This list includes some of the FQDNs and IP Addresses used by Microsoft Services, this may be useful for identifying outgoing traffic and creating web filtering exceptions.
| *.aadrm.com |
| *.acompli.net |
| *.adl.windows.com |
| *.appex.bing.com |
| *.appex-rf.msn.com |
| *.aria.microsoft.com |
| *.azure-apim.net |
| *.azureedge.net |
| *.azurerms.com |
| *.blob.core.windows.net |
| *.broadcast.skype.com |
| *.cdn.office.net |
| *.cloudapp.net |
| *.compliance.microsoft.com |
| *.config.office.net |
| *.events.data.microsoft.com |
| *.flow.microsoft.com |
| *.helpshift.com |
| *.hip.live.com |
| *.hockeyapp.net |
| *.informationprotection.azure.com |
| *.itunes.apple.com |
| *.keydelivery.mediaservices.windows.net |
| *.localytics.com |
| *.lync.com |
| *.manage.microsoft.com |
| *.manage.office.com |
| *.media.azure.net |
| *.microsoft.com |
| *.microsoftonline.com |
| *.microsoftonline-p.com |
| *.microsoftstream.com |
| *.microsoftusercontent.com |
| *.msauth.net |
| *.msauthimages.net |
| *.msecnd.net |
| *.msedge.net |
| *.msftauth.net |
| *.msftauthimages.net |
| *.msftidentity.com |
| *.msidentity.com |
| *.msocdn.com |
| *.mstea.ms |
| *.o365weve.com |
| *.office.com |
| *.office.net |
| *.office365.com |
| *.officeapps.live.com |
| *.onenote.com |
| *.online.office.com |
| *.onmicrosoft.com |
| *.outlook.com |
| *.outlookmobile.com |
| *.portal.cloudappsecurity.com |
| *.powerapps.com |
| *.protection.office.com |
| *.protection.outlook.com |
| *.secure.skypeassets.com |
| *.security.microsoft.com |
| *.sfbassets.com |
| *.sharepointonline.com |
| *.skype.com |
| *.skypeforbusiness.com |
| *.staffhub.office.com |
| *.streaming.mediaservices.windows.net |
| *.teams.microsoft.com |
| *.tenor.com |
| *.urlp.sfbassets.com |
| *.users.storage.live.com |
| *.virtualearth.net |
| 104.208.16.88 |
| 104.208.16.89 |
| 104.208.16.90 |
| 104.208.16.94 |
| 104.46.162.224 |
| 104.46.162.226 |
| 104.47.0.0/17 |
| 104.82.250.212 |
| 104.86.110.136 |
| 104.86.110.153 |
| 104.86.110.155 |
| 104.86.110.170 |
| 104.86.110.171 |
| 104.86.110.186 |
| 104.86.110.233 |
| 104.86.110.250 |
| 104.86.111.10 |
| 104.86.111.147 |
| 104.86.111.48 |
| 13.107.128.0/22 |
| 13.107.136.9 |
| 13.107.140.6/32 |
| 13.107.18.10/31 |
| 13.107.18.15/32 |
| 13.107.22.200 |
| 13.107.22.239 |
| 13.107.5.80 |
| 13.107.6.152/31 |
| 13.107.6.171/32 |
| 13.107.64.0/18 |
| 13.107.9.158 |
| 13.69.109.130 |
| 13.69.116.104 |
| 13.69.239.74 |
| 13.71.55.58 |
| 13.78.111.198 |
| 13.78.111.199 |
| 13.85.23.206 |
| 13.89.178.26 |
| 13.89.178.27 |
| 13.89.179.10 |
| 13.89.179.12 |
| 13.89.179.8 |
| 13.89.179.9 |
| 131.253.33.200 |
| 131.253.33.215/32 |
| 131.253.33.239 |
| 132.245.0.0/16 |
| 150.171.32.0/22 |
| 184.31.15.195 |
| 2.18.66.224 |
| 2.18.66.241 |
| 2.20.38.10 |
| 2.21.202.71 |
| 2.tlu.dl.delivery.mp.microsoft.com |
| 20.106.86.13 |
| 20.119.174.243 |
| 20.123.141.233 |
| 20.126.21.36 |
| 20.140.147.201 |
| 20.166.126.56 |
| 20.166.2.191 |
| 20.189.173.1 |
| 20.189.173.11 |
| 20.189.173.12 |
| 20.189.173.13 |
| 20.189.173.14 |
| 20.189.173.15 |
| 20.189.173.20 |
| 20.189.173.22 |
| 20.189.173.3 |
| 20.189.173.4 |
| 20.189.173.5 |
| 20.189.173.6 |
| 20.189.173.7 |
| 20.189.173.9 |
| 20.190.128.0/18 |
| 20.231.213.110 |
| 20.254.138.227 |
| 20.254.144.98 |
| 20.42.65.84 |
| 20.42.65.85 |
| 20.42.65.89 |
| 20.42.65.90 |
| 20.42.65.92 |
| 20.42.72.131 |
| 20.42.73.24 |
| 20.42.73.25 |
| 20.42.73.26 |
| 20.42.73.27 |
| 20.44.10.123 |
| 20.44.239.154 |
| 20.49.150.241 |
| 20.50.201.195 |
| 20.50.201.200 |
| 20.50.201.201 |
| 20.50.73.10 |
| 20.50.73.11 |
| 20.50.73.9 |
| 20.50.80.209 |
| 20.50.80.210 |
| 20.54.103.203 |
| 20.58.112.2 |
| 20.72.205.209 |
| 20.73.59.29 |
| 20.90.202.62 |
| 20.90.205.241 |
| 204.79.197.215/32 |
| 209.197.3.8 |
| 23.103.160.0/20 |
| 23.214.150.57 |
| 23.215.181.185 |
| 23.56.184.209 |
| 23.97.153.169 |
| 2603:1006::/40 |
| 2603:1006:1400::/40 |
| 2603:1006:2000::/48 |
| 2603:1007:200::/48 |
| 2603:1016::/36 |
| 2603:1016:1400::/48 |
| 2603:1016:2400::/40 |
| 2603:1017::/48 |
| 2603:1026::/36 |
| 2603:1026:2400::/40 |
| 2603:1026:3000::/48 |
| 2603:1027::/48 |
| 2603:1027:1::/48 |
| 2603:1036::/36 |
| 2603:1036:2400::/40 |
| 2603:1036:3000::/48 |
| 2603:1037::/48 |
| 2603:1037:1::/48 |
| 2603:1046::/36 |
| 2603:1046:1400::/40 |
| 2603:1046:2000::/48 |
| 2603:1047::/48 |
| 2603:1047:1::/48 |
| 2603:1056::/36 |
| 2603:1056:1400::/40 |
| 2603:1056:2000::/48 |
| 2603:1057::/48 |
| 2603:1057:2::/48 |
| 2603:1096::/38 |
| 2603:1096:400::/40 |
| 2603:1096:600::/40 |
| 2603:1096:a00::/39 |
| 2603:1096:c00::/40 |
| 2603:10a6:200::/40 |
| 2603:10a6:400::/40 |
| 2603:10a6:600::/40 |
| 2603:10a6:800::/40 |
| 2603:10d6:200::/40 |
| 2620:1ec:40::/42 |
| 2620:1ec:6::/48 |
| 2620:1ec:8f0::/46 |
| 2620:1ec:900::/46 |
| 2a01:111:200a:a::/64 |
| 2a01:111:2035:8::/64 |
| 2a01:111:f400::/48 |
| 2a01:111:f403::/48 |
| 2a01:111:f406:1::/64 |
| 2a01:111:f406:1004::/64 |
| 2a01:111:f406:1805::/64 |
| 2a01:111:f406:3404::/64 |
| 2a01:111:f406:8000::/64 |
| 2a01:111:f406:8801::/64 |
| 2a01:111:f406:a003::/64 |
| 2a01:111:f406:c00::/64 |
| 3.tlu.dl.delivery.mp.microsoft.com |
| 40.104.0.0/15 |
| 40.107.0.0/16 |
| 40.119.249.228 |
| 40.125.120.53 |
| 40.125.122.151 |
| 40.126.0.0/18 |
| 40.127.169.103 |
| 40.127.240.158 |
| 40.68.123.157 |
| 40.74.108.123 |
| 40.74.98.192 |
| 40.74.98.193 |
| 40.74.98.194 |
| 40.74.98.195 |
| 40.77.2.164 |
| 40.79.141.153 |
| 40.79.141.154 |
| 40.79.189.58 |
| 40.79.189.59 |
| 40.79.197.35 |
| 40.92.0.0/15 |
| 40.96.0.0/13 |
| 40.99.205.114 |
| 51.104.136.2 |
| 51.104.15.252 |
| 51.104.167.48 |
| 51.105.71.136 |
| 51.11.122.226 |
| 51.11.168.232 |
| 51.11.192.49 |
| 51.124.23.43 |
| 51.132.193.105 |
| 51.137.182.175 |
| 51.137.183.100 |
| 52.100.0.0/14 |
| 52.108.0.0/14 |
| 52.112.0.0/14 |
| 52.113.194.132 |
| 52.114.76.233 |
| 52.120.0.0/14 |
| 52.137.102.105 |
| 52.137.106.217 |
| 52.140.118.28 |
| 52.152.110.14 |
| 52.161.30.69 |
| 52.167.17.97 |
| 52.167.249.196 |
| 52.168.112.67 |
| 52.168.117.170 |
| 52.178.17.2 |
| 52.178.17.3 |
| 52.182.141.63 |
| 52.182.143.208 |
| 52.182.143.210 |
| 52.182.143.211 |
| 52.183.220.149 |
| 52.184.216.174 |
| 52.185.211.133 |
| 52.191.219.104 |
| 52.238.106.116/32 |
| 52.238.119.141/32 |
| 52.238.78.88/32 |
| 52.244.160.207/32 |
| 52.244.203.72/32 |
| 52.244.207.172/32 |
| 52.244.223.198/32 |
| 52.244.37.168/32 |
| 52.247.150.191/32 |
| 52.254.114.65 |
| 52.96.0.0/14 |
| 52.97.129.242 |
| 52.97.208.18 |
| 52.97.211.114 |
| 52.97.212.82 |
| 52.97.241.178 |
| 65.55.44.109 |
| 8.238.7.254 |
| 8.238.9.254 |
| 8.250.5.254 |
| 87.248.204.0 |
| 88.221.134.64 |
| 88.221.135.81 |
| 88.221.135.90 |
| 92.122.149.175 |
| 92.122.150.71 |
| 92.122.154.63 |
| 92.122.154.80 |
| 92.123.128.135 |
| 92.123.128.143 |
| 92.123.128.185 |
| 92.123.128.188 |
| 92.123.140.43 |
| 95.101.143.17 |
| 95.101.143.227 |
| 96.17.178.173 |
| 96.17.178.180 |
| a.clarity.ms |
| a.config.skype.com |
| account.activedirectory.windowsazure.com |
| account.live.com |
| account.office.net |
| accounts.accesscontrol.windows.net |
| acdc-direct.office.com |
| activation.sls.microsoft.com |
| activity.windows.com |
| admin.microsoft.com |
| adminwebservice.microsoftonline.com |
| agave.myanalytics.cdn.office.net |
| ajax.aspnetcdn.com |
| aka.ms |
| amp.azure.net |
| apc.delve.office.com |
| api.cdp.microsoft.com |
| api.diagnostics.office.com |
| api.office.com |
| api.passwordreset.microsoftonline.com |
| apibasic.diagnostics.office.com |
| apis.live.net |
| appsforoffice.microsoft.com |
| array501.prod.do.dsp.mp.microsoft.com |
| array502.prod.do.dsp.mp.microsoft.com |
| array505.prod.do.dsp.mp.microsoft.com |
| array507.prod.do.dsp.mp.microsoft.com |
| array508.prod.do.dsp.mp.microsoft.com |
| array511.prod.do.dsp.mp.microsoft.com |
| array512.prod.do.dsp.mp.microsoft.com |
| array513.prod.do.dsp.mp.microsoft.com |
| array603.prod.do.dsp.mp.microsoft.com |
| array604.prod.do.dsp.mp.microsoft.com |
| array605.prod.do.dsp.mp.microsoft.com |
| array609.prod.do.dsp.mp.microsoft.com |
| array611.prod.do.dsp.mp.microsoft.com |
| ars.smartscreen.microsoft.com |
| assets.onestore.ms |
| atm-fp-direct.office.com |
| attachments.office.net |
| augloop.office.com |
| aus.delve.office.com |
| auth.gfx.ms |
| autodiscover.outlook.com |
| autodiscover-s.outlook.com |
| autologon.microsoftazuread-sso.com |
| az416426.vo.msecnd.net |
| az826701.vo.msecnd.net |
| becws.microsoftonline.com |
| bing.com |
| broadcast.skype.com |
| browser.events.data.microsoft.com |
| browser.events.data.msn.com |
| browser.pipe.aria.microsoft.com |
| business.bing.com |
| c.bing.com |
| c.bing.net |
| c.live.com |
| c1.microsoft.com |
| can.delve.office.com |
| cdn.odc.officeapps.live.com |
| cdn.onenote.net |
| cdn.uci.officeapps.live.com |
| cdnprod.myanalytics.microsoft.com |
| checkappexec.microsoft.com |
| cl2.apple.com |
| client.wns.windows.com |
| clientconfig.microsoftonline-p.net |
| clients.config.office.net |
| cloudcheckenabler.azurewebsites.net |
| companymanager.microsoftonline.com |
| compass-ssl.microsoft.com |
| compliance.microsoft.com |
| config.edge.skype.com |
| config.office.com |
| connect.facebook.net |
| contentstorage.osi.office.net |
| cp501-prod.do.dsp.mp.microsoft.com |
| cp601-prod.do.dsp.mp.microsoft.com |
| crl.microsoft.com |
| ctldl.windowsupdate.com |
| cxcs.microsoft.net |
| d.docs.live.net |
| dc.services.visualstudio.com |
| delve.office.com |
| delve-gcc.office.com |
| device.login.microsoftonline.com |
| dgps.support.microsoft.com |
| directory.services.live.com |
| disc501.prod.do.dsp.mp.microsoft.com |
| disc601.prod.do.dsp.mp.microsoft.com |
| dmd.metaservices.microsoft.com |
| docs.live.net |
| docs.microsoft.com |
| eas.outlook.com |
| ecn.dev.virtualearth.net |
| ecs.office.com |
| edge.activity.windows.com |
| edge.microsoft.com |
| edge-enterprise.activity.windows.com |
| edgeservices.bing.com |
| enterprise-eudb.activity.windows.com |
| enterpriseregistration.windows.net |
| eu-office.events.data.microsoft.com |
| eur.delve.office.com |
| eu-teams.events.data.microsoft.com |
| excelbingmap.firstpartyapps.oaspapps.com |
| excelcs.officeapps.live.com |
| exo.nel.measure.office.net |
| fe2cr.update.microsoft.com |
| fe3cr.delivery.mp.microsoft.com |
| firstpartyapps.oaspapps.com |
| forms.office.com |
| fp-afd.azurefd.us |
| francecentral-prod.notifications.teams.microsoft.com |
| fs.microsoft.com |
| functional.events.data.microsoft.com |
| gbr.delve.office.com |
| geo.prod.do.dsp.mp.microsoft.com |
| go.microsoft.com |
| graph.microsoft.com |
| graph.windows.net |
| home.office.com |
| i.s-microsoft.com |
| ic3.events.data.microsoft.com |
| ieonlinews.microsoft.com |
| img-prod-cms-rt-microsoft-com.akamaized.net |
| in.applicationinsights.azure.com |
| ind.delve.office.com |
| informationprotection.hosting.portal.azure.net |
| insertmedia.bing.office.net |
| jpn.delve.office.com |
| kor.delve.office.com |
| kv501.prod.do.dsp.mp.microsoft.com |
| kv601.prod.do.dsp.mp.microsoft.com |
| lam.delve.office.com |
| licensing.md.mp.microsoft.com |
| licensing.mp.microsoft.com |
| livetileedge.dsx.mp.microsoft.com |
| login.live.com |
| login.microsoft.com |
| login.microsoftonline.com |
| login.microsoftonline-p.com |
| login.windows.net |
| login.windows-ppe.net |
| logincert.microsoftonline.com |
| loginex.microsoftonline.com |
| login-us.microsoftonline.com |
| loki.delve.office.com |
| manage.office.com |
| management.azure.com |
| mem.gfx.ms |
| messaging.office.com |
| mlccdn.blob.core.windows.net |
| mlccdnprod.azureedge.net |
| mscrl.microsoft.com |
| msdn.microsoft.com |
| msedge.api.cdp.microsoft.com |
| msedge.b.tlu.dl.delivery.mp.microsoft.com |
| msgapi.teams.microsoft.com |
| myanalytics.microsoft.com |
| myanalytics-gcc.microsoft.com |
| nam.delve.office.com |
| nexus.microsoftonline-p.com |
| nexusrules.officeapps.live.com |
| nleditor.osi.office.net |
| nps.onyx.azure.net |
| o15.officeredir.microsoft.com |
| o365diagtelemetry.trafficmanager.net |
| ocos-office365-s2s.msedge.net |
| ocps.manage.microsoft.com |
| ocsredir.officeapps.live.com |
| odc.officeapps.live.com |
| odcsm.officeapps.live.com |
| offcatedge.azureedge.net |
| office.live.com |
| office15client.microsoft.com |
| officeapps.live.com |
| officecdn.microsoft.com |
| officecdn.microsoft.com.edgesuite.net |
| officeclient.microsoft.com |
| officeimg.vo.msecnd.net |
| officepreviewredir.microsoft.com |
| officeredir.microsoft.com |
| oneclient.sfx.ms |
| onedriveclubproddm20043.blob.core.windows.net |
| outlook.office.com |
| outlook.office365.com |
| outlook.uservoice.com |
| outlookdiagnostics.azureedge.net |
| partnerservices.getmicrosoftkey.com |
| passwordreset.microsoftonline.com |
| peoplegraph.firstpartyapps.oaspapps.com |
| platform.linkedin.com |
| policykeyservice.dc.ad.msft.net |
| portal.microsoftonline.com |
| portal.office.com |
| pptcs.officeapps.live.com |
| presence.teams.microsoft.com |
| prod.firstpartyapps.oaspapps.com.akadns.net |
| prod.msocdn.com |
| products.office.com |
| protection.office.com |
| provisioningapi.microsoftonline.com |
| r.bing.com |
| r.clarity.ms |
| r.office.microsoft.com |
| r1.res.office365.com |
| r3.res.office365.com |
| r3.res.outlook.com |
| r4.res.office365.com |
| res.delve.office.com |
| roaming.officeapps.live.com |
| sara.api.support.microsoft.com |
| searchhighlights.bing.com |
| secure.aadcdn.microsoftonline-p.com |
| securescore.office.com |
| security.microsoft.com |
| self.events.data.microsoft.com |
| services.bingapis.com |
| settings-win.data.microsoft.com |
| sfdataservice.microsoft.com |
| sfgbr.loki.delve.office.com |
| shellprod.msocdn.com |
| shredder-eu.osi.office.net |
| signup.live.com |
| slscr.update.microsoft.com |
| smartscreen.microsoft.com |
| smartscreen-prod.microsoft.com |
| staffhub.ms |
| staffhub.office.com |
| staffhub.uservoice.com |
| stamp2.login.microsoftonline.com |
| statics.teams.cdn.office.net |
| storage.live.com |
| store.office.com |
| storecatalogrevocation.storequality.microsoft.com |
| substrate.office.com |
| suite.office.net |
| support.content.office.net |
| support.microsoft.com |
| support.office.com |
| tasks.office.com |
| tasks.teams.microsoft.com |
| teams.events.data.microsoft.com |
| teams.microsoft.com |
| technet.microsoft.com |
| telemetryservice.firstpartyapps.oaspapps.com |
| tellmeservice.osi.office.net |
| templates.office.com |
| templateservice.office.com |
| th.bing.com |
| trouter2-azsc-euno-4-b.trouter.teams.microsoft.com |
| tse1.mm.bing.net |
| tsfe.trafficshaping.dsp.mp.microsoft.com |
| uci.cdn.office.net |
| uci.officeapps.live.com |
| uk.ng.msg.teams.microsoft.com |
| uk-api.asm.skype.com |
| ukc-excel.officeapps.live.com |
| uk-prod.asyncgw.teams.microsoft.com |
| upload.fp.measure.office.com |
| v10.events.data.microsoft.com |
| v10.vortex-win.data.microsoft.com |
| videocontent.osi.office.net |
| videoplayercdn.osi.office.net |
| view.atdmt.com |
| vortex.data.microsoft.com |
| watson.events.data.microsoft.com |
| webshell.suite.office.com |
| wikipedia.firstpartyapps.oaspapps.com |
| wordcs.officeapps.live.com |
| workplaceanalytics.cdn.office.net |
| workplaceanalytics.office.com |
| world.ces.microsoftcloud.com |
| wus-firstpartyapps.oaspapps.com |
| www.bing.com |
| www.microsoft.com |
| www.office.com |
| www.onedrive.com |
| www.outlook.com |
Disclaimer — if you manually bypass Feature Update blocks, you risk causing issues with your device. The blocks exist for a reason and should be respected. This information is provided for educational purposes only. Proceed with caution.
Windows 10 Feature Updates are released twice per year. For each release, Microsoft has the ability to block the update from being installed or even showing up in Widows Update for applications/drivers/devices that have known compatibility issues. This is a pretty great feature since it helps prevent unnecessary failures for already known issues that Microsoft is possibly already working to address.
The flaw in this feature is the lack of visibility into what is being blocked and how/when it should be unblocked. Microsoft has gotten a little better with this area by keeping this site updated https://docs.microsoft.com/windows/release-information/status-windows-10-2004, however from a client installation perspective, it is often difficult or even impossible to match up an error message/code with anything published on that site (or any other Microsoft site). When Windows 10 2004 was released, there was a block in place for certain hardware models including the Surface line. When your boss has a Surface Pro 7 that can’t upgrade to the latest feature update, you’re not going to have a good time. This post is a deep dive into my experience with identifying Hard Blocks and making sense out of generic error messages like the one below. It will also contain some best guesses for how some things work where I may not have a 100% clear understanding.
Last things First
After writing this, I realized that I have crammed a lot if stuff in here. I want to highlight the main points to keep things from getting lost in the pile.
- Gain a better understanding of Feature Update blocks that prevent devices from upgrading — sometimes blocking the update from even showing up on the device as available.
- Understand how to manually convert Appraiser results to XML then compare to the Windows Compatibility Database (appraiser.sdb).
- Automate the collection and assessment of Feature Update blocks using custom PowerShell module FU.WhyAmIBlocked.
Blocked Upgrade Messages
When Windows 10 2004 shipped, the internet filled up with reports of people getting messages indicating that their devices couldn’t be upgraded. Everyone was asking — ‘Why am I blocked?’. Presenting a message telling us that we are blocked, but providing no actionable information is less than helpful. This needs to improve.
This PC can’t be upgraded to Windows 10
Let’s start with this message. It is very generic and less than helpful. It can appear in the setup UI if you are manually running setup.exe or in c:\$WINDOWS.~BT\Sources\Panther\ActionableReport.html.
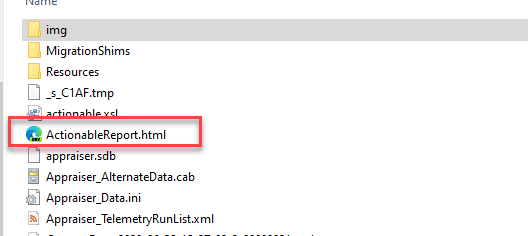
|
|
…Your device isn’t quite ready for it…
On these same devices, if you attempt to pull the feature update from Windows Update, you may see a message like this one that showed up for Windows 10 2004.
|
|
CompatData Hard Block
When a Feature Update fails to install, you can generally check in the last CompatData_*.xml file for information about the failure. Unfortunately, sometimes the information is vague.
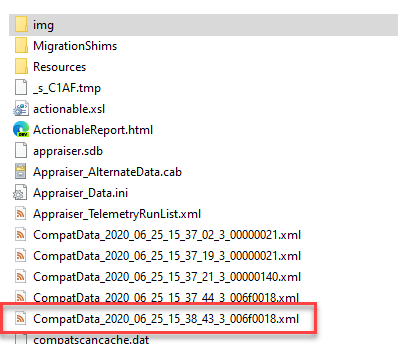
|
|
ConfigMgr and Desktop Analytics
If you are an enterprise customer and are fortunate enough to use ConfigMgr, you can leverage Desktop Analytics to assess device and app compatibility BEFORE attempting to install feature updates. We have been using this (And Windows Analytics before DA) since it was released and it has almost eliminated the need for testing ALL of our applications before deploying the latest Feature Update — we still test critical apps. The shortcoming with DA is that is simply reports back what the Microsoft Compatibility Appraiser reports. It doesn’t include details specific to the blocking app. Work is still being done with DA, so I think there’s hope for integrating more data in the future.
Microsoft Compatibility Appraiser
So, I mentioned the Microsoft Compatibility Appraiser in the previous section. Whether you are aware of it or not, your Windows 10 device is actively assessing your device’s compatibility with Windows releases (possibly other monthly updates as well). I’ll break down the pieces that I have put together, but I still feel like this a ‘black box’ that I don’t fully understand.
CompatTelRunner Scheduled Task
Open Task Scheduler and you will find the Microsoft Compatibility Appraiser task under Task Scheduler Library>Microsoft>Windows>Application Experience
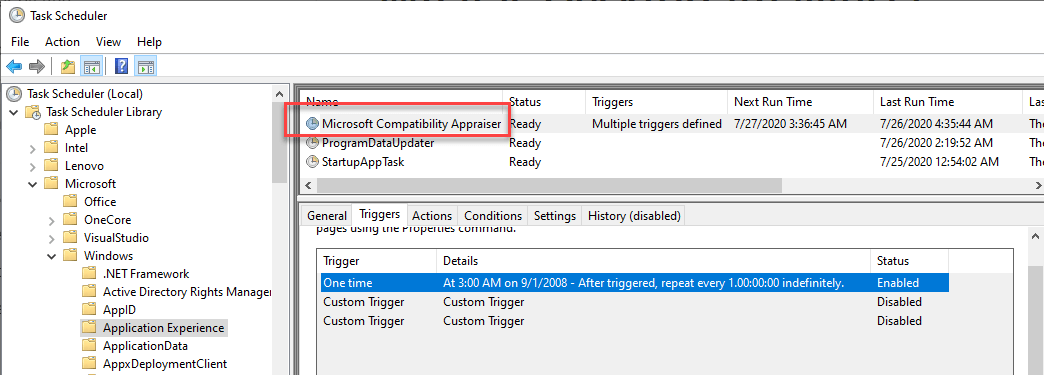
This task launches:
%windir%\system32\compattelrunner.exe
which in turn launches:
%windir%\system32\CompatTelRunner.exe -m:appraiser.dll -f:DoScheduledTelemetryRun
The output of this task produces a set of registry entries as well as some output files (possibly others that I’ve missed):
|
|
These .bin files that are generated contain a list of compatibility assessment results. Portions of the results are also listed in the registry. For example, if there are hard blocks, a SdbAppGUID will be listed in the .bin file and a corresponding entry will be listed in the registry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Appraiser\GWX\SdbEntries
Since the entries are in the registry, you can easily use ConfigMgr’s CMPivot tool to query the values to determine which SdbAppGUIDs are causing blocks using this CMPivot query:
|
|
Compattelrunner.exe also checked for any policies you may have enabled that prevent updates.
|
|
Appraiser.sdb and Alternate Appraiser Data
The appraiser consumes a database of info from Appraiser.sdb and uses a task list file Appraiser_TelemetryRunList.xml to tell it what to process. The default location of these files is C:\Windows\System32\appraiser.
If a machine is not on the latest Feature Update, compattelrunner.exe will download an Alternate_AppraiserData.cab file to c:\Windows\appcompat\appraiser from http://adl.windows.com/appraiseradl/YYYY_DD_MM_??_??_ARCH.CAB
Here’s a list of cab files that I’ve been able to find by looking at setupact.log files and searching the internet for other people’s logs. I don’t know where the current URL comes from to tell the client which file to get nor do I know what the last 2 sets of numbers stand for. I was thinking they may be HH_MM but that doesn’t seem to line up every time.
|
|
You can read more about data sharing and this URL here: https://docs.microsoft.com/mem/configmgr/desktop-analytics/enable-data-sharing. Be sure that you allow clients to access the listed URLs or you may experience issues with updates not having the latest compatibility information.
When you expand the cab files using, you will get the following contents:
|
|
These files are the key to understanding why machines will be blocked one day then unblocked the next and why you may experience different results on the same devices.
Dynamic Updates
If you disable Dynamic Updates or prevent your devices from going to the URLs listed above, you run the risk of preventing your devices from being able to install the latest Feature Update or install it properly. Whenever Windows setup runs, it will run a customized compatibility assessment and will download the latest Alternate_AppraiserData.cab files. This ensure that it has the latest compatibility information to assess a device against and provides a list of current migration shims that may mean the difference between success or failure of the upgrade.
Setupact.log
During or after a Feature Update, the setupact.log shows where it goes out to get the latest cab then runs a compatibility assessment. This one of several compatibility checks that are performed.
|
|
Just as the CompatTelRunner scheduled task will create new bin files, the process during Windows Setup will create a set of XML and BIN files in the Panther folder.
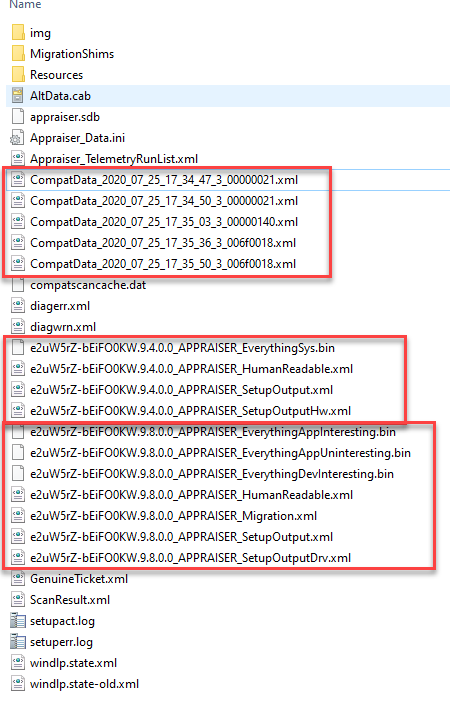
Appraiser_TelemetryRunList.xml
The Appraiser_TelemetryRunList.xml file tells the appraiser which actions to perform. It also tells it which sdb to use and where to output results of each scan. You could compare this xml to the xml files output during Windows setup and match up the components. I haven’t gotten that far into it. The module included at the end here has PowerShell to generate your own RunList.
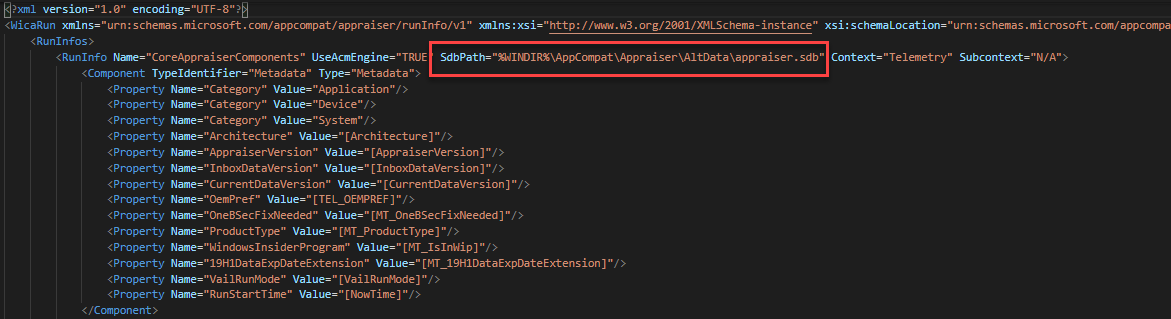
Force a new Appraiser.sdb to process
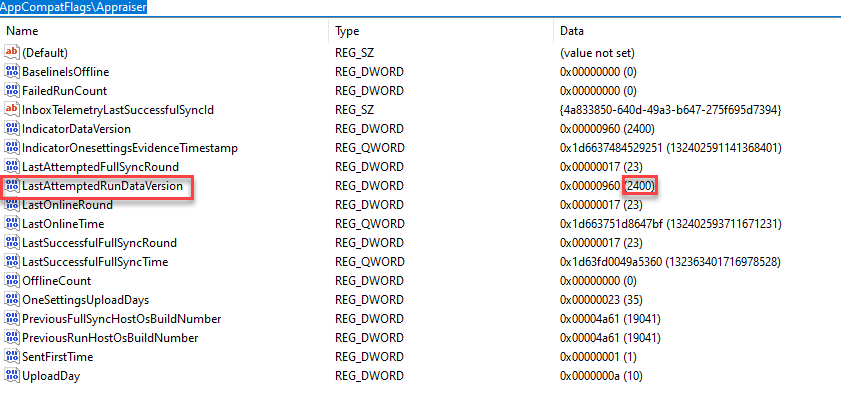
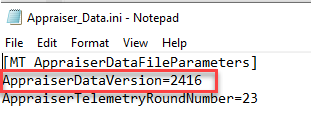
During testing, I was able to replace the current Appraiser_AlternateData.cab file with an older version and run the scheduled task and the old file would be used. This is because the registry key logs which files were used last. If the key isn’t updated or deleted, a new file won’t be downloaded. Comparing Appraiser_Data.ini with the registry key you can determine if the device has used the current database.
I was also able to delete the Appraiser_AlternateData.cab from C:\Windows\appcompat\appraiser and re-run the scheduled task and it would pull down the latest version.
Deserialize Appraiser BIN files
The output of the appraiser process will be a .bin file (and during a feature update an .xml file). The bin file is just a binary XML file that can be converted by using the appraiser process. It’s a configuration option built into the RunList XML. Here’s an example XML file that will take the file C:\Windows\appcompat\appraiser\APPRAISER_TelemetryBaseline_20H1.bin and deserialize it into the XML file APPRAISER_TelemetryBaseline_20H1_HUMANREADABLE.xml
|
|
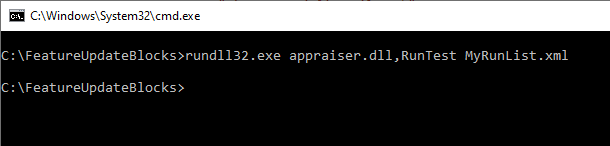
Run this in a cmd prompt and point to your RunList.
rundll32.exe appraiser.dll,RunTest MyRunList.xml
I used this script from Technet gallery (which will be going away soon) to get started down this process. It appears to be maintained by someone from the Microsoft CSS team but I’m not sure. https://gallery.technet.microsoft.com/scriptcenter/APPRAISE-APPRAISERbin-to-8399c0ee
*HumanReadable.XML
In the screenshot below of the Windows Panther folder, you’ll see bin and xml files. These files were generated during a Feature Update and you’ll see that they are already in XML format. From my experience, I’ve found that the second entry is the one that will generally contain block information. They correspond to the bin files that we see in the appraiser folder. There will be an *_UNV.bin and one that corresponds to the Windows release like *_20H1.bin. Likewise, the files created during setup appear to be broken out the same way.
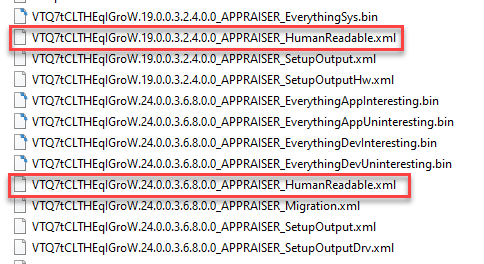
An example of a device that’s blocked by an entry in one of these files would look like this. This is from the appraiser output folder, not a Feature Update. Search the file for the BlockingMatchingInfo property to find blocks.
|
|
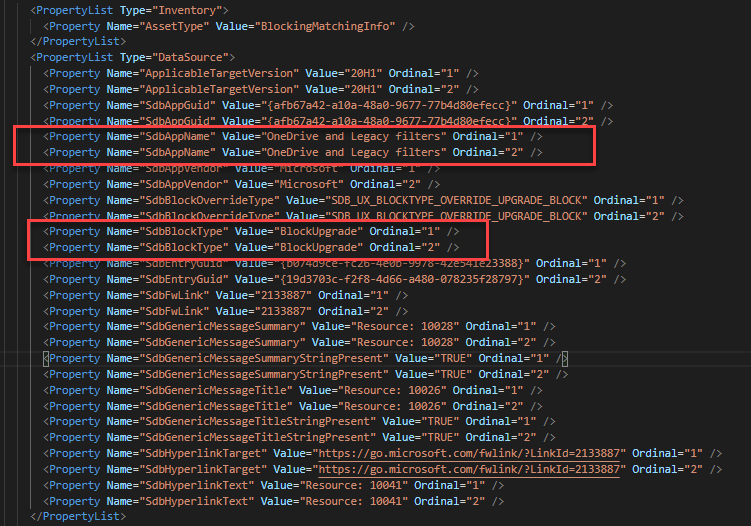
Here’s another example of the block generated during a Feature Update. The main differences are 1) there are 2 blocks in the first example 2) the feature update blocks render out the GenericMessage text where the appraiser version just points to a Resource ID.
|
|
The entries are grouped by Name, so you have to follow the Ordinal values. All Ordinal = "1" entries belong to the same block. In this case we can see that this device has 2 blocks for OneDrive and Legacy filters. Not all entries listed in this section will be hard blocks but it’s a good place to start.
What the Heck is OneDrive and Legacy filters?!?
In my search to find answers, the OneDrive and Legacy filters block has been the thing that I just didn’t understand. If you list an app or hardware model in the block, that makes sense, but this one was so vague that it drove me to dig deeper.
I had a hunch that the info I needed would be in the appraiser.sdb files. After some digging around and lots of trial and error, I found 2 tools that ultimately helped convert the Compatibility Appraiser Database to XML.
https://github.com/TheEragon/SdbUnpacker — Python script to decompress the sdb.
https://devblogs.microsoft.com/setup/shim-database-to-xml — EXE to convert from sdb format to XML using the SDB API.
Once I had extracted the SDB into XML. I was able to match the GUIDs from the appraiser bin files with entries in the database. Each entry lists the files and registry keys that are used to determine if something should be blocked. In my case, there were 4 relevant entries related to OneDrive and Legacy filters.
|
|
From this entry, we can see that the appraiser is looking for the existence of registry keys. If they exit, it will block the upgrade and display messaged tied to the IDs listed in the BLOCK_UPGRADE section. Once I removed the registry keys for all of the blocks and re-ran the appraiser, the blocks went away and I was able to apply the Feature Update.
|
|
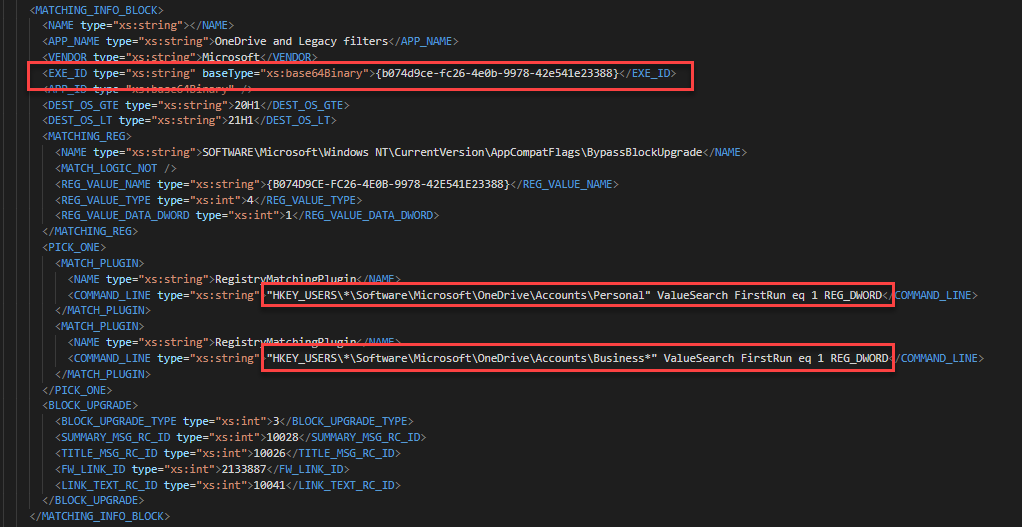
While I was in the sdb, I discovered another registry key that allowed me to bypass the block without actually deleting registry keys that may be critical to the app causing the block.
|
|
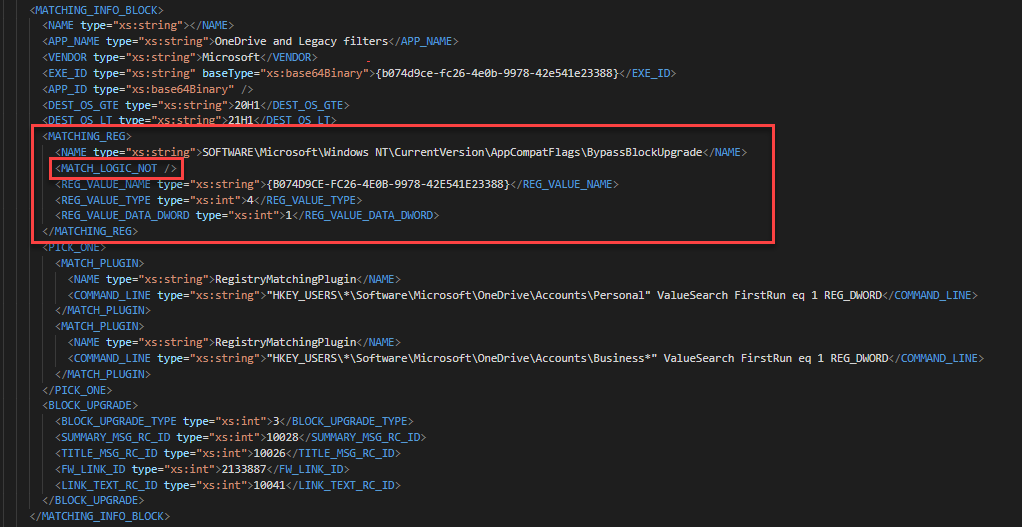
Once I created the regkeys and re-ran the appraiser, the blocks were still listed, but new entries appeared referencing the BypassBlockUpgrade keys.
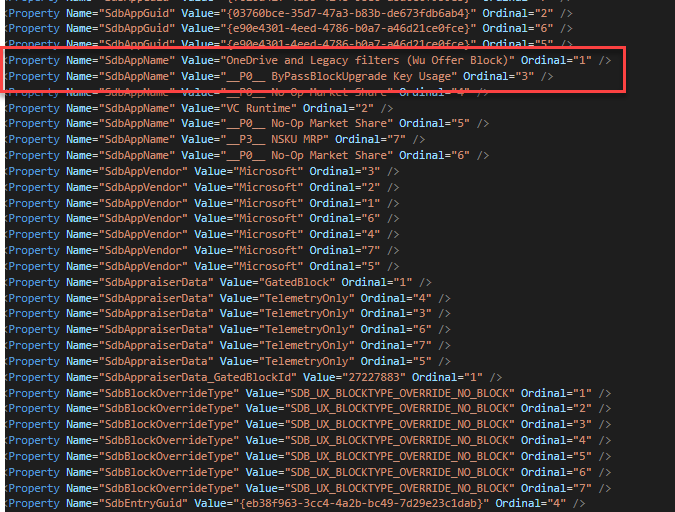
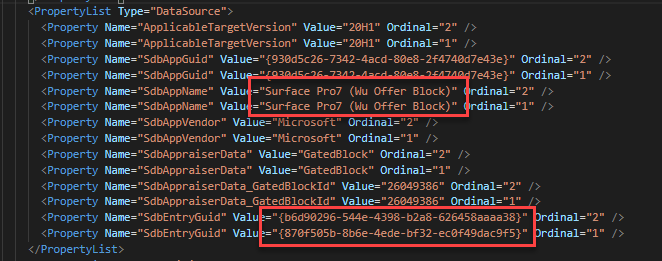
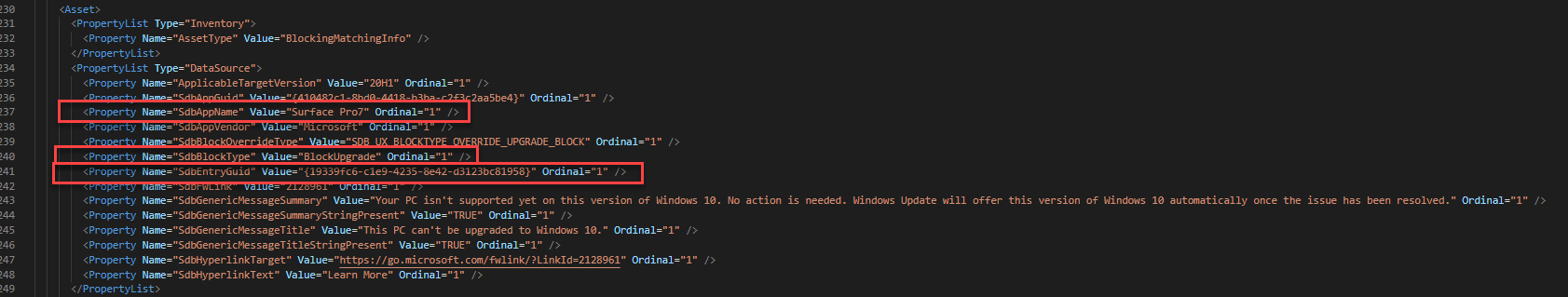
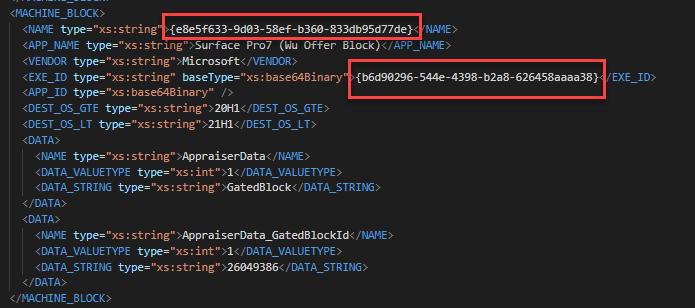
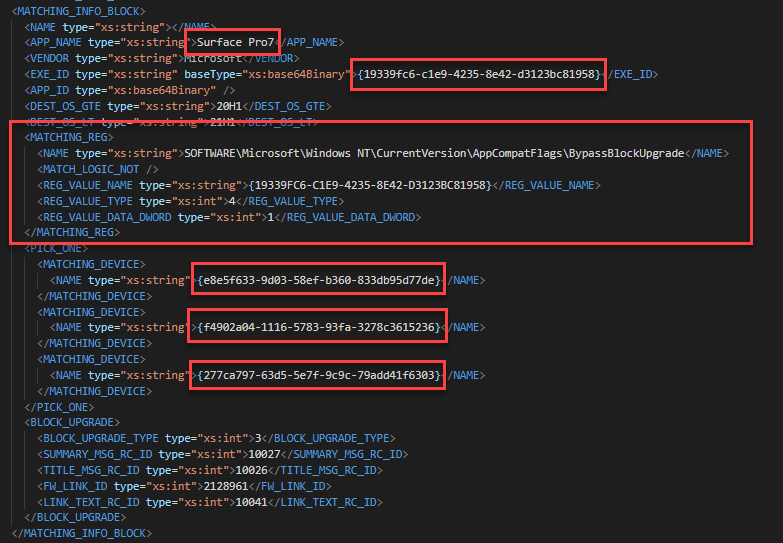
Here’s another example where the Surface Pro 7 was blocked for 2004. This one gets a bit tricky. The first image show 2 GUIDs that match the GUIDs for a MACHINE_BLOCK in the 4th image. The second image shows the SdbEntryGuid that matches the MATCHING_INFO_BLOCK in the 3rd image. You’ll also see the registry key to bypass the block in the 3rd image. This whole time, we could have bypassed the Surface Pro 7 block!!!
FU.WhyAmIBlocked Powershell Module
FU is short for Feature Update
After going through all of this, I decided that this was too many steps to perform on a per-machine basis, so I took everything and created a new PowerShell module to help. Detailed usage info and updates can be found on the GitHub project site https://github.com/AdamGrossTX/FU.WhyAmIBlocked.
It has been published to the PowerShell Gallery (My first one, thanks Ben!) and you can install it directly on any machine you need to troubleshoot. https://www.powershellgallery.com/packages/FU.WhyAmIBlocked
In order to process the database SDB files, you will need Python installed. I have tested with Python 3.8 using the msi installer or the Windows Store app (which is pretty sweet!).
Also, I was limited on the block scenarios that I could replicate in my environment so results and match text files may not show everything. I suggest manually searching the appraiser.sdb.XML file for additional entries.
|
|
Assessing your Compatibility Blocks at Scale
Here’s what I did to assess my environment:
- Collect SDB Block GUIDS and SDB Versions from the Registry using CMPivot
|
|
- Export results to CSV and get a distinct GUID list
- Process GUIDs against Appraiser.sdb.xml
|
|
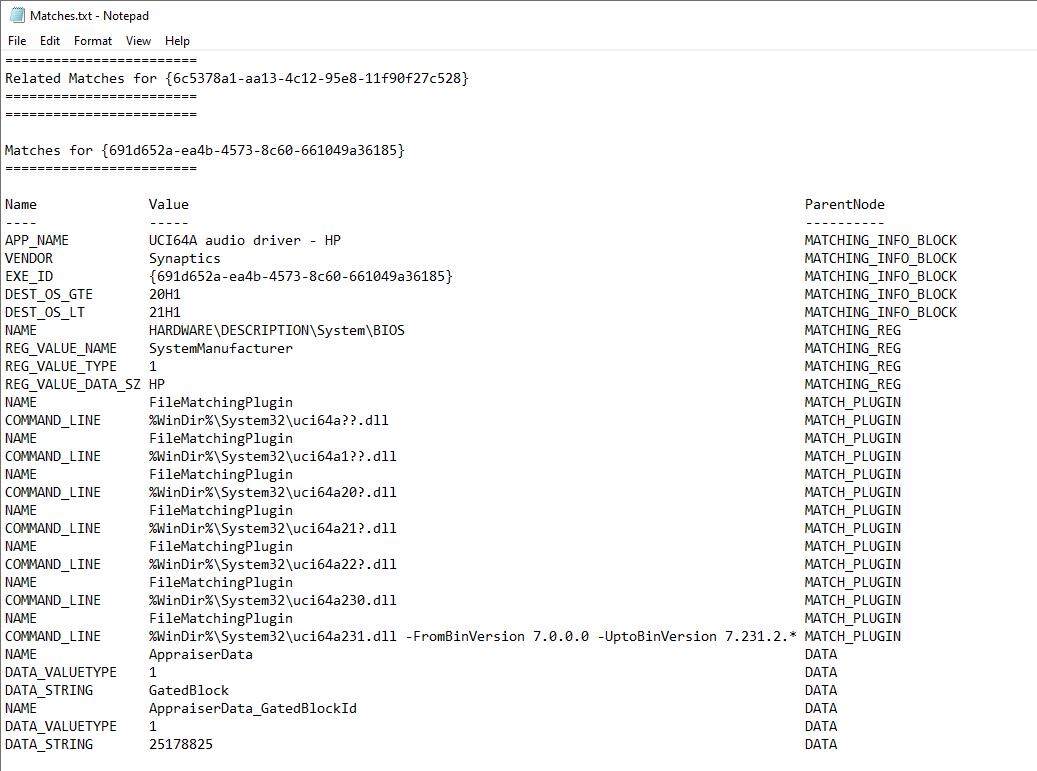
This should produce a Matches.txt file that you can use to review all of your enterprise’s blocks without having to collect any additional client information.
Summary
I feel like I’ve covered all of the pieces of the puzzle that I’ve put together at this point. I don’t think I’m finished with this process or the module, but needed to get this first round of info out of my head before I lose it. I’d love to hear your thoughts and get feedback on the module.
References
- sdbUnpacker — https://github.com/TheEragon/SdbUnpacker
- sdb2xml — https://devblogs.microsoft.com/setup/shim-database-to-xml/
- Shim Database API — https://docs.microsoft.com/windows/win32/devnotes/application-compatibility-database?redirectedfrom=MSDN
- Get-SDBFileInfo.ps1 — https://github.com/cinglis-msft/UpdateComplianceConfigurationScript/blob/1ab7c920ea81b86a1b36c698027c8fb8fdd064d5/Pilot/Diagnostics/Get-SdbFileInfo.ps1
- CSSAPRS — https://gallery.technet.microsoft.com/scriptcenter/APPRAISE-APPRAISERbin-to-8399c0ee
- AppRPS script. May be a predecessor to the one above — https://aka.ms/AppRPS
Addendum
After posting this, I got a message from Trevor Jones pointing me to a Microsoft doc with a buried registry key to bypass any data collection compatibly checks for Feature Updates. https://docs.microsoft.com/windows/deployment/update/update-compliance-feature-update-status#opting-out-of-compatibility-hold
Here’s the text from that post in case it ever goes away:
Compatibility holds
Microsoft uses diagnostic data to determine whether devices that use Windows Update are ready for a feature update in order to ensure a smooth experience. When Microsoft determines a device is not ready to update due to a known issue, a compatibility hold is generated to delay the device’s upgrade and safeguard the end-user experience. Holds are released over time as diagnostic data is analyzed and fixes are addressed. Details are provided on some, but not all compatibility holds on the Windows 10 release information page for any given release.
Opting out of compatibility hold
Microsoft will release a device from a compatibility hold when it has determined it can safely and smoothly install a feature update, but you are ultimately in control of your devices and can opt out if desired. To opt out, set the registry key HKLM\Software\Microsoft\Windows NT\CurrentVersion\502505fe-762c-4e80-911e-0c3fa4c63fb0 to a name of DataRequireGatedScanForFeatureUpdates and a value of «.
Setting this registry key to 0 will force the device to opt out from all compatibility holds. Any other value, or deleting the key, will resume compatibility protection on the device.
I will test this when I get some time and see if how it behaves compared to the other options mentioned. Thanks Trevor!
This post lists the internet communication targets of the Microsoft Windows operating system, including its various services and UWP apps. This post is a part of my application network connection monitoring series, a group of articles that explain how to analyze the network traffic of any Windows or macOS app.
The series consists of the following articles:
- Part 1: explanation of the methodology
- Part 2: list of MS Office & Teams communication targets
- Part 3 (this article): list of Windows, OS services & UWP apps communication targets
- Part 4: list of Citrix CVAD communication targets
- Part 5: list of Adobe Acrobat Reader, Photoshop, & Creative Cloud communication targets
TL;DR
The Microsoft Windows operating system talks to 291 hosts and 2,764 IPs on the internet. List of URLs & details below.
About This Data
What Is This List?
The table below lists the internet hosts the Microsoft Windows operating system, including its various services and UWP apps communicated with in a real environment. For each application, the table shows:
- Application name
- Application version(s)
- Process(es) of the application
- Number of distinct target IP addresses
- Names and ports of the target hosts
Where Does the Data Come From?
The data was collected in vast limits’ internal network by uberAgent, our endpoint monitoring and analytics product. The data spans a 30-day time range in early 2021.
The table contains metadata of actual network communications. It is accurate and complete insofar as I did not alter anything. I did, however, remove some internal systems and the results of manual web browsing (or similar). Some hostnames may be specific to our location (Germany).
List of Windows OS & UPW Apps Network Connection Target Hosts
| Application | App version(s) | Process(es) | #Target IPs | Targets |
|---|---|---|---|---|
| BDESVC | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 1 | enterpriseregistration.windows.net:443 |
| BitLocker Drive Encryption Service | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 2 | enterpriseregistration.windows.net:443 ocsp.digicert.com:80 status.rapidssl.com:80 |
| CDPUserSvc | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 4 | activity.windows.com:443 enterprise.activity.windows.com:443 |
| Connected Devices Platform Service | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 1 | aad.cs.dds.microsoft.com:443 continuum.dds.microsoft.com:443 cs.dds.microsoft.com:443 |
| Connected Devices Platform User Service | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 15 | activity.windows.com:443 discover.aadrm.com:443 enterprise.activity.windows.com:443 substrate.office.com:443 |
| Cryptographic Services | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 340 | 11.tlu.dl.delivery.mp.microsoft.com:80 2.au.download.windowsupdate.com:80 2.tlu.dl.delivery.mp.microsoft.com:80 3.au.download.windowsupdate.com:80 au.download.windowsupdate.com:80 crl.apple.com:80 crl.comodoca.com:80 crl.globalsign.net:80 crl.identrust.com:80 crl.usertrust.com:80 crl.verisign.com:80 crl3.digicert.com:80 ctldl.windowsupdate.com:80 dl.delivery.mp.microsoft.com:80 download.windowsupdate.com:80 ocsp.comodoca.com:80 ocsp.digicert.com:80 ocsp.globalsign.com:80 ocsp2.globalsign.com:80 status.rapidssl.com:80 |
| Delivery Optimization | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 431 | 11.au.download.windowsupdate.com:80 11.tlu.dl.delivery.mp.microsoft.com:80 2.au.download.windowsupdate.com:80 2.tlu.dl.delivery.mp.microsoft.com:80 3.au.download.windowsupdate.com:80 3.tlu.dl.delivery.mp.microsoft.com:80 9.tlu.dl.delivery.mp.microsoft.com:80 array602.prod.do.dsp.mp.microsoft.com:443 array603.prod.do.dsp.mp.microsoft.com:443 array604.prod.do.dsp.mp.microsoft.com:443 array605.prod.do.dsp.mp.microsoft.com:443 array606.prod.do.dsp.mp.microsoft.com:443 array607.prod.do.dsp.mp.microsoft.com:443 array608.prod.do.dsp.mp.microsoft.com:443 array609.prod.do.dsp.mp.microsoft.com:443 array610.prod.do.dsp.mp.microsoft.com:443 array611.prod.do.dsp.mp.microsoft.com:443 array612.prod.do.dsp.mp.microsoft.com:443 array614.prod.do.dsp.mp.microsoft.com:443 array615.prod.do.dsp.mp.microsoft.com:443 array616.prod.do.dsp.mp.microsoft.com:443 array801.prod.do.dsp.mp.microsoft.com:443 array805.prod.do.dsp.mp.microsoft.com:443 array808.prod.do.dsp.mp.microsoft.com:443 array810.prod.do.dsp.mp.microsoft.com:443 array812.prod.do.dsp.mp.microsoft.com:443 array813.prod.do.dsp.mp.microsoft.com:443 au.download.windowsupdate.com:80 cp501.prod.do.dsp.mp.microsoft.com:443 cp601.prod.do.dsp.mp.microsoft.com:443 cp801.prod.do.dsp.mp.microsoft.com:443 ctldl.windowsupdate.com:80 disc601.prod.do.dsp.mp.microsoft.com:443 disc801.prod.do.dsp.mp.microsoft.com:443 dl.delivery.mp.microsoft.com:80 download.windowsupdate.com:80 emdl.ws.microsoft.com:80 geo.prod.do.dsp.mp.microsoft.com:443 geover.prod.do.dsp.mp.microsoft.com:443 kv501.prod.do.dsp.mp.microsoft.com:443 kv601.prod.do.dsp.mp.microsoft.com:443 kv801.prod.do.dsp.mp.microsoft.com:443 msedge.b.tlu.dl.delivery.mp.microsoft.com:80 msedge.f.dl.delivery.mp.microsoft.com:80 officecdn.microsoft.com.edgesuite.net:80 officecdn.microsoft.com:80 tlu.dl.delivery.mp.microsoft.com:80 |
| Device Setup Manager | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 26 | crl3.digicert.com:80 displaycatalog.mp.microsoft.com:443 dmd.metaservices.microsoft.com:80 go.microsoft.com:80 ocsp.digicert.com:80 |
| DsmSvc | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 2 | dmd.metaservices.microsoft.com:80 go.microsoft.com:80 |
| Group Policy Client | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
backgroundTaskHost.exe | 2 | login.live.com:443 |
| LocalBridge | 18.2006.1031.0 18.2008.1271.0 |
LocalBridge.exe | 5 | config.edge.skype.com:443 officehomeblobs.blob.core.windows.net:443 |
| Microsoft Account Sign-in Assistant | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 48 | crl3.digicert.com:80 ctldl.windowsupdate.com:80 login.live.com:443 login.microsoftonline.com:443 ocsp.digicert.com:80 status.geotrust.com:80 sv.symcb.com:80 www.tm.a.prd.aadg.akadns.net:443 |
| Microsoft Edge Update | 1.3.117.29 1.3.119.43 1.3.121.21 1.3.133.5 1.3.135.29 1.3.135.41 |
MicrosoftEdgeUpdate.exe | 24 | msedge.api.cdp.microsoft.com:443 msedge.b.tlu.dl.delivery.mp.microsoft.com:80 ocsp.digicert.com:80 self.events.data.microsoft.com:443 |
| Microsoft Intune Management Extension | 1.37.200.3 1.38.300.1 1.39.200.3 |
ClientHealthEval.exe Microsoft.Management.Services.IntuneWindowsAgent.exe |
3 | fef.amsub0302.manage.microsoft.com:443 manage.microsoft.com:443 r.manage.microsoft.com:443 |
| Microsoft OneDrive | 19.192.0926.0012 20.114.0607.0002 20.169.0823.0006 20.169.0823.0008 20.201.1005.0009 21.002.0104.0005 |
FileCoAuth.exe OneDrive.exe OneDriveStandaloneUpdater.exe |
132 | am3pap004.storage.live.com:443 api.onedrive.com:443 arc.msn.com:443 config.teams.microsoft.com:443 ctldl.windowsupdate.com:80 g.live.com:443 login.live.com:443 login.microsoftonline.com:443 logincdn.msauth.net:443 mobile.pipe.aria.microsoft.com:443 ocsp.digicert.com:80 oneclient.sfx.ms:443 onedriveclucprodbn20007.blob.core.windows.net:443 onedriveclucprodbn20010.blob.core.windows.net:443 onedriveclucprodbn20036.blob.core.windows.net:443 onedriveclucproddm20012.blob.core.windows.net:443 onedriveclucproddm20013.blob.core.windows.net:443 onedriveclucproddm20030.blob.core.windows.net:443 par02p.wns.windows.com:443 skydrive.wns.windows.com:443 status.rapidssl.com:80 sv.symcb.com:80 v10.events.data.microsoft.com:443 www.microsoft.com:80 |
| Microsoft Update Health Tools | 2.70.0.0 | uhssvc.exe | 1 | payloadprod15.blob.core.windows.net:443 |
| Microsoft Windows Malicious Software Removal Tool | 5.85.17731.1 5.86.17836.1 |
MRT.exe | 7 | wdcp.microsoft.com:443 wdcpalt.microsoft.com:443 |
| Microsoft Windows OS | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
AppHostRegistrationVerifier.exe BitLockerDeviceEncryption.exe CompatTelRunner.exe DeviceCensus.exe DeviceEnroller.exe EngHost.exe InstallAgentUserBroker.exe LogonUI.exe MoUsoCoreWorker.exe RuntimeBroker.exe SIHClient.exe SettingSyncHost.exe SpeechModelDownload.exe SpeechRuntime.exe UpdateNotificationMgr.exe WaaSMedicAgent.exe WerFault.exe backgroundTaskHost.exe browser_broker.exe cleanmgr.exe cmd.exe dmclient.exe dxgiadaptercache.exe explorer.exe lsass.exe omadmclient.exe powershell_ise.exe rundll32.exe signtool.exe slui.exe smartscreen.exe svchost.exe taskhostw.exe usocoreworker.exe wermgr.exe wuauclt.exe |
895 | 11.au.download.windowsupdate.com:80 11.tlu.dl.delivery.mp.microsoft.com:80 2.au.download.windowsupdate.com:80 2.tlu.dl.delivery.mp.microsoft.com:80 3.au.download.windowsupdate.com:80 3.tlu.dl.delivery.mp.microsoft.com:80 7.au.download.windowsupdate.com:80 9.au.download.windowsupdate.com:80 9.tlu.dl.delivery.mp.microsoft.com:80 adl.windows.com:80 array507.prod.do.dsp.mp.microsoft.com:443 array508.prod.do.dsp.mp.microsoft.com:443 array509.prod.do.dsp.mp.microsoft.com:443 array601.prod.do.dsp.mp.microsoft.com:443 array607.prod.do.dsp.mp.microsoft.com:443 array614.prod.do.dsp.mp.microsoft.com:443 array809.prod.do.dsp.mp.microsoft.com:443 array810.prod.do.dsp.mp.microsoft.com:443 array812.prod.do.dsp.mp.microsoft.com:443 au.download.windowsupdate.com:80 bg2.v4.a.dl.ws.microsoft.com:80 bg2.v4.emdl.ws.microsoft.com:80 bg4.ds.a.dl.ws.microsoft.com:80 bg4.ds.emdl.ws.microsoft.com:80 bg5.v4.a.dl.ws.microsoft.com:80 bg5.v4.emdl.ws.microsoft.com:80 browser.events.data.msn.com:443 browser.pipe.aria.microsoft.com:443 ccs.play.king.com:443 cdn.onenote.net:443 checkappexec.microsoft.com:443 client.wns.windows.com:443 clients2.google.com:443 collections.mp.microsoft.com:443 cp501.prod.do.dsp.mp.microsoft.com:443 cp601.prod.do.dsp.mp.microsoft.com:443 cp801.prod.do.dsp.mp.microsoft.com:443 crl.comodoca.com:80 crl.identrust.com:80 crl3.digicert.com:80 crl4.digicert.com:80 cs.dds.microsoft.com:443 ctldl.windowsupdate.com:80 d23iz4esrwkib6.cloudfront.net:80 db3pap001.settings.live.net:443 db3pap001.storage.live.com:443 disc501.prod.do.dsp.mp.microsoft.com:443 disc601.prod.do.dsp.mp.microsoft.com:443 disc801.prod.do.dsp.mp.microsoft.com:443 discover.aadrm.com:443 displaycatalog.mp.microsoft.com:443 dl.delivery.mp.microsoft.com:80 dmd.metaservices.microsoft.com:80 download.windowsupdate.com:80 emdl.ws.microsoft.com:80 enrollment.manage.microsoft.com:443 enterpriseregistration.windows.net:443 fe2.update.microsoft.com:443 fe2.ws.microsoft.com:443 fe2cr.update.microsoft.com:443 fe3.delivery.mp.microsoft.com:443 fe3cr.delivery.mp.microsoft.com:443 fef.amsub0302.manage.microsoft.com:443 fs.microsoft.com:443 g.live.com:443 geo.prod.do.dsp.mp.microsoft.com:443 geover.prod.do.dsp.mp.microsoft.com:443 go.microsoft.com:443 go.microsoft.com:80 has.spserv.microsoft.com:443 iecvlist.microsoft.com:443 inference.location.live.net:443 kv501.prod.do.dsp.mp.microsoft.com:443 kv601.prod.do.dsp.mp.microsoft.com:443 kv801.prod.do.dsp.mp.microsoft.com:443 licensing.mp.microsoft.com:443 login.live.com:443 login.live.com:80 login.microsoftonline.com:443 login.microsoftonline.us:443 login.partner.microsoftonline.cn:443 login.windows-ppe.net:443 login.windows.net:443 manage.devcenter.microsoft.com:443 manage.microsoft.com:443 maps.windows.com:443 mobile.pipe.aria.microsoft.com:443 msdl.microsoft.com:443 msedge.b.tlu.dl.delivery.mp.microsoft.com:80 msedge.f.dl.delivery.mp.microsoft.com:80 nav.smartscreen.microsoft.com:443 ocsp.comodoca.com:80 ocsp.digicert.cn:80 ocsp.digicert.com:80 ocsp.globalsign.com:80 ocsp.godaddy.com:80 ocsp.msocsp.com:80 ocsp.sectigo.com:80 ocsp2.globalsign.com:80 officecdn.microsoft.com.edgesuite.net:80 officecdn.microsoft.com:80 oneclient.sfx.ms:443 onegetcdn.azureedge.net:443 oneocsp.microsoft.com:80 outlook.office365.com:443 par02p.wns.windows.com:443 pool.ntp.org:123 portal.manage-dogfood.microsoft.com:443 portal.manage-ppe.microsoftonline.cn:443 portal.manage-selfhost.microsoft.com:443 portal.manage.microsoft.us:443 portal.manage.microsoftonline.cn:443 pti.store.microsoft.com:443 purchase.mp.microsoft.com:443 r.manage.microsoft.com:443 r1—sn-4g5e6nlk.gvt1.com:80 r1—sn-4g5e6nzz.gvt1.com:80 r1—sn-4g5ednle.gvt1.com:80 r2—sn-4g5e6nsz.gvt1.com:80 r2—sn-4g5edne7.gvt1.com:80 r2—sn-4g5ednsk.gvt1.com:80 r3—sn-4g5e6nez.gvt1.com:80 r3—sn-4g5e6nzs.gvt1.com:80 r3.o.lencr.org:80 r4—sn-4g5e6nsz.gvt1.com:80 r5—sn-4g5edns6.gvt1.com:80 redirector.gvt1.com:80 self.events.data.microsoft.com:443 settings-win.data.microsoft.com:443 settings.data.microsoft.com:443 share.microsoft.com:443 sls.update.microsoft.com:443 slscr.update.microsoft.com:443 smartscreen-prod.microsoft.com:443 statsfe2.update.microsoft.com:80 statsfe2.ws.microsoft.com:80 storage.googleapis.com:443 storage.googleapis.com:80 store-images.s-microsoft.com:80 storecatalogrevocation.storequality.microsoft.com:443 substrate.office.com:443 sv.symcd.com:80 telecommand.telemetry.microsoft.com:443 tile-service.weather.microsoft.com:80 timestamp.digicert.com:80 to-do.microsoft.com:443 tsfe.trafficshaping.dsp.mp.microsoft.com:443 updates.logitech.com:80 v10.events.data.microsoft.com:443 v10.vortex-win.data.microsoft.com:443 v20.events.data.microsoft.com:443 validation-v2.sls.microsoft.com:443 vsblobprodscussu5shard10.blob.core.windows.net:443 vsblobprodscussu5shard12.blob.core.windows.net:443 vsblobprodscussu5shard26.blob.core.windows.net:443 vsblobprodscussu5shard3.blob.core.windows.net:443 vsblobprodscussu5shard50.blob.core.windows.net:443 vsblobprodscussu5shard67.blob.core.windows.net:443 vsblobprodscussu5shard88.blob.core.windows.net:443 watson.telemetry.microsoft.com:443 whiteboard.microsoft.com:443 whiteboard.ms:443 windows.policies.live.net:443 www.microsoft.com:80 www.powershellgallery.com:443 www.telecommandsvc.microsoft.com:443 |
| Microsoft.549981C3F5F10 | 2.2007.24732.0 | Cortana.exe | 1 | settings-win.data.microsoft.com:443 |
| Microsoft.People | 10.1909.10841.0 10.1909.12456.0 |
backgroundTaskHost.exe | 4 | graph.microsoft.com:443 ocsp.digicert.com:80 |
| Microsoft.ServiceHub.Controller | 1.3.2175297764 2.7.1004420301 |
Microsoft.ServiceHub.Controller.exe | 3 | az667904.vo.msecnd.net:443 az700632.vo.msecnd.net:443 az779572.vo.msecnd.net:443 az861674.vo.msecnd.net:443 msedge.b.tlu.dl.delivery.mp.microsoft.com:443 vortex.data.microsoft.com:443 |
| Microsoft.Windows.ContentDeliveryManager | 10.0.18362.449 10.0.19041.423 |
BackgroundTransferHost.exe backgroundTaskHost.exe |
33 | arc.msn.com:443 crl3.digicert.com:80 img-prod-cms-rt-microsoft-com.akamaized.net:443 mucp.api.account.microsoft.com:443 ocsp.digicert.com:80 ris.api.iris.microsoft.com:443 sv.symcb.com:80 |
| Microsoft.Windows.Cortana | 1.13.0.18362 | SearchUI.exe backgroundTaskHost.exe |
12 | b-ring.msedge.net:443 eafddirect.msedge.net:443 fp-vp-nocache.azureedge.net:443 fp.msedge.net:443 l-ring.msedge.net:443 msedge.b.tlu.dl.delivery.mp.microsoft.com:443 ocsp.digicert.com:80 r.bing.com:443 www.bing.com:443 |
| Microsoft.Windows.Photos | 2020.20070.10002.0 2020.20110.11001.0 |
Microsoft.Photos.exe | 8 | api.onedrive.com:443 crl3.digicert.com:80 db3pap001.settings.live.net:443 db3pap001.storage.live.com:443 evoke-windowsservices-tas.msedge.net:443 ocsp.digicert.com:80 outlookmobile-office365-tas.msedge.net:443 settings-win.data.microsoft.com:443 settings.data.microsoft.com:443 storage.live.com:443 visualstudio-devdiv-c2s.msedge.net:443 |
| Microsoft.Windows.Search | 1.14.0.19041 | SearchApp.exe | 26 | ocsp.digicert.com:80 outlook.office365.com:443 r.bing.com:443 substrate.office.com:443 www.bing.com:443 |
| Microsoft.WindowsFeedbackHub | 1.2006.10051.0 | PilotshubApp.exe | 3 | ocsp.digicert.com:80 settings-win.data.microsoft.com:443 uif.microsoft.com:443 |
| Microsoft.WindowsStore | 12008.1001.1.0 12011.1001.1.0 |
WinStore.App.exe | 42 | assets.onestore.ms:443 cid-ef9da447e9880355.users.storage.live.com:443 cid-fd728fd8cdb9865d.users.storage.live.com:443 img-prod-cms-rt-microsoft-com.akamaized.net:443 livetileedge.dsx.mp.microsoft.com:443 maps.windows.com:443 ocsp.digicert.com:80 status.rapidssl.com:80 store-images.s-microsoft.com:443 store-images.s-microsoft.com:80 storeedgefd.dsx.mp.microsoft.com:443 www.microsoft.com:443 |
| Microsoft.XboxGamingOverlay | 5.420.11102.0 5.420.8043.0 |
BackgroundTransferHost.exe GameBar.exe |
22 | crl3.digicert.com:80 dlassets-ssl.xboxlive.com:443 ocsp.digicert.com:80 settings-win.data.microsoft.com:443 settings.data.microsoft.com:443 www.xboxab.com:443 |
| Microsoft.YourPhone | 1.20081.116.0 1.20082.141.0 1.20112.72.0 1.20122.119.0 1.21011.101.0 1.21011.127.0 |
YourPhone.exe backgroundTaskHost.exe |
2 | crl3.digicert.com:80 evoke-windowsservices-tas.msedge.net:443 ocsp.digicert.com:80 ocsp.omniroot.com:80 outlookmobile-office365-tas.msedge.net:443 visualstudio-devdiv-c2s.msedge.net:443 |
| Microsoft.ZuneMusic | 10.20122.11121.0 | Music.UI.exe | 2 | cloudcollection-ssl.xboxlive.com:443 musicimage.xboxlive.com:443 |
| Microsoft.ZuneVideo | 10.20032.16211.0 10.20112.10111.0 |
Video.UI.exe | 5 | crl3.digicert.com:80 ocsp.digicert.com:80 settings-ssl.xboxlive.com:443 |
| Network Location Awareness | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 1 | www.msftconnecttest.com:80 |
| Skype | 8.63 8.67 8.68 |
Skype.exe | 135 | a-ring.msedge.net:443 a.config.skype.com:443 api.aps.skype.com:443 api.asm.skype.com:443 api3.cc.skype.com:443 avatar.skype.com:443 azeus1-client-s.gateway.messenger.live.com:443 b-ring.msedge.net:443 b.config.skype.com:443 browser.pipe.aria.microsoft.com:443 client-s.gateway.messenger.live.com:443 config.edge.skype.com:443 consumer.entitlement.skype.com:443 contacts.skype.com:443 download.visualstudio.microsoft.com:443 edge.skype.com:443 flighting.cc.skype.com:443 fp.config.skype.com:443 fpc.msedge.net:443 get.skype.com:443 go.trouter.skype.com:443 ic3.events.data.microsoft.com:443 k-ring.msedge.net:443 login.live.com:443 login.microsoftonline.com:443 mobile.pipe.aria.microsoft.com:443 ms-dotnettools.gallerycdn.vsassets.io:443 msgsearch.skype.com:443 options.skype.com:443 outlook.live.com:443 people.skype.com:443 pipe.skype.com:443 pnv.skype.com:443 prod.registrar.skype.com:443 s-ring.msedge.net:443 static-asm.secure.skypeassets.com:443 static.asm.skype.com:443 trouter-neu-a.trouter.skype.com:443 trouter-neu-b.trouter.skype.com:443 v10.events.data.microsoft.com:443 v20.events.data.microsoft.com:443 www.msftconnecttest.com:80 |
| SysInfoCap | 1.28.2197.0 | SysInfoCap.exe | 6 | ctldl.windowsupdate.com:80 ocsp.digicert.com:80 |
| Update Orchestrator Service | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 4 | settings-win.data.microsoft.com:443 settings.data.microsoft.com:443 |
| Windows Defender | 4.10.0209.0 4.18.2011.6 4.18.2101.4 4.18.2101.8 4.18.2101.9 |
MpCmdRun.exe MsMpEng.exe |
15 | definitionupdates.microsoft.com:443 go.microsoft.com:443 go.microsoft.com:80 wdcp.microsoft.com:443 wdcpalt.microsoft.com:443 www.microsoft.com:443 |
| Windows Insider Service | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 |
svchost.exe | 2 | settings-win.data.microsoft.com:443 settings.data.microsoft.com:443 |
| Windows Installer – Unicode | 5.0.14393.2430 5.0.19041.1 |
msiexec.exe | 2 | ocsp.digicert.com:80 payloadprod15.blob.core.windows.net:443 |
| Windows License Manager Service | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 21 | licensing.mp.microsoft.com:443 storecatalogrevocation.storequality.microsoft.com:443 substrate.office.com:443 |
| Windows Push Notifications System Service | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 |
svchost.exe | 2 | client.wns.windows.com:443 |
| Windows Push Notifications User Service | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 168 | assets.msn.com:443 cdn.content.prod.cms.msn.com:80 cdn.onenote.net:443 service.weather.microsoft.com:443 spclient.wg.spotify.com:443 tile-service.weather.microsoft.com:80 |
| Windows PushToInstall Service | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 |
svchost.exe | 2 | exchange-assets.azureedge.net:443 pti.store.microsoft.com:443 |
| Windows Time | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 1 | time.windows.com:123 |
| Windows Update | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 173 | 11.au.download.windowsupdate.com:80 11.tlu.dl.delivery.mp.microsoft.com:80 2.au.download.windowsupdate.com:80 3.au.download.windowsupdate.com:80 au.download.windowsupdate.com:80 ctldl.windowsupdate.com:80 dl.delivery.mp.microsoft.com:80 download.windowsupdate.com:80 fe2.update.microsoft.com:443 fe2cr.update.microsoft.com:443 fe3.delivery.mp.microsoft.com:443 fe3cr.delivery.mp.microsoft.com:443 officecdn.microsoft.com.edgesuite.net:80 settings-win.data.microsoft.com:443 sls.update.microsoft.com:443 slscr.update.microsoft.com:443 substrate.office.com:443 tsfe.trafficshaping.dsp.mp.microsoft.com:443 |
| Windows Update Medic Service | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 2 | settings-win.data.microsoft.com:443 settings.data.microsoft.com:443 |
| WpnUserService | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 7601 9600 |
svchost.exe | 10 | assets.msn.com:443 cdn.content.prod.cms.msn.com:80 service.weather.microsoft.com:443 tile-service.weather.microsoft.com:80 |
| Xbox Live Auth Manager | 14393.4169 14393.4225 17763.1697 17763.1757 18363.1316 18363.1379 19041.746 19041.804 19042.746 19042.789 19042.804 |
svchost.exe | 14 | device.auth.xboxlive.com:443 title.auth.xboxlive.com:443 title.mgt.xboxlive.com:443 user.auth.xboxlive.com:443 xsts.auth.xboxlive.com:443 |
| microsoft.microsoftskydrive | 19.23.11.0 | WWAHost.exe | 37 | browser.pipe.aria.microsoft.com:443 ocsp.digicert.com:80 |
| microsoft.windowscommunicationsapps | 16005.13426.20368.0 16005.13426.20566.0 |
HxTsr.exe | 52 | evoke-windowsservices-tas.msedge.net:443 ocsp.digicert.com:80 ocsp.globalsign.com:80 oneocsp.microsoft.com:80 outlook.office.com:443 outlook.office365.com:443 outlookmobile-office365-tas.msedge.net:443 settings-win.data.microsoft.com:443 settings.data.microsoft.com:443 www.microsoft.com:80 |
| windows.immersivecontrolpanel | 10.0.2.1000 | SystemSettings.exe | 15 | cxcs.microsoft.net:443 ocsp.digicert.com:80 onecs-live.azureedge.net:443 r.bing.com:443 www.bing.com:443 |
Introduction
Welcome, since I’ve been working with a number of clients using Windows Analytics I thought I would share some tips on getting up and running plus make sense of all the ways it can be configured. This blog series reviews the strategy and steps I have used to configure device telemetry for Windows Analytics with various organizations. And to add a twist I’ve decided to break with my tradition of making mega blog articles and break this one up into the following posts.
- Part 1: Prerequisites
- Part 2: Configuring Azure Log Analytics
- Part 3: Configuring Windows Analytics with Group Policy
- Part 4: Configuring Windows Analytics with SCCM
- Part 5: Configuring Windows Analytics with Intune
- Part 6: Using an MSI to enroll in Windows Analytics
Before we get into the technical weeds I’d like to take a moment to say that I have been busy helping organizations implement and assess their environment using this toolset for a variety of initiatives. This tool has been great in getting insights for organizations making the journey to Windows 10 but it also lives on as a tool to help you navigate the world of Windows as a Service.
No tool I have found for assessing application compatibility, software inventory and hardware inventory is perfect but considering that the base product is included with your Windows license you get a fair bit of information about your environment for using a free solution. I find once I get the solution deployed across the organization there is something of value for every customer so try to approach this with an open mind.
To sum it up Windows Analytics is a collection of Azure Log Analytics solutions that process telemetry from Windows clients for different solutions to analyze the data. The high-level architecture can be envisioned as follows:
- Client computers with the correct compatibility KB are configured to report data to Windows Analytics
- The Microsoft Data Management Service runs in secure data centers and collects the telemetry data sent to this service
- The Upgrade Readiness service processes the telemetry data
- On a nightly basis, the Azure Log Analytics workspace receives data from the Upgrade Readiness Service
- Using solutions provisioned to the Azure Log Analytics workspace the administrators can view various aspects of the telemetry to help with activities such as Windows Servicing
Azure Log Analytics
Usually, I avoid using an existing Azure Log Analytics workspace for Windows Analytics. What I find is that most workspaces are being used for server management, DevOps or application specific logging. I find that is it worthwhile to give this some thought to how you envisioning the usage of Azure Log Analytics in your organization. I could go down a rabbit hole with this one because you can add other data sources to the workspace but I suggest keeping it simple and only having one workspace for Windows Analytics in your tenant.
I’ll illustrate what is needed to deploy Azure Log Analytics in the next blog article and I would suggest reading that to help visualize the overall implementation before you start making design decisions.
Group Policy
In some environments, I’ve had conflicts with Group Policy settings so before going down the path of implementing anything I highly recommend that you check for and aware of what has been set in your environment. Under Computer Configuration open the Administrative
Templates, Windows Components then Data Collection and Preview Builds.
Note anything that is enabled especially the following settings:
- Allow device name to be sent in diagnostic data
- Allow Telemetry
- Configure the Commercial ID
- Configure collection of browsing data for Microsoft 365 Analytics
- Configure Microsoft 365 Update Readiness upload endpoint
- Configure Authenticated Proxy usage for Connected User Experience and Telemetry Service
- Configure collection of browsing data for Microsoft 365 Analytics
SCCM Policy
Next if using SCCM check to see if a client policy is configuring Windows Analytics.
Outbound Firewall/Proxy Configuration
Use the following guide to determine which endpoints need to be whitelisted in your organization.
Purpose: Windows Analytics
Purpose: Device Health
| Endpoint | Function |
| https://oca.telemetry.microsoft.com | Online Crash Analysis; required for Device Health reports. Not used by Upgrade Readiness or Update Compliance AV reports. |
| https://login.live.com | This endpoint is required by Device Health to ensure data integrity and provides a more reliable device identity for all of the Windows Analytics solutions on Windows 10. If you want to disable end-user managed service account (MSA) access, you should apply the appropriate policy instead of blocking this endpoint. |
Purpose: Device Health and Windows Error Reporting
Windows Client Requirements
Each endpoint will need to me the following requirements in order to support the collection and transmission of telemetry data for Windows Analytics.
| OS | Requirements |
| Windows 10 | No action needed, Windows 10 comes with the necessary sensors to deliver the required telemetry data. |
| Windows 8.1 | The following KB must be deployed. Compatibility update for keeping Windows up-to-date in Windows 8.1 https://support.microsoft.com/kb/2976978. |
| Windows 7 SP1 | The following KB must be deployed. Compatibility update for keeping Windows up-to-date in Windows 7 https://support.microsoft.com/kb/2952664. |
Licensing
For Upgrade Readiness the solution is covered under your standard Windows license however not everything I am about to configure is covered by this license.
Device Health
- Windows 10 Enterprise or Windows 10 Education per-device with active Software Assurance
- Windows 10 Enterprise E3 or E5 per-device or per-user subscription (including Microsoft 365 F1, E3, or E5)
- Windows 10 Education A3 or A5 (including Microsoft 365 Education A3 or A5)
- Windows VDA E3 or E5 per-device or per-user subscription
Update Compliance
-
Windows Defender
- Windows E3 license
- Cloud protection must be enabled
Organizations with a Windows E5 license should have Windows Defender ATP deployed and be looking for similar data in the Windows Defender ATP portal.
Part 1 Conclusion
As you can see there is a fair bit of work to do before you begin but I recommend going through the motions before proceeding to any of the implementation steps. Next, I’ll go into Azure Log Analytics in more detail and show you the steps necessary to get the backend up and running.




