApps #02 — Best Mac Apps, Utilities, Tips & Games для MacOS 2019
Computer Fundamentals — Windows 10 & Mac OS X — How to Use MS Microsoft and Apple Operating Systems
MacApps #23 — Best Mac Apps, Utilities, Tips для MacOS 2022 | 5 Best New macOS Apps 03.04.2022
Флешка Mac OS X из Windows с помощью BDU (Boot Disk Utility)
MacApps #19 — Best Mac Apps, Utilities, Tips для MacOS 2021 | 5 Best New macOS Apps 19.05.2021
CompTIA A+ Full Course — FREE — [31+ Hours]
How to Open the Utilities Folder On a Mac Computer — Basic Tutorial | New
Mac Tutorial for Beginners — Switching from Windows to macOS
MacApps #18 — Best Mac Apps, Utilities, Tips для MacOS 2021 | 5 Best New macOS Apps 28.02.2021
Table of Contents
There’s a lot of fanboyism when it comes to picking an operating system, with vocal supporters on all sides. The Linux vs Windows discussion is an age-old battle that has been fought over for years now.
It is important to stress that the ‘best’ operating system cannot have a single answer, as the best really depends upon the requirements of the user.
Here we discuss the pros and cons of both systems, as we hope to deliver a fair review based on specific criteria. Perhaps this will help you decide between Windows or Linux.
The ideal way to start this discussion is by talking about the differences between Linux and Windows. We dive into this after talking briefly about each OS.
Linux vs Windows: Head-to-Head Comparison
|
Parameters |
Linux |
Windows |
|
Developed By |
Linus Torvalds |
Microsoft Corporation |
|
Licensing |
Open-source |
Closed-source |
|
Price |
Free |
Costly |
|
Kernel Type |
Monolithic kernel |
Micro kernel |
|
Efficiency |
More efficient |
Less efficient |
|
Separating Directories |
Forward slash |
Back slash |
|
Security |
More secure |
Less secure than Linux |
|
Hacking Efficiency |
High |
Low |
|
Types of User Accounts |
|
|
|
Super User |
Root user |
Administrator user |
|
Reliability |
More reliable |
Less reliable than Linux |
|
Gaming |
Less suitable |
Ideal |
|
System Updates |
Easy and users have control |
Difficult for novice users |
What is Windows Operating System?
The Windows Operating System was first released in 1985 by Microsoft. It now dominates the OS market, with the largest user base around the globe. Through updates, every OS version gets a unique graphical user interface. Windows actually has two modes: the user mode and kernel. The latter runs critical system processes, while the former runs typical applications.
Most of the commercial systems that we see today work on the Windows Operating System, which is designed to work on the x86 hardware, including Intel and AMD.
Here’s a list of pros and cons of the Windows OS:
|
Pros |
Cons |
|
Intuitive and beginner-friendly |
Can slow down over time |
|
High-quality UI |
Can have bugs and reliability issues |
|
Lots of apps available |
Must be purchased |
|
Good support for legacy apps |
Subject to vulnerabilities |
|
Has plenty of hardware and driver support. |
Does have data collection, though it can be turned off |
What is Linux Operating System?
The Linux Operating System is an open-source OS created in the early 1990s by Linus Torvalds. Based on UNIX, Linux allows users to modify the existing code and produce different versions or distributions of it, which they can re-use and even sell.
Linux has emerged as the top choice for setting up servers, which is why most web pages on the internet are served via systems backed by one of its distributions. The OS is also popularly used in desktops, mobile, consoles, eBook readers, and much more.
Here’s a list of pros and cons of the Linux OS:
|
Pros |
Cons |
|
Free |
Unintuitive and not suitable for beginners |
|
Much faster than Windows |
Does not have as many apps as Windows |
|
Customizable |
Does not have extensive hardware or driver support |
|
Very reliable and secure |
|
|
High levels of privacy |
Differences between Linux and Windows
Here we’ll go over the difference between Windows and Linux based on select criteria.
1. Price and Licensing
The Linux OS and most of its utilities and libraries are entirely free and open-source for use and modification. While paid distributions of the Linux OS with additional support are available in the market, they are very moderately priced. Linux, under GNU General Public License, allows users to modify, re-use in any number of systems, and even sell their own modified versions.
Microsoft Windows OS comes with the Microsoft License, which does not give users access to the source code. Thus, no modification can be performed at the standard user level. The Microsoft License ranges from $70 to $200 for its standard versions, and can only be installed on a certain number of computers as specified in your purchase.
2. Ease of Use
This might be a tough comparison to make, as it may vary from person to person. However, Linux has revamped its usability standing over the years through constant modernization. With the release of distributions such as Linux Mint, the installation, and setup process has been made simpler. Through continuous updates, people with little or no technical knowledge can also install software and perform normal activities such as email, play music and videos, and browse the internet.
Due to the market dominance Windows has, it comes pre-installed on many devices. If you are purchasing a new device, there is a high chance that it will come with a Windows OS version installed. With the supremacy it has on the market, a vast majority of users are already accustomed to its interface.
Moreover, the easy-to-use toolbar and easy installation of programs make it an excellent choice for both new and old users alike.
3. Support
As Linux has a huge user base around the globe, there is massive online support available for Linux. The Linux OS community provides support to users through forums, question boards, and support websites.
Windows OS has easily accessible support through integrated and online help systems, dedicated websites, and forums. In addition, numerous videos and books about Windows are available online.
4. Variety
Linux is celebrated for being open-source with several modifications in existence. There are a lot of distributions available which are highly customizable, based on the needs of the user. If you have knowledge of code, you can even alter the code yourself and modify the OS. Some of the most popular customized Ubuntu environments are Gnome, Cinnamon, Deepin, and LXQT.
In the Windows OS, customization is not as easy and a comparatively fewer number of customizations are available. Users mostly have what they get right out of the box, which may not be to everyone’s liking.
5. Speed
When it comes to speed, Linux trumps Windows by a great margin. Unlike Windows, Linux tends to minimize the ‘bogging’ when it comes to the use of multiple processes. The file system Ext4 in Linux does a commendable job at keeping the device efficient. Defragmentation is now dead and buried in Linux.
Windows OS can slow down to sometimes intolerable levels, which is somewhat inevitable over time. Memory and disk hogging is common when multiple processes are being used.
6. Privacy
Over the past few years, Windows has become increasingly advertisement driven. Users can opt out, but those concerned about privacy can find the experience grating. Many people are fond of the tools that Microsoft Windows offers, but they are intrusive regardless.
Linux users, on the other hand, have an OS that makes the privacy of its users a priority. Linux devices are also equipped with strong encryption, which means that users can be sure of better security and less intrusion from third-party applications.
7. Security
Linux is also considerably more secure than Windows. Attack vectors are still being discovered in Linux, due to its open-source technology. However, anyone can review the vulnerabilities, which makes the identification and resolving process faster and easier.
Meanwhile, Windows has taken long strides in improving its security system over the years with a 5% decrease between 2020 and 2021, but it is still the primary target for malicious hackers. Due to its large user base, Microsoft is always vulnerable to new threats and when they do appear, they affect many users.
8. Run Level
A run level is the state of init (the first process started during booting) and the whole system which defines what system services are in operation. The run levels are identified using numbers. You can change run levels and the services that can run inside them, which offers more control over the system.
While Linux can stop at different run levels, Windows will reboot at run level 3 for an administrator to fix the encountered problem.
9. Command Line Usage
In the Linux OS, the command line is a very handy and powerful tool used for administration and daily tasks.
In Windows, the ‘cmd’ command can be used to open a command line and perform a basic set of operations, while PowerShell offers more flexibility.
Recommended Linux Command Line Course:
10. Reliability
The Linux OS has a strong focus on system security, process management, and uptime. Linux has compromised on this, and is the most secure and reliable OS available.
On the contrary, even though Microsoft has made improvements in reliability over the years, it is nowhere near Linux. It has let go of many features for the sake of user-friendliness and ease of access, which may lead to system instability and security vulnerabilities.
11. System Updates
In the Linux OS, the user has full control over when and what to install updates. Windows is infamous for its somewhat random updates which can pop up at inconvenient times. For the lay user, it may not matter, but those with more computer experience would prefer Linux for the flexibility.
12. Compatibility
Windows wins this category hands down, as there are many more apps that work on Windows than Linux. Most developers want to develop on Windows because of its large userbase, and legacy apps also have a lot of support.
Linux is not so lucky when it comes to compatibility.
13. Gaming
Windows wins the gaming race by a large margin. Steam, Epic, and many other clients are available to Windows users which provide them with the opportunity to play with both AAA titles and small indie games. Graphics card manufacturers focus their support on Windows due to the larger user base.
While Linux is slowly climbing its way into the gaming market, with the introduction of beta support for many games, it is hard to imagine that it will catch up with Windows. If you purchase a Linux OS, you will be missing out on a large number of games.
Linux Mastery: Master the Linux Command Line in 11.5 Hours
Windows vs Linux: Which is Better?
With the debate of Windows vs Linux operating systems explained briefly, you should be in a better position to choose between the two. It’s not that one is better than the other, it’s just that they both have different audiences in mind. Many people may ask is Linux better than Windows, or vice versa, but pick for yourself based on the information above.
Do you feel we left out any useful points in the article? Let us know in the comment section below. You can also check out some Linux System Administration Tutorials and Courses, which might help you get started with Linux.
Frequently Asked Questions
1. Is Linux or Windows Better?
There is no straight answer to this question, as both serve a different audience. If you want something that is easy to use and runs a lot of apps straight out of the box, choose Windows. If security, customizability, and reliability are important to you, choose Linux.
2. What is the Main Difference Between Linux and Windows?
The main differences between Linux and Windows are that Linux is more secure, private, and reliable. Windows is more intuitive and has support for more apps and hardware.
3. What Can Linux Do that Windows Can’t?
There are lots of such things. One major feature is that Linux does not need to restart the machine in order to install an update if the changes are minor.
4. Can Linux Run Windows Programs?
Yes, you can run Windows programs on Linux through third-party software. Bear in mind you cannot run all Windows programs, only a select few.
People are also Reading:
- Linux Cheat Sheet
- Best Linux Certifications
- Linux Interview Questions
- Data Science Interview Questions
- AWS Interview Questions
- Difference between Structure and Union
- Difference between float and double
- Data types in C
- Basic Linux Commands which you need to know
- Top DevOps Interview Questions and Answers
An operating system (OS) is system software that manages computer hardware, software resources, and provides common services for computer programs.
Time-sharing operating systems schedule tasks for efficient use of the system and may also include accounting software for cost allocation of processor time, mass storage, printing, and other resources.
For hardware functions such as input and output and memory allocation, the operating system acts as an intermediary between programs and the computer hardware,[1][2] although the application code is usually executed directly by the hardware and frequently makes system calls to an OS function or is interrupted by it. Operating systems are found on many devices that contain a computer – from cellular phones and video game consoles to web servers and supercomputers.
The dominant general-purpose personal computer operating system is Microsoft Windows with a market share of around 74.99%. macOS by Apple Inc. is in second place (14.84%), and the varieties of Linux are collectively in third place (2.81%).[3] In the mobile sector (including smartphones and tablets), Android’s share is 70.82% in the year 2020.[4] According to third quarter 2016 data, Android’s share on smartphones is dominant with 87.5 percent with a growth rate of 10.3 percent per year, followed by Apple’s iOS with 12.1 percent with per year decrease in market share of 5.2 percent, while other operating systems amount to just 0.3 percent.[5] Linux distributions are dominant in the server and supercomputing sectors. Other specialized classes of operating systems (special-purpose operating systems),[6][7] such as embedded and real-time systems, exist for many applications. Security-focused operating systems also exist. Some operating systems have low system requirements (e.g. light-weight Linux distribution). Others may have higher system requirements.
Some operating systems require installation or may come pre-installed with purchased computers (OEM-installation), whereas others may run directly from media (i.e. live CD) or flash memory (i.e. USB stick).
Types of operating systems
Single-tasking and multi-tasking
A single-tasking system can only run one program at a time, while a multi-tasking operating system allows more than one program to be running concurrently. This is achieved by time-sharing, where the available processor time is divided between multiple processes. These processes are each interrupted repeatedly in time slices by a task-scheduling subsystem of the operating system. Multi-tasking may be characterized in preemptive and cooperative types. In preemptive multitasking, the operating system slices the CPU time and dedicates a slot to each of the programs. Unix-like operating systems, such as Linux—as well as non-Unix-like, such as AmigaOS—support preemptive multitasking. Cooperative multitasking is achieved by relying on each process to provide time to the other processes in a defined manner. 16-bit versions of Microsoft Windows used cooperative multi-tasking; 32-bit versions of both Windows NT and Win9x used preemptive multi-tasking.
Single- and multi-user
Single-user operating systems have no facilities to distinguish users but may allow multiple programs to run in tandem.[8] A multi-user operating system extends the basic concept of multi-tasking with facilities that identify processes and resources, such as disk space, belonging to multiple users, and the system permits multiple users to interact with the system at the same time. Time-sharing operating systems schedule tasks for efficient use of the system and may also include accounting software for cost allocation of processor time, mass storage, printing, and other resources to multiple users.
Distributed
A distributed operating system manages a group of distinct, networked computers and makes them appear to be a single computer, as all computations are distributed (divided amongst the constituent computers).[9]
Embedded
Embedded operating systems are designed to be used in embedded computer systems. They are designed to operate on small machines with less autonomy (e.g. PDAs). They are very compact and extremely efficient by design and are able to operate with a limited amount of resources. Windows CE and Minix 3 are some examples of embedded operating systems.
Real-time
A real-time operating system is an operating system that guarantees to process events or data by a specific moment in time. A real-time operating system may be single- or multi-tasking, but when multitasking, it uses specialized scheduling algorithms so that a deterministic nature of behavior is achieved. Such an event-driven system switches between tasks based on their priorities or external events, whereas time-sharing operating systems switch tasks based on clock interrupts.
Library
A library operating system is one in which the services that a typical operating system provides, such as networking, are provided in the form of libraries and composed with the application and configuration code to construct a unikernel: a specialized, single address space, machine image that can be deployed to cloud or embedded environments[further explanation needed].
History
Early computers were built to perform a series of single tasks, like a calculator. Basic operating system features were developed in the 1950s, such as resident monitor functions that could automatically run different programs in succession to speed up processing. Operating systems did not exist in their modern and more complex forms until the early 1960s.[10] Hardware features were added, that enabled use of runtime libraries, interrupts, and parallel processing. When personal computers became popular in the 1980s, operating systems were made for them similar in concept to those used on larger computers.
In the 1940s, the earliest electronic digital systems had no operating systems. Electronic systems of this time were programmed on rows of mechanical switches or by jumper wires on plugboards. These were special-purpose systems that, for example, generated ballistics tables for the military or controlled the printing of payroll checks from data on punched paper cards. After programmable general-purpose computers were invented, machine languages(consisting of strings of the binary digits 0 and 1 on punched paper tape) were introduced that sped up the programming process (Stern, 1981).[full citation needed]
In the early 1950s, a computer could execute only one program at a time. Each user had sole use of the computer for a limited period and would arrive at a scheduled time with their program and data on punched paper cards or punched tape. The program would be loaded into the machine, and the machine would be set to work until the program completed or crashed. Programs could generally be debugged via a front panel using toggle switches and panel lights. It is said that Alan Turing was a master of this on the early Manchester Mark 1 machine, and he was already deriving the primitive conception of an operating system from the principles of the universal Turing machine.[10]
Later machines came with libraries of programs, which would be linked to a user’s program to assist in operations such as input and output and compiling (generating machine code from human-readable symbolic code). This was the genesis of the modern-day operating system. However, machines still ran a single job at a time. At Cambridge University in England, the job queue was at one time a washing line (clothesline) from which tapes were hung with different colored clothes-pegs to indicate job priority.[citation needed]
By the late 1950s, programs that one would recognize as an operating system were beginning to appear. Often pointed to as the earliest recognizable example is GM-NAA I/O, released in 1956 on the IBM 704. The first known example that actually referred to itself was the SHARE Operating System, a development of GM-NAA I/O, released in 1959. In a May 1960 paper describing the system, George Ryckman noted:
The development of computer operating systems have materially aided the problem of getting a program or series of programs on and off the computer efficiently.[11]
One of the more famous examples that is often found in discussions of early systems is the Atlas Supervisor, running on the Atlas in 1962.[12] It was referred to as such in a December 1961 article describing the system, but the context of «the Operating System» is more along the lines of «the system operates in the fashion». The Atlas team itself used the term «supervisor»,[13] which was widely used along with «monitor». Brinch Hansen described it as «the most significant breakthrough in the history of operating systems.»[14]
Mainframes
Through the 1950s, many major features were pioneered in the field of operating systems on mainframe computers, including batch processing, input/output interrupting, buffering, multitasking, spooling, runtime libraries, link-loading, and programs for sorting records in files. These features were included or not included in application software at the option of application programmers, rather than in a separate operating system used by all applications. In 1959, the SHARE Operating System was released as an integrated utility for the IBM 704, and later in the 709 and 7090 mainframes, although it was quickly supplanted by IBSYS/IBJOB on the 709, 7090 and 7094, which in turn influenced the later 7040-PR-150 (7040/7044) and 1410-PR-155 (1410/7010) operating systems.
During the 1960s, IBM’s OS/360 introduced the concept of a single OS spanning an entire product line, which was crucial for the success of the System/360 machines. IBM’s current mainframe operating systems are distant descendants of this original system and modern machines are backward compatible with applications written for OS/360.[citation needed]
OS/360 also pioneered the concept that the operating system keeps track of all of the system resources that are used, including program and data space allocation in main memory and file space in secondary storage, and file locking during updates. When a process is terminated for any reason, all of these resources are re-claimed by the operating system.
The alternative CP-67 system for the S/360-67 started a whole line of IBM operating systems focused on the concept of virtual machines. Other operating systems used on IBM S/360 series mainframes included systems developed by IBM: DOS/360[a] (Disk Operating System), TSS/360 (Time Sharing System), TOS/360 (Tape Operating System), BOS/360 (Basic Operating System), and ACP (Airline Control Program), as well as a few non-IBM systems: MTS (Michigan Terminal System), MUSIC (Multi-User System for Interactive Computing), and ORVYL (Stanford Timesharing System).
Control Data Corporation developed the SCOPE operating system in the 1960s, for batch processing. In cooperation with the University of Minnesota, the Kronos and later the NOS operating systems were developed during the 1970s, which supported simultaneous batch and timesharing use. Like many commercial timesharing systems, its interface was an extension of the Dartmouth BASIC operating systems, one of the pioneering efforts in timesharing and programming languages. In the late 1970s, Control Data and the University of Illinois developed the PLATO operating system, which used plasma panel displays and long-distance time sharing networks. Plato was remarkably innovative for its time, featuring real-time chat, and multi-user graphical games.
In 1961, Burroughs Corporation introduced the B5000 with the MCP (Master Control Program) operating system. The B5000 was a stack machine designed to exclusively support high-level languages with no assembler;[b] indeed, the MCP was the first OS to be written exclusively in a high-level language (ESPOL, a dialect of ALGOL). MCP also introduced many other ground-breaking innovations, such as being the first commercial implementation of virtual memory. During development of the AS/400, IBM made an approach to Burroughs to license MCP to run on the AS/400 hardware. This proposal was declined by Burroughs management to protect its existing hardware production. MCP is still in use today in the Unisys company’s MCP/ClearPath line of computers.
UNIVAC, the first commercial computer manufacturer, produced a series of EXEC operating systems.[15][16][17] Like all early main-frame systems, this batch-oriented system managed magnetic drums, disks, card readers and line printers. In the 1970s, UNIVAC produced the Real-Time Basic (RTB) system to support large-scale time sharing, also patterned after the Dartmouth BC system.
General Electric developed General Electric Comprehensive Operating Supervisor (GECOS), which primarily supported batch processing. After its acquisition by Honeywell, it was renamed General Comprehensive Operating System (GCOS).
Bell Labs,[c] General Electric and MIT developed Multiplexed Information and Computing Service (Multics), which introduced the concept of ringed security privilege levels.
Digital Equipment Corporation developed many operating systems for its various computer lines, including TOPS-10 and TOPS-20 time-sharing systems for the 36-bit PDP-10 class systems. Before the widespread use of UNIX, TOPS-10 was a particularly popular system in universities, and in the early ARPANET community. RT-11 was a single-user real-time OS for the PDP-11 class minicomputer, and RSX-11 was the corresponding multi-user OS.
From the late 1960s through the late 1970s, several hardware capabilities evolved that allowed similar or ported software to run on more than one system. Early systems had utilized microprogramming to implement features on their systems in order to permit different underlying computer architectures to appear to be the same as others in a series. In fact, most 360s after the 360/40 (except the 360/44, 360/75, 360/91, 360/95 and 360/195) were microprogrammed implementations.
The enormous investment in software for these systems made since the 1960s caused most of the original computer manufacturers to continue to develop compatible operating systems along with the hardware. Notable supported mainframe operating systems include:
- Burroughs MCP – B5000, 1961 to Unisys Clearpath/MCP, present
- IBM OS/360 – IBM System/360, 1966 to IBM z/OS, present
- IBM CP-67 – IBM System/360, 1967 to IBM z/VM
- UNIVAC EXEC 8 – UNIVAC 1108, 1967, to OS 2200 Unisys Clearpath Dorado, present
Microcomputers
PC DOS was an early personal computer OS that featured a command-line interface.
The first microcomputers did not have the capacity or need for the elaborate operating systems that had been developed for mainframes and minis; minimalistic operating systems were developed, often loaded from ROM and known as monitors. One notable early disk operating system was CP/M, which was supported on many early microcomputers and was closely imitated by Microsoft’s MS-DOS, which became widely popular as the operating system chosen for the IBM PC (IBM’s version of it was called IBM DOS or PC DOS). In the 1980s, Apple Computer Inc. (now Apple Inc.) abandoned its popular Apple II series of microcomputers to introduce the Apple Macintosh computer with an innovative graphical user interface (GUI) to the Mac OS.
The introduction of the Intel 80386 CPU chip in October 1985,[18] with 32-bit architecture and paging capabilities, provided personal computers with the ability to run multitasking operating systems like those of earlier minicomputers and mainframes. Microsoft responded to this progress by hiring Dave Cutler, who had developed the VMS operating system for Digital Equipment Corporation. He would lead the development of the Windows NT operating system, which continues to serve as the basis for Microsoft’s operating systems line. Steve Jobs, a co-founder of Apple Inc., started NeXT Computer Inc., which developed the NEXTSTEP operating system. NEXTSTEP would later be acquired by Apple Inc. and used, along with code from FreeBSD as the core of Mac OS X (macOS after latest name change).
The GNU Project was started by activist and programmer Richard Stallman with the goal of creating a complete free software replacement to the proprietary UNIX operating system. While the project was highly successful in duplicating the functionality of various parts of UNIX, development of the GNU Hurd kernel proved to be unproductive. In 1991, Finnish computer science student Linus Torvalds, with cooperation from volunteers collaborating over the Internet, released the first version of the Linux kernel. It was soon merged with the GNU user space components and system software to form a complete operating system. Since then, the combination of the two major components has usually been referred to as simply «Linux» by the software industry, a naming convention that Stallman and the Free Software Foundation remain opposed to, preferring the name GNU/Linux. The Berkeley Software Distribution, known as BSD, is the UNIX derivative distributed by the University of California, Berkeley, starting in the 1970s. Freely distributed and ported to many minicomputers, it eventually also gained a following for use on PCs, mainly as FreeBSD, NetBSD and OpenBSD.
Examples
Unix and Unix-like operating systems
Main article: Unix
Evolution of Unix systems
Unix was originally written in assembly language.[19] Ken Thompson wrote B, mainly based on BCPL, based on his experience in the MULTICS project. B was replaced by C, and Unix, rewritten in C, developed into a large, complex family of inter-related operating systems which have been influential in every modern operating system (see History).
The Unix-like family is a diverse group of operating systems, with several major sub-categories including System V, BSD, and Linux. The name «UNIX» is a trademark of The Open Group which licenses it for use with any operating system that has been shown to conform to their definitions. «UNIX-like» is commonly used to refer to the large set of operating systems which resemble the original UNIX.
Unix-like systems run on a wide variety of computer architectures. They are used heavily for servers in business, as well as workstations in academic and engineering environments. Free UNIX variants, such as Linux and BSD, are popular in these areas.
Five operating systems are certified by The Open Group (holder of the Unix trademark) as Unix. HP’s HP-UX and IBM’s AIX are both descendants of the original System V Unix and are designed to run only on their respective vendor’s hardware. In contrast, Sun Microsystems’s Solaris can run on multiple types of hardware, including x86 and SPARC servers, and PCs. Apple’s macOS, a replacement for Apple’s earlier (non-Unix) classic Mac OS, is a hybrid kernel-based BSD variant derived from NeXTSTEP, Mach, and FreeBSD. IBM’s z/OS UNIX System Services includes a shell and utilities based on Mortice Kerns’ InterOpen products.
Unix interoperability was sought by establishing the POSIX standard. The POSIX standard can be applied to any operating system, although it was originally created for various Unix variants.
BSD and its descendants
A subgroup of the Unix family is the Berkeley Software Distribution family, which includes FreeBSD, NetBSD, and OpenBSD. These operating systems are most commonly found on webservers, although they can also function as a personal computer OS. The Internet owes much of its existence to BSD, as many of the protocols now commonly used by computers to connect, send and receive data over a network were widely implemented and refined in BSD. The World Wide Web was also first demonstrated on a number of computers running an OS based on BSD called NeXTSTEP.
In 1974, University of California, Berkeley installed its first Unix system. Over time, students and staff in the computer science department there began adding new programs to make things easier, such as text editors. When Berkeley received new VAX computers in 1978 with Unix installed, the school’s undergraduates modified Unix even more in order to take advantage of the computer’s hardware possibilities. The Defense Advanced Research Projects Agency of the US Department of Defense took interest, and decided to fund the project. Many schools, corporations, and government organizations took notice and started to use Berkeley’s version of Unix instead of the official one distributed by AT&T.
Steve Jobs, upon leaving Apple Inc. in 1985, formed NeXT Inc., a company that manufactured high-end computers running on a variation of BSD called NeXTSTEP. One of these computers was used by Tim Berners-Lee as the first webserver to create the World Wide Web.
Developers like Keith Bostic encouraged the project to replace any non-free code that originated with Bell Labs. Once this was done, however, AT&T sued. After two years of legal disputes, the BSD project spawned a number of free derivatives, such as NetBSD and FreeBSD (both in 1993), and OpenBSD (from NetBSD in 1995).
macOS
macOS (formerly «Mac OS X» and later «OS X») is a line of open core graphical operating systems developed, marketed, and sold by Apple Inc., the latest of which is pre-loaded on all currently shipping Macintosh computers. macOS is the successor to the original classic Mac OS, which had been Apple’s primary operating system since 1984. Unlike its predecessor, macOS is a UNIX operating system built on technology that had been developed at NeXT through the second half of the 1980s and up until Apple purchased the company in early 1997.
The operating system was first released in 1999 as Mac OS X Server 1.0, followed in March 2001 by a client version (Mac OS X v10.0 «Cheetah»). Since then, six more distinct «client» and «server» editions of macOS have been released, until the two were merged in OS X 10.7 «Lion».
Prior to its merging with macOS, the server edition – macOS Server – was architecturally identical to its desktop counterpart and usually ran on Apple’s line of Macintosh server hardware. macOS Server included work group management and administration software tools that provide simplified access to key network services, including a mail transfer agent, a Samba server, an LDAP server, a domain name server, and others. With Mac OS X v10.7 Lion, all server aspects of Mac OS X Server have been integrated into the client version and the product re-branded as «OS X» (dropping «Mac» from the name). The server tools are now offered as an application.[20]
z/OS UNIX System Services
First introduced as the OpenEdition upgrade to MVS/ESA System Product Version 4 Release 3, announced[21] February 1993 with support for POSIX and other standards.[22][23][24] z/OS UNIX System Services is built on top of MVS services and cannot run independently. While IBM initially introduced OpenEdition to satisfy FIPS requirements, several z/OS component now require UNIX services, e.g., TCP/IP.
Linux
The Linux kernel originated in 1991, as a project of Linus Torvalds, while a university student in Finland. He posted information about his project on a newsgroup for computer students and programmers, and received support and assistance from volunteers who succeeded in creating a complete and functional kernel.
Linux is Unix-like, but was developed without any Unix code, unlike BSD and its variants. Because of its open license model, the Linux kernel code is available for study and modification, which resulted in its use on a wide range of computing machinery from supercomputers to smartwatches. Although estimates suggest that Linux is used on only 2.81% of all «desktop» (or laptop) PCs,[3] it has been widely adopted for use in servers[29] and embedded systems[30] such as cell phones. Linux has superseded Unix on many platforms and is used on most supercomputers including the top 385.[31] Many of the same computers are also on Green500 (but in different order), and Linux runs on the top 10. Linux is also commonly used on other small energy-efficient computers, such as smartphones and smartwatches. The Linux kernel is used in some popular distributions, such as Red Hat, Debian, Ubuntu, Linux Mint and Google’s Android, ChromeOS, and ChromiumOS.
Microsoft Windows
Microsoft Windows is a family of proprietary operating systems designed by Microsoft Corporation and primarily targeted to Intel architecture based computers, with an estimated 88.9 percent total usage share on Web connected computers.[32][33][34][35] The latest version is Windows 11.
In 2011, Windows 7 overtook Windows XP as the most common version in use.[36][37][38]
Microsoft Windows was first released in 1985, as an operating environment running on top of MS-DOS, which was the standard operating system shipped on most Intel architecture personal computers at the time. In 1995, Windows 95 was released which only used MS-DOS as a bootstrap. For backwards compatibility, Win9x could run real-mode MS-DOS[39][40] and 16-bit Windows 3.x[41] drivers. Windows ME, released in 2000, was the last version in the Win9x family. Later versions have all been based on the Windows NT kernel. Current client versions of Windows run on IA-32, x86-64 and ARM microprocessors.[42] In addition Itanium is still supported in older server version Windows Server 2008 R2. In the past, Windows NT supported additional architectures.
Server editions of Windows are widely used, however, Windows’ usage on servers is not as widespread as on personal computers as Windows competes against Linux and BSD for server market share.[43][44]
ReactOS is a Windows-alternative operating system, which is being developed on the principles of Windows – without using any of Microsoft’s code.
Other
There have been many operating systems that were significant in their day but are no longer so, such as AmigaOS; OS/2 from IBM and Microsoft; classic Mac OS, the non-Unix precursor to Apple’s macOS; BeOS; XTS-300; RISC OS; MorphOS; Haiku; BareMetal and FreeMint. Some are still used in niche markets and continue to be developed as minority platforms for enthusiast communities and specialist applications.
The z/OS operating system for IBM z/Architecture mainframe computers is still being used and developed, and
OpenVMS, formerly from DEC, is still under active development by VMS Software Inc. The IBM i operating system for IBM AS/400 and IBM Power Systems midrange computers is also still being used and developed.
Yet other operating systems are used almost exclusively in academia, for operating systems education or to do research on operating system concepts. A typical example of a system that fulfills both roles is MINIX, while for example Singularity is used purely for research. Another example is the Oberon System designed at ETH Zürich by Niklaus Wirth, Jürg Gutknecht and a group of students at the former Computer Systems Institute in the 1980s. It was used mainly for research, teaching, and daily work in Wirth’s group.
Other operating systems have failed to win significant market share, but have introduced innovations that have influenced mainstream operating systems, not least Bell Labs’ Plan 9.
Components
The components of an operating system all exist in order to make the different parts of a computer work together. All user software needs to go through the operating system in order to use any of the hardware, whether it be as simple as a mouse or keyboard or as complex as an Internet component.
Kernel
A kernel connects the application software to the hardware of a computer.
With the aid of firmware and device drivers, the kernel provides the most basic level of control over all of the computer’s hardware devices. It manages memory access for programs in the RAM, it determines which programs get access to which hardware resources, it sets up or resets the CPU’s operating states for optimal operation at all times, and it organizes the data for long-term non-volatile storage with file systems on such media as disks, tapes, flash memory, etc.
Program execution
The operating system provides an interface between an application program and the computer hardware, so that an application program can interact with the hardware only by obeying rules and procedures programmed into the operating system. The operating system is also a set of services which simplify development and execution of application programs. Executing an application program typically involves the creation of a process by the operating system kernel, which assigns memory space and other resources, establishes a priority for the process in multi-tasking systems, loads program binary code into memory, and initiates execution of the application program, which then interacts with the user and with hardware devices. However, in some systems an application can request that the operating system execute another application within the same process, either as a subroutine or in a separate thread, e.g., the LINK and ATTACH facilities of OS/360 and successors..
Interrupts
An interrupt (also known as abort, exception, fault, signal[45] and trap)[46] provides an efficient way for most operating systems to react to the environment. Interrupts cause the central processing unit (CPU) to have a control flow change away from the currently running program to an interrupt handler, also known as an interrupt service routine (ISR).[47][48] An interrupt service routine may cause the central processing unit (CPU) to have a context switch[49] [d]. The details of how a computer processes an interrupt vary from architecture to architecture, and the details of how interrupt service routines behave vary from operating system to operating system.[50] However, several interrupt functions are common.[50] The architecture and operating system must:[50]
- transfer control to an interrupt service routine.
- save the state of the currently running process.
- restore the state after the interrupt is serviced.
Software interrupt
A software interrupt is a message to a process that an event has occurred.[45] This contrasts with a hardware interrupt — which is a message to the central processing unit (CPU) that an event has occurred.[51] Software interrupts are similar to hardware interrupts — there is a change away from the currently running process.[52] Similarly, both hardware and software interrupts execute an interrupt service routine.
Software interrupts may be normally occurring events. It is expected that a time slice will occur, so the kernel will have to perform a context switch.[53] A computer program may set a timer to go off after a few seconds in case too much data causes an algorithm to take too long.[54]
Software interrupts may be error conditions, such as a malformed machine instruction.[54] However, the most common error conditions are division by zero and accessing an invalid memory address.[54]
Users can send messages to the kernel to modify the behavior of a currently running process.[54] For example, in the command-line environment, pressing the interrupt character (usually Control-C) might terminate the currently running process.[54]
To generate software interrupts for x86 CPUs, the INT assembly language instruction is available.[55] The syntax is INT X, where X is the offset number (in hexadecimal format) to the interrupt vector table.
Signal
To generate software interrupts in Unix-like operating systems, the kill(pid,signum) system call will send a signal to another process.[56] pid is the process identifier of the receiving process. signum is the signal number (in mnemonic format)[e] to be sent. (The abrasive name of kill was chosen because early implementations only terminated the process.)[57]
In Unix-like operating systems, signals inform processes of the occurrence of asynchronous events.[56] To communicate asynchronously, interrupts are required.[58] One reason a process needs to asynchronously communicate to another process solves a variation of the classic reader/writer problem.[59] The writer receives a pipe from the shell for its output to be sent to the reader’s input stream.[60] The command-line syntax is alpha | bravo. alpha will write to the pipe when its computation is ready and then sleep in the wait queue.[61] bravo will then be moved to the ready queue and soon will read from its input stream.[62] The kernel will generate software interrupts to coordinate the piping.[62]
Signals may be classified into 7 categories.[56] The categories are:
- when a process finishes normally.
- when a process has an error exception.
- when a process runs out of a system resource.
- when a process executes an illegal instruction.
- when a process sets an alarm event.
- when a process is aborted from the keyboard.
- when a process has a tracing alert for debugging.
Hardware interrupt
Input/Output (I/O) devices are slower than the CPU. Therefore, it would slow down the computer if the CPU had to wait for each I/O to finish. Instead, a computer may implement interrupts for I/O completion, avoiding the need for polling or busy waiting.[63]
Some computers require an interrupt for each character or word, costing a significant amount of CPU time. Direct memory access (DMA) is an architecture feature to allow devices to bypass the CPU and access main memory directly.[64] (Separate from the architecture, a device may perform direct memory access[f] to and from main memory either directly or via a bus.)[65][g]
Input/Output
Interrupt-driven I/O
|
This section needs expansion. You can help by adding to it. (April 2022) |
When a computer user types a key on the keyboard, typically the character appears immediately on the screen. Likewise, when a user moves a mouse, the cursor immediately moves across the screen. Each keystroke and mouse movement generates an interrupt called Interrupt-driven I/O. An interrupt-driven I/O occurs when a process causes an interrupt for every character[65] or word[66] transmitted.
Direct Memory Access
Devices such as hard disk drives, solid state drives, and magnetic tape drives can transfer data at a rate high enough that interrupting the CPU for every byte or word transferred, and having the CPU transfer the byte or word between the device and memory, would require too much CPU time. Data is, instead, transferred between the device and memory independently of the CPU by hardware such as a channel or a direct memory access controller; an interrupt is delivered only when all the data is transferred.[67]
If a computer program executes a system call to perform a block I/O write operation, then the system call might execute the following instructions:
- Set the contents of the CPU’s registers (including the program counter) into the process control block.[68]
- Create an entry in the device-status table.[69] The operating system maintains this table to keep track of which processes are waiting for which devices. One field in the table is the memory address of the process control block.
- Place all the characters to be sent to the device into a memory buffer.[58]
- Set the memory address of the memory buffer to a predetermined device register.[70]
- Set the buffer size (an integer) to another predetermined register.[70]
- Execute the machine instruction to begin the writing.
- Perform a context switch to the next process in the ready queue.
While the writing takes place, the operating system will context switch to other processes as normal. When the device finishes writing, the device will interrupt the currently running process by asserting an interrupt request. The device will also place an integer onto the data bus.[71] Upon accepting the interrupt request, the operating system will:
- Push the contents of the program counter (a register) followed by the status register onto the call stack.[50]
- Push the contents of the other registers onto the call stack. (Alternatively, the contents of the registers may be placed in a system table.)[71]
- Read the integer from the data bus. The integer is an offset to the interrupt vector table. The vector table’s instructions will then:
-
- Access the device-status table.
- Extract the process control block.
- Perform a context switch back to the writing process.
When the writing process has its time slice expired, the operating system will:[72]
- Pop from the call stack the registers other than the status register and program counter.
- Pop from the call stack the status register.
- Pop from the call stack the address of the next instruction, and set it back into the program counter.
With the program counter now reset, the interrupted process will resume its time slice.[50]
Modes
Privilege rings for the x86 microprocessor architecture available in protected mode. Operating systems determine which processes run in each mode.
Modern computers support multiple modes of operation. CPUs with this capability offer at least two modes: user mode and supervisor mode. In general terms, supervisor mode operation allows unrestricted access to all machine resources, including all MPU instructions. User mode operation sets limits on instruction use and typically disallows direct access to machine resources. CPUs might have other modes similar to user mode as well, such as the virtual modes in order to emulate older processor types, such as 16-bit processors on a 32-bit one, or 32-bit processors on a 64-bit one.
At power-on or reset, the system begins in supervisor mode. Once an operating system kernel has been loaded and started, the boundary between user mode and supervisor mode (also known as kernel mode) can be established.
Supervisor mode is used by the kernel for low level tasks that need unrestricted access to hardware, such as controlling how memory is accessed, and communicating with devices such as disk drives and video display devices. User mode, in contrast, is used for almost everything else. Application programs, such as word processors and database managers, operate within user mode, and can only access machine resources by turning control over to the kernel, a process which causes a switch to supervisor mode. Typically, the transfer of control to the kernel is achieved by executing a software interrupt instruction, such as the Motorola 68000 TRAP instruction. The software interrupt causes the processor to switch from user mode to supervisor mode and begin executing code that allows the kernel to take control.
In user mode, programs usually have access to a restricted set of processor instructions, and generally cannot execute any instructions that could potentially cause disruption to the system’s operation. In supervisor mode, instruction execution restrictions are typically removed, allowing the kernel unrestricted access to all machine resources.
The term «user mode resource» generally refers to one or more CPU registers, which contain information that the running program isn’t allowed to alter. Attempts to alter these resources generally cause a switch to supervisor mode, where the operating system can deal with the illegal operation the program was attempting; for example, by forcibly terminating («killing») the program.
Memory management
Among other things, a multiprogramming operating system kernel must be responsible for managing all system memory which is currently in use by the programs. This ensures that a program does not interfere with memory already in use by another program. Since programs time share, each program must have independent access to memory.
Cooperative memory management, used by many early operating systems, assumes that all programs make voluntary use of the kernel’s memory manager, and do not exceed their allocated memory. This system of memory management is almost never seen any more, since programs often contain bugs which can cause them to exceed their allocated memory. If a program fails, it may cause memory used by one or more other programs to be affected or overwritten. Malicious programs or viruses may purposefully alter another program’s memory, or may affect the operation of the operating system itself. With cooperative memory management, it takes only one misbehaved program to crash the system.
Memory protection enables the kernel to limit a process’ access to the computer’s memory. Various methods of memory protection exist, including memory segmentation and paging. All methods require some level of hardware support (such as the 80286 MMU), which doesn’t exist in all computers.
In both segmentation and paging, certain protected mode registers specify to the CPU what memory address it should allow a running program to access. Attempts to access other addresses trigger an interrupt, which causes the CPU to re-enter supervisor mode, placing the kernel in charge. This is called a segmentation violation or Seg-V for short, and since it is both difficult to assign a meaningful result to such an operation, and because it is usually a sign of a misbehaving program, the kernel generally resorts to terminating the offending program, and reports the error.
Windows versions 3.1 through ME had some level of memory protection, but programs could easily circumvent the need to use it. A general protection fault would be produced, indicating a segmentation violation had occurred; however, the system would often crash anyway.
Virtual memory
Many operating systems can «trick» programs into using memory scattered around the hard disk and RAM as if it is one continuous chunk of memory, called virtual memory.
The use of virtual memory addressing (such as paging or segmentation) means that the kernel can choose what memory each program may use at any given time, allowing the operating system to use the same memory locations for multiple tasks.
If a program tries to access memory that isn’t in its current range of accessible memory, but nonetheless has been allocated to it, the kernel is interrupted in the same way as it would if the program were to exceed its allocated memory. (See section on memory management.) Under UNIX this kind of interrupt is referred to as a page fault.
When the kernel detects a page fault it generally adjusts the virtual memory range of the program which triggered it, granting it access to the memory requested. This gives the kernel discretionary power over where a particular application’s memory is stored, or even whether or not it has actually been allocated yet.
In modern operating systems, memory which is accessed less frequently can be temporarily stored on a disk or other media to make that space available for use by other programs. This is called swapping, as an area of memory can be used by multiple programs, and what that memory area contains can be swapped or exchanged on demand.
«Virtual memory» provides the programmer or the user with the perception that there is a much larger amount of RAM in the computer than is really there.[73]
Multitasking
Multitasking refers to the running of multiple independent computer programs on the same computer, giving the appearance that it is performing the tasks at the same time. Since most computers can do at most one or two things at one time, this is generally done via time-sharing, which means that each program uses a share of the computer’s time to execute.
An operating system kernel contains a scheduling program which determines how much time each process spends executing, and in which order execution control should be passed to programs. Control is passed to a process by the kernel, which allows the program access to the CPU and memory. Later, control is returned to the kernel through some mechanism, so that another program may be allowed to use the CPU. This so-called passing of control between the kernel and applications is called a context switch.
An early model which governed the allocation of time to programs was called cooperative multitasking. In this model, when control is passed to a program by the kernel, it may execute for as long as it wants before explicitly returning control to the kernel. This means that a malicious or malfunctioning program may not only prevent any other programs from using the CPU, but it can hang the entire system if it enters an infinite loop.
Modern operating systems extend the concepts of application preemption to device drivers and kernel code, so that the operating system has preemptive control over internal run-times as well.
The philosophy governing preemptive multitasking is that of ensuring that all programs are given regular time on the CPU. This implies that all programs must be limited in how much time they are allowed to spend on the CPU without being interrupted. To accomplish this, modern operating system kernels make use of a timed interrupt. A protected mode timer is set by the kernel which triggers a return to supervisor mode after the specified time has elapsed. (See above sections on Interrupts and Dual Mode Operation.)
On many single user operating systems cooperative multitasking is perfectly adequate, as home computers generally run a small number of well tested programs. AmigaOS is an exception, having preemptive multitasking from its first version. Windows NT was the first version of Microsoft Windows which enforced preemptive multitasking, but it didn’t reach the home user market until Windows XP (since Windows NT was targeted at professionals).
Disk access and file systems
File systems allow users and programs to organize and sort files on a computer, often through the use of directories (or «folders»).
Access to data stored on disks is a central feature of all operating systems. Computers store data on disks using files, which are structured in specific ways in order to allow for faster access, higher reliability, and to make better use of the drive’s available space. The specific way in which files are stored on a disk is called a file system, and enables files to have names and attributes. It also allows them to be stored in a hierarchy of directories or folders arranged in a directory tree.
Early operating systems generally supported a single type of disk drive and only one kind of file system. Early file systems were limited in their capacity, speed, and in the kinds of file names and directory structures they could use. These limitations often reflected limitations in the operating systems they were designed for, making it very difficult for an operating system to support more than one file system.
While many simpler operating systems support a limited range of options for accessing storage systems, operating systems like UNIX and Linux support a technology known as a virtual file system or VFS. An operating system such as UNIX supports a wide array of storage devices, regardless of their design or file systems, allowing them to be accessed through a common application programming interface (API). This makes it unnecessary for programs to have any knowledge about the device they are accessing. A VFS allows the operating system to provide programs with access to an unlimited number of devices with an infinite variety of file systems installed on them, through the use of specific device drivers and file system drivers.
A connected storage device, such as a hard drive, is accessed through a device driver. The device driver understands the specific language of the drive and is able to translate that language into a standard language used by the operating system to access all disk drives. On UNIX, this is the language of block devices.
When the kernel has an appropriate device driver in place, it can then access the contents of the disk drive in raw format, which may contain one or more file systems. A file system driver is used to translate the commands used to access each specific file system into a standard set of commands that the operating system can use to talk to all file systems. Programs can then deal with these file systems on the basis of filenames, and directories/folders, contained within a hierarchical structure. They can create, delete, open, and close files, as well as gather various information about them, including access permissions, size, free space, and creation and modification dates.
Various differences between file systems make supporting all file systems difficult. Allowed characters in file names, case sensitivity, and the presence of various kinds of file attributes makes the implementation of a single interface for every file system a daunting task. Operating systems tend to recommend using (and so support natively) file systems specifically designed for them; for example, NTFS in Windows and ReiserFS, Reiser4, ext3, ext4 and Btrfs in Linux. However, in practice, third party drivers are usually available to give support for the most widely used file systems in most general-purpose operating systems (for example, NTFS is available in Linux through NTFS-3g, and ext2/3 and ReiserFS are available in Windows through third-party software).
Support for file systems is highly varied among modern operating systems, although there are several common file systems which almost all operating systems include support and drivers for. Operating systems vary on file system support and on the disk formats they may be installed on. Under Windows, each file system is usually limited in application to certain media; for example, CDs must use ISO 9660 or UDF, and as of Windows Vista, NTFS is the only file system which the operating system can be installed on. It is possible to install Linux onto many types of file systems. Unlike other operating systems, Linux and UNIX allow any file system to be used regardless of the media it is stored in, whether it is a hard drive, a disc (CD, DVD…), a USB flash drive, or even contained within a file located on another file system.
Device drivers
A device driver is a specific type of computer software developed to allow interaction with hardware devices. Typically this constitutes an interface for communicating with the device, through the specific computer bus or communications subsystem that the hardware is connected to, providing commands to and/or receiving data from the device, and on the other end, the requisite interfaces to the operating system and software applications. It is a specialized hardware-dependent computer program which is also operating system specific that enables another program, typically an operating system or applications software package or computer program running under the operating system kernel, to interact transparently with a hardware device, and usually provides the requisite interrupt handling necessary for any necessary asynchronous time-dependent hardware interfacing needs.
The key design goal of device drivers is abstraction. Every model of hardware (even within the same class of device) is different. Newer models also are released by manufacturers that provide more reliable or better performance and these newer models are often controlled differently. Computers and their operating systems cannot be expected to know how to control every device, both now and in the future. To solve this problem, operating systems essentially dictate how every type of device should be controlled. The function of the device driver is then to translate these operating system mandated function calls into device specific calls. In theory a new device, which is controlled in a new manner, should function correctly if a suitable driver is available. This new driver ensures that the device appears to operate as usual from the operating system’s point of view.
Under versions of Windows before Vista and versions of Linux before 2.6, all driver execution was co-operative, meaning that if a driver entered an infinite loop it would freeze the system. More recent revisions of these operating systems incorporate kernel preemption, where the kernel interrupts the driver to give it tasks, and then separates itself from the process until it receives a response from the device driver, or gives it more tasks to do.
Networking
Currently most operating systems support a variety of networking protocols, hardware, and applications for using them. This means that computers running dissimilar operating systems can participate in a common network for sharing resources such as computing, files, printers, and scanners using either wired or wireless connections. Networks can essentially allow a computer’s operating system to access the resources of a remote computer to support the same functions as it could if those resources were connected directly to the local computer. This includes everything from simple communication, to using networked file systems or even sharing another computer’s graphics or sound hardware. Some network services allow the resources of a computer to be accessed transparently, such as SSH which allows networked users direct access to a computer’s command line interface.
Client/server networking allows a program on a computer, called a client, to connect via a network to another computer, called a server. Servers offer (or host) various services to other network computers and users. These services are usually provided through ports or numbered access points beyond the server’s IP address. Each port number is usually associated with a maximum of one running program, which is responsible for handling requests to that port. A daemon, being a user program, can in turn access the local hardware resources of that computer by passing requests to the operating system kernel.
Many operating systems support one or more vendor-specific or open networking protocols as well, for example, SNA on IBM systems, DECnet on systems from Digital Equipment Corporation, and Microsoft-specific protocols (SMB) on Windows. Specific protocols for specific tasks may also be supported such as NFS for file access. Protocols like ESound, or esd can be easily extended over the network to provide sound from local applications, on a remote system’s sound hardware.
Security
A computer being secure depends on a number of technologies working properly. A modern operating system provides access to a number of resources, which are available to software running on the system, and to external devices like networks via the kernel.[74]
The operating system must be capable of distinguishing between requests which should be allowed to be processed, and others which should not be processed. While some systems may simply distinguish between «privileged» and «non-privileged», systems commonly have a form of requester identity, such as a user name. To establish identity there may be a process of authentication. Often a username must be quoted, and each username may have a password. Other methods of authentication, such as magnetic cards or biometric data, might be used instead. In some cases, especially connections from the network, resources may be accessed with no authentication at all (such as reading files over a network share). Also covered by the concept of requester identity is authorization; the particular services and resources accessible by the requester once logged into a system are tied to either the requester’s user account or to the variously configured groups of users to which the requester belongs.[citation needed]
In addition to the allow or disallow model of security, a system with a high level of security also offers auditing options. These would allow tracking of requests for access to resources (such as, «who has been reading this file?»). Internal security, or security from an already running program is only possible if all possibly harmful requests must be carried out through interrupts to the operating system kernel. If programs can directly access hardware and resources, they cannot be secured.[citation needed]
External security involves a request from outside the computer, such as a login at a connected console or some kind of network connection. External requests are often passed through device drivers to the operating system’s kernel, where they can be passed onto applications, or carried out directly. Security of operating systems has long been a concern because of highly sensitive data held on computers, both of a commercial and military nature. The United States Government Department of Defense (DoD) created the Trusted Computer System Evaluation Criteria (TCSEC) which is a standard that sets basic requirements for assessing the effectiveness of security. This became of vital importance to operating system makers, because the TCSEC was used to evaluate, classify and select trusted operating systems being considered for the processing, storage and retrieval of sensitive or classified information.
Network services include offerings such as file sharing, print services, email, web sites, and file transfer protocols (FTP), most of which can have compromised security. At the front line of security are hardware devices known as firewalls or intrusion detection/prevention systems. At the operating system level, there are a number of software firewalls available, as well as intrusion detection/prevention systems. Most modern operating systems include a software firewall, which is enabled by default. A software firewall can be configured to allow or deny network traffic to or from a service or application running on the operating system. Therefore, one can install and be running an insecure service, such as Telnet or FTP, and not have to be threatened by a security breach because the firewall would deny all traffic trying to connect to the service on that port.
An alternative strategy, and the only sandbox strategy available in systems that do not meet the Popek and Goldberg virtualization requirements, is where the operating system is not running user programs as native code, but instead either emulates a processor or provides a host for a p-code based system such as Java.
Internal security is especially relevant for multi-user systems; it allows each user of the system to have private files that the other users cannot tamper with or read. Internal security is also vital if auditing is to be of any use, since a program can potentially bypass the operating system, inclusive of bypassing auditing.
User interface
A screenshot of the bash command line. Each command is typed out after the ‘prompt’, and then its output appears below, working its way down the screen. The current command prompt is at the bottom.
Every computer that is to be operated by an individual requires a user interface. The user interface is usually referred to as a shell and is essential if human interaction is to be supported. The user interface views the directory structure and requests services from the operating system that will acquire data from input hardware devices, such as a keyboard, mouse or credit card reader, and requests operating system services to display prompts, status messages and such on output hardware devices, such as a video monitor or printer. The two most common forms of a user interface have historically been the command-line interface, where computer commands are typed out line-by-line, and the graphical user interface, where a visual environment (most commonly a WIMP) is present.
Graphical user interfaces
A screenshot of the KDE Plasma 5 graphical user interface. Programs take the form of images on the screen, and the files, folders (directories), and applications take the form of icons and symbols. A mouse is used to navigate the computer.
Most of the modern computer systems support graphical user interfaces (GUI), and often include them. In some computer systems, such as the original implementation of the classic Mac OS, the GUI is integrated into the kernel.
While technically a graphical user interface is not an operating system service, incorporating support for one into the operating system kernel can allow the GUI to be more responsive by reducing the number of context switches required for the GUI to perform its output functions. Other operating systems are modular, separating the graphics subsystem from the kernel and the Operating System. In the 1980s UNIX, VMS and many others had operating systems that were built this way. Linux and macOS are also built this way. Modern releases of Microsoft Windows such as Windows Vista implement a graphics subsystem that is mostly in user-space; however the graphics drawing routines of versions between Windows NT 4.0 and Windows Server 2003 exist mostly in kernel space. Windows 9x had very little distinction between the interface and the kernel.
Many computer operating systems allow the user to install or create any user interface they desire. The X Window System in conjunction with GNOME or KDE Plasma 5 is a commonly found setup on most Unix and Unix-like (BSD, Linux, Solaris) systems. A number of Windows shell replacements have been released for Microsoft Windows, which offer alternatives to the included Windows shell, but the shell itself cannot be separated from Windows.
Numerous Unix-based GUIs have existed over time, most derived from X11. Competition among the various vendors of Unix (HP, IBM, Sun) led to much fragmentation, though an effort to standardize in the 1990s to COSE and CDE failed for various reasons, and were eventually eclipsed by the widespread adoption of GNOME and K Desktop Environment. Prior to free software-based toolkits and desktop environments, Motif was the prevalent toolkit/desktop combination (and was the basis upon which CDE was developed).
Graphical user interfaces evolve over time. For example, Windows has modified its user interface almost every time a new major version of Windows is released, and the Mac OS GUI changed dramatically with the introduction of Mac OS X in 1999.[75]
Real-time operating systems
A real-time operating system (RTOS) is an operating system intended for applications with fixed deadlines (real-time computing). Such applications include some small embedded systems, automobile engine controllers, industrial robots, spacecraft, industrial control, and some large-scale computing systems.
An early example of a large-scale real-time operating system was Transaction Processing Facility developed by American Airlines and IBM for the Sabre Airline Reservations System.
Embedded systems that have fixed deadlines use a real-time operating system such as VxWorks, PikeOS, eCos, QNX, MontaVista Linux and RTLinux. Windows CE is a real-time operating system that shares similar APIs to desktop Windows but shares none of desktop Windows’ codebase.[76] Symbian OS also has an RTOS kernel (EKA2) starting with version 8.0b.
Some embedded systems use operating systems such as Palm OS, BSD, and Linux, although such operating systems do not support real-time computing.
Operating system development as a hobby
A hobby operating system may be classified as one whose code has not been directly derived from an existing operating system, and has few users and active developers.[citation needed]
In some cases, hobby development is in support of a «homebrew» computing device, for example, a simple single-board computer powered by a 6502 microprocessor. Or, development may be for an architecture already in widespread use. Operating system development may come from entirely new concepts, or may commence by modeling an existing operating system. In either case, the hobbyist is her/his own developer, or may interact with a small and sometimes unstructured group of individuals who have like interests.
Examples of a hobby operating system include Syllable and TempleOS.
Diversity of operating systems and portability
Application software is generally written for use on a specific operating system, and sometimes even for specific hardware.[citation needed] When porting the application to run on another OS, the functionality required by that application may be implemented differently by that OS (the names of functions, meaning of arguments, etc.) requiring the application to be adapted, changed, or otherwise maintained.
Unix was the first operating system not written in assembly language, making it very portable to systems different from its native PDP-11.[77]
This cost in supporting operating systems diversity can be avoided by instead writing applications against software platforms such as Java or Qt. These abstractions have already borne the cost of adaptation to specific operating systems and their system libraries.
Another approach is for operating system vendors to adopt standards. For example, POSIX and OS abstraction layers provide commonalities that reduce porting costs.
See also
- Comparison of operating systems
- Crash (computing)
- Hypervisor
- Interruptible operating system
- List of important publications in operating systems
- List of operating systems
- List of pioneers in computer science
- Live CD
- Glossary of operating systems terms
- Microcontroller
- Mobile device
- Mobile operating system
- Network operating system
- Object-oriented operating system
- Operating System Projects
- System Commander
- System image
- Timeline of operating systems
Notes
- ^ A combination of DOS/360 and emulation software was known as Compatibility Operating System (COS).
- ^ However, ESPOL did allow source programs to specify all of the operations of the instruction repertoire.
- ^ Bell Labs quickly dropped out, leaving GE and MIT.
- ^ Modern CPUs provide instructions (e.g. SYSENTER) to invoke selected kernel services without an interrupts. Visit https://wiki.osdev.org/SYSENTER for more information.
- ^ Examples include SIGINT, SIGSEGV, and SIGBUS.
- ^ often in the form of a DMA chip for smaller systems and I/O channels for larger systems
- ^ Modern motherboards have a DMA controller. Additionally, a device may also have one. Visit SCSI RDMA Protocol.
References
- ^ Stallings (2005). Operating Systems, Internals and Design Principles. Pearson: Prentice Hall. p. 6.
- ^ Dhotre, I.A. (2009). Operating Systems. Technical Publications. p. 1.
- ^ a b «Desktop Operating System Market Share Worldwide». StatCounter Global Stats. Archived from the original on 27 January 2020. Retrieved 12 October 2022.
- ^ «Mobile & Tablet Operating System Market Share Worldwide». StatCounter Global Stats. Archived from the original on 1 November 2020. Retrieved 12 October 2022.
- ^ «Strategy Analytics: Android Captures Record 88 Percent Share of Global Smartphone Shipments in Q3 2016». 2 November 2016. Archived from the original on 5 November 2016.
- ^ «VII. Special-Purpose Systems — Operating System Concepts, Seventh Edition [Book]». www.oreilly.com. Archived from the original on 13 June 2021. Retrieved 8 February 2021.
- ^ «Special-Purpose Operating Systems — RWTH AACHEN UNIVERSITY Institute for Automation of Complex Power Systems — English». www.acs.eonerc.rwth-aachen.de. Archived from the original on 14 June 2021. Retrieved 8 February 2021.
- ^ Lorch, Jacob R., and Alan Jay Smith. «Reducing processor power consumption by improving processor time management in a single-user operating system.» Proceedings of the 2nd annual international conference on Mobile computing and networking. ACM, 1996.
- ^ Mishra, B.; Singh, N.; Singh, R. (2014). «Master-slave group based model for co-ordinator selection, an improvement of bully algorithm». International Conference on Parallel, Distributed and Grid Computing (PDGC). pp. 457–460. doi:10.1109/PDGC.2014.7030789. ISBN 978-1-4799-7682-9. S2CID 13887160.
- ^ a b Hansen, Per Brinch, ed. (2001). Classic Operating Systems. Springer. pp. 4–7. ISBN 0-387-95113-X. Archived from the original on 11 January 2023. Retrieved 19 December 2020.
- ^ Ryckman, George (1960). «The computer operation language». IRE-AIEE-ACM ’60 (Western): 341. doi:10.1145/1460361.1460406. S2CID 30745551.
- ^ Lavington, Simon (1998). A History of Manchester Computers (2nd ed.). Swindon: The British Computer Society. pp. 50–52. ISBN 978-1-902505-01-5.
- ^ Kilburn, T.; Payne, R. B.; Howarth, D. J. (December 1961). «The Atlas Supervisor». Institute of Electrical Engineers: 279–294. doi:10.1145/1460764.1460786. S2CID 16466990. Archived from the original on 9 June 2022. Retrieved 17 June 2022.
- ^ Brinch Hansen, Per (2000). Classic Operating Systems: From Batch Processing to Distributed Systems. Springer-Verlag.
- ^ EXEC I UNIVAC 1107 Executive System (PDF) (rev. 1 ed.). Sperry Rand. UP-2577. Archived (PDF) from the original on 15 June 2022. Retrieved 15 May 2022.
- ^ UNIVAC DATA PROCESSING DIVISION MULTI-PROCESSOR SYSTEM EXEC II PROGRAMMERS REFERENCE MANUAL (PDF). Sperry Rand. 1966. UP-4058. Archived (PDF) from the original on 15 June 2022. Retrieved 15 May 2022.
- ^ UNIVAC 1108 MULTI-PROCESSOR SYSTEM Operating System EXEC 8 PROGRAMMERS REFERENCE (PDF) (rev. 1 ed.). Sperry Rand. 1968. UP-4144. Archived (PDF) from the original on 25 May 2022. Retrieved 15 May 2022.
- ^ «Intel® Microprocessor Quick Reference Guide — Year». www.intel.com. Archived from the original on 25 April 2016. Retrieved 24 April 2016.
- ^ Ritchie, Dennis. «Unix Manual, first edition». Lucent Technologies. Archived from the original on 18 May 2008. Retrieved 22 November 2012.
- ^ «OS X Mountain Lion – Move your Mac even further ahead». Apple. Archived from the original on 23 May 2011. Retrieved 7 August 2012.
- ^ «OPENEDITION SERVICES ON MVS/ESA SP VERSION 4 RELEASE 3 ANNOUNCED AND AVAILABILITY OF MVS/ESA SP VERSION 4 RELEASE 3 WITH ADDITIONAL ENHANCEMENTS». Announcement Letters. IBM. 9 February 1993. 293-060. Archived from the original on 19 March 2022. Retrieved 2 February 2022.
- ^ Introducing OpenEdition MVS. First Edition. IBM. December 1993. GC23-3010-00.
- ^ OpenEdition MVS POSIX.1 Conformance Document. First Edition. IBM. February 1993. GC23-3011-00.
- ^ OpenEdition MVS POSIX.2 Conformance Document. First Edition. IBM. December 1993. GC23-3012-00.
- ^ «Twenty Years of Linux according to Linus Torvalds». ZDNet. April 13, 2011. Archived from the original on September 19, 2016. Retrieved September 19, 2016.
- ^ Linus Benedict Torvalds (5 October 1991). «Free minix-like kernel sources for 386-AT». Newsgroup: comp.os.minix. Archived from the original on 2 March 2013. Retrieved 30 September 2011.
- ^ «What Is Linux: An Overview of the Linux Operating System». Medium. Archived from the original on June 12, 2020. Retrieved December 21, 2019.
- ^ Linux Online (2008). «Linux Logos and Mascots». Archived from the original on 15 August 2010. Retrieved 11 August 2009.
- ^ «IDC report into Server market share». Idc.com. Archived from the original on 27 September 2012. Retrieved 7 August 2012.
- ^ LinuxDevices Staff (23 April 2008). «Linux still top embedded OS». LinuxGizmos.com. Archived from the original on 19 April 2016. Retrieved 5 April 2016.
- ^ «Sublist Generator». Top500.org. Archived from the original on 27 February 2021. Retrieved 6 February 2017.
- ^ «Top 5 Operating Systems from January to April 2011». StatCounter. October 2009. Archived from the original on 26 May 2012. Retrieved 5 November 2009.
- ^ «Global Web Stats». Net Market Share, Net Applications. May 2011. Archived from the original on 25 January 2010. Retrieved 7 May 2011.
- ^ «Global Web Stats». W3Counter, Awio Web Services. September 2009. Archived from the original on 28 June 2012. Retrieved 24 October 2009.
- ^ «Operating System Market Share». Net Applications. October 2009. Archived from the original on 25 January 2010. Retrieved 5 November 2009.
- ^ «w3schools.com OS Platform Statistics». Archived from the original on 5 August 2011. Retrieved 30 October 2011.
- ^ «Stats Count Global Stats Top Five Operating Systems». Archived from the original on 26 May 2012. Retrieved 30 October 2011.
- ^ «Global statistics at w3counter.com». Archived from the original on 28 June 2012. Retrieved 23 January 2012.
- ^ «Troubleshooting MS-DOS Compatibility Mode on Hard Disks». Support.microsoft.com. Archived from the original on 10 August 2012. Retrieved 7 August 2012.
- ^ «Using NDIS 2 PCMCIA Network Card Drivers in Windows 95». Support.microsoft.com. Archived from the original on 17 February 2013. Retrieved 7 August 2012.
- ^ «INFO: Windows 95 Multimedia Wave Device Drivers Must be 16 bit». Support.microsoft.com. Archived from the original on 17 February 2013. Retrieved 7 August 2012.
- ^ Arthur, Charles. «Windows 8 will run on ARM chips — but third-party apps will need rewrite». The Guardian. Archived from the original on 12 October 2016.
- ^ «Operating System Share by Groups for Sites in All Locations January 2009». Archived from the original on 6 July 2009. Retrieved 3 May 2010.
- ^ «Behind the IDC data: Windows still No. 1 in server operating systems». ZDNet. 26 February 2010. Archived from the original on 1 March 2010.
- ^ a b Kerrisk, Michael (2010). The Linux Programming Interface. No Starch Press. p. 388. ISBN 978-1-59327-220-3.
A signal is a notification to a process that an event has occurred. Signals are sometimes described as software interrupts.
- ^ Hyde, Randall (1996). «Chapter Seventeen: Interrupts, Traps and Exceptions (Part 1)». The Art Of Assembly Language Programming. No Starch Press. Archived from the original on 22 December 2021. Retrieved 22 December 2021.
The concept of an interrupt is something that has expanded in scope over the years. The 80×86 family has only added to the confusion surrounding interrupts by introducing the int (software interrupt) instruction. Indeed, different manufacturers have used terms like exceptions, faults, aborts, traps and interrupts to describe the phenomena this chapter discusses. Unfortunately there is no clear consensus as to the exact meaning of these terms. Different authors adopt different terms to their own use.
- ^ Tanenbaum, Andrew S. (1990). Structured Computer Organization, Third Edition. Prentice Hall. p. 308. ISBN 978-0-13-854662-5.
Like the trap, the interrupt stops the running program and transfers control to an interrupt handler, which performs some appropriate action. When finished, the interrupt handler returns control to the interrupted program.
- ^ Silberschatz, Abraham (1994). Operating System Concepts, Fourth Edition. Addison-Wesley. p. 32. ISBN 978-0-201-50480-4.
When an interrupt (or trap) occurs, the hardware transfers control to the operating system. First, the operating system preserves the state of the CPU by storing registers and the program counter. Then, it determines which type of interrupt has occurred. For each type of interrupt, separate segments of code in the operating system determine what action should be taken.
- ^ Silberschatz, Abraham (1994). Operating System Concepts, Fourth Edition. Addison-Wesley. p. 105. ISBN 978-0-201-50480-4.
Switching the CPU to another process requires saving the state of the old process and loading the saved state for the new process. This task is known as a context switch.
- ^ a b c d e Silberschatz, Abraham (1994). Operating System Concepts, Fourth Edition. Addison-Wesley. p. 31. ISBN 978-0-201-50480-4.
- ^ Silberschatz, Abraham (1994). Operating System Concepts, Fourth Edition. Addison-Wesley. p. 30. ISBN 978-0-201-50480-4.
Hardware may trigger an interrupt at any time by sending a signal to the CPU, usually by way of the system bus.
- ^ Kerrisk, Michael (2010). The Linux Programming Interface. No Starch Press. p. 388. ISBN 978-1-59327-220-3.
Signals are analogous to hardware interrupts in that they interrupt the normal flow of execution of a program; in most cases, it is not possible to predict exactly when a signal will arrive.
- ^ Kerrisk, Michael (2010). The Linux Programming Interface. No Starch Press. p. 388. ISBN 978-1-59327-220-3.
Among the types of events that cause the kernel to generate a signal for a process are the following: A software event occurred. For example, … the process’s CPU time limit was exceeded[.]
- ^ a b c d e Kerrisk, Michael (2010). The Linux Programming Interface. No Starch Press. p. 388. ISBN 978-1-59327-220-3.
- ^ «Intel® 64 and IA-32 Architectures Software Developer’s Manual» (PDF). Intel Corporation. September 2016. p. 610. Archived (PDF) from the original on 23 March 2022. Retrieved 5 May 2022.
- ^ a b c Bach, Maurice J. (1986). The Design of the UNIX Operating System. Prentice-Hall. p. 200. ISBN 0-13-201799-7.
- ^ Kerrisk, Michael (2010). The Linux Programming Interface. No Starch Press. p. 400. ISBN 978-1-59327-220-3.
- ^ a b Tanenbaum, Andrew S. (1990). Structured Computer Organization, Third Edition. Prentice Hall. p. 308. ISBN 978-0-13-854662-5.
- ^ Silberschatz, Abraham (1994). Operating System Concepts, Fourth Edition. Addison-Wesley. p. 182. ISBN 978-0-201-50480-4.
- ^ Haviland, Keith; Salama, Ben (1987). UNIX System Programming. Addison-Wesley Publishing Company. p. 153. ISBN 0-201-12919-1.
- ^ Haviland, Keith; Salama, Ben (1987). UNIX System Programming. Addison-Wesley Publishing Company. p. 148. ISBN 0-201-12919-1.
- ^ a b Haviland, Keith; Salama, Ben (1987). UNIX System Programming. Addison-Wesley Publishing Company. p. 149. ISBN 0-201-12919-1.
- ^ Tanenbaum, Andrew S. (1990). Structured Computer Organization, Third Edition. Prentice Hall. p. 292. ISBN 978-0-13-854662-5.
- ^ IBM (September 1968), «Main Storage» (PDF), IBM System/360 Principles of Operation (PDF), Eighth Edition, p. 7, archived (PDF) from the original on 19 March 2022, retrieved 13 April 2022
- ^ a b
Tanenbaum, Andrew S. (1990). Structured Computer Organization, Third Edition. Prentice Hall. p. 294. ISBN 978-0-13-854662-5. - ^ «Program Interrupt Controller (PIC)» (PDF). Users Handbook — PDP-7 (PDF). Digital Equipment Corporation. 1965. pp. 48. F-75. Archived (PDF) from the original on 10 May 2022. Retrieved 20 April 2022.
- ^ PDP-1 Input-Output Systems Manual (PDF). Digital Equipment Corporation. pp. 19–20. Archived (PDF) from the original on 25 January 2019. Retrieved 16 August 2022.
- ^ Silberschatz, Abraham (1994). Operating System Concepts, Fourth Edition. Addison-Wesley. p. 32. ISBN 978-0-201-50480-4.
- ^ Silberschatz, Abraham (1994). Operating System Concepts, Fourth Edition. Addison-Wesley. p. 34. ISBN 978-0-201-50480-4.
- ^ a b Tanenbaum, Andrew S. (1990). Structured Computer Organization, Third Edition. Prentice Hall. p. 295. ISBN 978-0-13-854662-5.
- ^ a b Tanenbaum, Andrew S. (1990). Structured Computer Organization, Third Edition. Prentice Hall. p. 309. ISBN 978-0-13-854662-5.
- ^ Tanenbaum, Andrew S. (1990). Structured Computer Organization, Third Edition. Prentice Hall. p. 310. ISBN 978-0-13-854662-5.
- ^ Stallings, William (2008). Computer Organization & Architecture. New Delhi: Prentice-Hall of India Private Limited. p. 267. ISBN 978-81-203-2962-1.
- ^ «Operating Systems: Security». www.cs.uic.edu. Archived from the original on 7 December 2020. Retrieved 27 November 2020.
- ^ Poisson, Ken. «Chronology of Personal Computer Software» Archived 14 May 2008 at the Wayback Machine. Retrieved on 2008-05-07. Last checked on 2009-03-30.
- ^ «Reading: Operating System». Lumen. Archived from the original on 6 January 2019. Retrieved 5 January 2019.
- ^ «The History of Unix». BYTE. August 1983. p. 188. Retrieved 31 January 2015.
Further reading
- Anderson, Thomas; Dahlin, Michael (2014). Operating Systems: Principles and Practice. Recursive Books. ISBN 978-0-9856735-2-9.
- Auslander, M. A.; Larkin, D. C.; Scherr, A. L. (September 1981). «The Evolution of the MVS Operating System». IBM Journal of Research and Development. 25 (5): 471–482. doi:10.1147/rd.255.0471.
- Deitel, Harvey M.; Deitel, Paul; Choffnes, David (25 December 2015). Operating Systems. Pearson/Prentice Hall. ISBN 978-0-13-092641-8.
- Bic, Lubomur F.; Shaw, Alan C. (2003). Operating Systems. Pearson: Prentice Hall.
- Silberschatz, Avi; Galvin, Peter; Gagne, Greg (2008). Operating Systems Concepts. John Wiley & Sons. ISBN 978-0-470-12872-5.
- O’Brien, J. A., & Marakas, G. M.(2011). Management Information Systems. 10e. McGraw-Hill Irwin.
- Leva, Alberto; Maggio, Martina; Papadopoulos, Alessandro Vittorio; Terraneo, Federico (2013). Control-based Operating System Design. IET. ISBN 978-1-84919-609-3.
- Arpaci-Dusseau, Remzi; Arpaci-Dusseau, Andrea (2015). Operating Systems: Three Easy Pieces. Archived from the original on 25 July 2016. Retrieved 25 July 2016.
External links
- Operating Systems at Curlie
- Multics History and the history of operating systems
Table of contents
- What is an Operating System?
- History of Operating Systems
- Functions of Operating System
- Features of Operating Systems
- Components of Operating System
- What is Kernel?
- Functions of kernel
- Types of Kernel
- Types of Operating System
- Batch OS
- Distributed OS
- Multitasking OS
- Network OS
- Real-Time OS
- Mobile OS
- 32-bit OS versus 64-bit OS
- Operating Systems Market Share
- Examples of Operating System
- Advantages of Operating System
- Disadvantages of Operating System
- Real-Time Operating System
- What is RTOS?
- Applications of Real-Time Operating System
- Conclusion
- Operating System FAQs
An operating system (OS) manages all other applications and programs in a computer, and it is loaded into the computer by a boot program. It enables applications to interact with a computer’s hardware. Through a designated application programme interface, the application programmes request services from the operating system (API). The kernel is the software that contains the operating system’s core components. To run other programmes, every computer has to have at least one operating system installed.
Windows, Linux, and Android are examples of operating systems that enable the user to use programs like MS Office, Notepad, and games on the computer or mobile phone. It is necessary to have at least one operating system installed in the computer to run basic programs like browsers.
Know More About Operating System
History of Operating Systems
- The first computer, Z1, was made in 1936 – 1938. Unfortunately, this computer ran without an operating system.
- Twenty years later, the first-ever operating system was made in 1956.
- In the 1960s, bell labs started working on building UNIX, the first multitasking operating system.
- In 1977 the apple series came into existence. Apple Dos 3.3 was the first disk operating system.
- In 1981, Microsoft built the first operating system called DOS by purchasing 86 – DOS software from a Seattle company.
- The most famous Microsoft windows came into existence in 1985 when MS-DOS was paired with GUI, a graphics environment.
Functions of Operating System
- Processor Management: An operating system manages the processor’s work by allocating various jobs to it and ensuring that each process receives enough time from the processor to function properly.
- Memory Management: An operating system manages the allocation and deallocation of the memory to various processes and ensures that the other process does not consume the memory allocated to one process.
- Device Management: There are various input and output devices. An OS controls the working of these input-output devices. It receives the requests from these devices, performs a specific task, and communicates back to the requesting process.
- File Management: An operating system keeps track of information regarding the creation, deletion, transfer, copy, and storage of files in an organized way. It also maintains the integrity of the data stored in these files, including the file directory structure, by protecting against unauthorized access.
- Security: The operating system provides various techniques which assure the integrity and confidentiality of user data. Following security measures are used to protect user data:
- Protection against unauthorized access through login.
- Protection against intrusion by keeping Firefall active.
- Protecting the system memory against malicious access.
- Displaying messages related to system vulnerabilities.
- Error Detection: From time to time, the operating system checks the system for any external threat or malicious software activity. It also checks the hardware for any type of damage. This process displays several alerts to the user so that the appropriate action can be taken against any damage caused to the system.
- Job Scheduling: In a multitasking OS where multiple programs run simultaneously, the operating system determines which applications should run in which order and how time should be allocated to each application.
Features of Operating Systems
Here is a list of some important features of operating systems:
- Provides a platform for running applications
- Handles memory management and CPU scheduling
- Provides file system abstraction
- Provides networking support
- Provides security features
- Provides user interface
- Provides utilities and system services
- Supports application development
Components of Operating System
Now to perform the functions mentioned above, the operating system has two components:
- Shell
- Kernel
Shell handles user interactions. It is the outermost layer of the OS and manages the interaction between user and operating system by:
- Prompting the user to give input
- Interpreting the input for the operating system
- Handling the output from the operating system.
Shell provides a way to communicate with the OS by either taking the input from the user or the shell script. A shell script is a sequence of system commands that are stored in a file.
For an in-depth understanding of this topic, check out this free operating system course.
What is Kernel?
The kernel is the core component of an operating system for a computer (OS). All other components of the OS rely on the core to supply them with essential services. It serves as the primary interface between the OS and the hardware and aids in the control of devices, networking, file systems, and process and memory management.
Functions of kernel
The kernel is the core component of an operating system which acts as an interface between applications, and the data is processed at the hardware level.
When an OS is loaded into memory, the kernel is loaded first and remains in memory until the OS is shut down. After that, the kernel provides and manages the computer resources and allows other programs to run and use these resources. The kernel also sets up the memory address space for applications, loads the files with application code into memory, and sets up the execution stack for programs.
The kernel is responsible for performing the following tasks:
- Input-Output management
- Memory Management
- Process Management for application execution.
- Device Management
- System calls control
Earlier, all the basic system services like process and memory management, interrupt handling, etc., were packaged into a single module in the kernel space. This type of kernel was called the Monolithic Kernel. The problem with this approach was that the whole kernel had to be recompiled for even a small change.
In a modern-day approach to monolithic architecture, a microkernel contains different modules like device management, file management, etc. It is dynamically loaded and unloaded. With this modern-day approach, the kernel code size was reduced while its stability increased.
Types of Kernel
Linus Torvalds introduced the concept of a monolithic kernel in 1991 as a part of the Linux kernel. A monolithic kernel is a single large program that contains all operating system components. However, the Linux kernel evolved over the years and now consists of different types of kernels, as listed below.
1. Monolithic Kernel As the name suggests, a monolithic kernel is a single large program that contains all operating system components. The entire kernel executes in the processor’s privileged mode and provides full access to the system’s hardware. Monolithic kernels are faster than microkernels because they don’t have the overhead of message passing. This type of kernel is generally used in embedded systems and real-time operating systems.
2. Microkernel A microkernel is a kernel that contains only the essential components required for the basic functioning of the operating system. All other components are removed from the kernel and implemented as user-space processes. The microkernel approach provides better modularity, flexibility, and extensibility. It is also more stable and secure than monolithic kernels.
3. Hybrid Kernel A hybrid kernel is a kernel that combines the best features of both monolithic kernels and microkernels. It contains a small microkernel that provides the essential components for the basic functioning of the OS. The remaining components are implemented as user-space processes or as loadable kernel modules. This approach provides the best of both worlds, namely, the performance of monolithic kernels and the modularity of microkernels.
4. Exokernel An exokernel is a kernel that provides the bare minimum components required for the basic functioning of the operating system. All other components are removed from the kernel and implemented as user-space processes. The exokernel approach provides the best possible performance because there is no kernel overhead. However, it is also the most difficult to implement and is not widely used.
Now let’s look at the different types of operating systems.
Types of Operating System
There are several different types of operating systems present. In this section, we will discuss the advantages and disadvantages of these types of OS.
- Batch OS
- Distributed OS
- Multitasking OS
- Network OS
- Real-OS
- Mobile OS
Batch OS
Batch OS is the first operating system for second-generation computers. This OS does not directly interact with the computer. Instead, an operator takes up similar jobs and groups them together into a batch, and then these batches are executed one by one based on the first-come, first, serve principle.
Advantages of Batch OS
- Execution time taken for similar jobs is higher.
- Multiple users can share batch systems.
- Managing large works becomes easy in batch systems.
- The idle time for a single batch is very less.
Disadvantages of OS
- It is hard to debug batch systems.
- If a job fails, then the other jobs have to wait for an unknown time till the issue is resolved.
- Batch systems are sometimes costly.
Examples of Batch OS: payroll system, bank statements, data entry, etc.
Distributed OS
A distributed OS is a recent advancement in the field of computer technology and is utilized all over the world that too with great pace. In a distributed OS, various computers are connected through a single communication channel. These independent computers have their memory unit and CPU and are known as loosely coupled systems. The system processes can be of different sizes and can perform different functions. The major benefit of such a type of operating system is that a user can access files that are not present on his system but in another connected system. In addition, remote access is available to the systems connected to this network.
Advantages of Distributed OS
- Failure of one system will not affect the other systems because all the computers are independent of each other.
- The load on the host system is reduced.
- The size of the network is easily scalable as many computers can be added to the network.
- As the workload and resources are shared therefore the calculations are performed at a higher speed.
- Data exchange speed is increased with the help of electronic mail.
Disadvantages of Distributed OS
- The setup cost is high.
- Software used for such systems is highly complex.
- Failure of the main network will lead to the failure of the whole system.
Examples of Distributed OS: LOCUS, etc.
Multitasking OS
The multitasking OS is also known as the time-sharing operating system as each task is given some time so that all the tasks work efficiently. This system provides access to a large number of users, and each user gets the time of CPU as they get in a single system. The tasks performed are given by a single user or by different users. The time allotted to execute one task is called a quantum, and as soon as the time to execute one task is completed, the system switches over to another task.
Advantages of Multitasking OS
- Each task gets equal time for execution.
- The idle time for the CPU will be the lowest.
- There are very few chances for the duplication of the software.
Disadvantages of Multitasking OS
- Processes with higher priority cannot be executed first as equal priority is given to each process or task.
- Various user data is needed to be taken care of from unauthorized access.
- Sometimes there is a data communication problem.
Examples of Multitasking OS: UNIX, etc.
Network OS
Network operating systems are the systems that run on a server and manage all the networking functions. They allow sharing of various files, applications, printers, security, and other networking functions over a small network of computers like LAN or any other private network. In the network OS, all the users are aware of the configurations of every other user within the network, which is why network operating systems are also known as tightly coupled systems.
Advantages of Network OS
- New technologies and hardware can easily upgrade the systems.
- Security of the system is managed over servers.
- Servers can be accessed remotely from different locations and systems.
- The centralized servers are stable.
Disadvantages of Network OS
- Server costs are high.
- Regular updates and maintenance are required.
- Users are dependent on the central location for the maximum number of operations.
Examples of Network OS: Microsoft Windows server 2008, LINUX, etc.
Real-Time OS
Real-Time operating systems serve real-time systems. These operating systems are useful when many events occur in a short time or within certain deadlines, such as real-time simulations.
Types of the real-time OS are:
- Hard real-time OS
The hard real-time OS is the operating system for mainly the applications in which the slightest delay is also unacceptable. The time constraints of such applications are very strict. Such systems are built for life-saving equipment like parachutes and airbags, which immediately need to be in action if an accident happens.
- Soft real-time OS
The soft real-time OS is the operating system for applications where time constraint is not very strict.
In a soft real-time system, an important task is prioritized over less important tasks, and this priority remains active until the completion of the task. Furthermore, a time limit is always set for a specific job, enabling short time delays for future tasks, which is acceptable. For Example, virtual reality, reservation systems, etc.
Advantages of Real-Time OS
- It provides more output from all the resources as there is maximum utilization of systems.
- It provides the best management of memory allocation.
- These systems are always error-free.
- These operating systems focus more on running applications than those in the queue.
- Shifting from one task to another takes very little time.
Disadvantages of Real-Time OS
- System resources are extremely expensive and are not so good.
- The algorithms used are very complex.
- Only limited tasks can run at a single time.
- In such systems, we cannot set thread priority as these systems cannot switch tasks easily.
Examples of Real-Time OS: Medical imaging systems, robots, etc.
Mobile OS
A mobile OS is an operating system for smartphones, tablets, and PDA’s. It is a platform on which other applications can run on mobile devices.
Advantages of Mobile OS
- It provides ease to users.
Disadvantages of Mobile OS
- Some of mobile operating systems give poor battery quality to users.
- Some of the mobile operating systems are not user-friendly.
Examples of Mobile OS: Android OS, ios, Symbian OS, and Windows mobile OS.
32-bit OS versus 64-bit OS
| Parameter | 32-Bit OS | 64-Bit OS |
| Data and Storage | The 32 bit OS can store and manage less data than the 64 bit OS, as its name would imply. It addresses a maximum of 4,294,967,296 bytes (4 GB) of RAM in more detail. | In contrast, the 64 bit OS has a larger data handling capacity than the 32 bit OS. It indicates that a total of 264 memory addresses, or 18 quintillion gigabytes of RAM, can be addressed. |
| Compatibility of System | A 32-bit processor system will run only on 32-bit OS and not on 64 bit OS. | A 64-bit processor system can run either a 32-bit or 64-bit OS |
| Application Support | The 32-bit OS support applications with no hassle. | The 64-bit OS do not support applications. |
| Performance | Performance of 32- bit OS is less efficient. | Higher performance than the 32-bit processor. |
| Systems Available | These support Windows 7, Windows XP, Windows Vista, Windows 8, and Linux. | These support Windows XP Professional, Windows 7, Windows 8, Windows 10, Windows Vista, Linux, and Mac OS X. |
Examples of Operating System
Following are some examples of Operating Systems:
- Microsoft Windows
It is a series of graphical operating systems developed, marketed, and sold by Microsoft. The first version of Windows was released in 1985 as a GUI add-on to MS-DOS. The first version of Windows sold as a standalone operating system was Windows 95. - macOS
It is a series of graphical operating systems developed by Apple Inc. It is the successor to Mac OS X, and it is the operating system that powers Apple’s Mac family of computers.
- Linux
Linux is built around the Linux kernel and is a free and open-source software OS. It is one of the most popular operating systems for servers and embedded devices. It is also used by millions of desktop users around the world.
To learn more, check out this free Linux course.
- Android
It is a mobile OS developed by Google. It is based on the Linux kernel and designed primarily for touchscreen mobile devices such as smartphones and tablets.
- iOS
Another example of a mobile OS developed by Apple Inc. iOs is the successor to iPhone OS. It is an operating system that powers the iPhone, iPad, and iPod Touch products.
Advantages of Operating System
There are several advantages of operating systems. We have listed some of them below:
- Ensuring correct and efficient use of the computer’s hardware.
- Allowing different applications to run concurrently.
- Managing files and folders.
- Providing a user interface.
- Managing security.
- Managing resources.
- Managing printing.
- Providing a platform for software development.
Disadvantages of Operating System
There are several disadvantages of operating systems. We have listed some of them below:
- They can be complex and difficult to use.
- They can be expensive to purchase and maintain.
- They can be vulnerable to attacks from malicious users.
Real-Time Operating System
What is RTOS?
An operating system that can execute multi-threaded programmes and adhere to real-time deadlines is known as a “RTOS.” The majority of RTOSes incorporate device drivers, resource management, and schedulers. Remember that we don’t always mean “quick” when we talk about “deadlines.” Instead, this means that we can foresee when specific jobs will run before runtime.
If you’re writing intricate embedded applications, an RTOS can be a great tool. They support task isolation and enable concurrent operation.
Applications of Real-Time Operating System
- Defence application systems like RADAR.
- Airlines reservation system.
- Systems that provide immediate updating.
- Networked Multimedia Systems.
- Air traffic control system.
- Command Control Systems.
Conclusion
As the need for technology grows day by day in the coming days and as younger generations like Gen Alpha grow up & join the workforce good & efficient operating system will be the topmost priority of every business setting. If you are planning to get a degree in IT, now is the best time to start.
Operating System FAQs
What is operating system in explain?
An operating system (OS) is the programme that controls all other application programmes in a computer after being installed into the system first by a boot programme. The application programmes seek services from the operating system (API) through a specified application programme interface.
What is an operating system and example?
An operating system facilitates communication between a user and a system. Examples of operating systems are Microsoft Office, Notepad, and gaming on a computer or mobile device including Windows, Linux, and Android.
What are the 5 types of operating systems?
Types of an Operating System are
Batch Operating System.
Time-Sharing Operating System.
Distributed Operating System.
Embedded Operating System.
Real-time Operating System.
What is the importance of an operating system?
The most crucial piece of software that runs on a computer is the operating system. It controls the memory, operations, software, and hardware of the computer. Using this method, you can converse with the computer even if you don’t understand its language.
What is OS structure?
An operating system is a design that enables user application programmes to communicate with the hardware of the machine. The operating system should be built with the utmost care because it is such a complicated structure and should be simple to use and modify. Partially developing the operating system is a simple approach to accomplish this.
What is a process in OS?
A process is an instance of a computer programme that is being run by one or more threads in computing. It includes the programme code and all of its operations. A process may consist of several concurrently running threads of execution, depending on the operating system (OS).
| Operating systems |
|---|
|
|
| Common features |
|
| v · d · e |
An operating system (OS) is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system. A user cannot run an application program on the computer without an operating system, unless the application program is self booting.
Time-sharing operating systems schedule tasks for efficient use of the system and may also include accounting for cost allocation of processor time, mass storage, printing, and other resources.
For hardware functions such as input and output and memory allocation, the operating system acts as an intermediary between application programs and the computer hardware,[1][2] although the application code is usually executed directly by the hardware and will frequently call the OS or be interrupted by it. Operating systems are found on almost any device that contains a computer—from cellular phones and video game consoles to supercomputers and web servers.
Examples of popular modern operating systems include Android, iOS, Linux, Mac OS X, and Microsoft Windows.[3]
Contents
- 1 Types
- 2 Summary
- 3 History
- 3.1 Mainframes
- 3.2 Microcomputers
- 4 Examples of operating systems
- 4.1 Unix and Unix-like operating systems
- 4.1.1 BSD and its descendants
- 4.1.1.1 Mac OS X
- 4.1.2 Plan 9
- 4.1.3 Linux and GNU
- 4.1.3.1 Google Chrome OS
- 4.1.1 BSD and its descendants
- 4.2 AmigaOS
- 4.3 Microsoft Windows
- 4.4 Other
- 4.1 Unix and Unix-like operating systems
- 5 Components
- 5.1 Kernel
- 5.1.1 Program execution
- 5.1.2 Interrupts
- 5.1.3 Modes
- 5.1.4 Memory management
- 5.1.5 Virtual memory
- 5.1.6 Multitasking
- 5.1.7 Disk access and file systems
- 5.1.8 Device drivers
- 5.2 Networking
- 5.3 Security
- 5.4 User interface
- 5.4.1 Graphical user interfaces
- 5.1 Kernel
- 6 Real-time operating systems
- 7 Operating system development as a hobby
- 8 Diversity of operating systems and portability
- 9 See also
- 10 References
- 11 Further reading
- 12 External links
Types
- Real-time
- A real-time operating system is a multitasking operating system that aims at executing real-time applications. Real-time operating systems often use specialized scheduling algorithms so that they can achieve a deterministic nature of behavior. The main objective of real-time operating systems is their quick and predictable response to events. They have an event-driven or time-sharing design and often aspects of both. An event-driven system switches between tasks based on their priorities or external events while time-sharing operating systems switch tasks based on clock interrupts.
- Multi-user vs. Single-user
- A multi-user operating system allows multiple users to access a computer system concurrently. Time-sharing system can be classified as multi-user systems as they enable a multiple user access to a computer through the sharing of time. Single-user operating systems, as opposed to a multi-user operating system, are usable by a single user at a time. Being able to have multiple accounts on a Windows operating system does not make it a multi-user system. Rather, only the network administrator is the real user. But for a Unix-like operating system, it is possible for two users to login at a time and this capability of the OS makes it a multi-user operating system.
- Multi-tasking vs. Single-tasking
- When only a single program is allowed to run at a time, the system is grouped under a single-tasking system. However, when the operating system allows the execution of multiple tasks at one time, it is classified as a multi-tasking operating system. Multi-tasking can be of two types: pre-emptive or co-operative. In pre-emptive multitasking, the operating system slices the CPU time and dedicates one slot to each of the programs. Unix-like operating systems such as Solaris and Linux support pre-emptive multitasking. Cooperative multitasking is achieved by relying on each process to give time to the other processes in a defined manner. MS Windows prior to Windows 2000 used to support cooperative multitasking.
- Distributed
- A distributed operating system manages a group of independent computers and makes them appear to be a single computer. The development of networked computers that could be linked and communicate with each other gave rise to distributed computing. Distributed computations are carried out on more than one machine. When computers in a group work in cooperation, they make a distributed system.
- Embedded
- Embedded operating systems are designed to be used in embedded computer systems. They are designed to operate on small machines like PDAs with less autonomy. They are able to operate with a limited number of resources. They are very compact and extremely efficient by design. Windows CE and Minix 3 are some examples of embedded operating systems.
Summary
Early computers were built to perform a series of single tasks, like a calculator. Operating systems did not exist in their modern and more complex forms until the early 1960s.[4] Some operating system features were developed in the 1950s, such as monitor programs that could automatically run different application programs in succession to speed up processing. Hardware features were added that enabled use of runtime libraries, interrupts, and parallel processing. When personal computers by companies such as Apple Inc., Atari, IBM and Amiga became popular in the 1980s, vendors added operating system features that had previously become widely used on mainframe and mini computers. Later, many features such as graphical user interface were developed specifically for personal computer operating systems.
An operating system consists of many parts. One of the most important components is the kernel, which controls low-level processes that the average user usually cannot see: it controls how memory is read and written, the order in which processes are executed, how information is received and sent by devices like the monitor, keyboard and mouse, and decides how to interpret information received from networks. The user interface is a component that interacts with the computer user directly, allowing them to control and use programs. The user interface may be graphical with icons and a desktop, or textual, with a command line. Application programming interfaces provide services and code libraries that let applications developers write modular code reusing well defined programming sequences in user space libraries or in the operating system itself. Which features are considered part of the operating system is defined differently in various operating systems. For example, Microsoft Windows considers its user interface to be part of the operating system, while many versions of Linux do not.
History
In the 1940s, the earliest electronic digital systems had no operating systems. Electronic systems of this time were so primitive compared to those of today that instructions were often entered into the system one bit at a time on rows of mechanical switches or by jumper wires on plug boards. These were special-purpose systems that, for example, generated ballistics tables for the military or controlled the printing of payroll checks from data on punched paper cards. After programmable general purpose computers were invented, machine languages (consisting of strings of the binary digits 0 and 1 on punched paper tape) were introduced that speed up the programming process (Stern, 1981).
OS/360 was used on most IBM mainframe computers beginning in 1966, including the computers that helped NASA put a man on the moon.
In the early 1950s, a computer could execute only one program at a time. Each user had sole use of the computer for a limited period of time and would arrive at a scheduled time with program and data on punched paper cards and/or punched tape. The program would be loaded into the machine, and the machine would be set to work until the program completed or crashed. Programs could generally be debugged via a front panel using toggle switches and panel lights. It is said that Alan Turing was a master of this on the early Manchester Mark 1 machine, and he was already deriving the primitive conception of an operating system from the principles of the Universal Turing machine.[citation needed]
Later machines came with libraries of software, which would be linked to a user’s program to assist in operations such as input and output and generating computer code from human-readable symbolic code. This was the genesis of the modern-day operating system. However, machines still ran a single job at a time. At Cambridge University in England the job queue was at one time a washing line from which tapes were hung with different colored clothes-pegs to indicate job-priority.[citation needed]
Mainframes
Through the 1950s, many major features were pioneered in the field of operating systems, including batch processing, input/output interrupt, buffering, multitasking, spooling, runtime libraries, link-loading, and programs for sorting records in files. These features were included or not included in application software at the option of application programmers, rather than in a separate operating system used by all applications. In 1959 the SHARE Operating System was released as an integrated utility for the IBM 704, and later in the 709 and 7090 mainframes, although it was quickly supplanted by IBSYS/IBJOB on the 709, 7090 and 7094.
During the 1960s, IBM’s OS/360 introduced the concept of a single OS spanning an entire product line, which was crucial for the success of the System/360 machines. IBM’s current mainframe operating systems are distant descendants of this original system and applications written for OS/360 can still be run on modern machines.[citation needed]
OS/360 also pioneered the concept that the operating system keeps track of all of the system resources that are used, including program and data space allocation in main memory and file space in secondary storage, and file locking during update. When the process is terminated for any reason, all of these resources are re-claimed by the operating system.
The alternative CP-67 system for the S/360-67 started a whole line of IBM operating systems focused on the concept of virtual machines. Other operating systems used on IBM S/360 series mainframes included systems developed by IBM: COS/360 (Compatabililty Operating System), DOS/360 (Disk Operating System), TSS/360 (Time Sharing System), TOS/360 (Tape Operating System), BOS/360 (Basic Operating System), and ACP (Airline Control Program), as well as a few non-IBM systems: MTS (Michigan Terminal System), MUSIC (Multi-User System for Interactive Computing), and ORVYL (Stanford Timesharing System).
Control Data Corporation developed the SCOPE operating system in the 1960s, for batch processing. In cooperation with the University of Minnesota, the Kronos and later the NOS operating systems were developed during the 1970s, which supported simultaneous batch and timesharing use. Like many commercial timesharing systems, its interface was an extension of the Dartmouth BASIC operating systems, one of the pioneering efforts in timesharing and programming languages. In the late 1970s, Control Data and the University of Illinois developed the PLATO operating system, which used plasma panel displays and long-distance time sharing networks. Plato was remarkably innovative for its time, featuring real-time chat, and multi-user graphical games. Burroughs Corporation introduced the B5000 in 1961 with the MCP, (Master Control Program) operating system. The B5000 was a stack machine designed to exclusively support high-level languages with no machine language or assembler, and indeed the MCP was the first OS to be written exclusively in a high-level language – ESPOL, a dialect of ALGOL. MCP also introduced many other ground-breaking innovations, such as being the first commercial implementation of virtual memory. During development of the AS400, IBM made an approach to Burroughs to licence MCP to run on the AS400 hardware. This proposal was declined by Burroughs management to protect its existing hardware production. MCP is still in use today in the Unisys ClearPath/MCP line of computers.
UNIVAC, the first commercial computer manufacturer, produced a series of EXEC operating systems. Like all early main-frame systems, this was a batch-oriented system that managed magnetic drums, disks, card readers and line printers. In the 1970s, UNIVAC produced the Real-Time Basic (RTB) system to support large-scale time sharing, also patterned after the Dartmouth BC system.
General Electric and MIT developed General Electric Comprehensive Operating Supervisor (GECOS), which introduced the concept of ringed security privilege levels. After acquisition by Honeywell it was renamed to General Comprehensive Operating System (GCOS).
Digital Equipment Corporation developed many operating systems for its various computer lines, including TOPS-10 and TOPS-20 time sharing systems for the 36-bit PDP-10 class systems. Prior to the widespread use of UNIX, TOPS-10 was a particularly popular system in universities, and in the early ARPANET community.
In the late 1960s through the late 1970s, several hardware capabilities evolved that allowed similar or ported software to run on more than one system. Early systems had utilized microprogramming to implement features on their systems in order to permit different underlying architecture to appear to be the same as others in a series. In fact most 360s after the 360/40 (except the 360/165 and 360/168) were microprogrammed implementations. But soon other means of achieving application compatibility were proven to be more significant.
The enormous investment in software for these systems made since 1960s caused most of the original computer manufacturers to continue to develop compatible operating systems along with the hardware. The notable supported mainframe operating systems include:
- Burroughs MCP – B5000, 1961 to Unisys Clearpath/MCP, present.
- IBM OS/360 – IBM System/360, 1966 to IBM z/OS, present.
- IBM CP-67 – IBM System/360, 1967 to IBM z/VM, present.
- UNIVAC EXEC 8 – UNIVAC 1108, 1967, to OS 2200 Unisys Clearpath Dorado, present.
Microcomputers
PC-DOS was an early personal computer OS that featured a command line interface.
Mac OS by Apple Computer became the first widespread OS to feature a graphical user interface. Many of its features such as windows and icons would later become commonplace in GUIs.
The first microcomputers did not have the capacity or need for the elaborate operating systems that had been developed for mainframes and minis; minimalistic operating systems were developed, often loaded from ROM and known as Monitors. One notable early disk-based operating system was CP/M, which was supported on many early microcomputers and was closely imitated by Microsoft’s MS-DOS, which became wildly popular as the operating system chosen for the IBM PC (IBM’s version of it was called IBM DOS or PC DOS). In the ’80s, Apple Computer Inc. (now Apple Inc.) abandoned its popular Apple II series of microcomputers to introduce the Apple Macintosh computer with an innovative Graphical User Interface (GUI) to the Mac OS.
The introduction of the Intel 80386 CPU chip with 32-bit architecture and paging capabilities, provided personal computers with the ability to run multitasking operating systems like those of earlier minicomputers and mainframes. Microsoft responded to this progress by hiring Dave Cutler, who had developed the VMS operating system for Digital Equipment Corporation. He would lead the development of the Windows NT operating system, which continues to serve as the basis for Microsoft’s operating systems line. Steve Jobs, a co-founder of Apple Inc., started NeXT Computer Inc., which developed the Unix-like NEXTSTEP operating system. NEXTSTEP would later be acquired by Apple Inc. and used, along with code from FreeBSD as the core of Mac OS X.
The GNU Project was started by activist and programmer Richard Stallman with the goal of a complete free software replacement to the proprietary UNIX operating system. While the project was highly successful in duplicating the functionality of various parts of UNIX, development of the GNU Hurd kernel proved to be unproductive. In 1991, Finnish computer science student Linus Torvalds, with cooperation from volunteers collaborating over the Internet, released the first version of the Linux kernel. It was soon merged with the GNU user space components and system software to form a complete operating system. Since then, the combination of the two major components has usually been referred to as simply «Linux» by the software industry, a naming convention that Stallman and the Free Software Foundation remain opposed to, preferring the name GNU/Linux. The Berkeley Software Distribution, known as BSD, is the UNIX derivative distributed by the University of California, Berkeley, starting in the 1970s. Freely distributed and ported to many minicomputers, it eventually also gained a following for use on PCs, mainly as FreeBSD, NetBSD and OpenBSD.
Examples of operating systems
Unix and Unix-like operating systems
Evolution of Unix systems
Main article: Unix
Ken Thompson wrote B, mainly based on BCPL, which he used to write Unix, based on his experience in the MULTICS project. B was replaced by C, and Unix developed into a large, complex family of inter-related operating systems which have been influential in every modern operating system (see History).
The Unix-like family is a diverse group of operating systems, with several major sub-categories including System V, BSD, and GNU/Linux. The name «UNIX» is a trademark of The Open Group which licenses it for use with any operating system that has been shown to conform to their definitions. «Unix-like» is commonly used to refer to the large set of operating systems which resemble the original Unix.
Unix-like systems run on a wide variety of machine architectures. They are used heavily for servers in business, as well as workstations in academic and engineering environments. Free Unix variants, such as GNU/Linux and BSD, are popular in these areas.
Four operating systems are certified by the The Open Group (holder of the Unix trademark) as Unix. HP’s HP-UX and IBM’s AIX are both descendants of the original System V Unix and are designed to run only on their respective vendor’s hardware. In contrast, Sun Microsystems’s Solaris Operating System can run on multiple types of hardware, including x86 and Sparc servers, and PCs. Apple’s Mac OS X, a replacement for Apple’s earlier (non-Unix) Mac OS, is a hybrid kernel-based BSD variant derived from NeXTSTEP, Mach, and FreeBSD.
Unix interoperability was sought by establishing the POSIX standard. The POSIX standard can be applied to any operating system, although it was originally created for various Unix variants.
BSD and its descendants
The first server for the World Wide Web ran on NeXTSTEP, based on BSD.
A subgroup of the Unix family is the Berkeley Software Distribution family, which includes FreeBSD, NetBSD, and OpenBSD. These operating systems are most commonly found on webservers, although they can also function as a personal computer OS. The Internet owes much of its existence to BSD, as many of the protocols now commonly used by computers to connect, send and receive data over a network were widely implemented and refined in BSD. The world wide web was also first demonstrated on a number of computers running an OS based on BSD called NextStep.
BSD has its roots in Unix. In 1974, University of California, Berkeley installed its first Unix system. Over time, students and staff in the computer science department there began adding new programs to make things easier, such as text editors. When Berkely received new VAX computers in 1978 with Unix installed, the school’s undergraduates modified Unix even more in order to take advantage of the computer’s hardware possibilities. The Defense Advanced Research Projects Agency of the US Department of Defense took interest, and decided to fund the project. Many schools, corporations, and government organizations took notice and started to use Berkeley’s version of Unix instead of the official one distributed by AT&T.
Steve Jobs, upon leaving Apple Inc. in 1985, formed NeXT Inc., a company that manufactured high-end computers running on a variation of BSD called NeXTSTEP. One of these computers was used by Tim Berners-Lee as the first webserver to create the World Wide Web.
Developers like Keith Bostic encouraged the project to replace any non-free code that originated with Bell Labs. Once this was done, however, AT&T sued. Eventually, after two years of legal disputes, the BSD project came out ahead and spawned a number of free derivatives, such as FreeBSD and NetBSD.
Mac OS X
The standard user interface of Mac OS X
Mac OS X is a line of open core graphical operating systems developed, marketed, and sold by Apple Inc., the latest of which is pre-loaded on all currently shipping Macintosh computers. Mac OS X is the successor to the original Mac OS, which had been Apple’s primary operating system since 1984. Unlike its predecessor, Mac OS X is a UNIX operating system built on technology that had been developed at NeXT through the second half of the 1980s and up until Apple purchased the company in early 1997.
The operating system was first released in 1999 as Mac OS X Server 1.0, with a desktop-oriented version (Mac OS X v10.0) following in March 2001. Since then, six more distinct «client» and «server» editions of Mac OS X have been released, the most recent being Mac OS X 10.7, which was first made available on July 20, 2011. Releases of Mac OS X are named after big cats; the current version of Mac OS X is «Lion».
The server edition, Mac OS X Server, is architecturally identical to its desktop counterpart but usually runs on Apple’s line of Macintosh server hardware. Mac OS X Server includes work group management and administration software tools that provide simplified access to key network services, including a mail transfer agent, a Samba server, an LDAP server, a domain name server, and others. In Mac OS X v10.7 Lion, all server aspects of Mac OS X Server have been integrated into the client version.[5]
Plan 9
Ken Thompson, Dennis Ritchie and Douglas McIlroy at Bell Labs designed and developed the C programming language to build the operating system Unix. Programmers at Bell Labs went on to develop Plan 9 and Inferno, which were engineered for modern distributed environments. Plan 9 was designed from the start to be a networked operating system, and had graphics built-in, unlike Unix, which added these features to the design later. It is currently released under the Lucent Public License. Inferno was sold to Vita Nuova Holdings and has been released under a GPL/MIT license.
Linux and GNU
Main articles: GNU, Linux, and Linux kernel
Linux (or GNU/Linux) is a Unix-like operating system that was developed without any actual Unix code, unlike BSD and its variants. Linux can be used on a wide range of devices from supercomputers to wristwatches. The Linux kernel is released under an open source license, so anyone can read and modify its code. It has been modified to run on a large variety of electronics. Although estimates suggest that Linux is used on 1.82% of all personal computers,[6][7] it has been widely adopted for use in servers[8] and embedded systems[9] (such as cell phones). Linux has superseded Unix in most places[which?], and is used on the 10 most powerful supercomputers in the world.[10] The Linux kernel is used in some popular distributions, such as Red Hat, Debian, Ubuntu, Linux Mint and Google’s Android.
The GNU project is a mass collaboration of programmers who seek to create a completely free and open operating system that was similar to Unix but with completely original code. It was started in 1983 by Richard Stallman, and is responsible for many of the parts of most Linux variants. For this reason, some claim that the combined product of the Linux kernel and the GNU software collection is more correctly called GNU/Linux. Thousands of pieces of software for virtually every operating system are licensed under the GNU General Public License. Meanwhile, the Linux kernel began as a side project of Linus Torvalds, a university student from Finland. In 1991, Torvalds began work on it, and posted information about his project on a newsgroup for computer students and programmers. He received a wave of support and volunteers who ended up creating a full-fledged kernel. Programmers from GNU took notice, and members of both projects worked to integrate the finished GNU parts with the Linux kernel in order to create a full-fledged operating system.
Google Chrome OS
Chrome is an operating system based on the Linux kernel and designed by Google. Since Chrome OS targets computer users who spend most of their time on the Internet, it is mainly a web browser with no ability to run applications. It relies on Internet applications (or Web apps) used in the web browser to accomplish tasks such as word processing and media viewing, as well as online storage for storing most files.
AmigaOS
AmigaOS is the default native operating system of the Amiga personal computer. It was developed first by the Amiga Corporation then sold to Commodore International, and initially introduced in 1985 with the Amiga 1000. Early versions (1.0-3.9) run on the Motorola 68k series of 16-bit and 32-bit microprocessors, while the newer AmigaOS 4 runs only on PowerPC microprocessors. On top of a preemptive multitasking kernel called Exec, it includes an abstraction of the Amiga’s unique hardware, a disk operating system called AmigaDOS, a windowing system API called Intuition and a graphical user interface called Workbench. A command line interface called AmigaShell is also available and integrated into the system. The GUI and the CLI complement each other and share the same privileges. The current holder of the Amiga intellectual properties is Amiga Inc. They oversaw the development of AmigaOS 4 but did not develop it themselves, contracting it instead to Hyperion Entertainment. On 20 December 2006, Amiga Inc terminated Hyperion’s license to continue development of AmigaOS 4. However, in 30 September 2009, Hyperion was granted an exclusive, perpetual, worldwide right to AmigaOS 3.1 in order to use, develop, modify, commercialize, distribute and market AmigaOS 4.x and subsequent versions of AmigaOS (including AmigaOS 5).[11]
Microsoft Windows
Bootable Windows To Go USB flash drive
Microsoft Windows is a family of proprietary operating systems designed by Microsoft Corporation and primarily targeted to Intel architecture based computers, with an estimated 88.9 percent total usage share on Web connected computers.[7][12][13][14] The newest version is Windows 7 for workstations and Windows Server 2008 R2 for servers. Windows 7 recently overtook Windows XP as most used OS.[15][16]
Microsoft Windows originated in 1985 as an application running on top of MS-DOS, which was the standard operating system shipped on most Intel architecture personal computers at the time. In 1995, Windows 95 was released, combining MS-DOS 7.0 with Windows on the same medium, removing the need of getting a separate MS-DOS license. Keeping much legacy, it could run real-mode MS-DOS[17][18] and 16 bits Windows 3.x[19] drivers. Windows Me, released in 2000, was the latest version of Windows of the Windows 95 family. Later versions have all been based on the Windows NT kernel. Current versions of Windows run on IA-32 and x86-64 microprocessors, although Windows 8 will support ARM architecture. In the past, Windows NT supported a few non-Intel architectures.
Server editions of Windows are widely used. In recent years, Microsoft has expended significant capital in an effort to promote the use of Windows as a server operating environment. However, Windows’ usage on servers is not as widespread as on personal computers, as Windows competes against Linux and BSD for server market share.[20][21]
Other
Older operating systems which are still used in niche markets include OS/2 from IBM and Microsoft; Mac OS, the non-Unix precursor to Apple’s Mac OS X; BeOS; XTS-300. Some, most notably Haiku, RISC OS, MorphOS and FreeMint continue to be developed as minority platforms for enthusiast communities and specialist applications. OpenVMS formerly from DEC, is still under active development by Hewlett-Packard. Yet other operating systems are used almost exclusively in academia, for operating systems education or to do research on operating system concepts. A typical example of a system that fulfills both roles is MINIX, while for example Singularity is used purely for research.
Components
The components of an operating system all exist in order to make the different parts of a computer work together. All software—from financial databases to film editors—needs to go through the operating system in order to use any of the hardware, whether it be as simple as a mouse or keyboard or complex as an Internet connection.
Kernel
A kernel connects the application software to the hardware of a computer.
With the aid of the firmware and device drivers, the kernel provides the most basic level of control over all of the computer’s hardware devices. It manages memory access for programs in the RAM, it determines which programs get access to which hardware resources, it sets up or resets the CPU’s operating states for optimal operation at all times, and it organizes the data for long-term non-volatile storage with file systems on such media as disks, tapes, flash memory, etc.
Program execution
The operating system provides an interface between an application program and the computer hardware, so that an application program can interact with the hardware only by obeying rules and procedures programmed into the operating system. The operating system is also a set of services which simplify development and execution of application programs. Executing an application program involves the creation of a process by the operating system kernel which assigns memory space and other resources, establishes a priority for the process in multi-tasking systems, loads program binary code into memory, and initiates execution of the application program which then interacts with the user and with hardware devices.
Interrupts
Interrupts are central to operating systems, as they provide an efficient way for the operating system to interact with and react to its environment. The alternative — having the operating system «watch» the various sources of input for events (polling) that require action — can be found in older systems with very small stacks (50 or 60 bytes) but are unusual in modern systems with large stacks. Interrupt-based programming is directly supported by most modern CPUs. Interrupts provide a computer with a way of automatically saving local register contexts, and running specific code in response to events. Even very basic computers support hardware interrupts, and allow the programmer to specify code which may be run when that event takes place.
When an interrupt is received, the computer’s hardware automatically suspends whatever program is currently running, saves its status, and runs computer code previously associated with the interrupt; this is analogous to placing a bookmark in a book in response to a phone call. In modern operating systems, interrupts are handled by the operating system’s kernel. Interrupts may come from either the computer’s hardware or from the running program.
When a hardware device triggers an interrupt, the operating system’s kernel decides how to deal with this event, generally by running some processing code. The amount of code being run depends on the priority of the interrupt (for example: a person usually responds to a smoke detector alarm before answering the phone). The processing of hardware interrupts is a task that is usually delegated to software called device driver, which may be either part of the operating system’s kernel, part of another program, or both. Device drivers may then relay information to a running program by various means.
A program may also trigger an interrupt to the operating system. If a program wishes to access hardware for example, it may interrupt the operating system’s kernel, which causes control to be passed back to the kernel. The kernel will then process the request. If a program wishes additional resources (or wishes to shed resources) such as memory, it will trigger an interrupt to get the kernel’s attention.
Modes
Main articles: Protected mode and Supervisor mode
Privilege rings for the x86 available in protected mode. Operating systems determine which processes run in each mode.
Modern CPUs support multiple modes of operation. CPUs with this capability use at least two modes: protected mode and supervisor mode. The supervisor mode is used by the operating system’s kernel for low level tasks that need unrestricted access to hardware, such as controlling how memory is written and erased, and communication with devices like graphics cards. Protected mode, in contrast, is used for almost everything else. Applications operate within protected mode, and can only use hardware by communicating with the kernel, which controls everything in supervisor mode. CPUs might have other modes similar to protected mode as well, such as the virtual modes in order to emulate older processor types, such as 16-bit processors on a 32-bit one, or 32-bit processors on a 64-bit one.
When a computer first starts up, it is automatically running in supervisor mode. The first few programs to run on the computer, being the BIOS or EFI, bootloader, and the operating system have unlimited access to hardware — and this is required because, by definition, initializing a protected environment can only be done outside of one. However, when the operating system passes control to another program, it can place the CPU into protected mode.
In protected mode, programs may have access to a more limited set of the CPU’s instructions. A user program may leave protected mode only by triggering an interrupt, causing control to be passed back to the kernel. In this way the operating system can maintain exclusive control over things like access to hardware and memory.
The term «protected mode resource» generally refers to one or more CPU registers, which contain information that the running program isn’t allowed to alter. Attempts to alter these resources generally causes a switch to supervisor mode, where the operating system can deal with the illegal operation the program was attempting (for example, by killing the program).
Memory management
Among other things, a multiprogramming operating system kernel must be responsible for managing all system memory which is currently in use by programs. This ensures that a program does not interfere with memory already in use by another program. Since programs time share, each program must have independent access to memory.
Cooperative memory management, used by many early operating systems, assumes that all programs make voluntary use of the kernel’s memory manager, and do not exceed their allocated memory. This system of memory management is almost never seen any more, since programs often contain bugs which can cause them to exceed their allocated memory. If a program fails, it may cause memory used by one or more other programs to be affected or overwritten. Malicious programs or viruses may purposefully alter another program’s memory, or may affect the operation of the operating system itself. With cooperative memory management, it takes only one misbehaved program to crash the system.
Memory protection enables the kernel to limit a process’ access to the computer’s memory. Various methods of memory protection exist, including memory segmentation and paging. All methods require some level of hardware support (such as the 80286 MMU), which doesn’t exist in all computers.
In both segmentation and paging, certain protected mode registers specify to the CPU what memory address it should allow a running program to access. Attempts to access other addresses will trigger an interrupt which will cause the CPU to re-enter supervisor mode, placing the kernel in charge. This is called a segmentation violation or Seg-V for short, and since it is both difficult to assign a meaningful result to such an operation, and because it is usually a sign of a misbehaving program, the kernel will generally resort to terminating the offending program, and will report the error.
Windows 3.1-Me had some level of memory protection, but programs could easily circumvent the need to use it. A general protection fault would be produced, indicating a segmentation violation had occurred; however, the system would often crash anyway.
Virtual memory
Main article: Virtual memory
Many operating systems can «trick» programs into using memory scattered around the hard disk and RAM as if it is one continuous chunk of memory, called virtual memory.
The use of virtual memory addressing (such as paging or segmentation) means that the kernel can choose what memory each program may use at any given time, allowing the operating system to use the same memory locations for multiple tasks.
If a program tries to access memory that isn’t in its current range of accessible memory, but nonetheless has been allocated to it, the kernel will be interrupted in the same way as it would if the program were to exceed its allocated memory. (See section on memory management.) Under UNIX this kind of interrupt is referred to as a page fault.
When the kernel detects a page fault it will generally adjust the virtual memory range of the program which triggered it, granting it access to the memory requested. This gives the kernel discretionary power over where a particular application’s memory is stored, or even whether or not it has actually been allocated yet.
In modern operating systems, memory which is accessed less frequently can be temporarily stored on disk or other media to make that space available for use by other programs. This is called swapping, as an area of memory can be used by multiple programs, and what that memory area contains can be swapped or exchanged on demand.
«Virtual memory» provides the programmer or the user with the perception that there is a much larger amount of RAM in the computer than is really there.[22]
Multitasking
Further information: Context switch, Preemptive multitasking, and Cooperative multitasking
Multitasking refers to the running of multiple independent computer programs on the same computer; giving the appearance that it is performing the tasks at the same time. Since most computers can do at most one or two things at one time, this is generally done via time-sharing, which means that each program uses a share of the computer’s time to execute.
An operating system kernel contains a piece of software called a scheduler which determines how much time each program will spend executing, and in which order execution control should be passed to programs. Control is passed to a process by the kernel, which allows the program access to the CPU and memory. Later, control is returned to the kernel through some mechanism, so that another program may be allowed to use the CPU. This so-called passing of control between the kernel and applications is called a context switch.
An early model which governed the allocation of time to programs was called cooperative multitasking. In this model, when control is passed to a program by the kernel, it may execute for as long as it wants before explicitly returning control to the kernel. This means that a malicious or malfunctioning program may not only prevent any other programs from using the CPU, but it can hang the entire system if it enters an infinite loop.
Modern operating systems extend the concepts of application preemption to device drivers and kernel code, so that the operating system has preemptive control over internal run-times as well.
The philosophy governing preemptive multitasking is that of ensuring that all programs are given regular time on the CPU. This implies that all programs must be limited in how much time they are allowed to spend on the CPU without being interrupted. To accomplish this, modern operating system kernels make use of a timed interrupt. A protected mode timer is set by the kernel which triggers a return to supervisor mode after the specified time has elapsed. (See above sections on Interrupts and Dual Mode Operation.)
On many single user operating systems cooperative multitasking is perfectly adequate, as home computers generally run a small number of well tested programs. Windows NT was the first version of Microsoft Windows which enforced preemptive multitasking, but it didn’t reach the home user market until Windows XP (since Windows NT was targeted at professionals).
Disk access and file systems
Filesystems allow users and programs to organize and sort files on a computer, often through the use of directories (or «folders»)
Access to data stored on disks is a central feature of all operating systems. Computers store data on disks using files, which are structured in specific ways in order to allow for faster access, higher reliability, and to make better use out of the drive’s available space. The specific way in which files are stored on a disk is called a file system, and enables files to have names and attributes. It also allows them to be stored in a hierarchy of directories or folders arranged in a directory tree.
Early operating systems generally supported a single type of disk drive and only one kind of file system. Early file systems were limited in their capacity, speed, and in the kinds of file names and directory structures they could use. These limitations often reflected limitations in the operating systems they were designed for, making it very difficult for an operating system to support more than one file system.
While many simpler operating systems support a limited range of options for accessing storage systems, operating systems like UNIX and GNU/Linux support a technology known as a virtual file system or VFS. An operating system such as UNIX supports a wide array of storage devices, regardless of their design or file systems, allowing them to be accessed through a common application programming interface (API). This makes it unnecessary for programs to have any knowledge about the device they are accessing. A VFS allows the operating system to provide programs with access to an unlimited number of devices with an infinite variety of file systems installed on them, through the use of specific device drivers and file system drivers.
A connected storage device, such as a hard drive, is accessed through a device driver. The device driver understands the specific language of the drive and is able to translate that language into a standard language used by the operating system to access all disk drives. On UNIX, this is the language of block devices.
When the kernel has an appropriate device driver in place, it can then access the contents of the disk drive in raw format, which may contain one or more file systems. A file system driver is used to translate the commands used to access each specific file system into a standard set of commands that the operating system can use to talk to all file systems. Programs can then deal with these file systems on the basis of filenames, and directories/folders, contained within a hierarchical structure. They can create, delete, open, and close files, as well as gather various information about them, including access permissions, size, free space, and creation and modification dates.
Various differences between file systems make supporting all file systems difficult. Allowed characters in file names, case sensitivity, and the presence of various kinds of file attributes makes the implementation of a single interface for every file system a daunting task. Operating systems tend to recommend using (and so support natively) file systems specifically designed for them; for example, NTFS in Windows and ext3 and ReiserFS in GNU/Linux. However, in practice, third party drives are usually available to give support for the most widely used file systems in most general-purpose operating systems (for example, NTFS is available in GNU/Linux through NTFS-3g, and ext2/3 and ReiserFS are available in Windows through FS-driver and rfstool).
Support for file systems is highly varied among modern operating systems, although there are several common file systems which almost all operating systems include support and drivers for. Operating systems vary on file system support and on the disk formats they may be installed on. Under Windows, each file system is usually limited in application to certain media; for example, CDs must use ISO 9660 or UDF, and as of Windows Vista, NTFS is the only file system which the operating system can be installed on. It is possible to install GNU/Linux onto many types of file systems. Unlike other operating systems, GNU/Linux and UNIX allow any file system to be used regardless of the media it is stored in, whether it is a hard drive, a disc (CD,DVD…), a USB flash drive, or even contained within a file located on another file system.
Device drivers
Main article: Device driver
A device driver is a specific type of computer software developed to allow interaction with hardware devices. Typically this constitutes an interface for communicating with the device, through the specific computer bus or communications subsystem that the hardware is connected to, providing commands to and/or receiving data from the device, and on the other end, the requisite interfaces to the operating system and software applications. It is a specialized hardware-dependent computer program which is also operating system specific that enables another program, typically an operating system or applications software package or computer program running under the operating system kernel, to interact transparently with a hardware device, and usually provides the requisite interrupt handling necessary for any necessary asynchronous time-dependent hardware interfacing needs.
The key design goal of device drivers is abstraction. Every model of hardware (even within the same class of device) is different. Newer models also are released by manufacturers that provide more reliable or better performance and these newer models are often controlled differently. Computers and their operating systems cannot be expected to know how to control every device, both now and in the future. To solve this problem, operating systems essentially dictate how every type of device should be controlled. The function of the device driver is then to translate these operating system mandated function calls into device specific calls. In theory a new device, which is controlled in a new manner, should function correctly if a suitable driver is available. This new driver will ensure that the device appears to operate as usual from the operating system’s point of view.
Under versions of Windows before Vista and versions of Linux before 2.6, all driver execution was co-operative, meaning that if a driver entered an infinite loop it would freeze the system. More recent revisions of these operating systems incorporate kernel preemption, where the kernel interrupts the driver to give it tasks, and then separates itself from the process until it receives a response from the device driver, or gives it more tasks to do.
Networking
Currently most operating systems support a variety of networking protocols, hardware, and applications for using them. This means that computers running dissimilar operating systems can participate in a common network for sharing resources such as computing, files, printers, and scanners using either wired or wireless connections. Networks can essentially allow a computer’s operating system to access the resources of a remote computer to support the same functions as it could if those resources were connected directly to the local computer. This includes everything from simple communication, to using networked file systems or even sharing another computer’s graphics or sound hardware. Some network services allow the resources of a computer to be accessed transparently, such as SSH which allows networked users direct access to a computer’s command line interface.
Client/server networking allows a program on a computer, called a client, to connect via a network to another computer, called a server. Servers offer (or host) various services to other network computers and users. These services are usually provided through ports or numbered access points beyond the server’s network address[disambiguation needed ]. Each port number is usually associated with a maximum of one running program, which is responsible for handling requests to that port. A daemon, being a user program, can in turn access the local hardware resources of that computer by passing requests to the operating system kernel.
Many operating systems support one or more vendor-specific or open networking protocols as well, for example, SNA on IBM systems, DECnet on systems from Digital Equipment Corporation, and Microsoft-specific protocols (SMB) on Windows. Specific protocols for specific tasks may also be supported such as NFS for file access. Protocols like ESound, or esd can be easily extended over the network to provide sound from local applications, on a remote system’s sound hardware.
Security
A computer being secure depends on a number of technologies working properly. A modern operating system provides access to a number of resources, which are available to software running on the system, and to external devices like networks via the kernel.
The operating system must be capable of distinguishing between requests which should be allowed to be processed, and others which should not be processed. While some systems may simply distinguish between «privileged» and «non-privileged», systems commonly have a form of requester identity, such as a user name. To establish identity there may be a process of authentication. Often a username must be quoted, and each username may have a password. Other methods of authentication, such as magnetic cards or biometric data, might be used instead. In some cases, especially connections from the network, resources may be accessed with no authentication at all (such as reading files over a network share). Also covered by the concept of requester identity is authorization; the particular services and resources accessible by the requester once logged into a system are tied to either the requester’s user account or to the variously configured groups of users to which the requester belongs.
In addition to the allow/disallow model of security, a system with a high level of security will also offer auditing options. These would allow tracking of requests for access to resources (such as, «who has been reading this file?»). Internal security, or security from an already running program is only possible if all possibly harmful requests must be carried out through interrupts to the operating system kernel. If programs can directly access hardware and resources, they cannot be secured.
External security involves a request from outside the computer, such as a login at a connected console or some kind of network connection. External requests are often passed through device drivers to the operating system’s kernel, where they can be passed onto applications, or carried out directly. Security of operating systems has long been a concern because of highly sensitive data held on computers, both of a commercial and military nature. The United States Government Department of Defense (DoD) created the Trusted Computer System Evaluation Criteria (TCSEC) which is a standard that sets basic requirements for assessing the effectiveness of security. This became of vital importance to operating system makers, because the TCSEC was used to evaluate, classify and select computer systems being considered for the processing, storage and retrieval of sensitive or classified information.
Network services include offerings such as file sharing, print services, email, web sites, and file transfer protocols (FTP), most of which can have compromised security. At the front line of security are hardware devices known as firewalls or intrusion detection/prevention systems. At the operating system level, there are a number of software firewalls available, as well as intrusion detection/prevention systems. Most modern operating systems include a software firewall, which is enabled by default. A software firewall can be configured to allow or deny network traffic to or from a service or application running on the operating system. Therefore, one can install and be running an insecure service, such as Telnet or FTP, and not have to be threatened by a security breach because the firewall would deny all traffic trying to connect to the service on that port.
An alternative strategy, and the only sandbox strategy available in systems that do not meet the Popek and Goldberg virtualization requirements, is the operating system not running user programs as native code, but instead either emulates a processor or provides a host for a p-code based system such as Java.
Internal security is especially relevant for multi-user systems; it allows each user of the system to have private files that the other users cannot tamper with or read. Internal security is also vital if auditing is to be of any use, since a program can potentially bypass the operating system, inclusive of bypassing auditing.
User interface
A screenshot of the Bourne Again Shell command line. Each command is typed out after the ‘prompt’, and then its output appears below, working its way down the screen. The current command prompt is at the bottom.
Main article: User interface
Every computer that is to be operated by an individual requires a user interface. The user interface is not actually a part of the operating system—it generally runs in a separate program usually referred to as a shell, but is essential if human interaction is to be supported. The user interface requests services from the operating system that will acquire data from input hardware devices, such as a keyboard, mouse or credit card reader, and requests operating system services to display prompts, status messages and such on output hardware devices, such as a video monitor or printer. The two most common forms of a user interface have historically been the command-line interface, where computer commands are typed out line-by-line, and the graphical user interface, where a visual environment (most commonly with windows, buttons, icons and a mouse pointer) is present.
Graphical user interfaces
A screenshot of the KDE graphical user interface. Programs take the form of images on the screen, and the files, folders (directories), and applications take the form of icons and symbols. A mouse is used to navigate the computer.
Most of the modern computer systems support graphical user interfaces (GUI), and often include them. In some computer systems, such as the original implementation of Mac OS, the GUI is integrated into the kernel.
While technically a graphical user interface is not an operating system service, incorporating support for one into the operating system kernel can allow the GUI to be more responsive by reducing the number of context switches required for the GUI to perform its output functions. Other operating systems are modular, separating the graphics subsystem from the kernel and the Operating System. In the 1980s UNIX, VMS and many others had operating systems that were built this way. GNU/Linux and Mac OS X are also built this way. Modern releases of Microsoft Windows such as Windows Vista implement a graphics subsystem that is mostly in user-space; however the graphics drawing routines of versions between Windows NT 4.0 and Windows Server 2003 exist mostly in kernel space. Windows 9x had very little distinction between the interface and the kernel.
Many computer operating systems allow the user to install or create any user interface they desire. The X Window System in conjunction with GNOME or KDE is a commonly found setup on most Unix and Unix-like (BSD, GNU/Linux, Solaris) systems. A number of Windows shell replacements have been released for Microsoft Windows, which offer alternatives to the included Windows shell, but the shell itself cannot be separated from Windows.
Numerous Unix-based GUIs have existed over time, most derived from X11. Competition among the various vendors of Unix (HP, IBM, Sun) led to much fragmentation, though an effort to standardize in the 1990s to COSE and CDE failed for various reasons, and were eventually eclipsed by the widespread adoption of GNOME and KDE. Prior to free software-based toolkits and desktop environments, Motif was the prevalent toolkit/desktop combination (and was the basis upon which CDE was developed).
Graphical user interfaces evolve over time. For example, Windows has modified its user interface almost every time a new major version of Windows is released, and the Mac OS GUI changed dramatically with the introduction of Mac OS X in 1999.[23]
Real-time operating systems
A real-time operating system (RTOS) is a multitasking operating system intended for applications with fixed deadlines (real-time computing). Such applications include some small embedded systems, automobile engine controllers, industrial robots, spacecraft, industrial control, and some large-scale computing systems.
An early example of a large-scale real-time operating system was Transaction Processing Facility developed by American Airlines and IBM for the Sabre Airline Reservations System.
Embedded systems that have fixed deadlines use a real-time operating system such as VxWorks, PikeOS, eCos, QNX, MontaVista Linux and RTLinux. Windows CE is a real-time operating system that shares similar APIs to desktop Windows but shares none of desktop Windows’ codebase[citation needed]. Symbian OS also has an RTOS kernel (EKA2) starting with version 8.0b.
Some embedded systems use operating systems such as Palm OS, BSD, and GNU/Linux, although such operating systems do not support real-time computing.
Operating system development as a hobby
Operating system development is one of the most complicated activities in which a computing hobbyist may engage. A hobby operating system may be classified as one whose code has not been directly derived from an existing operating system, and has few users and active developers. [24]
In some cases, hobby development is in support of a «homebrew» computing device, for example, a simple single-board computer powered by a 6502 microprocessor. Or, development may be for an architecture already in widespread use. Operating system development may come from entirely new concepts, or may commence by modeling an existing operating system. In either case, the hobbyist is his/her own developer, or may interact with a small and sometimes unstructured group of individuals who have like interests.
Examples of a hobby operating system include ReactOS and Syllable.
Diversity of operating systems and portability
Application software is generally written for use on a specific operating system, and sometimes even for specific hardware. When porting the application to run on another OS, the functionality required by that application may be implemented differently by that OS (the names of functions, meaning of arguments, etc.) requiring the application to be adapted, changed, or otherwise maintained.
This cost in supporting operating systems diversity can be avoided by instead writing applications against software platforms like Java, or Qt for web browsers. These abstractions have already borne the cost of adaptation to specific operating systems and their system libraries.
Another approach is for operating system vendors to adopt standards. For example, POSIX and OS abstraction layers provide commonalities that reduce porting costs.
See also
- Comparison of operating systems
- Usage share of operating systems
- Computer systems architecture
- Disk operating system
- Electronic medical record
- Handheld computers
- History of IBM mainframe operating systems
- Interruptible operating system
- List of operating systems
- Microcontroller
- Network operating system
- Operating System Projects
- Operating systems
- Object-oriented operating system
- PCjacking
- System call
- System image
- Timeline of operating systems
- Trusted operating system
- Hypervisor
References
- ^ Stallings (2005). Operating Systems, Internals and Design Principles. Pearson: Prentice Hall. p. 6.
- ^ Dhotre, I.A. (2009). Operating Systems.. Technical Publications. p. 1.
- ^ «Operating System Market Share». Net Applications. http://marketshare.hitslink.com/operating-system-market-share.aspx?qprid=10.
- ^ Hansen, Per Brinch, ed (2001). Classic Operating Systems. Springer. pp. 4–7. ISBN 038795113X. http://books.google.com/?id=-PDPBvIPYBkC&lpg=PP1&pg=PP1#v=onepage&q.
- ^ http://www.apple.com/macosx/lion/
- ^ Usage share of operating systems
- ^ a b «Top 5 Operating Systems from January to April 2011». StatCounter. October 2009. http://gs.statcounter.com/#os-ww-monthly-201101-201104-bar. Retrieved November 5, 2009.
- ^ IDC report into Server market share
- ^ GNU/Linux still top embedded OS
- ^ TOP500 List – November 2010 (1–100) | TOP500 Supercomputing Sites
- ^ http://www.hyperion-entertainment.biz/
- ^ «Global Web Stats». Net Market Share, Net Applications. May 2011. http://marketshare.hitslink.com/operating-system-market-share.aspx?qprid=8. Retrieved 2011-05-07.
- ^ «Global Web Stats». W3Counter, Awio Web Services. September 2009. http://www.w3counter.com/globalstats.php. Retrieved 2009-10-24.
- ^ «Operating System Market Share». Net Applications. October 2009. http://marketshare.hitslink.com/operating-system-market-share.aspx?qprid=8. Retrieved November 5, 2009.
- ^ «w3schools.com OS Platform Statistics». http://www.w3schools.com/browsers/browsers_os.asp. Retrieved October 30, 2011.
- ^ «Stats Count Global Stats Top Five Operating Systems». http://gs.statcounter.com/#os-ww-monthly-201010-201110. Retrieved October 30, 2011.
- ^ http://support.microsoft.com/kb/130179/EN-US
- ^ http://support.microsoft.com/kb/134748/en
- ^ http://support.microsoft.com/kb/163354/en
- ^ «Operating System Share by Groups for Sites in All Locations January 2009». http://news.netcraft.com/SSL-Survey/CMatch/osdv_all.
- ^ «Behind the IDC data: Windows still No. 1 in server operating systems». ZDNet. 2010-02-26. http://blogs.zdnet.com/microsoft/?p=5408.
- ^ Stallings, William (2008). Computer Organization & Architecture. New Delhi: Prentice-Hall of India Private Limited. pp. 267. ISBN 978-81-203-2962-1.
- ^ Poisson, Ken. «Chronology of Personal Computer Software». Retrieved on 2008-05-07. Last checked on 2009-03-30.
- ^ «My OS is less hobby than yours». Osnews. December 21, 2009. http://www.osnews.com/story/22638/My_OS_Is_Less_Hobby_than_Yours. Retrieved December 21, 2009.
Further reading
- Auslander, Marc A.; Larkin, David C.; Scherr, Allan L. (1981). The evolution of the MVS Operating System. IBM J. Research & Development. http://www.research.ibm.com/journal/rd/255/auslander.pdf.
- Deitel, Harvey M.; Deitel, Paul; Choffnes, David. Operating Systems. Pearson/Prentice Hall. ISBN 978-0-13-092641-8.
- Bic, Lubomur F.; Shaw, Alan C. (2003). Operating Systems. Pearson: Prentice Hall.
- Silberschatz, Avi; Galvin, Peter; Gagne, Greg (2008). Operating Systems Concepts. John Wiley & Sons. ISBN 0-470-12872-0.
External links
- Operating Systems at the Open Directory Project
- Multics History and the history of operating systems
- How Stuff Works — Operating Systems
- Help finding your Operating System type and version
| v · d · eOperating system | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| General |
History · Timeline · List · Comparison · Usage share · Development · Advocacy |
||||||||||
| Kernel |
|
||||||||||
| Process management |
|
||||||||||
| Memory management |
Memory protection · Segmentation · Paging · Segmentation fault · General protection fault · Bus error |
||||||||||
| Examples |
AmigaOS · BeOS · BSD · DOS · GNU · Linux · Mac OS · MorphOS · OS/2 · ReactOS · Solaris · Unix · Windows · more… |
||||||||||
| Miscellaneous concepts |
Boot loader · Live CD · Live USB · PXE · API · Virtual file system · Virtual tape library · Computer network · CLI · TUI · GUI · VUI · HAL |
| v · d · eSystems and systems science | |
|---|---|
| Systems categories |
Systems theory · Systems science · Systems scientists (Conceptual · Physical · Social) |
| Systems |
Biological · Complex · Complex adaptive · Conceptual · Database management · Dynamical · Economical · Ecosystem · Formal · Global Positioning System · Human anatomy · Information systems · Legal systems of the world · Systems of measurement · Metric system · Multi-agent system · Nervous system · Nonlinearity · Operating system · Physical system · Political system · Sensory system · Social structure · Solar System · Systems art |
| Theoretical fields |
Chaos theory · Complex systems · Control theory · Cybernetics · Living systems · Sociotechnical systems theory · Systems biology · System dynamics · Systems ecology · Systems engineering · Systems neuroscience · Systems psychology · Systems science · Systems theory |
| Systems scientists |
Russell L. Ackoff · William Ross Ashby · Béla H. Bánáthy · Gregory Bateson · Richard E. Bellman · Stafford Beer · Ludwig von Bertalanffy · Murray Bowen · Kenneth E. Boulding · C. West Churchman · George Dantzig · Heinz von Foerster · Jay Wright Forrester · George Klir · Edward Lorenz · Niklas Luhmann · Humberto Maturana · Margaret Mead · Donella Meadows · Mihajlo D. Mesarovic · James Grier Miller · Howard T. Odum · Talcott Parsons · Ilya Prigogine · Anatol Rapoport · Claude Shannon · Francisco Varela · Kevin Warwick · Norbert Wiener · Anthony Wilden · Charles A S Hall |
Одной из самых распространенных ошибок при старте ОС, когда после первичной проверки в BIOS Windows или Linux не загружаются, является сбой с появлением на экране строки Operating system not found. Что делать в этом случае, далее и будет рассмотрено. В принципе, и сама ошибка, и методика ее исправления практически идентичны тем, которые применяются для устранения сбоя, когда выдается уведомление о потерянной (недоступной) операционной системе (Missing operating system), хотя имеет отличие только в том, что проблема никоим образом не связана с воздействием вирусов и вредоносных кодов, а больше относится к аппаратно-программной части самой компьютерной системы. В качестве примера возьмем Windows-системы, которые у нас являются более распространенными.
Отключение внешних USB устройств от компьютера
Если на компьютере подключены несколько внутренних жестких дисков, внешние и USB-флешки, вполне вероятно, что BIOS пытается найти операционную систему в неположенном месте. Следовательно, не обнаружив систему Windows, выдает ошибку «Не найдено операционной системы».
- Чтобы решить эту проблему, нужно отключить все внешние устройства хранения, подключенные к USB-портам, и повторить попытку. Мы также можем проверить наш оптический дисковод, чтобы убедиться, что он не пытается загрузить неправильный DVD.
Если после этого проблема все еще не решена, следующим шагом будет переход в BIOS настройки.
Методы исправления ошибки error 1962 no operating system found:
Лучший способ определить проблему — проверить состояние жесткого диска или SSD
-соединения в
BIOS
. Это поможет определить правильно или нет, подключен ваш жесткий диск.
Чтобы проверить состояние, просто откройте BIOS
вашего компьютера при запуске и найдите системную информацию, в меню
BIOS.
Условие № 1: Что делать, если ваш жесткий диск есть в списке в BIOS?
Если это так, то вполне возможно, что какое-то внешнее запоминающее устройство или может быть загрузочный том вашего жесткого диска создает какую-то проблему с BIOS.
Итак, как это исправить:
Способ 1
— Отключите все внешние устройства хранения, если они подключены, а затем снова загрузите компьютер. Если ошибка не появится, некоторые из ваших внешних
USB
создают проблему. Если она все еще осталась, попробуйте следующий способ.
Способ
3
Используйте средство восстановления при запуске, поскольку оно восстановит загрузочный том Windows. Эти ссылки помогут вам в этом. >> >>
Если ничего не может, боюсь, что придется переустанавливать операционную систему.
Условие № 2: Что делать, если вашего жесткого диска нет в списке BIOS?
Если вашего жесткого диска нет в списке BIOS, то вполне возможно, что эта проблема может быть связана с неисправностью HDD / SSD;
Изменение приоритета загрузки BIOS
Зайдите в конфигурации BIOS нажатием кнопок F2, F12 или Delete. После этого перейдите в раздел конфигурации Boot и выставить на первое место в графе Priority жесткий диск на котором рабочая и основная операционная система Windows. В разных версиях БИОС он называется по-разному, но вы ищите слово с сочетанием Priority, что означает «приоритетная загрузка». Вот несколько названий с разных BIOS: Hard Disk Priority, Boot Device Priority, Hard Disk Boot Priority.
После того как вы задали приоритет загрузки с жесткого диска на котором находится ваша система, не забудьте сохранить выставленные настройки кнопкой F10 и перезагрузите компьютер, чтобы убедиться «найдена ли система при включении компьютера».
Возможные причины возникновения
Если уж вдруг получился такой казус, и система постоянно выдает сообщение Operating System not found (Windows 7, 8 и т. д.), прежде всего, не паникуйте. Для начала просто проверьте, может быть, в компьютер или ноутбук вставлена флэшка, а в настройках BIOS приоритетным для загрузки является именно USB-девайс.
Если винчестер снимался или менялся на новый (это касается стационарных компьютеров), очень может быть, что при повторном его подключении были неправильно или неплотно подключены соответствующие шлейфы. Давайте посмотрим, что можно сделать в такой ситуации.
Включить или отключить Безопасную загрузку
Если вы используете современный компьютер с операционной системой, такой как Windows 8 или Windows 10, тогда возможно причина, по которой наша Windows не запускается, заключается в неправильной настройке безопасной загрузки UEFI.
Зайдите обратно в BIOS, найдите раздел конфигурации Secure Boot (Безопасная загрузка) и деактивируйте его или активируйте, если он отключен, чтобы проверить пропала ли ошибка «Операционная система не найдена при загрузке компьютера».
В разных версиях BIOS или UEFI расположение настроек выглядит по разному, но вы в любой версии БИОСа ищите графу Secure Boot, пробуйте отключить или включить.
В данной ошибке говорится о том, что операционка не найдена и нужно отключить все диски, её содержащие. Так сказать, небольшая подсказка, то проблема может быть связана именно с накопителями. Конечно, такое бывает не всегда, то есть это даже не физическое повреждение диска. Скорее всего из-за манипуляций пользователя при загрузке системы BIOS не смогла обнаружить загрузочную запись системы. В одной из статей про ошибку был описан похожий случай.
Если проблема в диске, то вероятно подсоединенные шлейфы могли быть повреждены или отсоединены. Это нужно проверить в первую очередь. Помимо этого, попробуйте отключить все внешние устройства – флешки, внешние жёсткие диски, карт ридеры и модемы. Короче всё, что подключается по USB и имеет понятие накопитель. А еще, как было рекомендовано из текста ошибки — отключить другие диски, на которых система не установлена, если диск один, то этот момент пропускаем.
Сбросьте BIOS на заводские настройки
В нижней части меню BIOS вы увидите ключ для настроек по умолчанию или сброс BIOS. На моей машине это F9. Подтвердите свое решение при появлении запроса и перезапустите компьютер.
Если вы не нашли примерную кнопку, как F9 для сброса настроек на заводские, то ищите строку Load Setup Default и сбросьте БИОС.
Проверка БИОС
Сначала потребуется осуществить проверку последовательности загрузки BIOS, удостоверившись в том, что HDD является приоритетным. В ином случае, надо поменять порядок вручную. Делается это так:
- войдя в БИОС, спуститься чуть ниже и выбрать «StandartCMOSFeatures»;
- отыскать HDD и спуститься к нему, нажать «Enter»;
- отобразятся дополнительные настройки HDD. Нужно нажать на «AccessMode» и выбрать «Large», сохранить изменения и выйти из BIOS с помощью F10.
Восстановить MBR жесткого диска
Если ваш жесткий диск с операционной системой помещен первым, но компьютер по-прежнему не загружается, возможно, что некоторые из начальных секторов диска были повреждены, такие-как основная загрузочная запись (MBR), загрузочная запись DOS (DBR) , или База данных конфигурации загрузки (BCD).
Ремонт этих секторов довольно прост. Все, что нам нужно — это создать установочную флешку Windows и через неё войти в дополнительные параметры загрузки.
Далее найдите «Командную строку», чтобы запустить ее, пройдите по пути Устранение неполадок > Дополнительные параметры > Командная строка.
Введите следующие команды в CMD по порядку, нажимая enter. Для выполнение каждой команды может потребоваться время.
- bootrec.exe / fixmbr
- bootrec.exe / fixboot
- bootrec.exe / rebuildbcd
Как избавиться от ошибки An operating system wasn t found
Конечно, парочку советов я уже дал чуть выше, но повторюсь. Так как многие пользователи просто не читают внимательно, как я заметил.
Отключите все внешние устройства, которые связаны по USB, особенно это касается накопителей памяти;
Проверьте, хорошо ли соединены шлейфы и прочие кабели с дисками. Проверьте подключение других комплектующих. Убедитесь в целостности оборудования в общем.
Войдите и проверьте наличие жёсткого диска в разделе Boot
. Если он отображается, значит диск работает, но проблема может касаться загрузочной записи Windows. Попробуйте . Чуть не забыл. Еще посмотрите на вкладке Boot правильное расположение устройств загрузки. Диск, на котором находится система должен быть на первом месте.
Также наличие и работоспособность диска можно проверить через .
Активируйте раздел Windows
Возможно, что раздел, на котором установлена Windows, отключен. Вы можете исправить это, используя собственный инструмент diskpart Windows. Чтобы выполнить следующие шаги, вам снова понадобится USB-носитель для установки Windows. Запустите командную строку, как описано выше, через диск восстановление или установочную флешку Windows и в командной строке вбейте следующие команды:
- diskpart — Запуск инструмента.
- list disk — Список подключенных дисков к компьютеру.
- select disk 0 — Выбор жесткого диска на котором нужно активировать раздел. В моем случае, основной жесткий диск 0.
- list volume — Показывает разделы на выбранном жестком диски.
- select volume 2 — Выбрать локальный диск для активации. Выбирайте тот, где установлена сама система widows.
- active — Активировать раздел.
Перезагрузите компьютер и удостоверьтесь, пропала ли ошибка при включении компьютера An operating system wasn’t found. Ttry disconnecting any drives that don’t contain an operating system. Press Ctrl+ Alt+Del to restart, что означает, операционная система не найдена, нажмите для перезагрузки ctrl+alt+del.
Смотрите еще:
- Установка Windows на данный диск невозможна, так как выбранный диск имеет стиль разделов GPT
- Как ограничить скорость интернета для скачивания обновлений Windows 10
- Windows не удается завершить форматирование
- Обновление функции до Windows 10 Версия 1709 Ошибка 0x80d02002
- Что такое ACPI INT33A0 0 в Windows 10 и как исправить
comments powered by HyperComments
How to fix «An operating system wasn»t found» error
1) Download Emergency Boot Kit
and deploy it to USB thumbdrive according to the instructions , then set up your BIOS to boot from USB thumbdrive. You need full version of Emergency Boot Kit to actually write changes to the disk, but it»s recommended to try demo version to make sure there are no hardware incompatibilities.
2) Boot into Emergency Boot Kit:
3) Run File Manager from the main menu:
4) Press Alt+F1 and choose your boot partition from the menu. For Windows 10 and Windows 8/8.1 this partition should have «System Reserved» volume label and is expected to be small (100-500MB). Use UP and DOWN arrow keys and ENTER to navigate the menu:
5) In this example, BOOTMGR file is missing from boot partition. If it exists in your environment, delete it (set cursor to the file using arrow keys UP and DOWN and then press F8). If BOOTMGR file is not deleteable, then rename it (for example, to BOOTMGR.OLD by pressing F6 key):
6) Insert Windows 10 installation USB thumbdrive to any of your computer»s USB ports and press Alt+F2. Choose Windows 10 installation USB thumbdrive drive from the menu using UP and DOWN arrow keys:
(Alternative approach
: if don»t have Windows 10 installation USB thumbdrive, then you can recover a copy of this file from WindowsBootPCAT folder on your system partition)

9) Press F5 to copy BOOTMGR to the left panel. Confirm with ENTER key:
Очень часто при отказе Windows 10 запускаться, на экране высвечивается ошибка Boot failure, а также An operating system wasn’t found. Press Ctrl+Alt+Del to restart. Причины возникновения этих ошибок одинаковые, способы их устранения тоже аналогичны.
В «десятке» могут появляться обе эти ошибки. К примеру, при удалении файла bootmgr на операционках с Legacy выскакивает первая ошибка, а при ликвидации всего раздела с загрузчиком появляется вторая ошибка.
Перед тем как начинать устранение ошибок, необходимо провести те манипуляции, которые написаны в тексте уведомления, а затем перезапустить компьютер. Первым делом необходимо отключить от ПК все накопители, которые не содержать операционку. Это могут быть флешки, оптические носители и сторонние винчестеры. Кроме того, к этой категории можно отнести все, что подключается по USB, кроме элементов управления.
Кроме того, необходимо проверить, чтобы запуск выполнялся с первого винчестера или файла Windows Boot Manager для систем UEFI. В таком случае нужно перейти в BIOS и проверить порядок запуска устройств. Для выполнения этого проще будет использовать Boot Menu. Если при его применении «десятка» запускается нормально, тогда стоит перейти в BIOS и изменить параметры.
Если это не принесло желаемого результата, тогда подобные ошибки возникают по более серьезным причинам, поэтому устранить их будет немного сложнее.
Настройка загрузчика «десятки»
Как можно понять из вышеописанного, искусственное возникновение ошибок довольно частое явление, если самостоятельно испортить содержимое скрытого отдела, зарезервированного операционкой или с загрузчиком операционки. В таком случае необходимо при появлении подобных ошибок попытаться восстановить загрузчик операционки.
Выполнить это можно довольно просто. Необходимо обзавестись загрузочным накопителем или диском восстановления с операционкой такой же разрядности, которая инсталлирована на компьютер. Стоит отметить, что подобный накопитель можно создать на другом компьютере.
Далее необходимо выполнить загрузку ПК с этого накопителя. Если применяется инсталляционный образ системы, тогда необходим перейти в среду восстановления. Для этого необходимо на экране указания языка кликнуть «Восстановление системы».
Здесь требуется указать «Поиск и устранение неисправностей». В следующем окне необходимо нажать «Дополнительные параметры». После этого требуется нажать «Восстановление при загрузке». Затем требуется выбрать версию операционки.
После этого запустится автоматический поиск проблем с загрузчиком и его восстановление. Эта функция функционирует отлично и в большинстве случаев вмешательство пользователя не требуется.
Если это не принесет желаемого результата, и ошибка опять высветится на черном экране, при этом загрузка должна выполняться с необходимого накопителя, стоит попытаться реанимировать загрузчик в ручном режиме.
Кроме того, проблемы с загрузчиком могут возникать после выключения одного из винчестеров от ПК. При этом загрузчик должен располагаться на этом накопителе, а операционка на другом. В таком случае необходимо потупить определенным образом.
Первым делом необходимо в начале диска с операционкой отвести немного места под FAT32 для UEFI или NTFS для Legacy. Выполнить это можно с использованием бесплатного образа MiniTool Bootable Partition Manager. После этого необходимо провести восстановление загрузчика в ручном режиме с использованием bcdboot.exe
Ошибка запуска «десятки» из-за проблем с винчестером или SSD
Если никакие манипуляции по реанимированию загрузчика не помогут устранить эти ошибки в «десятке», в таком случае на них могут влиять неисправности с винчестером или утерянные файлы.
Если есть предположения, что что-то из этого произошло, а на это могут влиять сбои питания, дефекты винчестера и др., в таком случае необходимо провести несколько манипуляций.
Первым делом необходимо переподключить винчестер или твердотельный накопитель. Для этого требуется отсоединить SATA шлейфы и шнуры питания от материнки и винчестера. Также можно отключить и остальные провода.
Затем требуется загрузиться в среде восстановления, и применяя командную строку, требуется просканировать винчестер на ошибки. Кроме того, есть возможность сбросить систему со стороннего накопителя. Также есть вариант устранения ошибки путем установки операционки с нуля, при этом выполняя форматирование.
Вот, в принципе, и все возможные причины появления проблем и методы их устранения. Очень хорошо, будет, если устранить проблему получиться простым отключением накопителей и восстановлением загрузчика. Если это не помогло, тогда необходимо переустановить операционку.
Всем известно, что операционная система в основном находится на жестком диске или на SSD. И когда люди видят эту ошибку на экране, первая мысль которая возникает в голове о том, что неисправен или поврежден именно жесткий диск. В большинстве случаев это так и есть, хотя бывают и исключения. Возможно повреждение загрузочного тома вашей операционной системы;
И после этих двух возможных причин, то приходит к возможности вашего жесткого диска, чтобы он мог немного стать неисправным, и я думаю, вы тоже это исправите;
Normal boot sequence
Normally computer boots as shown below (Windows 7 boot sequence is shown as example):
- BIOS loads 1st sector from HDD (Master Boot Record), verifies 55 AA signature and transfers control to Master Boot Record.
- Master Boot Record scans partition table for active partition, then it loads 1st sector from active partition, verifies 55 AA signature, and transfers control to Boot Sector.
- Boot Sector loads 15 additional sectors from the beginning of disk (Volume Boot Record) and transfers control to first additional sector of VBR.
- Volume Boot Record loads BOOTMGR file from root directory of boot partition into the memory and transfers control to it.
- BOOTMGR loads BootBCD registry hive and displays boot menu. BOOTMGR is able to run memory test and set safe mode boot flag per explicit user request. But normally, it loads winload.exe when computer boots normally (cold startup) or winresume.exe (when computer resumes from hibernation).
- Winload.exe opens SYSTEM registry hive, gets list of drivers, loads NTOSKRNL.exe, loads drivers (*.SYS files) and transfers control to NTOSKRNL.exe.
- Winresume.exe loads memory dump from hiberfil.sys and transfers control to it.
Objectives
Upon completion of this chapter, you will be able to answer the following questions:
- What is the history of the Windows operating system?
- What is the architecture of Windows and its operation?
- How do you configure and monitor Windows?
- How is Windows kept secure?
Key Terms
This chapter uses the following key terms. You can find the definitions in the Glossary.
Disk Operating System (DOS)
MS-DOS
vulnerability
Windows Defender
encryption
firewall
hardware abstraction layer (HAL)
kernel
File Allocation Table (FAT)
Extended FAT (exFAT)
Hierarchical File System Plus (HFS+)
Extended File System (EXT)
New Technology File System (NTFS)
Alternate Data Streams (ADSs)
Partition Boot Sector
Master File Table (MFT)
System Files
Basic Input-Output System (BIOS)
Unified Extensible Firmware Interface (UEFI)
master boot record (MBR)
Boot Configuration Database (BCD)
Kernel Mode Code Signing (KMCS)
Session Manager Subsystem (SMSS)
processes
thread
services
registry
domain
domain controllers (DCs)
command line interface (CLI)
PowerShell
Windows Management Instrumentation (WMI)
Task Manager page 49Resource Monitor
Server Message Block (SMB)
netstat
Event Viewer
Introduction (2.0)
From its humble beginnings over 30 years ago in 1985, the Windows operating system has seen many iterations; from Windows 1.0 to today’s current desktop version, Windows 10, and server version, Windows Server 2016.
This chapter covers some of the basic concepts of Windows, including how the operating system works and the tools used to secure Windows endpoints.
Class Activity 2.0.1.2: Identify Running Processes
In this lab, you will use TCP/UDP Endpoint Viewer, a tool in Sysinternals Suite, to identify any running processes on your computer.
Windows Overview (2.1)
In this section, you will learn about Window’s history, architecture, and operations.
Windows History (2.1.1)
In this topic, you will learn about the beginnings of Windows, the history of Windows versions, the Windows graphical user interface (GUI), and Windows vulnerabilities.
Disk Operating System (2.1.1.1)
The first computers did not have modern storage devices such as hard drives, optical drives, or flash storage. The first storage methods used punch cards, paper tape, magnetic tape, and even audio cassettes.
Floppy disk and hard disk storage requires software to read from, write to, and manage the data that they store. A Disk Operating System (DOS) is an operating system that the computer uses to enable these data storage devices to read and write files. The DOS provides a file system which organizes the files in a specific way on the disk. MS-DOS is a DOS created by Microsoft. MS-DOS used a command line as the interface for people to create programs and manipulate data files, as shown in Figure 2-1.
With MS-DOS, the computer had a basic working knowledge of how to access the disk drive and load the operating system files directly from the disk as part of the boot process. When it was loaded, MS-DOS could easily access DOS because it was built into the operating system.
Early versions of Windows consisted of a GUI that ran over MS-DOS, with the first being Windows 1.0 in 1985. The disk operating system still controlled the computer and its hardware. A modern operating system like Windows 10 is not considered a disk operating system. It is built on Windows NT, which stands for “New Technology.” The operating system itself is in direct control of thecomputer and its hardware. NT is an OS with support for multiple user processes. This is much different than the single-process, single-user MS-DOS.
Today, anything that used to be accomplished through the command line interface of MS-DOS can be accomplished in the Windows GUI. You can still experience what it was like to use MS-DOS by opening a command window, but what you see is no longer MS-DOS, it is a function of Windows. To experience a little of what it was like to work in MS-DOS, open a command window by typing cmd in Windows Search and pressing Enter. These are some commands that you can use:
- dir: Shows a listing of all the files in the current directory (folder)
- cd directory: Changes the directory to the indicated directory
- cd..: Changes the directory to the directory above the current directory
- cd\: Changes the directory to the root directory (often C:)
- copy: Copies files to another location
- del: Deletes one or more files
- find: Searches for text in files
- mkdir: Creates a new directory
- ren: Renames a file
- help: Displays all the commands that can be used, with a brief description
- help command: Displays extensive help for the indicated command
Windows Versions (2.1.1.2)
Since 1993, there have been more than 20 releases of Windows that are based on the NT operating system. Most of these versions were for use by the general public and businesses because of the file security offered by the file system that was used by the NT OS. Businesses also adopted NT OS-based Windows operating systems. This is because many editions were built specifically for the workstation, professional, server, advanced server, and datacenter server, to name just a few of the many purpose-built versions.
Beginning with Windows XP, a 64-bit edition was available. The 64-bit operating system was an entirely new architecture. It had a 64-bit address space instead of a 32-bit address space. This is not simply twice the amount of spacebecause these bits are binary numbers. While 32-bit Windows can address a little less than 4 GB of RAM, 64-bit Windows can theoretically address 16.8 million terabytes. When the OS and the hardware all support 64-bit operation, extremely large data sets can be used. These large data sets include very large databases, scientific computing, and manipulation of high-definition digital video with special effects. In general, 64-bit computers and operating systems are backward-compatible with older, 32-bit programs, but 64-bit programs cannot be run on older, 32-bit hardware.
With each subsequent release of Windows, the operating system has become more refined by incorporating more features. Windows 7 was offered with six different editions, Windows 8 was offered with as many as four different editions, and Windows 10 is offered with eight different editions! Each edition not only offers different capabilities, but also different price points. Microsoft has said that Windows 10 is the last version of Windows, that Windows has become a service rather than just an OS. They say that rather than purchasing new operating systems, users will just update Windows 10 instead.
Table 2-1 lists the popular modern versions of Windows.
Table 2-1 Modern Windows Versions
| OS Version | Editions |
|---|---|
| Windows 7 | Starter, Home Basic, Home Premium, Professional, Enterprise, Ultimate |
| Windows Server 2008 R2 | Foundation, Standard, Enterprise, Datacenter, Web Server, HPC Server, Itanium-Based Systems |
| Windows Home Server 2011 | None |
| Windows 8 | Windows 8, Windows 8 Pro, Windows 8 Enterprise, Windows RT |
| Windows Server 2012 | Foundation, Essentials, Standard, Datacenter |
| Windows 8.1 | Windows 8.1, Windows 8.1 Pro, Windows 8.1 Enterprise, Windows RT 8.1 |
| Windows Server 2012 R2 | Foundation, Essentials, Standard, Datacenter |
| Windows 10 | Home, Pro, Pro Education, Enterprise, Education, IoT Core, Mobile, Mobile Enterprise |
| Windows Server 2016 | Essentials, Standard, Datacenter, Multipoint Premium Server, Storage Server, Hyper-V Server |
Windows GUI (2.1.1.3)
Windows has a graphical user interface (GUI) for users to work with data files and software. The GUI has a main area that is known as the Desktop, shown in Figure 2-2. The Desktop can be customized with various colors and background images. Windows supports multiple users, so each user can customize the Desktop to their liking. The Desktop can store files, folders, shortcuts to locations and programs, and applications. The Desktop also has a recycle bin icon, where files are stored when the user deletes them. Files can be restored from the recycle bin or the recycle bin can be emptied of files, which truly deletes them.
Figure 2-2 Windows 10 GUI
At the bottom of the desktop is the Task Bar. The Task Bar has three areas that are used for different purposes. At the left is the Start menu. It is used to access all of the installed programs, configuration options, and the search feature. At the center of the Task Bar, users place quick launch icons that run specific programs or open specific folders when they are clicked. Finally, on the right of the Task Bar is the notification area. The notification area shows, at a glance, the functionality of many different programs and features. For example, a blinking envelope icon may indicate new email, or a network icon with a red “x” may indicate a problem with the network.
Often, right-clicking an icon will bring up additional functions that can be used.
This list is known as a Context Menu, shown in Figure 2-3. There are Context Menus for the icons in the notification area, and also for quick launch icons, system configuration icons, and for files and folders. The Context Menu provides many of the most commonly used functions by just clicking. For example, the Context Menu for a file will contain such items as Copy, Delete, Share, and Print. To open folders and manipulate files, Windows uses Windows
File Explorer, also shown in Figure 2-3.
Figure 2-3 Windows File Explorer
Windows File Explorer is a tool used to navigate the entire file system of a computer, including multiple storage devices and network locations. Using Windows File Explorer, you can easily create folders, copy files and folders, and move them around to different locations and devices. Basically, the tool has two main windows. The one on the left allows quick navigation to storage devices, parent folders, and child folders. The one on the right shows the content of the location that is selected in the left pane.
Operating System Vulnerabilities (2.1.1.4)
Operating systems consist of millions of lines of code. Installed software can also contain millions of lines of code. With all this code comes vulnerabilities. A vulnerability is some flaw or weakness that can be exploited by an attacker to reduce the viability of a computer’s information. To take advantage of an operating system vulnerability, the attacker must use a technique or a tool to exploit the vulnerability. The attacker can then use the vulnerability to get the computer to act in a fashion outside of its intended design. In general, the goal isto gain unauthorized control of the computer, change permissions, or manipulate data.
These are some common Windows OS security recommendations:
- Virus or malware protection: By default, Windows uses Windows Defender. Windows Defender provides a suite of protection tools built into the system. If Windows Defender is turned off, the system becomes more vulnerable to attacks and malware.
- Unknown or unmanaged services: There are many services that run behind the scenes. It is important to make sure that each service is identifiable and safe. With an unknown service running in the background, the computer can be vulnerable to attack.
- Encryption: When data is not encrypted, it can easily be gathered and exploited. This is important not only for desktop computers, but especially mobile devices.
- Security policy: A good security policy must be configured and followed. Many settings in the Windows Security Policy control can prevent attacks.
- Firewall: By default, Windows uses Windows Firewall to limit communication with devices on the network. Over time, rules may no longer apply. For example, a port may be left open that should no longer be readily available. It is important to review firewall settings periodically to ensure that the rules are still applicable and remove any that no longer apply.
- File and share permissions: These permissions must be set correctly. It is easy to just give the “Everyone” group Full Control, but this allows all people to do what they want to all files. It is best to provide each user or group with the minimum necessary permissions for all files and folders.
- Weak or no password: Many people choose weak passwords or do not use a password at all. It is especially important to make sure that all accounts, especially the Administrator account, have a very strong password.
- Login as Administrator: When a user logs in as an administrator, any program that they run will have the privileges of that account. It is best to log in as a Standard User and only use the Administrator password to accomplish certain tasks.
Windows Architecture and Operations (2.1.2)
In this topic, you will learn about the Windows hardware abstraction layer, user mode, kernel mode, file system, boot process, startup, shutdown, processes, threads, services, memory allocation, handles, and registry.
Hardware Abstraction Layer (2.1.2.1)
Windows computers use many different types of hardware. The operating system can be installed on a computer off of the shelf, or a computer built from the ground up. When the operating system is installed, it must be isolated from differences in hardware. The basic Windows architecture is shown in Figure 2-4.
A hardware abstraction layer (HAL) is code that handles all of the communication between the hardware and the kernel. The kernel is the core of the operating system and has control over the entire computer. It handles all of the input and output requests, memory, and all of the peripherals connected to the computer.
Figure 2-4 Basic Windows Architecture
In some instances, the kernel still communicates with the hardware directly, so it is not completely independent of the HAL. The HAL also needs the kernel to perform some functions.
User Mode and Kernel Mode (2.1.2.2)
There are two different modes in which a CPU operates when the computer has Windows installed: user mode and kernel mode. Installed applications run in user mode, and operating system code runs in kernel mode. Code that is executing in kernel mode has unrestricted access to the underlying hardware and is capable of executing any CPU instruction. Kernel mode code also can reference any memory address directly. Generally reserved for the most trusted functions of the OS, crashes in code running in kernel mode stop the operation of the entire computer. Conversely, programs such as user applications run in user mode and have no direct access to hardware or memory locations. User mode code must go through the operating system to access hardware resources.
Because of the isolation provided by user mode, crashes in user mode are restricted to the application only and are recoverable. Most of the programs in Windows run in user mode. Device drivers, pieces of software that allow the operating system and a device to communicate, may run in either kernel or user mode, depending on the driver.
All of the code that runs in kernel mode uses the same address space. Kernel-mode drivers have no isolation from the operating system. If an error occurs with the driver running in kernel mode, and it writes to the wrong address space, the operating system or another kernel-mode driver could be adversely affected. In this respect, the driver might crash, causing the entire operating system to crash.
When user mode code runs, it is granted its own restricted address space by the kernel, along with a process created specifically for the application. The reason for this functionality is mainly to prevent applications from changing operating system code that is running at the same time. By having its own process, that application has its own private address space, rendering other applications unable to modify the data in it. This also helps to prevent the operating system and other applications from crashing if that application crashes.
Windows File Systems (2.1.2.3)
A file system is how information is organized on storage media. Some filesystems may be a better choice to use than others, depending on the type of media that will be used. These are the file systems that Windows supports:
- File Allocation Table (FAT): This is a simple file system supported by many different operating systems. FAT has limitations to the number of partitions, partition sizes, and file sizes that it can address, so it is not usually used for hard drives (HDs) or solid state drives (SSDs) anymore. Both FAT16 and FAT32 are available to use, with FAT32 being the most common because it has many fewer restrictions than FAT16.
- Extended FAT (exFAT): This is an extended version of FAT that has even fewer restrictions than FAT32, but is not supported very well outside of the Windows ecosystem.
- Hierarchical File System Plus (HFS+): This file system is used on macOS X computers and allows much longer filenames, file sizes, and partition sizes than previous file systems. Although it is not supported by Windows without special software, Windows is able to read data from HFS+ partitions.
- Extended File System (EXT): This file system is used with Linux-based computers. Although it is not supported by Windows, Windows is able to read data from EXT partitions with special software.
- New Technology File System (NTFS): This is the most commonly used file system when installing Windows. All versions of Windows and Linux support NTFS, while macOS X computers can only read an NTFS partition (they can write to an NTFS partition after installing special drivers).
NTFS is the most widely used file system for Windows for many reasons. NTFS supports very large files and partitions; it is very compatible with other operating systems. NTFS is also very reliable and supports recovery features. Most importantly, it supports many security features. Data access control is achieved through security descriptors. These security descriptors contain file ownership and permissions all the way down to the file level. NTFS also tracks many timestamps to track file activity. Sometimes referred to as MACE, the timestamps Modify, Access, Create, and Entry Modified are often used in forensic investigations to determine the history of a file or folder. NTFS also supports file system encryption to secure the entire storage media.
Alternate Data Streams
NTFS stores files as a series of attributes, such as the name of the file, or a timestamp. The data which the file contains is stored in the attribute $DATA, and is known as a data stream. By using NTFS, you can connect Alternate Data Streams (ADSs) to the file. This is sometimes used by applications that are storing additional information about the file. The ADS is an important factor when discussing malware. This is because it is easy to hide data in an ADS. An attacker could store malicious code within an ADS that can then be called from a different file.
In the NTFS file system, a file with an ADS is identified after the filename and a colon, for example, Testfile.txt:ADSdata. This filename indicates an ADS called ADSdata is associated with the file called Testfile.txt. An example of ADS is shown in Example 2-1.
Example 2-1 Alternate Data Stream
C:\ADS> echo "Alternative Data Here" > Textfile.txt:ADS C:\ADS> dir Volume in drive C is OS Volume Serial Number is F244-E247 Directory of C:\ADS 12/27/2017 03:03 PM <DIR> . 12/27/2017 03:03 PM <DIR> .. 12/27/2017 03:03 PM 0 Textfile.txt 1 File(s) 0 bytes 2 Dir(s) 402,725,310,464 bytes free C:\ADS> more < Testfile.txt:ADS "Alternative Data Here" C:\ADS> dir /r Volume in drive C has no label. Volume Serial Number is F244-E247 Directory of C:\ADS 12/27/2017 03:03 PM <DIR> . 12/27/2017 03:03 PM <DIR> .. 12/27/2017 03:03 PM 0 Textfile.txt 24 Textfile.txt:ADS:$DATA 1 File(s) 0 bytes 2 Dir(s) 402,725,310,464 bytes free C:\ADS>
- The first command places the text “Alternate Data Here” into an ADS of the file Testfile.txt called “ADS”.
- The next command, dir, shows that the file was created, but the ADS is not visible.
- The next command shows that there is data in the Testfile.txt:ADS data stream.
- The last command shows the ADS of the Testfile.txt file because the r switch was used with the dir command.
Before a storage device such as a disk can be used, it must be formatted with a file system. In turn, before a file system can be put into place on a storage device, the device needs to be partitioned. A hard drive is divided into areas called partitions. Each partition is a logical storage unit that can be formatted to store information, such as data files or applications. During the installation process, most operating systems automatically partition and format the available drive space with a file system such as NTFS.
NTFS formatting creates important structures on the disk for file storage, and tables for recording the locations of files:
- Partition Boot Sector: This is the first 16 sectors of the drive. It contains the location of the Master File Table. The last 16 sectors contain a copy of the boot sector.
- Master File Table (MFT): This table contains the locations of all the files and directories on the partition, including file attributes such as security information and timestamps.
- System Files: These are hidden files that store information about other volumes and file attributes.
- File Area: The main area of the partition where files and directories are stored.
Note
When formatting a partition, the previous data may still be recoverable because not all the data is completely removed. The free space can be examined and files can be retrieved, which can compromise security. It is recommended to perform a secure wipe on a drive that is being reused. The secure wipe will write data to the entire drive multiple times to ensure there is no remaining data.
Windows Boot Process (2.1.2.4)
Many actions occur between the time when the computer power button is pressed and Windows is fully loaded, as shown in Figure 2-5.
Figure 2-5 Windows Boot Process
Two types of computer firmware exist: Basic Input-Output System (BIOS) and Unified Extensible Firmware Interface (UEFI). BIOS firmware was created in the early 1980s and works in the same way it did when it was created. As computers evolved, it became difficult for BIOS firmware to support all the newfeatures requested by users. UEFI was designed to replace BIOS and support the new features.
In BIOS firmware, the process begins with the BIOS initialization phase. This is when hardware devices are initialized and a power-on self-test (POST) is performed to make sure all of these devices are communicating. When the system disk is discovered, the POST ends. The last instruction in the POST is to look for the master boot record (MBR).
The MBR contains a small program that is responsible for locating and loading the operating system. The BIOS executes this code and the operating system starts to load.
In contrast to BIOS firmware, UEFI firmware has a lot of visibility into the boot process. UEFI boots by loading EFI program files, stored as .efi files in a special disk partition, known as the EFI System Partition (ESP).
Note
A computer that uses UEFI stores boot code in the firmware. This helps to increase the security of the computer at boot time because the computer goes directly into protected mode.
Whether the firmware is BIOS or UEFI, after a valid Windows installation is located, the Bootmgr.exe file is run. Bootmgr.exe switches the system from real mode to protected mode so that all of the system memory can be used.
Bootmgr.exe reads the Boot Configuration Database (BCD). The BCD contains any additional code needed to start the computer, along with an indication of whether the computer is coming out of hibernation, or if this is a cold start. If the computer is coming out of hibernation, the boot process continues with Winresume.exe. This allows the computer to read the Hiberfil.sys file, which contains the state of the computer when it was put into hibernation.
If the computer is being booted from a cold start, then the Winload.exe file is loaded. The Winload.exe file creates a record of the hardware configuration in the registry. The registry is a record of all of the settings, options, hardware, and software the computer has. The registry will be explored in depth later in this chapter. Winload.exe also uses Kernel Mode Code Signing (KMCS) to make sure that all drivers are digitally signed. This ensures that the drivers are safe to load as the computer starts.
After the drivers have been examined, Winload.exe runs Ntoskrnl.exe, whichstarts the Windows kernel and sets up the HAL. Finally, the Session Manager Subsystem (SMSS) reads the registry to create the user environment, start the Winlogon service, and prepare each user’s desktop as they log on.
Windows Startup and Shutdown (2.1.2.5)
There are two important registry items that are used to automatically start applications and services:
- HKEY_LOCAL_MACHINE: Several aspects of Windows configuration are stored in this key, including information about services that start with each boot.
- HKEY_CURRENT_USER: Several aspects related to the logged-in user are stored in this key, including information about services that start only when the user logs on to the computer.
Different entries in these registry locations define which services and applications will start, as indicated by their entry type. These types include Run, RunOnce, RunServices, RunServicesOnce, and Userinit. These entries can be manually entered into the registry, but it is much safer to use the Msconfig.exe tool. This tool is used to view and change all of the startup options for the computer. Use the search box to find and open the Msconfig tool.
There are five tabs which contain the configuration options:
General: Three different startup types can be chosen here. Normal loads all drivers and services. Diagnostic loads only basic drivers and services. Selective allows the user to choose what to load on startup. The General tab is shown in Figure 2-6.
Figure 2-6 General Tab of System Configuration
Boot: Any installed operating system can be chosen here to start. There are also options for Safe boot, which is used to troubleshoot startup. The Boot tab is shown in Figure 2-7.
Figure 2-7 Boot Tab of System Configuration
Services: All the installed services are listed here so that they can be chosen to start at startup. The Services tab is shown in Figure 2-8.
Figure 2-8 Services Tab of System Configuration
Startup: All the applications and services that are configured to automatically begin at startup can be enabled or disabled by opening Task Manager from this tab. The Startup tab is shown in Figure 2-9.
Figure 2-9 Startup Tab of System Configuration
Tools: Many common operating system tools can be launched directly from this tab. The Tools tab is shown in Figure 2-10.
Figure 2-10 Tools Tab of System Configuration
Shutdown
It is always best to perform a proper shutdown to turn off the computer. Files that are left open, services that are closed out of order, and applications that hang can all be damaged if the power is turned off without first informing the operating system. The computer needs time to close each application, shut down each service, and record any configuration changes before power is lost.
During shutdown, the computer will close user mode applications first, followed by kernel mode processes. If a user mode process does not respond within a certain amount of time, the OS will display notification and allow the user to wait for the application to respond, or forcibly end the process. If a kernel mode process does not respond, the shutdown will appear to hang, and it may be necessary to shut down the computer with the power button.
There are several ways to shut down a Windows computer: Start menu power options, the command line command shutdown, and using Ctrl-Alt-Delete and clicking the power icon. There are three different options from which to choose when shutting down the computer: Shutdown, which turns the computer off, Restart, which reboots the computer from scratch, and Hibernate, which records the current state of the computer and user environment and stores it in a file.
Hibernation allows the user to pick up right where they left off very quickly with all their files and programs still open.
Processes, Threads, and Services (2.1.2.6)
A Windows application is made up of processes. The application can have one or many processes dedicated to it. A process is any program that is currently executing. Each process that runs is made up of at least one thread. A thread is a part of the process that can be executed. The processor performs calculations on the thread. To configure Windows processes, search for Task Manager. The Processes tab of Task Manager is shown in Figure 2-11.
Figure 2-11 Windows Task Manager Processes Tab
All of the threads dedicated to a process are contained within the same address space. This means that these threads may not access the address space of any other process. This prevents corruption of other processes. Because Windows multitasks, multiple threads can be executed at the same time. The number of threads that can be executed at the same time is dependent on how manyprocessors the computer has.
Some of the processes that Windows runs are services. These are programs that run in the background to support the operating system and applications. They can be set to start automatically when Windows boots or they can be started manually. They can also be stopped, restarted, or disabled. Services provide long-running functionality, such as wireless or access to an FTP server. To configure Windows Services, search for services. The Windows Services control panel applet is shown in Figure 2-12. Be very careful when manipulating the setting of these services. Some programs rely on one or more services to operate properly. Shutting down a service may adversely affect applications, or other services.
Figure 2-12 Windows Services Control Panel Applet
Memory Allocation and Handles (2.1.2.7)
A computer works by storing instructions in RAM until the CPU processes them. The virtual address space for a process is the set of virtual addresses that the process can use. The virtual address is not the actual physical location in memory, but an entry in a page table that is used to translate the virtual address into the physical address.
Each process in a 32-bit Windows computer supports a virtual address space that enables addressing up to 4 gigabytes. Each process in a 64-bit Windows computer supports a virtual address space of 8 terabytes.
Each user space process runs in a private address space, separate from other user space processes. When the user space process needs to access kernel resources, it must use a process handle. This is because the user space process is not allowed to directly access these kernel resources. The process handle provides the access needed by the user space process without a direct connection to it.
One of the more powerful tools we use to view memory allocation is Sysinternals RamMap, shown in Figure 2-13.
Figure 2-13 Sysinternals RamMap
The Windows Registry (2.1. 2.8)
Windows stores all of the information about hardware, applications, users, and system settings in a large database known as the registry. The ways that these objects interact are also recorded, such as what files an application opens and all of the property details of folders and applications. The registry is a hierarchical database where the highest level is known as a hive, below which are keys, followed by subkeys. Values, which store data, are stored in keys and subkeys. The registry key can be up to 512 levels deep.
These are the five hives of the Windows registry:
- HKEY_CURRENT_USER (HKCU): Holds data concerning the currently logged-in user
- HKEY_USERS (HKU): Holds data concerning all the user accounts on the host
- HKEY_CLASSES_ROOT (HKCR): Holds data about object linking and embedding (OLE) registrations
- HKEY_LOCAL_MACHINE (HKLM): Holds system-related data
- HKEY_CURRENT_CONFIG (HKCC): Holds data about the current hardware profile
New hives cannot be created. The registry keys and values in the hives can be created, modified, or deleted by an account with administrative privileges. As shown in Figure 2-14, the tool regedit.exe is used to modify the registry. Be very careful when using this tool. Minor changes to the registry can have massive or even catastrophic effects.
Figure 2-14 Windows Registry Editor
Navigation in the registry is very similar to navigation in Windows File Explorer. Use the left panel to navigate the hives and the structure below it, and use the right panel to see the contents of the highlighted item in the left panel. With so many keys and subkeys, the key path can become very long. The path is displayed at the bottom of the window for reference. Because each key and subkey is essentially a container, the path is represented much like a folder in a file system. The backslash (\) is used to differentiate the hierarchy of the database.
Registry keys can contain either a subkey or a value. These are the different values that keys can contain:
- REG_BINARY: Numbers or Boolean values
- REG_DWORD: Numbers greater than 32 bits or raw data
- REG_SZ: String values
Because the registry holds almost all the operating system and user information, it is critical to make sure that it does not become compromised. Potentially malicious applications can add registry keys so that they start when the computer is started. During a normal boot, the user will not see the program start because the entry is in the registry and the application displays no windows or indication of starting when the computer boots. A keylogger, for example, would be devastating to the security of a computer if it were to start at boot without the user’s knowledge or consent. When performing normal security audits, or remediating an infected system, review the application startup locations within the registry to ensure that each item is known and safe to run.
The registry also contains the activity that a user performs during normal day-to-day computer use. This includes the history of hardware devices, including all devices that have been connected to the computer, identified by name, manufacturer, and serial number. Other information, such as what documents a user and program have opened, where they are located, and when they were accessed, is stored in the registry. This is all very useful information when a forensic investigation needs to be performed.
Activity 2.1.2.9: Identify the Windows Registry Hive
Refer to the online course to complete this Activity.
Lab 2.1.2.10: Exploring Processes, Threads, Handles, and Windows Registry
In this lab, you will explore the processes, threads, and handles using Process Explorer in Sysinternals Suite. You will also use the Windows registry to change a setting.
Windows Administration (2.2)
In this section, you will learn about Windows configuration, monitoring, and security.
Windows Configuration and Monitoring (2.2.1)
In this topic, you will learn about Windows configuration management, including running applications as the Administrator, configuring local users and domains, and working with the command line interface (CLI), PowerShell, and Windows Management Instrumentation (WMI). You will also learn how to monitor Windows using the net command, Task Manager, Resource Monitor, and networking tools.
Run as Administrator (2.2.1.1)
As a security best practice, it is not advisable to log on to Windows using the Administrator account or an account with administrative privileges. This is because any program that is executed while logged on with those privileges will inherit them. Malware that has administrative privileges has full access to all the files and folders on the computer.
Sometimes, it is necessary to run or install software that requires the privileges of the Administrator. To accomplish this, there are two different ways to install it:
Run as Administrator: Right-click the command in Windows File Explorer and choose Run as administrator from the Context Menu, shown in Figure 2-15.
Figure 2-15 Run as Administrator from Windows File Explorer
Administrator Command Prompt: Search for command, right-click the executable file, and choose Run as administrator from the Context Menu, shown in Figure 2-16. Every command that is executed from this command line will be carried out with administrative privileges, including installation of software.
Figure 2-16 Run as Administrator Using Administrator Command Prompt
Local Users and Domains (2.2.1.2)
When you start a new computer for the first time, or you install Windows, you will be prompted to create a user account. This is known as a local user. This account will contain all of your customization settings, access permissions, file locations, and many other user-specific data. There are also two other accounts that are present: Guest and Administrator. Both of these accounts are disabled by default.
As a security best practice, do not enable the Administrator account and do not give standard users administrative privileges. If a user needs to perform any function that requires administrative privileges, the system will ask for the Administrator password and allow only that task to be performed as an administrator. By entering the Administrator password, this protects the computer by preventing any software that is not authorized from installing, executing, or accessing files.
The Guest account should not be enabled. The Guest account does not have a password associated with it because it is created when a computer is going to be used by many different people who do not have accounts on the computer. Eachtime the Guest account logs on, a default environment is provided to them with limited privileges.
To make administration of users easier, Windows uses groups. A group will have a name and a specific set of permissions associated with it. When a user is placed into a group, the permissions of that group are given to that user. A user can be placed into multiple groups to be provided with many different permissions. When the permissions overlap, certain permissions, like “explicitly deny,” will override the permission provided by a different group. There are many different user groups built in to Windows that are used for specific tasks.
For example, the Performance Log Users group allows members to schedule logging of performance counters and collect logs either locally or remotely.
Local users and groups are managed with the lusrmgr.msc control panel applet, as shown in Figure 2-17.
Figure 2-17 lusrmgr.msc
In addition to groups, Windows can also use domains to set permissions. A domain is a type of network service where all of the users, groups, computers,peripherals, and security settings are stored on and controlled by a database. This database is stored on special computers or groups of computers called domain controllers (DCs). Each user and computer on the domain must authenticate against the DC to log on and access network resources. The security settings for each user and each computer are set by the DC for each session. Any setting supplied by the DC defaults to the local computer or user account setting.
CLI and PowerShell (2.2.1.3)
The Windows command line interface (CLI) can be used to run programs, navigate the file system, and manage files and folders. In addition, files called batch files can be created to execute multiple commands in succession, much like a basic script. To open the Windows CLI, search for cmd.exe and click the program. Remember that right-clicking the program provides the option to Run as Administrator, giving much more power to the commands that will be used.
The prompt displays the current location within the file system. These are a few things to remember when using the CLI:
- The filenames and paths are not case sensitive, by default.
- Storage devices are assigned a letter for reference. The letter, followed by a backslash (\), indicates the root of the device. Folder and file hierarchy on the device is indicated by separating them with the backslash. For example, C:\Users\Jim\Desktop\file.txt is the file called file.txt in the Desktop folder within the Jim folder within the Users folder on the device C:.
- Commands that have optional switches use the forward slash (/) to delineate between the command and each switch.
- You can use the Tab key to auto-complete commands when directories or files are referenced.
- Windows keeps a history of the commands that were entered during a CLI session. Access historical commands by using the Up Arrow and Down Arrow keys.
- To switch between storage devices, type the letter of the device, followed by a colon, and then press Enter.
Even though the CLI has many commands and features, it cannot work together with the core of Windows or the GUI. Another environment, called the Windows PowerShell, can be used to create scripts to automate tasks that the regular CLIis unable to create. PowerShell also provides a CLI for initiating commands.
PowerShell is an integrated program within Windows and can be opened by clicking Start, searching for PowerShell, and clicking the program. Like the CLI, PowerShell can also be run with administrative privileges.
These are the types of commands that PowerShell can execute:
- Cmdlets: These commands perform an action and return an output or object to the next command that will be executed.
- PowerShell scripts: These are files with a .ps1 extension that contain PowerShell commands that are executed.
- PowerShell functions: These are pieces of code that can be referenced in a script.
To see more information about Windows PowerShell and get started using it, type help in PowerShell, as shown in Example 2-2. You will be provided with much more information and resources to start using PowerShell.
Example 2-2 Windows PowerShell Help
PS C:\Windows\System32> help TOPIC Windows PowerShell Help System SHORT DESCRIPTION Displays help about Windows PowerShell cmdlets and concepts. LONG DESCRIPTION Windows PowerShell Help describes Windows PowerShell cmdlets, functions, scripts, and modules, and explains concepts, including the elements of the Windows PowerShell language. Windows PowerShell does not include help files, but you can read the help topics online, or use the Update-Help cmdlet to download help files to your computer and then use the Get-Help cmdlet to display the help topics at the command line.You can also use the Update-Help cmdlet to download updated help files as they are released so that your local help content is never obsolete. Without help files, Get-Help displays auto-generated help for cmdlets, functions, and scripts. ONLINE HELP You can find help for Windows PowerShell online in the TechNet Library beginning at http://go.microsoft.com/fwlink/?LinkID=108518. To open online help for any cmdlet or function, type: Get-Help <cmdlet-name> -Online UPDATE-HELP To download and install help files on your computer: 1. Start Windows PowerShell with the "Run as administrator" option. 2. Type: Update-Help After the help files are installed, you can use the Get-Help cmdlet to display the help topics. You can also use the Update-Help cmdlet to download updated help files so that your local help files are always up-to-date. For more information about the Update-Help cmdlet, type: Get-Help Update-Help -Online -- More --
There are four levels of help in Windows PowerShell:
- get-help PS command: Displays basic help for a command
- get-help PS command [-examples]: Displays basic help for a command with examples
- get-help PS command [-detailed]: Displays detailed help for a command with examples
- get-help PS command [-full]: Displays all help information for a command with examples in greater depth
Windows Management Instrumentation (2.2.1.4)
Windows Management Instrumentation (WMI) is used to manage remote
computers. It can retrieve information about computer components, display hardware and software statistics, and monitor the health of remote computers.
You can open WMI control by searching for and opening Computer Management, and then right-clicking the WMI Control entry under Services and Applications and choosing Properties. The WMI Control Properties window is shown in Figure 2-18.
Figure 2-18 WMI Control Panel Properties Window
These are the four tabs in the WMI Control Properties window:
- General: Summary information about the local computer and WMI
- Backup/Restore: Allows manual backup of statistics gathered by WMI
- Security: Settings to configure who has access to different WMI statistics
- Advanced: Settings to configure the default namespace for WMI
Some attacks today use WMI to connect to remote systems, modify the registry, and run commands. WMI helps them to avoid detection because it is common traffic, most often trusted by the network security devices, and the remote WMI commands do not usually leave evidence on the remote host. Because of this, WMI access should be strictly limited.
The net Command (2.2.1.5)
Windows has many commands that can be entered at the command line. One important command is the net command, used in the administration and maintenance of the OS. The net command supports many other commands that follow the net command and can be combined with switches to focus on specific output.
To see a list of the many net commands, type net help at the command prompt. Example 2-3 shows the commands that the net command can use. To see verbose help about any of the net commands, type net help command.
Example 2-3 Net Commands
C:\Users> net help The syntax of this command is: NET HELP command -or NET command /HELP Commands available are: NET ACCOUNTS NET HELPMSG NET STATISTICSNET COMPUTER NET LOCALGROUP NET STOP NET CONFIG NET PAUSE NET TIME NET CONTINUE NET SESSION NET USE NET FILE NET SHARE NET USER NET GROUP NET START NET VIEW NET HELP NET HELP NAMES explains different types of names in NET HELP syntax lines. NET HELP SERVICES lists some of the services you can start. NET HELP SYNTAX explains how to read NET HELP syntax lines. NET HELP command | MORE displays Help one screen at a time. C:\Users>
These are some common net commands:
- net accounts: Sets password and logon requirements for users
- net session: Lists or disconnects sessions between a computer and other computers on the network
- net share: Creates, removes, or manages shared resources
- net start: Starts a network service or lists running network services
- net stop: Stops a network service
- net use: Connects, disconnects, and displays information about shared network resources
- net view: Shows a list of computers and network devices on the network
Task Manager and Resource Monitor (2.2.1.6)
There are two very important and useful tools to help an administrator to understand the many different applications, services, and processes that are running on a Windows computer. These tools also provide insight into the performance of the computer, such as CPU, memory, and network usage. These tools are especially useful when investigating a problem where malware is suspected. When a component is not performing the way that it should be, thesetools can be used to determine what the problem might be.
Task Manager
Task Manager, shown in Figure 2-19, provides a lot of information about what is running, and general performance of the computer.
Figure 2-19 Windows 10 Task Manager
There are seven tabs in Task Manager:
- Processes: All of the programs and processes that are currently running are shown here. The CPU, memory, disk, and network utilization of each process is displayed in columns. You can examine the properties of any of these processes, or end a process that is not behaving properly or has stalled.
- Performance: A view of all the performance statistics provides a useful overview of the CPU, memory, disk, and network performance. Clicking each item in the left pane will show detailed statistics of that item in the right pane.
- App history: The use of resources by applications over time provides insight into applications that are consuming more resources than they should be. Click Options and Show history for all processes to see the history of every process that has run since the computer was started.
- Startup: All of the applications and services that start when the computer is booted are shown in this tab. To disable a program from starting at startup, right-click the item and choose Disable.
- Users: All of the users that are logged on to the computer are shown in this tab. Also shown are all the resources that each user’s applications and processes are using. From this tab, an administrator can disconnect a user from the computer.
- Details: Similar to the Processes tab, this tab provides additional management options for processes such as setting a priority to make the processor devote more or less time to a process. CPU affinity can also be set, which determines which core or CPU a program will use. Also, a useful feature called Analyze Wait Chain shows any process for which another process is waiting. This feature helps to determine if a process is simply waiting, or is stalled.
- Services: All the services that are loaded are shown in this tab. The process ID (PID) and a short description are also shown along with the status of either Running or Stopped. At the bottom, there is a button to open the Services console, which provides additional management of services.
Resource Monitor
When more detailed information about resource usage is needed, you can use Resource Monitor, shown in Figure 2-20. When searching for the reason a computer may be acting erratically, Resource Monitor can help to find the source of the problem.
Figure 2-20 Windows 10 Resource Monitor
Resource Monitor has five tabs:
- Overview: General usage for each resource is shown in this tab. If you select a single process, it will be filtered across all of the tabs to show only that process’s statistics.
- CPU: The PID, number of threads, which CPU the process is using, and the average CPU usage of each process are shown in this tab. Additional information about any services that the process relies on, and the associated handles and modules, can be seen by expanding the lower rows.
- Memory: All of the statistical information about how each process uses memory is shown in this tab. Also, an overview of usage of all the RAM is shown below the Processes row.
- Disk: All of the processes that are using a disk are shown in this tab, with read/write statistics and an overview of each storage device.
- Network: All of the processes that are using the network are shown in this tab, with read/write statistics. Most importantly, the current TCP connections are shown, along with all of the ports that are listening. Thistab is very useful when trying to determine which applications and processes are communicating over the network. It makes it possible to tell if an unauthorized process is accessing the network, listening for a communication, and the address with which it is communicating.
Networking (2.2.1.7)
One of the most important features of any operating system is the ability for the computer to connect to a network. Without this feature, there is no access to network resources or the Internet. To configure Windows networking properties and test networking settings, the Network and Sharing Center, shown in Figure 2-21, is used. The easiest way to run this tool is to search for Network and Sharing Center and click it in the search results.
Figure 2-21 Windows 10 Network and Sharing Center
The initial view shows an overview of the active network. This view shows whether there is Internet access and if the network is private, public, or guest.
The type of network, either wired or wireless, is also shown. From this window, you can see the HomeGroup the computer belongs to, or create one if it is not already part of a HomeGroup. This tool can also be used to change adaptersettings, change advanced sharing settings, set up a new connection, or troubleshoot problems.
To configure a network adapter, choose Change adapter settings to show all of the network connections that are available. Right-click the adapter you wish to configure and choose Properties, as shown in Figure 2-22.
Figure 2-22 Windows 10 Network Connections
This connection uses the following items: box, highlight Internet Protocol Version 4 (TCP/IPv4) or Internet Protocol Version 6 (TCP/IPv6) depending on which version you wish to use (see Figure 2-23). Click Properties to configure the adapter.
Figure 2-23 Windows 10 IPv4 Properties
In the Properties dialog box, shown in Figure 2-24, you can choose to Obtain an address automatically if there is a DHCP server available on the network. If you wish to configure addressing manually, you can fill in the address, subnet, default gateway, and DNS servers to configure the adapter. Click OK to accept the changes.
Figure 2-24 Windows 10 Ethernet Properties
You can also use the netsh.exe tool to configure networking parameters from a command prompt. This program can display and modify the network configuration. Type netsh /? at the command prompt to see a list of all the switches that can be used with this command.
After the network configuration is complete, there are some basic commands that can be used to test connectivity to the local network, and the Internet. The most basic test is performed with the ping command. To test the adapter itself, type ping 127.0.0.1 at the command prompt, as shown in Example 2-4. This will make sure that the adapter is able to send and receive data. It also confirms that the TCP/IP protocol suite is properly installed in the computer. The 127.0.0.1 address is known as the loopback address.
Example 2-4 Pinging the Loopback Address
C:\Users> ping 127.0.0.1 Pinging 127.0.0.1 with 32 bytes of data:Reply from 127.0.0.1: bytes=32 time<1ms TTL=128 Reply from 127.0.0.1: bytes=32 time<1ms TTL=128 Reply from 127.0.0.1: bytes=32 time<1ms TTL=128 Reply from 127.0.0.1: bytes=32 time<1ms TTL=128 Ping statistics for 127.0.0.1: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0ms, Maximum = 0ms, Average = 0ms C:\Users>
Next, ping any host on the network. If you do not know any IP addresses of other hosts on the network, you can ping the default gateway. To find the address of the default gateway, type ipconfig at the command prompt, as shown in Example 2-5.
Example 2-5 The ipconfig Command
C:\Users> ipconfig Windows IP Configuration Ethernet adapter Ethernet: Connection-specific DNS Suffix . : Link-local IPv6 Address . . . . . : fe80::1074:d6c8:f89d:43ad%17 IPv4 Address. . . . . . . . . . . : 10.10.10.4 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 10.10.10.1 Ethernet adapter VirtualBox Host-Only Network: Connection-specific DNS Suffix . : Link-local IPv6 Address . . . . . : fe80::1c12:a86f:b858:77ac%11 IPv4 Address. . . . . . . . . . . : 192.168.56.1 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : Tunnel adapter Local Area Connection* 14: Connection-specific DNS Suffix . . : IPv6 Address. . . . . . . . . . . : 2001:0:4137:9e76:c5c:17ab:bd3b:e62c Link-local IPv6 Address . . . . . : fe80::c5c:17ab:bd3b:e62c%4 Default Gateway . . . . . . . . . : :: C:\Users>
This command will return basic network information including the IP address of the host, the subnet mask, and the default gateway. You can also ping hosts on other connected networks to make sure that you have connectivity to those networks. The ipconfig command has many switches that are helpful when troubleshooting network issues. Type ipconfig /? to see a list of all the switches that can be used with this command.
When the ping command is issued, it will send four ICMP echo request messages to the indicated IP address. If there is no reply, there may be a problem with the network configuration. It is also possible that the intended host blocks ICMP echo requests. In this case, try to ping a different host on the network.
Most often, there are four replies to the requests, showing the size of each request, the time it took to travel, and the time to live (TTL). TTL is the number of hops a packet takes along the path to its destination.
Domain Name System (DNS) should also be tested because it is used very often to find the address of hosts by translating it from a name. Use the nslookup command to test DNS. Type nslookup cisco.com at the command prompt to find the address of the Cisco web server. When the address is returned, you know that DNS is functioning correctly. You can also check to see what ports are open, where they are connected, and what their current status is. Type netstat at the command line to see details of active network connections, as shown in Example 2-6. The netstat command will be examined further later in this chapter.
Example 2-6 The netstat Command
C:\Users> netstat Active ConnectionsProto Local Address Foreign Address State TCP 10.10.10.4:50008 bn3sch020022361:https ESTABLISHED TCP 10.10.10.4:56145 a23-204-181-116:https ESTABLISHED TCP 10.10.10.4:56630 a23-0-224-158:https ESTABLISHED TCP 10.10.10.4:57101 162.125.8.4:https CLOSE_WAIT TCP 10.10.10.4:57102 162.125.8.4:https CLOSE_WAIT C:\Users>
Accessing Network Resources (2.2.1.8)
Like other operating systems, Windows uses networking for many different applications such as web, email, and file services. Originally developed by IBM, Microsoft aided in the development of the Server Message Block (SMB) protocol to share network resources. SMB is mostly used for accessing files on remote hosts. The Universal Naming Convention (UNC) format is used to connect to resources, for example:
\\servername\sharename\file
In the UNC, servername is the server that is hosting the resource. This can be a DNS name, a NetBIOS name, or simply an IP address. The sharename is the root of the folder in the file system on the remote host, while the file is the resource that the local host is trying to find. The file may be deeper within the file system and this hierarchy will need to be indicated.
When sharing resources on the network, the area of the file system that will be shared will need to be identified. Access control can be applied to the folders and files to restrict users and groups to specific functions such as read, write, or deny. There are also special shares that are automatically created by Windows. These shares are called administrative shares. An administrative share is identified by the dollar sign ($) that comes after the share name. Each disk volume has an administrative share, represented by the volume letter and the $ such as C$, D$, or E$. The Windows installation folder is shared as admin$, the printers folder is shared as print$, and there are other administrative shares that can be connected. Only users with administrative privileges can access these shares.
The easiest way to connect to a share is to type the UNC of the share intoWindows File Explorer, in the box at the top of the screen which shows the breadcrumb listing of the current file system location. When Windows tries to connect to the share, you will be asked to provide credentials for accessing the resource. Remember that because the resource is on a remote computer, the credentials need to be for the remote computer, not the local computer.
Besides accessing shares on remote hosts, you can also log in to a remote host and manipulate that computer as if it were local, to make configuration changes, install software, or troubleshoot an issue with the computer. In Windows, this function is known as the Remote Desktop Protocol (RDP). When investigating security incidents, a security analyst uses RDP often to access remote computers.
To start RDP and connect to a remote computer, search for Remote Desktop and click the application. The Remote Desktop Connection window is shown in Figure 2-25.
Figure 2-25 Windows Remote Desktop Connection
Windows Server (2.2.1.9)
Most Windows installations are performed as desktop installation on desktopsand laptops. There is another edition of Windows that is mainly used in data centers called Windows Server. This is a family of Microsoft products that began with Windows Server 2003. Today, the latest release is Windows Server 2016. Windows Server hosts many different services and can fulfill different roles within a company.
Note
Although there is a Windows Server 2000, it is considered a client version of Windows NT 5.0. Windows Server 2003 is a server based on NT 5.2 and begins a new family of Windows Server versions.
These are some of the services that Windows Server hosts:
- Network Services: DNS, DHCP, Terminal services, Network Controller, and Hyper-V Network virtualization
- File Services: SMB, NFS, and DFS
- Web Services: FTP, HTTP, and HTTPS
- Management: Group policy and Active Directory domain services control
Lab 2.2.1.10: Create User Accounts
In this lab, you will create and modify user accounts in Windows.
Lab 2.2.1.11: Using Windows PowerShell
The objective of this lab is to explore some of the functions of PowerShell.
Lab 2.2.1.12: Windows Task Manager
In this lab, you will explore Task Manager and manage processes from within Task Manager.
Lab 2.2.1.13: Monitor and Manage System Resources in Windows
In this lab, you will use administrative tools to monitor and manage system resources.
Windows Security (2.2.2)
In this topic, you will learn about Windows security tools, including netstat, Event Viewer, Windows Update, Local Security Policy, Windows Defender, and Windows Firewall.
The netstat Command (2.2.2.1)
When malware is present in a computer, it will often open communication ports on the host to send and receive data. The netstat command can be used to look for inbound or outbound connections that are not authorized. When used on its own, the netstat command will display all of the active TCP connections that are available.
By examining these connections, it is possible to determine which of the programs are listening for connections that are not authorized. When a program is suspected of being malware, a little research can be performed to determine its legitimacy. From there, the process can be shut down with Task Manager, and malware removal software can be used to clean the computer.
To make this process easier, you can link the connections to the running processes in Task Manager. To do this, open a command prompt with administrative privileges and use the command netstat -abno, as shown in Example 2-7.
Example 2-7 The netstat -abno Command
C:\WINDOWS\system32> netstat -abno Active Connections Proto Local Address Foreign Address State PID TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 1128 RpcSs [svchost.exe] TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4 Can not obtain ownership information TCP 0.0.0.0:2869 0.0.0.0:0 LISTENING 4 Can not obtain ownership information TCP 0.0.0.0:5357 0.0.0.0:0 LISTENING 4 Can not obtain ownership information TCP 0.0.0.0:6646 0.0.0.0:0 LISTENING 5992 [MMSSHOST.EXE] TCP 0.0.0.0:8019 0.0.0.0:0 LISTENING 4828 [QBCFMonitorService.exe] TCP 0.0.0.0:18800 0.0.0.0:0 LISTENING 20020 [Amazon Music Helper.exe] TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 924 Can not obtain ownership information TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 1520 EventLog [svchost.exe] TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 2484 Schedule [svchost.exe] TCP 0.0.0.0:49689 0.0.0.0:0 LISTENING 364 [lsass.exe] TCP 0.0.0.0:49735 0.0.0.0:0 LISTENING 4772 [spoolsv.exe] TCP 0.0.0.0:49828 0.0.0.0:0 LISTENING 1012 Can not obtain ownership information TCP 10.10.10.4:139 0.0.0.0:0 LISTENING 4 Can not obtain ownership information <output omitted> C:\WINDOWS\system32>
By examining the active TCP connections, an analyst should be able to determine if there are any suspicious programs that are listening for incoming connections on the host. You can also trace that process to Task Manager and cancel the process. There may be more than one process listed with the same name. If this is the case, use the PID to find the correct process. Each process running on the computer has a unique PID. To display the PIDs for the processes in Task Manager, open Task Manager, right-click the table heading, and select PID.
Event Viewer (2.2.2.2)
Windows Event Viewer, shown in Figure 2-26, logs the history of application, security, and system events. These log files are a valuable troubleshooting tool because they provide information necessary to identify a problem. To open Event Viewer, search for it and click the program icon.
Figure 2-26 Windows Event Viewer
Windows includes two categories of event logs: Windows Logs, and Application and Services Logs. Each of these categories has multiple log types. Events that are displayed in these logs have a level: information, warning, error, or critical. They also have the date and time that the event occurred, along with the source of the event and an ID which relates to that type of event.
It is also possible to create a custom view. This is useful when looking for certain types of events, finding events that happened during a certain time period, displaying events of a certain level, and many other criteria. There is a built-in custom view called Administrative Events that shows all critical, error, and warning events from all of the administrative logs. This is a good view to start with when trying to troubleshoot a problem.
Windows Update Management (2.2.2.3)
No software is perfect, and the Windows operating system is no exception.
Attackers are constantly coming up with new ways to compromise computers and exploit bad code. Some of these attacks come so quickly that there is no defense against them. These are called zero-day exploits. Microsoft and security software developers are always trying to stay ahead of the attackers, but they are not always successful. To ensure the highest level of protection against these attacks, always make sure Windows is up to date with the latest service packs and security patches.
Patches are code updates that manufacturers provide to prevent a newly discovered virus or worm from making a successful attack. From time to time, manufacturers combine patches and upgrades into a comprehensive update application called a service pack. Many devastating virus attacks could have been much less severe if more users had downloaded and installed the latest service pack.
Windows routinely checks the Windows Update website for high-priority updates that can help protect a computer from the latest security threats. These updates include security updates, critical updates, and service packs. Depending on the setting you choose, Windows automatically downloads and installs any high-priority updates that your computer needs or notifies you as these updates become available. To configure the settings for Windows Update, search for Windows Update and click the application.
The Update status, shown in Figure 2-27, allows you to check for updates manually and see the update history of the computer. There are also settings for indicating the hours during which the computer will not automatically restart, for example during regular business hours. You can also choose when to restart the computer after an update, if necessary, with the Restart options. Advanced options are also available to choose how updates are installed and get updates for other Microsoft products.
Figure 2-27 Windows Update Status
Local Security Policy (2.2.2.4)
A security policy is a set of objectives that ensures the security of a network, the data, and the computer systems in an organization. The security policy is a constantly evolving document based on changes in technology, business, and employee requirements.
In most networks that use Windows computers, Active Directory is configured with domains on a Windows Server. Windows computers join the domain. The administrator configures a Domain Security Policy that applies to all computers that join the domain. Account policies are automatically set when a user logs in to a computer that is a member of a domain. Windows Local Security Policy, shown in Figure 2-28, can be used for stand-alone computers that are not part of an Active Directory domain. To open the Local Security Policy applet, search for Local Security Policy and click the program.
Figure 2-28 Windows Local Security Policy
Password guidelines are an important component of a security policy. Any user that must log on to a computer or connect to a network resource should be required to have a password. Passwords help prevent theft of data and malicious acts. Passwords also help to confirm that the logging of events is valid by ensuring that the user is the person they say that they are. Password Policy is found under Account Policies, and defines the criteria for the passwords for all of the users on the local computer.
Use the Account Lockout Policy in Account Policies to prevent brute-force login attempts. You can set the policy to allow the user to enter a wrong username and/or password five times. After five attempts, the account is locked out for 30 minutes. After 30 minutes, the number of attempts is reset to zero and the user can attempt to log in again.
It is important to make sure that computers are secure when users are away. A security policy should contain a rule about requiring a computer to lock when the screen saver starts. This will ensure that after a short time away from the computer, the screen saver will start and then the computer cannot be used until the user logs in.
If the Local Security Policy on every stand-alone computer is the same, then usethe Export Policy feature. Save the policy with a name, such as workstation.inf. Copy the policy file to an external media or network drive to use on other stand-alone computers. This is particularly helpful if the administrator needs to configure extensive local policies for user rights and security options.
The Local Security Policy applet contains many other security settings that apply specifically to the local computer. You can configure user rights, firewall rules, and even the ability to restrict the files that users or groups are allowed to run with AppLocker.
Windows Defender (2.2.2.5)
Malware includes viruses, worms, Trojan horses, keyloggers, spyware, and adware. These are designed to invade privacy, steal information, damage the computer, or corrupt data. It is important that you protect computers and mobile devices using reputable antimalware software. The following types of antimalware programs are available:
- Antivirus protection: This program continuously monitors for viruses. When a virus is detected, the user is warned, and the program attempts to quarantine or delete the virus.
- Adware protection: This program continuously looks for programs that display advertising on your computer.
- Phishing protection: This program blocks the IP addresses of known phishing websites and warns the user about suspicious sites.
- Spyware protection: This program scans for keyloggers and other spyware.
- Trusted/untrusted sources: This program warns you about unsafe programs about to be installed or unsafe websites before they are visited.
It may take several different programs and multiple scans to completely remove all malicious software. Run only one malware protection program at a time.
Several reputable security organizations, such as McAfee, Symantec, and Kaspersky, offer all-inclusive malware protection for computers and mobile devices. Windows has built-in virus and spyware protection called Windows Defender, shown in Figure 2-29. Windows Defender is turned on by default, providing real-time protection against infection.
Figure 2-29 Windows Defender
To open Windows Defender, search for it and click the program. Although Windows Defender works in the background, you can perform manual scans of the computer and storage devices. You can also manually update the virus and spyware definitions in the Update tab. Also, to see all of the items that were found during previous scans, click the History tab.
Windows Firewall (2.2.2.6)
A firewall selectively denies traffic to a computer or network segment. Firewalls generally work by opening and closing the ports used by various applications.
By opening only the required ports on a firewall, you are implementing a restrictive security policy. Any packet not explicitly permitted is denied. In contrast, a permissive security policy permits access through all ports, except those explicitly denied. In the past, software and hardware were shipped with permissive settings. As users neglected to configure their equipment, the default permissive settings left many devices exposed to attackers. Most devices now ship with settings as restrictive as possible, while still allowing easy setup.
To allow program access through Windows Firewall, search for Windows Firewall, click its name to run it, and click Allow an app or feature through Windows Firewall, as shown in Figure 2-30.
Figure 2-30 Windows Firewall
If you wish to use a different software firewall, you will need to disable Windows Firewall. To disable Windows Firewall, click Turn Windows Firewall on or off.
Many additional settings can be found under Advanced settings, as shown in Figure 2-31. Here you can create inbound or outbound traffic rules based on different criteria. You can also import and export policies or monitor different aspects of the firewall.
Figure 2-31 Windows Firewall Advanced Settings
Activity 2.2.2.7: Identify the Windows Command
Refer to the online course to complete this Activity.
Activity 2.2.2.8: Identify the Windows Tool
Refer to the online course to complete this Activity.
Summary (2.3)
In this chapter, you learned about the history and architecture of the Windows operating system. There have been over 40 versions of Windows desktop, Windows server, and Windows mobile operating systems.
HAL handles all the communication between the hardware and the kernel. The CPU can operate in two separate modes: kernel mode and user mode. Applications that are installed are run in user mode, and operating system coderuns in kernel mode.
NTFS formats the disk into four important data structures:
- Partition Boot Sector
- Master File Table (MFT)
- System Files
- File Area
Applications are generally made up of many processes. A process is any program that is currently executing. Each running process is made up of at least one thread. A thread is a part of the process that can be executed. Some of the processes that Windows runs are services. These are programs that run in the background to support the operating system and applications.
Each process in a 32-bit Windows computer supports a virtual address space that enables addressing up to 4 GB. Each process in a 64-bit Windows computer supports a virtual address space of up to 8 TB.
Windows stores all of the information about hardware, applications, users, and system settings in a large database known as the registry. The registry is a hierarchical database where the highest level is known as a hive. These are the five hives of the Windows registry:
- HKEY_CURRENT_USER (HKCU)
- HKEY_USERS (HKU)
- HKEY_CLASSES_ROOT (HKCR)
- HKEY_LOCAL_MACHINE (HKLM)
- HKEY_CURRENT_CONFIG (HKCC)
In this chapter, you also learned how to configure, monitor, and keep Windows secure. To do this normally requires that you run programs as Administrator. As Administrator, you can create users and groups, disable access to the Administrator and Guest accounts, and use a variety of administrator tools, including
- All commands available via the CLI and PowerShell
- Remote computer management using WMI and Remote Desktop
- Task Manager and Resource Monitor
- Networking configuration
As Administrator, you will also have the ability to use all the Windows security tools, including
- The netstat command to look for inbound and outbound connections that are not authorized
- Event Viewer for access to logs that document the history of application, security, and system events
- Windows Update configuration and scheduling
- Windows Local Security Policy to secure stand-alone computers that are not part of an Active Directory domain
- Windows Defender configuration for built-in virus and spyware protection
- Windows Firewall configuration to fine-tune the default settings
As a cybersecurity analyst, you need a basic understanding of how Windows operates and what tools are available to help keep Windows endpoints secure.
Practice
The following activities provide practice with the topics introduced in this chapter. The Labs and Class Activities are available in the companion CCNA Cybersecurity Operations Lab Manual (ISBN 9781587134388).
Class Activities
Class Activity 2.0.1.2: Identify Running Processes
Labs
Lab 2.1.2.10: Exploring Processes, Threads, Handles, and Windows Registry
Lab 2.2.1.10: Create User Accounts
Lab 2.2.1.11: Using Windows PowerShell
Lab 2.2.1.12: Windows Task Manager
Lab 2.2.1.13: Monitor and Manage System Resources in Windows
Updated May 30, 2023
Introduction to Windows
Windows is an operating system that manages a personal computer, known as a series of programs. It is a Microsoft-developed graphical operating system. This offers a way of data, running apps, playing video games, streaming videos, and internet access. Microsoft was first created in November 1985 and has frequently been modified as computer memory expanded, as chips got faster processing, and, of course, when the internet was invented. PCs used a set of text commands before Windows. After that, more than a dozen versions were released, including the latest Windows 10 edition.
Applications of Windows
Windows has already developed a range of valuable applications. Such applications will help you with many popular activities, including Web surfing, calendar management, and music shopping.
You can open most of these applications with a click on the Start button and then click on the user’s icon. You might need to navigate to the Start screen to find the app you’re searching for.
1. Web Browsers
Internet Explorer is one of the best-known Internet applications, mainly because many Windows models have bundled it in the last 20 years. The GUI and most common web browser features include your favorite bookmarking pages. Microsoft Edge substitutes Windows 10 for Internet Explorer but serves the same function. It has some additional features via Internet Explorer, including the option of easy-to-read and integrated Web pages with other Windows 10 components.
2. Productivity
Multiple productivity features, such as handling e-mails and schedules, following directions, and organizing notes, are included in Windows 8 and 10. Mail and Calendar are software that links your accounts, for example, to Microsoft, Google, and Apple. Within these services, you synchronize your mailboxes and calendars and display them on your computer in a single window.
Maps is a Bing Maps app that allows you to use all the same navigation and search apps. It also introduces a few additional functionalities, such as pinning and saving instructions on all Windows tools. One Note, which initially came with Microsoft Office, is the advanced notice management program, but now it’s a default Windows 10 feature. OneNote helps you create a notes list that you can search and share.
3. Settings
You can change the settings and configurations of your computer in the Control Panel. The Windows 8 Settings app provides you with access, for the most part, to your device settings, but instead of the traditional Windows, the modern tablet model.
Advantages and Disadvantages
Given below are the advantages and disadvantages mentioned:
Advantages:
- Ease to Use: The more modern ones are possibly simple for users familiar with previous versions. Perhaps that is due to the uniform look and feel of virtually perhaps the systems and the way the file system has been implemented since the days of MS Windows.
- Available Software: It is equipped with an extensive range of applications. This is because of and why Microsoft is a world leader in Desktop operating systems and bureau applications. When searching for your business program, a Windows version will likely be available somewhere if the product exists.
- Backward Compatibility: If you currently use the older edition and need more up-to-date details but don’t want to compromise the use of any older Window-only programs that are important to your business needs, such programs may operate with a newer version.
- Plug & Play: It is also a plug & plays support specialist for PC hardware as an operating system for the average home user. As long as you install the right drivers, it typically does an outstanding job recognizing new hardware. Many operating systems have Plug & Play features but require manual control to a lesser degree and more frequently.
- Games: You need Windows if you want the latest innovations in PC Gaming. It provides plenty of gaming games and other supporting gaming hardware. There are also some of the most common games for Linux and some for the Mac, but no comparison, really. Nevertheless, all the outdated games written for Windows 95 and 98 aren’t going to work with XP, as well.
Disadvantages:
- High Resource Requirements: By comparison, Microsoft wants its consumers to spend the most on their computer hardware, as compared to the manufacturers of other systems: faster processor (CPU), more internal memory, and a larger disk. Microsoft has also maintained that this is because of all the extra features its customers require.
- Closed Source: Fixing issues would be much simpler for users and support workers if they understood exactly what was happening. Unfortunately, only Microsoft has direct access to the source code of its software, and since no log file is created, its users can attempt to infer what causes their problems by trial and error.
Recommended Articles
This is a guide to What is Windows? Here we discuss the introduction, applications of windows, along with advantages and disadvantages. You may also have a look at the following articles to learn more –
- Windows Powershell Commands
- Windows Networking Commands
- Adobe Illustrator for Windows 8
- Install Python on Windows
MS Windows MCQs GK
1. An operating system version designed for use with a media center PC is Microsoft Window XP
Answer: Media center edition
2. Which one is the default ‘word Processor’ for Microsoft Windows?
A. MS Word
B. MS Paint
C. Word Pad
D. Notepad
Answer: C
3.Which mode loads minimal set of drivers when starting Windows?
Answer: Safe Mode
4. Which operating system doesn’t support networking between computers?
A. Windows 3.1
B. Windows 95
C. Windows 2000
D. Windows NT
Answer: A
5. Which key combination is used to minimize all open windows and displays in the screen?
Answer: Windows key + D
6. How many users can access a share folder simultaneously from a Windows XP machine?
A. 8
B. 9
C. 10
D. Unlimited
Answer: C
7. Which of the following windows do not have start button
A. Windows Vista
B. Windows 7
C. Windows 8
D. Windows 95
Answer: C
8. Which of the following Operating systems is better for implementing a Client Server network
A. MS DOS
B. Windows 95
C. Windows 98
D. Windows 2000
Answer: D
9. Which one is the latest release of Windows Client Operating system?
A. Windows XP
B. Windows 7
C. Windows 8
D. Windows 10
Answer: D
10. Which function key needs to be press during reboot to enter in Safe Mode of a Windows machine?
Answer: F8
11.To make a window wider, you would move the pointer until it changes to the Horizontal Resize shape and then _____.
Answer: Drag
12. Which one is used for making presentation file from Microsoft Office package?
Answer: MS PowerPoint
13.The window which shows icons for things like the mouse, sound, and display is_____.
Answer: Control Panel
14. To see Help for Windows itself you could_____
Answer: Open the start menu or screen and search for Help or Press F1 key
15. Which is used for making presentation file from Microsoft Office package?
Answer: MS PowerPoint
16.My computer was introduced from____
Answer: Windows 95
17. Which of these folders in Windows is used by browsers to cache web pages
Answer: Temporary Internet Files
18. What is the name of Virtual Assistant included in MS Windows 10
Answer: Cortana
19. What would you type in Run window to open ‘MS Word’
Answer: Winword.exe
20. Shortcut key to permanent delete the file without sending it to the recycle bin.
Answer: Shift + Del
21. What will be the shortcut key in windows to perform cut operation?
Answer: Ctrl + X
22. Zip files are
Answer: Compressed files
23. Which of the following is the files directly used by operating system?
Answer: .ini
24. In Windows operating system it is a very important part of Windows, clicking on it opens up what is called the start menu
Answer: Start Button
25. In Windows operating system the _____ is the main screen area that one sees after he turn on a computer and log on to Windows.
Answer: Desktop
26. Word Processors that is the part of Windows operating system
A. Adobe Photoshop
B. Word pad
Answer: B
27. In Windows operating system these are small pictures that represent files, folders, programs, and other items. Each one is used to make the computer do something.
Answer: Icons
28. Microsoft Windows provides a graphics application named
Answer: Paint
29. It is a visual aspect that indicates that a control is ready to receive input from you in Windows operating system
Answer: Text Boxes
30. In Windows operating system it is the long horizontal bar at the bottom of a screen. Unlike the desktop, which can get obscured by the windows on top of it, it is visible almost all time.
Answer: Taskbar
31. In Windows operating system it sits at the bottom of windows desktop screen. It shows you which programs are running and allows you to switch between them. It also contains the Start button which one can use to access programs, folders, and computer settings.
Answer: Taskbar
32. In Windows operating system it is a window that is used to display text or to receive text from you. The type of text it displays or the type of text you are asked to provide depends on the application or the situation.
Answer: Text boxes
33. In Windows operating system the clock in Windows xp sits on the_____ and displays the system time.
Answer: Taskbar
34. Text Editor that is the part of Windows operating system
Answer: Notepad
35. In Windows operating system when you delete a file or folder, it doesn’t actually get deleted right away, it goes to the _____.
Answer: Recycle bin
36. How can you find the amount of memory installed on your computer?
Answer: Right click on “My Computer”/Properties
37. How can you tell which printers are installed on a computer?
Answer: Open “My computer”/Printers
38. Which windows program allow you to quickly locate a file or folder?
Answer: Find under the start button and /or Windows Explorer
39. Where can you find the most recent files you worked on in Windows?
A. Under start/Document
B. Under Open Word Document
C. Start/Find/Files or folders
D. There is no way to find them by themselves
Answer: A
40. Which key starts the spell checker in all Windows applications?
Answer: F7



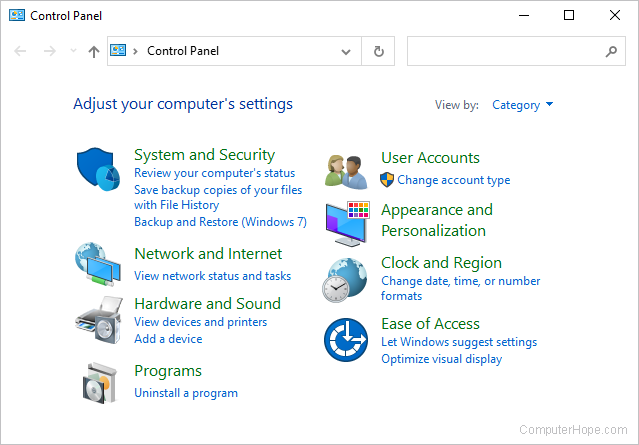
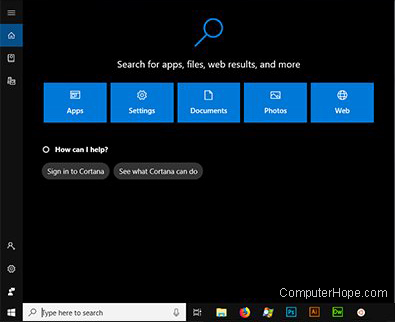





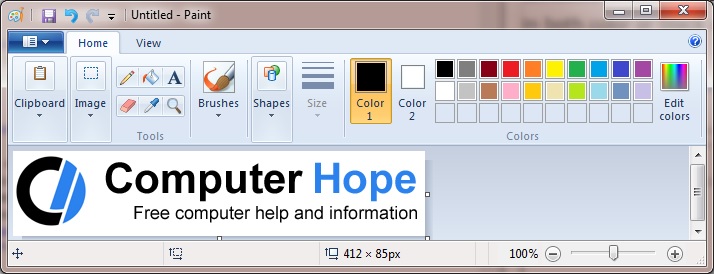




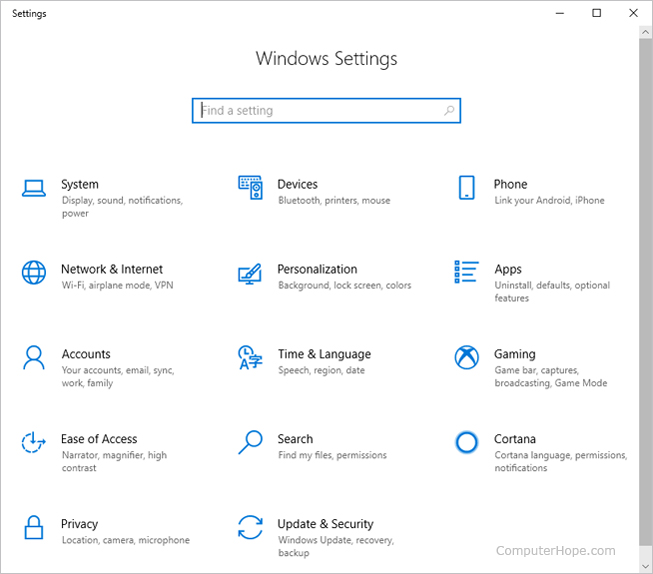

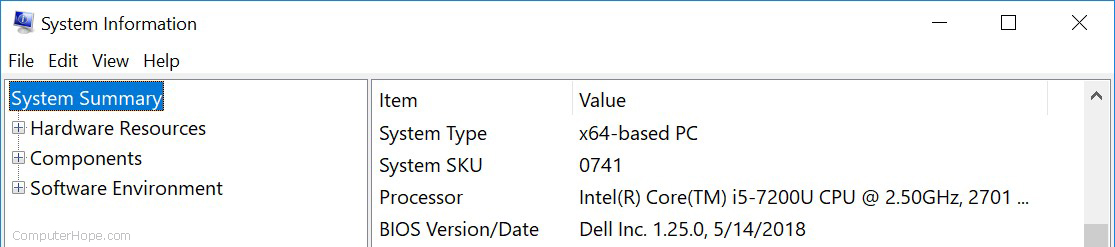

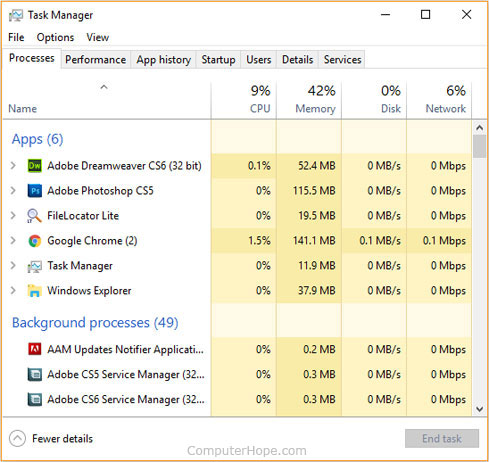









![CompTIA A+ Full Course - FREE - [31+ Hours]](https://i.ytimg.com/vi/1CZXXNKAY5o/0.jpg)